00-105 Interconnecting Cisco Networking Devices Part 1 (ICND1.pdf
- 1. 100-105.examsforall.premium.exam.729q Number: 100-105 Passing Score: 800 Time Limit: 120 min File Version: 19.041 100-105 Interconnecting Cisco Networking Devices Part 1 (ICND1) Version: 19.041
- 2. Exam A QUESTION 1 How does a switch differ from a hub? A. A switch does not induce any latency into the frame transfer time. B. A switch tracks MAC addresses of directly-connected devices. C. A switch operates at a lower, more efficient layer of the OSI model. D. A switch decreases the number of broadcast domains. E. A switch decreases the number of collision domains. Correct Answer: B Section: (none) Explanation Explanation/Reference: Explanation: Some of the features and functions of a switch include: A switch is essentially a fast, multi-port bridge, which can contain dozens of ports. Rather than creating two collision domains, each port creates its own collision domain. In a network of twenty nodes, twenty collision domains exist if each node is plugged into its own switch port. If an uplink port is included, one switch creates twenty-one single-node collision domains. A switch dynamically builds and maintains a Content-Addressable Memory (CAM) table, holding all of the necessary MAC information for each port. For a detailed description of how switches operate, and their key differences to hubs, see the reference link below. http://www.cisco.com/warp/public/473/lan-switch-cisco.shtml QUESTION 2 What must occur before a workstation can exchange HTTP packets with a web server? A. A UDP connection must be established between the workstation and its default gateway. B. A UDP connection must be established between the workstation and the web server. C. A TCP connection must be established between the workstation and its default gateway. D. A TCP connection must be established between the workstation and the web server. E. An ICMP connection must be established between the workstation and its default gateway. F. An ICMP connection must be established between the workstation and the web server. Correct Answer: D Section: (none) Explanation Explanation/Reference: Explanation: HTTP uses TCP port 80. http://pentestlab.wordpress.com/2012/03/05/common-tcpip-ports/ QUESTION 3 How does TCP differ from UDP? (Choose two.) A. TCP provides best effort delivery. B. TCP provides synchronized communication. C. TCP segments are essentially datagrams. D. TCP provides sequence numbering of packets. E. TCP uses broadcast delivery. Correct Answer: BD Section: (none) Explanation
- 3. Explanation/Reference: Explanation: TCP differs from UDP in the following ways: TCP provides best effort delivery. TCP provides synchronized communication. TCP segments are essentially datagrams. TCP provides sequence numbering of packets. TCP uses broadcast delivery. QUESTION 4 A workstation has just resolved a browser URL to the IP address of a server. What protocol will the workstation now use to determine the destination MAC address to be placed into frames directed toward the server? A. HTTP B. DNS C. DHCP D. RARP E. ARP Correct Answer: E Section: (none) Explanation Explanation/Reference: QUESTION 5 Refer to the exhibit. Host A is sending a packet to Host B for the first time. What destination MAC address will Host A use in the ARP request? A. 192.168.0.1 B. 172.16.0.50 C. 00-17-94-61-18-b0 D. 00-19-d3-2d-c3-b2 E. ff-ff-ff-ff-ff-ff F. 255.255.255.255 Correct Answer: E Section: (none) Explanation Explanation/Reference: Explanation: For the initial communication, Host A will send a broadcast ARP (all F's) to determine the correct address to use to reach the destination. QUESTION 6
- 4. The network manager has requested a 300-workstation expansion of the network. The workstations are to be installed in a single broadcast domain, but each workstation must have its own collision domain. The expansion is to be as cost-effective as possible while still meeting the requirements. Which three items will adequately fulfill the request? (Choose three). A. one IP subnet with a mask of 255.255.254.0 B. two IP subnets with a mask of 255.255.255.0 C. seven 48-port hubs D. seven 48-port switches E. one router interface F. seven router interfaces Correct Answer: ADE Section: (none) Explanation Explanation/Reference: Explanation: of 255.255.254.0 can absorb 510 hosts being 23 bits mask and also 7*48 port switches can handle this much hosts and router interface is required to be minimum to avoid unnecessary wastage hence the answers. QUESTION 7 What are two common TCP applications? (Choose two.) A. TFTP B. SMTP C. SNMP D. FTP E. DNS Correct Answer: BD Section: (none) Explanation Explanation/Reference: Explanation: SMTP uses TCP port 25, while FTP uses TCP ports 20 and 21. http://pentestlab.wordpress.com/2012/03/05/common-tcpip-ports/ QUESTION 8 Which two statements describe the operation of the CSMA/CD access method? (Choose two.) A. In a CSMA/CD collision domain, multiple stations can successfully transmit data simultaneously. B. In a CSMA/CD collision domain, stations must wait until the media is not in use before transmitting. C. The use of hubs to enlarge the size of collision domains is one way to improve the operation of the CSMA/CD access method. D. After a collision, the station that detected the collision has first priority to resend the lost data. E. After a collision, all stations run a random backoff algorithm. When the backoff delay period has expired, all stations have equal priority to transmit data. F. After a collision, all stations involved run an identical backoff algorithm and then synchronize with each other prior to transmitting data. Correct Answer: BE Section: (none) Explanation Explanation/Reference:
- 5. Explanation: Ethernet networking uses Carrier Sense Multiple Access with Collision Detect (CSMA/CD), a protocol that helps devices share the bandwidth evenly without having two devices transmit at the same time on the network medium. CSMA/CD was created to overcome the problem of those collisions that occur when packets are transmitted simultaneously from different nodes. And trust me, good collision management is crucial, because when a node transmits in a CSMA/CD network, all the other nodes on the network receive and examine that transmission. Only bridges and routers can effectively prevent a transmission from propagating throughout the entire network! So, how does the CSMA/CD protocol work? Like this: when a host wants to transmit over the network, it first checks for the presence of a digital signal on the wire. If all is clear (no other host is transmitting), the host will then proceed with its transmission. But it doesn't stop there. The transmitting host constantly monitors the wire to make sure no other hosts begin transmitting. If the host detects another signal on the wire, it sends out an extended jam signal that causes all nodes on the segment to stop sending data (think, busy signal). The nodes respond to that jam signal by waiting a while before attempting to transmit again. Backoff algorithms determine when the colliding stations can retransmit. If collisions keep occurring after 15 tries, the nodes attempting to transmit will then time out. QUESTION 9 Refer to the exhibit. SwitchA receives the frame with the addressing shown in the exhibit. According to the command output also shown in the exhibit, how will SwitchA handle this frame? A. It will drop the frame. B. It will forward the frame out port Fa0/6 only. C. It will forward the frame out port Fa0/3 only. D. It will flood the frame out all ports. E. It will flood the frame out all ports except Fa0/3. Correct Answer: E Section: (none) Explanation Explanation/Reference: Explanation: When frame receives the frame, it checks the source address on MAC table if MAC address found in MAC table it tries to forward if not in MAC table adds the Address on MAC table. After checking the source address, it checks the destination address on MAC table, if MAC address found on MAC table it forwards to proper ports otherwise floods on all ports except the source port. QUESTION 10 Refer to the exhibit. The exhibit is showing the topology and the MAC address table. Host A sends a data frame to host D. What will the switch do when it receives the frame from host A?
- 6. A. The switch will add the source address and port to the MAC address table and forward the frame to host D. B. The switch will discard the frame and send an error message back to host A. C. The switch will flood the frame out of all ports except for port Fa0/3. D. The switch will add the destination address of the frame to the MAC address table and forward the frame to host D. Correct Answer: A Section: (none) Explanation Explanation/Reference: Explanation: When switch receives the data frame from the host not having the MAC address already on the MAC table, it will add the MAC address to source port on MAC address table and sends the data frame. QUESTION 11 Refer to the exhibit. If the resume command is entered after the sequence that is shown in the exhibit, which router prompt will be displayed? A. Router1> B. Router1# C. Router2> D. Router2# Correct Answer: C Section: (none) Explanation Explanation/Reference: Explanation:
- 7. The Ctrl-Shift-6 x command suspends the telnet session and hence the prompt will again be Router2> QUESTION 12 Refer to the exhibit. Which default gateway address should be assigned to HostA? A. 192.168.1.1 B. 192.168.1.65 C. 192.168.1.66 D. 192.168.1.129 E. 10.1.1.1 F. 10.1.1.2 Correct Answer: B Section: (none) Explanation Explanation/Reference: Explanation: It should be one less than the switch IP to which it is connected so it will be B. QUESTION 13 Refer to the exhibit. A network has been planned as shown. Which three statements accurately describe the areas and devices in the network plan? (Choose three.)
- 8. A. Network Device A is a switch. B. Network Device B is a switch. C. Network Device A is a hub. D. Network Device B is a hub. E. Area 1 contains a Layer 2 device. F. Area 2 contains a Layer 2 device. Correct Answer: ADE Section: (none) Explanation Explanation/Reference: Explanation: Switches use a separate collision domain for each port, so device A must be a switch. Hubs, however, place all ports in the same collision domain so device B is a hub. Switches reside in layer 2 while hubs are layer 1 devices. QUESTION 14 Which two options will help to solve the problem of a network that is suffering a broadcast storm? (Choose two.) A. a bridge B. a router C. a hub D. a Layer 3 switch E. an access point Correct Answer: BD Section: (none) Explanation Explanation/Reference: Explanation: Routers and layer 3 switches will not propagate broadcast traffic beyond the local segment, so the use of these devices is the best method for eliminating broadcast storms. QUESTION 15 Refer to the exhibit. All devices attached to the network are shown. How many collision domains are present in this network?
- 9. A. 2 B. 3 C. 6 D. 9 E. 15 Correct Answer: E Section: (none) Explanation Explanation/Reference: Explanation: A switch uses a separate collision domain for each port so there are a total of 9 for each device shown. In addition to this, the switch to switch connections (3) are a separate collision domain. Finally, we add the switch to router connections (2) and the router to router connection (1) for a total of 15. QUESTION 16 What does a host on an Ethernet network do when it is creating a frame and it does not have the destination address? A. drops the frame B. sends out a Layer 3 broadcast message C. sends a message to the router requesting the address D. sends out an ARP request with the destination IP address Correct Answer: D Section: (none) Explanation Explanation/Reference: Explanation: Understanding this concept is prime for understanding that when switch receives the data frame from the host not having the MAC address already in the MAC table, it will add the MAC address to the source port on the MAC address table and sends the data frame. If the switch already has the MAC address in it's table for the destination, it will forward the frame directly to the destination port. If it was not already in it's MAC table, then they frame would have been flooded out all ports except for the port that it came from. QUESTION 17 Refer to the exhibit. The ports that are shown are the only active ports on the switch. The MAC address table is shown in its entirety. The Ethernet frame that is shown arrives at the switch. What two operations
- 10. will the switch perform when it receives this frame? (Choose two.) A. The MAC address of 0000.00aa.aaaa will be added to the MAC address table. B. The MAC address of 0000.00dd.dddd will be added to the MAC address table. C. The frame will be forwarded out port fa0/3 only. D. The frame will be forwarded out fa0/1, fa0/2, and fa0/3. E. The frame will be forwarded out all the active ports. Correct Answer: AD Section: (none) Explanation Explanation/Reference: Explanation: If the switch already has the MAC address in its table for the destination, it will forward the frame directly to the destination port. If it was not already in its MAC table, then they frame would have been flooded out all ports except for the port that it came from.It will also add the MAC address of the source device to its MAC address table QUESTION 18 A switch has 48 ports and 4 VLANs. How many collision and broadcast domains exist on the switch (collision, broadcast)? A. 4, 48 B. 48, 4 C. 48, 1 D. 1, 48 E. 4, 1 Correct Answer: B Section: (none) Explanation Explanation/Reference: Explanation: A switch uses a separate collision domain for each port, and each VLAN is a separate broadcast domain.
- 11. QUESTION 19 Which address type does a switch use to make selective forwarding decisions? A. source IP address B. destination IP address C. source and destination IP address D. source MAC address E. destination MAC address Correct Answer: E Section: (none) Explanation Explanation/Reference: Explanation: Switches analyze the destination MAC to make its forwarding decision since it is a layer 2 device. Routers use the destination IP address to make forwarding decisions. QUESTION 20 Refer to the exhibit. The MAC address table is shown in its entirety. The Ethernet frame that is shown arrives at the switch. What two operations will the switch perform when it receives this frame? (Choose two.) A. The switch will not forward a frame with this destination MAC address. B. The MAC address of 0000.00aa.aaaa will be added to the MAC Address Table. C. The MAC address of ffff.ffff.ffff will be added to the MAC address table. D. The frame will be forwarded out all active switch ports except for port fa0/0. E. The frame will be forwarded out fa0/0 and fa0/1 only. F. The frame will be forwarded out all the ports on the switch. Correct Answer: BD Section: (none) Explanation
- 12. Explanation/Reference: Explanation: If the switch already has the MAC address in its table for the destination, it will forward the frame directly to the destination port. If it was not already in its MAC table, then they frame would have been flooded out all ports except for the port that it came from. QUESTION 21 On a Cisco switch, which protocol determines if an attached VoIP phone is from Cisco or from another vendor? A. RTP B. TCP C. CDP D. UDP Correct Answer: C Section: (none) Explanation Explanation/Reference: Explanation: The Cisco Unified IP Phone uses CDP to communicate information such as auxiliary VLAN ID, per port power management details, and Quality of Service (QoS) configuration information with the Cisco Catalyst switch. QUESTION 22 Refer to the exhibit. What must be configured to establish a successful connection from Host A to switch SW-A through router RT-A? A. VLAN 1 on RT-A B. IP routing on SW-A C. default gateway on SW-A D. crossover cable connecting SW-A and RT-A Correct Answer: C Section: (none) Explanation Explanation/Reference: Explanation: In order for the switch to reach networks that are not local, such as networks attached to different interfaces of the router, it will need to set its default gateway to be the IP address of the attached router. QUESTION 23 A switch receives a frame on one of its ports. There is no entry in the MAC address table for the destination MAC address. What will the switch do with the frame? A. drop the frame B. forward it out of all ports except the one that received it C. forward it out of all ports
- 13. D. store it until it learns the correct port Correct Answer: B Section: (none) Explanation Explanation/Reference: Explanation: Understanding this concept is prime for understanding that when switch receives the data frame from the host not having the MAC address already in the MAC table, it will add the MAC address to the source port on the MAC address table and sends the data frame. If the switch already has the MAC address in it's table for the destination, it will forward the frame directly to the destination port. If it was not already in it's MAC table, then they frame would have been flooded out all ports except for the port that it came from. QUESTION 24 At which layer of the OSI model does the protocol that provides the information that is displayed by the show cdp neighbors command operate? A. application B. transport C. network D. physical E. data link Correct Answer: E Section: (none) Explanation Explanation/Reference: Explanation: CDP is a device discovery protocol that runs over Layer 2 (the data link layer) on all Cisco- manufactured devices (routers, bridges, access servers, and switches) and allows network management applications to discover Cisco devices that are neighbors of already known devices. With CDP, network management applications can learn the device type and the Simple Network Management Protocol (SNMP) agent address of neighboring devices running lower-layer, transparent protocols. QUESTION 25 Which two characteristics apply to Layer 2 switches? (Choose two.) A. increases the number of collision domains B. decreases the number of collision domains C. implements VLAN D. decreases the number of broadcast domains E. uses the IP address to make decisions for forwarding data packets Correct Answer: AC Section: (none) Explanation Explanation/Reference: Explanation: Layer 2 switches offer a number of benefits to hubs, such as the use of VLANs and each switch port is in its own separate collision domain, thus eliminating collisions on the segment. QUESTION 26 Which two commands will display the current IP address and basic Layer 1 and 2 status of an interface? (Choose two.) A. router#show version
- 14. B. router#show ip interface C. router#show protocols D. router#show controllers E. router#show running-config Correct Answer: BC Section: (none) Explanation Explanation/Reference: QUESTION 27 Which two characteristics describe the access layer of the hierarchical network design model? (Choose two.) A. layer 3 support B. port security C. redundant components D. VLANs E. PoE Correct Answer: BD Section: (none) Explanation Explanation/Reference: Explanation: The primary function of an access-layer is to provide network access to the end user. The hardware and software attributes of the access layer that support high availability include security services for additional security against unauthorized access to the network through the use of tools such as 802.1x, port security, DHCP snooping, Dynamic ARP Inspection, and IP Source Guard. QUESTION 28 Refer to the topology and switching table shown in the graphic. Host B sends a frame to Host C. What will the switch do with the frame? A. drop the frame B. send the frame out all ports except port 0/2 C. return the frame to Host B D. send an ARP request for Host C E. send an ICMP Host Unreachable message to Host B F. record the destination MAC address in the switching table and send the frame directly to Host C
- 15. Correct Answer: B Section: (none) Explanation Explanation/Reference: Explanation: QUESTION 29 What is the purpose of assigning an IP address to a switch? A. provides local hosts with a default gateway address B. allows remote management of the switch C. allows the switch to respond to ARP requests between two hosts D. ensures that hosts on the same LAN can communicate with each other Correct Answer: B Section: (none) Explanation Explanation/Reference: Explanation: Switch is a layer 2 device and doesn't use network layer for packet forwarding. The IP address may be used only for administrative purposes such as Telnet access or for network management purposes. QUESTION 30 Which three statements are true about the operation of a full-duplex Ethernet network? (Choose three.) A. There are no collisions in full-duplex mode. B. A dedicated switch port is required for each full-duplex node. C. Ethernet hub ports are preconfigured for full-duplex mode. D. In a full-duplex environment, the host network card must check for the availability of the network media before transmitting. E. The host network card and the switch port must be capable of operating in full-duplex mode. Correct Answer: ABE Section: (none) Explanation Explanation/Reference: Explanation: Half-duplex Ethernet is defined in the original 802.3 Ethernet and Cisco says you only use one wire pair
- 16. with a digital signal running in both directions on the wire. It also uses the CSMA/CD protocol to help prevent collisions and to permit retransmitting if a collision does occur. If a hub is attached to a switch, it must operate in half-duplex mode because the end stations must be able to detect collisions. Half-duplex Ethernet--typically 10BaseT--is only about 30 to 40 percent efficient as Cisco sees it, because a large 10BaseT network will usually only give you 3- to 4Mbps--at most. Full-duplex Ethernet uses two pairs of wires, instead of one wire pair like half duplex. Also, full duplex uses a point-to-point connection between the transmitter of the transmitting device and the receiver of the receiving device, which means that with full-duplex data transfer, you get a faster data transfer compared to half duplex. And because the transmitted data is sent on a different set of wires than the received data, no collisions occur. The reason you don't need to worry about collisions is because now Full-duplex Ethernet is like a freeway with multiple lanes instead of the single-lane road provided by half duplex. Full-duplex Ethernet is supposed to offer 100 percent efficiency in both directions; this means you can get 20Mbps with a 10Mbps Ethernet running full duplex, or 200Mbps for FastEthernet. QUESTION 31 What is the subnet address for the IP address 172.19.20.23/28? A. 172.19.20.0 B. 172.19.20.15 C. 172.19.20.16 D. 172.19.20.20 E. 172.19.20.32 Correct Answer: C Section: (none) Explanation Explanation/Reference: QUESTION 32 What is the subnet address of 172.16.159.159/22? A. 172.16.0.0 B. 172.16.128.0 C. 172.16.156.0 D. 172.16.159.0 E. 172.16.159.128 F. 172.16.192.0 Correct Answer: C Section: (none) Explanation Explanation/Reference: Explanation: Converting to binary format it comes to 11111111.11111111.11111100.00000000 or 255.255.252.0 Starting with 172.16.0.0 and having increment of 4 we get. QUESTION 33 An administrator is working with the 192.168.4.0 network, which has been subnetted with a /26 mask. Which two addresses can be assigned to hosts within the same subnet? (Choose two.) A. 192.168.4.61 B. 192.168.4.63 C. 192.168.4.67 D. 192.168.4.125
- 17. E. 192.168.4.128 F. 192.168.4.132 Correct Answer: CD Section: (none) Explanation Explanation/Reference: Explanation: Only the values of host with 67 and 125 fall within the range of /26 CIDR subnet mask, all others lie beyond it. QUESTION 34 Refer to the exhibit. The internetwork is using subnets of the address 192.168.1.0 with a subnet mask of 255.255.255.224. The routing protocol in use is RIP version 1. Which address could be assigned to the FastEthernet interface on RouterA? A. 192.168.1.31 B. 192.168.1.64 C. 192.168.1.127 D. 192.168.1.190 E. 192.168.1.192 Correct Answer: D Section: (none) Explanation Explanation/Reference: Explanation: Subnet mask 255.255.255.224 with CIDR of /27 which results in 32 hosts per. 192.168.1.31 is the broadcast address for sunbet '0' 192.168.1.64 is the network address for subnet '2' 192.168.1.127 is the broadcast address for subnet '3' 192.168.1.192 is the network address for subnet '6'
- 18. QUESTION 35 What is the network address for the host with IP address 192.168.23.61/28? A. 192.168.23.0 B. 192.168.23.32 C. 192.168.23.48 D. 192.168.23.56 E. 192.168.23.60 Correct Answer: C Section: (none) Explanation Explanation/Reference: Explanation: convert bit-length prefix to quad-dotted decimal representation, then from it find the number of bits used for subnetting you can find previously calculated number of subnets by separating subnets each having value of last bit used for subnet masking Find that your IP address is in which subnet, that subnet's first address is network address and last address is broadcast address. Based on above steps the answer is option C. QUESTION 36 What is the best practice when assigning IP addresses in a small office of six hosts? A. Use a DHCP server that is located at the headquarters. B. Use a DHCP server that is located at the branch office. C. Assign the addresses by using the local CDP protocol. D. Assign the addresses statically on each node. Correct Answer: D Section: (none) Explanation Explanation/Reference: Explanation: Its best to use static addressing scheme where the number of systems is manageable rather than use dynamic protocol as it is easy to operate and manage. QUESTION 37 Refer to the exhibit. The enterprise has decided to use the network address 172.16.0.0. The network administrator needs to design a classful addressing scheme to accommodate the three subnets, with 30, 40, and 50 hosts, as shown. What subnet mask would accommodate this network?
- 19. A. 255.255.255.192 B. 255.255.255.224 C. 255.255.255.240 D. 255.255.255.248 E. 255.255.255.252 Correct Answer: A Section: (none) Explanation Explanation/Reference: Explanation: Subnet mask A i.e. 255.255.255.192 with CIDR of /26 which means 64 hosts per subnet which are sufficient to accommodate even the largest subnet of 50 hosts. QUESTION 38 Which two statements describe the IP address 10.16.3.65/23? (Choose two.) A. The subnet address is 10.16.3.0 255.255.254.0.
- 20. B. The lowest host address in the subnet is 10.16.2.1 255.255.254.0. C. The last valid host address in the subnet is 10.16.2.254 255.255.254.0 D. The broadcast address of the subnet is 10.16.3.255 255.255.254.0. E. The network is not subnetted. Correct Answer: BD Section: (none) Explanation Explanation/Reference: Explanation: The mask 255.255.254.0 (/23) used with a Class A address means that there are 15 subnet bits and 9 host bits. The block size in the third octet is 2 (256 - 254). So this makes the subnets in 0, 2, 4, 6, etc., all the way to 254. The host 10.16.3.65 is in the 2.0 subnet. The next subnet is 4.0, so the broadcast address for the 2.0 subnet is 3.255. The valid host addresses are 2.1 through 3.254 QUESTION 39 Given a Class C IP address subnetted with a /30 subnet mask, how many valid host IP addresses are available on each of the subnets? A. 1 B. 2 C. 4 D. 8 E. 252 F. 254 Correct Answer: B Section: (none) Explanation Explanation/Reference: Explanation: /30 CIDR corresponds to mask 55.255.255.252 whose binary is 11111100 which means 6 subnet bits and 2 host bits which means 62 subnets and 2 hosts per subnet. QUESTION 40 Which one of the following IP addresses is the last valid host in the subnet using mask 255.255.255.224? A. 192.168.2.63 B. 192.168.2.62 C. 192.168.2.61 D. 192.168.2.60 E. 192.168.2.32 Correct Answer: B Section: (none) Explanation Explanation/Reference: Explanation: With the 224 there are 8 networks with increments of 32 One of these is 32 33 62 63 where 63 is broadcast so 62 is last valid host out of given choices. QUESTION 41 An administrator is in the process of changing the configuration of a router. What command will allow the administrator to check the changes that have been made prior to saving the new configuration?
- 21. A. Router# show startup-config B. Router# show current-config C. Router# show running-config D. Router# show memory E. Router# show flash F. Router# show processes Correct Answer: C Section: (none) Explanation Explanation/Reference: Explanation: This command followed by the appropriate parameter will show the running config hence the admin will be able to see what changes have been made, and then they can be saved. QUESTION 42 Which statements accurately describe CDP? (Choose three.) A. CDP is an IEEE standard protocol. B. CDP is a Cisco proprietary protocol. C. CDP is a datalink layer protocol. D. CDP is a network layer protocol. E. CDP can discover directly connected neighboring Cisco devices. F. CDP can discover Cisco devices that are not directly connected. Correct Answer: BCE Section: (none) Explanation Explanation/Reference: Explanation: CDP (Cisco Discovery Protocol) is a proprietary protocol designed by Cisco to help administrators collect information about both locally attached and remote devices. By using CDP, you can gather hardware and protocol information about neighbor devices containing useful info for troubleshooting and documenting the network. QUESTION 43 On a live network, which commands will verify the operational status of router interfaces? (Choose two.) A. Router# show interfaces B. Router# show ip protocols C. Router# debug interface D. Router# show ip interface brief E. Router# show start Correct Answer: AD Section: (none) Explanation Explanation/Reference: Explanation: Both these commands will show the current status of the interfaces, either in show or debug mode both will display the information. QUESTION 44 Which router command will configure an interface with the IP address 10.10.80.1/19?
- 22. A. router(config-if)# ip address 10.10.80.1/19 B. router(config-if)# ip address 10.10.80.1 255.255.0.0 C. router(config-if)# ip address 10.10.80.1 255.255.255.0 D. router(config-if)# ip address 10.10.80.1 255.255.224.0 E. router(config-if)# ip address 10.10.80.1 255.255.240.0 F. router(config-if)# ip address 10.10.80.1 255.255.255.240 Correct Answer: D Section: (none) Explanation Explanation/Reference: Explanation: 255.255.224 equal /19 in CIDR format hence the answer QUESTION 45 Refer to the exhibit. If CDP is enabled on all devices and interfaces, which devices will appear in the output of a show cdp neighbors command issued from R2? A. R2 and R3 B. R1 and R3 C. R3 and S2 D. R1, S1, S2, and R3 E. R1, S1, S2, R3, and S3 Correct Answer: C Section: (none) Explanation Explanation/Reference: Explanation: A Cisco device enabled with CDP sends out periodic interface updates to a multicast address in order to make itself known to neighbors. Since it is a layer two protocol, these packets are not routed. So the devices detected would be immediate connected neighbors. QUESTION 46 Refer to the exhibit. The two routers have had their startup configurations cleared and have been restarted. At a minimum, what must the administrator do to enable CDP to exchange information between R1 and R2? A. Configure the router with the cdp enable command.
- 23. B. Enter no shutdown commands on the R1 and R2 fa0/1 interfaces. C. Configure IP addressing and no shutdown commands on both the R1 and R2 fa0/1 interfaces. D. Configure IP addressing and no shutdown commands on either of the R1 or R2 fa0/1 interfaces. Correct Answer: B Section: (none) Explanation Explanation/Reference: Explanation: If the shut down commands are not entered, then CDP can exchange information between the two routers, else it would fail. QUESTION 47 Refer to the exhibit. The network administrator is testing connectivity from the branch router to the newly installed application server. What is the most likely reason for the first ping having a success rate of only 60 percent? A. The network is likely to be congested, with the result that packets are being intermittently dropped. B. The branch router had to resolve the application server MAC address. C. There is a short delay while NAT translates the server IP address. D. A routing table lookup delayed forwarding on the first two ping packets. E. The branch router LAN interface should be upgraded to FastEthernet. Correct Answer: B Section: (none) Explanation Explanation/Reference: Explanation: Initially the MAC address had to be resolved, but later on it was confirmed to ping went straight away
- 24. QUESTION 48 What two things does a router do when it forwards a packet? (Choose two.) A. switches the packet to the appropriate outgoing interfaces B. computes the destination host address C. determines the next hop on the path D. updates the destination IP address E. forwards ARP requests Correct Answer: AC Section: (none) Explanation Explanation/Reference: Explanation: Without following these two processes namely switching the packet to appropriate interface and telling the packet where to go by providing it with a destination IP address, the purpose of the same would not be solved. QUESTION 49 Which two of these functions do routers perform on packets? (Choose two.) A. examine the Layer 2 headers of inbound packets and use that information to determine the next hops for the packets B. update the Layer 2 headers of outbound packets with the MAC addresses of the next hops C. examine the Layer 3 headers of inbound packets and use that information to determine the next hops for the packets D. examine the Layer 3 headers of inbound packets and use that information to determine the complete paths along which the packets will be routed to their ultimate destinations E. update the Layer 3 headers of outbound packets so that the packets are properly directed to valid next hops F. update the Layer 3 headers of outbound packets so that the packets are properly directed to their ultimate destinations Correct Answer: BC Section: (none) Explanation Explanation/Reference: Explanation: This is the basic function of the router to receive incoming packets and then forward them to their required destination. This is done by reading layer 3 headers of inbound packets and update the info to layer 2 for further hopping. QUESTION 50 Refer to the exhibit. Which two statements are correct? (Choose two.)
- 25. A. This is a default route. B. Adding the subnet mask is optional for the ip route command. C. This will allow any host on the 172.16.1.0 network to reach all known destinations beyond RouterA. D. This command is incorrect, it needs to specify the interface, such as s0/0/0 rather than an IP address. E. The same command needs to be entered on RouterA so that hosts on the 172.16.1.0 network can reach network 10.0.0.0. Correct Answer: AC Section: (none) Explanation Explanation/Reference: Explanation: This is obviously the default value for the route which is set between the routers and since it is entered in such a manner that it ensures connectivity between the stub network and any host lying beyond RouterA. QUESTION 51 Which statements are true regarding ICMP packets? (Choose two.) A. They acknowledge receipt of TCP segments. B. They guarantee datagram delivery. C. TRACERT uses ICMP packets. D. They are encapsulated within IP datagrams. E. They are encapsulated within UDP datagrams. Correct Answer: CD Section: (none) Explanation Explanation/Reference: Explanation: Ping may be used to find out whether the local machines are connected to the network or whether a remote site is reachable. This tool is a common network tool for determining the network connectivity which uses ICMP protocol instead of TCP/IP and UDP/IP. This protocol is usually associated with the
- 26. network management tools which provide network information to network administrators, such as ping and traceroute (the later also uses the UDP/IP protocol). ICMP is quite different from the TCP/IP and UDP/IP protocols. No source and destination ports are included in its packets. Therefore, usual packet-filtering rules for TCP/IP and UDP/IP are not applicable. Fortunately, a special "signature" known as the packet's Message type is included for denoting the purposes of the ICMP packet. Most commonly used message types are namely, 0, 3, 4, 5, 8, 11, and 12 which represent echo reply, destination unreachable, source quench, redirect, echo request, time exceeded, and parameter problem respectively. In the ping service, after receiving the ICMP "echo request" packet from the source location, the destination QUESTION 52 The command ip route 192.168.100.160 255.255.255.224 192.168.10.2 was issued on a router. No routing protocols or other static routes are configured on the router. Which statement is true about this command? A. The interface with IP address 192.168.10.2 is on this router. B. The command sets a gateway of last resort for the router. C. Packets that are destined for host 192.168.100.160 will be sent to 192.168.10.2. D. The command creates a static route for all IP traffic with the source address 192.168.100.160. Correct Answer: C Section: (none) Explanation Explanation/Reference: Explanation: 160 it's actually network address of /27 so any address within the range of 160 network will be sent to 192.168.10.2 QUESTION 53 Refer to the exhibit. Host A can communicate with Host B but not with Hosts C or D. How can the network administrator solve this problem?
- 27. A. Configure Hosts C and D with IP addresses in the 192.168.2.0 network. B. Install a router and configure a route to route between VLANs 2 and 3. C. Install a second switch and put Hosts C and D on that switch while Hosts A and B remain on the original switch. D. Enable the VLAN trunking protocol on the switch. Correct Answer: B Section: (none) Explanation Explanation/Reference: Explanation: Two VLANs require a router in between otherwise they cannot communicate through a simple switch mechanism QUESTION 54 Refer to the exhibit. What is the simplest way to configure routing between the regional office network 10.89.0.0/20 and the corporate network?
- 28. A. router1(config)#ip route 10.89.0.0 255.255.240.0 10.89.16.2 B. router2(config)#ip route 10.89.3.0 255.255.0.0 10.89.16.2 C. router1(config)#ip route 10.89.0.0 255.255.240.0 10.89.16.1 D. router2(config)#ip route 0.0.0.0 0.0.0.0 10.89.16.1 Correct Answer: D Section: (none) Explanation Explanation/Reference: Explanation: The fourth command makes it possible for all hosts beyond R2 and all hosts beyond R1 to interact with each other, hence it is the most simplest technique. QUESTION 55 Refer to the exhibit. Which command would you use to configure a static route on Router1 to network 192.168.202.0/24 with a nondefault administrative distance? A. router1(config)#ip route 1 192.168.201.1 255.255.255.0 192.168.201.2 B. router1(config)#ip route 192.168.202.0 255.255.255.0 192.168.201.2 1 C. router1(config)#ip route 5 192.168.202.0 255.255.255.0 192.168.201.2 D. router1(config)#ip route 192.168.202.0 255.255.255.0 192.168.201.2 5 Correct Answer: D
- 29. Section: (none) Explanation Explanation/Reference: Explanation: Since it has /24 CIDR and it also has a non default administrative distance, the answer has to be option D. QUESTION 56 What does administrative distance refer to? A. the cost of a link between two neighboring routers B. the advertised cost to reach a network C. the cost to reach a network that is administratively set D. a measure of the trustworthiness of a routing information source Correct Answer: D Section: (none) Explanation Explanation/Reference: Explanation: Administrative distance is the first criterion that a router uses to determine which routing protocol to use if two protocols provide route information for the same destination. Administrative distance is a measure of the trustworthiness of the source of the routing information. The smaller the administrative distance value, the more reliable the protocol. QUESTION 57 Which IOS command is used to initiate a login into a VTY port on a remote router? A. router# login B. router# telnet C. router# trace D. router# ping E. router(config)# line vty 0 5 F. router(config-line)# login Correct Answer: B Section: (none) Explanation Explanation/Reference: Explanation: VTY ports are telnet ports hence command B will initiate login to the telnet port. QUESTION 58 In the configuration of NAT, what does the keyword overload signify? A. When bandwidth is insufficient, some hosts will not be allowed to access network translation. B. The pool of IP addresses has been exhausted. C. Multiple internal hosts will use one IP address to access external network resources. D. If the number of available IP addresses is exceeded, excess traffic will use the specified address pool. Correct Answer: C Section: (none) Explanation Explanation/Reference: Explanation: Overload simply means using multiple hosts to access the network using the same translated IP address.
- 30. QUESTION 59 What happens when computers on a private network attempt to connect to the Internet through a Cisco router running PAT? A. The router uses the same IP address but a different TCP source port number for each connection. B. An IP address is assigned based on the priority of the computer requesting the connection. C. The router selects an address from a pool of one-to-one address mappings held in the lookup table. D. The router assigns a unique IP address from a pool of legally registered addresses for the duration of the connection. Correct Answer: A Section: (none) Explanation Explanation/Reference: Explanation: http://www.cisco.com/en/US/docs/security/asa/asa82/configuration/guide/nat_staticpat.html Static PAT translations allow a specific UDP or TCP port on a global address to be translated to a specific port on a local address. That is, both the address and the port numbers are translated. Static PAT is the same as static NAT, except that it enables you to specify the protocol (TCP or UDP) and port for the real and mapped addresses. Static PAT enables you to identify the same mapped address across many different static statements, provided that the port is different for each statement. You cannot use the same mapped address for multiple static NAT statements. Port Address Translation makes the PC connect to the Internet but using different TCP source port. QUESTION 60 When configuring NAT, the Internet interface is considered to be what? A. local B. inside C. global D. outside Correct Answer: D Section: (none) Explanation Explanation/Reference: Explanation: Network address translation or NAT requires the Internet to be considered as an outside interface else it won't serve the purpose it intends to. QUESTION 61 The ip helper-address command does what? A. assigns an IP address to a host B. resolves an IP address from a DNS server C. relays a DHCP request across networks D. resolves an IP address overlapping issue Correct Answer: C Section: (none) Explanation Explanation/Reference: Explanation: When the DHCP client sends the DHCP request packet, it doesn't have an IP address. So it uses the all- zeroes address, 0.0.0.0, as the IP source address. And it doesn't know how to reach the DHCP server, so
- 31. it uses a general broadcast address, 255.255.255.255, for the destination. So the router must replace the source address with its own IP address, for the interface that received the request. And it replaces the destination address with the address specified in the ip helper- address command. The client device's MAC address is included in the payload of the original DHCP request packet, so the router doesn't need to do anything to ensure that the server receives this information. QUESTION 62 Refer to the exhibit. The network administrator made the entries that are shown and then saved the configuration. From a console connection, what password or password sequence is required for the administrator to access privileged mode on Router1? A. cisco B. sanfran C. sanjose D. either cisco or sanfran E. either cisco or sanjose F. sanjose and sanfran Correct Answer: B Section: (none) Explanation Explanation/Reference: Explanation: The enable secret password takes precedence over the enable password, so sanfran will be used. QUESTION 63 The following commands are entered on the router: Burbank(config)# enable secret fortress Burbank(config)# line con 0 Burbank(config-line)# login Burbank(config-line)# password n0way1n Burbank(config-line)# exit Burbank(config)# service password-encryption What is the purpose of the last command entered? A. to require the user to enter an encrypted password during the login process B. to prevent the vty, console, and enable passwords from being displayed in plain text in the configuration files C. to encrypt the enable secret password D. to provide login encryption services between hosts attached to the router Correct Answer: B Section: (none) Explanation Explanation/Reference: Explanation:
- 32. Certain types of passwords, such as Line passwords, by default appear in clear text in the configuration file. You can use the service password-encryption command to make them more secure. Once this command is entered, each password configured is automatically encrypted and thus rendered illegible inside the configuration file (much as the Enable/Enable Secret passwords are). Securing Line passwords is doubly important in networks on which TFTP servers are used, because TFTP backup entails routinely moving config files across networks--and config files, of course, contain Line passwords. QUESTION 64 What is the effect of using the service password-encryption command? A. Only the enable password will be encrypted. B. Only the enable secret password will be encrypted. C. Only passwords configured after the command has been entered will be encrypted. D. It will encrypt the secret password and remove the enable secret password from the configuration. E. It will encrypt all current and future passwords. Correct Answer: E Section: (none) Explanation Explanation/Reference: Explanation: Encryption further adds a level of security to the system as anyone having access to the database of passwords cannot reverse the process of encryption to know the actual passwords which isn't the case if the passwords are stored simply. QUESTION 65 An administrator has connected devices to a switch and, for security reasons, wants the dynamically learned MAC addresses from the address table added to the running configuration. What must be done to accomplish this? A. Enable port security and use the keyword sticky. B. Set the switchport mode to trunk and save the running configuration. C. Use the switchport protected command to have the MAC addresses added to the configuration. D. Use the no switchport port-security command to allow MAC addresses to be added to the configuration. Correct Answer: A Section: (none) Explanation Explanation/Reference: Explanation: One can configure MAC addresses to be sticky. These can be dynamically learned or manually configured, stored in the address table, and added to the running configuration. If these addresses are saved in the configuration file, the interface does not need to dynamically relearn them when the switch restarts, hence enabling security as desired. QUESTION 66 A company has placed a networked PC in a lobby so guests can have access to the corporate directory. A security concern is that someone will disconnect the directory PC and re-connect their laptop computer and have access to the corporate network. For the port servicing the lobby, which three configuration steps should be performed on the switch to prevent this? (Choose three.) A. Enable port security. B. Create the port as a trunk port. C. Create the port as an access port. D. Create the port as a protected port. E. Set the port security aging time to 0.
- 33. F. Statically assign the MAC address to the address table. G. Configure the switch to discover new MAC addresses after a set time of inactivity. Correct Answer: ACF Section: (none) Explanation Explanation/Reference: Explanation: If port security is enabled and the port is only designated as access port, and finally static MAC address is assigned, it ensures that even if a physical connection is done by taking out the directory PC and inserting personal laptop or device, the connection cannot be made to the corporate network, hence ensuring safety. QUESTION 67 Why would a network administrator configure port security on a switch? A. to prevent unauthorized Telnet access to a switch port B. to prevent unauthorized hosts from accessing the LAN C. to limit the number of Layer 2 broadcasts on a particular switch port D. block unauthorized access to the switch management interfaces Correct Answer: B Section: (none) Explanation Explanation/Reference: Explanation: You can use the port security feature to restrict input to an interface by limiting and identifying MAC addresses of the stations allowed to access the port. When you assign secure MAC addresses to a secure port, the port does not forward packets with source addresses outside the group of defined addresses. If you limit the number of secure MAC addresses to one and assign a single secure MAC address, the workstation attached to that port is assured the full bandwidth of the port. If a port is configured as a secure port and the maximum number of secure MAC addresses is reached, when the MAC address of a station attempting to access the port is different from any of the identified secure MAC addresses, a security violation occurs. Also, if a station with a secure MAC address configured or learned on one secure port attempts to access another secure port, a violation is flagged. QUESTION 68 How can you ensure that only the MAC address of a server is allowed by switch port Fa0/1? A. Configure port Fa0/1 to accept connections only from the static IP address of the server. B. Configure the server MAC address as a static entry of port security. C. Use a proprietary connector type on Fa0/1 that is incomputable with other host connectors. D. Bind the IP address of the server to its MAC address on the switch to prevent other hosts from spoofing the server IP address. Correct Answer: B Section: (none) Explanation Explanation/Reference: Explanation: When the MAC address is configured as static entry, no other address is allowed. QUESTION 69 Refer to the exhibit. A network administrator has configured a Catalyst 2950 switch for remote management by pasting into the console the configuration commands that are shown in the exhibit. However, a Telnet session cannot be successfully established from a remote host. What should be done to fix this problem?
