Process Whitelisting and Resource Access Control For ICS Computers, Kuniyasu Suzaki of National Institute of AIST and CSSC
- 1. Process Whitelisting And Resource Access Control For ICS Computers Kuniyasu Suzaki National Institute of Advanced Industrial Science and Technology (AIST) & Control System Security Center (CSSC) At S4x14 SCADA Security Scientific Symposium OTDay 14/Jan/2014
- 2. Who am I? • Kuniyasu Suzaki is a researcher of – National Institute of Advanced Industrial Science and Technology (AIST) – Control System Security Center (CSSC) Entrance of Tohoku Tagajo Headquarters (TTHQ) of CSSC
- 3. What is CSSC? ■Outline http://www.css-center.or.jp/ Total 23 corporations (As of Dec, 2013) Control System Security Center • • • • • (Abbreviation) CSSC Name Established ※A corporation authorized by the Minister of Economics, Trade and Industry March 6, 2012 (The registration date) [Tohoku Tagajo Headquarters (TTHQ)] Tagajo City, Miyagi, Japan Location [Tokyo Research Center (TRC)] National Institute of Advanced Industrial Science and Technology Waterfront, Tokyo, Japan Association members (In alphabetical order) • • • • • • • • • • • • • • • • • • *8 starting member corporations Azbil Corporation * Fuji Electric Co., Ltd. FUJITSU LIMITED Hitachi, Ltd.* Information-technology Promotion Agency, Japan (IPA) Japan Quality Assurance Organization(JQA) LAC Co., Ltd. McAfee Co.,Ltd. Mitsubishi Electric Corporation Mitsubishi Heavy Industries Ltd.* Mitsubishi Research Institute Inc.* Mori Building Co., Ltd.* National Institute of Advanced Industrial Science and Technology (AIST) * NEC Corporation NRI Secure Technologies Ltd. NTT Corporation OMRON Corporation The University of Electro-Communications, Tohoku Information Systems Company, Incorporated Toshiba Corporation* Toyota InfoTechnology Center Co., Ltd. Trend Micro Incorporated Yokogawa Electric Corporation*
- 4. Organization and Activity • Under the supervision of the Steering Committee, 4 task committees were established. • Certification Laboratory (CSSC-CL) has also launched since 01/08/2013. Task Committee Activities R&D and Testbed Task Committee It sets the direction of R&D regarding control system security as well as the construction of testbeds and promotes R&D and leverages the testbeds. Certification and Standardization Task Committee It examines evaluation certification regarding control system security and strategies and policies of standardization. It leverages the testbeds for evaluation certification and standardization. Incident Handling Task Committee It prepares for security incidents in control systems and examines the directions of technical development needed for incident handling including the countermeasures of security incidents. Promotion and Human Resource Development Task Committee It sets the direction of awareness and human resource development for control system security as a technical research association. It enhances situational awareness and promotes human resource development, making the use of the testbeds. CL CSSC-CL Activities It promotes International standard compliance certification. Especially it conducts evaluation/certification of ICS and “Communication Robustness Test” defined in EDSA.
- 5. Testbed of CSSC Process automation systems Factory automation
- 6. Today’s Topic Why white list control is used on ICS? • Contents – Background – OS lockdown by white list control – Implementation detail – Case study on SCADA System
- 7. Background to introduce white list (1/3) • OSes on ICS were changed from Special to Commodity. – Commodity OS is cheap. It has plenty of functions, developers, users and vulnerabilities. – Example: Many SCADA systems on Windows Special OS Commodity OS Functions Few Many Vulnerabilities Few Many Apply White List Technology (Lockdown) inactivate necessary functions Reduce vulnerabilities
- 8. Background to introduce white list (2/3) • Best Effort vs.. Quality Control (Taguchi Method) – Quality Control is not real time processing. • Dispersion of overhead (time delay) must be controlled. – Commodity OS has many security tools(Anti-Virus tools), but they are based on best effort. • There is no guarantee for delay, because the black list must be updated periodically. • ICS systems require predictable delay. – The delay caused by security tools should be predictable.
- 9. Background to introduce white list (3/3) • White list control – The overhead is predictable. – It can add on an existing OS of ICS. • ICS does not need to run many applications. – E.g., SCADA system requires few applications. • White list control orders a lockdown of OS.
- 10. OS Lockdown • Lockdown for malware. • Legitimate applications work well, if necessary computing resources are registered. (1) Process Creation (2) Computing Resources Access from a process
- 11. Function of OS Lockdown (1) Limit the process creation – Parent-child relation • Necessary applications must register its parent applications on a process white list. – Integrity check for binary • SHA-1 of binaries must register to process white list. – [Useful Option] Conflict of interest • If an application must run exclusively with another application, they cannot run at the same time. • It can prevent TOCTOU attack (Time of check to time of use) • False operation is also prevented. – For example, administrator cannot run office applications during SCADA.
