End-To-End Asymmetric Encryption of Biomedical Data In-Transit and At-Rest
- 1. End-To-End Asymmetric Encryption of Biomedical Data In-Transit and At-Rest Ryan M Harrison, Ph.D. Head of Engineering BioBright BioIT World Track 13: Data Security 24 May 2017
- 3. Data store 3
- 4. Data store 4
- 6. 6 Data accessibility ad hoc Image Metadata Objective Intranet Excitation Emission Label Reagents Protocols Exp Metadata Analysis MetadataRaw Image
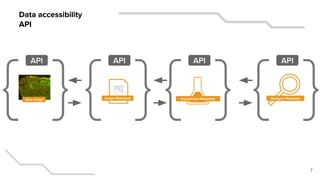
- 7. 7 Raw Image Analysis Metadata Data accessibility API Experiment MetadataImage Metadata API APIAPIAPI
- 8. 8 Encrypted File Encrypted File Decrypted Original File AES AES Internet Intranet Cloud Encryption TLS Original File Encrypted AES Key
- 9. 9 Encrypted File Encrypted File Decrypted Original File AES AES Internet Intranet Cloud Encryption Original File Encrypted AES Key RSA Encrypted AES KeyEncrypted AES Key RSA Encrypted AES Key
- 10. 10 Encrypted File Encrypted File Decrypted Original File AES AES Intranet Cloud Encryption Original File Encrypted AES Key RSA Encrypted AES KeyEncrypted AES Key RSA Encrypted AES Key In-mem On disk
- 11. 11 Encrypted File Encrypted File Decrypted Original File AES AES Intranet Cloud Key management Vendor Original File RSA Encrypted AES Key RSA Encrypted AES Key RSA Pub Key RSA Pri Key
- 12. 12 Encrypted File Encrypted File Decrypted Original File AES AES Intranet Cloud Key management Client Original File RSA RSA Encrypted AES Key Encrypted AES Key Encrypted AES KeyEncrypted AES Key
- 13. 13 Encrypted File Encrypted File Decrypted Original File AES AES Intranet Cloud Key management AWS Key Management Service Original File RSA Encrypted AES Key RSA Encrypted AES Key RSA Pub Key RSA Pri Key Encrypted AES KeyEncrypted AES KeyEncrypted AES KeyEncrypted AES Key
- 16. Considerations 16 ● Data store ● API access ● Encryption ○ Per session ○ Per file ● Key management: Client, Vendor, AWS ● Metadata extraction: Client, Vendor
- 17. Implementation
- 18. Design choices 18 Deployment Cloud-prefered; on-prem optionality Architecture Single-tenant SOA (service-oriented architecture) Key management Vendor Metadata extraction Vendor Sync
- 19. Stack 1 Bio-equipment Co Single tenant 19 Stack 2Pharma Co VPC Bio-equipment Co Stack 1Stack 1 VPC Pharma Co
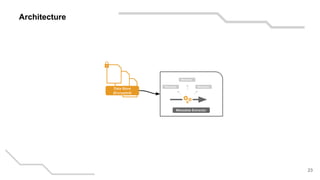
- 20. Architecture 20 Metadata Metadata Metadata Metadata Metadata Metadata Analysis Metadata Image Metadata API API Raw Image API Metadata Metadata Metadata Client Indexing Metadata Extractor Metadata Extractor Data Store (Encrypted)
- 22. Architecture 22 drag file Encrypted File + Initiation Vector AES256-GCM Original File Client Encrypted AES KeyEncrypted AES KeyEncrypted AES Key RSA Pub Key Per Device AES Key Per File Lab Network (Intranet) VPC RDS S3RSA-4096
- 24. Architecture 24 Metadata Metadata Metadata Encrypted File + Initiation Vector Encrypted AES KeyEncrypted AES KeyEncrypted AES Key RSA Pri Key Per Device Decrypted AES Key Decrypted File Stream AES256-GCM RSA-4096 vs RDS RDS S3 Optional: SQS SNS + DynamoDB
- 25. Architecture 25 Raw Image API +vs Service oriented Microservices API Gateway LambdaElastic Beanstalk
- 26. On prem optionality 26 Elastic Beanstalk and or RDS DynamoDB S3 minio vs Pick your poison :-)