Abusing, Exploiting and Pwning with Firefox Add-ons: OWASP Appsec 2013 Presentation
1 like3,608 views
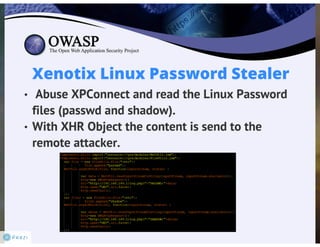
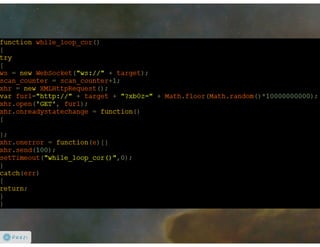
Paper: http://keralacyberforce.in/abusing-exploiting-and-pwning-with-firefox-add-ons/
1 of 44
Downloaded 97 times










































More Related Content
Viewers also liked (18)
More from Ajin Abraham (15)
Ad
Recently uploaded (20)
Ad
