A Secure Cloud Gateway based upon XML and Web Services
- 1. A Secure Cloud Gateway based upon XML and Web Services PhD Symposium, ECOWS ’11 2011-09-16 Sebastian Graf supervised by Prof. Marcel Waldvogel Distributed Systems Group University of Konstanz [email protected] 1 Sonntag, 18. September 11
- 2. Problem Statement What approaches support secure storage of data in the cloud ? 2 Sonntag, 18. September 11
- 3. Problem Statement What approaches support secure storage of data in the cloud ? Availability: Integrity: • access to data • System Integrity • no unauthorized deletion • Data Integrity Accountability: Confidentiality: • traceability of changes • closure of private data G. Stoneburner: Underlaying technical models for information technology security National Institute of Standards and Technology 2 Sonntag, 18. September 11
- 4. Security and Cloud Storage Web Web Services Services Integrity Auditing Rev874 Web Web Services Services Rev25 3 Sonntag, 18. September 11
- 5. How to provide… Goals Measurements (Availability Cloud-based Service) R1: How can integrity be ensured Integrity within a distributed environment with focus on fast processing? Security Confidentiality R2: How can key handling be adapted to support collaborative use cases? Accountability R3: How can current versioning approaches be adapted to fit a distributed environment? 4 Sonntag, 18. September 11
- 6. Integrity ‣ Data must be consistent while → in transfer → in process → in storage ‣ Data is handled in decrypted form within client but stored encrypted into the cloud → Consistency check must guard data in all representations 5 Sonntag, 18. September 11
- 7. Dual Integrity Decrypted Data Encrypted Data ‣ Data is wrapped in XML ‣ XML is mapped to pages ‣ Tree-structure to offer ‣ Pages are encrypted recursive checksums ‣ Pages are ordered within hierarchy to offer versioning and consistency checks 6 Sonntag, 18. September 11
- 8. Decrypted Integrity Check <?xml version="1.0" encoding="UTF-8"?> ... <country id='f0_404' 3 lr9c name='Switzerland' capital='f0_1627' population='7207060' sl24 19ak datacode='SZ' 4 7 total_area='41290' ...> ... </country> 5 6 67 8 9 ... 56bd 234g mbkl 1117 345v 3 lr9c 3 997d 19ak 8h5y 19ak sl24 4 7 4 7 5 6 67 8 9 5 6 8 9 56bd 234g mbkl 1117 345v 56bd 234g 1117 345v 7 Sonntag, 18. September 11
- 9. Decrypted Integrity Check <?xml version="1.0" encoding="UTF-8"?> ... <country id='f0_404' 3 lr9c name='Switzerland' capital='f0_1627' population='7207060' sl24 19ak datacode='SZ' 4 7 total_area='41290' ...> ... </country> 5 6 67 8 9 ... 56bd 234g mbkl 1117 345v 3 lr9c 3 997d 19ak 8h5y 19ak sl24 4 7 4 7 5 6 67 8 9 5 6 8 9 56bd 234g mbkl 1117 345v 56bd 234g 1117 345v R. Merkle: A digital signature based on a conventional encryption function Advances in Cryptology, ’86 7 Sonntag, 18. September 11
- 10. Decrypted Integrity Check 5e+05 ! Merkle−Hash ! ! ! ! Incremental Checksum ! ! No Hashing ! ! ! ! ! ! 5e+04 ! ! ! ! Time[ms] 5e+03 ! ! 5e+02 ! 5e+01 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 xmark factor[f*0.001] 8 Sonntag, 18. September 11
- 11. Decrypted Integrity Check 5e+05 ! Merkle−Hash ! ! ! ! Incremental Checksum ! ! No Hashing ! ! ! ! ! ! 5e+04 ! ! ! ! Time[ms] 5e+03 ! ! 5e+02 ! 5e+01 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 xmark factor[f*0.001] S. Graf, S. K. Belle, and M. Waldvogel, Rolling boles, optimal XML structure integrity for updating operations, in Poster on the 20th International Conference on World Wide Web 8 Sonntag, 18. September 11
