Attacking Embedded Devices (No Axe Required)
- 1. Attacking Embedded Systems: No Axe Required Paul Asadoorian Special thanks to Allison Nixon, Craig Heffner & Robert Kornmeyer
- 2. Copyright 2013 Paul Asadoorian • Day Job: Tenable Network Security Product Evangelist (Primarily Nessus) • Founder of Security Weekly(weekly podcast, Internet TV) • Gets hands dirty on penetration tests • Loves family, embedded devices, cigars, fishing and Kung Fu movies
- 3. Attacking Embedded Systems FACT: Embedded systems security stinks.
- 4. Attacking Embedded Systems GOAL: Give you methods to finding embedded device vulnerabilities easily.
- 5. Copyright 2013 Topics We Will Cover • Why should you care about embedded device vulnerabilities? • Detection & Enumeration • Combat Firmware Analysis • Light Reverse Engineering: Ripping apart firmware, emulating firmware
- 6. Why We Care About Embedded Device Vulnerabilities
- 7. Hacking Like its 1999 Copyright 2013 • Devices ship with all sorts of vulnerabilities (buffer overflows, command injection, CSRF) • Small footprint means security it often left out (ASLR, DEP) • High occurrence of re-use (esp. on Linux devices, someone gets it working once and no one wants to change)
- 8. No One Pays Attention Copyright 2013 • If it ain’t broke... • Dedicated devices often just work, updates break things • They receive a lower priority to patching desktops and servers • They don’t contain sensitive data (dangerous notion!) • End users don’t even know they can be updated
- 9. Critical Path (Direct and Copyright 2013 Indirect) • Sensitive data passes through devices (printers, WAPs, switches, routers) • Attackers use them to gain a foothold (proxies, sniff passwords, scan the network) • Easily allows attackers to monitor (web cameras, video teleconferencing) Evil Router
- 10. Copyright 2013 Getting Worse? http://securityevaluators.com/content/case-studies/routers/soho_router_hacks.jsp
- 11. Doomed To Repeat Independent Security Evaluators (ISE), which is a security consultancy based in Baltimore, found that all of the routers they tested could be taken over if the hacker had access credentials. The tested products came from Linksys, Belkin, Netgear, Verizon and D-Link. (April 2013) Phil Perviance, Application Security Consultant, AppSec Consulting, Inc. discloses 5 vulnerabilities in Linksys routers. Cisco does not issue fixes (April 2013) Unnamed researcher used a simple, binary technique to take control of more than 420,000 insecure devices including Webcams, routers, and printers running on the Internet (March 2013) In March, 2013, Michael Messner disclosed vulnerabilities ranging from minor to critical in D-Link, TP-Link, In January, 2013, HD Moore disclosed that numerous home routers exposed UPnP services, including SSDP Discovery and SOAP, to the Internet (WAN) side of the device. In January, 2013, DefenseCode released an advisory describing a remote, unauthenticated format string vulnerability in the Broadcom UPnP software that escalated to root shell access. In May, 2012, it was disclosed that WiFi Protected Setup (WPS) uses an eight-digit PIN for authentication, and an attacker can determine if the first four digits of an attempted PIN are correct, without regard to the last four At BlackHat 2012, Phil Purviance (Superevr) demonstrated a cross-site file upload vulnerability in the Linksys WRT54GL. At BlackHat 2009, Felix Lindner explored the feasibility and techniques that could be used to attack commercial grade routers. Copyright 2013 Netgear, and Linksys routers. Primary Source: http://securityevaluators.com/content/case-studies/routers/soho_router_hacks.jsp