- 34. A. Change the first line to interface fastethernet 0/1. B. Change the first line to interface vlan 0/1. C. Change the fifth line to ip default-gateway 192.168.17.241. D. Change the fifth line to ip route 0.0.0.0 0.0.0.0 192.168.17.1. E. Change the sixth line to line con 0. Correct Answer: C Section: (none) Explanation Explanation/Reference: Explanation: The default gateway for remote session is 192.168.17.241 and not the one given in the exhibit. QUESTION 70 Which IP addresses are valid for hosts belonging to the 10.1.160.0/20 subnet? (Choose three.) A. 10.1.168.0 B. 10.1.176.1 C. 10.1.174.255 D. 10.1.160.255 E. 10.1.160.0 F. 10.1.175.255 Correct Answer: ACD Section: (none) Explanation Explanation/Reference: Explanation: All IP address in IP ranges between : 10.1.160.1 and 10.1.175.254 are valid as shown below Address: 10.1.160.0 00001010.00000001.1010 0000.00000000 Netmask:255.255.240.0 = 2011111111.11111111.1111 0000.00000000 Wildcard:0.0.15.25500000000.00000000.0000 1111.11111111 Which implies that Network: 10.1.160.0/20 00001010.00000001.1010 0000.00000000 HostMin:10.1.160.100001010.00000001.1010 0000.00000001 HostMax:10.1.175.25400001010.00000001.1010 1111.11111110 Broadcast:10.1.175.25500001010.00000001.1010 1111.11111111 QUESTION 71 Refer to the exhibit. An administrator cannot connect from R1 to R2. To troubleshoot this problem, the administrator has entered the command shown in the exhibit. Based on the output shown, what could be
- 35. the problem? A. The serial interface is configured for half duplex. B. The serial interface does not have a cable attached. C. The serial interface has the wrong type of cable attached. D. The serial interface is configured for the wrong frame size. E. The serial interface has a full buffer. Correct Answer: C Section: (none) Explanation Explanation/Reference: Explanation: since the output is not forthcoming it shows that the type of cable attached is wrong, though the cable is connected since it shows the cable type. According to the figure DTE cable should connect to R1 on interface but while examining using show controllers serial 0/0 command it showing that a DCE is connected so the wrong type of cable is being used. QUESTION 72 Refer to the exhibit. A TFTP server has recently been installed in the Atlanta office. The network administrator is located in the NY office and has made a console connection to the NY router. After establishing the connection they are unable to backup the configuration file and IOS of the NY router to the TFTP server. What is the cause of this problem?
- 36. A. The NY router has an incorrect subnet mask. B. The TFTP server has an incorrect IP address. C. The TFTP server has an incorrect subnet mask. D. The network administrator computer has an incorrect IP address. Correct Answer: C Section: (none) Explanation Explanation/Reference: Explanation: The subnet mast of the TFTP server needs to be in tune with the other network requirements else it wont be possible. QUESTION 73 If a host experiences intermittent issues that relate to congestion within a network while remaining connected, what could cause congestion on this LAN? A. half-duplex operation B. broadcast storms C. network segmentation D. multicasting Correct Answer: B Section: (none) Explanation Explanation/Reference: Explanation: A broadcast storm can consume sufficient network resources so as to render the network unable to transport normal traffic. QUESTION 74 Refer to the exhibit. The junior network support staff provided the diagram as a recommended configuration for the first phase of a four-phase network expansion project. The entire network expansion will have over 1000 users on 14 network segments and has been allocated this IP address space. 192.168.1.1 through 192.168.5.255 192.168.100.1 through 192.168.100.255 What are three problems with this design? (Choose three.)
- 37. A. The AREA 1 IP address space is inadequate for the number of users. B. The AREA 3 IP address space is inadequate for the number of users. C. AREA 2 could use a mask of /25 to conserve IP address space. D. The network address space that is provided requires a single network-wide mask. E. The router-to-router connection is wasting address space. F. The broadcast domain in AREA 1 is too large for IP to function. Correct Answer: ACE Section: (none) Explanation Explanation/Reference: Explanation: The given IP addresses of areas 1 and 3 along with network masks of 24 cannot accommodate 500 users so are inadequate, while the area 2 is having over capacity so its network mask can be reduced to 25 to accommodate the only 60 users it has. QUESTION 75 Given an IP address of 192.168.1.42 255.255.255.248, what is the subnet address? A. 192.168.1.8/29 B. 192.168.1.32/27 C. 192.168.1.40/29 D. 192.168.1.16/28 E. 192.168.1.48/29 Correct Answer: C Section: (none) Explanation Explanation/Reference: Explanation: 248 mask uses 5 bits (1111 1000) 42 IP in binary is (0010 1010)
- 38. The base subnet therefore is the lowest binary value that can be written without changing the output of an AND operation of the subnet mask and IP ... 1111 1000 AND 0010 1010 equals 0010 1000 - which is .40 /24 is standard class C mask. adding the 5 bits from the .248 mask gives /29 QUESTION 76 Which OSI layer header contains the address of a destination host that is on another network? A. application B. session C. transport D. network E. data link F. physical Correct Answer: D Section: (none) Explanation Explanation/Reference: Explanation: Only network address contains this information. To transmit the packets the sender uses network address and datalink address. But the layer 2 address represents just the address of the next hop device on the way to the sender. It is changed on each hop. Network address remains the same. QUESTION 77 Which layer of the TCP/IP stack combines the OSI model physical and data link layers?
- 39. A. Internet layer B. transport layer C. application layer D. network access layer Correct Answer: D Section: (none) Explanation Explanation/Reference: Explanation: The Internet Protocol Suite, TCP/IP, is a suite of protocols used for communication over the internet. The TCP/IP model was created after the OSI 7 layer model for two major reasons. First, the foundation of the Internet was built using the TCP/IP suite and through the spread of the World Wide Web and Internet, TCP/IP has been preferred. Second, a project researched by the Department of Defense (DOD) consisted of creating the TCP/IP protocols. The DOD's goal was to bring international standards which could not be met by the OSI model. Since the DOD was the largest software consumer and they preferred the TCP/IP suite, most vendors used this model rather then the OSI. Below is a side by side comparison of the TCP/IP and OSI models. TCP/IP Model VS. OSI Model Application Layer 7 Application Layer 6 Presentation Layer 5 Session Transport Layer 4 Transport Internet Layer 3 Network Network Access Layer 2 Data Link Layer 1 Physical QUESTION 78 Which protocol uses a connection-oriented service to deliver files between end systems? A. TFTP B. DNS C. FTP D. SNMP E. RIP Correct Answer: C Section: (none) Explanation Explanation/Reference: Explanation: FTP is an acronym for File Transfer Protocol. As the name suggests, FTP is used to transfer files between computers on a network. You can use FTP to exchange files between computer accounts, transfer files between an account and a desktop computer, or access online software archives QUESTION 79 Refer to the exhibit. If the hubs in the graphic were replaced by switches, what would be virtually eliminated?
- 40. A. broadcast domains B. repeater domains C. Ethernet collisions D. signal amplification E. Ethernet broadcasts Correct Answer: C Section: (none) Explanation Explanation/Reference: Explanation: Modern wired networks use a network switch to eliminate collisions. By connecting each device directly to a port on the switch, either each port on a switch becomes its own collision domain (in the case of half duplex links) or the possibility of collisions is eliminated entirely in the case of full duplex links. QUESTION 80 Refer to the exhibit. If host A sends an IP packet to host B, what will the source physical address be in the frame when it reaches host B? A. 10.168.10.99 B. 10.168.11.88 C. A1:A1:A1:A1:A1:A1
- 41. D. B2:B2:B2:B2:B2:B2 E. C3:C3:C3:C3:C3:C3 F. D4:D4:D4:D4:D4:D4 Correct Answer: E Section: (none) Explanation Explanation/Reference: Explanation: When packets transfer from one host to another across a routed segment, the source IP address always remains the same source IP address, and the source physical (MAC) address will be the existing router's interface address. Similarly, the destination IP address always remains the same and the destination physical (MAC) address is the destination router's interface address. QUESTION 81 Refer to the exhibit. HostX is transferring a file to the FTP server. Point A represents the frame as it goes toward the Toronto router. What will the Layer 2 destination address be at this point? A. abcd.1123.0045 B. 192.168.7.17 C. aabb.5555.2222 D. 192.168.1.1 E. abcd.2246.0035 Correct Answer: E Section: (none) Explanation Explanation/Reference: Explanation: For packets destined to a host on another IP network, the destination MAC address will be the LAN interface of the router. Since the FTP server lies on a different network, the host will know to send the frame to its default gateway, which is Toronto. QUESTION 82 Which network device functions only at Layer 1 of the OSI model?
- 42. A. B. C. D. E. Correct Answer: B Section: (none) Explanation Explanation/Reference: Explanation: Most hubs are amplifying the electrical signal; therefore, they are really repeaters with several ports. Hubs and repeaters are Layer 1 (physical layer) devices. QUESTION 83 Refer to the exhibit. The host in Kiev sends a request for an HTML document to the server in Minsk. What will be the source IP address of the packet as it leaves the Kiev router?
- 43. A. 10.1.0.1 B. 10.1.0.5 C. 10.1.0.6 D. 10.1.0.14 E. 10.1.1.16 F. 10.1.2.8 Correct Answer: E Section: (none) Explanation Explanation/Reference: Explanation: Although the source and destination MAC address will change as a packet traverses a network, the source and destination IP address will not unless network address translation (NAT) is being done, which is not the case here. QUESTION 84 Refer to the exhibit. As packets travel from Mary to Robert, which three devices will use the destination MAC address of the packet to determine a forwarding path? (Choose three.)
- 44. A. Hub1 B. Switch1 C. Router1 D. Switch2 E. Router2 F. Switch3 Correct Answer: BDF Section: (none) Explanation Explanation/Reference: Explanation: Switches use the destination MAC address information for forwarding traffic, while routers use the destination IP address information. Local Area Networks employ Layer 2 Switches and Bridges to forward and filter network traffic. Switches and Bridges operate at the Data Link Layer of the Open System Interconnect Model (OSI). Since Switches and Bridges operate at the Layer 2 they operate more intelligently than hubs, which work at Layer 1 (Physical Layer) of the OSI. Because the switches and bridges are able to listen to the traffic on the wire to examine the source and destination MAC address. Being able to listen to the traffic also allows the switches and bridges to compile a MAC address table to better filter and forward network traffic. To accomplish the above functions switches and bridges carry out the following tasks: MAC address learning by a switch or a bridge is accomplished by the same method. The switch or bridge listens to each device connected to each of its ports and scan the incoming frame for the source MAC address. This creates a MAC address to port map that is cataloged in the switches/bridge MAC database. Another name for the MAC address table is content addressable memory orCAM table. When a switch or bridge is listening o the network traffic, it receives each frame and compares it to the MAC address table. By checking the MAC table the switch/ bridge are able o determine which port the frame came in on. If the frame is on the MAC table the frame is filtered or transmitted on only that port. If the switch determines that the frame is not on the MAC table, the frame is forwarded out to all ports except the incoming port. QUESTION 85 Refer to the exhibit. Mary is sending an instant message to Robert. The message will be broken into a series of packets that will traverse all network devices. What addresses will populate these packets as they are forwarded from Router1 to Router2?
- 45. A. B. C. D. E. Correct Answer: B Section: (none) Explanation Explanation/Reference: Explanation: The Source and Destination IP address is not going to change. Host 1 IP address will stay as being the source IP and the Host 2 IP address will stay the destination IP address. Those two are not going to change. For the MAC address it is going to change each time it goes from one hope to another. (Except
- 46. switches... they don't change anything) Frame leaving HOST 1 is going to have a source MAC of Host 1 and a destination MAC of Router1. Router 1 is going to strip that info off and then will make the source MAC address of Router1's exiting interface, and making Router2's interface as the destination MAC address. Then the same will happen... Router2 is going to change the source/destination info to the source MAC being the Router2 interface that it is going out, and the destination will be Host2's MAC address. QUESTION 86 Refer to the exhibit. A network device needs to be installed in the place of the icon labeled Network Device to accommodate a leased line attachment to the Internet. Which network device and interface configuration meets the minimum requirements for this installation? A. a router with two Ethernet interfaces B. a switch with two Ethernet interfaces C. a router with one Ethernet and one serial interface D. a switch with one Ethernet and one serial interface E. a router with one Ethernet and one modem interface Correct Answer: C Section: (none) Explanation Explanation/Reference: Explanation: Only a router can terminate a leased line attachment access circuit, and only a router can connect two different IP networks. Here, we will need a router with two interfaces, one serial connection for the line attachment and one Ethernet interface to connect to the switch on the LAN. QUESTION 87 Which transport layer protocol provides best-effort delivery service with no acknowledgment receipt required? A. HTTP B. IP C. TCP D. Telnet E. UDP Correct Answer: E Section: (none) Explanation Explanation/Reference: Explanation: UDP provides a connectionless datagram service that offers best-effort delivery, which means that UDP
- 47. does not guarantee delivery or verify sequencing for any datagrams. A source host that needs reliable communication must use either TCP or a program that provides its own sequencing and acknowledgment services. QUESTION 88 Which layer of the OSI model controls the reliability of communications between network devices using flow control, sequencing and acknowledgments? A. Physical B. Data-link C. Transport D. Network Correct Answer: C Section: (none) Explanation Explanation/Reference: Explanation: There are many services that can be optionally provided by a transport-layer protocol, and different protocols may or may not implement them. Connection-oriented communication: It is normally easier for an application to interpret a connection as a data stream rather than having to deal with the underlying connection-less models, such as the datagram model of the User Datagram Protocol (UDP) and of the Internet Protocol (IP). Byte orientation: Rather than processing the messages in the underlying communication system format, it is often easier for an application to process the data stream as a sequence of bytes. This simplification helps applications work with various underlying message formats. Same order delivery: The network layer doesn't generally guarantee that packets of data will arrive in the same order that they were sent, but often this is a desirable feature. This is usually done through the use of segment numbering, with the receiver passing them to the application in order. This can cause head-of-line blocking. Reliability: Packets may be lost during transport due to network congestion and errors. By means of an error detection code, such as a checksum, the transport protocol may check that the data is not corrupted, and verify correct receipt by sending an ACK or NACK message to the sender. Automatic repeat request schemes may be used to retransmit lost or corrupted data. Flow control: The rate of data transmission between two nodes must sometimes be managed to prevent a fast sender from transmitting more data than can be supported by the receiving data buffer, causing a buffer overrun. This can also be used to improve efficiency by reducing buffer underrun. Congestion avoidance: Congestion control can control traffic entry into a telecommunications network, so as to avoid congestive collapse by attempting to avoid oversubscription of any of the processing or link capabilities of the intermediate nodes and networks and taking resource reducing steps, such as reducing the rate of sending packets. For example, automatic repeat requests may keep the network in a congested state; this situation can be avoided by adding congestion avoidance to the flow control, including slow-start. This keeps the bandwidth consumption at a low level in the beginning of the transmission, or after packet retransmission. Multiplexing: Ports can provide multiple endpoints on a single node. For example, the name on a postal address is a kind of multiplexing, and distinguishes between different recipients of the same location. Computer applications will each listen for information on their own ports, which enables the use of more than one network service at the same time. It is part of the transport layer in the TCP/IP model, but of the session layer in the OSI model. QUESTION 89 Refer to the output of the corporate router routing table shown in the graphic. The corporate router receives an IP packet with a source IP address of 192.168.214.20 and a destination address of 192.168.22.3. What will the router do with this packet?
- 48. A. It will encapsulate the packet as Frame Relay and forward it out interface Serial 0/0.117. B. It will discard the packet and send an ICMP Destination Unreachable message out interface FastEthernet 0/0. C. It will forward the packet out interface Serial 0/1 and send an ICMP Echo Reply message out interface serial 0/0.102. D. It will change the IP packet to an ARP frame and forward it out FastEthernet 0/0. Correct Answer: B Section: (none) Explanation Explanation/Reference: QUESTION 90 An administrator must assign static IP addresses to the servers in a network. For network 192.168.20.24/29, the router is assigned the first usable host address while the sales server is given the last usable host address. Which of the following should be entered into the IP properties box for the sales server? A. IP address: 192.168.20.14 Subnet Mask: 255.255.255.248 Default Gateway: 192.168.20.9 B. IP address: 192.168.20.254 Subnet Mask: 255.255.255.0 Default Gateway: 192.168.20.1 C. IP address: 192.168.20.30 Subnet Mask: 255.255.255.248 Default Gateway: 192.168.20.25 D. IP address: 192.168.20.30 Subnet Mask: 255.255.255.240 Default Gateway: 192.168.20.17 E. IP address: 192.168.20.30 Subnet Mask: 255.255.255.240 Default Gateway: 192.168.20.25 Correct Answer: C Section: (none) Explanation Explanation/Reference:
- 49. QUESTION 91 What is the default administrative distance of the OSPF routing protocol? A. 90 B. 100 C. 110 D. 120 E. 130 F. 170 Correct Answer: C Section: (none) Explanation Explanation/Reference: Explanation: Default Distance Value Table This table lists the administrative distance default values of the protocols that Cisco supports: If the administrative distance is 255, the router does not believe the source of that route and does not install the route in the routing table. QUESTION 92 The network administrator has found the following problem. The remote networks 172.16.10.0, 172.16.20.0, and 172.16.30.0 are accessed through the Central router's serial 0/0 interface. No users are able to access 172.16.20.0. After reviewing the command output shown in the graphic, what is the most likely cause of the problem?
- 50. A. no gateway of last resort on Central B. Central router's not receiving 172.16.20.0 update C. incorrect static route for 172.16.20.0 D. 172.16.20.0 not located in Central's routing table Correct Answer: C Section: (none) Explanation Explanation/Reference: QUESTION 93 Refer to the exhibit. The output is from a router in a large enterprise. From the output, determine the role of the router.
- 51. A. A Core router. B. The HQ Internet gateway router. C. The WAN router at the central site. D. Remote stub router at a remote site. Correct Answer: D Section: (none) Explanation Explanation/Reference: QUESTION 94 Refer to the exhibit. For security reasons, information about RTA, including platform and IP addresses, should not be accessible from the Internet. This information should, however, be accessible to devices on the internal networks of RTA. Which command or series of commands will accomplish these objectives? A. RTA(config)#no cdp run B. RTA(config)#no cdp enable C. RTA(config)#interface s0/0 RTA(config-if)#no cdp run
- 52. D. RTA(config)#interface s0/0 RTA(config-if)#no cdp enable Correct Answer: D Section: (none) Explanation Explanation/Reference: QUESTION 95 Refer to the exhibit. The two connected ports on the switch are not turning orange or green. What would be the most effective steps to troubleshoot this physical layer problem? (Choose three.) A. Ensure that the Ethernet encapsulations match on the interconnected router and switch ports. B. Ensure that cables A and B are straight-through cables. C. Ensure cable A is plugged into a trunk port. D. Ensure the switch has power. E. Reboot all of the devices. F. Reseat all cables. Correct Answer: BDF Section: (none) Explanation Explanation/Reference: QUESTION 96 Wich command can you use to manually assign a static IPV6 address to a router interface? A. ipv6 address PREFIX_1::1/64 B. ipv6 autoconfig 2001:db8:2222:7272::72/64 C. ipv6 autoconfig D. ipv6 address 2001:db8:2222:7272::72/64 Correct Answer: D Section: (none) Explanation
- 53. Explanation/Reference: QUESTION 97 The network administrator is using a Windows PC application that is called putty.exe for remote communication to a switch for network troubleshooting. Which two protocols could be used during this communication? (Choose two). A. SNMP B. HTTP C. Telnet D. RMON E. SSH Correct Answer: CE Section: (none) Explanation Explanation/Reference: QUESTION 98 What should be part of a comprehensive network security plan? A. Allow users to develop their own approach to network security. B. Physically secure network equipment from potential access by unauthorized individuals. C. Encourage users to use personal information in their passwords to minimize the likelihood of passwords being forgotten. D. Delay deployment of software patches and updates until their effect on end-user equipment is well known and widely reported. E. Minimize network overhead by deactivating automatic antivirus client updates. Correct Answer: B Section: (none) Explanation Explanation/Reference: QUESTION 99 Which two of these statements are true of IPv6 address representation? (Choose two.) A. There are four types of IPv6 addresses: unicast, multicast, anycast, and broadcast. B. A single interface may be assigned multiple IPv6 addresses of any type. C. Every IPv6 interface contains at least one loopback address. D. The first 64 bits represent the dynamically created interface ID. E. Leading zeros in an IPv6 16 bit hexadecimal field are mandatory. Correct Answer: BC Section: (none) Explanation Explanation/Reference: Explanation: http://www.cisco.com/en/US/technologies/tk648/tk872/technologies_white_paper0900aecd 8026003d.pdf A single interface may be assigned multiple addresses of any type (unicast, anycast, multicast). Every IPv6-enabled interface must contain at least one loopback and one link-local address. Optionally, every interface can have multiple unique local and global addresses. IPv6 host addresses can
- 54. be assigned in multiple ways: Static configuration Stateless autoconfiguration DHCPv6 When IPv6 is used over Ethernet networks, the Ethernet MAC address can be used to generate the 64-bit interface ID for the host. This is called the EUI-64 address. Since MAC addresses use 48 bits, additional bits must be inserted to fill the 64 bits required. QUESTION 100 A network administrator cannot connect to a remote router by using SSH. Part of the show interfaces command is shown. router#show interfaces Serial0/1/0 is up, line protocol is down At which OSI layer should the administrator begin troubleshooting? A. physical B. data link C. network D. transport Correct Answer: B Section: (none) Explanation Explanation/Reference: Explanation: https://learningnetwork.cisco.com/thread/12389 I think the indication here is "Serial 0 is up, line protocol is down". What causes this indication? Correct me if I am wrong. When you have this indication, a cable unplugged is not a correct answer. If you check the output of your "show interface serial 0" command again, you should notice it as "Serial 0 is down, line protocol is down. Under the "show ip int brief" you should see status = down and protocol = down as opposed to up, down. Because you disconnected the cable, layer 1 will go down, which is indicated by the serial 0 down status. The line protocol status is for layer 2. So, a cable unplugged is not a correct answer to "Serial 0 is up, line protocol is down". Hope this helps. QUESTION 101
- 55. Refer to the exhibit. A person is trying to send a file from a host on Network A of the JAX Company to a server on Network Z of the XYZ Company. The file transfer fails. The host on Network A can communicate with other hosts on Network A. Which command, issued from router RTA, would be the most useful for troubleshooting this problem? A. show flash: B. show history C. show version D. show interfaces E. show controllers serial Correct Answer: D Section: (none) Explanation Explanation/Reference: QUESTION 102 Refer to the exhibit. A user cannot reach any web sites on the Internet, but others in the department are not having a problem. What is the most likely cause of the problem? A. IP routing is not enabled. B. The default gateway is not in the same subnet. C. A DNS server address is not reachable by the PC. D. A DHCP server address is not reachable by the PC. E. NAT has not been configured on the router that connects to the Internet.
- 56. Correct Answer: C Section: (none) Explanation Explanation/Reference: QUESTION 103 Which option is a valid IPv6 address? A. 2001:0000:130F::099a::12a B. 2002:7654:A1AD:61:81AF:CCC1 C. FEC0:ABCD:WXYZ:0067::2A4 D. 2004:1:25A4:886F::1 Correct Answer: D Section: (none) Explanation Explanation/Reference: Explanation: http://www.ipv6.com/articles/general/IPv6-Addressing.htm IPv6 Address Notation IPv6 addresses are denoted by eight groups of hexadecimal quartets separated by colons in between them. Following is an example of a valid IPv6 address: 2001:cdba:0000:0000:0000:0000:3257:9652 Any four-digit group of zeroes within an IPv6 address may be reduced to a single zero or altogether omitted. Therefore, the following IPv6 addresses are similar and equally valid: 2001:cdba:0000:0000:0000:0000:3257:9652 2001:cdba:0:0:0:0:3257:9652 2001:cdba::3257:9652 The URL for the above address will be of the form: http://[2001:cdba:0000:0000:0000:0000:3257:9652]/ QUESTION 104 What is the purpose of the switchport command? Switch(config-if)# switchport port-security maximum 1 Switch(config-if)# switchport port-security mac-address 0018.DE8B.4BF8 A. It ensures that only the device with the MAC address 0018.DE8B.4BF8 will be able to connect to the port that is being configured. B. It informs the switch that traffic destined for MAC address 0018.DE8B.4BF8 should only be sent to the port that is being configured. C. It will act like an access list and the port will filter packets that have a source or destination MAC of 0018.DE8B.4BF8. D. The switch will shut down the port of any traffic with source MAC address of 0018.DE8B.4BF8. Correct Answer: A Section: (none) Explanation Explanation/Reference: QUESTION 105 Refer to the exhibit. A network administrator is troubleshooting a connectivity problem on the serial interfaces. The output from the show interfaces command on both routers shows that the serial interface is
- 57. up, line protocol is down. Given the partial output for the show running-config in the exhibit, what is the most likely cause of this problem? A. The serial cable is bad. B. The MTU is incorrectly configured. C. The Layer 2 framing is misconfigured. D. The IP addresses are not in the same subnet. Correct Answer: C Section: (none) Explanation Explanation/Reference: QUESTION 106 How many bits are contained in each field of an IPv6 address? A. 24 B. 4 C. 8 D. 16 Correct Answer: D Section: (none) Explanation Explanation/Reference: Explanation: http://www.cisco.com/en/US/technologies/tk648/tk872/technologies_white_paper0900aecd 8026003d.pdf One of the key advantages IPv6 brings is the exponentially larger address space. The following will outline the basic address architecture of IPv6. 128-bit-long addresses Represented in hexadecimal format: Uses CIDR principles: prefix/prefix length x:x:x:x:x:x:x:x, where x is a 16-bit hex field The last 64 bits are used for the interface ID QUESTION 107 Refer to the exhibit. The DHCP settings have recently been changed on the DHCP server and the client is no longer able to reach network resources. What should be done to correct this situation?
- 58. A. Verify that the DNS server address is correct in the DHCP pool. B. Ping the default gateway to populate the ARP cache. C. Use the tracert command on the DHCP client to first determine where the problem is located. D. Clear all DHCP leases on the router to prevent address conflicts. E. Issue the ipconfig command with the /release and /renew options in a command window. Correct Answer: E Section: (none) Explanation Explanation/Reference: QUESTION 108 Which three approaches can be used while migrating from an IPv4 addressing scheme to an IPv6 scheme (choose three) A. static mapping of IPv4 address to IPv6 addresses B. configuring IPv4 tunnels between IPv6 islands C. use DHCPv6 to map IPv4 addresses to IPv6 addresses D. use proxying and translation (NAT-PT) to translate IPv6 packets into IPv4 packets E. configure IPv6 directly F. enable dual-stack routing Correct Answer: BDF Section: (none) Explanation Explanation/Reference: Explanation: http://www.opus1.com/ipv6/howdoitransitiontoipv6.html Connecting IPv6 islands with tunnels An IPv6 island is a network made of IPv6 links directly connected by IPv6 routers. In the early days of IPv6 deployment, there are many IPv6 islands. IPv6 in IPv4 tunnels are used to connect those islands together. In each island, one (or more) dual stack routers are designated to encapsulate and decapsulate IPv6 packets within IPv4 packets. Different mechanisms have been developed to manage tunnels: automatic tunnels3, configured tunnels3, tunnel brokers3, 6over43, 6to43,... http://www.petri.co.il/ipv6-transition.htm Network Address Translation - Protocol Translation (NAT-PT) The NAT-PT method enables the ability to either statically or dynamically configure a translation of a IPv4 network address into an IPv6 network address and vice versa. For those familiar with more typically NAT implementations, the operation is very similar but includes a protocol translation function. NAT-PT also ties in an Application Layer Gateway (ALG) functionality that converts Domain Name System (DNS) mappings between protocols. Dual Stack
- 59. The simplest approach when transitioning to IPv6 is to run IPv6 on all of the devices that are currently running IPv4. If this is something that is possible within the organizational network, it is very easy to implement. However, for many organizations, IPv6 is not supported on all of the IPv4 devices; in these situations other methods must be considered. QUESTION 109 Refer to the exhibit. A network technician is asked to design a small network with redundancy. The exhibit represents this design, with all hosts configured in the same VLAN. What conclusions can be made about this design? A. This design will function as intended. B. Spanning-tree will need to be used. C. The router will not accept the addressing scheme. D. The connection between switches should be a trunk. E. The router interfaces must be encapsulated with the 802.1Q protocol. Correct Answer: C Section: (none) Explanation Explanation/Reference: QUESTION 110 Refer to the exhibit. An administrator replaced the 10/100 Mb NIC in a desktop PC with a 1 Gb NIC and now the PC will not connect to the network. The administrator began troubleshooting on the switch. Using the switch output shown, what is the cause of the problem?
- 60. A. Speed is set to 100Mb/s. B. Input flow control is off. C. Encapsulation is set to ARPA. D. The port is administratively down. E. The counters have never been cleared. Correct Answer: A Section: (none) Explanation Explanation/Reference: QUESTION 111 Refer to the exhibit. A technician is troubleshooting a host connectivity problem. The host is unable to ping a server connected to Switch_A. Based on the results of the testing, what could be the problem? A. A remote physical layer problem exists. B. The host NIC is not functioning. C. TCP/IP has not been correctly installed on the host. D. A local physical layer problem exists. Correct Answer: D Section: (none) Explanation
- 61. Explanation/Reference: QUESTION 112 Which statement about IPv6 is true? A. Addresses are not hierarchical and are assigned at random. B. Only one IPv6 address can exist on a given interface. C. There are 2.7 billion addresses available. D. Broadcasts have been eliminated and replaced with multicasts. Correct Answer: D Section: (none) Explanation Explanation/Reference: Explanation: http://technet.microsoft.com/en-us/library/cc757359(v=ws.10).aspx IPv6 has three types of addresses, which can be categorized by type and scope: Unicast addresses. A packet is delivered to one interface. Multicast addresses. A packet is delivered to multiple interfaces. Anycast addresses. A packet is delivered to the nearest of multiple interfaces (in terms of routing distance). IPv6 does not use broadcast messages. Unicast and anycast addresses in IPv6 have the following scopes (for multicast addresses, the scope are built into the address structure): Link-local. The scope is the local link (nodes on the same subnet). Site-local. The scope is the organization (private site addressing). Global. The scope is global (IPv6 Internet addresses). In addition, IPv6 has special addresses such as the loopback address. The scope of a special address depends on the type of special address. Much of the IPv6 address space is unassigned. QUESTION 113 What are two recommended ways of protecting network device configuration files from outside network security threats? (Choose two.) A. Allow unrestricted access to the console or VTY ports. B. Use a firewall to restrict access from the outside to the network devices. C. Always use Telnet to access the device command line because its data is automatically encrypted. D. Use SSH or another encrypted and authenticated transport to access device configurations. E. Prevent the loss of passwords by disabling password encryption. Correct Answer: BD Section: (none) Explanation Explanation/Reference: QUESTION 114 Refer to the exhibit. A problem with network connectivity has been observed. It is suspected that the cable connected to switch port Fa0/9 on Switch1 is disconnected. What would be an effect of this cable being disconnected?
- 62. A. Host B would not be able to access the server in VLAN9 until the cable is reconnected. B. Communication between VLAN3 and the other VLANs would be disabled. C. The transfer of files from Host B to the server in VLAN9 would be significantly slower. D. For less than a minute, Host B would not be able to access the server in VLAN9. Then normal network function would resume. Correct Answer: D Section: (none) Explanation Explanation/Reference: QUESTION 115 A receiving host has failed to receive all of the segments that it should acknowledge. What can the host do to improve the reliability of this communication session? A. decrease the window size B. use a different source port for the session C. decrease the sequence number D. obtain a new IP address from the DHCP server E. start a new session using UDP Correct Answer: A Section: (none) Explanation Explanation/Reference: QUESTION 116 Which command enables IPv6 forwarding on a cisco router? A. ipv6 host B. ipv6 unicast-routing C. ipv6 local D. ipv6 neighbor Correct Answer: B Section: (none) Explanation
- 63. Explanation/Reference: Explanation: Enabling IPv6 on Cisco IOS Software Technology http://www.ciscopress.com/articles/article.asp?p=31948&seqNum=4 The first step of enabling IPv6 on a Cisco router is the activation of IPv6 traffic forwarding to forward unicast IPv6 packets between network interfaces. By default, IPv6 traffic forwarding is disabled on Cisco routers. The ipv6 unicast-routing command is used to enable the forwarding of IPv6 packets between interfaces on the router. The syntax for this command is as follows: Router(config)#ipv6 unicast-routing The ipv6 unicast-routing command is enabled on a global basis. QUESTION 117 Refer to the exhibit. A host is connected to switch port fa0/3. The host and switch have been fully configured for IP connectivity as shown. However, the indicator LED on switch port fa0/3 is not on, and the host cannot communicate with any other hosts including those connected to VLAN 2 on the same switch. Based on the given information, what is the problem? A. switch port fa0/3 is not configured as a trunk port B. there is a bad cable C. the switch has been assigned an incorrect subnet mask D. switch port fa0/3 has been blocked by STP E. the switch and the host must be in the same subnet Correct Answer: B Section: (none) Explanation Explanation/Reference: QUESTION 118 Identify the four valid IPv6 addresses. (Choose four.) A. :: B. ::192:168:0:1 C. 2000:: D. 2001:3452:4952:2837:: E. 2002:c0a8:101::42 F. 2003:dead:beef:4dad:23:46:bb:101 Correct Answer: ABEF Section: (none) Explanation Explanation/Reference:
- 64. Explanation: http://www.intermapper.com/ipv6validator http://www.ripe.net/lir-services/new-lir/ipv6_reference_card.pdf QUESTION 119 Which two statements describe characteristics of IPv6 unicast addressing? (Choose two.) A. Global addresses start with 2000::/3. B. Link-local addresses start with FE00:/12. C. Link-local addresses start with FF00::/10. D. There is only one loopback address and it is ::1. E. If a global address is assigned to an interface, then that is the only allowable address for the interface. Correct Answer: AD Section: (none) Explanation Explanation/Reference: QUESTION 120 A network administrator is trying to add a new router into an established OSPF network. The networks attached to the new router do not appear in the routing tables of the other OSPF routers. Given the information in the partial configuration shown below, what configuration error is causing this problem? Router(config)# router ospf 1 Router(config-router)# network 10.0.0.0 255.0.0.0 area 0 A. The process id is configured improperly. B. The OSPF area is configured improperly. C. The network wildcard mask is configured improperly. D. The network number is configured improperly. E. The AS is configured improperly. F. The network subnet mask is configured improperly.
- 65. Correct Answer: C Section: (none) Explanation Explanation/Reference: Explanation: When configuring OSPF, the mask used for the network statement is a wildcard mask similar to an access list. In this specific example, the correct syntax would have been "network 10.0.0.0 0.0.0.255 area 0." QUESTION 121 Which statement is true? A. An IPv6 address is 64 b long and is represented as hexadecimal characters. B. An IPv6 address is 32 b long and is represented as decimal digits. C. An IPv6 address is 128 b long and is represented as decimal digits. D. An IPv6 address is 128 b long and is represented as hexadecimal characters. Correct Answer: D Section: (none) Explanation Explanation/Reference: QUESTION 122 What information does a router running a link-state protocol use to build and maintain its topological database? (Choose two) A. hello packets B. SAP messages sent by other routers C. LSAs from other routers D. beacons received on point-to-point links E. routing tables received from other link-state routers F. TTL packets from designated routers Correct Answer: AC Section: (none) Explanation Explanation/Reference: QUESTION 123 ROUTER# show ip route 192.168.12.0/24 is variably subnetted, 9 subnets, 3 masks C 192.168.12.64 /28 is directly connected, Loopback1 C 192.168.12.32 /28 is directly connected, Ethernet0 C 192.168.12.48 /28 is directly connected, Loopback0 O 192.168.12.236 /30 [110/128] via 192.168.12.233, 00:35:36, Serial0 C 192.168.12.232 /30 is directly connected, Serial0 O 192.168.12.245 /30 [110/782] via 192.168.12.233, 00:35:36, Serial0 O 192.168.12.240 /30 [110/128] via 192.168.12.233, 00:35:36, Serial0 O 192.168.12.253 /30 [110/782] via 192.168.12.233, 00:35:37, Serial0 O 192.168.12.249 /30 [110/782] via 192.168.12.233, 00:35:37, Serial0 O 192.168.12.240/30 [110/128] via 192.168.12.233, 00:35:36, Serial 0 To what does the 128 refer to in the router output above? A. OSPF cost B. OSPF priority
- 66. C. OSPF hop count D. OSPF ID number E. OSPF administrative distance Correct Answer: A Section: (none) Explanation Explanation/Reference: Explanation: The first parameter is the Administrative Distance of OSPF (110) while the second parameter is the cost of OSPF. QUESTION 124 Which of the following describe the process identifier that is used to run OSPF on a router? (Choose two) A. It is locally significant. B. It is globally significant. C. It is needed to identify a unique instance of an OSPF database. D. It is an optional parameter required only if multiple OSPF processes are running on the router. E. All routers in the same OSPF area must have the same process ID if they are to exchange routing information. Correct Answer: AC Section: (none) Explanation Explanation/Reference: Explanation: https://learningnetwork.cisco.com/thread/6248 They are locally significant only, and have no bearing on the structure of any OSPF packet or LSA update. So you can have a separate process-id on every single router in your network if you so desire! QUESTION 125 Open Shortest Path First (OSPF) is a routing protocol developed for Internet Protocol (IP) networks by the Interior Gateway Protocol (IGP) working group of the Internet Engineering Task Force (IETF). What is the default administrative distance of the OSPF routing protocol? A. 90 B. 100 C. 110 D. 20 E. 130 F. 170 Correct Answer: C Section: (none) Explanation Explanation/Reference: QUESTION 126 The internetwork infrastructure of company XYZ consists of a single OSPF area as shown in the graphic. There is concern that a lack of router resources is impeding internetwork performance. As part of examining the router resources, the OSPF DRs need to be known. All the router OSPF priorities are at the default and the router IDs are shown with each router. Which routers are likely to have been elected as DR? (Choose two.)
- 67. A. Corp-1 B. Corp-2 C. Corp-3 D. Corp-4 E. Branch-1 F. Branch-2 Correct Answer: DF Section: (none) Explanation Explanation/Reference: Explanation There are 2 segments on the topology above which are separated by Corp-3 router. Each segment will have a DR so we have 2 DRs. To select which router will become DR they will compare their router-IDs. The router with highest (best) router-ID will become DR. The router-ID is chosen in the order below: + The highest IP address assigned to a loopback (logical) interface. + If a loopback interface is not defined, the highest IP address of all active router's physical interfaces will be chosen. In this question, the IP addresses of loopback interfaces are not mentioned so we will consider IP addresses of all active router's physical interfaces. Router Corp-4 (10.1.40.40) & Branch-2 (10.2.20.20) have highest "active" IP addresses so they will become DRs. QUESTION 127 Which address are OSPF hello packets addressed to on point-to-point networks? A. 224.0.0.5 B. 172.16.0.1 C. 192.168.0.5 D. 223.0.0.1 E. 254.255.255.255 Correct Answer: A Section: (none) Explanation Explanation/Reference: Explanation: Why Does the show ip ospf neighbor Command Reveal Neighbors in the Init State? http://www.cisco.com/en/US/tech/tk365/technologies_tech_note09186a0080093f11.shtml
- 68. OSPF hello packets have a destination address of 224.0.0.5 (the all ospf routers multicast address). QUESTION 128 Which statements describe the routing protocol OSPF? (Choose three) A. It supports VLSM. B. It is used to route between autonomous systems. C. It confines network instability to one area of the network. D. It increases routing overhead on the network. E. It allows extensive control of routing updates. F. It is simpler to configure than RIP v2. Correct Answer: ACE Section: (none) Explanation Explanation/Reference: Explanation: The OSPF protocol is based on link-state technology, which is a departure from the Bellman-Ford vector based algorithms used in traditional Internet routing protocols such as RIP. OSPF has introduced new concepts such as authentication of routing updates, Variable Length Subnet Masks (VLSM), route summarization, and so forth. OSPF uses flooding to exchange link-state updates between routers. Any change in routing information is flooded to all routers in the network. Areas are introduced to put a boundary on the explosion of link-state updates. Flooding and calculation of the Dijkstra algorithm on a router is limited to changes within an area. QUESTION 129 Refer to the graphic. R1 is unable to establish an OSPF neighbor relationship with R3. What are possible reasons for this problem? (Choose two) A. All of the routers need to be configured for backbone Area 1 B. R1 and R2 are the DR and BDR, so OSPF will not establish neighbor adjacency with R3 C. A static route has been configured from R1 to R3 and prevents the neighbor adjacency from being established. D. The hello and dead interval timers are not set to the same values on R1 and R3 E. EIGRP is also configured on these routers with a lower administrative distance F. R1 and R3 are configured in different areas Correct Answer: DF Section: (none) Explanation Explanation/Reference: Explanation: This question is to examine the conditions for OSPF to create neighborhood. So as to make the two
- 69. routers become neighbors, each router must be matched with the following items: 1. The area ID and its types; 2. Hello and failure time interval timer; 3. OSPF Password (Optional); QUESTION 130 Given the output for this command, if the router ID has not been manually set, what router ID will OSPF use for this router? A. 10.1.1.2 B. 10.154.154.1 C. 172.16.5.1 D. 192.168.5.3 Correct Answer: C Section: (none) Explanation Explanation/Reference: Explanation: The highest IP address of all loopback interfaces will be chosen -> Loopback 0 will be chosen as the router ID. QUESTION 131 Which parameter or parameters are used to calculate OSPF cost in Cisco routers? A. Bandwidth B. Bandwidth and Delay C. Bandwidth, Delay, and MTU D. Bandwidth, MTU, Reliability, Delay, and Load Correct Answer: A Section: (none) Explanation Explanation/Reference: Explanation: The well-known formula to calculate OSPF cost is Cost = 108 / Bandwidth QUESTION 132 Why do large OSPF networks use a hierarchical design? (Choose three.) A. to decrease latency by increasing bandwidth B. to reduce routing overhead C. to speed up convergence D. to confine network instability to single areas of the network E. to reduce the complexity of router configuration F. to lower costs by replacing routers with distribution layer switches
- 70. Correct Answer: BCD Section: (none) Explanation Explanation/Reference: Explanation: OSPF implements a two-tier hierarchical routing model that uses a core or backbone tier known as area zero (0). Attached to that backbone via area border routers (ABRs) are a number of secondary tier areas. The hierarchical approach is used to achieve the following: - Rapid convergence because of link and/or switch failures - Deterministic traffic recovery - Scalable and manageable routing hierarchy, reduced routing overhead. QUESTION 133 Refer to the exhibit. When running OSPF, what would cause router A not to form an adjacency with router B? A. The loopback addresses are on different subnets. B. The values of the dead timers on the routers are different. C. Route summarization is enabled on both routers. D. The process identifier on router A is different than the process identifier on router B. Correct Answer: B Section: (none) Explanation Explanation/Reference: Explanation: To form an adjacency (become neighbor), router A & B must have the same Hello interval, Dead interval and AREA numbers QUESTION 134 A router has learned three possible routes that could be used to reach a destination network. One route is from EIGRP and has a composite metric of 20514560. Another route is from OSPF with a metric of 782. The last is from RIPv2 and has a metric of 4. Which route or routes will the router install in the routing table? A. the OSPF route B. the EIGRP route C. the RIPv2 route D. all three routes E. the OSPF and RIPv2 routes Correct Answer: B Section: (none) Explanation
- 71. Explanation/Reference: Explanation: When one route is advertised by more than one routing protocol, the router will choose to use the routing protocol which has lowest Administrative Distance. The Administrative Distances of popular routing protocols are listed below: QUESTION 135 Which command is used to display the collection of OSPF link states? A. show ip ospf link-state B. show ip ospf lsa database C. show ip ospf neighbors D. show ip ospf database Correct Answer: D Section: (none) Explanation Explanation/Reference: Explanation: The "show ip ospf database" command displays the link states. Here is an example: Here is the lsa database on R2. QUESTION 136 Refer to the exhibit. A network associate has configured OSPF with the command: City(config-router)# network 192.168.12.64 0.0.0.63 area 0 After completing the configuration, the associate discovers that not all the interfaces are participating in OSPF. Which three of the interfaces shown in the exhibit will participate in OSPF according to this configuration statement? (Choose three.)
