CDIC 2013-Mobile Application Pentest Workshop
- 1. CDIC 2013 : Cyber Defense Initiative Conference 2013 www.cdicconference.com 27 th – 28 th February 2013, Centara Grand & Bangkok Convention Centre at Central World, Bangkok Advanced Mobile Penetration Testing Application Attacks and Defense Mr. Prathan Phongthiproek Consulting Manager GIAC GPEN, E|CSA, C|EH, eCPPT, CPTS, CIW Security Analyst, CWNA, CWSP, Security+
- 2. CDIC 2013 : Cyber Defense Initiative Conference 2013 www.cdicconference.com Speaker Profile . Mr. Prathan Phongthiproek GIAC GPEN, E|CSA, C|EH, eCPPT, CPTS, CIW Security Analyst, CWNA, CWSP, Security+ ACIS Professional Center E-mail: [email protected] 2
- 3. CDIC 2013 : Cyber Defense Initiative Conference 2013 www.cdicconference.com Let’s Talk and Workshop Introduction Attack Vectors for Pentest Pentest iOS App Pentest Android App Workshop !! 3
- 4. CDIC 2013 : Cyber Defense Initiative Conference 2013 www.cdicconference.com INTRODUCTION 4
- 5. CDIC 2013 : Cyber Defense Initiative Conference 2013 www.cdicconference.com Past few years….. Just Mobile phone – Phone calls – Sending text message or MMS – Alarm clock – Calculator – Listen music Edge for Surf internet !! 5
- 6. CDIC 2013 : Cyber Defense Initiative Conference 2013 www.cdicconference.com Now… 3G, 4G and WIFI support on Mobile network Became more intelligent – Smart Phones – Sending email – Surf internet – Check-in for flights – Online Banking transactions – Social network (Facebook, Twitter, Instagram) 6
- 7. CDIC 2013 : Cyber Defense Initiative Conference 2013 www.cdicconference.com Now… Companies started creating mobile applications to offer services to clients – Storing and synchronizing data files in the cloud – Participating in social network sites – As the data that stored, processed and transferred can often be considered sensitive. 7
- 8. CDIC 2013 : Cyber Defense Initiative Conference 2013 www.cdicconference.com ATTACK VECTORS FOR PENTEST 8
- 9. CDIC 2013 : Cyber Defense Initiative Conference 2013 www.cdicconference.com Three Attack Surfaces Client Software on Mobile device Communications Channel Server Side Infrastructure Client Software Comm. Channel Server Side Infrastructure 9
- 10. CDIC 2013 : Cyber Defense Initiative Conference 2013 www.cdicconference.com Client Software Packages are typically downloaded from an AppStore, Google Play or provided via Company website Testing requires a device that is rooted or jailbroken for access to all files and folders on the local file system Be able to decompiled, tampered or reverse engineered 10
- 11. CDIC 2013 : Cyber Defense Initiative Conference 2013 www.cdicconference.com Client Software Attention points – Files on the local file system – Application authentication & authorization – Error Handling & Session Management – Business logic – Decompiling and analyzing 11
- 12. CDIC 2013 : Cyber Defense Initiative Conference 2013 www.cdicconference.com iExplorer for iPhone 12
- 13. CDIC 2013 : Cyber Defense Initiative Conference 2013 www.cdicconference.com Profile.properties and user_info.pref.xml 13
- 14. CDIC 2013 : Cyber Defense Initiative Conference 2013 www.cdicconference.com Plist files 14
- 15. CDIC 2013 : Cyber Defense Initiative Conference 2013 www.cdicconference.com Decompiled 15
- 16. CDIC 2013 : Cyber Defense Initiative Conference 2013 www.cdicconference.com Communications Channel Channel between the client and the server (HTTPs, Edge-3G) Testing with HTTP Proxy (Burp, ZAP) to intercept and manipulate alter traffic If the application does not use the HTTP protocol, can use transparent TCP and UDP proxy like Mallory 16
- 17. CDIC 2013 : Cyber Defense Initiative Conference 2013 www.cdicconference.com Communications Channel Attention points – Replay attack vulnerabilities – Secure transfer of sensitive information – SSLStrip for HTTPS via Wifi – Setup SSL for Proxy 17
- 18. CDIC 2013 : Cyber Defense Initiative Conference 2013 www.cdicconference.com Sniff traffic 18
- 19. CDIC 2013 : Cyber Defense Initiative Conference 2013 www.cdicconference.com Server-Side Infrastructure The attack vectors for the web servers behind a mobile application is similar to those use for regular websites Perform host and service scans on the target system to identify running services 19
- 20. CDIC 2013 : Cyber Defense Initiative Conference 2013 www.cdicconference.com Server-Side Infrastructure Attention points – OWASP Top 10 vulnerabilities (SQL Injection, XSS, ...) – Running services and versions – Infrastructure vulnerability scanning 20
- 21. CDIC 2013 : Cyber Defense Initiative Conference 2013 www.cdicconference.com Real Case Study: Mobile App Pentest Client Software – Found backend path in Localizable.strings Server-Side Infrastructure – Access to port 8080 (Tomcat) – Logged in with default tomcat username and password – Upload Malicious JSP code into webserver (Bypass Symantec AV) – Access to configuration file that contain database credentials – OWNED !! Database Server – Capture the Flag !! 21
