2019 - Tech Talk DC - Token-based security for web applications using OAuth2 and OpenID Connect
- 1. TOKEN-BASED SECURITY FOR WEB APPLICATIONS USING OAUTH2 AND OPENID CONNECT Presented by Vladimir Bychkov Email: [email protected] 1 Tech Talk DC 2019
- 2. About Vladimir Bychkov • SOFTWARE CRAFTSMAN AT EASTBANC TECHNOLOGIES • LINKEDIN: WWW.LINKEDIN.COM/IN/BYCHKOFF/ • EMAIL: [email protected] WEBSITE: EASTBANCTECH.COM WEBSITE: WWW.KUBLR.COM
- 3. EastBanc Technologies | Custom Software Development Cutting Edge Software Development. Based in Georgetown. We are hiring! www.eastbanctech.com
- 4. Agenda • AUTHORIZATION FOR WEB APPLICATIONS • OAUTH 2.0 • OPENID CONNECT • DEMO AUTHORIZATION GRANTS (FLOWS) • FEDERATED GATEWAY PATTERN
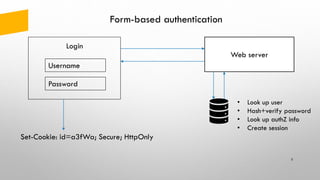
- 5. Form-based authentication 5 Username Password Login Web server Set-Cookie: id=a3fWa; Secure; HttpOnly • Look up user • Hash+verify password • Look up authZ info • Create session
- 6. Modern Application Landscape 6 Browser Mobile Server App Web App Web Service Web Service Web Service Enterprise IdP Social IdP
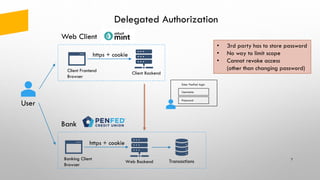
- 7. Delegated Authorization 7 https + cookie Web Client Client Frontend Browser Client Backend User Web Backend Bank https + cookie Banking Client Browser Transactions Username Password Enter PenFed login • 3rd party has to store password • No way to limit scope • Cannot revoke access (other than changing password)
- 8. OAuth 2.0 - Overview • OAUTH 2.0 IS THE INDUSTRY-STANDARD PROTOCOL FOR DELEGATED AUTHORIZATION • PUBLISHED AS IETF RFC6749 IN OCTOBER 2012 • INITIAL PURPOSE – GIVE 3RD PARTY SOFTWARE ACCESS ON USER’S BEHALF • LINGO: • RESOURCE OWNER => USER (HUMAN) • CLIENT => 3RD PARTY SOFTWARE (APP/SERVICE) • AUTHORIZATION SERVER => WEB SERVICE (VERIFIES IDENTITY AND ISSUES TOKENS) • RESOURCE SERVER => WEB SERVICE/API HOSTING PROTECTED RESOURCES • AUTHORIZATION GRANT (FLOW) => STANDARD PROCESS TO OBTAIN USER’S AUTHORIZATION • SCOPE => LEVEL OF ACCESS • CONSENT => USER’S PERMISSION TO GRANT ACCESS • ACESS CODE => TEMP CODE TO OBTAIN ACCESS TOKEN • ACCESS TOKEN => TEMP AND SCOPED CREDENTIALS TO ACCESS USER’S RESOURCES
- 9. OAuth 2.0 – Endpoints (SSL required) • AUTHORIZATION ENDPOINT • USED TO INTERACT WITH THE RESOURCE OWNER AND OBTAIN AN AUTHORIZATION GRANT. THE AUTHORIZATION SERVER MUST FIRST VERIFY THE IDENTITY OF THE RESOURCE OWNER. • TOKEN ENDPOINT • USED BY THE CLIENT TO OBTAIN AN ACCESS TOKEN BY PRESENTING ITS AUTHORIZATION GRANT OR REFRESH TOKEN. • REDIRECTION ENDPOINT (CLIENT)
- 10. OAuth 2.0 - Protocol Flow 10
- 11. OAuth 2.0 - Architecture Resource owner (User) Client (Relying Party - RP) Resource server (Resources) Authorization server (Security Token Service – STS) Token Grant (Credentials) Token
- 12. OAuth 2.0 - Grants Grant type Client type / Use case Client Credentials For clients, such as web services, acting on their own behalf. Authorization code w/ PKCE Intended for traditional web applications with a backend as well as native (mobile or desktop) applications to take advantage of single sign-on via the system browser. Resource Owner Password For trusted native clients where the application and the authorization server belong to the same provider. Implicit Intended for browser-based (JavaScript) applications without a backend. Refresh token A special grant to let clients refresh their access token without having to go through the steps of a code or password grant again. Device code For devices without a browser or with constrained input, such as a smart TV, media console, printer, etc. Token exchange Lets applications and services obtain an access token in delegation and impersonation scenarios.