- 72. A. FastEthernet0 /0 B. FastEthernet0 /1 C. Serial0/0 D. Serial0/1.102 E. Serial0/1.103 F. Serial0/1.104 Correct Answer: BCD Section: (none) Explanation Explanation/Reference: Explanation: The "network 192.168.12.64 0.0.0.63 equals to network 192.168.12.64/26. This network has: + Increment: 64 (/26= 1111 1111.1111 1111.1111 1111.1100 0000) + Network address: 192.168.12.64 + Broadcast address: 192.168.12.127 Therefore all interface in the range of this network will join OSPF. QUESTION 137 What is the default administrative distance of OSPF? A. 90 B. 100 C. 110 D. 120 Correct Answer: C Section: (none) Explanation Explanation/Reference: Explanation: Administrative distance is the feature that routers use in order to select the best path when there are two or more different routes to the same destination from two different routing protocols. Administrative distance defines the reliability of a routing protocol. Each routing protocol is prioritized in order of most to least reliable (believable) with the help of an administrative distance value. Default Distance Value Table This table lists the administrative distance default values of the protocols that Cisco supports:
- 73. QUESTION 138 Which two statements describe the process identifier that is used in the command to configure OSPF on a router? (Choose two.) Router(config)# router ospf 1 A. All OSPF routers in an area must have the same process ID. B. Only one process number can be used on the same router. C. Different process identifiers can be used to run multiple OSPF processes D. The process number can be any number from 1 to 65,535. E. Hello packets are sent to each neighbor to determine the processor identifier. Correct Answer: CD Section: (none) Explanation Explanation/Reference: Explanation: Multiple OSPF processes can be configured on a router using multiple process ID's. The valid process ID's are shown below: Edge-B(config)#router ospf ? <1-65535> Process ID QUESTION 139 Which commands are required to properly configure a router to run OSPF and to add network 192.168.16.0/24 to OSPF area 0? (Choose two.) A. Router(config)# router ospf 0 B. Router(config)# router ospf 1 C. Router(config)# router ospf area 0
- 74. D. Router(config-router)# network 192.168.16.0 0.0.0.255 0 E. Router(config-router)# network 192.168.16.0 0.0.0.255 area 0 F. Router(config-router)# network 192.168.16.0 255.255.255.0 area 0 Correct Answer: BE Section: (none) Explanation Explanation/Reference: Explanation: In the router ospf command, the ranges from 1 to 65535 so o is an invalid number -> but To configure OSPF, we need a wildcard in the "network" statement, not a subnet mask. We also need to assgin an area to this process -> . QUESTION 140 What is the default maximum number of equal-cost paths that can be placed into the routing table of a Cisco OSPF router? A. 2 B. 8 C. 16 D. unlimited Correct Answer: B Section: (none) Explanation Explanation/Reference: Explanation: maximum-paths (OSPF) To control the maximum number of parallel routes that Open Shortest Path First (OSPF) can support, use the maximum-paths command. Syntax Description Command Default 8 paths QUESTION 141 A network administrator is troubleshooting the OSPF configuration of routers R1 and R2. The routers cannot establish an adjacency relationship on their common Ethernet link.
- 75. The graphic shows the output of the show ip ospf interface e0 command for routers R1 and R2. Based on the information in the graphic, what is the cause of this problem? A. The OSPF area is not configured properly. B. The priority on R1 should be set higher. C. The cost on R1 should be set higher. D. The hello and dead timers are not configured properly. E. A backup designated router needs to be added to the network. F. The OSPF process ID numbers must match. Correct Answer: D Section: (none) Explanation Explanation/Reference: Explanation: In OSPF, the hello and dead intervals must match and here we can see the hello interval is set to 5 on R1 and 10 on R2. The dead interval is also set to 20 on R1 but it is 40 on R2. QUESTION 142 OSPF routing uses the concept of areas. What are the characteristics of OSPF areas? (Choose Three.) A. Each OSPF area requires a loopback interface to be configured. B. Areas may be assigned any number from 0 to 65535. C. Area 0 is called the backbone area. D. Hierarchical OSPF networks do not require multiple areas. E. Multiple OSPF areas must connect to area 0. F. Single area OSPF networks must be configured in area 1. Correct Answer: BCE Section: (none) Explanation Explanation/Reference: Explanation: Definition of OSPF areas: An OSPF network may be structured, or subdivided, into routing areas to simplify administration and optimize traffic and resource utilization. Areas are identified by 32- bit numbers, expressed either simply in decimal, or often in octet-based dot-decimal notation, familiar from IPv4 address notation. See discussion following Cisco Learning discussion. https://learningnetwork.cisco.com/message/90832 QUESTION 143
- 76. Refer to the exhibit. Assume that all router interfaces are operational and correctly configured. In addition, assume that OSPF has been correctly configured on router R2. How will the default route configured on R1 affect the operation of R2? A. Any packet destined for a network that is not directly connected to router R2 will be dropped immediately. B. Any packet destined for a network that is not referenced in the routing table of router R2 will be directed to R1. R1 will then send that packet back to R2 and a routing loop will occur. C. Any packet destined for a network that is not directly connected to router R1 will be dropped. D. The networks directly connected to router R2 will not be able to communicate with the 172.16.100.0, 172.16.100.128, and 172.16.100.64 subnetworks. E. Any packet destined for a network that is not directly connected to router R2 will be dropped immediately because of the lack of a gateway on R1. Correct Answer: B Section: (none) Explanation Explanation/Reference: Explanation: First, notice that the more-specific routes will always be favored over less-specific routes regardless of the administrative distance set for a protocol. In this case, because we use OSPF for three networks (172.16.100.0 0.0.0.3, 172.16.100.64 0.0.0.63, 172.16.100.128 0.0.0.31) so the packets destined for these networks will not be affected by the default route. The default route configured on R1 "ip route 0.0.0.0 0.0.0.0 serial0/0 will send any packet whose destination network is not referenced in the routing table of router R1 to R2, it doesn't drop anything. These routes are declared in R1 and the question says that "OSPF has been correctly configured on router R2, so network directly connected to router R2 can communicate with those three subnetworks. As said above, the default route configured on R1 will send any packet destined for a network that is not referenced in its routing table to R2; R2 in turn sends it to R1 because it is the only way and a routing loop will occur. QUESTION 144 Refer to the exhibit. Which two statements are true about the loopback address that is configured on RouterB? (Choose two.)
- 77. A. It ensures that data will be forwarded by RouterB. B. It provides stability for the OSPF process on RouterB. C. It specifies that the router ID for RouterB should be 10.0.0.1. D. It decreases the metric for routes that are advertised from RouterB. E. It indicates that RouterB should be elected the DR for the LAN. Correct Answer: BC Section: (none) Explanation Explanation/Reference: Explanation: A loopback interface never comes down even if the link is broken so it provides stability for the OSPF process (for example we use that loopback interface as the router-id) - The router-ID is chosen in the order below: + The highest IP address assigned to a loopback (logical) interface. + If a loopback interface is not defined, the highest IP address of all active router's physical interfaces will be chosen. -> The loopback interface will be chosen as the router ID of RouterB - QUESTION 145 Which characteristics are representative of a link-state routing protocol? (Choose three.) A. provides common view of entire topology B. exchanges routing tables with neighbors C. calculates shortest path D. utilizes event-triggered updates E. utilizes frequent periodic updates Correct Answer: ACD Section: (none) Explanation Explanation/Reference: Explanation: Each of routers running link-state routing protocol learns paths to all the destinations in its "area" so we can say although it is a bit unclear. Link-state routing protocols generate routing updates only (not the whole routing table) when a change occurs in the network topology so Link-state routing protocol like OSPF uses Dijkstra algorithm to calculate the shortest path -> . Unlike Distance vector routing protocol (which utilizes frequent periodic updates), link-state routing protocol
- 78. utilizes event-triggered updates (only sends update when a change occurs) -> QUESTION 146 Refer to the exhibit. The network is converged.After link-state advertisements are received from Router_A, what information will Router_E contain in its routing table for the subnets 208.149.23.64 and 208.149.23.96? A. 208.149.23.64[110/13] via 190.173.23.10, 00:00:07, FastEthemet0/0 208.149.23.96[110/13] via 190.173.23.10, 00:00:16, FastEthemet0/0 B. 208.149.23.64[110/1] via 190.172.23.10, 00:00:07, Serial1/0 208.149.23.96[110/3] via 190.173.23.10, 00:00:16, FastEthemet0/0 C. 208.149.23.64[110/13] via 190.173.23.10, 00:00:07, Serial1/0 208.149.23.96[110/13] via 190.173.23.10, 00:00:16, Serial1/0 208.149.23.96[110/13] via 190.173.23.10, 00:00:16, FastEthemet0/0 D. 208.149.23.64[110/3] via 190.172.23.10, 00:00:07, Serial1/0 208.149.23.96[110/3] via 190.173.23.10, 00:00:16, Serial1/0 Correct Answer: A Section: (none) Explanation Explanation/Reference: Explanation: Router_E learns two subnets subnets 208.149.23.64 and 208.149.23.96 via Router_A through FastEthernet interface. The interface cost is calculated with the formula 108 / Bandwidth. For FastEthernet it is 108 / 100 Mbps = 108 / 100,000,000 = 1. Therefore the cost is 12 (learned from Router_A) + 1 = 13 for both subnets -> The cost through T1 link is much higher than through T3 link (T1 cost = 108 / 1.544 Mbps = 64; T3 cost = 108 / 45 Mbps = 2) so surely OSPF will choose the path through T3 link -> Router_E will choose the path from Router_A through FastEthernet0/0, not Serial1/0. In fact, we can quickly eliminate answers B, C and D because they contain at least one subnet learned from Serial1/0 -> they are surely incorrect. QUESTION 147 What information can be used by a router running a link-state protocol to build and maintain its topological database? (Choose two.) A. hello packets B. SAP messages sent by other routers C. LSAs from other routers D. beacons received on point-to-point links
- 79. E. routing tables received from other link-state routers F. TTL packets from designated routers Correct Answer: AC Section: (none) Explanation Explanation/Reference: QUESTION 148 Which router command can be used to determine the status of Serial 0/0? A. show ip route B. show interfaces C. show s0/0 status D. debug s0/0 E. show run F. show version Correct Answer: B Section: (none) Explanation Explanation/Reference: QUESTION 149 To what type of port would a cable with a DB-60 connector attach? A. Serial port B. Console port C. Ethernet port D. Fibre optic port Correct Answer: A Section: (none) Explanation Explanation/Reference: QUESTION 150 A network administrator is connecting PC hosts A and B directly through their Ethernet interfaces as shown in the graphic. Ping attempts between the hosts are unsuccessful. What can be done to provide connectivity between the hosts? (Choose two.) A. A crossover cable should be used in place of the straight-through cable. B. A rollover cable should be used in place of the straight-through cable.
- 80. C. The subnet masks should be set to 255.255.255.192 D. A default gateway needs to be set on each host. E. The hosts must be reconfigured to use private IP addresses for direct connections of this type. F. The subnet masks should be set to 255.255.255.0 Correct Answer: AF Section: (none) Explanation Explanation/Reference: QUESTION 151 Refer to the exhibit. What kind of cable should be used to make each connection that is identified by the numbers shown? A. 1 - Ethernet Crossover cable 2 - Ethernet straight-through cable 3 - Fiber Optic cable 4 - Rollover cable B. 1 - Ethernet straight-through cable 2 - Ethernet straight-through cable 3 - Serial cable 4 - Rollover cable C. 1 - Ethernet rollover cable 2 - Ethernet crossover cable 3 - Serial cable 4 - Null-modem cable D. 1 - Ethernet straight-through cable 2 - Ethernet Crossover cable 3 - Serial cable 4 - Rollover cable E. 1 - Ethernet straight-through cable 2 - Ethernet Crossover cable 3 - Serial cable 4 - Ethernet Straight-through cable Correct Answer: B Section: (none) Explanation Explanation/Reference: QUESTION 152 Which of the following are types of flow control? (Choose three.)
- 81. A. buffering B. cut-through C. windowing D. congestion avoidance E. load balancing Correct Answer: ACD Section: (none) Explanation Explanation/Reference: Explanation: http://www.info-it.net/cisco/ccna/exam-tips/flow-control.php During Transfer of data, a high speed computer is generating data traffic a lot faster than the network device can handle in transferring to destination, so single gateway or destination device cannot handle much amount of traffic that is called "Congestion". Buffering The Technie is used to control the data transfer when we have congestion, when a network device receive a data it stores in memory section and then transfer to next destination this process called "Buffering". Windowing Whereas Windowing is used for flow control by the Transport layer. Say the sender device is sending segments and the receiver device can accommodate only a fixed number of segments before it can accept more, the two devices negotiate the window size during the connection setup. This is done so that the sending device doesn't overflow the receiving device's buffer. Also the receiving device can send a single acknowledgement for the segments it has received instead of sending an acknowledgement after every segment received. Also, this window size is dynamic meaning, the devices can negotiate and change the window size in the middle of a session. So if initially the window size is three and the receiving device thinks that it can accept more number of segments in its buffer it can negotiate with the sending device and it increase it to say 5 for example. Windowing is used only by TCP since UDP doesn't use or allow flow control. QUESTION 153 How many simultaneous Telnet sessions does a Cisco router support by default? A. 1 B. 2 C. 3 D. 4 E. 5 F. 6 Correct Answer: E Section: (none) Explanation Explanation/Reference: QUESTION 154 What is the purpose of flow control? A. To ensure data is retransmitted if an acknowledgement is not received. B. To reassemble segments in the correct order at the destination device. C. To provide a means for the receiver to govern the amount of data sent by the sender. D. To regulate the size of each segment. Correct Answer: C Section: (none) Explanation
- 82. Explanation/Reference: Explanation: http://whatis.techtarget.com/definition/flow-control Flow control is the management of data flow between computers or devices or between nodes in a network so that the data can be handled at an efficient pace. Too much data arriving before a device can handle it causes data overflow, meaning the data is either lost or must be retransmitted. For serial data transmission locally or in a network, the Xon/Xoff protocol can be used. For modem connections, either Xon/Xoff or CTS/RTS (Clear to Send/Ready to Send) commands can be used to control data flow. In a network, flow control can also be applied by refusing additional device connections until the flow of traffic has subsided. QUESTION 155 Refer to the exhibit. How many collision domains are shown? A. one B. two C. three D. four E. six F. twelve Correct Answer: B Section: (none) Explanation Explanation/Reference: Explanation: Hubs create single collision and broadcast domains. QUESTION 156 Which IP address is a private address? A. 12.0.0.1 B. 168.172.19.39 C. 172.20.14.36 D. 172.33.194.30 E. 192.169.42.34 Correct Answer: C Section: (none) Explanation Explanation/Reference: Explanation:
- 83. QUESTION 157 Which statement is true? A. An IPv6 address is 64 bits long and is represented as hexadecimal characters. B. An IPv6 address is 32 bits long and is represented as decimal digits. C. An IPv6 address is 128 bits long and is represented as decimal digits. D. An IPv6 address is 128 bits long and is represented as hexadecimal characters. Correct Answer: D Section: (none) Explanation Explanation/Reference: Explanation: http://www.cisco.com/en/US/technologies/tk648/tk872/technologies_white_paper0900aecd 8026003d.pdf One of the key advantages IPv6 brings is the exponentially larger address space. The following will outline the basic address architecture of IPv6. 128-bit-long addresses Represented in hexadecimal format: Uses CIDR principles: prefix/prefix length x:x:x:x:x:x:x:x, where x is a 16-bit hex field The last 64 bits are used for the interface ID QUESTION 158 If an Ethernet port on a router was assigned an IP address of 172.16.112.1/20, what is the maximum number of hosts allowed on this subnet? A. 1024 B. 2046 C. 4094 D. 4096 E. 8190 Correct Answer: C Section: (none) Explanation Explanation/Reference: Explanation: Each octet represents eight bits. The bits, in turn, represent (from left to right): 128, 64, 32 , 16 , 8, 4, 2, 1 Add them up and you get 255. Add one for the all zeros option, and the total is 256. Now take away one of these for the network address (all zeros) and another for the broadcast address (all ones). Each octet represents 254 possible hosts. Or 254 possible networks. Unless you have subnet zero set on your network gear, in which case you could conceivably have 255. The CIDR addressing format (/20) tells us that 20 bits are used for the network portion, so the maximum number of networks are 2^20 minus one if you have subnet zero enabled, or minus 2 if not. You asked about the number of hosts. That will be 32 minus the number of network bits, minus two. So calculate it as (2^(32-20))-2, or (2^12)-2 = 4094
- 84. QUESTION 159 Which statements are TRUE regarding Internet Protocol version 6 (IPv6) addresses? (Choose three.) A. An IPv6 address is divided into eight 16-bit groups. B. A double colon (::) can only be used once in a single IPv6 address. C. IPv6 addresses are 196 bits in length. D. Leading zeros cannot be omitted in an IPv6 address. E. Groups with a value of 0 can be represented with a single 0 in IPv6 address. Correct Answer: ABE Section: (none) Explanation Explanation/Reference: Explanation: IPv6 addresses are divided into eight 16-bit groups, a double colon (::) can only be used once in an IPv6 address, and groups with a value of 0 can be represented with a single 0 in an IPv6 address. The following statements are also true regarding IPv6 address: IPv6 addresses are 128 bits in length. Eight 16-bit groups are divided by a colon (:). Multiple groups of 16-bit 0s can be represented with double colon (::). Double colons (::) represent only 0s. Leading zeros can be omitted in an IPv6 address. The option stating that IPv6 addresses are 196 bits in length is incorrect. IPv6 addresses are 128 bits in length. The option stating that leading zeros cannot be omitted in an IPv6 address is incorrect. Leading zeros can be omitted in an IPv6 address. QUESTION 160 Which of the following IP addresses are valid Class B host addresses if a default Class B mask is in use? (Choose two.) A. 10.6.8.35 B. 133.6.5.4 C. 192.168.5.9 D. 127.0.0.1 E. 190.6.5.4 Correct Answer: BE Section: (none) Explanation Explanation/Reference: Explanation: The IP addresses 133.6.5.4 and 190.6.5.4 are both valid Class B addresses when a default mask is in use. The Class B default mask is 255.255.0.0 and the range of valid addresses is 128.0.0.0- 191.255.255.255. The IP address 10.6.8.35 is a Class A address. The Class A default mask is 255.0.0.0 and the range of valid addresses is 1.0.0.0 - 127.255.255.255, with the exception of the range 127.0.0.1 - 127.255.255.255, which is reserved and cannot be assigned. The IP address 192.168.5.9 is a Class C address. The Class C default mask is 255.255.255.0 and the range of valid addresses is 192.0.0.0 - 223.255.255.255. The IP address 127.0.0.1 is a Class A address, but it comes from a reserved portion that cannot be assigned. The range 127.0.0.1 - 127.255.255.255 is used for diagnostics, and although any address in the range will work as a diagnostic address, 127.0.0.1 is known as the loopback address. If you can ping this address, or any address in the 127.0.0.1 - 127.255.255.255 range, then the NIC is working and TCP/IP is installed. The Class A default mask is 255.0.0.0 and the range of valid addresses is 1.0.0.0 - 127.255.255.255, with the exception of the range 127.0.0.1 - 127.255.255.255, which is reserved and cannot be assigned.
- 85. QUESTION 161 How many addresses will be available for dynamic NAT translation when a router is configured with the following commands? Router(config)#ip nat pool TAME 209.165.201.23 209.165.201.30 netmask 255.255.255.224 Router(config)#ip nat inside source list 9 pool TAME A. 7 B. 8 C. 9 D. 10 E. 24 F. 32 Correct Answer: B Section: (none) Explanation Explanation/Reference: Explanation: 209.165.201.23 to 209.165.201.30 provides for 8 addresses. QUESTION 162 Some routers have been configured with default routes. What are some of the advantages of using default routes? (Choose two) A. They establish routes that will never go down. B. They keep routing tables small. C. They require a great deal of CPU power. D. They allow connectivity to remote networks that are not in the routing table E. They direct traffic from the internet into corporate networks. Correct Answer: BD Section: (none) Explanation Explanation/Reference: Explanation: Cisco administration 101: What you need to know about default routes http://www.techrepublic.com/article/ cisco-administration-101-what-you-need-to-know-about- default-routes/ QUESTION 163
- 86. Refer to the exhibit. PC1 pings PC2. What three things will CORE router do with the data that is received from PC1? (Choose three.) A. The data frames will be forwarded out interface FastEthernet0/1 of CORE router. B. The data frames will be forwarded out interface FastEthernet1/0 of CORE router. C. CORE router will replace the destination IP address of the packets with the IP address of PC2. D. CORE router will replace the MAC address of PC2 in the destination MAC address of the frames. E. CORE router will put the IP address of the forwarding FastEthernet interface in the place of the source IP address in the packets. F. CORE router will put the MAC address of the forwarding FastEthernet interface in the place of the source MAC address. Correct Answer: BDF Section: (none) Explanation Explanation/Reference: QUESTION 164 Which three statements are correct about RIP version 2? (Choose three) A. It uses broadcast for its routing updates. B. It supports authentication. C. It is a classless routing protocol. D. It has a lower default administrative distance then RIP version 1. E. It has the same maximum hop count as RIP version 1. F. It does not send the subnet mask any updates. Correct Answer: BCE Section: (none) Explanation Explanation/Reference: QUESTION 165 Refer to the exhibit. Why are two OSPF designated routers identified on Core-Router?
- 87. A. Core-Router is connected to more than one multi-access network. B. The router at 208.149.23.130 is a secondary DR in case the primary fails. C. Two router IDs have the same OSPF priority and are therefore tied for DR election D. The DR election is still underway and there are two contenders for the role. Correct Answer: A Section: (none) Explanation Explanation/Reference: Explanation: OSPF elects one DR per multi-access network. In the exhibit there are two DR so there must have more than one multi-access network. QUESTION 166 What is the OSPF default frequency, in seconds, at which a Cisco router sends hello packets on a multi- access network? A. 10 B. 40 C. 30 D. 20 Correct Answer: A Section: (none) Explanation Explanation/Reference: Explanation: On broadcast multiacess and point-to-point links, the default is 10 seconds. On NBMA, the default is 30 seconds. QUESTION 167 What does the "Inside Global" address represent in the configuration of NAT? A. the summarized address for all of the internal subnetted addresses B. the MAC address of the router used by inside hosts to connect to the Internet C. a globally unique, private IP address assigned to a host on the inside network D. a registered address that represents an inside host to an outside network Correct Answer: D Section: (none) Explanation Explanation/Reference: Explanation: NAT: Local and Global Definitions http://www.cisco.com/en/US/tech/tk648/tk361/technologies_tech_note09186a0080094837.shtml Cisco defines these terms as: Inside local address--The IP address assigned to a host on the inside network. This is the address configured as a parameter of the computer OS or received via dynamic address allocation protocols such as DHCP. The address is likely not a legitimate IP address assigned by the Network Information Center
- 88. (NIC) or service provider. Inside global address--A legitimate IP address assigned by the NIC or service provider that represents one or more inside local IP addresses to the outside world. Outside local address--The IP address of an outside host as it appears to the inside network. Not necessarily a legitimate address, it is allocated from an address space routable on the inside. Outside global address--The IP address assigned to a host on the outside network by the host owner. The address is allocated from a globally routable address or network space. These definitions still leave a lot to be interpreted. For this example, this document redefines these terms by first defining local address and global address. Keep in mind that the terms inside and outside are NAT definitions. Interfaces on a NAT router are defined as inside or outside with the NAT configuration commands, ip nat inside destination and ip nat outside source . Networks to which these interfaces connect can then be thought of as inside networks or outside networks, respectively. Local address--A local address is any address that appears on the inside portion of the network. Global address--A global address is any address that appears on the outside portion of the network. QUESTION 168 Refer to the exhibit. A company wants to use NAT in the network shown. Which commands will apply the NAT configuration to the proper interfaces? (Choose two.) A. R1(config)# interface serial0/1 R1(config-if)# ip nat inside B. R1(config)# interface serial0/1 R1(config-if)# ip nat outside C. R1(config)# interface fastethernet0/0 R1(config-if)# ip nat inside D. R1(config)# interface fastethernet0/0 R1(config-if)# ip nat outside E. R1(config)# interface serial0/1 R1(config-if)# ip nat outside source pool 200.2.2.18 255.255.255.252 F. R1(config)# interface fastethernet0/0 R1(config-if)# ip nat inside source 10.10.0.0 255.255.255.0 Correct Answer: BC Section: (none) Explanation Explanation/Reference: QUESTION 169 Which of the following statements are TRUE regarding Cisco access lists? (Choose two.) A. In an inbound access list, packets are filtered as they enter an interface. B. In an inbound access list, packets are filtered before they exit an interface. C. Extended access lists are used to filter protocol-specific packets. D. You must specify a deny statement at the end of each access list to filter unwanted traffic. E. When a line is added to an existing access list, it is inserted at the beginning of the access list.
- 89. Correct Answer: AC Section: (none) Explanation Explanation/Reference: Explanation: In an inbound access list, packets are filtered as they enter an interface. Extended access lists are used to filter protocol specific packets. Access lists can be used in a variety of situations when the router needs to be given guidelines for decision-making. These situations include: Filtering traffic as it passes through the router To control access to the VTY lines (Telnet) To identify "interesting" traffic to invoke Demand Dial Routing (DDR) calls To filter and control routing updates from one router to another There are two types of access lists, standard and extended. Standard access lists are applied as close to the destination as possible (outbound), and can only base their filtering criteria on the source IP address. The number used while creating an access list specifies the type of access list created. The range used for standard access lists is 1 to 99 and 1300 to 1999. Extended access lists are applied as close to the source as possible (inbound), and can base their filtering criteria on the source or destination IP address, or on the specific protocol being used. The range used for extended access lists is 100 to 199 and 2000 to 2699. Other features of access lists include: Inbound access lists are processed before the packet is routed. Outbound access lists are processed after the packet has been routed to an exit interface. An "implicit deny" is at the bottom of every access list, which means that if a packet has not matched any preceding access list condition, it will be filtered (dropped). Access lists require at least one permit statement, or all packets will be filtered (dropped). One access list may be configured per direction for each Layer 3 protocol configured on an interface The option stating that in an inbound access list, packets are filtered before they exit an interface is incorrect. Packets are filtered as they exit an interface when using an outbound access list. The option stating that a deny statement must be specified at the end of each access list in order to filter unwanted traffic is incorrect. There is an implicit deny at the bottom of every access list. When a line is added to an existing access list, it is not inserted at the beginning of the access list. It is inserted at the end. This should be taken into consideration. For example, given the following access list, executing the command access-list 110 deny tcp 192.168.5.0 0.0.0.255 any eq www would have NO effect on the packets being filtered because it would be inserted at the end of the list, AFTER the line that allows all traffic. access-list 110 permit ip host 192.168.5.1 any access-list 110 deny icmp 192.168.5.0 0.0.0.255 any echo access-list 110 permit any any QUESTION 170 From which of the following attacks can Message Authentication Code (MAC) shield your network? A. DoS B. DDoS C. spoofing D. SYN floods Correct Answer: C Section: (none) Explanation Explanation/Reference: Explanation: Message Authentication Code (MAC) can shield your network from spoofing attacks. Spoofing, also known as masquerading, is a popular trick in which an attacker intercepts a network packet, replaces the source address of the packets header with the address of the authorized host, and reinserts fake information which is sent to the receiver. This type of attack involves modifying packet contents. MAC can prevent this type of attack and ensure data integrity by ensuring that no data has changed. MAC also protects against frequency analysis, sequence manipulation, and ciphertext-only attacks. MAC is a secure message digest that requires a secret key shared by the sender and receiver, making it impossible for sniffers to change both the data and the MAC as the receiver can detect the changes. A denial-of-service (DoS) attack floods the target system with unwanted requests, causing the loss of service to users. One form of this attack generates a flood of packets requesting a TCP connection with
- 90. the target, tying up all resources and making the target unable to service other requests. MAC does not prevent DoS attacks. Stateful packet filtering is the most common defense against a DoS attack. A Distributed Denial of Service attack (DDoS) occurs when multiple systems are used to flood the network and tax the resources of the target system. Various intrusion detection systems, utilizing stateful packet filtering, can protect against DDoS attacks. In a SYN flood attack, the attacker floods the target with spoofed IP packets and causes it to either freeze or crash. A SYN flood attack is a type of denial of service attack that exploits the buffers of a device that accept incoming connections and therefore cannot be prevented by MAC. Common defenses against a SYN flood attack include filtering, reducing the SYN- RECEIVED timer, and implementing SYN cache or SYN cookies. QUESTION 171 Refer to the exhibit. After the power-on-self test (POST), the system LED of a Cisco 2950 switch turns amber. What is the status of the switch? A. The POST was successful. B. The switch has a problem with the internal power supply and needs an external power supply to be attached. C. POST failed and there is a problem that prevents the operating system from being loaded. D. The switch has experienced an internal problem but data can still be forwarded at a slower rate. E. The switch passed POST, but all the switch ports are busy. Correct Answer: C Section: (none) Explanation Explanation/Reference: Explanation: http://www.cisco.com/en/US/products/hw/switches/ps607/products_tech_note09186a00801 25913.shtml Each time you power up the switch, eight Power-On Self Tests (POSTs) run automatically. POSTs check the most important system components before the switch begins to forward packets. When the switch begins the POST, the port status LEDs display amber for two seconds, and then display green. As each test runs, the port status LEDs go out. 1x is the first to go out. The port status LEDs for ports 2x through 8x go out sequentially as the system completes a test. When the POST completes successfully, the port status LEDs go out. This indicates that the switch is operational. If a test fails, the port status LED associated with the test displays amber. The system LED also displays amber. NotE. From Cisco IOS Software Release 11.2(8.5) SA6 onwards, the port and system LEDs both remain amber after a POST failure. In the earlier Cisco IOS Software Releases, only the LEDs of failed linked ports remained amber.
- 91. QUESTION 172 Refer to the exhibit. A technician pastes the configurations in the exhibit into the two new routers shown. Otherwise, the routers are configured with their default configurations. A ping from Host1 to Host 2 fails, but the technician is able to ping the S0/0 interface of R2 from Host 1. The configurations of the hosts have been verified as correct. What could be the cause of the problem? A. The serial cable on R1 needs to be replaced. B. The interfaces on R2 are not configured properly C. R1 has no route to the 192.168.1.128 network. D. The IP addressing scheme has overlapping subnetworks. E. The ip subnet-zero command must be configured on both routers. Correct Answer: C Section: (none) Explanation Explanation/Reference: Explanation: Without a static route pointing to host 2 network the router is unaware of the path to take to reach that network and reply traffic cannot be sent. QUESTION 173 Refer to the exhibit. Why did the device return this message? A. The command requires additional options or parameters B. There is no show command that starts with ru. C. The command is being executed from the wrong router mode. D. There is more than one show command that starts with the letters ru.
- 92. Correct Answer: D Section: (none) Explanation Explanation/Reference: Explanation: Answer D is correct because when you type the incomplete command having more same more command same up to types characters it shows display the ambiguous command error. QUESTION 174 Refer to the exhibit. Serial 0/0 does not respond to a ping request from a host on the FastEthernet 0/0 LAN. How can this problem be corrected? A. Enable the Serial 0/0 interface. B. Correct the IP address for Serial 0/0. C. Correct the IP address for FastEthernet 0/0 D. Change the encapsulation type on Serial 0/0 E. Enable autoconfiguration on the Serial 0/0 interface Correct Answer: A Section: (none) Explanation Explanation/Reference: Explanation: Serial 0/0 interface is administratively down therefore, you will have to run the "no shutdown" command to enable the interface for data. QUESTION 175 Refer to the exhibit. Why was this message received? A. No VTY password has been set. B. No enable password has been set. C. No console password has been set. D. No enable secret password has been set. E. The login command has not been set on CON 0 F. The login command has not been set on the VTY ports.
- 93. Correct Answer: A Section: (none) Explanation Explanation/Reference: QUESTION 176 Refer to the exhibit. After configuring two interfaces on the HQ router, the network administrator notices an error message. What must be done to fix this error? A. The serial interface must be configured first. B. The serial interface must use the address 192.168.1.2 C. The subnet mask of the serial interface should be changed to 255.255.255.0 D. The subnet mask of the FastEthernet interface should be changed to 255.255.255.240 E. The address of the FastEthernet interface should be changed to 192.168.1.66 Correct Answer: D Section: (none) Explanation Explanation/Reference: QUESTION 177 Two routers named Atlanta and Brevard are connected by their serial interfaces as shown in the exhibit, but there is no data connectivity between them. The Atlanta router is known to have a correct configuration. Given the partial configurations shown in the exhibit, what is the problem on the Brevard router that is causing the lack of connectivity?
- 94. A. A loopback is not set. B. The IP address is incorrect. C. The subnet mask is incorrect. D. The serial line encapsulations are incompatible. E. The maximum transmission unit (MTU) size is too large. F. The bandwidth setting is incompatible with the connected interface. Correct Answer: B Section: (none) Explanation Explanation/Reference: QUESTION 178 What are two benefits of using a single OSPF area network design? (Choose two.) A. It is less CPU intensive for routers in the single area. B. It reduces the types of LSAs that are generated. C. It removes the need for virtual links. D. It increases LSA response times. E. It reduces the number of required OSPF neighbor adjacencies. Correct Answer: BC Section: (none) Explanation Explanation/Reference: QUESTION 179 What command sequence will configure a router to run OSPF and add network 10.1.1.0 /24 to area 0? A. router ospf area 0 network 10.1.1.0 255.255.255.0 area 0 B. router ospf network 10.1.1.0 0.0.0.255 C. router ospf 1 network 10.1.1.0 0.0.0.255 area 0 D. router ospf area 0 network 10.1.1.0 0.0.0.255 area 0 E. router ospf network 10.1.1.0 255.255.255.0 area 0 F. router ospf 1 network 10.1.1.0 0.0.0.255 Correct Answer: C Section: (none) Explanation Explanation/Reference: QUESTION 180 Refer to the exhibit. If the router Cisco returns the given output and has not had its router ID set manually, what value will OSPF use as its router ID?
- 95. A. 192.168.1.1 B. 172.16.1.1 C. 1.1.1.1 D. 2.2.2.2 Correct Answer: D Section: (none) Explanation Explanation/Reference: QUESTION 181 What OSPF command, when configured, will include all interfaces into area 0? A. network 0.0.0.0 255.255.255.255 area 0 B. network 0.0.0.0 0.0.0.0 area 0 C. network 255.255.255.255 0.0.0.0 area 0 D. network all-interfaces area 0 Correct Answer: A Section: (none) Explanation Explanation/Reference: QUESTION 182 Which statement describes the process ID that is used to run OSPF on a router? A. It is globally significant and is used to represent the AS number. B. It is locally significant and is used to identify an instance of the OSPF database. C. It is globally significant and is used to identify OSPF stub areas. D. It is locally significant and must be the same throughout an area. Correct Answer: B Section: (none) Explanation Explanation/Reference: QUESTION 183 After the show ip route command has been entered, the following routes are displayed. Which route will
- 96. not be entered into the routing table of a neighboring router? A. R 192.168.8.0/24 [120/1] via 192.168.2.2, 00:00:10, Serial0 B. R 192.168.11.0/24 [120/7] via 192.168.9.1, 00:00:03, Serial1 C. C 192.168.1.0/24 is directly connected, Ethernet0 D. R 192.168.5.0/24 [120/15] via 192.168.2.2, 00:00:10, Serial0 Correct Answer: D Section: (none) Explanation Explanation/Reference: Explanation: The route 192.168.5.0/24 currently has the metric of 15 so this router will add 1 hop count before sending out to its neighboring router. With RIP, a metric of 16 means that network is down -> it will not be installed in the routing table of the neighboring router. QUESTION 184 Refer to Exhibit. Based on the network shown in the graphic which option contains both the potential networking problem and the protocol or setting that should be used to prevent the problem? A. routing loops, hold down timers B. switching loops, split horizon C. routing loops, split horizon D. switching loops, VTP E. routing loops, STP F. switching loops, STP Correct Answer: F Section: (none) Explanation Explanation/Reference: QUESTION 185 If all OSPF routers in a single area are configured with the same priority value, what value does a router use for the OSPF router ID in the absence of a loopback interface? A. the IP address of the first Fast Ethernet interface B. the IP address of the console management interface C. the highest IP address among its active interfaces D. the lowest IP address among its active interfaces E. the priority value until a loopback interface is configured
- 97. Correct Answer: C Section: (none) Explanation Explanation/Reference: QUESTION 186 The OSPF Hello protocol performs which of the following tasks? (Choose two.) A. It provides dynamic neighbor discovery. B. It detects unreachable neighbors in 90 second intervals. C. It maintains neighbor relationships. D. It negotiates correctness parameters between neighboring interfaces. E. It uses timers to elect the router with the fastest links as the designated router. F. It broadcasts hello packets throughout the internetwork to discover all routers that are running OSPF. Correct Answer: AC Section: (none) Explanation Explanation/Reference: QUESTION 187 Which of the following is a characteristic of full-duplex communication? A. It is a CSMA/CD network. B. It is a CSMA/CA network. C. It is point-to-point only. D. Hub communication is done via full duplex. Correct Answer: C Section: (none) Explanation Explanation/Reference: QUESTION 188 Which commands display information about the Cisco IOS software version currently running on a router? (Choose three.) A. show running-config B. show stacks C. show version D. show flash E. show protocols F. show IOS Correct Answer: ACD Section: (none) Explanation Explanation/Reference: QUESTION 189
- 98. After the shutdown command has been issued on the serial 0/0 interface, what will be displayed when the show interface serial 0/0 command is issued by the administrator? A. Serial0/0 is administratively down, line protocol is down B. Serial0/0 is down, line protocol is down C. Serial0/0 is up, line protocol is down D. Serial0/0 is administratively down, line protocol is administratively down E. Serial0/0 is up, line protocol is up F. Serial0/0 is down, line protocol is up Correct Answer: A Section: (none) Explanation Explanation/Reference: QUESTION 190 Refer to the output of the three router commands shown in the exhibit. A new technician has been told to add a new LAN to the company router. Why has the technician received the error message that is shown following the last command? A. The interface was already configured.
- 99. B. The interface type does not exist on this router platform. C. The IOS software loaded on the router is outdated. D. The router does not support LAN interfaces that use Ethernet. E. The command was entered from the wrong prompt. Correct Answer: B Section: (none) Explanation Explanation/Reference: Explanation: From the output of the "show version" command, we learn that there are only 2 FastEthernet interfaces (2 FastEthernet/IEEE 802.3 interfaces) and this router does not have any Ethernet interface so an error will occur when we enter the "interface e0" command. QUESTION 191 The system LED is amber on a Cisco Catalyst 2950 series switch. What does this indicate? A. The system is malfunctioning. B. The system is not powered up. C. The system is powered up and operational. D. The system is forwarding traffic. E. The system is sensing excessive collisions. Correct Answer: A Section: (none) Explanation Explanation/Reference: Explanation: The system LED shows whether the system is receiving power and functioning properly. Below lists the LED colors and meanings: Color System Status Off System is not powered up. Green System is operating normally. Amber System is receiving power but is not functioning properly. http://www.cisco.com/en/US/docs/switches/lan/catalyst2950/hardware/installation/guide/hgovrev.html QUESTION 192 Refer to the topology and partial configurations shown in the exhibit. The network administrator has finished configuring the NewYork and Sydney routers and issues the command ping Sydney from the NewYork router. The ping fails. What command or set of commands should the network administrator issue to correct this problem?
- 100. A. Sydney(config)# interface s0/0 Sydney(config-if)# cdp enable B. Sydney(config)# interface s0/0 Sydney(config-if)# no shut C. Sydney(config)# line vty 0 4 Sydney(config)# login Sydney(config)# password Sydney D. Sydney(config)# ip host Sydney 10.1.1.9 E. Sydney(config)# interface s0/0 Sydney(config-if)# ip address 10.1.1.5 255.255.255.252 NewYork(config)# ip host Sydney 10.1.1.5 Correct Answer: E Section: (none) Explanation Explanation/Reference: Explanation: The IP addresses on the two Serial interfaces of two routers are not in the same subnet so they could not recognize each other and the ping failed. Therefore we must correct the IP address of one of the router so that they are in the same subnet. QUESTION 193 Refer to the topology and MAC address table shown in the exhibit. Host A sends a data frame to host D. What will the switch do when it receives the frame from host A?