- 12. Encrypted Integrity Check Uber Uber Indirect Indirect Indirect Indirect Indirect Indirect RevRoot,0 RevRoot,0 RevRoot,1 Indirect Indirect Indirect Name Name Name Indirect Indirect Indirect Node,1 Node,2 Node,1 Node,2 Node,1 Node,3 J. Bonwick, M. Ahrens,V. Henson, M. Maybee, and M. Shellenbaum, “The zettabyte file system,” in FAST 2003: 2nd Usenix Conference on File and Storage Technologies. 9 Sonntag, 18. September 11
- 13. Summary of archiving integrity Goals Measurements Integrity Dual Integrity Security ✓ Checks of decrypted data on XML within Treetank ✓ Checks of encrypted data in the cloud and within the transfer based on pages ✓ All integrity structures are persisted 10 Sonntag, 18. September 11
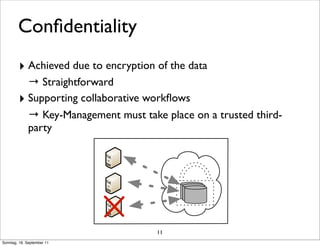
- 14. Confidentiality ‣ Achieved due to encryption of the data → Straightforward ‣ Supporting collaborative workflows → Key-Management must take place on a trusted third- party 11 Sonntag, 18. September 11
- 15. Versakey 23 3 23 3 TEK 2 TEK' 2 1 01 0 01' 0 E0 (010 ) 0 E 010 (T EK ) E23 (T EK 0 ) M. Waldvogel, G. Caronni, D.Sun, N. Weiler, B. Plattner: “The VersaKey framework:Versatile group key management” IEEE Journal on Selected Areas of Communication 1999 12 Sonntag, 18. September 11
- 16. Key Management on the Data DEK 01 DEK 0 01 1 DEK 23 2 Key Manager DEK 23 3 23 DEK 2 3 1 01 0 Sonntag, 18. September 11
- 17. Key Management on the Data DEK 01 DEK 0 01 E0 (010 ) E010 (DEK 0 ) 1 DEK E23 (DEK 0 ) 23 2 Key Manager Key Manager Key Trails DEK 23 23 3 3 23 DEK DEK' E0 (010 ) 2 2 E010 (DEK 0 ) 1 E23 (DEK 0 ) 3 01 0 01' 0 Sonntag, 18. September 11
- 18. Key Management on the Data DEK' 01' E0 (010 ) E010 (DEK 0 ) DEK 0 01 E0 (010 ) E010 (DEK 0 ) 1 DEK' E23 (DEK 0 ) 23 2 E23 (DEK 0 ) Key Manager DEK' 23 3 23 DEK' 2 3 15 01' 0 Sonntag, 18. September 11
- 19. Summary of archiving confidentiality Goals Measurements Confidentiality VersaKey Security ✓ Encryption itself straightforward ✓ Key handling supports changing client-sets ✓ Exposing & supporting versioning ✓ Different handling of keys (within Key Manager) and updates (within the cloud storage) 16 Sonntag, 18. September 11
- 20. Accountability “Accountability is the requirement that actions of an entity may be traced uniquely to that entity.” ‣ Achieved due to versioning the data → Tracing of insertions, deletions and modifications ‣ Together with signatures on the action → Non-Repudiation of modifications G.Stoneburner: Underlaying technical models for information technology security National Institute of Standards and Technology 17 Sonntag, 18. September 11
- 21. Classic Approaches Differential Differential 4 5 3 4 2 4 1 … 0 0 18 Sonntag, 18. September 11
- 22. Classic Approaches Differential Differential 4 5 3 4 2 4 1 … 0 0 Incremental Incremental 4 6 3 5 2 4 1 … 0 0 18 Sonntag, 18. September 11
- 23. Paging the data Uber Uber Indirect Indirect Indirect Indirect Indirect Indirect RevRoot,0 RevRoot,0 RevRoot,1 Indirect Indirect Indirect Name Name Name Indirect Indirect Indirect Node,1 Node,2 Node,1 Node,2 Node,1 Node,3 J. Bonwick, M. Ahrens,V. Henson, M. Maybee, and M. Shellenbaum, “The zettabyte file system,” in FAST 2003: 2nd Usenix Conference on File and Storage Technologies. 19 Sonntag, 18. September 11
- 24. Summary of archiving accountability Goals Measurements Accountability Adaptive Pagelayer ✓ Each modification on the data results in one Security subtree ✓ Versions consists out of modifications & injected full-dumps ✓ Robustness and consistent read-write-effort 20 Sonntag, 18. September 11
