An Adaptive Mobility Based Attack Detection Mechanism to Detect Selective Forwarding Attack in Wireless Sensor Network
- 1. ISSN 2350-1022 International Journal of Recent Research in Mathematics Computer Science and Information Technology Vol. 4, Issue 1, pp: (23-29), Month: April 2017 – September 2017, Available at: www.paperpublications.org Page | 23 Paper Publications An Adaptive Mobility Based Attack Detection Mechanism to Detect Selective Forwarding Attack in Wireless Sensor Network S.K.Shaju1 , R.Isaac Sajan2 , Bibin Christopher3 , Dr.A.J.Deepa4 1 PG Scholar CSE, 2 Research Scholar CSE, 3 Research Scholar, 4 Professor CSE, Ponjesly College of Engineering, Nagercoil, India Abstract: In this paper propose Mobile network based attack detection of Selective Forwarding Attacks in Wireless Sensor Networks. In existing method only used static network and mobility network require high energy and time. So these problems can be overcome by using Mobile network based attack detection. The wireless sensor network has become a hot research area due its wide range of application in military and civilian domain, but as it uses wireless media for communication these are easily prone to security attacks. Selective forwarding attacks are most effective when the attacker is explicitly included on the path of a data flow. Selective forwarding and black hole attacks are very disastrous attacks for sensor networks if used with sinkhole attack because the intruder can drop most of the important packets. Moreover, the technique involves energy efficiency, reliability and scalability. Simulation results demonstrate that our proposed method can accurately detect selective forwarding attacks and identify the compromised sensor nodes. Experimental result show analytically and through simulation experiments that our schemes achieve effective and robust detection capability with reasonable overheads. Keywords: Wireless Sensor Network, Selective Forwarding attack, Reputation System, Packet Dropping, Channel- aware, Routing. I. INTRODUCTION In recent days, wireless sensor network has become an interesting area of research. Where the nodes are free to move anywhere in network. Due to the non-flexibility of wired network the demand of wireless network has increased. When compare to wired network the wireless sensor networks suffers from lot of security problems, due to the open medium, changing of topology structure and distributed architecture. The wireless sensor nodes are communicates through nonlinear channel. Most popular applications of wireless sensor network are weather monitoring (example: temperature sensor), area monitoring, waste water monitoring, industrial monitoring and military application etc. This work, we focus specially on Denial of Service (DoS) attack known as selective forwarding attack and it is otherwise called as gray hole attack. Some of the security measures are not suitable for wireless sensor network reason due to resource wastage of both energy and memory. The wireless sensor nodes uses air as a medium to communicate with the neighbor nodes. As it has the limited transmission range, a sensor nodes transferred the information from source to sink through multi-hop transmission. In the multi-hop transmission the information are first transfer to the nearby neighbor and then the process goes on. Mostly the sensor nodes are placed in unfriendly environment. It is difficult to detect some internal nodes that may react as malicious nodes. Such kind of attack related to it is selective forwarding attack. In the selective forwarding attack the nodes will selectively drops some set of packets during the communication period. The black hole attack is something related to gray hole. In black hole attack the node drop all the packets during the communication period. So that the selective forwarding attack has given a special consideration to detect the malicious nodes. The wireless sensor nodes does has the ability to withstand the failure during the communication, due to the noise in communication medium which result in a great loss of data packets.