- 101. A. The switch will add the source address and port to the MAC address table and forward the frame to host D. B. The switch will discard the frame and send an error message back to host A. C. The switch will flood the frame out of all ports except for port Fa0/3. D. The switch will add the destination address of the frame to the MAC address table and forward the frame to host D. Correct Answer: A Section: (none) Explanation Explanation/Reference: QUESTION 194 Refer to the exhibit. Host B has just been added to the network and must acquire an IP address. Which two addresses are possible addresses that will allow host B to communicate with other devices in the network? (Choose two.) A. 192.168.10.32 B. 192.168.10.38 C. 192.168.10.46 D. 192.168.10.47 E. 192.168.10.49 F. 192.168.10.51 Correct Answer: BC Section: (none) Explanation Explanation/Reference: Explanation: The IP address of host B must be in the range of 192.168.10.32/28 subnet, which ranges from 192.168.10.32 to 192.168.10.47 (Increment: 16), except the IP addresses of 192.168.10.32, 192.168.10.46 (which are the network and broadcast addresses of the subnet), 192.168.10.33, 192.168.10.34 (which have been assigned to the interface's router and the switch). Therefore there are only two IP addresses of
- 102. 192.168.10.38 & 192.168.10.46. QUESTION 195 Refer to the exhibit. HostB is sending a file to HostA. B represents the frame as it leaves the Oshawa router. What is the Layer 2 destination address of the frame at this point? A. abcd.1123.0045 B. abcd.1234.5678 C. abcd.2246.0035 D. abcd.4444.0012 E. aabb.5555.2222 Correct Answer: D Section: (none) Explanation Explanation/Reference: QUESTION 196 Refer to the exhibit. A network technician is unable to ping from R1 to R2. Using the output of the show interfaces serial0/1 command, what should the administrator do to correct the problem?
- 103. A. Replace the serial cable between R1 and R2. B. Reseat the serial connectors on the R1 and R2 routers. C. Configure the serial0/1 interface on R2 with the no shutdown command. D. Configure the serial0/1 interface on R1 with the clock rate 56000 command. E. Configure the serial0/1 interface on R1 with the ip address 192.1.1.7 255.255.255.252 command. Correct Answer: C Section: (none) Explanation Explanation/Reference: QUESTION 197 Examine the network diagram and router output shown in the exhibit. Users on the BHM LAN are unable to access the server attached to the BHE router. What two things should be done to fix this problem? (Choose two.) A. Enter the configuration mode for interface fastethernet0/0. B. Enter the configuration mode for interface serial0/0. C. Enter the configuration mode for interface serial0/1. D. Issue the run command. E. Issue the enable command. F. Issue the no shutdown command. Correct Answer: BF Section: (none) Explanation Explanation/Reference: QUESTION 198 From where does a small network get its IP network address? A. Internet Assigned Numbers Authority (IANA)
- 104. B. Internet Architecture Board (IAB) C. Internet Service Provider (ISP) D. Internet Domain Name Registry (IDNR) Correct Answer: C Section: (none) Explanation Explanation/Reference: QUESTION 199 A network administrator has subnetted the 172.16.0.0 network using a subnet mask of 255.255.255.192. A duplicate IP address of 172.16.2.120 has accidentally been configured on a workstation in the network. The technician must assign this workstation a new IP address within that same subnetwork. Which address should be assigned to the workstation? A. 172.16.1.80 B. 172.16.2.80 C. 172.16.1.64 D. 172.16.2.64 E. 172.16.2.127 F. 172.16.2.128 Correct Answer: B Section: (none) Explanation Explanation/Reference: QUESTION 200 Refer to the exhibit. A network technician is unable to ping from R1 to R2. What will help correct the problem? A. Ensure that the serial cable is correctly plugged in to the interfaces. B. Apply the clock rate 56000 configuration command to the serial0/1 interface of R1. C. Configure the serial0/1 interfaces on R1 and R2 with the no shutdown command. D. Change the address of the serial0/1 interface of R1 to 192.1.1.4. E. Change the subnet masks of both interfaces to 255.255.255.240.
- 105. Correct Answer: A Section: (none) Explanation Explanation/Reference: QUESTION 201 SW-C has just been added to the network shown in the graphic. What is the purpose of assigning a default gateway to this switch? A. allows connectivity to Router B from the switch prompt B. allows console port connectivity to the switch from Host A C. allows connectivity to remote network devices from Host B D. allows the switch to pass traffic between Host A and Host B Correct Answer: A Section: (none) Explanation Explanation/Reference: QUESTION 202 What is the maximum number of bits that can be borrowed to create subnets if a Class B network address is being used? A. 2 B. 6 C. 8 D. 14 E. 16 Correct Answer: D Section: (none) Explanation Explanation/Reference: QUESTION 203 Which three network addresses are reserved for private network use? (Choose three.) A. 10.0.0.0 B. 172.15.0.0 C. 172.31.0.0
- 106. D. 192.162.24.0 E. 192.168.255.0 F. 224.192.0.0 Correct Answer: ACE Section: (none) Explanation Explanation/Reference: QUESTION 204 Which form of NAT maps multiple private IP addresses to a single registered IP address by using different ports? A. static NAT B. dynamic NAT C. overloading D. overlapping E. port loading Correct Answer: C Section: (none) Explanation Explanation/Reference: QUESTION 205 Refer to the exhibit. A network technician has added host A to the network. Host A cannot communicate on the network. A ping that is issued on the host to address 127.0.0.1 fails. What is the problem? A. The router is not forwarding the ping packets to network 127.0.0.0. B. The remote host at 127.0.0.1 is unreachable. C. The default gateway is incorrect. D. The IP address of host A is incorrect. E. The TCP/IP protocols are not loaded. Correct Answer: E Section: (none) Explanation
- 107. Explanation/Reference: QUESTION 206 Refer to the exhibit. Pierre has just installed the mail server and Switch2. For security reasons UDP packets are not permitted outbound on the Fa0/1 router interface. Pierre is now at his workstation testing the new installation and is not able to establish SMTP communication to the mail server. What is the most likely cause for lack of communication between Pierre's workstation and the mail server? A. The crossover cable should be a straight-through cable. B. UDP is blocked coming out of the Fa0/1 interface on the router. C. The server should be directly connected to the router. D. The IP addresses are all on the same network. No router is required. Correct Answer: A Section: (none) Explanation Explanation/Reference: QUESTION 207 Refer to the exhibits labeled A through E. All devices are to be connected over Ethernet. Which three device-to-device configurations are likely to require the use of a crossover connection? (Choose three.)
- 108. A. exhibit A B. exhibit B C. exhibit C D. exhibit D E. exhibit E Correct Answer: ADE Section: (none) Explanation Explanation/Reference: QUESTION 208 Refer to the exhibit. Which two statements are true of the interface configuration? (Choose two.)
- 109. A. The encapsulation in use on this interface is PPP. B. The default serial line encapsulation is in use on this interface. C. The address mask of this interface is 255.255.255.0. D. This interface is connected to a LAN. E. The interface is not ready to forward packets. Correct Answer: AC Section: (none) Explanation Explanation/Reference: QUESTION 209 Refer to the exhibit. What value should be displayed in Box 1 of the ipconfig output of host A?
- 110. A. 172.18.14.5 B. 172.18.14.6 C. 192.168.1.10 D. 192.168.1.11 E. 192.168.1.250 F. 192.168.1.254 Correct Answer: F Section: (none) Explanation Explanation/Reference: QUESTION 210 The internetwork shown in the diagram is experiencing network connectivity problems. What is the cause of the problem? A. The cabling connecting host A to Switch3 is too long. B. The address of host B is a broadcast address. C. The IP address of interface Fa0/0 of Router1 is not a usable address. D. The cable connecting Switch2 and Switch3 should be a crossover. E. The IP address of Server 1 is in the wrong subnet. Correct Answer: D Section: (none) Explanation Explanation/Reference: QUESTION 211 Refer to the exhibit. Which two of the output fields could help you determine if a broadcast storm has occurred? (Choose two.)
- 111. A. giants B. no buffer C. collisions D. ignored E. dribble condition Correct Answer: BD Section: (none) Explanation Explanation/Reference: QUESTION 212 Refer to the exhibit. What does the address 192.168.2.167 represent? A. the TFTP server from which the file startup-config is being transferred B. the router from which the file startup-config is being transferred C. the TFTP server from which the file router-confg is being transferred D. the TFTP server to which the file router-confg is being transferred E. the router to which the file router-confg is being transferred F. the router to which the file startup-config is being transferred Correct Answer: D Section: (none)
- 112. Explanation Explanation/Reference: QUESTION 213 Refer to the exhibit. Two 2950 switches connect through ports fa0/24 using a straight-through cable. Based on the output that is shown in the exhibit and the information that is given, what can be concluded about this network? A. STP can not be configured on a FastEthernet ports. B. An IP address and default gateway must be configured on each switch. C. The switches do not share the same VTP domain. D. Port fa0/24 must be configured as a trunk in order for the switches to share neighbor information. E. The switches are cabled incorrectly. Correct Answer: E Section: (none) Explanation Explanation/Reference: QUESTION 214 In which situation would the use of a static route be appropriate? A. To configure a route to the first Layer 3 device on the network segment. B. To configure a route from an ISP router into a corporate network. C. To configure a route when the administrative distance of the current routing protocol is too low. D. To reach a network is more than 15 hops away. E. To provide access to the Internet for enterprise hosts. Correct Answer: B Section: (none) Explanation Explanation/Reference: QUESTION 215 Which NTP command configures the local device as an NTP reference clock source? A. ntp peer
- 113. B. ntp broadcast C. ntp master D. ntp server Correct Answer: C Section: (none) Explanation Explanation/Reference: QUESTION 216 Which routing protocol has the smallest default administrative distance? A. IBGP B. OSPF C. IS-IS D. EIGRP E. RIP Correct Answer: D Section: (none) Explanation Explanation/Reference: Explanation: http://www.cisco.com/c/en/us/support/docs/ip/border-gateway-protocol-bgp/15986-admin-distance.html QUESTION 217 Which statement about static routes is true? A. The source interface can be configured to make routing decisions. B. A subnet mask is entered for the next-hop address.
- 114. C. The subnet mask is 255.255 255.0 by default D. The exit interface can be specified to indicate where the packets will be routed. Correct Answer: D Section: (none) Explanation Explanation/Reference: Explanation: Static routing can be used to define an exit point from a router when no other routes are available or necessary. This is called a default route. QUESTION 218 Under which circumstance should a network administrator implement one-way NAT? A. when the network must route UDP traffic B. when traffic that originates outside the network must be routed to internal hosts C. when traffic that originates inside the network must be routed to internal hosts D. when the network has few public IP addresses and many private IP addresses require outside access Correct Answer: B Section: (none) Explanation Explanation/Reference: Explanation: NAT operation is typically transparent to both the internal and external hosts. Typically the internal host is aware of the true IP address and TCP or UDP port of the external host. Typically the NAT device may function as the default gateway for the internal host. However the external host is only aware of the public IP address for the NAT device and the particular port being used to communicate on behalf of a specific internal host. NAT and TCP/UDP "Pure NAT", operating on IP alone, may or may not correctly parse protocols that are totally concerned with IP information, such as ICMP, depending on whether the payload is interpreted by a host on the "inside" or "outside" of translation. As soon as the protocol stack is traversed, even with such basic protocols as TCP and UDP, the protocols will break unless NAT takes action beyond the network layer. IP packets have a checksum in each packet header, which provides error detection only for the header. IP datagrams may become fragmented and it is necessary for a NAT to reassemble these fragments to allow correct recalculation of higher-level checksums and correct tracking of which packets belong to which connection. The major transport layer protocols, TCP and UDP, have a checksum that covers all the data they carry, as well as the TCP/UDP header, plus a "pseudo-header" that contains the source and destination IP addresses of the packet carrying the TCP/UDP header. For an originating NAT to pass TCP or UDP successfully, it must recompute the TCP/UDP header checksum based on the translated IP addresses, not the original ones, and put that checksum into the TCP/UDP header of the first packet of the fragmented set of packets. The receiving NAT must recompute the IP checksum on every packet it passes to the destination host, and also recognize and recompute the TCP/UDP header using the retranslated addresses and pseudo-header. This is not a completely solved problem. One solution is for the receiving NAT to reassemble the entire segment and then recompute a checksum calculated across all packets. The originating host may perform Maximum transmission unit (MTU) path discovery to determine the packet size that can be transmitted without fragmentation, and then set the don't fragment (DF) bit in the appropriate packet header field. Of course, this is only a one- way solution, because the responding host can send packets of any size, which may be fragmented before reaching the NAT. QUESTION 219 Which component of a routing table entry represents the subnet mask? A. routing protocol code B. prefix C. metric D. network mask
- 115. Correct Answer: D Section: (none) Explanation Explanation/Reference: Explanation: IP Routing Table Entry TypesAn entry in the IP routing table contains the following information in the order presented: Network ID. The network ID or destination corresponding to the route. The network ID can be class-based, subnet, or supernet network ID, or an IP address for a host route. Network Mask. The mask that is used to match a destination IP address to the network ID. Next Hop. The IP address of the next hop. Interface. An indication of which network interface is used to forward the IP packet. Metric. A number used to indicate the cost of the route so the best route among possible multiple routes to the same destination can be selected. A common use of the metric is to indicate the number of hops (routers crossed) to the network ID. Routing table entries can be used to store the following types of routes: Directly Attached Network IDs. Routes for network IDs that are directly attached. For directly attached networks, the Next Hop field can be blank or contain the IP address of the interface on that network. Remote Network IDs. Routes for network IDs that are not directly attached but are available across other routers. For remote networks, the Next Hop field is the IP address of a local router in between the forwarding node and the remote network. Host Routes. A route to a specific IP address. Host routes allow routing to occur on a per- IP address basis. For host routes, the network ID is the IP address of the specified host and the network mask is 255.255.255.255. Default Route. The default route is designed to be used when a more specific network ID or host route is not found. The default route network ID is 0.0.0.0 with the network mask of 0.0.0.0. QUESTION 220 When a router makes a routing decision for a packet that is received from one network and destined to another, which portion of the packet does if replace? A. Layer 2 frame header and trailer B. Layer 3 IP address C. Layer 5 session D. Layer 4 protocol Correct Answer: A Section: (none) Explanation Explanation/Reference: Explanation: Router Switching Function (1.2.1.1)A primary function of a router is to forward packets toward their destination. This is accomplished by using a switching function, which is the process used by a router to accept a packet on one interface and forward it out of another interface. A key responsibility of the switching function is to encapsulate packets in the appropriate data link frame type for the outgoing data link. NOTE: In this context, the term "switching" literally means moving packets from source to destination and should not be confused with the function of a Layer 2 switch. After the router has determined the exit interface using the path determination function, the router must encapsulate the packet into the data link frame of the outgoing interface. What does a router do with a packet received from one network and destined for another network? The router performs the following three major steps: Step 1. De-encapsulates the Layer 3 packet by removing the Layer 2 frame header and trailer. Step 2. Examines the destination IP address of the IP packet to find the best path in the routing table. Step 3. If the router finds a path to the destination, it encapsulates the Layer 3 packet into a new Layer 2 frame and forwards the frame out the exit interface. QUESTION 221 On which type of device is every port in the same collision domain?
- 116. A. a router B. a Layer 2 switch C. a hub D. switch E. a Layer 3 switch Correct Answer: C Section: (none) Explanation Explanation/Reference: Explanation: Collision domainA collision domain is, as the name implies, a part of a network where packet collisions can occur. A collision occurs when two devices send a packet at the same time on the shared network segment. The packets collide and both devices must send the packets again, which reduces network efficiency. Collisions are often in a hub environment, because each port on a hub is in the same collision domain. By contrast, each port on a bridge, a switch or a router is in a separate collision domain. QUESTION 222 Which statement about routing protocols is true? A. Link-state routing protocols choose a path by the number of hops to the destination. B. OSPF is a link-state routing protocol. C. Distance-vector routing protocols use the Shortest Path First algorithm. D. IS-IS is a distance-vector routing protocol. Correct Answer: B Section: (none) Explanation Explanation/Reference: Explanation: Link State Routing Protocols Link state protocols are also called shortest-path-first protocols. Link state routing protocols have a complete picture of the network topology. Hence they know more about the whole network than any distance vector protocol. Three separate tables are created on each link state routing enabled router. One table is used to hold details about directly connected neighbors, one is used to hold the topology of the entire internetwork and the last one is used to hold the actual routing table. Link state protocols send information about directly connected links to all the routers in the network. Examples of Link state routing protocols include OSPF - Open Shortest Path First and IS-IS - Intermediate System to Intermediate System. There are also routing protocols that are considered to be hybrid in the sense that they use aspects of both distance vector and link state protocols. EIGRP - Enhanced Interior Gateway Routing Protocol is one of those hybrid routing protocols. QUESTION 223 Which technology supports the stateless assignment of IPv6 addresses? A. DNS B. DHCPv6 C. DHCP D. autoconfiguration Correct Answer: D Section: (none) Explanation Explanation/Reference: Explanation:
- 117. Stateless Auto Configuration is an important feature offered by the IPv6 protocol. It allows the various devices attached to an IPv6 network to connect to the Internet using the Stateless Auto Configuration without requiring any intermediate IP support in the form of a Dynamic Host Configuration Protocol (DHCP) server. http://ipv6.com/articles/general/Stateless-Auto-Configuration.htm QUESTION 224 Which feature allows a device to use a switch port that is configured for half-duplex to access the network? A. CSMA/CD B. IGMP C. port security D. split horizon Correct Answer: A Section: (none) Explanation Explanation/Reference: Explanation: Ethernet began as a local area network technology that provided a half-duplex shared channel for stations connected to coaxial cable segments linked with signal repeaters. In this appendix, we take a detailed look at the half-duplex shared-channel mode of operation, and at the CSMA/CD mechanism that makes it work. In the original half-duplex mode, the CSMA/CD protocol allows a set of stations to compete for access to a shared Ethernet channel in a fair and equitable manner. The protocol's rules determine the behavior of Ethernet stations, including when they are allowed to transmit a frame onto a shared Ethernet channel, and what to do when a collision occurs. Today, virtually all devices are connected to Ethernet switch ports over full-duplex media, such as twisted-pair cables. On this type of connection, assuming that both devices can support the full-duplex mode of operation and that Auto-Negotiation (AN) is enabled, the AN protocol will automatically select the highest-performance mode of operation supported by the devices at each end of the link. That will result in full-duplex mode for the vast majority of Ethernet connections with modern interfaces that support full duplex and AN. QUESTION 225 Which function enables an administrator to route multiple VLANs on a router? A. IEEE 802 1X B. HSRP C. port channel D. router on a stick Correct Answer: D Section: (none) Explanation Explanation/Reference: QUESTION 226 Which dynamic routing protocol uses only the hop count to determine the best path to a destination? A. IGRP B. RIP C. EIGRP D. OSPF Correct Answer: B Section: (none)
- 118. Explanation Explanation/Reference: Explanation: Determining the best path involves the evaluation of multiple paths to the same destination network and selecting the optimum or shortest path to reach that network. Whenever multiple paths to the same network exist, each path uses a different exit interface on the router to reach that network. The best path is selected by a routing protocol based on the value or metric it uses to determine the distance to reach a network. A metric is the quantitative value used to measure the distance to a given network. The best path to a network is the path with the lowest metric. Dynamic routing protocols typically use their own rules and metrics to build and update routing tables. The routing algorithm generates a value, or a metric, for each path through the network. Metrics can be based on either a single characteristic or several characteristics of a path. Some routing protocols can base route selection on multiple metrics, combining them into a single metric. The following lists some dynamic protocols and the metrics they use: Routing Information Protocol (RIP): Hop count Open Shortest Path First (OSPF): Cisco routers use a cost based on cumulative bandwidth from source to destination Enhanced Interior Gateway Routing Protocol (EIGRP): Bandwidth, delay, load, reliability QUESTION 227 What is one requirement for interfaces to run IPv6? A. An IPv6 address must be configured on the interface. B. An IPv4 address must be configured. C. Stateless autoconfiguration must be enabled after enabling IPv6 on the interface. D. IPv6 must be enabled with the ipv6 enable command in global configuration mode. Correct Answer: A Section: (none) Explanation Explanation/Reference: Explanation: To use IPv6 on your router, you must, at a minimum, enable the protocol and assign IPv6 addresses to your interfaces. QUESTION 228 Which destination IP address can a host use to send one message to multiple devices across different subnets? A. 172.20.1.0 B. 127.0.0.1 C. 192.168.0.119 D. 239.255.0.1 Correct Answer: D Section: (none) Explanation Explanation/Reference: Explanation: Multicast is a networking protocol where one host can send a message to a special multicast IP address and one or more network devices can listen for and receive those messages. Multicast works by taking advantage of the existing IPv4 networking infrastructure, and it does so in something of a weird fashion. As you read, keep in mind that things are a little confusing because multicast was "shoe-horned" in to an existing technology. For the rest of this article, let's use the multicast IP address of 239.255.0.1. We'll not worry about port numbers yet, but make a mental note that they are used in multicast. We'll discuss that later.
- 119. QUESTION 229 Which MTU size can cause a baby giant error? A. 1500 B. 9216 C. 1600 D. 1518 Correct Answer: C Section: (none) Explanation Explanation/Reference: Explanation: Standard Ethernet frame MTU is 1500 bytes. This does not include the Ethernet header and Cyclic Redundancy Check (CRC) trailer, which is 18 bytes in length, to make the total Ethernet frame size of 1518. In this document, MTU size or packet size refers only to Ethernet payload. http://www.cisco.com/c/en/us/support/docs/switches/catalyst-4000-series-switches/29805-175.html QUESTION 230 Which entity assigns IPv6 addresses to end users? A. ICANN B. APNIC C. RIR D. ISPs Correct Answer: D Section: (none) Explanation Explanation/Reference: Explanation: Before going forward that far it is important to note that like IPv4, the placement of the devices that will be allocated with IPv6 addresses can affect the numbers and the method of assignment. If the IPv6 addresses in question will be used solely for the internal purposes of a business and do not need to be directly routable to the public Internet, then the Unique Local IPv6 range (RFC 4193) and assignment method can be used; these would be the equivalent of RFC 1918 IPv4 private address ranges. If, however, the IPv6 addresses are intended to be directly routable on the public Internet, a range must be assigned (just like with IPv4) by an Internet Service Provider (ISP), or a Regional Internet Registry (RIR) if allocating for an ISP. As of this writing, the Unique Local address range includes all addresses that fall under the FC00::/7 prefix (they begin with ‘1111110’ in binary), while the Global Unicast address range includes all addresses that fall under the 2000::/3 prefix (they begin with ‘001’ in binary). Global Unicast ranges are divided by a number of different entities; at the top of these entities is Internet Corporation for Assigned Names and Numbers (ICANN) who assigns addresses to the RIR’s (for all regional registries except APNIC), who will in turn assign addresses to ISP’s who will in turn assign addresses to End Users (EU). QUESTION 231 Which option is the default switch port port-security violation mode? A. shutdown B. protect C. shutdown vlan D. restrict Correct Answer: A Section: (none) Explanation
- 120. Explanation/Reference: Explanation: Shutdown--This mode is the default violation mode; when in this mode, the switch will automatically force the switchport into an error disabled (err-disable) state when a violation occurs. While in this state, the switchport forwards no traffic. The switchport can be brought out of this error disabled state by issuing the errdisable recovery cause CLI command or by disabling and reenabling the switchport. Shutdown VLAN--This mode mimics the behavior of the shutdown mode but limits the error disabled state the specific violating VLAN. QUESTION 232 Which statement about the inside interface configuration in a NAT deployment is true? A. It is defined globally B. It identifies the location of source addresses for outgoing packets to be translated using access or route maps. C. It must be configured if static NAT is used D. It identifies the public IP address that traffic will use to reach the internet. Correct Answer: B Section: (none) Explanation Explanation/Reference: Explanation: This module describes how to configure Network Address Translation (NAT) for IP address conservation and how to configure inside and outside source addresses. This module also provides information about the benefits of configuring NAT for IP address conservation. NAT enables private IP internetworks that use nonregistered IP addresses to connect to the Internet. NAT operates on a device, usually connecting two networks, and translates the private (not globally unique) addresses in the internal network into legal addresses before packets are forwarded onto another network. NAT can be configured to advertise to the outside world only one address for the entire network. This ability provides additional security by effectively hiding the entire internal network behind that one address. NAT is also used at the enterprise edge to allow internal users access to the Internet and to allow Internet access to internal devices such as mail servers. QUESTION 233 Which value is indicated by the next hop in a routing table? A. preference of the route source B. IP address of the remote router for forwarding the packets C. how the route was learned D. exit interface IP address for forwarding the packets Correct Answer: B Section: (none) Explanation Explanation/Reference: Explanation: From official Odom cisco book is Routes for remote subnets typically list both an outgoing interface and next-hop router IP address. Routes for subnets that connect directly to the router list only the outgoing interface, because packets to these destinations do not need to be sent to another router. QUESTION 234 Which option is a valid hostname for a switch? A. 5witch-Cisco B. Switch-Cisco! C. 5witchCisco
- 121. D. SwitchCisc0 Correct Answer: D Section: (none) Explanation Explanation/Reference: Explanation: Hostnames can’t start with a number, and can’t have special characters (bangs/exclamation) (but can have a dash). A starts with a number. B has a bang at the end. C starts with a number. Only D is correct. QUESTION 235 Which component of the routing table ranks routing protocols according to their preferences? A. administrative distance B. next hop C. metric D. routing protocol code Correct Answer: A Section: (none) Explanation Explanation/Reference: Explanation: Administrative distance - This is the measure of trustworthiness of the source of the route. If a router learns about a destination from more than one routing protocol, administrative distance is compared and the preference is given to the routes with lower administrative distance. In other words, it is the believability of the source of the route. QUESTION 236 Which statement about unicast frame forwarding on a switch is true? A. The TCAM table stores destination MAC addresses B. If the destination MAC address is unknown, the frame is flooded to every port that is configured in the same VLAN except on the port that it was received on. C. The CAM table is used to determine whether traffic is permitted or denied on a switch D. The source address is used to determine the switch port to which a frame is forwarded Correct Answer: B Section: (none) Explanation Explanation/Reference: QUESTION 237 Which statement about native VLAN traffic is true? A. Cisco Discovery Protocol traffic travels on the native VLAN by default B. Traffic on the native VLAN is tagged with 1 by default C. Control plane traffic is blocked on the native VLAN. D. The native VLAN is typically disabled for security reasons Correct Answer: A
- 122. Section: (none) Explanation Explanation/Reference: Explanation: The native VLAN is the VLAN that is configured for packets that don’t have a tag. The default native VLAN on all Cisco Switches is VLAN 1. It is always enabled by default. These settings can all be changed: That is: you can designate a different VLAN as the native VLAN, disable VLAN 1, etc. Knowing that, we can eliminate D) as the correct answer because it is enabled by default. We can also eliminate B) because Native VLAN packets don’t get tags by default (you can change this). Finally, Control Plane traffic is never blocked on Native VLAN 1, and even if you change the Native VLAN, the control plane traffic still comes across VLAN 1. QUESTION 238 Which route source code represents the routing protocol with a default administrative distance of 90 in the routing table? A. S B. E C. D D. R E. O Correct Answer: C Section: (none) Explanation Explanation/Reference: Explanation: SStatic EEGP DEIGRP RRIP OOSPF Default Administrative distance of EIGRP protocol is 90 then answer is C. Default Distance Value TableThis table lists the administrative distance default values of the protocols that Cisco supports: Route Source Default Distance Values Connected interface Static route Enhanced Interior Gateway Routing Protocol (EIGRP) summary route External Border Gateway Protocol (BGP) Internal EIGRP IGRP OSPF Intermediate System-to-Intermediate System (IS-IS) Routing Information Protocol (RIP) Exterior Gateway Protocol (EGP) On Demand Routing (ODR) External EIGRP Internal BGP Unknown*
- 123. QUESTION 239 Refer to the exhibit. Which statement describes the effect of this configuration? A. The VLAN 10 VTP configuration is displayed. B. VLAN 10 spanning-tree output is displayed. C. The VLAN 10 configuration is saved when the router exits VLAN configuration mode. D. VLAN 10 is added to the VLAN database. Correct Answer: D Section: (none) Explanation Explanation/Reference: Explanation: With the configuration above, when we type "do show vlan" we would not see VLAN 10 in the VLAN database because it has not been created yet. VLAN 10 is only created when we exits VLAN configuration mode (with "exit" command). QUESTION 240 When enabled, which feature prevents routing protocols from sending hello messages on an interface'? A. virtual links B. passive-interface C. directed neighbors D. OSPF areas Correct Answer: B Section: (none) Explanation Explanation/Reference: Explanation: You can use the passive-interface command in order to control the advertisement of routing information. The command enables the suppression of routing updates over some interfaces while it allows updates to be exchanged normally over other interfaces. With most routing protocols, the passive-interface command restricts outgoing advertisements only. But, when used with Enhanced Interior Gateway Routing Protocol (EIGRP), the effect is slightly different. This document demonstrates that use of the passive-interface command in EIGRP suppresses the exchange of hello packets between two routers, which results in the loss of their neighbor relationship. This stops not only routing updates from being advertised, but it also suppresses incoming routing updates. This document also discusses the configuration required in order to allow the suppression of outgoing routing updates, while it also allows incoming routing updates to be learned normally from the neighbor. QUESTION 241 Which device allows users to connect to the network using a single or double radio? A. access point B. switch
- 124. C. wireless controller D. firewall Correct Answer: A Section: (none) Explanation Explanation/Reference: QUESTION 242 Two hosts are attached to a switch with the default configuration. Which statement about the configuration is true? A. IP routing must be enabled to allow the two hosts to communicate. B. The two hosts are in the same broadcast domain. C. The switch must be configured with a VLAN to allow the two hosts to communicate. D. Port security prevents the hosts from connecting to the switch. Correct Answer: B Section: (none) Explanation Explanation/Reference: Explanation: http://www.cisco.com/c/en/us/support/docs/lan-switching/inter-vlan- routing/41860-howto-L3- intervlanrouting.html QUESTION 243 By default, how many MAC addresses are permitted to be learned on a switch port with port security enabled? A. 8 B. 2 C. 1 D. 0 Correct Answer: C Section: (none) Explanation Explanation/Reference: QUESTION 244 Which statement about a router on a stick is true? A. Its date plane router traffic for a single VI AN over two or more switches. B. It uses multiple subinterfaces of a single interface to encapsulate traffic for different VLANs on the same subnet. C. It requires the native VLAN to be disabled. D. It uses multiple subinterfaces of a single interface to encapsulate traffic for different VLANs. Correct Answer: D Section: (none) Explanation Explanation/Reference: Explanation:
- 125. https://www.freeccnaworkbook.com/workbooks/ccna/configuring-inter-vlan-routing-router-on-a-stick QUESTION 245 Which network topology allows all traffic to flow through a central hub? A. bus B. star C. mesh D. ring Correct Answer: B Section: (none) Explanation Explanation/Reference: Explanation: Star topology is the most popular topology for the network which allows all traffic to flow through a central device. QUESTION 246 Which NAT type is used to translate a single inside address to a single outside address? A. dynamic NAT B. NAT overload C. PAT D. static NAT Correct Answer: D Section: (none) Explanation Explanation/Reference:
- 126. Explanation: Network address translation (NAT) is the process of modifying IP address information in IP packet headers while in transit across a traffic routing device. There are two different types of NAT: NAT PAT QUESTION 247 What is the default lease time for a DHCP binding? A. 24 hours B. 12 hours C. 48 hours D. 36 hours Correct Answer: A Section: (none) Explanation Explanation/Reference: Explanation: By default, each IP address assigned by a DHCP Server comes with a one-day lease, which is the amount of time that the address is valid. To change the lease value for an IP address, use the following command in DHCP pool configuration mode: QUESTION 248 Which RFC was created to alleviate the depletion of IPv4 public addresses? A. RFC 4193 B. RFC 1519 C. RFC 1518 D. RFC 1918 Correct Answer: B Section: (none) Explanation Explanation/Reference: Explanation: RFC 4193: Unique Local IPv6 Unicast Addresses. RFC 1519: Classless Inter-Domain Routing (CIDR): an Address Assignment and Aggregation Strategy . RFC 1518: An Architecture for IP Address Allocation with CIDR. RFC 1918: Address Allocation for Private Internets. QUESTION 249 Which method does a connected trunk port use to tag VLAN traffic? A. IEEE 802 1w B. IEEE 802 1D C. IEEE 802 1Q D. IEEE 802 1p Correct Answer: C Section: (none) Explanation Explanation/Reference: Explanation: IEEE 802.1Q is the networking standard that supports virtual LANs (VLANs) on an Ethernet network.
- 127. When a frame enters the VLAN-aware portion of the network (a trunk link, for example), a VLAN ID tag is added to represent the VLAN membership of that frame. The picture below shows how VLAN tag is added and removed while going through the network. http://www.cisco.com/c/en/us/support/docs/lan-switching/8021q/17056-741-4.html QUESTION 250 Configuration of which option is required on a Cisco switch for the Cisco IP phone to work? A. PortFast on the interface B. the interface as an access port to allow the voice VLAN ID C. a voice VLAN ID in interface and global configuration mode D. Cisco Discovery Protocol in global configuration mode Correct Answer: B Section: (none) Explanation Explanation/Reference: Explanation: Configure the Switch Port to Carry Both Voice and Data TrafficWhen you connect an IP phone to a switch using a trunk link, it can cause high CPU utilization in the switches. As all the VLANs for a particular interface are trunked to the phone, it increases the number of STP instances the switch has to manage. This increases the CPU utilization. Trunking also causes unnecessary broadcast / multicast / unknown unicast traffic to hit the phone link. In order to avoid this, remove the trunk configuration and keep the voice and access VLAN configured along with Quality of Service (QoS). Technically, it is still a trunk, but it is called a Multi-VLAN Access Port (MVAP). Because voice and data traffic can travel through the same port, you should specify a different VLAN for each type of traffic. You can configure a switch port to forward voice and data traffic on different VLANs. Configure IP phone ports with a voice VLAN configuration. This configuration creates a pseudo trunk, but does not require you to manually prune the unnecessary VLANs. The voice VLAN feature enables access ports to carry IP voice traffic from an IP phone. The voice VLAN feature is disabled by default. The Port Fast feature is automatically enabled when voice VLAN is configured. When you disable voice VLAN, the Port Fast feature is not automatically disabled. QUESTION 251 Which statement describes the effect of the overload keyword in the ip nat inside source list 90 interface ethernet 0/0 overload command? A. Addresses that match address list inside are translated to the IP address of the Ethernet 0/0 interface. B. Hosts that match access inside are translated to an address m the Ethernet 0/0 network. C. Hosts on the Ethernet 0/0 LAN are translated to the address pool in access list 90. D. Addresses that match access list 90 are translated through PAT to the IP address of the Ethernet 0/0 interface Correct Answer: D Section: (none) Explanation QUESTION 252 Which statement describes the effect of the copy run start command on a router in enable mode? A. The running configuration of the router is saved to NVRAM and used during the boot process. B. The router reboots and loads the last saved running configuration. C. A copy of the running configuration of the router is sent by FTP to a designated server. D. A new running configuration is loaded from flash memory to the router. Correct Answer: A Section: (none)
- 128. Explanation Explanation/Reference: QUESTION 253 After you configure a default route to the Internet on a router, the route is missing from the routing table. Which option describes a possible reason for the problem? A. The next-hop address is unreachable. B. The default route was configured on a passive interface. C. Dynamic routing is disabled. D. Cisco Discovery Protocol is disabled on the interface used to reach the next hop. Correct Answer: A Section: (none) Explanation Explanation/Reference: QUESTION 254 You have configured the host computers on a campus LAN to receive their DHCP addresses form the local router to be able to browse their corporate site. Which statement about the network environment is true? A. It supports a DNS server for use by DHCP clients. B. Two host computers may be assigned the same IP address. C. The DNS server must be configured manually on each host. D. The domain name must be configured locally on each host computer. Correct Answer: A Section: (none) Explanation Explanation/Reference: QUESTION 255 Which protocol verifies connectivity between two switches that are configured with IP addresses in the same network? A. ICMP B. STP C. VTP D. HSRP Correct Answer: A Section: (none) Explanation Explanation/Reference: QUESTION 256 On which OSI layer does a VLAN operate? A. Layer 1 B. Layer 2
- 129. C. Layer 3 D. Layer 4 Correct Answer: B Section: (none) Explanation QUESTION 257 Which NAT command can be applied to an interface? A. ip nat inside B. ip nat inside test access-list-number pool pool-name C. ip nat inside source static 10.10.10.0 10.10.10.50 D. ip nat pool test 10.10.10.0 10.10.10.50 255.255.255.0 Correct Answer: A Section: (none) Explanation Explanation/Reference: QUESTION 258 Which technique can you use to route IPv6 traffic over an IPv4 infrastructure? A. NAT B. 6to4 tunneling C. L2TPv3 D. dual-stack Correct Answer: B Section: (none) Explanation Explanation/Reference: QUESTION 259 Which Ethernet interface command is present when you boot a new Cisco router for the first time? A. speed 100 B. shutdown C. ip address 192.168.1.1 255.255.255.0 D. duplex half Correct Answer: B Section: (none) Explanation Explanation/Reference: QUESTION 260 Which table displays the MAC addresses that are learned on a switch? A. FIB B. ARP
- 130. C. TCAM D. CAM Correct Answer: D Section: (none) Explanation Explanation/Reference: Explanation: The table is built by recording the source address and inbound port of all frames. As frames arrive on switch ports, the source MAC addresses are learned and recorded in the CAM table. The port of arrival and the VLAN are both recorded in the table, along with a timestamp. If a MAC address learned on one switch port has moved to a different port, the MAC address and timestamp are recorded for the most recent arrival port. Then, the previous entry is deleted. If a MAC address is found already present in the table for the correct arrival port, only its timestamp is updated. QUESTION 261 Which statement is a Cisco best practice for switch port security? A. Vacant switch ports must be shut down. B. Empty ports must be enabled in VLAN 1. C. VLAN 1 must be configured as the native VLAN. D. Err-disabled ports must be configured to automatically re-enable. Correct Answer: A Section: (none) Explanation Explanation/Reference: QUESTION 262 Which NTP concept indicates the distance between a device and the reliable time source? A. clock offset B. stratum C. reference D. dispersion Correct Answer: B Section: (none) Explanation QUESTION 263 Which command displays the number of times that an individual router translated an inside address to an outside address? A. show ip protocol 0 B. show ip nat translation C. show counters D. show ip route E. show ip nat statistics Correct Answer: E Section: (none) Explanation
- 131. Explanation/Reference: QUESTION 264 Which set of conditions comprises a successful ping attempt between two connected routers configured with IP addresses on the same subnet? A. The destination host receives an echo reply from the source host within one second and the source host receives an echo request from the destination host. B. The destination host receives an echo request from the source host within one second. C. The destination host receives an echo reply from the source host within one second and the source host receives an echo reply from the destination host within two seconds. D. The destination host receives an echo request from the source host and the source host receives an echo request from the destination host within one second. E. The destination host receives an echo request from the source host and the source host receives an echo reply from the destination host within two seconds. Correct Answer: E Section: (none) Explanation Explanation/Reference: QUESTION 265 What happens when the cable is too long? A. Baby Giant B. Late collision Correct Answer: B Section: (none) Explanation QUESTION 266 Which two VLANs are reserved for system use only? (Choose two) A. 1 B. 4095 C. 4096 D. 0 E. 1001 Correct Answer: BD Section: (none) Explanation Explanation/Reference: Explanation: The VLANs 0 and 4095 are reserved by the IEEE 802.1Q standard and you cannot create, delete, or modify them so they are the correct answers. Note: + VLAN 0 and 4095 are reserved for system use only. You cannot see or use these VLANs. + VLAN 1 and VLANs 1002-1005 are default VLANs. Default VLANs are created automatically and cannot be configured or deleted by users. + VLAN 2 to 1001 are normal VLANs. You can create, use and delete them. + VLAN 1002 to 1005 are normal VLANs too but Cisco reserved for FDDI an Token Ring.
- 132. QUESTION 267 What is the requirement of configuring 6to4 tunnelling on two routers? A. Both ipv6 and ipv4 must be configured B. Only IPv6 C. Only IPv4 Correct Answer: A Section: (none) Explanation QUESTION 268 Which name describes an IPV6 host-enable tunneling technique that uses IPV4 UDP,does not require dedicated gateway tunnels,and can pass through existing IPV4 NAT gateways? A. dual stack XX B. dynamic C. Teredo D. Manual 6to4 Correct Answer: C Section: (none) Explanation QUESTION 269 Which sequence begins a unique local IPv6 address in binary notation? A. 00000000 B. 1111110 C. 1111100 D. 1111111 Correct Answer: B Section: (none) Explanation QUESTION 270 Which statement about 6to4 tunneling is true? A. One tunnel endpoint must be configured with IPv4 only B. It establishes a point-to-point tunnel C. Both tunnel endpoints must be configured with IPv4 only D. Both tunnel endpoints must support IPv4 and IPv6 Correct Answer: D Section: (none) Explanation QUESTION 271 What is true about ipv6 unique local addresses: A. Global id B. Public routable C. Summarization
- 133. D. Unique prefix Correct Answer: D Section: (none) Explanation QUESTION 272 How do you bypass password on cisco device? A. Change the configuration register to 0x2142. With this setting when that router reboots, it bypasses the startup-config and no password is required. Correct Answer: A Section: (none) Explanation QUESTION 273 How many primary ipv4 addresses can be assigned on router interface ? A. 0 B. 1 C. 4 D. Unlimited Correct Answer: D Section: (none) Explanation Explanation/Reference: QUESTION 274 Which command is used to build DHCP pool? A. ipdhcp conflict B. ipdhcp-server pool DHCP C. ipdhcp pool DHCP D. ipdhcp-client pool DHCP Correct Answer: C Section: (none) Explanation QUESTION 275 What occurs when an Ethernet cable is too long? A. Giants B. Runts C. late collisions D. interface resets Correct Answer: C Section: (none) Explanation
- 134. QUESTION 276 You are configuring dynamic NAT on your Cisco IOS router. Which command is used to verify the interfaces that are being used as the outside interface and the inside interface? A. show interfaces B. show ip route C. show ip nat translations D. show ip interface brief E. show ip interface F. show ip nat statistics Correct Answer: F Section: (none) Explanation Explanation/Reference: QUESTION 277 What disables CEF? A. RIB B. IPv6 C. Ping D. Disable Logging Correct Answer: D Section: (none) Explanation QUESTION 278 What is the default configuration of a Cisco switch? A. No default gateway assigned B. System name is Cisco Correct Answer: A Section: (none) Explanation QUESTION 279 When you configure router# ipnat pool 10.10.10.1 10.10.10.20 255.255.255.0 A. nat pool B. dynamicnat C. nat translation D. dhcp pool Correct Answer: B Section: (none) Explanation QUESTION 280 Which technology allows a large number of private IP addresses to be represented by a smaller number of
- 135. public IP addresses? A. NAT B. NTP C. RFC 1631 D. RFC 1918 Correct Answer: A Section: (none) Explanation QUESTION 281 Which command can you enter to verify that a 128-bit address is live and responding? A. traceroute B. telnet C. ping D. ping ipv6 Correct Answer: C Section: (none) Explanation QUESTION 282 Refer to the exhibit. You have discovered that computers on the 192 168 10 0/24 network can ping their default gateway, but they cannot connect to any resources on a remote network. Which reason for the problem is most likely true? A. The 192.168.12 0/24 network is missing from OSPF B. The OSPF process ID is incorrect C. The OSPF area number is incorrect. D. An ARP table entry is missing for 192.168.10.0. E. A VLAN number is incorrect for 192.168.10.0. Correct Answer: A Section: (none) Explanation Explanation/Reference:
- 136. QUESTION 283 If three devices are plugged into one port on a switch and two devices are plugged into a different port, how many collision domains are on the switch? A. 2 B. 4 C. 5 D. 6 Correct Answer: A Section: (none) Explanation Explanation/Reference: QUESTION 284 Which three commands must you enter to create a trunk that allows VLAN 20? (Choose three) A. Switch(config-if)#switchport mode dynamic auto B. Switch(config-if)#switchport mode trunk C. Switch(config-if)#switchport trunk allowed vlan 20 D. Switch(config-if)#switchport mode dynamic desirable E. Switch(config-if)#switchport trunk encapsulation dotlq F. Switch(config-if)#switchport trunk native vlan 20 Correct Answer: BCE Section: (none) Explanation Explanation/Reference: QUESTION 285 Which three options are types of Layer 2 network attack? (Choose three.) A. ARP attacks B. brute force attacks C. spoofing attacks D. DDOS attacks E. VLAN hopping F. botnet attacks Correct Answer: ACE Section: (none) Explanation Explanation/Reference: QUESTION 286 How does a router handle an incoming packet whose destination network is missing from the Routing table? A. it discards the packet. B. it broadcasts the packet to each network on the router. C. it routes the packet to the default route.