- 13. Copyright 2013 Identify The Device: Passive • DNS Recon - Zone transfer, brute force forward lookups, reverse lookup IPs • Look for devices with suspicious names (router, camera, video teleconference related) • Search public sources of information • Forum post: “We just bought a new XYZ device” • Public web page • Shodan: “net:<cidr range>”
- 14. Identify The Device: Active • Nessus • I wrote an article: Scanning Embedded Systems In The Enterprise With Copyright 2013 Nessus (http://bit.ly/10nRtdT) • Nmap • nmap -P0 -vv -sS -r -n -p 1-65535 192.168.1.7 • nmap -P0 -T5 -sU -r -n -p 1-1024 192.168.1.7 • Peeper.py (https://github.com/invisiblethreat/peeper) • Takes screenshots of all web sites in Nessus results • recon-ng - General purposes recon tool
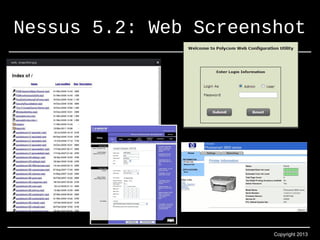
- 15. Nessus 5.2: Web Screenshot Copyright 2013
- 16. Other People’s Research • Once you identify the device, see if others have reverse engineered the firmware • Or disclosed vulnerabilities • Great resources: • http://www.devttys0.com • http://this8bitlife.com/adventures-in-linux-reverse-engineering-firmware/ • http://www.digitalworldz.co.uk/47718-looking-inside-jffs2-images.html • http://bramp.net/blog/2012/01/hacking-linksys-e4200v2-firmware/ • http://wiki.securityweekly.com/wiki/index.php/Episode320#Interview:_Crai g_Heffner < Interview w/ binwalk author Copyright 2013
- 17. Determine Device Type Copyright 2013 • Visit web configuration screen • Banners: • SNMP • FTP • TELNET • SSH • Is it running FOSS that has known vulnerabilities?
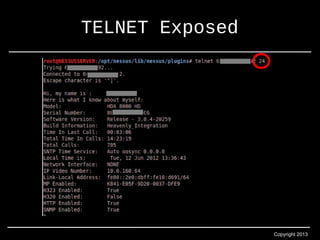
- 18. Copyright 2013 TELNET Exposed
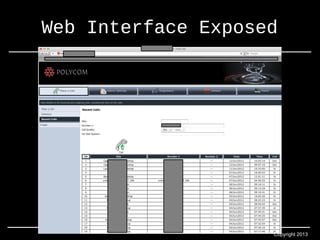
- 19. Web Interface Exposed Copyright 2013
- 20. Conference Room Exposed Copyright 2013
- 22. Copyright 2013 Offline Work • Visit manufacturers web site: • Read manuals (default passwords? Win!) • Review software license (GNU software? Runs Linux!) Download firmware - Starts an entirely new process, we won’t cover debugging with IDA, but quicker wins
- 24. Basic Analysis: strings Copyright 2013 $ strings -8 firmware.bin | grep "^/" | less /webauth/login.htm /webauth/login_fail.htm /webauth/login_fail_held.htm /webauth/login_full.htm /webauth/login_success.htm /webauth/login.htm?oriurl= Find all lines with 8 characters or more that begin with “/”.
- 25. Find Authentication Bypass Copyright 2013 #!/bin/bash PAGES=`cat webfiles` for p in $PAGES do wget http://192.168.1.7$p done “webfiles” contains all web page URLs dumped from firmware
- 26. Basic Analysis: hexdump File system headers, boot devices, firmware type, etc... Copyright 2013
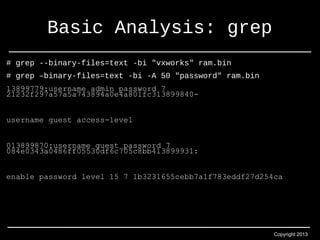
- 27. Copyright 2013 Basic Analysis: grep # grep --binary-files=text -bi "vxworks" ram.bin # grep –binary-files=text -bi -A 50 "password" ram.bin 13899779:username admin password 7 21232f297a57a5a743894a0e4a801fc313899840- username guest access-level 013899870:username guest password 7 084e0343a0486ff05530df6c705c8bb413899931: enable password level 15 7 1b3231655cebb7a1f783eddf27d254ca
- 29. Firmware Parts Flash Device (MTD) Boot Loader u-boot nvram Kernel File system nvram Firmware nvram(1): used to store information for the BIOS (such as booting instructions, e.g. how long to wait) Boot Loader: Boots up the kernel, u-boot, redboot, etc.. Kernel: Linux, VxWorks or other OS specific kernel. File System: Squashfs, CramFS, usually compressed, sometimes more than one nvram(2) - Stores device settings permanently on MTD Reference: http://wiki.openwrt.org/doc/techref/start