- 2. ISSN 2350-1022 International Journal of Recent Research in Mathematics Computer Science and Information Technology Vol. 4, Issue 1, pp: (23-29), Month: April 2017 – September 2017, Available at: www.paperpublications.org Page | 24 Paper Publications In certain cases, the sensor nodes get deep sleep or get in to sleep mode in order to save the power and during that period of time the node cannot send and receive the data. So system has to know the reason for the drop of packet, is due to selectively loss the packet or may be any other reason. But in this paper importance has given to the selective forwarding attack. Where some period of time the malicious nodes may be behaves like black hole attack. And the neighboring nodes will get confused and decide to seek distinct routing path for the transmission. An alternative approach is non- cryptographic detection techniques which provide a reliable mechanism. The non-cryptographic technique is used for detecting gray hole attack or selective forwarding attack by analyzing and monitoring the wireless sensor nodes. Similarly in watch dog technique, neighbor node can monitor whether it has forwarded the packet to correct destination or not. By studying more about the selective forwarding attack, it mainly focus on the error-free wireless channel and dropping of packet due to malicious nodes. The selective forwarding attack is mostly focus on the network layer. This will leads a great loss of data packets in wireless sensor networks. The wireless sensor nodes consists of battery as important component for power source. And the solar panels is used as secondary power supply to the nodes. The energy conservation in a wireless sensor network should be minimized which increases the life-time and can able to provide reliable wireless communication. Next important component in wireless sensor network is storage device. It has only the limited storage capacity. Each node has to collect the information about the neighbor node and uses information to carry out routing very efficient. Synchronization time is also important parameter in wireless sensor network reason as the lack of accuracy in time may significantly reduce the network lifetime. II. RELATED WORK In the CRS-A section, it includes the following sub task as listed below. A. Normal Packet Loss Estimation: In the Wireless Sensor Network, the normal packet loss will occur easily due to the impact of unstable radio environment. Normal packet loss are occur due to the following two aspects as follows. 1) Unstable Radio Link Cause Packet Loss: Due to the poor quality in the radio signal cause the time-varied packet losses. The packet loss rate estimated over a long period of time and the average value shows the time-varied during the evaluation of forwarding behavior. 2) Collision in MAC Layer Cause Packet Loss: The data transmission between two neighbor nodes based on IEEE 802.11 DCF and the MAC layer collision may increase the normal packet loss rate. Since the location of the sensor nodes are static in its location and has fixed number of neighbor nodes. B. Cluster Head Selection: In a Wireless Sensor Network for simplifying the complexity of the operation, cluster are used. The cluster is the collection of limited number of devices or nodes. In a cluster the important aspect is selection of cluster header. The cluster header will have the overall responsibility where it will maintain a table called reputation table. The reputation table includes the reputation value where it help to detect the malicious nodes. The selection of cluster head is an elected node which is very nearer to the base station. And the full control goes to the cluster head which is responsible for transmission of data from source to destination. C. Reputation Evaluation: The reputation evaluation has includes reputation value where the value is initially fixed as 2. The evaluation of reputation score is performed with the help of first-hand reputation score. ri,j 1 (t) = { ( ) ( ) ( ) ( ) ( ) ( ) ( ) ( ) ( ) (1.1) Where, ƛ is a punishment factor and is a adjustment factor, we set ƛ and the function as follows.
- 3. ISSN 2350-1022 International Journal of Recent Research in Mathematics Computer Science and Information Technology Vol. 4, Issue 1, pp: (23-29), Month: April 2017 – September 2017, Available at: www.paperpublications.org Page | 25 Paper Publications If mi,j(t) pi,j(t).si,j(t), the sampling test is acceptable. If pi,j(t).si,j(t) < mi,j(t), the sampling test is normal. When mi,j(t) ( ) the sampling test is misbehave In the reputation table, entry has been done through the reputation evaluation as the Equation (1.1) has shown above. If the node get loss the packet during the communication the reputation score has been get decreased. Based on above condition and if the packet get transfer successfully means the reputation score get increased. Normally the reputation value is range from 0 to 255. D. Reputation Propagation: While forwarding the data from source to destination, it has to improve the attack detection accuracy. Score of reputation is calculated from the neighboring nodes which are called as Second-hand reputation scores. And the equation has shown below. ( ) ∑ ∑ ( ) ∑ ∑ ( ) ( ) The Equation (1.2) has shown above is used to repeat the process of calculating reputation score for each and every nodes in the wireless sensor network. Where is a penalty factor to reduce the reputation score of the sensor nodes E. Reputation Integration: After the completion of reputation integration and reputation propagation, the first hand and second hand short term reputation score will be integrated together and assign as single entry and update the reputation table in regular period of time. F. Malicious Nodes Identification: Finally, the identification of malicious nodes is performed with help of reputation table. The reputation value get decrease from 2 if there is packet loss during the transmission of data from source to destination. And the detection of malicious nodes can be performed based on the attack probability value. The attack probability is assign based on the threshold value. The threshold value is calculated based on iterative algorithm. If the reputation value is greater than the attack probability then it is assign as malicious node. For example: Consider three sensor nodes S, A and B. Where the ten packets are transmitted from S to both A and B. But the node A has loss only one packet during the transmission. And the node B has loss nearly five packet during the transmission. Therefore the normal loss rate is calculated for the node both A and B. The normal loss rate for the node A is 10% and for the node B is 50%. Based on the historical records the attack probability is fixed as 20%. Therefore node B is assigned as malicious nodes due to the dissatisfaction of attack probability value. III. SYSTEM MODEL AND DESIGN GOALS A. Network Model: Consider a Wireless Sensor Network, where the nodes are placed in randomly and distributed manner. And the node is denoted by N. On the other hand the sink node or destination node are monitored in regular period of time in an open areas And the information are transmitted to the sink through Multi-hop routing among the sensor nodes. Sensor nodes are communicate with the neighbor nodes based on IEEE 802.11 p. Since the environment is using unstable radio signal therefore it increases the packet loss rate exponential over time. Sensor nodes are deployed in open area like war field, forest area etc. Due to the placement of sensor nodes in open area it causes lack of physical protection and therefore they can compromise the nodes in very easy manner. By the study of existing works, the sensor nodes will monitor the data traffic for the neighbor nodes with the help of watchdog or acknowledgement based techniques. But it is difficult to monitor or distinguish the normal packet loss of data and the packet loss occur due to the malicious nodes.