- 12. Function of OS Lockdown (2) Limit computing resource access from a process – The computing resources are file, device, and network (IP address and port). • If a relation between a resource and processes is registered to the white list, the resource is accessed from the processes only. – “don’t care” setting • If a resource is not registered, all process can access to it. • It is a request from ICS developers! • Traditional access control is too strict and difficult to make white list (e.g., SELinux). Furthermore, many elements of white list cause access delay. • Availability is important on ICS.
- 13. Example of OS Lockdown Normal OS on HMI Lockdown OS on HMI Process White List (1) A creates B,D, and G. (2) D creates E. (3) E and G cannot run at same time. Resource Access Control Applications have vulnerabilities, and resources have no limitation to use. is opened by A and B. Attack creates malicious C process. A B C creates G process to access the disk. Attack creates malicious C process. A Attack is opened by E and G B C D E No rule for the process creation Attack D E Attack accesses the green file. G creates G process to access the disk. No rule to access the file Attack accesses the green file. G G can be created by A and can access to the disk. However, G cannot run along with E at the same time to protect same resource access.
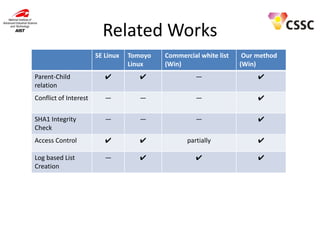
- 14. Related Works SE Linux Tomoyo Linux Commercial white list (Win) Our method (Win) Parent-Child relation ✔ ✔ ― ✔ Conflict of Interest ― ― ― ✔ SHA1 Integrity Check ― ― ― ✔ Access Control ✔ ✔ partially ✔ Log based List Creation ― ✔ ✔ ✔
- 15. Current Implementation • Process creation is implemented by a hook function – PsSetCreateProcessNotifyRoutineEX() • Resource Access control is implemented by Filter Manager PWC and RAC are implemented on Windows OS as device driver. User Space Parent Process Request to create process (system Call) Kernel Space White Child (SHA1)―Parent Request to access resources (system Call) Executive API Hook create process system call by PsSetCreateProcessNotifyRoutine Process List Child Process Process white list module … Executive API Access Control List I/O Manger Process Manger File Creation is denied if no statement on Process White List. Network Device File System Return “CreationStatus” to allow or disallow If process creation is allowed, a child process is created. Filter Manager (Resource Access Control) Device Driver Resource Access is denied if target resource is listed and the access is not allowed.
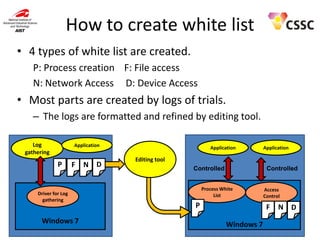
- 16. How to create white list • 4 types of white list are created. P: Process creation F: File access N: Network Access D: Device Access • Most parts are created by logs of trials. – The logs are formatted and refined by editing tool. Log gathering Application P F Driver for Log gathering Windows 7 N D Application Application Editing tool Controlled Controlled Process White List P Access Control F Windows 7 N D
- 17. Sample: Process White List Child process SHA-1 of child process binary Parent process C:WindowsSystem32smss.exe,ad34f33130393425d3d4ce671e0d4488ed8d1b6c,System C:WindowsSystem32autochk.exe,1bd90caff9f3ab1d3cb7136ce9146c1c2e69368b,C:WindowsSystem32smss.exe C:WindowsSystem32smss.exe,ad34f33130393425d3d4ce671e0d4488ed8d1b6c,C:WindowsSystem32smss.exe C:WindowsSystem32csrss.exe,53bc9b2ae89fcad6197ec519ae588f926c88e460,C:WindowsSystem32smss.exe C:WindowsSystem32smss.exe,ad34f33130393425d3d4ce671e0d4488ed8d1b6c,C:WindowsSystem32smss.exe C:WindowsSystem32wininit.exe,c7bba9840c44e7739fb314b7a3efe30e6b25cc48,C:WindowsSystem32smss.exe C:WindowsSystem32csrss.exe,53bc9b2ae89fcad6197ec519ae588f926c88e460,C:WindowsSystem32smss.exe C:WindowsSystem32services.exe,54a90c371155985420f455361a5b3ac897e6c96e,C:WindowsSystem32wininit.exe C:WindowsSystem32lsass.exe,d49245356dd4dc5e8f64037e4dc385355882a340,C:WindowsSystem32wininit.exe C:WindowsSystem32lsm.exe,e16beae2233832547bac23fbd82d5321cfc5d645,C:WindowsSystem32wininit.exe C:WindowsSystem32winlogon.exe,b8561be07a37c7414d6e059046ab0ad2c24bd2ad,C:WindowsSystem32smss.exe Parent-Child relation