- 13. OpenID Connect • ID TOKEN (JWT) • DISCOVERY ENDPOINT • USER-INFO ENDPOINT (JSON SCHEMA) • USES OAUTH 2 FLOWS TO OBTAIN ID TOKENS
- 14. JWT – JSON Web Token 14
- 15. OpenID Connect Protocol Suite
- 16. DEMO – Client Credentials Flow https://docs.pivotal.io POST http://localhost:5000/connect/token Authorization: Basic Y2xpZW50OnNlY3JldA== grant_type=client_credentials&scope=api1 1 HTTP/1.1 200 OK Content-Type: application/json; charset=UTF-8 … {"access_token":"eyJhbGciO… 2 GET http://localhost:5001/identity Authorization: Bearer eyJhbGciO… 3 HTTP/1.1 200 OK Content-Type: application/json; charset=UTF-8 … [{"type":"nbf","value":"1531258758"}, … 4
- 17. DEMO – Resource Owner Credentials Flow https://docs.pivotal.io POST http://localhost:5000/connect/token Authorization: Basic cm8uY2xpZW50OnNlY3JldA== grant_type=password&username=alice &password=password&scope=api1 2 HTTP/1.1 200 OK Content-Type: application/json; charset=UTF-8 … {"access_token":"eyJhbGciO… 3 GET http://localhost:5001/identity Authorization: Bearer eyJhbGciO… 4 HTTP/1.1 200 OK Content-Type: application/json; charset=UTF-8 … [{"type":"nbf","value":"1531258758"}, … 5 1 Username Password
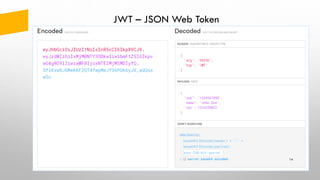
- 18. DEMO – Authorization Code Flow https://docs.pivotal.io GET /Home/Secure 1 HTTP/1.1 302 Found Location: http://localhost:5000/connect/authorize? client_id=mvc &redirect_uri=http//localhost:5002/signin-oidc &response_type=code id_token &scope=openid profile api1 offline_access &response_mode=form_post … 2 GET /connect/authorize?client_id=mvc&… 3 302 /account/login… 302 /account/consent… HTTP/1.1 200 OK … <form method='post' action='http://localhost:5002/signin-oidc’> <input type='hidden' name='code’ value=‘deba7f4c87….’ /> … <script>(function(){document.forms[0].submit();})();</script> 4 POST http://localhost:5000/connect/token client_id=mvc&client_secret=secret &code=deba7f4c87…&grant_type=authorization_code 5 HTTP/1.1 200 OK Content-Type: application/json; charset=UTF-8 … {“id_token”=…, "access_token":"eyJhbGciO…” 6 GET http://localhost:5001/identity Authorization: Bearer eyJhbGciO… 7 HTTP/1.1 200 OK Content-Type: application/json; charset=UTF-8 … [{"type":"nbf","value":"1531258758"}, … 8
- 19. DEMO – Implicit Flow https://docs.pivotal.io
- 20. Authorization Code Interception Attack 20
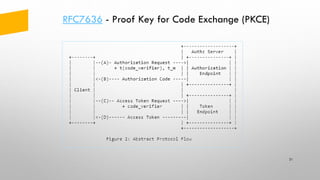
- 21. RFC7636 - Proof Key for Code Exchange (PKCE) 21
- 22. Web Apps – Other security concerns • HTTPS ALL THE WAY! • CROSS-SITE REQUEST FORGERY (CSRF) • ASP.NET CORE 2+ INJECTS ANTIFORGERY TOKENS AUTOMATICALLY WHEN USING TAG HELPERS • BUILT-IN ACTION FILTERS: • VALIDATEANTIFORGERYTOKEN • AUTOVALIDATEANTIFORGERYTOKEN • IGNOREANTIFORGERYTOKEN • CROSS-SITE SCRIPTING (XSS) • VALIDATE USER INPUT (FORMS, QUERY STRING, HTTP HEADERS) • HTML/URL ENCODING
- 23. Web Apps – Other security concerns (cont.) • CROSS-ORIGIN REQUESTS (CORS) • ENABLE CORS AND SET EXPLICIT POLICIES • SECRET/KEY MANAGEMENT AND DATA PROTECTION • OPEN REDIRECTS
- 24. Auth Middleware Federation gateway (Before impl) ASP.NET Core Internet Google Facebook … Azure AD Google Facebook … Azure AD Web Application
- 25. STS Federation gateway (After impl) Internet Google Facebook … Azure AD Google Facebook … Azure AD Internet Auth MiddlewareASP.NET Core Web Application STS Auth MiddlewareASP.NET Core Web Application STS
- 26. THANK YOU VLADIMIR BYCHKOV SOFTWARE CRAFTSMAN [email protected]













![DEMO – Authorization Code Flow
https://docs.pivotal.io
GET /Home/Secure
1
HTTP/1.1 302 Found
Location: http://localhost:5000/connect/authorize?
client_id=mvc
&redirect_uri=http//localhost:5002/signin-oidc
&response_type=code id_token
&scope=openid profile api1 offline_access
&response_mode=form_post …
2
GET /connect/authorize?client_id=mvc&…
3
302 /account/login… 302 /account/consent…
HTTP/1.1 200 OK
…
<form method='post' action='http://localhost:5002/signin-oidc’>
<input type='hidden' name='code’ value=‘deba7f4c87….’ /> …
<script>(function(){document.forms[0].submit();})();</script>
4
POST http://localhost:5000/connect/token
client_id=mvc&client_secret=secret
&code=deba7f4c87…&grant_type=authorization_code
5
HTTP/1.1 200 OK
Content-Type: application/json; charset=UTF-8
…
{“id_token”=…, "access_token":"eyJhbGciO…”
6
GET http://localhost:5001/identity
Authorization: Bearer eyJhbGciO…
7
HTTP/1.1 200 OK
Content-Type: application/json; charset=UTF-8
…
[{"type":"nbf","value":"1531258758"}, …
8](https://image.slidesharecdn.com/2019-techtalkdc-token-basedsecurityforwebapplicationsusingoauth2andopenidconnect-191031194242/85/2019-Tech-Talk-DC-Token-based-security-for-web-applications-using-OAuth2-and-OpenID-Connect-18-320.jpg)