- 30. Basic Firmware Analysis # binwalk DIR-850L_FW_v1.03b02.bin DECIMAL HEX DESCRIPTION--------------------------------------------------------------------------- ---------------------------------------- 0 0x0 DLOB firmware header, boot partition: "dev=/dev/mtdblock/ 1"589 0x24D LZMA compressed data, properties: 0x88, dictionary size: 1048576 bytes, uncompressed size: 65535 bytes10376 0x2888 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 5034652 bytes1638512 0x190070 PackImg section delimiter tag, little endian size: 12610048 bytes; big endian size: 6995968 bytes1638544 0x190090 Squashfs filesystem, little endian, version 4.0, compression: lzma, size: 6992339 bytes, 2435 inodes, blocksize: 131072 bytes, created: Tue Mar 12 06:45:03 2013 http://wiki.securityweekly.com/wiki/index.php/Reverse_Engineering_Firmware_Primer Copyright 2013
- 31. Copyright 2013 Extract File System # binwalk --dd=squashfs:1 DIR-850L_FW_v1.03b02.bin # cd _DIR-850L_FW_v1.03b02.bin.extracted/# file 190090.1 190090.1: Squashfs filesystem, little endian, version 4.0, 1778655743 bytes, 2435 inodes, blocksize: 0 bytes, created: Mon Sep 21 17:59:44 2026 Apply this method to several types of firmware to extract file system and mount it. sqaushfs and cramfs are easier. JFFS2 is a PITA.
- 32. Copyright 2013 Firmware Toolkit • Now we understand at least one building block • Time to automate! • Works best with home routers and access points • Firmware toolkit is a collection of scripts and tools to extract firmware: • Firmware headers • Kernel • File system
- 33. Copyright 2013 Firmware Magic # ./extract-ng.sh DIR-850L_FW_v1.03b02.bin Firmware Mod Kit (build-ng) 0.78 beta, (c)2011-2012 Craig Heffner, Jeremy Collake http://www.bitsum.com Scanning firmware... DECIMAL HEX DESCRIPTION -------------------------------------------------------------------------------------- 0 0x0 DLOB firmware header, signature=wrgac05_dlob.hans_dir850l, dev=/dev/mtdblock/1 1638544 0x190090 Squashfs filesystem, little endian, version 4.0, compression: lzma, size: 6992339 bytes, 2435 inodes, blocksize: 131072 bytes, created: Tue Mar 12 06:45:03 2013 Extracting 1638544 bytes of dlob header image at offset 0 Extracting squashfs file system at offset 1638544 Extracting squashfs files... Firmware extraction successful! Firmware parts can be found in 'fmk/*' Mounts file systems for you!
- 34. File System Treasures Copyright 2013 • Configuration files • Password files • SSL and SSH keys • Web server pages and code • Reverse engineer binaries • Load binaries in a debugger • Run strings against binaries
- 35. Copyright 2013 qemu is Your Friend • Run ARM or MIPS binaries on your i386 system • Allows you to debug them too • And run the web server • Then test using something like Burp • Test devices without actually having the device! • Find vulnerabilities pre-purchase # chroot . ./qemu-mips-static sbin/httpd -f var/run/httpd.conf # ./qemu-mips-static bin/ls
- 36. Enumerate The Web Pages Copyright 2013 • root@ubuntu:/usr/src/firmware-mod-kit-read-only/ trunk/fmk/rootfs/htdocs# ls • cgibin HNAP1 neap phplib upnpdevdesc web webinc • fileaccess.cgi mydlink parentalcontrols upnp upnpinc webaccess widget Review source code for vulnerabilities!
- 37. Copyright 2013 Metasploit Payloads • Metasploit now has a MIPS payload • http://bit.ly/ZE9zVN • Several web command execution vulnerabilities • Post-exploitation for embedded systems
- 38. Copyright 2013 The Sequel? • We didn’t cover: • Manually extracting parts from unknown firmware • Manually mounting file systems (tips and tricks) • Running ARM firmware in full emulation • Debugging binaries • Stay tuned...
- 39. Copyright 2013 [email protected] Listen: http://securityweekly.com/podcast Watch: http://blip.tv/securityweekly Read: http://securityweekly.com/wiki Participate: http://mail.securityweekly.com