- 18. Sample: Process White List Child process SHA-1 of child process binary Parent process C:WindowsSystem32smss.exe,ad34f33130393425d3d4ce671e0d4488ed8d1b6c,System C:WindowsSystem32autochk.exe,1bd90caff9f3ab1d3cb7136ce9146c1c2e69368b,C:WindowsSystem32smss.exe C:WindowsSystem32smss.exe,ad34f33130393425d3d4ce671e0d4488ed8d1b6c,C:WindowsSystem32smss.exe C:WindowsSystem32csrss.exe,53bc9b2ae89fcad6197ec519ae588f926c88e460,C:WindowsSystem32smss.exe C:WindowsSystem32smss.exe,ad34f33130393425d3d4ce671e0d4488ed8d1b6c,C:WindowsSystem32smss.exe C:WindowsSystem32wininit.exe,c7bba9840c44e7739fb314b7a3efe30e6b25cc48,C:WindowsSystem32smss.exe C:WindowsSystem32csrss.exe,53bc9b2ae89fcad6197ec519ae588f926c88e460,C:WindowsSystem32smss.exe C:WindowsSystem32services.exe,54a90c371155985420f455361a5b3ac897e6c96e,C:WindowsSystem32wininit.exe C:WindowsSystem32lsass.exe,d49245356dd4dc5e8f64037e4dc385355882a340,C:WindowsSystem32wininit.exe C:WindowsSystem32lsm.exe,e16beae2233832547bac23fbd82d5321cfc5d645,C:WindowsSystem32wininit.exe C:WindowsSystem32winlogon.exe,b8561be07a37c7414d6e059046ab0ad2c24bd2ad,C:WindowsSystem32smss.exe Parent-Child relation SHA-1 of binary is used for the integrity check. – It works as integrity check.
- 19. Sample: Resource Access Control • File Access Control File processes C:optSCADAlog.txt, C:optSCADASACA.exe,C:Windowsexplorer.exe C:optSCADAconfig, C:optSCADASACA.exe,C:Windowsexplorer.exe C:optOPCconfig, C:optOPCOPC.exe,C:Windowsexplorer.exe • Network Access Control IP Address, Port, Applications 192.168.0.12,80,C:Program FilesInternet Exploreriexplore.exe 192.168.0.11,80,C:UserstestGoogleChromeApplicationchrome.exe 192.168.0.10,0,C:optnetperfnetperf.exe,C:optnetperfnetserver.exe
- 20. Optimization for ICS • Small white list – “don’t care” setting allows small white list. • White list mechanism for file is applied on open() function only. It does not care for read()and write(). – String match takes much time. It takes about 200-300 μ-sec on current CPU. • White list mechanism for IP address and port takes less than 20 μ-sec, because it is achieved by arithmetic operations.
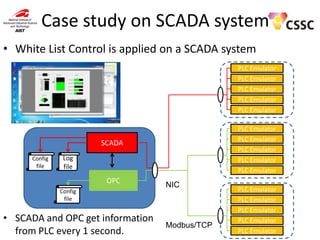
- 21. Case study on SCADA system • White List Control is applied on a SCADA system PLC Emulator PLC Emulator PLC Emulator PLC Emulator PLC Emulator PLC Emulator PLC Emulator PLC Emulator PLC Emulator PLC Emulator SCADA Config file Log file OPC Config file • SCADA and OPC get information from PLC every 1 second. NIC Modbus/TCP PLC Emulator PLC Emulator PLC Emulator PLC Emulator PLC Emulator
- 22. Detail of SCADA System • Server (Windows7 32bit) – SCADA (3 types are tested) PA-Panel, Winlog, OpenSCADA http://openscada.org/ – OPC DeviceExplore • PLC – Modbus PLC emulator http://www.plcsimulator.org/ • 5 emulators run on 3 PCs (Total 15).
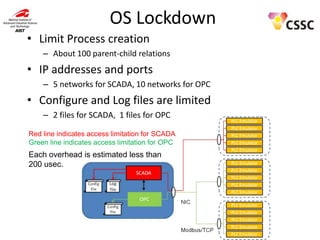
- 23. OS Lockdown • Limit Process creation – About 100 parent-child relations • IP addresses and ports – 5 networks for SCADA, 10 networks for OPC • Configure and Log files are limited – 2 files for SCADA, 1 files for OPC Red line indicates access limitation for SCADA Green line indicates access limitation for OPC Each overhead is estimated less than 200 usec.
