How to hack android phones with Phonesploit
Last Updated :
14 Oct, 2024
Understanding how to hack Android phones with Phonesploit has become a topic of interest and concern. Phonesploit is a powerful tool that allows users to remotely access and control Android devices, offering capabilities ranging from retrieving sensitive information to executing commands on the target device. This tool leverages vulnerabilities in Android's debugging interface, ADB, to gain unauthorized access.
Whether for ethical testing or malicious intent, knowing about Phonesploit is crucial in understanding mobile security risks and defenses. This article explores the workings of Phonesploit in simple terms, highlighting its implications and precautions for both users and security professionals alike.
What is PhoneSploit?
PhoneSploit Pro is a powerful open-source tool written in Python language to remotely exploit Android devices using ADB (Android Debug Bridge) and Metasploit-Framework. It comes with Metasploit Integration. With only one click, this tool can fully hack an Android smartphone by automatically creating, installing, and running a payload on the target device using the Metasploit Framework and ADB.
This project aims to simplify Android device penetration testing. Now PhoneSploit Pro handles learning commands and parameters for you. You may quickly test the security of your Android devices using this tool.
 Main Menu
Main MenuRequirements for PhoneSploit:
- Kali Linux: Recommended for penetration testing due to pre-installed tools like Metasploit.
- Metasploit: Essential for generating and executing payloads.
- Python3: Python 3.10 or Newer
- ADB: Android Debug Bridge (ADB) from Android SDK Platform Tool.
- Scrcpy: A tool that provides screen mirroring for Android devices.
- Nmap: A network scanning tool, useful for identifying open ports on target devices.
Steps to Install PhoneSploit for Android
Step 1: Clone the GitHub Repository
On your Linux system, move to the Desktop directory and clone the GitHub repository by entering the below command.
cd Desktop
git clone https://github.com/AzeemIdrisi/PhoneSploit-Pro.git
 Installation
InstallationNow after cloning into PhoneSploit-Pro, move to the tool directory and list the files inside it.
cd PhoneSploit-Pro
ls
Run the tool by entering the command given below.
sudo python3 phonesploitpro.py
 Running Tool
Running ToolBefore using PhoneSploit, you need to configure the Developer Options and enable USB Debugging on the target Android device.
Step 1: Enabling the Developer Options
- Open Settings.
- Go to About Phone.
- Find the Build Number.
- Tap on Build Number 7 times.
- Enter your pattern, PIN, or password to enable the Developer options menu.
- The Developer options menu will now appear in your Settings menu.
Step 2: Enabling USB Debugging
- Open Settings.
- Go to System > Developer options.
- Scroll down and Enable USB debugging.
After enabling USB debugging, Now Connect the device to the host computer with a USB cable. After connecting the Android device to the computer, Return back to the tool terminal:
 Main Menu
Main MenuExample 1: Mirror and Control Device
Step 1: Let's first Mirror & Control Device, Enter the 5th option for it.
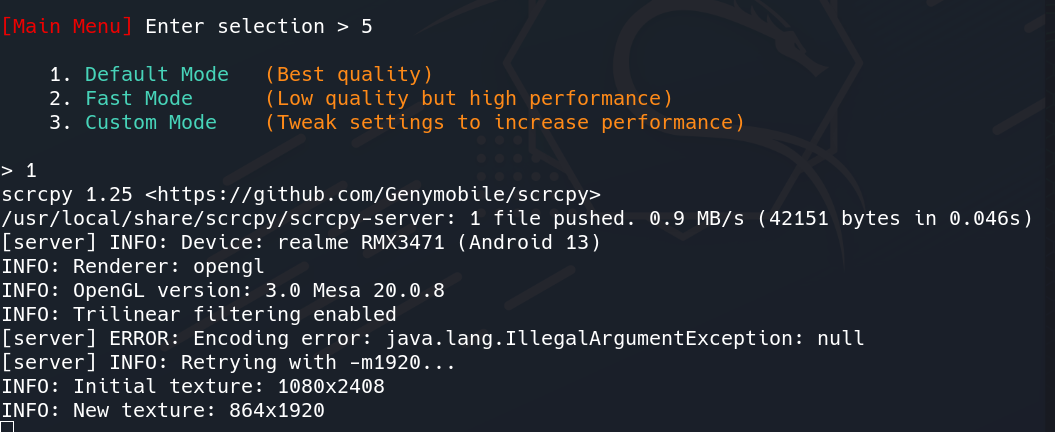 Creating Mirror & Control Device
Creating Mirror & Control DeviceStep 2: After that, it will ask for the quality of the casting. Let's choose the Best Quality by entering option 1. A pop-up will come on your Android Device asking to allow USB debugging.