- 25. Putting everything together Client Server Treetank PaaS-Implementation XML Data Interf. Storage Data Store node layer Key Trail Propag. Key Trails page layer storage layer Local Keys Key Manager DEK Key Trail Propag. 01 NoSQL File 0 Access Ctrl. Key Mgmt. 21 Sonntag, 18. September 11
- 26. Workflow of Change on Clientset Ext.Tigger Cloud Storage Key Mg 23 3 DEK 2 1 Delete Client "1" 01 0 E0 (010 ) E010 (DEK 0 ) E23 (DEK 0 ) POST Key Trails 22 Sonntag, 18. September 11
- 27. Workflow of Storage Client Cloud Storage Session begin Keycheck Challenge Keycheck Validate Hash H(H(DEK) ⊕ Challenge) Recompute Keys Key Sync [Keys differ] Send Key Trails Data Validate Request Send read/write request Data [Hashs differ] Request resend Session close 23 Sonntag, 18. September 11
- 28. the new insertion operation. Figure 7. Shredding and Serializing of XMark XMark, Time XMark serialize, f=0.1 XMark serialize, f=1.0 XMark shredding, f=0.1 2e+05 5e+04 XMark shredding, f=1.0 [ms] 2e+04 5e+03 0 20 40 60 80 100 revisions 24 Sonntag, 18. September 11 Figure 7 shows the result. The shredding represents the insertion process while the serializing stand
- 29. Figure 8. Performing random insert, Time Random Insert, Time 20000 5000 2000 250 nodes per commit [ms] 500 nodes per commit 1000 nodes per commit 1000 500 200 100 0 200 400 600 800 1000 revisions 25 Sonntag, 18. September 11
- 30. Figure 9. Performing random insert, File Random Insert, Space 2e+06 5e+05 [bytes] 250 nodes per commit 1e+05 500 nodes per commit 1000 nodes per commit 2e+04 5e+03 0 200 400 600 800 1000 revisions 26 Sonntag, 18. September 11
- 31. Next Steps Dual Integrity ✓Implementation of XML-check ‣ Improving performance within cryptographic checksums ‣ Extending with signatures ‣ Introducing page-based integrity-check VersaKey ✓Implementation of encryption ✓Versakey implementation ‣ Access to old revisions within new client-joins 27 Sonntag, 18. September 11
- 32. Next Steps, .cont Versioning ✓Implementation and first results ✓Analysis of read-/write-effort ‣ Working directly on Versioning Framework ✓ Client partly released ✓ Key Management ‣ Server 28 Sonntag, 18. September 11
- 33. Thanks for your attention… Questions? (or even better: Suggestions!) Sebastian Graf Distributed Systems Group University of Konstanz [email protected] 29 Sonntag, 18. September 11
- 34. Publications 1. S.Graf, M.Kramis, M.Waldvogel, "Distributing XML with Focus on Parallel Evaluation" in Proceedings of the 6th Workshop on DBISP2P 2. S. Graf, L. Lewandowski, and M. Waldvogel, “Integrity assurance for RESTful XML,” in Proceedings of the 7th Workshop on Web Information Systems 3. S. Graf, M. Kramis, and M. Waldvogel, “Treetank: Designing a versioned XML storage,” in XMLPrague’11, 2011. 4. S.Graf, V.Zhouldev, L. Lewandowski, and M. Waldvogel, “Hecate, managing authorization with restful xml,” in Proceedings of the 2nd Workshop on RESTful Services, 5. S. Graf, S. K. Belle, and M. Waldvogel, “Rolling boles, optimal XML structure integrity for updating operations,” in Poster on the 20th International Conference on World Wide Web, ser. WWW ‘11.2011 6. Trailing Versioning (joint work with Marc Kramis, in progress) 7. Versakey on distributed storage (in planning) 30 Sonntag, 18. September 11









![Decrypted Integrity Check
5e+05
! Merkle−Hash !