- 137. D. it broadcasts the packet to each interface on the router. Correct Answer: A Section: (none) Explanation Explanation/Reference: QUESTION 287 Which feature facilitates the tagging of frames on a specific VLAN? A. Routing B. hairpinning C. switching D. encapsulation Correct Answer: D Section: (none) Explanation Explanation/Reference: QUESTION 288 When you troubleshoot an IPv4 connectivity issue on a router, which three router configuration checks you must perform? (Choose three) A. Verify that the router interface IP address IP address is correct. B. Verify that the DNS is configured correctly. C. Verify that the router and the host use the same subnet mask. D. Verify that the router firmware is up-to-date. E. Verify that a default route is configured. F. Verify that the route appears in the Routing table Correct Answer: ACF Section: (none) Explanation Explanation/Reference: QUESTION 289 Which two statements about unique local IPv6 addresses are true? (Choose two) A. They are identical to IPv4 private addresses. B. They are defined by RFC 1884. C. They use the prefix FEC0::/10 D. They use the prefix FC00::/7 E. They can be routed on the IPv6 global internet. Correct Answer: AD Section: (none) Explanation Explanation/Reference:
- 138. QUESTION 290 Which header field is new in IPv6? A. Hop Limit B. Flow Label C. Version D. Traffic Class Correct Answer: B Section: (none) Explanation Explanation/Reference: QUESTION 291 Hotspot Questions
- 139. Select two options which are security Issues which need to be modified before RouterA is used? (Choose two.) A. unencrypted weak password is configured to protect privilege mode B. inappropriate wording in banner message C. the virtual terminal lines have a weak password configured D. virtual terminal lines have a password, but it will not be used E. configuration supports un-secure web server access Correct Answer: BD Section: (none) Explanation Explanation/Reference: Explanation: (This answer can be done by simulation only, don't know user name password and banner message etc) QUESTION 292 Hotspot Questions
- 140. Select three options which are security issues with the current configuration of SwitchA . (Choose three.) A. privilege mode is protected with an unencrypted password B. inappropriate wording in banner message C. virtual terminal lines are protected only by a password requirement D. both the username and password are weak E. telnet connections can be used to remotely manage the switch F. cisco user will be granted privilege level 15 by default Correct Answer: ABD Section: (none) Explanation Explanation/Reference: Explanation:
- 141. (This answer can be done by simulation only, don't know user name password and banner message etc) QUESTION 293 Hotspot Questions Which two of the following are true regarding the configuration of RouterA? (Choose two.) A. at least 5 simultaneous remote connections are possible B. only telnet protocol connections to RouterA are supported C. remote connections to RouterA using telnet will succeed D. console line connections will nevertime out due to inactivity E. since DHCP is not used on FaO/1 there is not a need to use the NAT protocol Correct Answer: AC Section: (none)
- 142. Explanation Explanation/Reference: Explanation: The IP address can accommodate 5 hosts at least, telnet can be accessed on the router QUESTION 294 Hotspot Questions Which of the following is true regarding the configuration of SwitchA? A. only 5 simultaneous remote connections are possible B. remote connections using ssh will require a username and password C. only connections from the local network will be possible D. console access to SwitchA requires a password
- 143. Correct Answer: B Section: (none) Explanation Explanation/Reference: Explanation: Ssh login requires a user name and password always while other conditions may or may not be true. QUESTION 295 To allow or prevent load balancing to network 172.16.3.0/24, which of the following commands could be used in R2? (Choose two.) A. R2(config-if)#clock rate B. R2(config-if)#bandwidth C. R2(config-if)#ip ospf cost D. R2(config-if)#ip ospf priority E. R2(config-router)#distance ospf Correct Answer: BC Section: (none) Explanation
- 144. Explanation/Reference: Explanation: http://www.cisco.com/en/US/tech/tk365/technologies_white_paper09186a0080094e9e.sht ml#t6 The cost (also called metric) of an interface in OSPF is an indication of the overhead required to send packets across a certain interface. The cost of an interface is inversely proportional to the bandwidth of that interface. A higher bandwidth indicates a lower cost. There is more overhead (higher cost) and time delays involved in crossing a 56k serial line than crossing a 10M Ethernet line. The formula used to calculate the cost is: Cost = 10000 0000/bandwidth in bps For example, it will cost 10 EXP8/10 EXP7 = 10 to cross a 10M Ethernet line and will cost 10 EXP8/1544000 =64 to cross a T1 line. By default, the cost of an interface is calculated based on the bandwidth; you can force the cost of an interface with the ip ospf cost <value> interface subconfiguration mode command. QUESTION 296 After the network has converged, what type of messaging, if any, occurs between R3 and R4? A. No messages are exchanged B. Hellos are sent every 10 seconds. C. The full database from each router is sent every 30 seconds. D. The routing table from each router is sent every 60 seconds.
- 145. Correct Answer: B Section: (none) Explanation Explanation/Reference: Explanation: HELLO messages are used to maintain adjacent neighbors so even when the network is converged, hellos are still exchanged. On broadcast and point-to-point links, the default is 10 seconds, on NBMA the default is 30 seconds. Although OSPF is a link-state protocol but the full database from each router is sent every 30 minutes (not seconds) -> C and D are not correct. QUESTION 297 OSPF is configured using default classful addressing. With all routers and interfaces operational, how many networks will be in the routing table of R1 that are indicated to be learned by OSPF? A. 2 B. 3 C. 4 D. 5
- 146. E. 6 F. 7 Correct Answer: C Section: (none) Explanation Explanation/Reference: QUESTION 298 R1 is configured with the default configuration of OSPF. From the following list of IP addresses configured on R1, which address will the OSPF process select as the router ID? A. 192.168.0.1 B. 172.16.1.1 C. 172.16.2.1 D. 172.16.2.225 Correct Answer: A Section: (none)
- 147. Explanation Explanation/Reference: Explanation: The Router ID (RID) is an IP address used to identify the router and is chosen using the following sequence: + The highest IP address assigned to a loopback (logical) interface. + If a loopback interface is not defined, the highest IP address of all active router's physical interfaces will be chosen. + The router ID can be manually assigned In this case, because a loopback interface is not configured so the highest active IP address 192.168.0.1 is chosen as the router ID. QUESTION 299 R1 is unable to establish an OSPF neighbor relationship with R3. What are possible reasons for this problem? (Choose two) A. All of the routers need to be configured for backbone Area 1. B. R1 and R2 are the DR and BDR, so OSPF will not establish neighbor adjacency with R3. C. A static route has been configured from R1 to R3 and prevents the neighbor adjacency from being established. D. The hello and dead interval timers are not set to the same values on R1 and R3.
- 148. E. EIGRP is also configured on these routers with a lower administrative distance. F. R1 and R3 are configured in different areas. Correct Answer: DF Section: (none) Explanation Explanation/Reference: Explanation: To become OSPF neighbors, routers must meet these requirements: Hello interval, Dead interval and AREA number -> D and F are correct. QUESTION 300 Lab Simulation - OSPF A. See Explanation Correct Answer: A Section: (none) Explanation Explanation/Reference: The question mentioned Boston router was not configured correctly or incomplete so we should check this router first. Click on Host B to access the command line interface (CLI) of Boston router. Boston>enable (type cisco as its password here) Boston#show running-config
- 149. First, remember that the current OSPF Process ID is 2 because we will need it for later configuration. Next notice that in the second “network” command the network and wildcard mask are 192.168.155.0 and 0.0.0.3 which is equivalent to 192.168.155.0 255.255.255.252 in term of subnet mask. Therefore this subnetwork’s range is from 192.168.155.0 to 192.168.155.3 but the ip address of s0/0 interface of Boston router is192.168.155.5 which don’t belong to this range -> this is the reason why OSPF did not recognize s0 interface of Boston router as a part of area 0. So we need to find a subnetwork that s0 interface belongs to. IP address of S0 interface: 192.168.155.5/30 Subnet mask: /30 = 1111 1111.1111 1111.1111 1111.1111 1100 Increment: 4 Network address (which IP address of s0 interface belongs to): 192.168.155.4 (because 4 * 1 = 4 < 5) Therefore we must use this network instead of 192.168.155.0 network Boston#configure terminal Boston(config)#router ospf 2 Boston(config-router)#no network 192.168.155.0 0.0.0.3 area 0 Boston(config-router)#network 192.168.155.4 0.0.0.3 area 0 Boston(config-router)#end Boston#copy running-config startup-config Finally, you should issue a ping command from Boston router to Lancaster router to make sure it works well. Boston#ping 192.168.43.1 QUESTION 301 This topology contains 3 routers and 1 switch. Complete the topology. Drag the appropriate device icons to the labeled Device Drag the appropriate connections to the locations labeled Connections. Drag the appropriate IP addresses to the locations labeled IP address (Hint: use the given host addresses and Main router information) To remove a device or connection, drag it away from the topology. Use information gathered from the Main router to complete the configuration of any additional routers. No passwords are required to access the Main router. The config terminal command has been disabled for the HQ router. The router does not require any configuration. Configure each additional router with the following: Configure the interfaces with the correct IP address and enable the interfaces. Set the password to allow console access to consolepw Set the password to allow telnet access to telnetpw Set the password to allow privilege mode access to privpw Note: Because routes are not being added to the configurations, you will not be able to ping through the internetwork.
- 150. All devices have cable autosensing capabilities disabled. All hosts are PC's A. See Explanation Correct Answer: A Section: (none) Explanation Explanation/Reference:
- 151. Explanation: (1) Configure two routers on the left and right with these commands: Router1 = router on the left (2) Assign appropriate IP addresses to Fa0/0 & Fa0/1 interfaces: Router1>enable Router1#configure terminal Router1(config)#interface fa0/0 Router1(config-if)#ip address 192.168.152.190 255.255.255.240 Router1(config-if)#no shutdown Router1(config-if)#interface fa0/1 Router1(config-if)#ip address 192.168.152.142 255.255.255.240 Router1(config-if)#no shutdown (3) Set passwords (configure on two routers) + Console password: Router1(config-if)#exit Router1(config)#line console 0 Router1(config-line)#password consolepw Router1(config-line)#login Router1(config-line)#exit + Telnet password: Router1(config)#line vty 0 4 Router1(config-line)#password telnetpw Router1(config-line)#login
- 152. Router1(config-line)#exit + Privilege mode password: Router1(config)#enable password privpw Save the configuration: Router1(config)#exit Router1#copy running-config startup-config (4) Configure IP addresses of Router2 (router on the right) Router2>enable Router2#configure terminal Router2(config)#interface fa0/0 Router2(config-if)#ip address 192.168.152.238 255.255.255.240 Router2(config-if)#no shutdown Router2(config-if)#interface serial0/0 Router2(config-if)#ip address 192.168.152.174 255.255.255.240 Router2(config-if)#no shutdown QUESTION 302 Lab Questions
- 153. Correct Answer: See Explanation Section: (none) Explanation Explanation/Reference:
- 154. Answer: 192.168.8.15 Explanation: The IP address assigned to FA0/1 is 192.168.8.9/29, making 192.168.8.15 the broadcast address. Answer: 16 Kbit/sec Explanation: Use the "show interface s0/0" to see the bandwidth set at 16 Kbit/sec. Answer: 6 Explanation: This is a /29 address, so there are 6 usable IP's on this subnet.
- 155. Answer: Router1(conf)# interface fa0/1 Router1(conf0if)# no shutdown Explanation: Do a "show ip int brief" and you will see that Fa0/1 has an IP address assigned, but it is shut down. QUESTION 303 Lab Simulation - CLI Configuration
- 156. Attention: In practical examinations, please note the following, the actual information will prevail. 1. Name of the router is xxx 2. Enable. secret password is xxx 3. Password In access user EXEC mode using the console is xxx 4. The password to allow telnet access to the router is xxx 5. IP information Correct Answer: See Explanation Section: (none) Explanation Explanation/Reference: Answer: Router>enable Router#config terminal Router(config)#hostname Gotha 2) Enable-secret password (cisco10): Gotha(config)#enable secret mi222ke 3) Set the console password to G8tors1:
- 157. Gotha(config)#line console 0 Gotha(config-line)#password G8tors1 Gotha(config-line)#login Gotha(config-line)#exit 4) Set the Telnet password to dun63lap: Gotha(config)#line vty 0 4 Gotha(config-line)#password dun63lap Gotha(config-line)#login Gotha(config-line)#exit 5) Configure Ethernet interface (on the right) of router Gotha: Ethernet network 209.165.201.0 /27 - Router has the fourth assignable host address in subnet. Ethernet Interface on router R2 is Fast Ethernet 0/0 as per the exhibit First we need to identify the subnet mask Network: 209.165.201.0 /27 Subnet mask: /27: 27 bits = 8 + 8 + 8 + 3 =8(bits).8(bits).8(bits) .11100000 (3bits) =255.255.255.11100000 =11100000 = 128+64+32+0+0+0+0+0 = 224 Subnet mask: 255.255.255.224 Different subnet networks and there valid first and last assignable host address range for above subnet mask are Subnet Networks :::::: Valid Host address range :::::: Broadcast address 209.165.201.0 :::::: 209.165.201.1 - 209.165.201.30 ::::: 209.165.201.31 209.165.201.32 :::::: 209.165.201.33 - 209.165.201.62 ::::: 209.165.201.63 209.165.201.64 :::::: 209.165.201.65 - 209.165.201.94 :::::: 209.165.201.95 209.165.201.96 :::::: 209.165.201.97 - 209.165.201.126 :::::: 209.165.201.127 209.165.201.128 :::::: 209.165.201.129 - 209.165.201.158 :::::: 209.165.201.159 209.165.201.160 :::::: 209.165.201.161 - 209.165.201.190 :::::: 209.165.201.191 209.165.201.192 :::::: 209.165.201.193 - 209.165.201.222 :::::: 209.165.201.223 209.165.201.224 :::::: 209.165.201.225 - 209.165.201.254 :::::: 209.165.201.255 Use above table information for network 209.165.201.0 /27 to identify First assignable host address: 209.165.201.1 Last assignable host address: 209.165.201.30 Fourth assignable host address: 209.165.201.4 Assign the fourth assignable host address to Fa0/0 interface of Gotha router: Gotha(config)#interface Fa0/0 Gotha(config-if)#ip address 209.165.201.4 255.255.255.224 Gotha(config-if)#no shutdown Gotha(config-if)#exit 6) Configure Serial interface (on the left) of router Gotha: Serial Network is 192.0.2.176 /28 - Router has the last assignable host address in subnet. Serial Interface on R2 is Serial 0/0/0 as per the exhibit First we need to identify the subnet mask Network: 192.0.2.176 /28 Subnet mask: /28: 28bits = 8bits+8bits+8bits+4bits =8(bits).8(bits).8(bits) .11110000 (4bits) =255.255.255.11100000 =11100000 = 128+64+32+16+0+0+0+0 = 240 Subnet mask: 255.255.255.240 Different subnet networks and there valid first and last assignable host address range for above subnet mask are Subnet Networks ::::: Valid Host address ::::::::::: Broadcast address 192.0.2.0 :::::: 192.0.2.1 - 192.0.2.14 ::::::: 192.0.2.15 192.0.2.16 ::::::: 192.0.2.17 - 192.0.2.30 ::::::: 192.0.2.31 192.0.2.32 :::::::: 192.0.2.33 - 192.0.2.46 :::::: 192.0.2.47
- 158. 192.0.2.48 :::::: 192.0.2.49 - 192.0.2.62 ::::::: 192.0.2.64 192.0.2.64 ::::::: 192.0.2.65 - 192.0.2.78 ::::::: 192.0.2.79 192.0.2.80 :::::::: 192.0.2.81 - 192.0.2.94 :::::: 192.0.2.95 192.0.2.96 :::::: 192.0.2.97 - 192.0.2.110 ::::::: 192.0.2.111 192.0.2.112 ::::::: 192.0.2.113 - 192.0.2.126 ::::::: 192.0.2.127 192.0.2.128 :::::::: 192.0.2.129 - 192.0.2.142 :::::: 192.0.2.143 192.0.2.144 :::::: 192.0.2.145 - 192.0.2.158 ::::::: 192.0.2.159 192.0.2.160 ::::::: 192.0.2.161 - 192.0.2.174 ::::::: 192.0.2.175 192.0.2.176 :::::::: 192.0.2.177 - 192.0.2.190 :::::: 192.0.2.191 and so on …. Use above table information for network 192.0.2.176 /28 to identify First assignable host address: 192.0.2.177 Last assignable host address: 192.0.2.190 We need to configure Last assignable host address (192.0.2.190) on serial 0/0/0 using the subnet mask 255.255.255.240 Assign the last assignable host address to S0/0/0 interface of Gotha router: Gotha(config)#interface S0/0/0 (or use interface S0/0 if not successful) Gotha(config-if)#ip address 192.0.2.190 255.255.255.240 Gotha(config-if)#no shutdown Gotha(config-if)#exit 7) Configure RIP v2 routing protocol: Gotha(config)#router rip Gotha(config-router)#version 2 Gotha(config-router)#network 209.165.201.0 Gotha(config-router)#network 192.0.2.176 Gotha(config-router)#end Save the configuration: Gotha#copy running-config startup-config Finally, you should use the ping command to verify all are working properly! QUESTION 304 Hotspot Question Refer to the topology. Your company has decided to connect the main office with three other remote branch offices using point-to-point serial links. You are required to troubleshoot and resolve OSPF neighbor adjacency issues between the main office and the routers located in the remote branch offices.
- 159. An OSPF neighbor adjacency is not formed between R3 in the main office and R5 in the Branch2 office. What is causing the problem? A. There is an area ID mismatch. B. There is a PPP authentication issue; a password mismatch. C. There is an OSPF hello and dead interval mismatch. D. There is a missing network command in the OSPF process on R5. Correct Answer: C Section: (none) Explanation Explanation/Reference: Explanation: The "show ip ospf interface command on R3 and R5 shows that the hello and dead intervals do not match. They are 50 and 200 on R3 and 10 and 40 on R5.
- 160. QUESTION 305 Hotspot Question Refer to the topology. Your company has decided to connect the main office with three other remote branch offices using point-to-point serial links. You are required to troubleshoot and resolve OSPF neighbor adjacency issues between the main office and the routers located in the remote branch offices.
- 161. R1 does not form an OSPF neighbor adjacency with R2. Which option would fix the issue? A. R1 ethernetO/1 is shutdown. Configure no shutdown command. B. R1 ethernetO/1 configured with a non-default OSPF hello interval of 25: configure no ip ospf hello-interval 25 C. R2 ethernetO/1 and R3 ethernetO/O are configured with a non-default OSPF hello interval of 25; configure no ip ospf hello-interval 25 D. Enable OSPF for R1 ethernetO/1; configure ip ospf 1 area 0 command under ethernetO/1 Correct Answer: B Section: (none) Explanation Explanation/Reference: Explanation: Looking at the configuration of R1, we see that R1 is configured with a hello interval of 25 on interface Ethernet 0/1 while R2 is left with the default of 10 (not configured).
- 162. QUESTION 306 Hotspot Question Refer to the topology. Your company has decided to connect the main office with three other remote branch offices using point-to-point serial links. You are required to troubleshoot and resolve OSPF neighbor adjacency issues between the main office and the routers located in the remote branch offices.
- 163. An OSPF neighbor adjacency is not formed between R3 in the main office and R6 in the Branch3 office. What is causing the problem? A. There is an area ID mismatch. B. There is a PPP authentication issue; the username is not configured on R3 and R6. C. There is an OSPF hello and dead interval mismatch. D. The R3 router ID is configured on R6. Correct Answer: D Section: (none) Explanation Explanation/Reference: Explanation: Using the show running-config command we see that R6 has been incorrectly configured with the same router ID as R3 under the router OSPF process.
- 164. QUESTION 307 Hotspot question. Click on the correct location or locations in the exhibit.
- 165. A. See Explanation Correct Answer: A Section: (none) Explanation Explanation/Reference:
- 166. Answer: 192.168.200.31 Explanation: User the "show ip interface brief" command User the "show interface fa0/1" command
- 167. From the output we learn that the ip address of the FastEthernet0/1 interface of Router1 is 192.168.200.23 and the subnet mask is /28. -> The broadcast address of this subnetwork is 192.168.200.31 Answer: 512 Kbit/sec Explanation: Use the "show interfaces serial 0/0" command
- 168. Answer: FastEthernet0/0 and Serial 0/1 Explanation: User the "show ip interface brief" command Notice that Router1 does not have Ethernet 0 and Serial 0 interfaces. FastEthernet 0/1 and Serial 0/0 were configured with their IP addresses therefore only FastEthernet 0/0 and Serial0/1 have not had any configurations applied.
- 169. Answer: 14 Explanation: The mask address of interface Fa0/1 of Router1 is /28, which has four 0 bits (1111 1111.1111 1111.1111 1111.1111 0000). Therefore there are 24 – 2 = 14 assignable IP addresses for hosts on the LAN.
- 170. Answer: Router1(conf)# interface s0/0 Router1(conf-if)# no shutdown Explanation: User the "show ip interface brief" command From the output, we learn that the status of Serial0/0 interface which connects to ISP router is currently "administratively down". This status indicates this interface is shutting down so we need to turn it on. QUESTION 308 Hotspot question. Click on the correct location or locations in the exhibit.
- 171. A. See Explanation Correct Answer: A Section: (none) Explanation
- 172. Explanation/Reference: Answer: 172.16.236.4 Answer: 10.4.8.1 Answer: The router with the address 172.16.236.1 has a route it can use to reach network of the DNS server
- 173. Answer: The network card on the computer is functioning correctly. The device with the IP address 172.16.236.1 is reachable over the network. Answer: The router uses an ARP request to obtain the correct MAC address for the computer. It then encapsulates the packet in a frame addressed to the MAC address 00-0D-60-FD-F0-34. QUESTION 309 Drag and Drop Question On the left are various network protocols. On the right are the layers of the TCP/IP model. Assuming a reliable connection is required, move the protocols on the left to the TCP/IP layers on the right to show the proper encapsulation for an email message sent by a host on a LAN. (Not all options are used) Select and Place:
- 174. Correct Answer: Section: (none) Explanation Explanation/Reference: + application layer: SMTP + transport layer: TCP + internet layer: IP + network access layer: Ethernet QUESTION 310 Drag and Drop Question Various protocols are listed on the left On the right are applications for the use of those protocols. Drag the
- 175. protocol on the left to an associated function for that protocol on the right (Not all options are used) Select and Place: Correct Answer: Section: (none) Explanation Explanation/Reference:
- 176. + ARP: A PC sends packets to the default gateway IP address the first time since the PC turned on. + ICMP: The network administrator is checking basic IP connectivity from a workstation to a server. + DNS: The TCP/IP protocol stack must find an IP address for packets destined for a URL. + DHCP: A network device will automatically assign IP addresses to workstations. QUESTION 311 Drag and Drop Question Move the protocol or service on the left to a situation on the right where it would be used. (Not all options are used) Select and Place: Correct Answer:
- 177. Section: (none) Explanation Explanation/Reference: + NAT: A PC with address 10.1.5.10 must access devices on the Internet. + DHCP: Only routers and servers require static IP addresses. Easy IP administration is required. + DNS: A PC only knows a server as MediaServer. IP needs to send data to that server. + OSPF: A protocol is needed to replace current static routes with automatic route updates. QUESTION 312 Drag and Drop Question Drag the definition on the left to the correct term on the right. Not all definitions on the left will be used. Select and Place:
- 178. Correct Answer: Section: (none) Explanation Explanation/Reference: + SNMP: a protocol used to monitor and manage network devices + FTP: a reliable, connection-oriented service that uses TCP to transfer files between systems + TFTP: a connectionless service that uses UDP to transfer files between systems + DNS: a protocol that converts human-readable names into machine-readable addresses + DHCP: used to assign IP addresses automatically and set parameters such as subnet mask and default gateway
- 179. QUESTION 313 Drag and Drop Question Drag the appropriate command on the left to the configuration task it accomplishes (not all options are used) Select and Place: Correct Answer: Section: (none)
- 180. Explanation Explanation/Reference: QUESTION 314 Hotspot Question - RIPv2 Troubleshooting I Scenario: You work for a company that provides managed network services, and of your real estate clients running a small office is experiencing network issues, Troubleshoot the network issues. Router R1 connects the main office to internet, and routers R2 and R3 are internal routers NAT is enabled on Router R1. The routing protocol that is enable between routers R1, R2, and R3 is RIPv2. R1 sends default route into RIPv2 for internal routers to forward internet traffic to R1. Server1 and Server2 are placed in VLAN 100 and 200 respectively, and dare still running router on stick configuration with router R2. You have console access on R1, R2, R3, and L2SW1 devices. Use only show commands to troubleshoot the issues.
- 181. -- More configuration please check the PDF file --- Server1 and Server2 are unable to communicate with the rest of the network. Your initial check with system administrators shows that IP address settings are correctly configured on the server side. What could be an issue? A. The VLAN encapsulation is misconfigured on the router subinterfaces. B. The Router is missing subinterface configuration. C. The Trunk is not configured on the L2SW1 switch. D. The IP address is misconfigured on the primary router interface. Correct Answer: A Section: (none) Explanation Explanation/Reference: Explanation: Check the configuration of the interface that is connected to Server1 and Server2 on R2 with “show running-config” command.
- 182. We see that subinterface E0/1.100 has been configured with VLAN 200 (via “encapsulation dot1Q 200” command) while Server1 belongs to VLAN 100. Therefore this configuration is not correct. It should be “encapsulation dot1Q 100” instead. The same thing for interface E0/1.200, it should be “encapsulation dot1Q 200” instead. QUESTION 315 Hotspot Question - RIPv2 Troubleshooting I Scenario: You work for a company that provides managed network services, and of your real estate clients running a small office is experiencing network issues, Troubleshoot the network issues. Router R1 connects the main office to internet, and routers R2 and R3 are internal routers NAT is enabled on Router R1. The routing protocol that is enable between routers R1, R2, and R3 is RIPv2. R1 sends default route into RIPv2 for internal routers to forward internet traffic to R1. Server1 and Server2 are placed in VLAN 100 and 200 respectively, and dare still running router on stick configuration with router R2. You have console access on R1, R2, R3, and L2SW1 devices. Use only show commands to troubleshoot the issues.
- 183. -- More configuration please check the PDF file --- Users in the main office complain that they are unable to reach internet sites. You observe that internet traffic that is destined towards ISP router is not forwarded correctly on Router R1. What could be an issue? Ping to Internet server shows the following results from R1: A. The next hop router address for the default route is incorrectly configured. B. Default route pointing to ISP router is not configured on Router R1. C. Default route pointing to ISP router is configured with AD of 225. D. Router R1 configured as DHCP client is not receiving default route via DHCP from ISP router. Correct Answer: B Section: (none) Explanation Explanation/Reference: Explanation: When all the users cannot reach internet sites we should check on the router connecting to the ISP to see if it has a default route pointing to the ISP or not. Use the “show ip route” command on R1:
- 184. We cannot find a default route on R1 (something like this: S* 0.0.0.0/0 [1/0] via 209.165.201.2) so maybe R1 was not configured with a default route. We can check with the “show running-config” on R1: We need a default route (like “ip route 0.0.0.0 0.0.0.0 209.165.201.2”) but we cannot find here so we can conclude R1 was not be configured with a default route pointing to the ISP router. QUESTION 316 Hotspot Question - RIPv2 Troubleshooting I Scenario: You work for a company that provides managed network services, and of your real estate clients running a small office is experiencing network issues, Troubleshoot the network issues. Router R1 connects the main office to internet, and routers R2 and R3 are internal routers NAT is enabled on Router R1. The routing protocol that is enable between routers R1, R2, and R3 is RIPv2. R1 sends default route into RIPv2 for internal routers to forward internet traffic to R1. Server1 and Server2 are placed in VLAN 100 and 200 respectively, and dare still running router on stick configuration with router R2.
- 185. You have console access on R1, R2, R3, and L2SW1 devices. Use only show commands to troubleshoot the issues. -- More configuration please check the PDF file --- Examine R2 configuration,the traffic that is destined to R3 LAN network sourced from Router R2 is forwarded to R1 instead R3. What could be an issue? A. RIPv2 enabled on R3, but R3 LAN network that is not advertised into RIPv2 domain. B. RIPv2 routing updates are suppressed between R2 and R3 using passive interface feature. C. RIPv2 not enabled on R3. D. No issue that is identified; this behavior is normal since default route propagated into RIPv2 domain by
- 186. Router R1. Correct Answer: C Section: (none) Explanation Explanation/Reference: Explanation: First we should check the routing table of R2 with the “show ip route” command. In this table we cannot find the subnet “10.10.12.0/24” (R3 LAN network) so R2 will use the default route advertised from R1 (with the command “default-information originate” on R1) to reach unknown destination, in this case subnet 10.10.12.0/24 -> R2 will send traffic to 10.10.12.0/24 to R1. Next we need to find out why R3 did not advertise this subnet to R2. A quick check with the “show running- config” on R3 we will see that R3 was not configured with RIP ( no “router rip” section). Therefore we can conclude RIPv2 was not enabled on R3. QUESTION 317 Hotspot Question - RIPv2 Troubleshooting I
- 187. Scenario: You work for a company that provides managed network services, and of your real estate clients running a small office is experiencing network issues, Troubleshoot the network issues. Router R1 connects the main office to internet, and routers R2 and R3 are internal routers NAT is enabled on Router R1. The routing protocol that is enable between routers R1, R2, and R3 is RIPv2. R1 sends default route into RIPv2 for internal routers to forward internet traffic to R1. Server1 and Server2 are placed in VLAN 100 and 200 respectively, and dare still running router on stick configuration with router R2. You have console access on R1, R2, R3, and L2SW1 devices. Use only show commands to troubleshoot the issues. -- More configuration please check the PDF file --- What is the correct statement below after examining the R1 routing table? A. Traffic that is destined to 10.10.10.0/24 from R1 LAN network uses static route instead RIPv2 Because the static route AD that is configured is less than the AD of RIPv2 B. Traffic that is destined to 10.10.10.0/24 from R1 LAN network uses RIPv2 instead static route Because the static route AD that is configured is higher than the AD of RIPv2 C. Traffic that is destined to 10.10.10.0/24 from R1 LAN network uses static route instead RIPv2 But the traffic is forwarded to the ISP instead of the internal network.
- 188. D. Traffic that is destined to 10.10.10.0/24 from R1 LAN network uses RIPv2 instead static route Because the static route AD that is configured is 255 Correct Answer: B Section: (none) Explanation Explanation/Reference: Explanation: Surely we have to use the “show ip route” command to check the R1 routing table. As we see here, 10.10.10/24 is learned from RIP. Notice that although there is a static route on R1 to this destination (you can check with the “show running-config” on R1 to see the line “ip route 10.10.10.0 255.255.255.0 172.16.14.2 200”), this static route is not installed to the routing table because it is not the best path because the Administrative Distance (AD) of this static route is 200 while the AD of RIP is 120 -> R1 chose the path with lowest AD so it chose path advertised via RIP. QUESTION 318 Hotspot Question - RIPv2 Troubleshooting II Scenario: You are a junior network engineer for a financial company, and the main office network is experiencing network issues. Troubleshoot the network issues. Router R1 connects the main office to the internet, and routers R2 and R3 are internal routers.
- 189. NAT is enabled on router R1. The routing protocol that is enabled between routers R1, R2 and R3 is RIPv2. R1 sends the default route into RIPv2 for the internal routers to forward internet traffic to R1. You have console access on R1, R2 and R3 devices. Use only show commands to troubleshoot the issues.
- 196. Why applications that are installed on PC's in R2 LAN network 10.100.20.0/24 are unable to communicate with Server1? A. A standard ACL statement that is configured on R1 is blocking the traffic sourced from Server1 network. B. A standard ACL statement that is configured on R2 is blocking the traffic sourced from Server1 network. C. A standard ACL statement that is configured on R2 is blocking the traffic sourced from R2 LAN network. D. A standard ACL statement that is configured on R1 is blocking the traffic sourced from R2 LAM network Correct Answer: B Section: (none) Explanation Explanation/Reference: Explanation: Check the below now:
- 197. QUESTION 319 Hotspot Question - RIPv2 Troubleshooting II Scenario: You are a junior network engineer for a financial company, and the main office network is experiencing network issues. Troubleshoot the network issues. Router R1 connects the main office to the internet, and routers R2 and R3 are internal routers. NAT is enabled on router R1. The routing protocol that is enabled between routers R1, R2 and R3 is RIPv2. R1 sends the default route into RIPv2 for the internal routers to forward internet traffic to R1. You have console access on R1, R2 and R3 devices. Use only show commands to troubleshoot the issues.
- 205. Users complain that they are unable to reach internet sites. You are troubleshooting internet connectivity problem at main office. Which statement correctly identifies the problem on Router R1? A. Interesting traffic for NAT ACL is incorrectly configured. B. NAT configurations on the interfaces are incorrectly configured C. NAT translation statement incorrectly configured. D. Only static NAT translation configured for the server, missing Dynamic NAT or Dynamic NAT overloading for internal networks. Correct Answer: B Section: (none) Explanation Explanation/Reference: QUESTION 320 Hotspot Question - RIPv2 Troubleshooting II Scenario: You are a junior network engineer for a financial company, and the main office network is experiencing network issues. Troubleshoot the network issues. Router R1 connects the main office to the internet, and routers R2 and R3 are internal routers. NAT is enabled on router R1. The routing protocol that is enabled between routers R1, R2 and R3 is RIPv2. R1 sends the default route into RIPv2 for the internal routers to forward internet traffic to R1. You have console access on R1, R2 and R3 devices. Use only show commands to troubleshoot the issues.
- 213. R1 router clock is synchronized with ISP router R2 is supposed to receive NTP updates from R1. But you observe that R2 clock is not synchronized with R1. What is the reason R2 is not receiving NTP updates from R1? A. The IP address that is used in the NTP configuration on R2 router is incorrect. B. The NTP server command not configured on R2 router. C. R2 router Ethernet interface that is connected to R1 is placed in shutdown condition. D. R1 router Ethernet interface that is connected to R2 is placed in shutdown condition. Correct Answer: A Section: (none) Explanation Explanation/Reference: Explanation: Check the below configuration for this
- 214. QUESTION 321 Hotspot Question - RIPv2 Troubleshooting II Scenario: You are a junior network engineer for a financial company, and the main office network is experiencing network issues. Troubleshoot the network issues. Router R1 connects the main office to the internet, and routers R2 and R3 are internal routers. NAT is enabled on router R1. The routing protocol that is enabled between routers R1, R2 and R3 is RIPv2. R1 sends the default route into RIPv2 for the internal routers to forward internet traffic to R1. You have console access on R1, R2 and R3 devices. Use only show commands to troubleshoot the issues.
- 222. Examine the DHCP configuration between R2 and R3; R2 is configured as the DHCP server and R3 as the client. What is the reason R3 is not receiving the IP address via DHCP? A. On R2. The network statement In the DHCP pool configuration is incorrectly configured. B. On R3. DHCP is not enabled on the interface that is connected to R2. C. On R2, the interface that is connected to R3 is in shutdown condition. D. On R3, the interface that is connected to R2 is in shutdown condition. Correct Answer: A Section: (none) Explanation Explanation/Reference: Explanation: Please check the below:
- 223. QUESTION 322 Which feature automatically disables CEF when it is enabled? A. RIB B. ACL logging C. multicast D. IP redirects Correct Answer: B Section: (none) Explanation Explanation/Reference: Explanation: ACL Logging means to use the "log" or "log-input" parameters at the end of the ACL statements. For example: "access-list 100 deny icmp any any echo reply log-input". In either situation, remember that using either of these two parameters disables CEF switching, which seriously impacts the performance of the router. QUESTION 323 Which NAT term is defined as a group of addresses available for NAT use? A. one-way nat B. static nat C. dynamic nat D. nat pool Correct Answer: D Section: (none) Explanation QUESTION 324 Which statement about NTP is true? A. each device is enabled as server by default B. the default authentication key number is 1 C. the default stratum number is 5 D. the default source of an ntp message is the interface connected to the next-hop for server peer address Correct Answer: D Section: (none) Explanation QUESTION 325 Which information is used to install the best route to a destination in IP routing table? A. the tunnel ID B. the interface number C. the prefix length D. the autonoums system Correct Answer: C Section: (none) Explanation
- 224. QUESTION 326 If a router has 3 hosts connected in one port and two other hosts connected in another port, how may broadcast domains are present on the router? A. 5 B. 2 C. 3 D. 4 Correct Answer: B Section: (none) Explanation QUESTION 327 Which feature facilitate the tagging of a specific VLAN? A. Routing B. Hairpinning C. Encapsulation D. Switching Correct Answer: C Section: (none) Explanation QUESTION 328 What does split horizon prevent? A. routing loops, link state B. routing loops, distance vector C. switching loops, STP D. switching loops, VTP Correct Answer: B Section: (none) Explanation QUESTION 329 Which value to use in HSRP protocol election process ? A. interface B. virtual IP address C. priority D. router ID Correct Answer: C Section: (none) Explanation QUESTION 330 Which of the following is needed to be enable back the role of active in HSRP?
- 225. A. prempt B. priority Correct Answer: A Section: (none) Explanation QUESTION 331 Which command is used to show the interface status of a router? A. show interface status B. show ip interface brief C. show ip route D. show interface Correct Answer: B Section: (none) Explanation QUESTION 332 Which of the following privilege level is the most secured? A. Level 0 B. Level 1 C. Level 15 D. Level 16 Correct Answer: C Section: (none) Explanation QUESTION 333 Which IPV6 feature is supported in IPV4 but is not commonly used? A. unicast B. multicast C. anycast D. broadcast Correct Answer: C Section: (none) Explanation QUESTION 334 Which range represents the standard access list? A. 99 B. 150 C. 299 D. 2000 Correct Answer: A Section: (none)
- 226. Explanation QUESTION 335 What to do when the router password was forgotten? A. use default password cisco to reset B. access router physically C. use ssl/vpn D. Type confreg 0x2142 at the rommon 1 Correct Answer: D Section: (none) Explanation QUESTION 336 What 8-bit field exists in IP packet for QoS? A. Tos Field B. DSCP C. IP Precedence D. Cos Correct Answer: A Section: (none) Explanation QUESTION 337 What feature uses a random time to re-sent a frame? A. CSMA/CA B. CSMA/CD Correct Answer: B Section: (none) Explanation QUESTION 338 Which mode is compatible with Trunk, Access, and desirable ports? A. Trunk Ports B. Access Ports C. Dynamic Auto D. Dynamic Desirable Correct Answer: C Section: (none) Explanation QUESTION 339 If you configure syslog messages without specifying the logging trap level, which log messages will the router send? A. 0-4
- 227. B. 0-5 C. 0-6 D. 0-2 E. 0-1 Correct Answer: C Section: (none) Explanation QUESTION 340 Which of the following are found in a TCP header, but not in a UDP header? (Choose three.) A. sequence number B. acknowledgment number C. source port D. destination port E. window size F. checksum Correct Answer: ABE Section: (none) Explanation QUESTION 341 When you power up a Cisco router, in what memory is the start-up configuration normally stored in? A. RAM B. ROM C. FLASH D. NVRAM Correct Answer: D Section: (none) Explanation QUESTION 342 Which transport layer protocol is best suited for the transport of VoIP data? A. RIP B. UDP C. TCP D. OSPF E. HTTP Correct Answer: B Section: (none) Explanation QUESTION 343 An administrator issues the show ip interface s0/0 command and the output displays that interface Serial0/0 is up, line protocol is up. What does "line protocol is up" specifically indicate about the interface?
