Building an Analytics - Enabled SOC Breakout Session
- 1. Copyright © 2014 Splunk Inc. Building an Analytics - Enabled SOC & Best Practices & Demo Joe Goldberg Technical Product Marketing Security, Compliance, Anti-Fraud/Theft/Abuse
- 2. Who Can Benefit From This PPT? Primary: Secondary: 2 Wants to Build a SOC Wants to Enhance Existing SOC Performs SOC-Like Functions
- 3. What is a Security Operations Center (SOC)? 3 PRIMARY GOAL: Reduce risk via improved security SECONDARY GOALS: Compliance, anti-DDOS attack, fraud detection Centralized location(s) where key IT systems of an organization are monitored, assessed and defended from cyber attacks. Security Operations Center
- 4. 4
- 5. Before Building SOC Need to Understand: 5 Significant upfront and ongoing investment of money and time Prerequisite is a certain security maturity level Structure will vary for each organization Important to prioritize and phase the build-out Executive-level and business unit support required
- 6. Three Interrelated Components of a SOC 6 Process PeopleTechnology
- 7. Process
- 8. Threat Modeling & Playbooks 8 • Intellectual property or customer data loss, DDOS, compliance, etc. • Prioritize based on impact 1 What threats does the organization care about? • How it would access and exfiltrate confidential data or harm the network 2 What would the threat look like? • Requires machine data and external context • Searches or visualizations that would detect it (correlated events, anomaly detection, deviations from a baseline, risk scoring) 3 How would we detect/block the threat? • Severity, response process, roles and responsibilities, how to document, how to remediate, when to escalate or close, etc. 4 What is the playbook/process for each type of threat?
- 9. Simplified SOC Tiers TIER 1 • Monitoring • Opens tickets, closes false positives • Basic investigation and mitigation TIER 2 • Deep investigations/CSIRT • Mitigation/recommends changes TIER 3+ • Advanced investigations/CSIRT • Prevention • Threat hunting • Forensics • Counter-intelligence • Malware reverser 9 (MINIMIZE INCIDENTS REACHING THEM) ALERTS FROM: • Splunk • Help Desk • Other IT Depts.
- 10. One vs. Multiple Locations Morning Afternoon Midnight West Coast East Coast APAC One Location Multiple Locations 10 Morning Midnight Afternoon
- 11. Shift Rotations – One Location SHIFT 1 TIER 1 TIER 2 TIER 3 TIER 1 TIER 2 TIER 1 11 SHIFT 2 SHIFT 3 7AM — 5PM 3PM — 1AM 11PM — 9AM Seattle
- 12. Shift Rotations – Multiple Locations SHIFT 1 TIER 1 TIER 2 TIER 3 TIER 1 TIER 2 TIER 1 12 SHIFT 2 SHIFT 3 9AM — 5PM 9AM — 5PM 9AM — 5PM New York Hong KongSeattle TIER 2
- 14. Other Process Items 14 Involve Outside Groups to Assist • Business people, IT teams, SMEs • Threat modeling, investigations, remediation Incorporate Learnings Into the SOC and Organization • Adjust Splunk correlation rules or IT configurations, user education, change business processes Automate Processes • Splunk custom UI to accelerate investigations and alerting, ticketing system
- 15. Demonstrate SOC Value 15 Metrics on events/tickets, resolution time Show reduced business risk via KPIs Regular communication to execs and rest of org Anecdotes of threats defeated
- 16. People
- 17. Types of People 17 Multiple roles with different background, skills, pay levels, personalities SOC Director SOC Manager SOC Architect Tier 1 Analyst Tier 2 Analyst Tier 3 Analyst Forensics Specialist Malware Engineer Counter- Intel On-the-job training and mentoring, and external training & certifications Need motivation via promotion path and challenging work Operating hours and SOC scope play key role in driving headcount
- 18. 18 Different Skillsets Needed Role/Title Desired Skills Tier 1 Analyst Few years in security, basic knowledge of systems and networking Tier 2 Analyst Former Tier 1 experience, deeper knowledge of security tools, strong networking / system / application experience, packet analysis, incident response tools Tier 3 Analyst All the above + can adjust the security intelligence platform, knows reverse engineering/threat intelligence/forensics SOC Director Hiring and staffing, interfacing with execs to show value and get resources, establishing metrics and KPIs SOC Architect Experience designing large scale security operations, security tools and processes