- 4. ISSN 2350-1022 International Journal of Recent Research in Mathematics Computer Science and Information Technology Vol. 4, Issue 1, pp: (23-29), Month: April 2017 – September 2017, Available at: www.paperpublications.org Page | 26 Paper Publications B. Attack model: In these model, each node assign a value called as reliability value. Where if the reliability value is low means the probability of getting attack is high and the reliability value is high means the probability of getting attack is low. Here cryptographic technique can be implemented for providing data confidentiality and authentication. For example: Consider the two neighboring sensor nodes A and B. where the data traffic between nodes A and B are partially analyzed. And the node A has assign that node B as normal node and the information will transmit all the neighboring nodes but the real fact behind this the node B is a malicious node. Therefore it is very difficult to judge the malicious node and the proposed technique will detect the malicious nodes in very accurate way. Fig 3.1 Packet loss occur due to both attack node and without attack node C. Design Goals: The selective forwarding attack is used to monitoring the forwarding traffic information and increase the data delivery ratio. The proposed techniques is focused on the following two goals. 1)Accuracy Detection: The selective forwarding attack has high accuracy in detection of malicious nodes. It has includes the two metric. First, the detection of malicious nodes should have high accuracy. Next, the normal node can be mistakenly identified as malicious node, which creates lot of problem in wireless sensor network. 2) Delivery Rate Increased: Behind the proposed techniques, the data delivery rate has increased by the selective forwarding attack but the negative impact is caused by the attack nodes. Therefore the proposed techniques concentrates on high accuracy in detection of malicious nodes. IV. ADAPTIVE MOBILITY BASED ATTACK DETECTION TECHNIQUE Reputation Evaluation to evaluate short-term reputation score for the forwarding behaviors of sensor nodes based on the deviation of estimated normal packet loss rate and monitored actual packet loss rate.
- 5. ISSN 2350-1022 International Journal of Recent Research in Mathematics Computer Science and Information Technology Vol. 4, Issue 1, pp: (23-29), Month: April 2017 – September 2017, Available at: www.paperpublications.org Page | 27 Paper Publications Figure 4.1 System Architecture With Reputation Propagation, the evaluated short-term reputation scores can be propagated within the neighboring nodes to achieve a more comprehensive evaluation. Finally, by Reputation Integration, sensor nodes integrate the reputation scores evaluated by themselves and the propagated reputation scores from their neighboring nodes to update the reputation table along with the trust value. Figure 4.1 shows the architecture of Adaptive Mobility based attack detection. 1. Predicted Trust Calculation: In this stage, the predicted trust rating of node i on node k, is calculated with Tik . Let Si be the set of most similar nodes for node i . Tik is calculated as follows. Reputation Evaluation is to evaluate short-term reputation scores for the forwarding behaviors of sensor nodes, based on the deviation of estimated normal packet loss rate and monitored actual packet loss rate. With Reputation Propagation, the evaluated short-term reputation scores can be propagated within the neighboring nodes to achieve a more comprehensive evaluation. Finally, by Reputation Integration, sensor nodes integrate the reputation scores evaluated by them and the propagated reputation scores from their neighboring nodes to update the reputation table. 2. Trust Rating Formulation: In this stage the trust rating of each and every node is created and form a matrix R. The trust rating play vital role in the detection of malicious nodes. 3. Trusted Neighbor Selection: In this stage, all the similarities between nodes in the model are computed and the top K most similar nodes are selected. Note that the functional trust of each selected node will also be inspected to make sure that only recommendations from the nodes which can fulfill their tasks expected will be trusted. 4. Calculate the Local Evidence: The Dempster-Shafer Theory is used to calculate the local evidence. In this work, Dempster-Shafer theory of evidence is used to fuse together multiple piece of evidence even if some of them might not be accurate. In DST probability is replaced by an uncertainty interval bounded by belief and plausibility. Belief is the lower bound of this interval and represents supporting evidence. Plausibility is the upper bound of the interval and represents non-refuting evidence. For instance, if a node NK observes that one of its neighbors say node Nj has dropped packets with probability p then node Nk has p degree of belief in its absence. The belief value with respect to an event and observed by node Nk can be computed.
