Workshop Consul .- Service Discovery & Failure Detection
- 1. www.eleven-labs.com WORKSHOP Factory Vincent Composieux @vcomposieux … to beyond and CONSULSERVICE DISCOVERY & FAILURE DETECTION
- 2. 2013 FIRST COMMIT WHAT ABOUT CONSUL? Open-source & built by HashiCorp. “Consul has multiple components, but as a whole, it is a tool for discovering and configuring services in your infrastructure.” GO WRITTEN
- 3. WHAT ABOUT CONSUL? FRONT 01 FRONT 02 FRONT 03 Terminal $ curl http://frontend.eleven-labs.com .. DNS API UP UPDOWN
- 4. WHAT ABOUT CONSUL? SERVICE DISCOVERY ➔ Register new services via configuration or API ➔ Access all available services or a specific one ➔ Updates automatically when new services are available or not FAILURE DETECTION ➔ Updates automatically Consul services when a service is down ➔ Manages services states (we can put a service in maintenance for instance)
- 5. CONSENSUS PROTOCOL http://thesecretlivesofdata.com/raft/ WHAT ABOUT CONSUL? GOSSIP PROTOCOL This is for consistency: nodes inherit from a state: follower, candidate or leader. Propagation of information (epidemy)
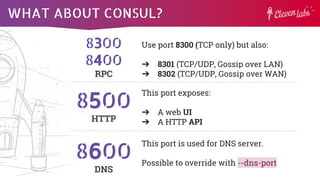
- 6. WHAT ABOUT CONSUL? 8600 DNS 8500 HTTP 8300 8400 RPC Use port 8300 (TCP only) but also: ➔ 8301 (TCP/UDP, Gossip over LAN) ➔ 8302 (TCP/UDP, Gossip over WAN) This port exposes: ➔ A web UI ➔ A HTTP API This port is used for DNS server. Possible to override with --dns-port
- 7. WHAT ABOUT CONSUL? https://demo.consul.io WEB UI LOOKS LIKE THIS
- 9. swarm → registrator → ekofr/http-ip swarm → registrator → ekofr/http-ip ARCHITECTURE CONSUL (Machine / Swarm Discovery) NODE #01 (Machine / Master) NODE #02 (Machine) HTTP DNS 1 2 33 DOCKER MACHINES 1 SWARM CLUSTER 7 DOCKER CONTAINERS
- 10. CONSUL > Machine Terminal $ docker-machine create -d virtualbox consul .. Create the “consul-master” machine under Docker, using the Virtualbox driver. CONSUL (Machine)
- 11. CONSUL > Container Terminal $ eval $(docker-machine env consul) $ docker run -d -p 8301:8301 -p 8302:8302 -p 8400:8400 -p 8500:8500 -p 53:8600/udp consul .. Enter your consul-master environment and run the “consul” Docker image (as server). CONSUL (Machine)
- 12. NODE #01 > Machine (New tab) Terminal $ docker-machine create -d virtualbox --swarm --swarm-master --swarm-discovery="consul://$(docker-machine ip consul):8500" --engine-opt="cluster-store=consul://$(docker-machine ip consul):8500" --engine-opt="cluster-advertise=eth1:2376" swarm-node-01 .. Create the “swarm-node-01” machine under Docker and map Swarm discovery with Consul. CONSUL (Machine) NODE #01
- 13. NODE #01 > Registrator Terminal $ eval $(docker-machine env swarm-node-01) $ docker run -d --volume=/var/run/docker.sock:/tmp/docker.sock gliderlabs/registrator -ip $(docker-machine ip swarm-node-01) consul://$(docker-machine ip consul):8500 .. Enter “swarm-node-01” machine and run a Registrator Docker image as a daemon. CONSUL (Machine) NODE #01
- 14. NODE #01 > HTTP Container Terminal $ docker network create --subnet=172.18.0.0/16 network-node-01 $ docker run -d --net network-node-01 -p 80:8080 ekofr/http-ip .. Create a “network-node-01” Docker network and run “ekofr/http-ip” using this network. CONSUL (Machine) NODE #01
- 15. NODE #02 > Machine (New tab) Terminal $ docker-machine create -d virtualbox --swarm --swarm-discovery="consul://$(docker-machine ip consul):8500" --engine-opt="cluster-store=consul://$(docker-machine ip consul):8500" --engine-opt="cluster-advertise=eth1:2376" swarm-node-02 .. Create the “swarm-node-02” machine under Docker and map Swarm discovery with Consul. CONSUL (Machine) NODE #01 NODE #02
- 16. NODE #02 > Registrator Terminal $ eval $(docker-machine env swarm-node-02) $ docker run -d --volume=/var/run/docker.sock:/tmp/docker.sock gliderlabs/registrator -ip $(docker-machine ip swarm-node-02) consul://$(docker-machine ip consul):8500 .. Enter “swarm-node-02” machine and run a Registrator Docker image as a daemon. CONSUL (Machine) NODE #01 NODE #02