- 19. Technology
- 20. Monitoring, Correlations, Alerts Ad Hoc Search & Investigate Custom Dashboards And Reports Analytics And Visualization Developer Platform Meets Key Needs of SOC Personnel Splunk, a Security Intelligence Platform (SIEM + more!) 20 Real-time Machine Data Cloud Apps Servers Email Web Network Flows DHCP/ DNS Custom Apps Badges Intrusion Detection Firewall Data Loss Prevention Anti-Malware Vulnerability Scans Authentication Storage Industrial Control Mobile Threat Feeds Asset Info Employee Info Data Stores Network Segments External Lookups / Enrichment
- 21. Enables Many Security Use Cases SECURITY & COMPLIANCE REPORTING REAL-TIME MONITORING OF KNOWN THREATS DETECTING UNKNOWN THREATS INCIDENT INVESTIGATIONS & FORENSICS FRAUD DETECTION INSIDER THREAT 21
- 22. Flexibility & Performance to Meet SOC Needs SIEM Splunk Data Sources to Index Limited Any technology, device Add Intelligence & Context Difficult Easy Speed & Scalability Slow and limited scale Fast and horizontal scale Search, Reporting, Analytics Difficult and rigid Easy and flexible Anomaly/Outlier Detection and Risk Scoring Limited Flexible Open Platform Closed Open with API and SDKs 22
- 23. Connect the “Data-Dots” to See the Whole Story Persist, Repeat 23 Delivery, Exploit Installation Gain Trusted Access ExfiltrationData GatheringUpgrade (Escalate) Lateral Movement Persist, Repeat Threat Pattern Threat Intelligence Attacker, know C2 sites, infected sites, IOC, attack/campaign intent and attribution • External threat intel • Internal threat intel • Indicators of compromise Network Activity/Security Where they went to, who talked to whom, attack transmitted, abnormal traffic, malware download • Malware sandbox • Web proxy • NetFlow • Firewall • IDS / IPS • Vulnerability scanner Endpoint Activity/Security What process is running (malicious, abnormal, etc.) Process owner, registry mods, attack/malware artifacts, patching level, attack susceptibility • DHCP • DNS • Patch mgmt • Endpoint (AV/IPS/FW) • ETDR • OS logs Authorization – User/Roles Access level, privileged users, likelihood of infection, where they might be in kill chain • Active Directory • LDAP • CMDB • Operating System • Database • VPN, AAA, SSO
- 24. Other SOC Technologies Advanced Incident Response Tools 24 • Packet Capture • Disk Forensics • Reverse Malware Tools Ticketing/Case Management System
- 25. Splunk Enterprise A Security Intelligence Platform
- 26. Reactive Search and Investigate Proactive Monitoring and Alerting Security Situational Awareness Proactive Real-Time Risk Insight Splunk Gives Path to SOC Maturity Technology that enhances all your SOC personnel and processes
- 27. Splunk Can Complement an Existing SIEM Scenario 1 Scenario 2 Scenario 3 INTEGRATION None Splunk feeds SIEM SIEM feeds Splunk LOGGING & SIEM SIEM INVESTIGATIONS / FORENSICS CORRELATIONS / ALERTING / REPORTING SIEM SIEM COMPLIANCE SIEM NOTES May have different data sources going to Splunk vs SIEM Splunk typically sends just subset of its raw data to SIEM Initially, SIEM connectors are on too many hosts to be replaced 27
- 28. Splunk App for Enterprise Security Pre-built searches, alerts, reports, dashboards, workflow Incident Investigations & ManagementDashboards and Reports Statistical Outliers Asset and Identity Aware 28
- 29. Splunk App for ES – How Helps With SOC App for ES Section Function Title Security Posture High level risk, incidents CISO, Tier 1 Incident Review Incident response Tier 1-3 Event Investigators/Stream Deeper incident response Tier 2-3 Advanced Threat Proactive threat hunting Tier 3 Security Domains Proactive threat hunting, reporting Tier 3, Auditors 29
- 30. Key Takeaways SOC requires investment in people, process and technology Splunk Enterprise is a security intelligence platform that can power your SOC Splunk software makes your SOC personnel and processes more efficient 30