- 24. Attack on the SCADA system • IE’en [BlackHat’02] attacks on DCOM (port 135) which is used by OPC. – http://www.securityfriday.com/tools/IEen.html • The attack is prevented by white list control, because the attack requires process creation which is not registered on the white list.
- 25. Limitation of Current White List • Current White List control cannot reduce vulnerabilities. – Malware can exploit, but the activity is limited. • It is not easy to make perfect white list automatically. – Current white list is made from several trials. It is also refined by hand. – A method to create white list from a specification is needed. [future work]
- 26. Conclusions • OS Lockdown (White List Control) for Industrial Control Systems – ICS does not need to run many applications. – The white list control offers predictable time delay. – Some techniques for optimization reduce the overhead. • White List Control is applied on SCADA systems and confirmed its feasibility. It will be applied on testbed systems of CSSC.



![What is CSSC?
■Outline
http://www.css-center.or.jp/
Total 23 corporations (As of Dec, 2013)
Control System Security Center
•
•
•
•
•
(Abbreviation) CSSC
Name
Established
※A corporation authorized by the
Minister of Economics, Trade and
Industry
March 6, 2012 (The registration date)
[Tohoku Tagajo Headquarters
(TTHQ)]
Tagajo City, Miyagi, Japan
Location
[Tokyo Research Center (TRC)]
National Institute of Advanced Industrial
Science and Technology Waterfront,
Tokyo, Japan
Association
members
(In
alphabetical
order)
•
•
•
•
•
•
•
•
•
•
•
•
•
•
•
•
•
•
*8 starting member corporations
Azbil Corporation *
Fuji Electric Co., Ltd.
FUJITSU LIMITED
Hitachi, Ltd.*
Information-technology Promotion Agency, Japan
(IPA)
Japan Quality Assurance Organization(JQA)
LAC Co., Ltd.
McAfee Co.,Ltd.
Mitsubishi Electric Corporation
Mitsubishi Heavy Industries Ltd.*
Mitsubishi Research Institute Inc.*
Mori Building Co., Ltd.*
National Institute of Advanced Industrial Science
and Technology (AIST) *
NEC Corporation
NRI Secure Technologies Ltd.
NTT Corporation
OMRON Corporation
The University of Electro-Communications,
Tohoku Information Systems
Company, Incorporated
Toshiba Corporation*
Toyota InfoTechnology Center Co., Ltd.
Trend Micro Incorporated
Yokogawa Electric Corporation*](https://image.slidesharecdn.com/5-suzaki-1-13-140202162600-phpapp02/85/Process-Whitelisting-and-Resource-Access-Control-For-ICS-Computers-Kuniyasu-Suzaki-of-National-Institute-of-AIST-and-CSSC-3-320.jpg)







![Function of OS Lockdown
(1) Limit the process creation
– Parent-child relation
• Necessary applications must register its parent applications
on a process white list.
– Integrity check for binary
• SHA-1 of binaries must register to process white list.
– [Useful Option] Conflict of interest
• If an application must run exclusively with another
application, they cannot run at the same time.
• It can prevent TOCTOU attack (Time of check to time of use)
• False operation is also prevented.
– For example, administrator cannot run office applications during
SCADA.](https://image.slidesharecdn.com/5-suzaki-1-13-140202162600-phpapp02/85/Process-Whitelisting-and-Resource-Access-Control-For-ICS-Computers-Kuniyasu-Suzaki-of-National-Institute-of-AIST-and-CSSC-11-320.jpg)








![Attack on the SCADA system
• IE’en [BlackHat’02] attacks on DCOM (port 135) which is
used by OPC.
– http://www.securityfriday.com/tools/IEen.html
• The attack is prevented by white list control, because the
attack requires process creation which is not registered
on the white list.](https://image.slidesharecdn.com/5-suzaki-1-13-140202162600-phpapp02/85/Process-Whitelisting-and-Resource-Access-Control-For-ICS-Computers-Kuniyasu-Suzaki-of-National-Institute-of-AIST-and-CSSC-24-320.jpg)
![Limitation of Current White List
• Current White List control cannot reduce vulnerabilities.
– Malware can exploit, but the activity is limited.
• It is not easy to make perfect white list automatically.
– Current white list is made from several trials. It is
also refined by hand.
– A method to create white list from a specification is
needed. [future work]](https://image.slidesharecdn.com/5-suzaki-1-13-140202162600-phpapp02/85/Process-Whitelisting-and-Resource-Access-Control-For-ICS-Computers-Kuniyasu-Suzaki-of-National-Institute-of-AIST-and-CSSC-25-320.jpg)