 Allowing USB Debugging
Allowing USB DebuggingWhen you click on allow, it will start casting your Device to the System.
 Casting of Device
Casting of DeviceExample 2: Hacking the Device
Let's now move to another feature of this tool which is the best among others i.e. hacking the device
Step 1: Enter option 15 in the main menu i.e. Hack Device. (Our Android phone must be connected to the system).
 Hack Device Feature
Hack Device FeatureMetasploit-Framework will be launched. Wait for 10 seconds.
 Launching Metasploit
Launching MetasploitStep 2: Continuing the process of APK creation using the tool.
 Creating APK
Creating APKStep 3: We can Modify LHOST and LPORT by typing M or just pressing Enter. After that, it will ask for setting up a database, for storing the payload.
 Installing APK to Target Device
Installing APK to Target DeviceStep 4: Now the tool has started installing the payload APK to the device. A pop-up will come on your Android Device which will ask you to allow for installing the APK.
 Payload APK Installation
Payload APK InstallationStep 5: Select the install anyway option or you can turn off google play protect in google play settings to skip this step. After installation, the tool will now open the app asking for various permissions.
 Granting Permissions
Granting PermissionsStep 6: Allow all the permissions and click on continue to successfully install the payload APK.
 Launching App
Launching AppStep 5: Now the tool will launch Metasploit-Framework and Meterpreter session will be started automatically. Now unplug the USB cable and further exploit the Android Device.
 Access Gained to Target Device
Access Gained to Target DeviceStep 6: Type help and press enter. It will list all the possible attacks on the device.
 List of Possible attacks
List of Possible attacksStep 7: Type dump_callog to fetch all the call history of the device and store it in your system.
 Fetching Call History
Fetching Call HistoryAs you can see the call log has been dumped and saved in a text file.
Step 8: Type record_mic to record the voice of the surroundings of the Android device.
 Record surrounding voice
Record surrounding voiceThese were examples of exploiting the device and gaining sensitive information about the Android device. There are many more attacks which you can see in the help menu of the meterpreter. You can exit from the session by typing the exit command.
Conclusion
PhoneSploit Pro simplifies the process of exploiting Android devices, making it an essential tool for cybersecurity professionals who need to assess mobile security. Its integration with the Metasploit Framework enables users to automate the creation, installation, and execution of payloads with ease. However, it’s important to use this tool ethically and legally, ensuring that any penetration testing activities are performed with proper authorization.
Similar Reads
How to Install Termux on Android? Termux is a Free and Open-source Terminal Emulator which allows you to work under a Linux environment on Android or IOS Phones. It contains a built-in package manager that enables you to download and set up numerous testing and development apps across your phones. Using its package manager, it autom
2 min read
Phonia - Advanced Toolkits To Scan Phone Numbers Phonia tool is an automated tool used in the process of OSINT for getting the information about the target with the help of a phone number. Phonia tools developed in the Python Language and its available on the GitHub platform. It's free and open-source to use. This tool aims to get accurate results
2 min read
How To Perform Advanced Man-in-the-Middle Attacks with Xerosploit? A man-in-the-middle (MITM) attack is a malicious technique in which an attacker intercepts and possibly alters the communication between two parties by positioning themselves between them. By exploiting vulnerabilities in the communication channel, the attacker gains unauthorized access to sensitive
2 min read
Hacktronian - All in one hacking tool for Linux and Android Hacktronian is a free and open-source tool available on GitHub which is used as an information-gathering tool. Hacktronian is one of the easiest and useful tools for performing reconnaissance on websites and web applications. Hacktronian have different Modules such as information gathering, password
2 min read
How to Install Santoku on a Virtual Machine ? Santoku is a bootable Linux distribution that is focused on mobile forensics, analysis, and security. It comes with pre-installed platform drivers SDKs, and utilities and also allows auto-detection and setup of new connected mobile devices. It is a free and open community project sponsored by NowSec
3 min read
Types of VoIP Hacking and Countermeasures Voice over IP or Voice over Internet Protocol (VoIP) is a collection of different technologies and practices that allows the delivery of voice communication, images, audio, video, through packet data networks over the internet protocol. This makes it very cost-efficient, flexible, and various other
4 min read