- 31. Splunk SOC Assessment/Building Service •Process review tier 1 - 4 •Assess geo coverage and processes •Assess staffing, coverage, shifts, etc •Review ticketing, reporting, continuity •Develop gap assessment •Document road map •SOC maturation document •Peer review •Static analysis review •Dynamic analysis review •Behavioral analysis and review •Timeline and Task Review •Evaluate threat detection models •Input sources priority •Review and confirm monitoring components •Dashboard / View review Visibility Analysis Actions and Processes Document Project Team Security Consultant Project Manager SOC Expert
- 32. Next Steps Read the “Building a SOC with Splunk” technical brief – Splunk.com > Solutions > Security & Fraud Splunk Security Advisory Services – Help assess, build, implement, optimize a SOC – Includes people, process, and technology – Can include how to use Splunk within the SOC Evaluate Splunk Enterprise and the Splunk App for Enterprise Security – Splunk.com > Contact Us 32
- 33. Q&A
- 34. The 6th Annual Splunk Worldwide Users’ Conference September 21-24, 2015 The MGM Grand Hotel, Las Vegas Did you like this session on “Building an Analytics-Enabled SOC”? You should check out these sessions at .conf2015? • Three customer sessions around building a SOC – technology and process • Over 40 sessions just on security, compliance, and anti-fraud/theft/abuse Register at: conf.splunk.com
- 35. The 6th Annual Splunk Worldwide Users’ Conference September 21-24, 2015 The MGM Grand Hotel, Las Vegas • 50+ Customer Speakers • 50+ Splunk Speakers • 35+ Apps in Splunk Apps Showcase • 65 Technology Partners • 4,000+ IT & Business Professionals • 2 Keynote Sessions • 3 days of technical content (150+ Sessions) • 3 days of Splunk University – Get Splunk Certified – Get CPE credits for CISSP, CAP, SSCP, etc. – Save thousands on Splunk education! 35 Register at: conf.splunk.com
- 36. www.splunk.com/apptitude July 20th, 2015 Submission deadline
- 37. We Want to Hear your Feedback! After the Breakout Sessions conclude Text Splunk to 878787 And be entered for a chance to win a $100 AMEX gift card!
- 38. Thank You!
- 39. Appendix
- 40. Ticketing Best Practices Plan Your Queues Think of Automating Escalations Attack/Incident Reports Are Your Receipt 40
- 41. MSSP Model PROS CONS Around the Clock Higher Visibility of the Threat Landscape Dedicated Specialties Lacks Agility Actionable Alerting Does not know your infrastructure 41
- 42. Whiteboard: Splunk SOC/ES Architecture 42 PRESENTER: XXXXXXX Points: • Build from previous architecture • Layer in ES components • Cover ES Search Head – Function – Sizing • Cover TAs – Function – Benefits Offload Search load to Splunk Search Heads Auto load-balanced forwarding to Splunk Indexers Send data from thousands of servers using any combination of Splunk forwarders
- 43. Merge the Entity And Adversary Models Entity Controls SSCM Chef Audit Tripwire AD Monitor GraphingIntel Exposure Nmap Nessus High •Tripwire •Chef •AD Medium •Scans •Intel Low •Nessus •Graphing High •Tripwire •Proxy •Email Medium •DNS •Red Team Low •IDS/IPS •Outbound Recon Nmap OSINT Delivery Proxy Email Exploitation Tripwire IDS/IPS C2 DNS Outbound Mon Intent Red Team 43
- 44. Example: Connecting the “data-dots” Machine data Traffic data Abnormal behavior High confidence event Med confidence event Low confidence event Malware download Program installation Blacklisted IP Malware install Blacklisted IP Malware and endpoint execution data User on machine, link to program and process Sessions across different access points (web, remote control, tunneled) Continued sessions during abnormal hours, periodicity, patterns, etc. Delivery, Exploit Installation Gain Trusted Access ExfiltrationData GatheringUpgrade (Escalate) Lateral movement Threat Intelligence Auth - User Roles Host Activity/Security Network Activity/Security 44
- 45. Sample Job Description – Tier 2/3/CSIRT
- 46. Sample Job Description – Tier 1 SOC
- 47. Security Services What are we doing? 3 Pillars of Security Professional Services – Security Beyond Deployment – Trusted Advisor – Holistic Security Program Security Beyond Deployment Trusted Advisor Holistic Security Program