- 228. A. The cable is attached properly. B. CDP has discovered the connected device. C. Keepalives are being received on the interface. D. A carrier detect signal has been received from the connected device. E. IP is correctly configured on the interface. Correct Answer: C Section: (none) Explanation QUESTION 344 Refer to the exhibit. Which statement is correct regarding the configuration shown? A. This will not work as the subnet mask on serial interfaces must be /30. B. What is shown as being configured would be considered a default route. C. This configuration creates a bidirectional path between RouterA and RouterB. D. The command ip route 172.16.1.0 255.255.255.0 s0/0/0 would provide similar routing functionality. Correct Answer: D Section: (none) Explanation Explanation/Reference: QUESTION 345 How can an administrator determine if a router has been configured when it is first powered up? A. A configured router prompts for a password. B. A configured router goes to the privileged mode prompt. C. An unconfigured router goes into the setup dialog. D. An unconfigured router goes to the enable mode prompt. Correct Answer: C Section: (none) Explanation
- 229. QUESTION 346 Refer to the exhibit. Which statement is correct regarding the results shown for the show interface s0/0/0 command? A. The subnet mask for this interface is 255.255.255.248. B. The subnet mask for this interface is 255.255.255.252. C. The IP address that is configured on s0/0/0 is a public address. D. This interface can be enabled by issuing a no shutdown command. E. The default encapsulation protocol for a Cisco serial interface is PPP. Correct Answer: D Section: (none) Explanation Explanation/Reference: QUESTION 347 Which of the following commands enables a network administrator to verify the application layer connectivity between source and destination? A. ping B. telnet C. traceroute D. verify E. trace Correct Answer: B Section: (none) Explanation QUESTION 348 An administrator previously changed the encapsulation on a synchronous serial line and saved the
- 230. configuration. Now the administrator wants to restore the encapsulation back to the default. What action can the administrator do to return the interface back to its default encapsulation? A. Change the encapsulation to ARPA. B. Configure the interface for HDLC encapsulation. C. Reboot the router and allow it to reload the configuration. D. Issue the shutdown then no shutdown commands to reset the encapsulation on the interface. E. Remove the cable and plug it back in to allow the router to autonegotiate encapsulation settings. Correct Answer: B Section: (none) Explanation QUESTION 349 WAN data link encapsulation types include which of the following? (Choose two.) A. T1 B. Frame Relay C. DSL D. PPP E. ISDN Correct Answer: BD Section: (none) Explanation QUESTION 350 Regarding the extended ping command, which of the statements below are true? (Choose three) A. The extended ping command is supported from user EXEC mode. B. The extended ping command is available from privileged EXEC mode. C. With the extended ping command you can specify the TCP and UDP port to be pinged. D. With the extended ping command you can specify the timeout value. E. With the extended ping command you can specify the datagram size. Correct Answer: BDE Section: (none) Explanation QUESTION 351 Which sequence of actions will allow telneting from a user's PC to a router using TCP/IP? A. Connect the PC's COM port to the router's console port using a straight-through cable. B. Connect the PC's COM port to the router's console port using a crossover cable. C. Connect the PC's COM port to the router's Ethernet port using a straight-through cable. D. Connect the PC's Ethernet port to the router's Ethernet port using a crossover cable. E. Connect the PC's Ethernet port to the router's Ethernet port using a rollover cable. F. Connect the PC's Ethernet port to the router's Ethernet port using a straight-through cable. Correct Answer: D Section: (none) Explanation Explanation/Reference:
- 231. QUESTION 352 Which Layer 1 devices can be used to enlarge the area covered by a single LAN segment? (Choose two.) A. switch B. router C. NIC D. hub E. repeater F. RJ-45 transceiver Correct Answer: DE Section: (none) Explanation QUESTION 353 When troubleshooting a LAN interface operating in full duplex mode, which error condition can be immediately ruled out? A. giants B. no buffers C. collisions D. ignored E. dribble condition Correct Answer: C Section: (none) Explanation QUESTION 354 When you use the ping command to send ICMP messages across a network, what's the most common request/reply pair you'll see? (Select one answer choice) A. Echo request and Echo reply B. ICMP hold and ICMP send C. ICMP request and ICMP reply D. Echo off and Echo on Correct Answer: A Section: (none) Explanation QUESTION 355 Which of the following statements describe the network shown in the graphic? (Choose two.)
- 232. A. There are two broadcast domains in the network. B. There are four broadcast domains in the network. C. There are six broadcast domains in the network. D. There are four collision domains in the network. E. There are five collision domains in the network. F. There are seven collision domains in the network. Correct Answer: A Section: (none) Explanation Explanation/Reference: QUESTION 356 Which protocol provides best-effort delivery of user data in a network? A. TCP B. MAC C. IP D. ARP E. SMTP Correct Answer: C Section: (none) Explanation QUESTION 357 If NVRAM lacks boot system commands, where does the router look for the Cisco IOS by default? A. ROM B. RAM C. Flash D. bootstrap E. startup-config Correct Answer: C Section: (none) Explanation
- 233. QUESTION 358 Assuming a subnet mask of 255.255.248.0, three of the following addresses are valid host addresses. Which are these addresses? (Choose three.) A. 172.16.9.0 B. 172.16.8.0 C. 172.16.31.0 D. 172.16.20.0 Correct Answer: ACD Section: (none) Explanation QUESTION 359 Which cloud service is typically used to provide DNS and DHCP services to an enterprise? A. IaaS B. DaaS C. SaaS D. PaaS Correct Answer: C Section: (none) Explanation QUESTION 360 Which two pieces of information can be shared with LLDP TLVs? (Choose two) A. device management address. B. device type C. spanning-tree topology D. routing configuration E. access-list configuration Correct Answer: AB Section: (none) Explanation Explanation/Reference: Explanation: TLV advertises a single type of information such as its device ID, type or management addresses. QUESTION 361 Which symptom most commonly indicates that two connecting interfaces are configured with a duplex mismatch? A. the spanning-tree process shutting down B. collisions on the interface C. an interface with a down/down status D. an interface with an up/down status Correct Answer: B Section: (none) Explanation
- 234. QUESTION 362 Which statement about upgrading a cisco ios device with TFTP is True? A. The Cisco IOS device must be on the same lan as the TFTP server B. The operation is performed in passive mode C. The operation is performed in an unencrypted format D. The operation is performed in active mode Correct Answer: A Section: (none) Explanation QUESTION 363 Which two statements about UDP are true? (Choose two) A. It can transmit data at a rate higher than the path capacity B. It uses a three-way handshake to ensure that traffic is transmated properly C. It guarantees packet delivery D. it includes protection against duplicate packets E. it can be used for multicast and broadcast traffic Correct Answer: AE Section: (none) Explanation QUESTION 364 Which two types of information are held in the mac address table ? A. destination ip addresses B. protocols C. port numbers D. mac address E. source ip address Correct Answer: CD Section: (none) Explanation QUESTION 365 Refer to the exhibit, what is the metric for the router from R1 to 192.168.10.1 ?
- 235. A. 2 B. 90 C. 110 D. 52778 Correct Answer: D Section: (none) Explanation Explanation/Reference: QUESTION 366 Which command can you enter in a network switch configuration so that learned mac addresses are saved in configuration as they connect ? A. Switch(confg-if)#Switch port-security B. Switch(confg-if)#Switch port-security Mac-address sticky C. Switch(confg-if)#Switch port-security maximum 10 D. Switch(confg-if)#Switch mode access Correct Answer: B Section: (none) Explanation QUESTION 367
- 236. Which two security appliances will you use in a network? (Choose two.) A. ATM B. IDS C. IOS D. IOX E. IPS F. SDM Correct Answer: BE Section: (none) Explanation QUESTION 368 Which NTP type designates a router without an external referee clock as an authoritative time source ? A. Client B. Server C. peer D. master Correct Answer: D Section: (none) Explanation QUESTION 369 Which command can you enter to re enable cisco discovery protocol on a local router after it has been disabled ? A. Router (config)# cdp run B. Router (config-if)# cdp run C. Router (config)# cdp enable D. Router (config-if)# cdp enable Correct Answer: A Section: (none) Explanation QUESTION 370 Which three options are switchport configuration that can always avoid duplex mismatch errors between two switches? (Choose three.) A. Set both sides of the connection to half duplex. B. Set one side of the connection to auto-negotiate and the other side to full duplex. C. Set both sides of the connection to auto-negotiate. D. Set one side of the connection to auto-negotiate and the other side to half duplex. E. Set one side of the connection to full ruplex and the other side to half duplex. F. Set both sides of the connection to full duplex. Correct Answer: ACF Section: (none) Explanation
- 237. QUESTION 371 In which CLI configuration mode can you configure the hostname of a device? A. line mode B. interface mode C. global mode D. router mode Correct Answer: C Section: (none) Explanation QUESTION 372 What are the two minimum required components of a DHCP binding? (Choose two.) A. a DHCP pool B. an exclusion list C. a hardware address D. an IP address E. an ip-helper statement Correct Answer: CD Section: (none) Explanation QUESTION 373 Which Two options are features of the extended ping command ? A. it can send packets from a specified interface or ip address B. it can resolve the destination host name C. it can ping multiple hosts at the same time D. it can count the number of hops to the remote host E. it can send a specified number of packets Correct Answer: AE Section: (none) Explanation QUESTION 374 For which two protocols can PortFast alleviate potential host startup issues? (Choose two.) A. DHCP B. DNS C. OSPF D. RIP E. CDP Correct Answer: AE Section: (none) Explanation QUESTION 375 Which major ipv6 address type is supported in ipv4 but rarely used ?
- 238. A. Broadcast B. multicast C. unicast D. anycast Correct Answer: D Section: (none) Explanation QUESTION 376 Which two steps must you perform to enable router-on-a-stick on a switch? (Choose two.) A. Configure an IP route to the VLAN destination network. B. Connect the Router to a trunk port. C. Configure full duplex. D. Configure the subinterface number exactly the same as the matching VLAN. E. Assign the access port to a VLAN. Correct Answer: BC Section: (none) Explanation QUESTION 377 Which two statements about syslog logging are true? (Choose two.) A. Messages are stored external to the device. B. The size of the log file is dependent on the resources of the device. C. Syslog logging is disabled by default. D. Messages can be erased when the device reboots. E. Messages are stored in the internal memory of the device. Correct Answer: AD Section: (none) Explanation QUESTION 378 Which address block identifies all link-local address A. fc00::/7 B. fc00::/8 C. fe80::/10 Correct Answer: C Section: (none) Explanation QUESTION 379 Which two options are fields in an ethernet frame ? (Choose two) A. destination ip address B. source ip address C. type
- 239. D. frame check sequence E. header Correct Answer: AB Section: (none) Explanation QUESTION 380 Refer to Exhibit. If Computer A is sending traffic to computer B, which option is the source ip address when a packet leaves R1 on interface F0/1? A. IP address of the R2 interface F0/1 B. Ip address of computer B C. Ip address of R1 interface F0/1 D. Ip address of Computer A Correct Answer: D Section: (none) Explanation Explanation/Reference: QUESTION 381 Refer to the exhibit. After you apply the given configuration to arouter, the DHCP clients behind the device connot communicate with hosts outside of their subnet. Which action is most likely to correct the problem? A. Configure the dns server on the same subnet as the clients B. Activate the dhcp pool
- 240. C. Correct the subnet mask D. configure the default gateway Correct Answer: D Section: (none) Explanation Explanation/Reference: QUESTION 382 For which two reasons was RFC 1918 address space define (Choose two) A. to preserve public IPv4 address space B. to reduce the occurrence of overlapping IP addresses C. to preserve public IPv6 address space D. reduce the size of ISP routing tables E. to support the NAT protocol Correct Answer: DE Section: (none) Explanation QUESTION 383 In which two circumstances are private IPv4 addresses appropriate? (Choose two) A. on internal hosts that stream data solely to external resources B. on hosts that communicates only with other internal hosts C. on the public-facing interface of a firewall D. on hosts that require minimal access to external resources E. to allow hosts inside an enterprise to communicate in both directions with hosts outside the enterprise Correct Answer: BD Section: (none) Explanation QUESTION 384 Which command can you enter to re-enable Cisco Discovery Protocol on a local router after it has been disabled? A. Router(config)# cdp run B. Router(config-if)# cdp enable C. Router(config)# cdp enable D. Router(config-if)# cdp run Correct Answer: A Section: (none) Explanation Explanation/Reference: QUESTION 385 Which type of routing protocol operates by using first information from each device peers? A. link-state protocols
- 241. B. distance-vector protocols C. path-vector protocols D. exterior gateway protocols Correct Answer: A Section: (none) Explanation QUESTION 386 Refer to the exhibit. You have determined that computer A cannot ping computer B. Which reason for the problem is most likely true? A. The computer A subnet mask is incorrect. B. The computer B subnet mask is incorrect. C. The computer B default gateway address is incorrect. D. The computer A default gateway address is incorrect. Correct Answer: D Section: (none) Explanation Explanation/Reference: QUESTION 387 Which two statements about access points are true? (Choose Two) A. They can provide access within enterprises and to the public. B. in Most cases, they are physically connected to other network devices to provide network connectivity. C. They can proterct a network from internal and external threats. D. Most access points provide Wi-Fi and Bluetooth connectivity. E. They must be hardwired to a modem. Correct Answer: BD Section: (none) Explanation
- 242. QUESTION 388 When is a routing table entry identified as directly connected? A. when the local router is in use as the network default gateway B. when the network resides on a remote router that is physically connected to the local router C. when an interface on the route is configure with an ip address and enabled D. when the route is statically assigned to reach a specific network Correct Answer: C Section: (none) Explanation QUESTION 389 Which type of cable must you use to connect two device with mdi interfaces ? A. rolled B. crosseover C. crossed D. straight through Correct Answer: B Section: (none) Explanation QUESTION 390 Which statements is true about Router on Stick? A. When a router have multiple subnets on a single physical link. B. When a router have single subnet on multiple physical links. C. When a router have multiple interface on single physical links. D. When a router have single interface on multiple physical links Correct Answer: A Section: (none) Explanation QUESTION 391 Which two options are the best reasons to use an ipv4 private ip space ? A. to manage routing overhead B. to implement nat C. to connect applications D. to enable intra-enterprise communication E. to conserve global address space Correct Answer: DE Section: (none) Explanation QUESTION 392 Which two options are benefits of dhcp snooping ? A. it prevents dhcp reservations
- 243. B. it simplifies the process of adding DHCP Servers to the network C. it prevents the deployment of rogue DHCP Servers D. it prevents static reservations E. it Tracks the location of hosts in the network Correct Answer: CE Section: (none) Explanation QUESTION 393 Which three options are fields in a basic ethernet data frame? A. preamble B. time to live C. version D. header checksum E. length type F. frame check sequence Correct Answer: AEF Section: (none) Explanation QUESTION 394 Which two statements about the extended traceroute command are true? (Choose two.) A. It can be repeated automatically at a specified interval. B. It can validate the reply data. C. It can use a specified TTL value. D. It can send packets from a specified interface or IP address. E. It can use a specified ToS. Correct Answer: CD Section: (none) Explanation QUESTION 395 Which functionality does split horizon provide ? A. it Prevents routing loops in distance vector protocols B. it Prevents switching loops in distance vector protocols C. it Prevents switching loops in link-state protocols D. it Prevents routing loops in link-state protocols Correct Answer: A Section: (none) Explanation QUESTION 396 Which two statements about RIPv2 are true? (Choose two ) A. It must be manually enabled after RIP is configured as the routing protocol B. It uses multicast address 224.0.0.2 to share routing information between peers
- 244. C. its default administrative distances 120 D. It is a link-state routing protocol E. It is an EGP routing protocol Correct Answer: AC Section: (none) Explanation QUESTION 397 Which command can be used from a router to verify the Layer 3 path to a host? A. tracert address B. traceroute address C. telnet address D. ssh address Correct Answer: B Section: (none) Explanation QUESTION 398 Which statement about Cisco Discovery Protocol is true? A. It is a Cisco-proprietary protocol. B. It runs on the network layer. C. It can discover information from routers, firewalls, and switches. D. It runs on the physical layer and the data link layer. Correct Answer: A Section: (none) Explanation QUESTION 399 Under which circumstance is a router on a stick most appropriate? A. When the router must route a single across multiple physical links. B. When the router must route multiple subnets across multiple physical links. C. When the router must route a single across single physical links. D. When the router must route multiple subnets across single physical links. Correct Answer: D Section: (none) Explanation QUESTION 400 Dhcp client in the back can not communicate with hosts in the outside of their subnet? ***ip dhcp pool my pool****** ***network 192.168.10.0/27*** ***domain name cisco.com*** ****name server some ip*** A. need to activate dhcp pool B. need to configure default gateway
- 245. C. other option D. other option Correct Answer: B Section: (none) Explanation QUESTION 401 What command can you enter to configure the switch as an authoritative ntp server with site id : 15122473? A. Switch(config)#ntp master 3 B. Switch(config)#ntp peer IP 193.168.2.2 C. Switch(config)#ntp server IP 193.168.22 D. Switch(config)#ntp source IP 193.168.2.2 Correct Answer: A Section: (none) Explanation QUESTION 402 Router R1 has a static router that is configured to a destination network. A directly connected inference is configured with an ip address in the same destination network. Which statement about R1 is true ? A. It refuses to advertise the dynamic route to other neighbors B. It sends a withdrawal signal to the neighboring router C. It disables the routing protocol D. It prefers the static route Correct Answer: D Section: (none) Explanation QUESTION 403 To enable router on a stick on a router subinterface, which two steps must you perform? choose two A. configure full duplex and speed B. configure a default to route traffic between subinterfaces C. configure the subinterface with an ip address D. configure encapsulation dot1q E. configure an ip route to the vlan destination network Correct Answer: CD Section: (none) Explanation QUESTION 404 Which command can you enter to determine the addresses that have been assigned on a DHCP Server? A. Show ip DHCP database. B. Show ip DHCP pool. C. Show ip DHCP binding. D. Show ip DHCP server statistic.
- 246. Correct Answer: C Section: (none) Explanation QUESTION 405 Which statement about recovering a password on a cisco router is true ? A. it requires physical access to the router B. the default reset password is cisco C. a factory reset is required if you forget the password D. it requires a secure SSL/VPN connection Correct Answer: A Section: (none) Explanation QUESTION 406 While troubleshooting a DCHP client that is behaving erratically, you discover that the client has been assigned the same IP address as a printer that is a staticIP address. Which option is the best way to resolve the problem? A. Configurea static route to the client. B. Assign the client the same IP address as the router. C. Move the client to another IP subnet D. Move the printer to another IP subnet. E. Reservethe printer IP address. Correct Answer: E Section: (none) Explanation QUESTION 407 Which symptom can cause duplex mismatch problem? A. no earner B. collisions on interface C. giants D. CRC errors Correct Answer: B Section: (none) Explanation QUESTION 408 Which type of routing protocol operates by exchanging the entire routing information ? A. distance vector protocols B. link state protocols C. path vector protocols D. exterior gateway protocols Correct Answer: A Section: (none)
- 247. Explanation QUESTION 409 Which port security violation mode allows traffic from valid mac address to pass but block traffic from invalid mac address? A. protect B. shutdown C. shutdown vlan D. restrict Correct Answer: A Section: (none) Explanation QUESTION 410 Which IPsec security protocol should be used when confidentiality is required? A. MD5 B. PSK C. AH D. ESP Correct Answer: D Section: (none) Explanation QUESTION 411 Which definition of a host route is true? A. A route that is manually configured B. A route used when a destination route is missing. C. A route to the exact /32 destination address D. Dynamic route learned from the server. Correct Answer: B Section: (none) Explanation Explanation/Reference: QUESTION 412 which statement about upgrading a cisco IOS device with TFTP server ? A. the operation is performed in active mode B. the operation is performed in unencrypted format C. the operation is performed in passive mode D. the cisco IOS device must be on the same LAN as the TFTP server Correct Answer: D Section: (none) Explanation
- 248. QUESTION 413 Which statement about DHCP snooping is true? A. it blocks traffic from DHCP servers on untrusted interfaces. B. it can be configured on switches and routers. C. it allows packets from untrusted ports if their source MAC address is found in the binding table. D. it uses DHCPDiscover packets to identify DHCP servers. Correct Answer: A Section: (none) Explanation QUESTION 414 Which three commands are required to enable NTP authentication on a Cisco router? (Choose three) A. ntp peer B. ntp max-associations C. ntp authenticate D. ntp trusted-key E. ntp authentication-key F. ntp refclock Correct Answer: CDE Section: (none) Explanation QUESTION 415 Which IPv6 routing protocol uses multicast group FF02::9 to send updates? A. static B. RIPng C. OSPFv3 D. IS-IS for IPv6 Correct Answer: B Section: (none) Explanation QUESTION 416 Which three statements about IPv6 address fd14:920b:f83d:4079::/64 are true? (Choose three) A. The subnet ID is 14920bf83d B. The subnet ID is 4079 C. The global ID is 14920bf83d D. The address is a link-local address E. The global ID is 4079 F. The address is a unique local address Correct Answer: BCF Section: (none) Explanation QUESTION 417
- 249. Which three statements about DWDM are true? (Choose three) A. It allows a single strand of fiber to support bidirectional communications B. It is used for long-distance and submarine cable systems C. It can multiplex up to 256 channels on a single fiber D. It supports both the SDH and SONET standards E. Each channel can carry up to a 1-Gbps signal F. It supports simplex communications over multiple strands of fiber Correct Answer: CDE Section: (none) Explanation QUESTION 418 Which tunneling mechanism embeds an IPv4 address within an IPv6 address? A. Teredo B. 6to4 C. 4to6 D. GRE E. ISATAP Correct Answer: B Section: (none) Explanation QUESTION 419 Which protocol does ipv6 use to discover other ipv6 nodes on the same segment? A. CLNS B. TCPv6 C. NHRP D. NDP E. ARP Correct Answer: D Section: (none) Explanation QUESTION 420 What is the most efficient subnet mask for a point to point ipv6 connection? A. /127 B. /128 C. /64 D. /48 E. /32 Correct Answer: A Section: (none) Explanation QUESTION 421
- 250. Refer to the exhibit. After you apply the given configuration to R1, you determine that it is failing to advertise the 172.16.10.32/27 network .Which action most likely to correct the problem? A. Enable passive interface B. Enable RIPv2 C. Enable manual summarization D. Enable autosummarization. Correct Answer: B Section: (none) Explanation Explanation/Reference: QUESTION 422 Which type of secure MAC address must be configured manually? A. dynamic B. bia C. static D. sticky Correct Answer: C Section: (none) Explanation QUESTION 423 Which two options are fields in an Ethernet frame? (Choose two) A. frame check sequence B. header C. source IP address D. destination IP address E. type Correct Answer: CD Section: (none) Explanation
- 251. Explanation/Reference: QUESTION 424 Where does a switch maintain DHCP snooping information ? A. in the MAC address table B. in the CAM table C. in the DHCP binding database D. in the VLAN database Correct Answer: C Section: (none) Explanation QUESTION 425 To enable router on a router subinterface, which two steps must you perform?(choose two) A. Configure full duplex and speed B. configure the subinterface with an IP address C. Configure an IP route to the VLAN destination network D. Configure a default to route traffic between subinterface E. Configure encapsulation dot1q Correct Answer: BE Section: (none) Explanation QUESTION 426 Which two statements about IPv6 address 2002:ab10:beef::/48 are true?(choose two) A. The embedded IPv4 address can be globally routed. B. It is used for an ISATAP tunnel C. The embedded IPv4 address is an RFC 1918 address D. The MAC address 20:02:b0:10:be:ef is embedded into the IPv6 address E. It is used for a 6to4 tunnel Correct Answer: AE Section: (none) Explanation QUESTION 427 If a router has four interfaces and each interface is connected to four switches, how many broadcast domains are present on the router? A. 1 B. 2 C. 4 D. 8 Correct Answer: C Section: (none) Explanation
- 252. QUESTION 428 What are three parts of an IPv6 global unicast address? (Choose three.) A. an interface ID that is used to identify the local host on the network B. an interface ID that is used to identify the local network for a particular host. C. a subnet ID that is used to identify networks inside of the local enterprise site D. a global routing prefix that is used to identify the network portion of the address that has been provided by an ISP E. a global routing prefix that is used to identify the portion of the network address provided by a local administrator Correct Answer: ACD Section: (none) Explanation QUESTION 429 What is true about Cisco Discovery Protocol? A. it discovers the routers, switches and gateways. B. it is network layer protocol C. it is physical and data link layer protocol D. it is proprietary protocol Correct Answer: D Section: (none) Explanation QUESTION 430 What layer of the OSI Model is included in TCP/IP Model's INTERNET layer? A. Application B. Session C. Data Link D. Presentation E. Network Correct Answer: E Section: (none) Explanation QUESTION 431 What are types of IPv6 static routes? (Choose Three.) A. Recursive routes B. Directly connected routes C. Fully specified routes D. Advertised routes E. Virtual links F. Redistributed routes Correct Answer: ABC Section: (none) Explanation
- 253. Explanation/Reference: QUESTION 432 How to configure RIPv2? (Choose Two.) A. Enable RIP B. Connect RIP to WAN interface C. Enable no auto-summary D. Enable authentication Correct Answer: AC Section: (none) Explanation QUESTION 433 What feature uses a random time to re-sent a frame? A. CSMA/CA B. CSMA/CD Correct Answer: B Section: (none) Explanation QUESTION 434 If you configure syslog messages without specifying the logging trap level, which log messages will the router send? A. 0-4 B. 0-5 C. 0-6 D. 0-2 E. 0-1 Correct Answer: C Section: (none) Explanation QUESTION 435 If a router has 3 hosts connected in one port and two other hosts connected in another port, how may broadcast domains are present on the router? A. 5 B. 2 C. 3 D. 4 Correct Answer: B Section: (none) Explanation QUESTION 436 Which command is used to show the interface status of a router?
- 254. A. show interface status B. show ip interface brief C. show ip route D. show interface Correct Answer: B Section: (none) Explanation QUESTION 437 Which of the following privilege level is the most secured? A. Level 0 B. Level 1 C. Level 15 D. Level 16 Correct Answer: C Section: (none) Explanation QUESTION 438 Which IPV6 feature is supported in IPV4 but is not commonly used? A. unicast B. multicast C. anycast D. broadcast Correct Answer: C Section: (none) Explanation QUESTION 439 Which range represents the standard access list? A. 99 B. 150 C. 299 D. 2000 Correct Answer: A Section: (none) Explanation QUESTION 440 What to do when the router password was forgotten? A. use default password cisco to reset B. access router physically C. use ssl/vpn D. Type confreg 0x2142 at the rommon 1
- 255. Correct Answer: D Section: (none) Explanation QUESTION 441 Which definition of default route is true? A. A route that is manually configured. B. A route used when a destination route is missing. C. A route to the exact /32 destination address D. Dynamic route learned from the server. Correct Answer: B Section: (none) Explanation QUESTION 442 Which value must the device send as its username when using CHAP to authenticate with the remote peer site id:17604704 over a PPP link? A. The automatically generated user name B. The local host name C. The user name defined by the administrator D. The host name of the remote device. Correct Answer: B Section: (none) Explanation QUESTION 443 Refer to exhibit. What Administrative distance has route to 192.168.10.1 ?
- 256. A. 1 B. 90 C. 110 D. 120 Correct Answer: B Section: (none) Explanation Explanation/Reference: QUESTION 444 Which statement about IPv6 link-local addresses is true ? A. They must be configured on all IPv6 interface B. They must be globally unique C. They must be manually configured D. They are advertised globally on the network Correct Answer: A Section: (none) Explanation QUESTION 445 Which configuration can be used with PAT to allow multiple inside address to be translated to a single
- 257. outside address ? A. Dynamic Routing B. DNS C. Preempt D. overload Correct Answer: D Section: (none) Explanation QUESTION 446 Which two types of information are held in the MAC address table? (Choose two) A. MAC address B. soure IP address C. destination IP address D. Protocols E. Port numbers Correct Answer: AE Section: (none) Explanation QUESTION 447 Which command can you enter to create a NAT pool of 6 addresses? A. Router(config)#ip nat pool test 175.17.12.69 175.17.12.74 prefix-length 24 B. Router(config)#ip nat pool test 175.17.12.69 175.17.13.74 prefix-length 16 C. Router(config)#ip nat pool test 175.17.12.66 175.17.12.72 prefix-length 8 D. Router(config)#ip nat pool test 175.17.12.69 175.17.12.76 prefix-length 8 Correct Answer: A Section: (none) Explanation QUESTION 448 Which header field is new on IPv6? A. Version B. Hop Limit C. Flow Label D. Traffic Class Correct Answer: C Section: (none) Explanation QUESTION 449 Refer to the exhibit. If R1 sends traffic to 192.168.10.45 the traffic is sent through which interface?
- 258. A. FastEthernet0/1 B. FastEthernet0/0 C. FastEthernet1/0 D. FastEthernet1/1 Correct Answer: A Section: (none) Explanation Explanation/Reference: QUESTION 450 If router R1 knows a static route to a destination network and then learns about the same destination network through a dynamic routing protocol, how does R1 respond? A. It refuses to advertise the dynamic route to other neighbors B. It sends a withdrawal signal to the neighboring router C. It disables the routing protocol D. It prefers the static route Correct Answer: D Section: (none) Explanation QUESTION 451
- 259. Which IEEE mechanism is responsible for the authentication of devices when they attempt to connect to a local network? A. 802.1x B. 802.11 C. 802.2x D. 802.3x Correct Answer: A Section: (none) Explanation QUESTION 452 Which two statements about floating static routes are true? (Choose two) A. They are routes to the exact /32 destination address B. They are used when a route to the destination network is missing C. They have a higher administrative distance than the default static route administrative distance D. They are used as back-up routes when the primary route goes down E. They are dynamic routes that are learned from a server Correct Answer: CD Section: (none) Explanation QUESTION 453 Which networking Technology is currently recognized as the standard for computer networking? A. System network architecture B. Transmission control protocol/Internet protocol C. Open system Interconnect D. Open network architecture Correct Answer: B Section: (none) Explanation QUESTION 454 Which command you enter on a switch to display the ip address associated with connected devices? A. Show cdp neighbors detail B. Show cdp neighbor C. Show cdp interface D. Show cdp traffic Correct Answer: A Section: (none) Explanation QUESTION 455 Which Type of ipv6 unicast ip address is reachable across the internet ? A. Unique Local
- 260. B. Compatible C. Link local D. Globa Correct Answer: D Section: (none) Explanation QUESTION 456 Which NTP command configures the local devices as an NTP reference clock source? A. NTP Peer B. NTP Broadcast C. NTP Master D. NTP Server Correct Answer: C Section: (none) Explanation QUESTION 457 Which value indicate the distance from the ntp authoritative time source? A. priority B. location C. layer D. stratum Correct Answer: D Section: (none) Explanation QUESTION 458 Which NTP type designates a router without an external reefrence clock as an authoritative time source? A. server B. peer C. master D. client Correct Answer: C Section: (none) Explanation QUESTION 459 If you want multiple hosts on a network, where do you configure the setting? A. in the IP protocol B. in the multicast interface C. in the serial interface D. in the global configuration Correct Answer: A
- 261. Section: (none) Explanation QUESTION 460 What will you do if you forgot the password of your router? A. remote connection B. physical connection is needed Correct Answer: B Section: (none) Explanation QUESTION 461 Where information about untrusted hosts are stored? A. CAM table B. Trunk table C. MAC table D. binding database Correct Answer: D Section: (none) Explanation Explanation/Reference: Explanation: Builds and maintains the DHCP snooping binding database, which contains information about untrusted hosts with leased IP addresses. QUESTION 462 In which two situations should you use out-of-band management? A. when a network device fails to forward packets B. when you require ROMMON access C. when management applications need concurrent access to the device D. when you require administrator access from multiple locations E. when the control plane fails to respond Correct Answer: AB Section: (none) Explanation QUESTION 463 What happens when an 802.11a node broadcasts within the range of an 802.11g access point? A. The access point transmits, but the node is unable to receive. B. A connection occurs C. Both the node and the access point are unable to transmit. D. The node transmits, but the access point is unable to receive. Correct Answer: D Section: (none) Explanation
- 262. QUESTION 464 Which two command can you enter to display the current time sources statistics on devices ? (Choose two) A. Show ntp associations. B. Show clock details C. Show clock. D. Show time. E. Show ntp status Correct Answer: AE Section: (none) Explanation QUESTION 465 Which two options are the best reasons to use an IPV4 private IP space?(choose two) A. to enable intra-enterprise communication B. to implement NAT C. to connect applications D. to conserve global address space E. to manage routing overhead Correct Answer: AD Section: (none) Explanation QUESTION 466 Which three encapsulation layers in the OSI model are combined into the TCP/IP application layer? (Choose three) A. Session B. transport C. presentation D. application E. data-link F. network Correct Answer: ACD Section: (none) Explanation QUESTION 467 Which effect of the passive-interface command on R1 is true?
- 263. A. It prevents interface Fa0/0 from sending updates. B. Interface Fa 0/0 operates in RIPv1 mode. C. It removes the 172.16.0.0 network from all updates on all interfaces on R1. D. It removes the 172.16.0.0 network from all updates on all interfaces on R1. Correct Answer: A Section: (none) Explanation Explanation/Reference: QUESTION 468 Refer to the exhibit, you determine that Computer A cannot ping Computer. Which reason for the problem is most likely true? A. The Subnet mask for Computer A is incorrect B. The default gateway address for Computer A is incorrect C. The subnet mask for computer B is incorrect. D. The default gateway address for computer B is incorrect
- 264. Correct Answer: A Section: (none) Explanation Explanation/Reference: QUESTION 469 What is the command to see assigned address in DHCP? A. show ip DHCP statistic B. show ip dhcp pool C. show ip dhcp binding D. show ip dhcp database Correct Answer: C Section: (none) Explanation QUESTION 470 Refer to the exhibit. If R1 receives a packet destined to 172.16.1.1, to which IP address does it send the packet? A. 192.168.14.4 B. 192.168.12.2 C. 192.168.13.3 D. 192.168.15.5 Correct Answer: A
- 265. Section: (none) Explanation Explanation/Reference: QUESTION 471 Drag and Drop Question Drag and drop each broadcast IP address on the left to the Broadcast Address column on the right. Not all options are used. Select and Place: Correct Answer: Section: (none) Explanation Explanation/Reference: QUESTION 472 Drag and Drop Question
- 266. Drag and drop the DNS lookup components from the left onto the correct functions on the right. Select and Place: Correct Answer: Section: (none) Explanation Explanation/Reference: QUESTION 473 Drag and Drop Question Drag and drop each advantage of static or dynamic routing from the left onto the correct routing type on the right. Select and Place:
- 267. Correct Answer: Section: (none) Explanation Explanation/Reference: QUESTION 474 Drag and Drop Question Drag and drop the MAC address types from the left onto the correct descriptions on the right? Select and Place:
- 268. Correct Answer: Section: (none) Explanation Explanation/Reference: QUESTION 475 Drag and Drop Question Drag and Drop the descriptions of IP protocol transmissions from the left onto the correct IP traffic types on the right. Select and Place:
- 269. Correct Answer:
- 270. Section: (none) Explanation Explanation/Reference: QUESTION 476 Drag and Drop Question Refer to the exhibit. You are configuring the router to provide Static NAT for the web server. Drag and drop the configuration commands from left onto the letters that correspond to its position in the configuration on the right.
- 271. Select and Place: Correct Answer:
- 272. Section: (none) Explanation Explanation/Reference: QUESTION 477 Drag and Drop Question Drag and drop the extended traceout option from the left onto the correct description on the right. Select and Place: Correct Answer:
- 273. Section: (none) Explanation Explanation/Reference: QUESTION 478 Drag and Drop Question Drag and drop the descriptions of logging from the left onto the correct logging features or compenents on the right. Select and Place: Correct Answer:
- 274. Section: (none) Explanation Explanation/Reference: QUESTION 479 Drag and Drop Question You are performing the initial configuration on a new Cisco device. Drag the task from the left onto the required or optional category on the right. Select and Place:
- 275. Correct Answer: Section: (none) Explanation Explanation/Reference: QUESTION 480 Drag and Drop Question Drag and drop each cable type from the left onto the type of connection for which it is best suited on the right . Select and Place: Correct Answer:
- 276. Section: (none) Explanation Explanation/Reference: QUESTION 481 Syslog - what does not belong? A. host name B. severity C. timestamp D. message Correct Answer: A Section: (none) Explanation Explanation/Reference: QUESTION 482 What does a switch use for communication between VLANs? A. STP B. CDP C. VTP D. Etherchannel Correct Answer: C Section: (none) Explanation QUESTION 483 What is the maximum size of an Ethernet frame that uses 802.1Q tagging? A. 1514 bytes B. 128 bytes C. 68 bytes D. 1522 bytes Correct Answer: D Section: (none) Explanation
- 277. QUESTION 484 Which of the following is true about port security? A. In stick, port retrain dynamically learned B. Configure spanning destination C. The default configuration with max 10 D. Not supported by VLAN Correct Answer: A Section: (none) Explanation QUESTION 485 Which option does the route 0.0.0.0/0 represent? A. Route with the lowest administrative distance B. Gateway of last resort C. Null route D. Empty routing table Correct Answer: B Section: (none) Explanation QUESTION 486 What is the purpose of a standard access list? A. to filter traffic based on destination address B. to deny traffic C. to filter traffic based on source address Correct Answer: C Section: (none) Explanation QUESTION 487 If you are in VLAN 10 and it gets a packet from VLAN 2 with 802.1q enabled, what does it do with the packet? A. Drops the packet B. forwards it to VLAN 2 C. configures the port to handle traffic from VLAN 2 D. adds it to the VLAN database Correct Answer: A Section: (none) Explanation QUESTION 488 Drag drop question about cable types A. Coaxial <-> TV connection Twisted <-> 10/100/1000 base
- 278. Fiber <-> BASE-5 BX USB <-> connects two computers Crossed-over <-> devices of the same type Correct Answer: A Section: (none) Explanation QUESTION 489 Which forwarding technology stores destination addresses in the cache? A. MPLS B. Cisco express forwarding C. Process switching D. Fast switching Correct Answer: B Section: (none) Explanation QUESTION 490 Which type of network topology requires each network node to be connected to one another? A. Ring B. Star C. Mesh D. Bus Correct Answer: C Section: (none) Explanation QUESTION 491 A router receives identical prefixes from OSPF, EIGRP, RIP and the same route is configured statically. Which route does the router use to forward traffic? A. Static route B. RIP route C. EIGRP route D. OSPF route Correct Answer: A Section: (none) Explanation QUESTION 492 Which device can be used to extend the LAN without using layer3 device? A. Access point B. Switch C. Wireless controller D. Firewall Correct Answer: A
- 279. Section: (none) Explanation QUESTION 493 Which syslog severity level logs informational messages? A. 2 B. 6 C. 4 D. 0 Correct Answer: B Section: (none) Explanation QUESTION 494 Which option describes a standard role that a firewall plays in an enterprise network? A. It can permit unauthorized packets to pass to less secure segments of the network B. It can decide which packets can traverse from a less secure segment of the network to a more secure C. It can forward packets based on rules that are predetermined by IEEE standards D. It can deny all packets from entering an administrative domain. Correct Answer: B Section: (none) Explanation QUESTION 495 A question with the mac table on a switch with mac 1111:1111:1111 and port 0/1 and the question was asking : You received a packet with destination mac 1111:1111:1111 on port 0/1 , how does the switch will handle the frame. A. The switch forwards the frame to port 0/1 only. Correct Answer: A Section: (none) Explanation QUESTION 496 What cable use in star topology? (Choose two) A. 10 base2 B. 10 base5 C. 100Base-T D. 10Base-T Correct Answer: CD Section: (none) Explanation QUESTION 497 What is the binary of the IPv6 multicast address?
- 280. A. 11111111 Correct Answer: A Section: (none) Explanation Explanation/Reference: Explanation: IPv6 multicast addresses are distinguished from unicast addresses by the value of the high-order octet of the addresses: a value of 0xFF (binary 11111111) identifies an address as a multicast address; any other value identifies an address as a unicast address QUESTION 498 What is the lowest AD? A. OSPF B. EIGRP C. IS-IS D. IBGP E. RIPv2 Correct Answer: B Section: (none) Explanation QUESTION 499 Assume all the routing protocol have the same length prefix, what would the router prefer? A. OSPF B. EIGRP C. CONNECTED D. BGP Correct Answer: C Section: (none) Explanation QUESTION 500 In which circumstances is static routing most useful? A. On a stub network B. On a large network that must share routes quickly between routers C. On a network that experiences frequent link failures D. On a network with frequent routing changes Correct Answer: A Section: (none) Explanation QUESTION 501 Which statement describes the dynamic route correctly? A. more secure than static B. high scaling for large network C. easier to configure than static route
- 281. D. build for small network Correct Answer: B Section: (none) Explanation QUESTION 502 Which statement is correct when comparing dynamic route and static route? A. static route is more secure Correct Answer: A Section: (none) Explanation QUESTION 503 What would the router use as metrics when having different routing protocol in the routing table A. Prefix length Correct Answer: A Section: (none) Explanation QUESTION 504 Which of the following description is correct about DNS? A. Host will sends a request to a DNS server... Correct Answer: A Section: (none) Explanation QUESTION 505 Which statement about standard access list is true? A. They have an implicit permit statement at the end to allow all traffic B. They can use either a wildcard mask or a subnet mask to identify host C. They can be identified by a number from 1 to 99 D. They must be placed close to the source of traffic Correct Answer: C Section: (none) Explanation QUESTION 506 Which of the following item is used to establish telnet session by having the host name? A. DNS lookup B. Ping C. Syslog D. ARP Correct Answer: A
- 282. Section: (none) Explanation QUESTION 507 Which of the following command can be use to access all the files in a system? A. syslog B. IFS C. ping D. NTP Correct Answer: B Section: (none) Explanation QUESTION 508 For which important purpose was IPv6 addressing developed? A. To reduce the number of public IP addresses on the internet B. To replace network address translation C. To remove the need for classless inter-domain routing D. To relieve the shortage of public IP addresses on the internet Correct Answer: D Section: (none) Explanation QUESTION 509 What does the 0.0.0.0/0 mean in a routing table? A. wildcard B. empty routing table C. default route D. Gateway of last resort Correct Answer: C Section: (none) Explanation QUESTION 510 A host is attempting to communicate with a server from an application layer. The connection has failed, what would be the first layer to start from the troubleshooting standpoint? A. network B. Application C. physical D. session Correct Answer: C Section: (none) Explanation QUESTION 511
- 283. Which destination IP address can a host use to send one message to multiple devices across ...? A. 239.255.0.1 B. 172.20.1.0 C. 192.168.0.119 D. 127.0.0.1 Correct Answer: A Section: (none) Explanation QUESTION 512 Which value is of primary importance when a router populates its routing table for unique routes? A. Administrative distance B. Prefix length C. Network address D. Metric Correct Answer: A Section: (none) Explanation QUESTION 513 Which IPv6 address type is a public address? A. Global unicast B. Multicast C. Link local D. Unique-local Correct Answer: A Section: (none) Explanation QUESTION 514 How is the MAC address table of a switch populated? A. When the switch receives an Ethernet frame with a new destination MAC address, it installs the destination MAC address and the ingress switch port in the MAC address table B. When the switch receives an Ethernet frame with a new source MAC address, it installs the source MAC address and the ingress switch port in the MAC address table C. When the switch receives an Ethernet frame with a new destination MAC address, it installs the destination MAC address and the egress switch port in the MAC address table D. When the switch receives an Ethernet frame in which the source and destination MAC address are new, it installs the destination MAC address and the ingress switch port in the MAC address table Correct Answer: B Section: (none) Explanation QUESTION 515 Which statement describes the effect of exec-timeout 30 command?