- 22. CDIC 2013 : Cyber Defense Initiative Conference 2013 www.cdicconference.com Localizable.strings 22
- 23. CDIC 2013 : Cyber Defense Initiative Conference 2013 www.cdicconference.com Logged in with Default Tomcat credentials 23
- 24. CDIC 2013 : Cyber Defense Initiative Conference 2013 www.cdicconference.com Upload Malicious code 24
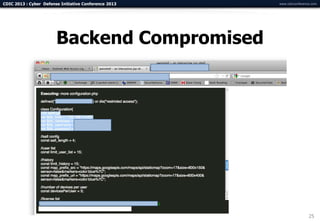
- 25. CDIC 2013 : Cyber Defense Initiative Conference 2013 www.cdicconference.com Backend Compromised 25
- 26. CDIC 2013 : Cyber Defense Initiative Conference 2013 www.cdicconference.com Database Compromised 26
- 27. CDIC 2013 : Cyber Defense Initiative Conference 2013 www.cdicconference.com PENTEST IOS APPLICATION Fast Track 27
- 28. CDIC 2013 : Cyber Defense Initiative Conference 2013 www.cdicconference.com iOS Application Distributed as “.ipa” file (Simply zip file) Deployed as “.app” directories (Same as Mac OSX) Objective-C Data storage – Plist files – SQLite – Binary data files 28
- 29. CDIC 2013 : Cyber Defense Initiative Conference 2013 www.cdicconference.com Fast and Furious Step Preparing a Device – Jailbreak Install Tools on Device – Cydia (OpenSSH, MobileTerminal, Etc) Install Tools on Workstation – SSH Client – Plist Editor – SQLite Database Browser – Wireshark, Burp proxy 29
- 30. CDIC 2013 : Cyber Defense Initiative Conference 2013 www.cdicconference.com Fast and Furious Step Read application’s data files 30
- 31. CDIC 2013 : Cyber Defense Initiative Conference 2013 www.cdicconference.com Fast and Furious Step Setup Proxy for Intercept and Manipulate traffic data 31
- 32. CDIC 2013 : Cyber Defense Initiative Conference 2013 www.cdicconference.com Fast and Furious Step 32
- 33. CDIC 2013 : Cyber Defense Initiative Conference 2013 www.cdicconference.com PENTEST ANDROID APPLICATION Fast and Furious 33
- 34. CDIC 2013 : Cyber Defense Initiative Conference 2013 www.cdicconference.com Android Application Distributed as “.apk” file (Simply zip file) Multiuser OS running DalvikVM Android runs .dex files on DalvikVM Data storage – XML files – SQLite 34
- 35. CDIC 2013 : Cyber Defense Initiative Conference 2013 www.cdicconference.com Android Application 35
- 36. CDIC 2013 : Cyber Defense Initiative Conference 2013 www.cdicconference.com Android and Java 36
- 37. CDIC 2013 : Cyber Defense Initiative Conference 2013 www.cdicconference.com Preparation Tools for Pentest Android SDK Tools – AVD Manager and ADK Manager Java 5,6, or 7 Eclipse for code review purpose MITM proxy Tools such as Burp Dex2jar, JD GUI 37
- 38. CDIC 2013 : Cyber Defense Initiative Conference 2013 www.cdicconference.com Setting up the environment 38
- 39. CDIC 2013 : Cyber Defense Initiative Conference 2013 www.cdicconference.com Setting up the environment 39
- 40. CDIC 2013 : Cyber Defense Initiative Conference 2013 www.cdicconference.com Setting up the environment 40
- 41. CDIC 2013 : Cyber Defense Initiative Conference 2013 www.cdicconference.com Adb install <apk path> 41
- 42. CDIC 2013 : Cyber Defense Initiative Conference 2013 www.cdicconference.com Configuring the proxy 42
- 43. CDIC 2013 : Cyber Defense Initiative Conference 2013 www.cdicconference.com Configuring the proxy 43
- 44. CDIC 2013 : Cyber Defense Initiative Conference 2013 www.cdicconference.com Adb shell 44
- 45. CDIC 2013 : Cyber Defense Initiative Conference 2013 www.cdicconference.com Access Database via adb shell 45
- 46. CDIC 2013 : Cyber Defense Initiative Conference 2013 www.cdicconference.com Android Debug Bridge (ADB) Packaged with the Android Software Development Kit Essential adb commands: – Adb devices: returns serial number of device(s) attached – Adb kill-server: shuts down the adb daemon – Adb shell: remote terminal – Adb push: moves files from the local workstation to device – Adb pull: moves files from the device to local workstation – Adb remount: remounts the system partition on the device as read-write or write, depending on switch – Adb forward: forwards adb traffic from one port to another – Adb –h: help file for adb commands 46
- 47. CDIC 2013 : Cyber Defense Initiative Conference 2013 www.cdicconference.com Source Code Review Convert the .apk file into .zip Extract the zipped file, Found classes.dex Dex2jar for convert .dex to .jar Using JD GUI to open JAR file and review source code 47
- 48. CDIC 2013 : Cyber Defense Initiative Conference 2013 www.cdicconference.com Decompiled Application 48
- 49. CDIC 2013 : Cyber Defense Initiative Conference 2013 www.cdicconference.com Java Decompiler 49
- 50. CDIC 2013 : Cyber Defense Initiative Conference 2013 www.cdicconference.com Tip!! Prevent Application Reverse Engineering ProGuard (Free) and DexGuard – Obfuscator for Android – Encrypt strings – Encrypt entire classes – Add tamper detection 50
- 51. CDIC 2013 : Cyber Defense Initiative Conference 2013 www.cdicconference.com WORKSHOP !! 51
- 52. CDIC 2013 : Cyber Defense Initiative Conference 2013 www.cdicconference.com Thank You www.cdicconference.com