- 48. Security Services Offerings Breach response SPR (Security Program Review) SOC Assessment / Buildout Validation Services (Partner lead and executed…not offered yet) Security Advisory Services SIEM Migration Services Security Workshop
- 49. Anatomy of an Offering Breach response (Proactive) •Simulate breach •Review and contrast actions and policy adherence •Assess any gaps •Develop gap assessment •Document road map •Map back to customer needs and process review •Peer review •Assess key data tracked •Review false/true positives •Confirm “alert actions” •Interviews •Policy Review •“Tribal knowledge” Review •Compliance requirements •Escalation / Partner interaction Process Review ES / SIEM Assessment Tabletop Exercise Document Project Team ES Consultant Security Consultant Project Manager
- 50. Anatomy of an Offering SPR (Security Program Review) •Validate customer timeline •Review preliminary roadmap •Re-engagement schedule (based on execution of findings) •Develop gap assessment •Document road map •Map back to customer needs and process review •Peer review •Validate best practices •Industry trends assessment •Recent breach review (per industry or customer) •Gap assessment •Interviews •Policy Review •“Tribal knowledge” Review •Compliance requirements •Escalation / Partner interaction Process Review Industry / Vertical Correlation Timeline and Task Review Document Project Team Security Consultant Project Manager Vertical Expert
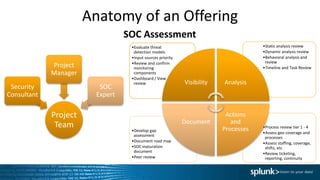
- 51. Anatomy of an Offering SOC Assessment •Process review tier 1 - 4 •Assess geo coverage and processes •Assess staffing, coverage, shifts, etc •Review ticketing, reporting, continuity •Develop gap assessment •Document road map •SOC maturation document •Peer review •Static analysis review •Dynamic analysis review •Behavioral analysis and review •Timeline and Task Review •Evaluate threat detection models •Input sources priority •Review and confirm monitoring components •Dashboard / View review Visibility Analysis Actions and Processes Document Project Team Security Consultant Project Manager SOC Expert
- 52. Anatomy of an Offering Validation Services •Execute mock attack on target(s) •Validate notification on dashboard / reports •Continue additional tests •Create test deliverable •Review deliverable with customer •Peer review •Edit (if necessary) •Duplicate targets and isolate •Confirm tracking and monitoring •Set test window and open any internal tickets •Determine infrastructure •Identify monitored test targets Environment Review Pre-attack Validation Test Execution Document Project Team Security Consultant Project Manager
- 53. Anatomy of an Offering SIEM Migration •Create use cases for 1-to-1 mapping •Develop new use cases for gaps •Deploy services, dashboards, reporting, etc •Develop mapping document •Develop executive summary •Develop end-state document •Peer review •Map current use cases to Splunk use cases •Document new use cases where none exist •Create engagement model •Review current use cases •Review current reporting •Review current dashboards •Review Log sources •Assess current gaps Environment Review Planning and Mapping ExecutionDocument Project Team Security Consultant Project Manager SOC Expert
- 54. Anatomy of an Offering Security Workshop •Review interview notes •Review security policy notes •Review architecture information •Create executive summary •Create abbreviated gap assessment •Peer review •Overview discussion with customer team •Individual interviews to confirm pre-work •Cross-interview assessment •Provide customer with needed information questionnaire •Assess received documents (Architecture, security policies, AUP, etc) Pre-Work Workshop and Interviews Assessmen t Document Project Team Security Consultant Project Manager
Editor's Notes
- #3: “Want to build a SOC” customers are primary audience and others are secondary. But even small orgs with no formal SOC plans can learn from this PPT. The material in this PPT is what our customers across many industries and sizes tend to do. It’s just a summary…precise SOC requirements will be different for each organization.