- 284. A. The router disconnects the user session if it is inactive for 30 minutes B. The router maintains a user session indefinitely after it is active for 30 mins C. The router disconnects a user session if it is inactive for 30 seconds D. The router maintains a user session indefinitely after it is active for 30 seconds. Correct Answer: A Section: (none) Explanation Explanation/Reference: Explanation: The "exec-timeout" command is used to configure the inactive session timeout on the console port or the virtual terminal. The syntax of this command is: exec-timeout minutes [seconds] Therefore we need to use the "exec-timeout 30" command to set the user inactivity timer to 30 minutes. To set the user inactivity timer to 30 seconds we use the "exec-timeout 0 30". QUESTION 516 Which statement is true about port-security violations is true? A. When a violation occurs on a switch port in restrict mode, the switch port continues to accept traffic from unknown MAC address until the administrator manually disables it. B. When a violation occurs on a switch port in protect mode, it sends a syslog notification message C. A port In the err-disabled state must be re-enabled manually, if recovery is disabled D. When a switch port is in protect mode, it allows traffic from unknown MAC address until it has learned the maximum allowable number of MAC addresses Correct Answer: C Section: (none) Explanation QUESTION 517 Which statement is true about static and dynamic routing is true? A. Only static routes are shared between connected interfaces B. Dynamic routing is more scalable than static routing C. Only dynamic routes are secure D. Static routing is easier to maintain in a large network than dynamic routing. Correct Answer: B Section: (none) Explanation QUESTION 518 Which metric or metrics does RIP use to determine the routing table metric for a route? A. Bandwidth and delay B. Hop count C. Bandwidth and hop count D. Bandwidth Correct Answer: B Section: (none) Explanation
- 285. QUESTION 519 Which network configuration allows a switch to send traffic from multiple VLANS over a single link to a router that routes between the VLANs? A. Port channel B. Router-on-a-stick C. Virtual trunking D. Spanning-tree Correct Answer: B Section: (none) Explanation QUESTION 520 Which statement about native VLAN traffic over 802.1Q trunk is true? A. It is discarded by STP B. It is placed is a high-priority queue C. It is tagged with a value of 1 D. It is untagged Correct Answer: D Section: (none) Explanation QUESTION 521 Which feature allows a device to use a switch port that is configured for half-duplex to access the network? A. Split horizon B. CSMA/CD C. IGMP D. Port security Correct Answer: B Section: (none) Explanation QUESTION 522 Refer to the exhibit. <exhibit missing> If switch-A receives a frame with destination MAC address 0000.0000.0001 on its Fa0/1 interface, how does it process the frame? A. It forwards the frame back out of interface Fa0/1 B. It floods the frame to all interfaces except Fa0/1 C. It holds the packet until the MAC address timer expires and then drops the frame D. It drops the frame immediately Correct Answer: B Section: (none) Explanation
- 286. QUESTION 523 When a router makes a routing decision for a packet that is received from one network and destined to another, which portion of the packet does it replace? A. Layer 4 protocol B. Layer 3 IP address C. Layer 2 frame header and trailer D. Layer 5 session Correct Answer: C Section: (none) Explanation Explanation/Reference: Explanation: During the transmission of a packet from source to destination, only Layer 2 information is replaced in the path. Layer 3 information remains the same (except when NAT is used). QUESTION 524 Which protocol can identify connected devices within a mixed-vendor infrastructure? A. Virtual terminal protocol B. Network time protocol C. Link level discovery protocol D. Cisco discovery protocol Correct Answer: C Section: (none) Explanation QUESTION 525 Which interface configuration is used with a router-on-a-stick configuration? A. VRF B. Subinterfaces C. PIM sparse mode D. Passive-interface Correct Answer: B Section: (none) Explanation QUESTION 526 You have configured the host computers on a campus LAN to receive their DHCP addresses from the local router to be able to browse their corporate site. Which statement about the network environment is true? A. Two host computers may be assigned manually on each host B. The DNS server must be configured manually on each host C. It supports a DNS server for use by DHCP clients D. The domain name must be configured locally on each host computer Correct Answer: C Section: (none) Explanation
- 287. Explanation/Reference: Explanation: DHCP supports configuring a domain name to assign to the DHCP clients. For example: Router(config)#ip dhcp pool CLIENTS Router(dhcp-config)#domain-name lead2pass.com ... QUESTION 527 Where is private IPv4 addressing used? A. On the endpoints of a VPN tunnel that traverses outside an administrator domain B. At a remote site that connects over public infrastructure to a hub C. Within an enterprise D. Over the internet Correct Answer: C Section: (none) Explanation QUESTION 528 Which protocol allows VLANs to be dynamically configured between multiple switches? A. IGMP B. STP C. VTP D. 802.1Q Correct Answer: C Section: (none) Explanation QUESTION 529 Client A cannot reach client B by its hostname. Which reason for the problem is most likely true? A. The connected router is using the default domain lookup configuration B. The hostname for client B is missing from the connected router C. A DNS server has been misconfigured D. Telnet has been disabled on the connected router. Correct Answer: C Section: (none) Explanation QUESTION 530 Which first step must a client perform to connect to an internal host when the hostname is known, but the IP address is unknown? A. The client sends the host name in a DNS reply to a DNS server, and the DNS server responds with the host IP address B. The client exchanges IP address information with a DNS server on the same LAN C. The client looks up the hostname in the ARP table to determine the IP address D. The client sends the host name in a DNS request to a DNS server, and the DNS server responds with the host IP address.
- 288. Correct Answer: D Section: (none) Explanation Explanation/Reference: Explanation: When a client knew about the hostname but not the IP address, it needs to resolve the hostname to the IP address by sending a DNS request to its DNS server. Notice that the ARP table is responsible for resolving IP address to MAC address only. It has nothing to do with the hostname. QUESTION 531 Which route option can be used to back-up in case of fail? A. floating route Correct Answer: A Section: (none) Explanation QUESTION 532 Which of the following is true about TCP and UDP? A. only TCP order the transmission packets Correct Answer: A Section: (none) Explanation QUESTION 533 If a switch received a frame while forwarding others, how frame would be handled? A. It will interrupt the frames B. The switch will put the frame in a queue C. Will be forwarded at the same time with the current frame D. The new frame will forward first Correct Answer: C Section: (none) Explanation QUESTION 534 Which of the following true about access point? A. It used physically to connect network devices B. It is used as a router C. Provide full duplex communication D. It is a layer 2 device used to extend the LAN coverage to wireless devices Correct Answer: D Section: (none) Explanation QUESTION 535
- 289. Which of the following used to identify immediate destination? A. Administrative distance B. Metric C. Next hop D. Destination network Correct Answer: C Section: (none) Explanation QUESTION 536 Which of the following options could be used on router to prevent reassign IP address statically? A. Pool B. Lease C. Client ID D. Exclude address Correct Answer: D Section: (none) Explanation QUESTION 537 A router with a default setting deployed, how will act if it received mistype command? A. Disable DNS look up B. Recognizing the command C. Try to resolve the command to an IP address D. Try to correct the command E. Show error message Correct Answer: C Section: (none) Explanation QUESTION 538 Which symbol ping of the following is for unknown packet? A. . B. * C. ? D. U Correct Answer: C Section: (none) Explanation QUESTION 539 Which cables could be used for star topology? (Choose two) A. 10 Base T B. 100 Base T
- 290. C. 10 Base 5 D. 10 Base 2 Correct Answer: AB Section: (none) Explanation QUESTION 540 Which of the following is true about dynamic route? A. Reduce CPU of the network B. More secure than static C. Complicate the maintenance D. Allow fast convergence when fail happen Correct Answer: D Section: (none) Explanation QUESTION 541 What RIPv2 use to elect of route? A. Hop count B. Administrative distance C. Bandwidth Correct Answer: A Section: (none) Explanation QUESTION 542 Which of the following are two local host characters? A. 32/prefix B. 255.255.255.0 C. The administrative distance is 0 D. Dynamically learned E. ? Correct Answer: AC Section: (none) Explanation QUESTION 543 Which attributes change all the path way (Choose two) A. MAC Source address B. MAC destination address C. IP Source address D. IP destination address Correct Answer: AB Section: (none)
- 291. Explanation Explanation/Reference: QUESTION 544 Why a host uses DNS server? A. DNS client request to server B. To resolve IP to FQDN C. To resolve FQDN to IP D. Assign IP Correct Answer: C Section: (none) Explanation QUESTION 545 Which six-byte field in a basic ethernet frame must be an individual address? A. FCS B. SOF C. Sa D. Da Correct Answer: C Section: (none) Explanation QUESTION 546 Which of the following true about the dynamic route? A. Reduce CPU of the network B. More secure than static C. Complicate the maintenance D. Allow fast convergence when fail happen Correct Answer: D Section: (none) Explanation QUESTION 547 If a switch received a frame while forwarding others, how frame would be handled? A. It will interrupt the frames B. The switch will put the frame in a queue C. Will be forwarded at the same time with the current frame D. The new frame will forward first Correct Answer: C Section: (none) Explanation QUESTION 548
- 292. Which three statements are true about the operation of a full-duplex Ethernet network? (Choose three.) A. The host network card and the switch port must be capable of operating in full-duplex mode. B. Ethernet hub ports are preconfigured for full-duplex mode. C. A dedicated switch port is required for each full-duplex node. D. There are no collisions in full-duplex mode. E. In a full-duplex environment, the host network card must check for the availability of the network media before transmitting. Correct Answer: ACD Section: (none) Explanation Explanation/Reference: QUESTION 549 Why would a network administrator configure port security on a switch? A. to limit the number of Layer 2 broadcasts on a particular switch port B. to prevent unauthorized Telnet access to a switch port C. to prevent unauthorized hosts from accessing the LAN D. block unauthorized access to the switch management interfaces Correct Answer: C Section: (none) Explanation Explanation/Reference: QUESTION 550 How many primary IPv4 addresses can be assigned to an interface? A. unlimited B. 8 C. 2 D. 1 Correct Answer: A Section: (none) Explanation Explanation/Reference: Explanation: Cisco IOS software supports multiple IP addresses per interface. You can specify an unlimited number of secondary addresses. QUESTION 551 After you configure a new router to connect to a host through the GigabitEthernet0/0 port of the router, you log in to the router and observe that the new link is down. Which action corrects the problem? A. Use a crossover cable between the host and R1. B. Use a straight through cable between the host and R1. C. Configure the host to use R1 as the default gateway. D. Use a rollover cable between the host and R1. Correct Answer: A
- 293. Section: (none) Explanation Explanation/Reference: QUESTION 552 How does a Cisco switch respond if you boot it without a valid configuration in the NVRAM? A. it enters setup mode. B. it uses the running-configuration C. It prompts you to restore the startup configuration D. it enters user EXEC mode. Correct Answer: B Section: (none) Explanation Explanation/Reference: QUESTION 553 Which table displays the MAC addresses that are learned on a switch? A. FIB B. ARP C. TCAM D. CAM Correct Answer: D Section: (none) Explanation Explanation/Reference: QUESTION 554 Which statement describes the effect of the copy run start command on a router in enable mode? A. The running configuration of the router is savedto NVRAM and used during the boot process. B. The router reboots and loads the last saved running configuration. C. A copy of the running configuration of the router is sent by FTP to a designated server. D. A new running configuration is loaded from flashmemory to the router. Correct Answer: A Section: (none) Explanation Explanation/Reference: QUESTION 555 Which two things does a router do when it forwards a packet? (Choose two.) A. determines the next hop on the path B. switches the packet to the appropriate outgoing interfaces C. computes the destination host address D. forwards ARP requests
- 294. E. updates the destination IP address Correct Answer: AB Section: (none) Explanation Explanation/Reference: QUESTION 556 Refer to the exhibit. The MAC address table is shown in its entirety. The Ethernet frame that is shown arrives at the switch. What two operations will the switch perform when it receives this frame? (Choose two.) A. The switch will not forward a frame with this destination MAC address. B. The frame will be forwarded out of all the ports on the switch. C. The MAC address of ffff.ffff.ffff will be added to the MAC address table. D. The frame will be forwarded out of all the active switch ports except for port fa0/0. E. The MAC address of 0000.00aa.aaaa will be added to the MAC Address Table. F. The frame will be forwarded out of fa0/0 and fa0/1 only. Correct Answer: DE Section: (none) Explanation Explanation/Reference: QUESTION 557 Refer to the exhibit. If the resume command is entered after the sequence that is shown in the exhibit, which router prompt will be displayed?
- 295. A. Router2# B. Router2> C. Router1# D. Router1> Correct Answer: B Section: (none) Explanation Explanation/Reference: QUESTION 558 Which NAT term is defined as a group of addresses available for NAT use? A. NAT pool B. dynamic NAT C. static NAT D. one-way NAT Correct Answer: A Section: (none) Explanation Explanation/Reference: QUESTION 559 How does a Layer 2 switch differ from a hub? A. A switch tracks MAC addresses of directly-connected devices. B. A switch always induces latency into the frame transfer time. C. A switch operates at a lower, more efficient layer of the OSI model. D. A switch decreases the number of collision domains. Correct Answer: A Section: (none) Explanation Explanation/Reference: QUESTION 560
- 296. Under which two circumstances is network traffic most likely to use an Exterior Gateway Routing Protocol? (Choose two) A. When an employee connects to an employer branch office in a different city. B. When network traffic is routing to a different building on a corporate campus. C. When an employee is browsing the public internet. D. When an employee checks email while working onsite at the data center. E. When a user browsing the web site of a business partner. Correct Answer: AD Section: (none) Explanation Explanation/Reference: QUESTION 561 Which two address are defined as private ip addresses ? A. 192.169.32.10 B. 10.172.76.200 C. 172.15.2.250 D. 12.17.1.20 E. 172.31.255.100 Correct Answer: BE Section: (none) Explanation Explanation/Reference: QUESTION 562 At which layer of the OSI model does the protocol that provides the information that is displayed by the show cdp neighbors command operate? A. data link B. application C. network D. transport E. physical Correct Answer: A Section: (none) Explanation Explanation/Reference: QUESTION 563 Refer to the exhibit. How will the router handle a packet destined for 192.0.2.156?
- 297. A. The router will forward the packet via either Serial0 or Serial1. B. The router will return the packet to its source. C. The router will forward the packet via Serial2. D. The router will drop the packet. Correct Answer: C Section: (none) Explanation Explanation/Reference: QUESTION 564 Which functions can be centralized by an SDN controller? A. services-plane functions B. control-plane functions C. data-plane functions D. management-plane functions Correct Answer: B Section: (none) Explanation Explanation/Reference: QUESTION 565 Refer to the exhibit. If CDP is enabled on all devices and interfaces, which devices will appear in the output of a show cdp neighbors command issued from R2?
- 298. A. R1, S1, S2, R3 and S3 B. R2 and R3 C. R3 and S2 D. R1 and R3 E. R1, S1, S2, and R3 Correct Answer: C Section: (none) Explanation Explanation/Reference: QUESTION 566 Refer to the exhibit. The exhibit is showing the topology and the MAC address table. Host A sends a data frame to host D. Which option describes what the switch will do when it receives the frame from host A? A. The switch will flood the frame out of all ports except for port Fa0/3. B. The switch will add the destination address of the frame to the MAC address table and forward theframe to host D. C. The switch will add the source address and port tothe MAC address table and forward the frame to host D. D. The switch will discard the frame and send an error message back to host A. Correct Answer: C Section: (none) Explanation Explanation/Reference: QUESTION 567 Which two statements about Cisco Discovery Protocol are true? (Choose two )
- 299. A. It is used to initiate a VTP server and client relationship. B. It uses SNMP to share device information to an external server C. It uses TLVs to share device information. D. It runs on the data link layer only E. It runs on the network layer and the data link layer. Correct Answer: AC Section: (none) Explanation Explanation/Reference: QUESTION 568 Which task must you perform to enable an lOS device to use DNS services? A. Configure manual bindings B. Configure a name server C. Configure the relay agentinformation option. D. Configure a relay agentinformation reforwarding policy Correct Answer: B Section: (none) Explanation Explanation/Reference: QUESTION 569 Which two statements describe the operation of the CSMA/CD access method? (Choose two.) A. After a collision, all stations run a random backoff algorithm. When the backoff delay period has expired, all stations have equal priority to transmit data. B. In a CSMA/CDcollision domain, multiple stations can successfully transmit data simultaneously. C. After a collision, the station that detected the collision has first priority to resend the lost data. D. The use of hubs to enlarge the size of collision domain is one way to improve the operation of the CSMA/CD access method. E. After a collision, all stations involved run an identical backoff algorithm and then synchronize with each other prior to transmitting data. F. In a CSMA/CD collision domain, stations must wait until media is not in use before transmitting. Correct Answer: AF Section: (none) Explanation Explanation/Reference: QUESTION 570 If you change the weight and distance parameters on a device with an established bgp neighbor, which additional task must you perform to allow two devices to continue exchanging routes ? A. Change the weight and distance settings on the other device to match B. reset the gateway interface C. reset the BGP connections on the device D. Clear the IP routers on the device
- 300. Correct Answer: A Section: (none) Explanation Explanation/Reference: QUESTION 571 Which statement about the default switch configuration for remote access managements is true? A. The system name is set to Cisco. B. The Telnet password is set to cisco. C. No default gateway is defined. D. One IP address is preconfigured. Correct Answer: C Section: (none) Explanation Explanation/Reference: QUESTION 572 Which statement about DHCP address pools is true? A. A network must be defined before you can configure a manual binding. B. Only one DNSserver can be identified for an individual DHCP group. C. You can use a subnet mask of prefix length to define a network. D. The domain name of the DHCP pool is specified in the global configuration of the router. Correct Answer: C Section: (none) Explanation Explanation/Reference: QUESTION 573 How many bits represent the network ID in iPv6? A. 32 B. 48 C. 64 D. 128 Correct Answer: C Section: (none) Explanation Explanation/Reference: QUESTION 574 On which OSI layer does a VLAN operate? A. Layer 1 B. Layer 2 C. Layer 3
- 301. D. Layer 4 Correct Answer: B Section: (none) Explanation Explanation/Reference: QUESTION 575 Which two statements about ipv6 anycast addresses are true? (choose two) A. They receive packets on the closest interface that is dissolved by the routing protocol B. They are used in conjunction with source specific multicast for ipv6 C. They are allocated from the ipv6 broadcast address space D. They are allocated from the ipv6 unicast address space E. They use the prefix fC00: /8 Correct Answer: AD Section: (none) Explanation Explanation/Reference: QUESTION 576 Which two characteristics are representatives of a link-state routing protocol? (Choose two.) A. provides common view of entire topology B. exchanges routing tables for it own routes with neighbors C. calculates feasible path D. utilizes event-triggered updates E. utilizes frequent periodic updates Correct Answer: AD Section: (none) Explanation Explanation/Reference: QUESTION 577 Which two functions can be performed by a local DNS server? (Choose two) A. transferring sprit horizon traffic between zones B. Forwarding name resolution requests to an external DNS server C. Assigning IP addresses to local clients D. resolving names locally E. Copying updated IOS images to Cisco switches Correct Answer: BC Section: (none) Explanation Explanation/Reference: QUESTION 578
- 302. Refer to the exhibit. A network has been planned as shown. Which three statements accurately describe the areas and devices in the network plan? (Choose three.) A. Area 2 contains a Layer 2 device. B. Network DeviceB is a hub. C. Network Device A is a hub. D. Network Device A is a switch. E. Area 1 contains a Layer 2 device. F. Network Device B is a switch. Correct Answer: BDE Section: (none) Explanation Explanation/Reference: QUESTION 579 Which configuration register value can you set on a cisco device so that it ignores the nvram when it boots? A. 0x2120 B. 0x2124 C. 0x2102 D. 0x2142 Correct Answer: C Section: (none) Explanation Explanation/Reference: QUESTION 580 Which three statements accurately describe CDP? (Choose three.)
- 303. A. CDP can discover Cisco devices that are not directly connected. B. CDP is a network layer protocol. C. CDP can discover directly connected neighboring Cisco devices. D. CDP is a datalink layer protocol. E. CDP is a Cisco proprietary protocol. F. CDP is an IEEE standard protocol. Correct Answer: CDE Section: (none) Explanation Explanation/Reference: QUESTION 581 Refer to the exhibit. The network administrator is testing connectivity from the branch router to the newly installed application server. Which reason is the most likely for the first ping having a success rate of only 60 percent? A. The branch router LAN interface should be upgraded to FastEthernet. B. The branch router had to resolve the application server MAC address. C. The network is likely to be congested, with the result that packets are being intermittently dropped. D. There is a short delay while NAT translates the server IP address. Correct Answer: B Section: (none)
- 304. Explanation Explanation/Reference: QUESTION 582 Which feature automatically disables Cisco Express Forwarding when it is enabled? A. multicast B. IP redirects C. RIB D. ACL logging Correct Answer: D Section: (none) Explanation Explanation/Reference: Explanation: If you enable CiscoExpress Forwarding and then create an access list that uses the logkeyword, the packets that match the access list are not Cisco Express Forwarding switched. They are process switched. Logging disables Cisco Express Forwarding. QUESTION 583 Which two statements about stateful firewalls in an enterprise network are true? (Choose two ) A. They can fitter HTTP and HTTPS traffic in the inbound direction only B. They can use information about previous packets to make decisions about future packets. C. They are most effective when placed in front of the router connected to the Internet D. They are more susceptible to DoS attacks than stateless firewalls E. They can track the number of active TCP connections Correct Answer: BD Section: (none) Explanation Explanation/Reference: QUESTION 584 Which statement about NTP is true? A. The default authentication key number is 1. B. The default source address of an NTP message is the interface connected to the next- hop for the server peer address. C. The default stratum number is 5. D. Each device is enabled as a server by default and propagates NTP messages to all peers on its default LAN. Correct Answer: B Section: (none) Explanation Explanation/Reference: QUESTION 585 Which statement describes the effect of the exec-timeout 30 command?
- 305. A. The router maintains a user session indefinitely after it is active for 30 seconds. B. The router disconnects the user session if it is inactive for 30 minutes. C. The router maintains a user session indefinitely after it is active for 30 minutes. D. The router disconnects a user session if it is inactive for 30 seconds. Correct Answer: B Section: (none) Explanation Explanation/Reference: QUESTION 586 Refer to the exhibit. All devices attached to the network are shown. Which number of collision domains are present in this network? A. 9 B. 3 C. 6
- 306. D. 2 E. 15 Correct Answer: E Section: (none) Explanation Explanation/Reference: QUESTION 587 Refer to the exhibit. An administrator cannot connect from R1 to R2. To troubleshoot this problem, the administrator has entered the command shown in the exhibit. Based on the output shown, what could be the problem? A. The serial interface is configured for the wrong frame size. B. The serial interface does not have a cable attached. C. The serial interface has the wrong type of cable attached. D. The serialinterface has a full buffer. E. The serial interface is configured for half duplex. Correct Answer: C Section: (none) Explanation Explanation/Reference:
- 307. QUESTION 588 Refer to the exhibit. Which feature is enabled by this configuration? A. static NAT translation B. a DHCP pool C. a dynamic NAT address pool D. PAT Correct Answer: C Section: (none) Explanation Explanation/Reference: QUESTION 589 Refer to the exhibit. The two routers have had their startup configurations cleared and have been restarted. At a minimum, which option below must the administrator do to enable CDP to exchange information between R1 and R2? A. Configure the router with thecdp enablecommand. B. Configure IP addressing andno shutdowncommands on both the R1 and R2 fa0/1 interfaces. C. Configure IP addressing andno shutdowncommands on either of the R1 or R2 fa0/1 interfaces. D. Enterno shutdowncommands on the R1 and R2 fa0/1 interfaces. Correct Answer: D Section: (none) Explanation Explanation/Reference: QUESTION 590 In which circumstance is static routing most useful? A. on a stub network B. on a network with frequent routing changes C. on a network that experiences frequent link failures D. on a large network that must share routes quickly between routers Correct Answer: A Section: (none)
- 308. Explanation Explanation/Reference: QUESTION 591 Which Ethernet interface command is present when you boot a new Cisco router for the first time? A. speed 100 B. shutdown C. ip address 192.168.1.1 255.255.255.0 D. duplex half Correct Answer: B Section: (none) Explanation Explanation/Reference: QUESTION 592 Which NTP concept indicates the distance between a device and the reliable time source? A. clock offset B. stratum C. reference D. dispersion Correct Answer: B Section: (none) Explanation Explanation/Reference: QUESTION 593 On a Cisco switch, which protocol determines if an attached VoIP phone is from Cisco or from another vendor? A. CDP B. RTP C. UDP D. TCP Correct Answer: A Section: (none) Explanation Explanation/Reference: QUESTION 594 Refer to the exhibit. The enterprise has decided to use the network address 172.16.0.0. The network administrator needs to design a classful addressing scheme to accommodate the three subnets, with 30, 40, and 50 hosts, as shown. Which subnet mask would accommodate this network?
- 309. A. 255.255.255.224 B. 255.255.255.240 C. 255.255.255.252 D. 255.255.255.248 E. 255.255.255.192 Correct Answer: E Section: (none) Explanation Explanation/Reference: QUESTION 595 Which port-security feature allows a switch to learn MAC addresses dynamically and add them to the running configuration? A. security violation restrict mode B. switch port protection C. sticky learning D. security violation protect mode Correct Answer: C Section: (none) Explanation Explanation/Reference: Explanation: You can configure an interface to convert the dynamic MAC addresses tosticky secure MAC addresses and to add them to the running configuration by enabling sticky learning. To enable sticky learning, enter the switchport port-security mac-address sticky interface configuration command. When you enter this command, the interface converts all the dynamic secure MAC addresses, including those that were dynamically learned before sticky learning was enabled, to sticky secure MAC addresses. QUESTION 596 After you configure a default route to the Internet on a router, the route is missing from the routing table. Which option describes a possible reason for the problem? A. The next-hop address is unreachable. B. The default route was configured on a passive interface. C. Dynamic routing is disabled.
- 310. D. Cisco Discovery Protocol is disabled on the interface used to reach the next hop. Correct Answer: A Section: (none) Explanation Explanation/Reference: QUESTION 597 A workstation has just resolved a browser URL to the IP address of a server. Which protocol will the workstation now use to determine the destination MAC address to be placed into frames directed toward the sever? A. ARP B. RARP C. DNS D. DHCP E. HTTP Correct Answer: A Section: (none) Explanation Explanation/Reference: QUESTION 598 Which two statements about stacking Cisco switches are true? (Choose two ) A. Each switch manages its own MAC address table. B. It enables the administrator to manage multiple switches from a single management interface. C. When a new master switch is elected, it queries the previous master for its running configuration D. The administrator can create only one stack of switches in a network which is under the same administrative domain E. The administrator can add additional switches to the stack as demand increases Correct Answer: AB Section: (none) Explanation Explanation/Reference: QUESTION 599 Which adverse situation can occur if an Ethernet cable is too long? A. late collisions B. giants C. interface resets D. runts Correct Answer: A Section: (none) Explanation Explanation/Reference:
- 311. QUESTION 600 Which keyword in a NAT configuration enables the use of one outside IP address for multiple inside hosts? A. source B. static C. pool D. overload Correct Answer: D Section: (none) Explanation Explanation/Reference: QUESTION 601 You have configured the host computers on a campus LAN to receive their DHCP addresses from the local router to be able to browse their corporate site. Which statement about the network environment is true? A. It supports a DNS server for use by DHCP clients. B. Two host computers may be assigned the same IP address. C. The DNS server mustbe configured manually on each host. D. The domain name must be configured locally on each host computer. Correct Answer: A Section: (none) Explanation Explanation/Reference: QUESTION 602 What are two advantages of dynamic routing? (Choose two) A. It produces minimal CPU load. B. It can load-balance traffic over multiple link without manual intervention C. It allows the network administrator to choose the best route. D. it can be implemented easily even in large environments. E. it can operate without a Layer 3 device Correct Answer: CD Section: (none) Explanation Explanation/Reference: QUESTION 603 Refer to the exhibit. Which option describes how SwitchA will handle the frame just received?
- 312. A. It will flood the frame out of all the ports except Fa0/3. B. It will drop the frame. C. It will flood the frame out all ports. D. It will forward the frame out of portFa0/3 only. E. It will forward the frame out of port Fa0/6 only. Correct Answer: E Section: (none) Explanation Explanation/Reference: QUESTION 604 Refer to the exhibit. A TFTP server has recently been instated in the Atlanta office. The network administrator is located in the NY office and has made a console connection to the NY router. After establishing the connection they are unable to backup the configuration file and iOS of the NY router to the TFTP server. What is the cause of this problem?
- 313. A. The TFTP server has an incorrect subnet mask. B. The TFTP server has an incorrect IP address. C. The network administrator computer has an incorrect IP address. D. The NY router has an incorrect subnet mask. Correct Answer: A Section: (none) Explanation Explanation/Reference: QUESTION 605 Which statement about unique local IPv6 addresses is true? A. Summarization is not supported. B. They require all prefixes to be unique. C. Their global IDs are assigned sequentially. D. They are routable to the public Internet. Correct Answer: B Section: (none) Explanation Explanation/Reference: QUESTION 606 Which NAT command can be applied to an interface? A. ip nat inside B. ip nat inside test access-list-number pool pool-name C. ip nat inside source static 10.10.10.010.10.10.50 D. ip nat pool test 10.10.10.0 10.10.10.50 255.255.255.0 Correct Answer: A Section: (none)
- 314. Explanation Explanation/Reference: QUESTION 607 After you configure theip dns spoofingcommand globally on a device, under which two conditions is DNS spoofing enabled on the device? (Choose two) A. The ip dns spoofing command is disabled on the local interface B. The ip host command is disabled C. All configured IP name server addresses are removed D. The DNS server queue limit is disabled E. The no ip domain lookup command is configured Correct Answer: BC Section: (none) Explanation Explanation/Reference: QUESTION 608 Refer to the exhibit. Which command is simplest to configure routing between the regional office network 10.89.0.0/20 and the corporate network? A. router2(config)#ip route 0.0.0.0 0.0.0.0 10.89.16.1 B. router2(config)#ip route 10.89.3.0 255.255.0.0 10.89.16.2 C. router1(config)#ip route 10.89.0.0 255.255.240.0 10.89.16.1 D. router1(config)#ip route 10.89.0.0 255.255.240.0 10.89.16.2 Correct Answer: A Section: (none) Explanation Explanation/Reference: QUESTION 609 What is the subnet address of 192.168.1.42 255.255.255.248?
- 315. A. 192.168.1.16/28 B. 192.168.1.32/27 C. 192.168.1.40/29 D. 192.168.1.8/29 E. 192.168.1.48/29 Correct Answer: C Section: (none) Explanation Explanation/Reference: QUESTION 610 Which command can you enter to configure an IPv6 floating static route? A. router(config)#ipv6 route FE80:0202::/32 serial 0/1 1 B. router (config)#ipv6 route ::/0 serial 0/1 C. router(config)#ipv6 route static resolve default D. router(config)#ipv6 route FE80.0202::/32serial 0/1 201 Correct Answer: D Section: (none) Explanation Explanation/Reference: QUESTION 611 Which sequence begins a unique local IPv6 address in binary notation? A. 1111110 B. 1111111 C. 00000000 D. 1111100 Correct Answer: A Section: (none) Explanation Explanation/Reference: QUESTION 612 Which two statements about fiber cable are true? (Choose two) A. Single-mode fiber supports SC and LC connectors only. B. Multimode cable supports speeds between 100 Mbps and 9.92 Gbps. C. Single-mode cable is most appropriate for installations longer than 10 km. D. Fiber cable is relatively inexpensive and supports a higher data rate than coaxial cable. E. Mulitimode cable supports speeds between 100 Mbps and 100 Gpbs. Correct Answer: DE Section: (none) Explanation Explanation/Reference:
- 316. QUESTION 613 What feature you should use to analyse and monitor your traffic for troubleshooting? A. RSPAN B. SPAN C. Netflow D. SNMP Correct Answer: C Section: (none) Explanation Explanation/Reference: QUESTION 614 Which information is used to install the best route to a destination in IP routing table? A. the tunnel ID B. the prefix length C. the interface number D. the autonomous system Correct Answer: B Section: (none) Explanation Explanation/Reference: QUESTION 615 An administrator has connected devices to a switch and, for security reasons, wants the dynamically learned MAC addresses from the address table added to the running configuration. Which action must be taken to accomplish this? A. Use theno switchport port-security command to allow MAC addresses to be added to the configuration. B. Enable port security and use the keyword sticky. C. Set the switchport mode to trunk and save the running configuration. D. Use theswitchport protectedcommand to have the MAC addresses added to the configuration. Correct Answer: B Section: (none) Explanation Explanation/Reference: QUESTION 616 Which two of these functions do routers perform on packets? (Choose two.) A. update the Layer 3 headers of outbound packets so that the packets are properly directed to valid next hops B. update the Layer 2 headers of outbound packets with the MAC addresses of the next hops C. examine the Layer 3 headers of inbound packets and use that information to determine the complete paths along which the packets will be routed to their ultimate destinations D. examine the Layer 3 headers of inbound packets and use that information to determine the next hops for the packets
- 317. E. examine the Layer 2 headers of inbound packets and use that information to determine the next hops for the packets F. update the Layer 3 headers of outbound packets so that the packets are properly directed to their ultimate destinations Correct Answer: BD Section: (none) Explanation Explanation/Reference: QUESTION 617 Which two options will help to solve the problem of a network that is suffering a broadcast storm? (Choose two.) A. a Layer 3 switch B. a hub C. a bridge D. an access point E. a router Correct Answer: AE Section: (none) Explanation Explanation/Reference: QUESTION 618 A switch has 48 ports and 4 VLANs. How many collision and broadcast domains exist on the switch (collision, broadcast)? A. 4,48 B. 48,4 C. 48,1 D. 4,1 E. 1,48 Correct Answer: B Section: (none) Explanation Explanation/Reference: QUESTION 619 Which statement describes the effect of the overload keyword in the ip nat inside source list 90 interface ethernet 0/0 overload command? A. Addresses that match access listinsideare translated to the IP address of the Ethernet 0/0 interface. B. Hosts that match access listinsideare translated to an address in the Ethernet 0/0 network. C. Hosts on the Ethernet 0/0 LAN are translated to the address pool in access list90. D. Addressesthat match access list90are translated through PAT to the IP address of the Ethernet 0/0 interface. Correct Answer: D Section: (none)
- 318. Explanation Explanation/Reference: QUESTION 620 How many host addresses are available on the network 192.168.1.0 subnet 255.255.255.240 ? A. 6 B. 8 C. 14 D. 16 Correct Answer: C Section: (none) Explanation Explanation/Reference: QUESTION 621 Which two statements are true for multicast MAC address directions? A. 01:00:5E:xx:xx:xx B. one to one C. 01 00 xx xxxxxxx D. 02 xx xxxxxxx E. one to many Correct Answer: AE Section: (none) Explanation Explanation/Reference: Explanation: The Internet authorities have reserved the multicast address range of 01:00:5E:00:00:00 to 01:00:5E:7F:FF:FF for Ethernet and Fiber Distributed Data Interface (FDDI) media access control (MAC) addresses. QUESTION 622 Which subnet address is for the IP address 172.19.20.23/28? A. 172.19.20.20 B. 172.19.20.0 C. 172.19.20.32 D. 172.19.20.15 E. 172.19.20.16 Correct Answer: E Section: (none) Explanation Explanation/Reference: QUESTION 623 The command ip route 192.168.100.160 255.255.255.224 192.168.10.2 was issued on a router. No routing protocols or other static routes are configured on the router. Which statement is true about this command?