- 17. NODE #02 > HTTP Container Terminal $ docker network create --subnet=172.19.0.0/16 network-node-02 $ docker run -d --net network-node-02 -p 80:8080 ekofr/http-ip .. Create a “network-node-02” Docker network and run “ekofr/http-ip” using this network. CONSUL (Machine) NODE #01 NODE #02
- 18. What’s happening on DNS? Terminal $ dig @$(docker-machine ip consul) http-ip.service.consul .. ;; QUESTION SECTION: ;http-ip.service.consul. IN A ;; ANSWER SECTION: http-ip.service.consul. 0 IN A 192.168.99.100 http-ip.service.consul. 0 IN A 192.168.99.102 Let’s make a DNS call to ensure that our “http-ip” service is available under 2 machines! Shutdown them! DNS
- 19. What’s happening on DNS? Terminal $ dig @$(docker-machine ip consul) http-ip.service.consul SRV .. ;; ANSWER SECTION: http-ip.service.consul. 0 IN SRV 1 1 80 c0a86366.addr.dc1.consul. http-ip.service.consul. 0 IN SRV 1 1 80 c0a86364.addr.dc1.consul. SRV records allows to define a priority and a weight for DNS entries but it is not supported by Consul at this time. You can find more information on SRV records on Wikipedia.
- 20. Add DNS to your system Let’s make an HTTP call to ensure that both nodes answers. Add Consul DNS server as a resolver. CONSUL (Machine)
- 21. Call HTTP service Terminal $ curl http://http-ip.service.consul hello from 172.18.0.2 $ curl http://http-ip.service.consul .. hello from 172.19.0.2 Now, perform your HTTP request and confirm that you are balanced between your two machines. HTTP DNS
- 23. NODE #01 > Add a HTTP check Terminal $ eval $(docker-machine env swarm-node-01) $ docker kill $(docker ps -q --filter='ancestor=ekofr/http-ip') .. First, kill the docker container that runs ekofr/http-ip. We will launch it just after with a health check.
- 24. NODE #01 > Add a HTTP check Terminal $ docker run -d --net network-node-01 -p 80:8080 -e SERVICE_CHECK_SCRIPT="curl -s -f http://$(docker-machine ip swarm-node-01)" -e SERVICE_CHECK_INTERVAL=5s -e SERVICE_CHECK_TIMEOUT=1s ekofr/http-ip .. Add a check to the ekofr/http-ip container. We add a HTTP check here but it could be what you want. More information about Registrator available environment variables here. More information on Consul check definition here.
- 25. NODE #02 > Add a HTTP check Terminal $ eval $(docker-machine env swarm-node-02) $ docker kill $(docker ps -q --filter='ancestor=ekofr/http-ip') .. First, kill the docker container that runs ekofr/http-ip. We will launch it just after with a health check.
- 26. NODE #02 > Add a HTTP check Terminal $ docker run -d --net network-node-02 -p 80:8080 -e SERVICE_CHECK_SCRIPT="curl -s -f http://$(docker-machine ip swarm-node-02)" -e SERVICE_CHECK_INTERVAL=5s -e SERVICE_CHECK_TIMEOUT=1s ekofr/http-ip .. Add a check to the ekofr/http-ip container. We add a HTTP check here but it could be what you want. More information about Registrator available environment variables here. More information on Consul check definition here.
- 27. Check services health via web UI If you launch the UI, you should see your health checks:
- 28. Check services health via API Terminal $ curl http://$(docker-machine ip consul):8500/v1/health/checks/http-ip .. [ { "Status": "passing", "Output": "hello from 172.18.0.2", "ServiceName": "http-ip", }, … ] Note that you can also check your services’s health via the Consul API “/health” endpoint:
- 29. THANK YOU



























![Check services health via API
Terminal
$ curl http://$(docker-machine ip consul):8500/v1/health/checks/http-ip ..
[
{
"Status": "passing",
"Output": "hello from 172.18.0.2",
"ServiceName": "http-ip",
},
…
]
Note that you can also check your services’s health via the
Consul API “/health” endpoint:](https://image.slidesharecdn.com/workshopconsul-170217203117/85/Workshop-Consul-Service-Discovery-Failure-Detection-28-320.jpg)