- #4: Without a SOC there often is siloed, incomplete visibility which leads to a weaker security posture. So by consolidating all the security experts and relevant data into a central location, threats can be spotted faster and efficiencies can be had.
- #5: Without a SOC there often is siloed, incomplete visibility which leads to a weaker security posture. So by consolidating all the security experts and relevant data into a central location, threats can be spotted faster and efficiencies can be had.
- #6: To build a SOC you need basic security products/process in place and tuned (see SANS 20 for examples), as well as enough skilled people to run a SOC. If you do not have a basic level of maturity, you may need to address this first before building a SOC. Prioritization includes: data sources to onboard (onboard the most critical sources first), which threats to model out and look for, playbooks, people, staffing hours (start 8x5 and move to 24/7, etc)
- #7: Any SOC is comprised of people, process, and technology. All 3 are critical to a successful SOC
- #9: This is step one of the SOC build out and prioritizes where to get started. 1. Could also include DDOS, protecting an asset or person, etc. Business people will help you decide this, perhaps based on overall $$ a specific threat could cost the organization. 2. The “indicators of compromise” 3. Includes: machine data to spot the threat (this drives which data sources to prioritize). Also searches needed to detect it (correlated events, anomaly detection, deviations) 4. This is all the detail on what to do when a specific alert is generated. Will vary based on the threat, but the playbook should have a lot of detail so when the alert pops up, everyone knows how to deal with it appropriately. Not shown here, but red team or simulation exercises are helpful to make sure processes work correctly. Red team exercises can also find unknown weaknesses that should be addressed in threat modeling.
- #10: This is a list of the basic process/incident flow in a SOC. Incidents come in at top left. They then are processed by the different Tiers personnel in the SOC. Typically tier-1 analysts are the least skilled analysts. They try to quickly dismiss false positives and for real incidents open a ticket and attempt to remediate the incident. If they cannot remediate it or do not fully understand the threat, they can escalate it to the more skilled tier-2 analysts. These tier-2 analysts often use more advanced tools, such as packet capture tools, to research an incident. Tier 2 tries to investigate/remediate all incidents but if they cannot, they may escalate the incident to the most advanced analysts, the tier 3 analysts. Since Tier 3 analysts are the most skilled and expensive, it is key to limit incidents reaching them to the very “difficult” or critical ones. Notice the responsibilities of the tiers on the right. We will come back to this later and how the proper technology can help with most of these use cases. Tier 2/3 can relay feedback into the rest of the org to improve security Tier 3 may be part of the incident review process, but in some orgs it is not – it is a separate team within the SOC. Also sometimes CSIRT (Computer Security Incident Response Team) is within the SOC as the tier2/2 levels, but sometimes it outside of the SOC and distributed across the organization
- #11: Most do one location. One Location – Better communication easier continuity and management. More expensive as differential for the late hours will have to be paid to employees. Multiple location – harder to work on same issues including language issues, but cheaper as no need for differential pay
- #14: Overlap is key so knowledge is transferred over smoothly and the outgoing shift can bring the incoming shift up to speed. Handover is key – everyone gets into a room and shares what is going on. Agree/disagree on next steps. Shift report is paperwork is a collection of many attack reports. Lists: case worked with comments, ongoing attacks and where they stood