- 319. A. The interface with IP address 192.168.10.2 is on this router. B. The command sets a gateway of last resort for the router. C. Packets that are destined for host 192.168.100.160 will be sent to 192.168.10.2. D. The command creates a static route for all IP traffic with the source address 192.168.100.160. Correct Answer: C Section: (none) Explanation Explanation/Reference: QUESTION 624 Which feature can validate address requests and filter out invalid messages? A. IP Source Guard B. port security C. DHCP snooping D. dynamic ARP inspection Correct Answer: C Section: (none) Explanation Explanation/Reference: QUESTION 625 An administrator is working with the 192.168.4.0 netwrok, which has been subnetted with a /26 mask. Which two addresses can be assigned to hosts within the same subnet? (Choose two.) A. 192.168.4.67 B. 192.168.4.61 C. 192.168.4.128 D. 192.168.4.132 E. 192.168.4.125 F. 192.168.4.63 Correct Answer: AE Section: (none) Explanation Explanation/Reference: QUESTION 626 On a live network, which two commands will verify the operational status of router interfaces? (Choose two.) A. Router# show ip interface brief B. Router# debug interface C. Router# show ip protocols D. Router# show interfaces E. Router# show start Correct Answer: AD Section: (none)
- 320. Explanation Explanation/Reference: QUESTION 627 Which set of conditions comprises a successful ping attempt between two connected routers configured with IP addresses on the same subnet? A. The destination host receives an echo reply from the source host within one second and the source host receives an echo request from the destination host. B. The destination host receives an echo request from the source host within one second. C. The destination host receives an echo replyfrom the source host within one second and the source host receives an echo reply from the destination host within two seconds. D. The destination host receives an echo request from the source host and the source host receives an echo request from the destination host within one second. E. The destination host receives an echo request from the source host and the source host receives an echo reply from the destination host within two seconds. Correct Answer: E Section: (none) Explanation Explanation/Reference: QUESTION 628 Which command can you enter to configure an IPv6 static route? A. router(config)#ipv6 route FE80:0202::/32 serial 0/1 1 B. router(config)#ipv6 route FE80:0202::/32 serial 0/1 201 C. router(config)#ipv6 route ::/0 serial 0/1 D. router(config)#ipv6 route static resolve default Correct Answer: B Section: (none) Explanation Explanation/Reference: QUESTION 629 Which option must occur before a workstation can exchange HTTP packets with a web server? A. An ICMP connection must be established between the workstation and the web server. B. A UDP connection must be established between the workstation and its default gateway. C. A TCP connection must be established between the workstation and its default gateway. D. A UDP connection must be established between the workstation and the web server. E. An ICMP connection must be established between the workstation and its default gateway. F. A TCP connection must be established between the workstation and the web server. Correct Answer: F Section: (none) Explanation Explanation/Reference:
- 321. QUESTION 630 Which Cisco SDN controller supports existing enterprise network devices? A. APIC-EM B. OpenFlow C. Open SDN D. ACI Correct Answer: A Section: (none) Explanation Explanation/Reference: QUESTION 631 Drag and Drop Question Drag and drop the switching concepts from the left onto the correct descriptions on the right. Select and Place: Correct Answer:
- 322. Section: (none) Explanation Explanation/Reference: QUESTION 632 Drag and Drop Question Drag and drop the values in a routing table from the left onto the correct meanings on the right . Select and Place:
- 323. Correct Answer: Section: (none) Explanation Explanation/Reference: QUESTION 633 Drag and Drop Question Drag and drop the IPv6 IP addresses from the left onto the correct IPv6 address types on the right. Select and Place:
- 324. Correct Answer: Section: (none) Explanation Explanation/Reference: QUESTION 634 Drag and Drop Question Drag and Drop the protocols from the left onto the correct IP traffic types on the right. Select and Place:
- 325. Correct Answer:
- 326. Section: (none) Explanation Explanation/Reference: QUESTION 635 Drag and Drop Question Drag and drop the benefits of a cisco wireless Lan controller from the left onto the correct examples on the right. Select and Place:
- 327. Correct Answer: Section: (none) Explanation Explanation/Reference: QUESTION 636 Drag and Drop Question Drag and drop the IEEE standard Cable names from the left onto the correct cable types on the right. Select and Place:
- 329. QUESTION 637 Drag and Drop Question Drag and drop the route source codes in a routing table from the left onto the correct meanings on the right. Select and Place: Correct Answer:
- 330. Section: (none) Explanation Explanation/Reference: QUESTION 638 Drag and Drop Question Drag and drop the PDUs from the left onto the correct TCP/IP layers on the right. Select and Place:
- 331. Correct Answer:
- 332. Section: (none) Explanation Explanation/Reference: Explanation: http://knutsonco.tripod.com/id9.html QUESTION 639 Drag and Drop Question Drag and drop the DNS lookup commands from the left onto the correct effects on the right. Select and Place:
- 334. QUESTION 640 Drag and Drop Question Drag and drop the DHCP client states from the left into the standard order in which the Client passes through them on the right. Select and Place: Correct Answer:
- 335. Section: (none) Explanation Explanation/Reference: QUESTION 641 Drag and Drop Question The left describes the types of cables, while the right describes the purposes of the cables. Drag the items on the left to the proper locations. (Not all items can be used.) Select and Place:
- 336. Correct Answer: Section: (none) Explanation Explanation/Reference: QUESTION 642 Which two statements about 802.1Q are true? (Choose two.) A. It is an open-standard trunking protocol
- 337. B. It is a Cisco-proprietary trunking protocol C. It inserts a 4-byte identifying tag in the Ethernet frame after the source MAC address field. D. It encapsulates the original data frame inside a trunking header. E. It uses a 20-bit label to identify packets within a trunk. Correct Answer: AC Section: (none) Explanation QUESTION 643 Multicast IP addresses can be grouped into which two address-range assignments? (Choose two.) A. registered B. dynamic C. GLOP D. source-specific multicast E. private Correct Answer: AB Section: (none) Explanation QUESTION 644 Which hashing algorithm does NTP use for its authentication keys? A. MD5 B. AES-256 C. 3DES D. SHA Correct Answer: A Section: (none) Explanation QUESTION 645 Which value or values does RIP use to determine the routing table metric for a route? A. bandwidth and delay B. bandwidth C. hop count D. bandwidth and hop count Correct Answer: C Section: (none) Explanation QUESTION 646 Which command do you enter on a router running RIP so that it advertises a route on the same interface on which it received the route? A. no auto-summary B. no ip split-horizon C. passive-interface default
- 338. D. ip rip v2-broadcast Correct Answer: B Section: (none) Explanation QUESTION 647 Which description refers to administrative distance? A. the advertised metric to reach a network B. the cost of a link between two neighboring routers C. the cost to reach a network that is administratively set D. a measure of the trustworthiness of a routing information source Correct Answer: D Section: (none) Explanation QUESTION 648 Which two configuration steps will prevent an unauthorized PC from accessing the corporate network? (Choose two.) A. set the port security aging time to 0 B. create the port as a protected port and statically assign the MAC address to the address table C. configure the switch to discover new MAC addresses after a set time of inactivity D. enable port security on the switch E. create the port as an access port and statically assign the MAC address to the address table Correct Answer: DE Section: (none) Explanation QUESTION 649 Which command do you enter to configure a device as an authoritative time server? A. ntp authenticate B. ntp server 127.0.0.1 C. ntp source 127.0.0.1 D. ntp master 1 Correct Answer: D Section: (none) Explanation QUESTION 650 Which difference between TCP and UDP is true? A. Only TCP orders the packets that are transmitted. B. Only UDP retransmits packets to ensure delivery. C. Only TCP has eliminated error checking. D. Only UDP requires recipients to acknowledge packet receipt. Correct Answer: A Section: (none)
- 339. Explanation QUESTION 651 Which device mode must you use to recover a password on a Cisco IOS device? A. privileged EXEC B. global configuration C. user EXEC D. ROMmon Correct Answer: D Section: (none) Explanation QUESTION 652 What is the default number of secure MAC addresses for an interface configured with port security? A. 1 B. 255 C. 1042 D. 3072 Correct Answer: A Section: (none) Explanation Explanation/Reference: Explanation: https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst4500/12-2/20ewa/configuration/guide/ conf/ port_sec.html QUESTION 653 Which value is calculated by the sender and receiver of a frame to determine whether the frame has been damaged in transit? A. the runt value B. the CRC value C. the giant value D. the collision value Correct Answer: B Section: (none) Explanation QUESTION 654 Which value does RIPv2 use to calculate its route metric? A. delay B. bandwidth C. hop count D. reliability Correct Answer: C Section: (none) Explanation
- 340. QUESTION 655 A router is deployed with the default factory settings. If a user on the router mistypes a command, which option is the result? A. The router immediately returns an error message. B. The router recognizes the mistake and discards the request. C. The router autocorrects the mistyped command. D. The router attempts to resolve the command to an IP address. E. The router disables DNS lookup. Correct Answer: D Section: (none) Explanation QUESTION 656 Which statement about the default Cisco Discovery Protocol configuration is true? A. CDPv1 is disabled on FastEthernet interfaces. B. CDPv2 advertisements are unicast. C. CDPv1 is enabled on Frame Relay subinterfaces. D. CDPv2 advertisements are broadcast. Correct Answer: D Section: (none) Explanation QUESTION 657 Which information is missing from a default syslog message? A. HOSTNAME B. SEVERITY C. MESSAGE D. TIMESTAMP Correct Answer: A Section: (none) Explanation Explanation/Reference: Explanation: https://www.cisco.com/c/en/us/td/docs/routers/access/wireless/software/guide/SysMsgLogging.html QUESTION 658 Which statement about a router-on-a-stick configuration is true? A. It is most appropriate for use on large networks with both Layer2 and Layer3 switches. B. It can perform 802.1q encapsulation. C. It can act as a multilayer switch. D. It can classify packets for QoS. Correct Answer: B Section: (none) Explanation
- 341. QUESTION 659 Which two statements about the default configuration of a Cisco IOS router are true? (Choose two.) A. In privileged EXEC mode, the console times out after 10 minutes of inactivity. B. The loopback 0 interface is enabled. C. The first connected interface becomes the gateway of last resort. D. The enable password password and enable secret password are both set to cisco. E. The hostname of the device is displayed in lower-case letters only, even if you specify capital letters. F. The default hostname is Router. Correct Answer: AF Section: (none) Explanation QUESTION 660 Which Cisco IOS feature can dynamically assign IP addresses to hosts? A. DHCP Relay B. TFTP C. DNS D. DHCP Correct Answer: D Section: (none) Explanation QUESTION 661 Which value represents a host route? A. 192.168.1.0/30 B. 192.168.1.0/24 C. 192.168.1.2/31 D. 192.168.1.0/32 Correct Answer: D Section: (none) Explanation QUESTION 662 Which two statements are true about the operation of a full-duplex Ethernet network? (Choose two.) A. There are no collisions in full-duplex mode. B. A dedicated switch port is not required for each full-duplex node. C. Ethernet hub ports are preconfigured for full-duplex mode. D. The device network card and the switch port must be capable of operating in full-duplex mode. E. In a full-duplex environment, the host network card must check for the availability of the network media before transmitting. Correct Answer: AD Section: (none) Explanation
- 342. QUESTION 663 How are MAC addresses removed from a MAC address table? A. They are removed automatically if they remain inactive for the duration of the switch aging timer. B. They are removed automatically on a FIFO basis when the address-table limit has been reached. C. They must be manually cleared from the table. D. They are removed automatically if they remain inactive for the duration of the global MAC address timer. Correct Answer: D Section: (none) Explanation QUESTION 664 Which IPv6 address does a device use for neighbor discovery? A. the link-local address B. the multicast address C. the unique local address D. the global unicast address Correct Answer: A Section: (none) Explanation QUESTION 665 If a router receives a route 192.168.1.0/24 from peers running OSPF and EIGRP, how does the router forward traffic destined to that network? A. It uses the path with the lowest metric. B. It always uses the path learned from OSPF because OSPF is a vendor-neutral protocol. C. It load-balances traffic across both paths. D. It always uses the path learned from EIGRP because EIGRP has a lower administrative distance. Correct Answer: D Section: (none) Explanation QUESTION 666 Which static route can be used to forward a packet that is destined to 192.168.1.23? A. ip route 192.168.1.16 255.255.255.252 192.168.255.1 B. ip route 192.168.1.0 255.255.255.240 192.168.255.1 C. ip route 192.168.0.0 255.255.255.0 192.168.255.1 D. ip route 192.168.1.20 255.255.255.252 192.168.255.1 Correct Answer: D Section: (none) Explanation QUESTION 667 How does a switch handle a frame in which it detects an error in the frame check sequence? A. It updates the frame check sequence and forwards the frame to its destination.
- 343. B. It discards the damaged frame without further action. C. It forwards the frame to its destination unchanged. D. It discards the damaged frame and requests the sender to retransmit it. Correct Answer: B Section: (none) Explanation QUESTION 668 For what reason do you use a standard access list? A. to filter traffic from identified source addresses B. to deny traffic to identified destination addresses C. to load-balance traffic over different interfaces D. to identify traffic to be label-switched through the network E. to deny traffic to unidentified destination addresses Correct Answer: A Section: (none) Explanation QUESTION 669 Which statement about the enable password is true? A. The space character is not supported. B. It is not stored in a secured format. C. It can be up to 32 characters long. D. It is stored in a secured format. Correct Answer: B Section: (none) Explanation Explanation/Reference: Explanation: https://www.cisco.com/c/en/us/td/docs/ios/12_2/security/command/reference/fsecur_r/srfpass.html QUESTION 670 Which type of route is the most trusted? A. BGP B. OSPF C. static D. connected Correct Answer: D Section: (none) Explanation QUESTION 671 You have configured two hosts that are connected to a single switch, but reside in different VLANs. Which statement about the configuration is true? A. The two hosts are unable to communicate without a router. B. The two hosts can communicate with ICMP.
- 344. C. The two hosts are unable to communicate without a trunk port. D. The two hosts are unable to communicate without a hub. Correct Answer: A Section: (none) Explanation QUESTION 672 Which circumstance causes a security violation on a switch port with port security enabled? A. The maximum number of secure MAC addresses is reached on a secure port and an unidentified MAC address attempts an ingress connection. B. A configured MAC address attempts an ingress connection on a different port in a different VLAN. C. The minimum number of secure MAC addresses is configured on a secure port and an unidentified MAC address attempts an ingress connection. D. A minimum number of secure MAC addresses has filled the dynamic table. Correct Answer: A Section: (none) Explanation Explanation/Reference: Explanation: https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst6500/ios/12-2SX/configuration/guide/ book/ port_sec.html QUESTION 673 Which option is the default time zone used on Cisco devices? A. CST B. UTC C. EST D. GMT E. PST Correct Answer: B Section: (none) Explanation QUESTION 674 Which statement about wireless access points is true? A. They are Layer 2 devices that are used to extend a LAN to wireless clients. B. They provide full duplex connectivity to host devices. C. They are used as routers between LANs in a wireless network. D. They are used to physically connect host devices to the wireless network. Correct Answer: A Section: (none) Explanation QUESTION 675 Which two commands must you apply router to configure it as a router-on-a-stick (Choose two.) A. vtp domain
- 345. B. encapsulation C. vtp transparent D. spanning-tree portfast E. ip address Correct Answer: CD Section: (none) Explanation QUESTION 676 In which network topology does each network devices have a direct have physical connection to every other device? A. mesh B. point-to-multipoint C. star D. bus Correct Answer: A Section: (none) Explanation QUESTION 677 Which component of an Ethernet frame supports error detection? A. Ether Type B. preamble C. frame check sequence D. 802 1Q tag Correct Answer: C Section: (none) Explanation QUESTION 678 Which Statement describes the action of the ip helper-address command? A. relays a DHCP request across networks B. assigns an IP address to a host C. resolves an IP address from a DNS server D. resolves an IP address overlapping issue Correct Answer: A Section: (none) Explanation QUESTION 679 Which two ACL types support IP access List Entry Sequence Numbering? (Choose two.) A. dynamic B. named C. firewall D. standard
- 346. E. reflexive Correct Answer: BE Section: (none) Explanation QUESTION 680 Refer to the exhibit. If Host A pings Host B which statement about the ping is true? A. The ping packet includes both the destination MAC address and the source address B. The router looks up the destination IP network of the ping in its MAC address C. Host A encapsulates the packet within a frame before sending D. Host A sends the packet one byte at a time Correct Answer: B Section: (none) Explanation Explanation/Reference: QUESTION 681 Which command or command sequence do you enter to install a default route into a router that is configured with the no ip routing command? A. router rip ip default-gateway B. ip default-network C. ip default-gateway D. ip route 0.0.0.0 0.0.0.0 Correct Answer: D Section: (none) Explanation QUESTION 682 Which two syslog configuration commands do you use to log warnings to the syslog server? (Choose two.) A. logging trap level alerts B. logging trap level notice C. logging trap level error D. logging trap level informational E. logging trap level critical Correct Answer: AD Section: (none)
- 347. Explanation QUESTION 683 Under which circumstance should a network administrator implement only outgoing NAT towards an ISP? A. when traffic that originates outside the network must be routed to internal hosts B. when traffic that originates inside the network must be routed to internal hosts C. when the network has few public IP addresses and many private IP addresses that require outside access D. when the network must route UDP traffic Correct Answer: A Section: (none) Explanation QUESTION 684 Refer to the exhibit. Router R1 produced this partial output running on a current IOS. Which two statements about R1 and its network environment are true? (Choose two.) A. R1 has learned at least one network via routing protocols. B. R1 has a network environment that supports a maximum of 16 hosts. C. R1 has a maximum of two connected subnets including local route. D. R1 has learned a maximum of four networks via routing protocols. E. R1 has a combination of local and connected routes totaling two subnets. Correct Answer: CE Section: (none) Explanation Explanation/Reference: QUESTION 685 In which two scenarios do you implement private IPv4 IP addresses? (Choose two.) A. to connect network equipment between different IDFs B. on the webmail portal of an organization C. for the VPN solution that end users use to connect to the local network D. on an application server that connects to a local database server E. on the connection that a mobile device uses for application updates Correct Answer: BE Section: (none) Explanation QUESTION 686 Which two IPv6 multicast groups are joined when an IPv6 address is configure on an interface? A. FF02::1
- 348. B. FF80 6 C. FF80::5 D. 2002: 5 E. FF02::2 Correct Answer: AE Section: (none) Explanation QUESTION 687 Which two characteristics of plenum cable are true? (Choose two ) A. It is more fire-resistant than nonplenum cable. B. It requires additional safety precautions when installed above a drop down ceiling. C. When it bums, it may release more toxins than nonplenum cable. D. It is less fire-resistant than nonplenum cable. E. It can be installed above a drop-down ceiling without additional safety precautions. Correct Answer: AB Section: (none) Explanation QUESTION 688 Which statement about port security on a trunk link is true? A. It is not supported B. It error-disables the port after 10 MAC addresses are statically configured C. When it is enabled, it disables the native VLAN configuration D. By default, it shuts down the port rt it learns more than one MAC address. Correct Answer: B Section: (none) Explanation QUESTION 689 Which command do you enter to assign all untagged packets on a trunk to VLAN 999? A. switchport trunk native vlan 999 B. switchport trunk allowed vlan add 999 C. switchport trunk pruning vlan add 999 D. switchport trunk allowed vlan 999 Correct Answer: A Section: (none) Explanation QUESTION 690 Which three values must you specify to resequence an IP access list? (Choose three ) A. starting sequence number B. interface C. ending D. dynamic access list number
- 349. E. increment F. access list name Correct Answer: ACF Section: (none) Explanation QUESTION 691 How does an access port configured for VLAN 10 handle an incoming packet within an 802. 1q tag for VLAN 2? A. It processes the packets and places it in a queue for future delivery B. It dynamically configures the port to accept on VLAN 2. C. It forwards the packet to port on VLAN 2. D. It adds VLAN to the VLAN database. E. It drops the packets. Correct Answer: E Section: (none) Explanation QUESTION 692 For which two reasons might you choose to configure dynamic routing instead of static routing on a router? (Choose two.) A. The router needs access only to a single default route. B. The network is growing intermittently. C. The router is part of a stub network. D. Dynamic routing requires less router configuration throughout the network than static routing. E. Dynamic routing updates are more secure than static routing updates. Correct Answer: DE Section: (none) Explanation QUESTION 693 Which two statements about IPv6 SLAAC are true? (Choose two.) A. The host uses the EUI-64 algorithm to calculate the first 64 bits of the destination IPv6 address from the MAC address B. It is incompatible with DHCP. C. The host sends a router advertisement message to begin the SLAAC process D. It has a built-in mechanism to identify duplicate IP addresses on the network. E. The default gateway of the host is configured during the SLAAC process Correct Answer: CD Section: (none) Explanation QUESTION 694 All protocols on a network are using their default administrator distances with no redistribution. In which two different ways can you modify them OSPF and RlPv2 learned routes are preferred over EIGRP- learned routes? (Choose two.)
- 350. A. Change the EIGRP administrative distance to 100. B. Change the OSPF administrative distance to 5. C. Change the RIP administrative distance to 70. D. Change the RIP administrative distance to 100. E. Change the EIGRP administrative distance to 70. Correct Answer: AD Section: (none) Explanation QUESTION 695 Which two statements about administrative distance are true? (Choose two) A. It identifies the routing protocol priority B. The metric uses the administrative distance to calculate a path C. The metric is used to determine which administer D. The metric is calculated independently of the administrative distance is selected from the routing table. E. It identifies the metric used for path calculation. Correct Answer: BE Section: (none) Explanation QUESTION 696 Refer to the exhibit. You ping a remote device by name from a router, and the ping operation returns this response. What are two reasons for this problem? (Choose two) A. The DNS server database does not include a record for the name. B. The router is blacklisted by the DNS server C. A firewall blocked the ping D. Only one DNS server is configured on the router E. An ACL on the router blocked the ping Correct Answer: CD Section: (none) Explanation Explanation/Reference: QUESTION 697 Which command can you enter in ROMmon to bypass the password in the router startup configuration? A. config-register 0x2102 B. confreg 0x2142 C. reset D. configure terminal Correct Answer: A Section: (none) Explanation
- 351. QUESTION 698 For which reason is a DHCP client unable to reach a host in a different subnet? A. DNS lookup has been disabled on the gateway router. B. The client is connected to a switch in the same VLAN as its gateway router. C. The client has been configured with only one DNS server. D. The client and its gateway router have been assigned different subnet masks. Correct Answer: D Section: (none) Explanation QUESTION 699 Which IPv4 address type can reach each node on a network? A. anaycast B. unicast C. multicast D. broadcast Correct Answer: B Section: (none) Explanation QUESTION 700 Which MTU size can cause a baby gaint error? A. 1600 B. 1618 C. 1600 D. 9216 Correct Answer: B Section: (none) Explanation QUESTION 701 What is the defining characteristic of IPv4 multicast traffic? A. Multiple sources send traffic to all destinations on the local network. B. A single source sends traffic to a group of destinations. C. A single source sends traffic to a single destination. D. A single source sends traffic to all destinations on the local network. Correct Answer: B Section: (none) Explanation QUESTION 702 Which two conditions must be met before you can perform the password recovery process on a Cisco router? (Choose two)
- 352. A. You must have physical access to the device. B. You must be able establish a Telnet connection to the device. C. You must connect the console to the router with a straight-through cable D. You must connect the console to the router with a crossover cable E. You must connect the console to the router with a rollover cable Correct Answer: AE Section: (none) Explanation QUESTION 703 Which two management protocols operate over TCP? (Choose two) A. FTP B. CDP C. SNMP D. SCP E. TFTP F. NTP Correct Answer: AC Section: (none) Explanation QUESTION 704 You recently applied a common configuration to several PCs on different VLANs. The PCs are connected to the same switch with a router-on-a-stick but users report that the PCs cannot ping one another. Which two are possible reasons for the problem? (Choose two.) A. The access ports on the PCs are misconfigured B. The trunking protocol is configured incorrectly on the router subinterfaces C. The VLAN is configured incorrectly on the router subinterfaces D. The ip default-network command is misconfigured on the router E. The native VLAN on the router is misconfigured. Correct Answer: AB Section: (none) Explanation QUESTION 705 Which three statements about a mesh topology are true? (Choose Three) A. Every core device is connected to a distribution device. B. Every upstream distribution device is connected to an access switch C. Each access switch must be connected to exactly one upstream distribution device. D. Each access switch must be connected to at least one upstream distribution device and at least one core device D E. Each distribution device is connected to exactly one core device. F. Each access switch must be connected to at least two upstream distribution devices Correct Answer: ABF Section: (none) Explanation
- 353. QUESTION 706 Refer to the exhibit. Which utility is used to test DNS connectivity on each device on the given network? A. ipconfig B. ping C. show interfaces D. show hosts Correct Answer: B Section: (none) Explanation Explanation/Reference: QUESTION 707 Which two subnets are reserved for private use? (Choose two) A. 172.16.0 0/11 B. 172.16.0.0/12 C. 172.32.0.0/19 D. 192.168.0.0/15 E. 192.168.0.0/16 Correct Answer: BE Section: (none) Explanation QUESTION 708 Refer to the exhibit. Which command is entered to generate this output? A. logging history 6 B. logging console 6 C. logging facility sys9 D. service sequence-numbers Correct Answer: B Section: (none) Explanation Explanation/Reference: QUESTION 709
- 354. From which numeric range can a standard VLAN D be assigned? A. 1- 1001 B. 1 - 1006 C. 1 - 4094 D. 1006-4094 Correct Answer: B Section: (none) Explanation QUESTION 710 Which step is first in the DHCP process between a DHCP client and a DHCP server? A. The client sends a DHCP Discover packet to the server. B. The server sends a DHCP Offer packet to the client. C. The client sends a DHCP Request packet to the server. D. The server sends a DHCP Ack packet to the client. Correct Answer: A Section: (none) Explanation QUESTION 711 How does a switch with the default configuration respond when the destination MAC address of an incoming frame is missing from the switch lookup table? A. The switch floods the frame out all ports except the receiving port B. The switch sends a discovery packet to all directly-connected switches C. The switch queues a connected router for the MAC address. D. The switch discards the frame Correct Answer: A Section: (none) Explanation QUESTION 712 Which two statements about prefixes m a routing table are true? (Choose two) A. The router prefers prefixes that have more bit positions for the host than for the network. B. The router prefers the prefix that includes the most 0 bits in the subnet mask. C. The router prefers longer prefixes over shorter prefixes. D. The router prefers shorter prefixes over longer prefixes. E. The router prefers the prefix that includes the most 1 bits in the subnet mask. Correct Answer: CE Section: (none) Explanation QUESTION 713 Which condition is most important to support the use of syslog messages for troubleshooting? A. Messages are logged to a UNIX-based server.
- 355. B. Messages are logged to a Cisco UCS Server. C. The router has a large internal buffer space. D. NTP is in use to ensure accurate timestamps. Correct Answer: D Section: (none) Explanation QUESTION 714 Which two steps are part of the IPv6 SLAAC address configuration process? (Choose two ) A. The host uses the EUI-64 algorithm to calculate the first 64 bits of the destination IPv6 address B. The client performs duplicate address detection C. The router sends a solicitation message. D. The host sends a solicitation message E. The host combines the MAC addresses of the host and the router to generate a global unicast message. Correct Answer: AE Section: (none) Explanation QUESTION 715 Which two commands do you use to identify the ports that are assigned to VLAN 250? (Choose two) A. show vlan id 250 B. show vlan name 250 C. show vlan brief D. show vlan private-vlan E. show vlan port provisioning Correct Answer: AC Section: (none) Explanation QUESTION 716 Which two commands must you apply to a router to configure it as a router-on-a-stick? (Choose two) A. vtp transparent B. encapsulation C. ip address D. spanning-tree portfast E. vtp domain Correct Answer: BC Section: (none) Explanation QUESTION 717 Which statement about the dynamically-teamed MAC address feature is true? A. Individual ports are restricted to 10 dynamically-learned addresses B. After the switch is reloaded, the address table is empty until ingress traffic arrives on the port
- 356. C. A minimum number of secure MAC addresses must be filled dynamically. D. Ports can dynamically learn MAC addresses from disconnected devices. Correct Answer: B Section: (none) Explanation QUESTION 718 Which route will not be entered into the routing table of a neighboring router? A. R 192.168.8.0/24 [120/1] via 192.168.2.2, 00:00:10, Serial0 B. R 192.168.11.0/24 [120/7] via 192.168.9.1, 00:00:03, Serial1 C. C 192.168.1.0/24 is directly connected, Ethernet0 D. R 192.168.5.0/24 [120/15] via 192.168.2.2, 00:00:10, Serial0 Correct Answer: D Section: (none) Explanation Explanation/Reference: Explanation: The route 192.168.5.0/24 currently has the metric of 15 so this router will add 1 hop count before sending out to its neighboring router. With RIP, a metric of 16 means that network is down -> it will not be installed in the routing table of the neighboring router. QUESTION 719 Drag and Drop Question Drag and drop the OSI model layers from the left onto the correct TCP/IP model layers on the right. Select and Place: Correct Answer: Section: (none) Explanation
- 357. Explanation/Reference: QUESTION 720 Drag and Drop Question Refer to the exhibit. Drag and drop the TCP header filed from the left into the correct positions on the right. Select and Place: Correct Answer:
- 358. Section: (none) Explanation Explanation/Reference: QUESTION 721 Drag and Drop Question Drag and drop the logging types from the left onto the correct descriptions on the right. Not all togging types are used. Select and Place: Correct Answer: Section: (none) Explanation Explanation/Reference: Explanation: Deletes old log messages to prevent the RAM consumption from exceeding a specified limit. Displays logs to users who are physically connected to the device = console logging Displays logs to users who are remotely connected to the device QUESTION 722 Drag and Drop Question
- 359. Drag and drop the steps in the frame-rewrite process from the left into the correct sequence on the right: Select and Place: Correct Answer: Section: (none) Explanation Explanation/Reference:
- 360. QUESTION 723 Drag and Drop Question Drag and drop the routing protocols from the left onto the default administrative distances on the right. Select and Place: Correct Answer: Section: (none) Explanation Explanation/Reference: QUESTION 724 Drag and Drop Question A host is send no packets to a router. Drag and drop the steps in the packet-handling process from the left in to the correct sequence on the right. Select and Place:
- 361. Correct Answer: Section: (none) Explanation Explanation/Reference: QUESTION 725 Drag and Drop Question Drag and drop the DNS-lookup configuration commands from the left on to the correct effects on the right. Select and Place:
- 362. Correct Answer: Section: (none) Explanation Explanation/Reference: QUESTION 726 Drag and Drop Question Drag and drop the VLAN port membership modes from the left onto the correct descriptions on the right. Select and Place:
- 363. Correct Answer: Section: (none) Explanation Explanation/Reference: QUESTION 727 Drag and Drop Question Drag and drop the features from the left onto the wireless components that support them on the right. Select and Place:
- 364. Correct Answer: Section: (none) Explanation Explanation/Reference: QUESTION 728 Drag and Drop Question Drag and drop the address blocks from the left onto the correct address types on the right Select and Place:
- 365. Correct Answer: Section: (none) Explanation Explanation/Reference: QUESTION 729 Drag and Drop Question Drag and drop the cable types from the left onto the correct descriptions on the right. Select and Place:














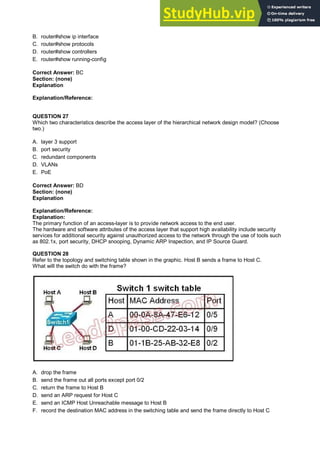







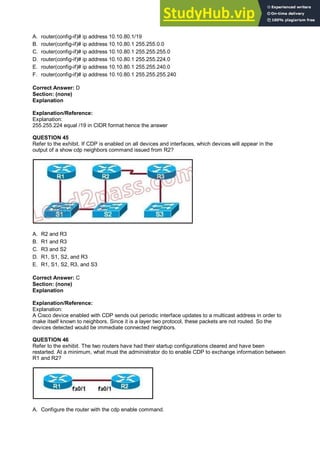

































![Correct Answer: C
Section: (none)
Explanation
Explanation/Reference:
QUESTION 103
Which option is a valid IPv6 address?
A. 2001:0000:130F::099a::12a
B. 2002:7654:A1AD:61:81AF:CCC1
C. FEC0:ABCD:WXYZ:0067::2A4
D. 2004:1:25A4:886F::1
Correct Answer: D
Section: (none)
Explanation
Explanation/Reference:
Explanation:
http://www.ipv6.com/articles/general/IPv6-Addressing.htm
IPv6 Address Notation
IPv6 addresses are denoted by eight groups of hexadecimal quartets separated by colons in between
them.
Following is an example of a valid IPv6 address:
2001:cdba:0000:0000:0000:0000:3257:9652
Any four-digit group of zeroes within an IPv6 address may be reduced to a single zero or altogether
omitted.
Therefore, the following IPv6 addresses are similar and equally valid:
2001:cdba:0000:0000:0000:0000:3257:9652
2001:cdba:0:0:0:0:3257:9652
2001:cdba::3257:9652
The URL for the above address will be of the form:
http://[2001:cdba:0000:0000:0000:0000:3257:9652]/
QUESTION 104
What is the purpose of the switchport command?
Switch(config-if)# switchport port-security maximum 1
Switch(config-if)# switchport port-security mac-address 0018.DE8B.4BF8
A. It ensures that only the device with the MAC address 0018.DE8B.4BF8 will be able to connect to the
port that is being configured.
B. It informs the switch that traffic destined for MAC address 0018.DE8B.4BF8 should only be sent to the
port that is being configured.
C. It will act like an access list and the port will filter packets that have a source or destination MAC of
0018.DE8B.4BF8.
D. The switch will shut down the port of any traffic with source MAC address of 0018.DE8B.4BF8.
Correct Answer: A
Section: (none)
Explanation
Explanation/Reference:
QUESTION 105
Refer to the exhibit. A network administrator is troubleshooting a connectivity problem on the serial
interfaces. The output from the show interfaces command on both routers shows that the serial interface is](https://image.slidesharecdn.com/00-105interconnectingcisconetworkingdevicespart1icnd1-230807160856-f59274f2/85/00-105-Interconnecting-Cisco-Networking-Devices-Part-1-ICND1-pdf-56-320.jpg)








![Correct Answer: C
Section: (none)
Explanation
Explanation/Reference:
Explanation:
When configuring OSPF, the mask used for the network statement is a wildcard mask similar to an access
list. In this specific example, the correct syntax would have been "network 10.0.0.0 0.0.0.255 area 0."
QUESTION 121
Which statement is true?
A. An IPv6 address is 64 b long and is represented as hexadecimal characters.
B. An IPv6 address is 32 b long and is represented as decimal digits.
C. An IPv6 address is 128 b long and is represented as decimal digits.
D. An IPv6 address is 128 b long and is represented as hexadecimal characters.
Correct Answer: D
Section: (none)
Explanation
Explanation/Reference:
QUESTION 122
What information does a router running a link-state protocol use to build and maintain its topological
database? (Choose two)
A. hello packets
B. SAP messages sent by other routers
C. LSAs from other routers
D. beacons received on point-to-point links
E. routing tables received from other link-state routers
F. TTL packets from designated routers
Correct Answer: AC
Section: (none)
Explanation
Explanation/Reference:
QUESTION 123
ROUTER# show ip route
192.168.12.0/24 is variably subnetted, 9 subnets, 3 masks
C 192.168.12.64 /28 is directly connected, Loopback1
C 192.168.12.32 /28 is directly connected, Ethernet0
C 192.168.12.48 /28 is directly connected, Loopback0
O 192.168.12.236 /30 [110/128] via 192.168.12.233, 00:35:36, Serial0 C
192.168.12.232 /30 is directly connected, Serial0
O 192.168.12.245 /30 [110/782] via 192.168.12.233, 00:35:36, Serial0 O
192.168.12.240 /30 [110/128] via 192.168.12.233, 00:35:36, Serial0 O
192.168.12.253 /30 [110/782] via 192.168.12.233, 00:35:37, Serial0 O
192.168.12.249 /30 [110/782] via 192.168.12.233, 00:35:37, Serial0 O
192.168.12.240/30 [110/128] via 192.168.12.233, 00:35:36, Serial 0
To what does the 128 refer to in the router output above?
A. OSPF cost
B. OSPF priority](https://image.slidesharecdn.com/00-105interconnectingcisconetworkingdevicespart1icnd1-230807160856-f59274f2/85/00-105-Interconnecting-Cisco-Networking-Devices-Part-1-ICND1-pdf-65-320.jpg)












![utilizes event-triggered updates (only sends update when a change occurs) ->
QUESTION 146
Refer to the exhibit. The network is converged.After link-state advertisements are received from
Router_A, what information will Router_E contain in its routing table for the subnets 208.149.23.64 and
208.149.23.96?
A. 208.149.23.64[110/13] via 190.173.23.10, 00:00:07, FastEthemet0/0 208.149.23.96[110/13] via
190.173.23.10, 00:00:16, FastEthemet0/0
B. 208.149.23.64[110/1] via 190.172.23.10, 00:00:07, Serial1/0 208.149.23.96[110/3] via 190.173.23.10,
00:00:16, FastEthemet0/0
C. 208.149.23.64[110/13] via 190.173.23.10, 00:00:07, Serial1/0 208.149.23.96[110/13] via
190.173.23.10,
00:00:16, Serial1/0 208.149.23.96[110/13] via 190.173.23.10, 00:00:16, FastEthemet0/0
D. 208.149.23.64[110/3] via 190.172.23.10, 00:00:07, Serial1/0 208.149.23.96[110/3] via 190.173.23.10,
00:00:16, Serial1/0
Correct Answer: A
Section: (none)
Explanation
Explanation/Reference:
Explanation:
Router_E learns two subnets subnets 208.149.23.64 and 208.149.23.96 via Router_A through
FastEthernet interface. The interface cost is calculated with the formula 108 / Bandwidth. For FastEthernet
it is 108 / 100 Mbps = 108 / 100,000,000 = 1. Therefore the cost is 12 (learned from Router_A) + 1 = 13 for
both subnets ->
The cost through T1 link is much higher than through T3 link (T1 cost = 108 / 1.544 Mbps = 64; T3 cost =
108 / 45 Mbps = 2) so surely OSPF will choose the path through T3 link -> Router_E will choose the path
from Router_A through FastEthernet0/0, not Serial1/0. In fact, we can quickly eliminate answers B, C and
D because they contain at least one subnet learned from Serial1/0 -> they are surely incorrect.
QUESTION 147
What information can be used by a router running a link-state protocol to build and maintain its topological
database? (Choose two.)
A. hello packets
B. SAP messages sent by other routers
C. LSAs from other routers
D. beacons received on point-to-point links](https://image.slidesharecdn.com/00-105interconnectingcisconetworkingdevicespart1icnd1-230807160856-f59274f2/85/00-105-Interconnecting-Cisco-Networking-Devices-Part-1-ICND1-pdf-78-320.jpg)












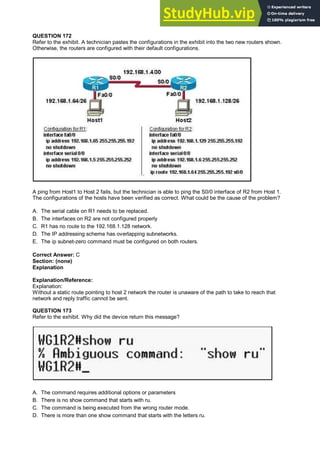

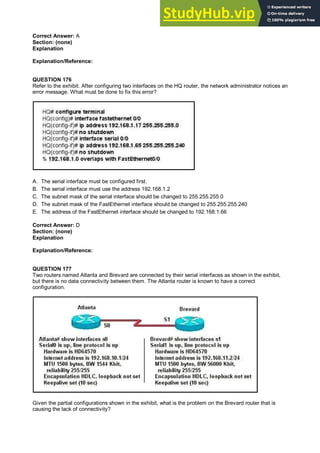


![not be entered into the routing table of a neighboring router?
A. R 192.168.8.0/24 [120/1] via 192.168.2.2, 00:00:10, Serial0
B. R 192.168.11.0/24 [120/7] via 192.168.9.1, 00:00:03, Serial1
C. C 192.168.1.0/24 is directly connected, Ethernet0
D. R 192.168.5.0/24 [120/15] via 192.168.2.2, 00:00:10, Serial0
Correct Answer: D
Section: (none)
Explanation
Explanation/Reference:
Explanation:
The route 192.168.5.0/24 currently has the metric of 15 so this router will add 1 hop count before sending
out to its neighboring router. With RIP, a metric of 16 means that network is down -> it will not be installed
in the routing table of the neighboring router.
QUESTION 184
Refer to Exhibit. Based on the network shown in the graphic which option contains both the potential
networking problem and the protocol or setting that should be used to prevent the problem?
A. routing loops, hold down timers
B. switching loops, split horizon
C. routing loops, split horizon
D. switching loops, VTP
E. routing loops, STP
F. switching loops, STP
Correct Answer: F
Section: (none)
Explanation
Explanation/Reference:
QUESTION 185
If all OSPF routers in a single area are configured with the same priority value, what value does a router
use for the OSPF router ID in the absence of a loopback interface?
A. the IP address of the first Fast Ethernet interface
B. the IP address of the console management interface
C. the highest IP address among its active interfaces
D. the lowest IP address among its active interfaces
E. the priority value until a loopback interface is configured](https://image.slidesharecdn.com/00-105interconnectingcisconetworkingdevicespart1icnd1-230807160856-f59274f2/85/00-105-Interconnecting-Cisco-Networking-Devices-Part-1-ICND1-pdf-96-320.jpg)






















































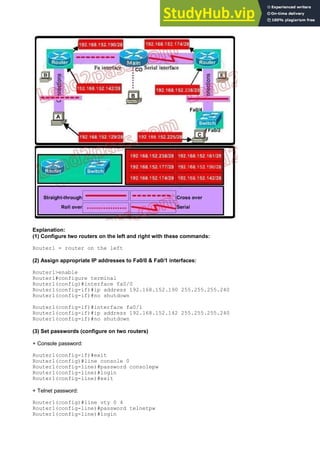
































![We cannot find a default route on R1 (something like this: S* 0.0.0.0/0 [1/0] via 209.165.201.2) so maybe
R1 was not configured with a default route. We can check with the “show running-config” on R1:
We need a default route (like “ip route 0.0.0.0 0.0.0.0 209.165.201.2”) but we cannot find here so we can
conclude R1 was not be configured with a default route pointing to the ISP router.
QUESTION 316
Hotspot Question - RIPv2 Troubleshooting I
Scenario:
You work for a company that provides managed network services, and of your real estate clients running a
small office is experiencing network issues, Troubleshoot the network issues.
Router R1 connects the main office to internet, and routers R2 and R3 are internal routers
NAT is enabled on Router R1.
The routing protocol that is enable between routers R1, R2, and R3 is RIPv2.
R1 sends default route into RIPv2 for internal routers to forward internet traffic to R1.
Server1 and Server2 are placed in VLAN 100 and 200 respectively, and dare still running router on stick
configuration with router R2.](https://image.slidesharecdn.com/00-105interconnectingcisconetworkingdevicespart1icnd1-230807160856-f59274f2/85/00-105-Interconnecting-Cisco-Networking-Devices-Part-1-ICND1-pdf-184-320.jpg)


















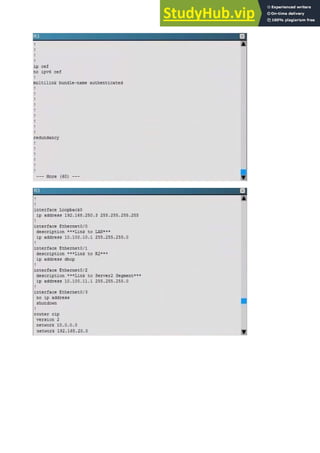




























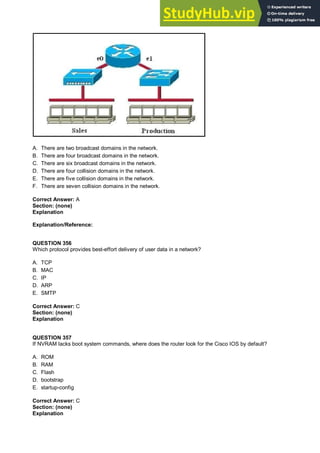



















































![A. The router disconnects the user session if it is inactive for 30 minutes
B. The router maintains a user session indefinitely after it is active for 30 mins
C. The router disconnects a user session if it is inactive for 30 seconds
D. The router maintains a user session indefinitely after it is active for 30 seconds.
Correct Answer: A
Section: (none)
Explanation
Explanation/Reference:
Explanation:
The "exec-timeout" command is used to configure the inactive session timeout on the console port or the
virtual terminal. The syntax of this command is:
exec-timeout minutes [seconds]
Therefore we need to use the "exec-timeout 30" command to set the user inactivity timer to 30 minutes.
To set the user inactivity timer to 30 seconds we use the "exec-timeout 0 30".
QUESTION 516
Which statement is true about port-security violations is true?
A. When a violation occurs on a switch port in restrict mode, the switch port continues to accept traffic
from unknown MAC address until the administrator manually disables it.
B. When a violation occurs on a switch port in protect mode, it sends a syslog notification message
C. A port In the err-disabled state must be re-enabled manually, if recovery is disabled
D. When a switch port is in protect mode, it allows traffic from unknown MAC address until it has learned
the maximum allowable number of MAC addresses
Correct Answer: C
Section: (none)
Explanation
QUESTION 517
Which statement is true about static and dynamic routing is true?
A. Only static routes are shared between connected interfaces
B. Dynamic routing is more scalable than static routing
C. Only dynamic routes are secure
D. Static routing is easier to maintain in a large network than dynamic routing.
Correct Answer: B
Section: (none)
Explanation
QUESTION 518
Which metric or metrics does RIP use to determine the routing table metric for a route?
A. Bandwidth and delay
B. Hop count
C. Bandwidth and hop count
D. Bandwidth
Correct Answer: B
Section: (none)
Explanation](https://image.slidesharecdn.com/00-105interconnectingcisconetworkingdevicespart1icnd1-230807160856-f59274f2/85/00-105-Interconnecting-Cisco-Networking-Devices-Part-1-ICND1-pdf-284-320.jpg)







































































![C. A minimum number of secure MAC addresses must be filled dynamically.
D. Ports can dynamically learn MAC addresses from disconnected devices.
Correct Answer: B
Section: (none)
Explanation
QUESTION 718
Which route will not be entered into the routing table of a neighboring router?
A. R 192.168.8.0/24 [120/1] via 192.168.2.2, 00:00:10, Serial0
B. R 192.168.11.0/24 [120/7] via 192.168.9.1, 00:00:03, Serial1
C. C 192.168.1.0/24 is directly connected, Ethernet0
D. R 192.168.5.0/24 [120/15] via 192.168.2.2, 00:00:10, Serial0
Correct Answer: D
Section: (none)
Explanation
Explanation/Reference:
Explanation:
The route 192.168.5.0/24 currently has the metric of 15 so this router will add 1 hop count before sending
out to its neighboring router. With RIP, a metric of 16 means that network is down -> it will not be installed
in the routing table of the neighboring router.
QUESTION 719
Drag and Drop Question
Drag and drop the OSI model layers from the left onto the correct TCP/IP model layers on the right.
Select and Place:
Correct Answer:
Section: (none)
Explanation](https://image.slidesharecdn.com/00-105interconnectingcisconetworkingdevicespart1icnd1-230807160856-f59274f2/85/00-105-Interconnecting-Cisco-Networking-Devices-Part-1-ICND1-pdf-356-320.jpg)