!
!
!
Incremental Checksum !
!
No Hashing !
!
!
!
!
!
5e+04
!
!
!
!
Time[ms]
5e+03
!
!
5e+02
!
5e+01
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19
xmark factor[f*0.001]
8
Sonntag, 18. September 11](https://image.slidesharecdn.com/sebastiangrafphdsymposium-110919074602-phpapp01/85/A-Secure-Cloud-Gateway-based-upon-XML-and-Web-Services-10-320.jpg)
![Decrypted Integrity Check
5e+05
! Merkle−Hash !
!
!
!
Incremental Checksum !
!
No Hashing !
!
!
!
!
!
5e+04
!
!
!
!
Time[ms]
5e+03
!
!
5e+02
!
5e+01
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19
xmark factor[f*0.001]
S. Graf, S. K. Belle, and M. Waldvogel, Rolling boles, optimal XML structure integrity for updating
operations, in Poster on the 20th International Conference on World Wide Web
8
Sonntag, 18. September 11](https://image.slidesharecdn.com/sebastiangrafphdsymposium-110919074602-phpapp01/85/A-Secure-Cloud-Gateway-based-upon-XML-and-Web-Services-11-320.jpg)














![Workflow of Storage
Client Cloud Storage
Session
begin
Keycheck
Challenge
Keycheck Validate
Hash
H(H(DEK) ⊕ Challenge)
Recompute
Keys
Key Sync
[Keys differ]
Send Key Trails
Data Validate
Request
Send read/write request
Data
[Hashs differ]
Request resend
Session
close
23
Sonntag, 18. September 11](https://image.slidesharecdn.com/sebastiangrafphdsymposium-110919074602-phpapp01/85/A-Secure-Cloud-Gateway-based-upon-XML-and-Web-Services-27-320.jpg)
![the new insertion operation.
Figure 7. Shredding and Serializing of XMark
XMark, Time
XMark serialize, f=0.1
XMark serialize, f=1.0
XMark shredding, f=0.1
2e+05
5e+04 XMark shredding, f=1.0
[ms]
2e+04
5e+03
0 20 40 60 80 100
revisions
24
Sonntag, 18. September 11 Figure 7 shows the result. The shredding represents the insertion process while the serializing stand](https://image.slidesharecdn.com/sebastiangrafphdsymposium-110919074602-phpapp01/85/A-Secure-Cloud-Gateway-based-upon-XML-and-Web-Services-28-320.jpg)
![Figure 8. Performing random insert, Time
Random Insert, Time
20000
5000
2000
250 nodes per commit
[ms]
500 nodes per commit
1000 nodes per commit
1000
500
200
100
0 200 400 600 800 1000
revisions
25
Sonntag, 18. September 11](https://image.slidesharecdn.com/sebastiangrafphdsymposium-110919074602-phpapp01/85/A-Secure-Cloud-Gateway-based-upon-XML-and-Web-Services-29-320.jpg)
![Figure 9. Performing random insert, File
Random Insert, Space
2e+06
5e+05
[bytes]
250 nodes per commit
1e+05
500 nodes per commit
1000 nodes per commit
2e+04
5e+03
0 200 400 600 800 1000
revisions
26
Sonntag, 18. September 11](https://image.slidesharecdn.com/sebastiangrafphdsymposium-110919074602-phpapp01/85/A-Secure-Cloud-Gateway-based-upon-XML-and-Web-Services-30-320.jpg)