- #15: Have a process for involving business people, other IT and security teams (incl red teams) , and SMEs outside the SOC to help with threat modeling, incident investigations, and remediation. It is key to have the business people involved in telling you what the mission critical apps/data is so you can then protect it. Also, you perhaps can even share machine data or UI access with these other IT teams to help them with their jobs, increase uptime, and to improve collaboration Have a process so learnings are incorporated back into the SOC, IT security, and the organization Adjust correlation rules in the securrity intelligence platform, change product settings and configurations, recommend user education, fix unsafe business processes, etc Automate processes where possible: Use security intelligence platform to prioritize alerts, and give incident investigators interfaces to accelerate reviews. An example could be SOC analyst can type in an IP or user name in a form box on the UI and then get back a lot of relevant info that reflect the playbook. Or a right-click workflow action to grab a PCAP file. Ticketing systems for workflow and incident management
- #16: SOCs require a significant ongoing investment so it is key to show the value of the SOC to keep the resources coming Ongoing metrics to show the value of the SOC could include: Total events, total cases opened and closed, total threats remediated, average time to escalate, average time to remediate number of recommendations the SOC has made to the rest of the organization to reduce risk Show how the SOC has met the original goal of reducing business risk Periodic communication to key stakeholders and others groups to promote the value of the SOC Have meaningful anecdotes and high-level metrics ready to show value to executives
- #18: Need to staff multiple roles. Different background, skills, pay levels, personalities for each role: SOC architect, SOC manager, tier 1 analyst, tier 2 analyst, tier 3 analyst, malware engineer, forensics specialist, counter-intelligence specialist, content developer, etc For tier 2/3 it is helpful to have staff who know the environment well and what “abnormal” looks like. Also staff who are willing to leverage stats to find threats. Provide a promotion path so personnel can move up the tiers. Staffing model drives headcount Some 3rd-party sources indicate a minimum of 7 people are needed for 24x7 monitoring. Others indicate 10 people for 24x7. Another source says for 8x5 at least 2 people are needed. Then again, at large SOCs (for example at a major defense contractor) there can be 50+ people in the SOC and also more than 3 tiers.
- #21: Need a Security Intelligence platform which is a SIEM plus more. We will come back to that later. In summary this platform can automatically sift through hundreds or thousands of daily security-related events to alert on and assign severity levels to only the handful of incidents that really matter. For these incidents, the platform then enables SOC analysts to quickly research and remediate incidents. This platform can ingest any type of machine data, from any source in real time. These are listed here on the left and are flowing into the platform for indexing. The platform should also be able to leverage lookups and external data to enrich existing data. This is showed on the bottom and includes employee information from AD, asset information from a CMDB, blacklists of bad external IPs from 3rd-party threat intelligence feeds, application lookups, and more. Correlation searches can include this external content. So for example the platform can alert you if a low-level employee accesses a file share with critical data, but not if the file share has harmless data. Or the platform can alert you if a user name is used specifically for an employee who no longer works for your organization. These are especially high-risk events. A SOC can then perform the use cases on the top right on the data. These use cases cover all the personnel tiers in the SOC so they can all leverage the platform. They can search through the data, monitor the data and be alerted in real-time if search parameters are met. This includes cross-data source correlation rules which help find the proverbial needle in the haystack so the SOC only needs to focus on the tiny number of priority incidents that matter hidden among a sea of events. The raw data can be aggregated in seconds for custom reports and dashboards. Also the platform should be one that developers can build on. It uses a well documented Rest API and several SDKs so developers and external applications can directly access and act on the data within it.
- #22: The security intelligence platform enables all these use cases. Put in the data once then do all of this. In theory it could also extend to non-security use cases for an even stronger ROI.
- #23: This slide has come from many customers that have used and evaluated multiple SIEM technologies. Traditional SIEMs have limitations because: Only selected data sources can be brought into the system – inflexible. Challenge to support diverse environment, esp if there are custom devices, applications, environments Slow query and reporting, Slow response from reports coming back. Security intelligence platform scalability refers to a flat file data store (not a structured database), distributed search, and installation on commodity hardware. Also the ability to scale out horizontally to handle the largest and most demanding global SOC needs, with the ability to index over 100 TB a day Forced to build custom reporting suite outside of the actual SIEM - out of box functionality looks good, but limited flexibility. Caution, companies that don’t need or want customization will see this as a strength and not a weakness Traditional SIEMs have limited ability to so anomaly detection and risk scoring so it is more difficult to find the advanced threats that evade detection from traditional security products b/c they are not signature based. For these, anomaly detection is helpful to uncover them and their atypical patterns. SIEMS often are closed platforms with no APIs/SDKs, rigid UIs and configuration settings, and difficulty integrating them with other apps in the SOC or IT environment. A security intelligence platform is the opposite with APIs/SDKs, underlying configurations that are all exposed and adjustable, and a flexible UI in XML that can be customized. SOC teams have the full ability to customize the platform to meet their needs and integrate into anything else in the SOC.
- #24: Threats follow the steps at the top right -to-to enter an org and exfiltrate data. To spot this you need to connect the dots as they move through this process. To do this you need data from the 4 data source categories on the far left. Examples are to the right. Note – “malware sandbox” includes FireEye and Palo Alto Network’s Wildfire technology which detonates email and web-based payloads and attachments and links in a virtual sandbox to see what they do & if they are malicious. Sometimes this category is also called “payload analysis” or “advanced malware detection”. ETDR is Endpoint Threat Detection and Response, an emerging category of next-gen endpoint technology. Cyvera (now part of Palo Alto Networks), Carbon Black (part of Bit9), RSA ECAT, Bromium, and Mandiant MIR fall into this category. Tell this slide perhaps as a “story” where you start with an alert at top (threat intel) and then pivot and use the other data sources to complete the investigation. See the appendix slide with a sample story.
- #25: Other specialized tools are needed in a SOC. Other advanced tools for complex incident investigations. A ticketing system to hand off incidents among the SOC tiers.
- #28: In scenario 1 the products are completely standalone. The SIEM alerts and the SOC analysts then walk over to Splunk for the deep investigation. In Scenario 2 it is Splunk feeding the SIEM. Usually the SOC analysts are comfortable with the UI and reports of the existing SIEM so want it in place for correlations/alerting/reporting. Splunk still used for deep investigations. In scenario 3 the existing SIEM feeds Splunk but all SOC use cases are done in Splunk. The existing SIEM is only in place because SIEM connectors to bring in data are on hundreds or thousands of hosts already so removing/replacing them is difficult. Usually with time the organization will start sending data from the sources directly to Splunk, often with the universal forwarder, and eventually the traditional SIEM is retired.
- #29: Over 45 pre-built searches 37 predefined dashboards 160 reports Supporting common security metrics
- #32: SOC Assessment – Utilizing highly experienced SOC consultants, Splunk will review or create an engagement model for the customer specifically designed to provide a detailed “rules of engagement” document for their SOC and usage of Splunk. Depending on the needs of the customer, this can include anything from Core/ES tuning, dashboard and correlation search creation, SOC process flows for notifications and alerts, and tabletop exercises to confirm the processes are being executed upon by SOC analysts. Average engagement size: 3-6 week
- #36: And finally, I would like to encourage all of you to attend our user conference in September. The energy level and passion that our customers bring to this event is simply electrifying. Combined with inspirational keynotes and 150+ breakout session across all areas of operational intelligence, It is simply the best forum to bring our Splunk community together, to learn about new and advanced Splunk offerings, and most of all to learn from one another.
- #41: Have in place strong ticketing/case management system. Think about queues and interaction with groups outside the SOC. If you need to hand a task to a different group keep in mind you may need to open a ticket on their system as well. Also determine how to receive tickets and when to open a ticket Automating escalations is way in the security intelligence platform to automatically grab relevant data for the ticket Attack/Incident Reports is the ticket with all the detail
- #45: An example of an advanced threat. You need data from the 4 data source categories on the far left in order to connect the dots to see the full activity of the threat
- #46: An example of an advanced threat. You need data from the 4 data source categories on the far left in order to connect the dots to see the full activity of the threat
- #47: An example of an advanced threat. You need data from the 4 data source categories on the far left in order to connect the dots to see the full activity of the threat
- #49: Breach response – Using the tools incumbent with Splunk (Bro, Stream, ES, etc), hand-picked security consultants will help a customer identify compromised hosts, origin of breach, malicious payload research and inspection, and gap analysis / remediation recommendations SPR (Security Program Review) – Using a “10,000 foot view,” consultants will review the customer’s current security posture around their Splunk deployment, assess any gaps and pitfalls, create and deliver a remediation and roadmap deliverable, and provide ongoing touchpoints and engagements throughout the life of the SPR. SPRs are not meant to be a tactical engagement type. Instead, they are meant to be long term (1+ years) partnership with the customer to solidify their security posture around their Splunk deployment SOC Assessment – Utilizing highly experienced SOC consultants, Splunk will review or create an engagement model for the customer specifically designed to provide a detailed “rules of engagement” document for their SOC and usage of Splunk. Depending on the needs of the customer, this can include anything from Core/ES tuning, dashboard and correlation search creation, SOC process flows for notifications and alerts, and tabletop exercises to confirm the processes are being executed upon by SOC analysts. Validation Services – Using similar methodologies of penetration testers, Splunk Security Consultants will perform penetration tests (or vulnerability scans) that will validate the dashboards, reports, and alerts identify nefarious activities. This service could also include the creation of breach logs to confirm the implementation of Splunk and the response activities of a customer’s SOC, security team, and/or IT team. Security Advisory Services – An all-encompassing engagement that is meant to be a gap analysis, assessment, deployment, tuning, and ongoing health check all in one. This offering is meant to be a long-term strategy focused engagement with the customer. SIEM Migration Services – An offering that implements the usage of SIEM specific experts to efficiently migrate from one of our competitors to either Core or ES. A secondary path for this service is supplementing Splunk with the information coming from a competing SIEM. Security Workshop – A non-product workshop with the customer to review a customer’s security posture. Can include discussion points such as: governance/compliance, network security (firewall, IDS, endpoint, etc), SOC positioning, and overall security placement. This is meant to be a precursor to additional security services and Splunk license sales.
- #50: Breach response (Proactive) – The point of this offering is to review the customer’s current breach response protocol, confirm their own internal processes, and provide them a path toward better breach response. A common project team would consist of an ES/SIEM consultant, a security consultant, and a project manager. There is a heavy documentation requirement at the end of the engagement that could include a gap assessment, future road map, and could possible include rewritten or new process and procedure documentation for the customer. Average engagement size: 2-4 weeks.
- #51: SPR (Security Program Review) – Using a “10,000 foot view,” consultants will review the customer’s current security posture around their Splunk deployment, assess any gaps and pitfalls, create and deliver a remediation and roadmap deliverable, and provide ongoing touchpoints and engagements throughout the life of the SPR. SPRs are not meant to be a tactical engagement type. Instead, they are meant to be long term (1+ years) partnership with the customer to solidify their security posture around their Splunk deployment Average engagement size: 3-6 weeks which will extend over the lifecycle of the customer (assumed re-engagement on a regular basis)
- #52: SOC Assessment – Utilizing highly experienced SOC consultants, Splunk will review or create an engagement model for the customer specifically designed to provide a detailed “rules of engagement” document for their SOC and usage of Splunk. Depending on the needs of the customer, this can include anything from Core/ES tuning, dashboard and correlation search creation, SOC process flows for notifications and alerts, and tabletop exercises to confirm the processes are being executed upon by SOC analysts. Average engagement size: 3-6 week
- #53: Validation Services – Using similar methodologies of penetration testers, Splunk Security Consultants will perform penetration tests (or vulnerability scans) that will validate the dashboards, reports, and alerts identify nefarious activities. This service could also include the creation of breach logs to confirm the implementation of Splunk and the response activities of a customer’s SOC, security team, and/or IT team. Average engagement size: 2-4 weeks