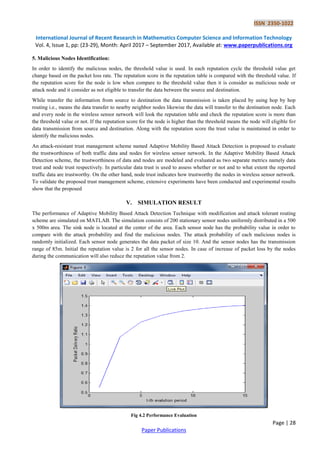
- 6. ISSN 2350-1022 International Journal of Recent Research in Mathematics Computer Science and Information Technology Vol. 4, Issue 1, pp: (23-29), Month: April 2017 – September 2017, Available at: www.paperpublications.org Page | 28 Paper Publications 5. Malicious Nodes Identification: In order to identify the malicious nodes, the threshold value is used. In each reputation cycle the threshold value get change based on the packet loss rate. The reputation score in the reputation table is compared with the threshold value. If the reputation score for the node is low when compare to the threshold value then it is consider as malicious node or attack node and it consider as not eligible to transfer the data between the source and destination. While transfer the information from source to destination the data transmission is taken placed by using hop by hop routing i.e., means the data transfer to nearby neighbor nodes likewise the data will transfer to the destination node. Each and every node in the wireless sensor network will look the reputation table and check the reputation score is more than the threshold value or not. If the reputation score for the node is higher than the threshold means the node will eligible for data transmission from source and destination. Along with the reputation score the trust value is maintained in order to identify the malicious nodes. An attack-resistant trust management scheme named Adaptive Mobility Based Attack Detection is proposed to evaluate the trustworthiness of both traffic data and nodes for wireless sensor network. In the Adaptive Mobility Based Attack Detection scheme, the trustworthiness of data and nodes are modeled and evaluated as two separate metrics namely data trust and node trust respectively. In particular data trust is used to assess whether or not and to what extent the reported traffic data are trustworthy. On the other hand, node trust indicates how trustworthy the nodes in wireless sensor network. To validate the proposed trust management scheme, extensive experiments have been conducted and experimental results show that the proposed V. SIMULATION RESULT The performance of Adaptive Mobility Based Attack Detection Technique with modification and attack tolerant routing scheme are simulated on MATLAB. The simulation consists of 200 stationary sensor nodes uniformly distributed in a 500 x 500m area. The sink node is located at the center of the area. Each sensor node has the probability value in order to compare with the attack probability and find the malicious nodes. The attack probability of each malicious nodes is randomly initialized. Each sensor node generates the data packet of size 10. And the sensor nodes has the transmission range of 85m. Initial the reputation value is 2 for all the sensor nodes. In case of increase of packet loss by the nodes during the communication will also reduce the reputation value from 2. Fig 4.2 Performance Evaluation
- 7. ISSN 2350-1022 International Journal of Recent Research in Mathematics Computer Science and Information Technology Vol. 4, Issue 1, pp: (23-29), Month: April 2017 – September 2017, Available at: www.paperpublications.org Page | 29 Paper Publications The above Fig 4.2 shows that performance evaluation of Adaptive Mobility Based Attack Detection Technique techniques. As a result implementing these technique the detection rate of malicious nodes get increased therefore it will reduce the packet loss rate and improve the performance of the wireless sensor network during communication between the nodes VI. CONCLUSION In this paper, a cluster Adaptive Mobility Based Attack Detection Technique with modification is used to detect the selective forwarding attack in Mobile Wireless Sensor Network. Where the proposed system includes high throughput, high rate in detection of malicious nodes. REFERENCES [1] Baker.M, Giuli.T.J, Lai.K and Marti.S. (2000) ‘Mitigating routing misbehavior in mobile ad hoc networks’, in Proc. ACM MobiCom, pp. 255-256. [2] Chen.Z, Liu.A, Shen.X, Zhang.C and Zheng.Z. (2012) ‘Secure and energy-efficient disjoint multipath routing for wsns’, IEEE Trans. Vehic. Tech, vol. 61, no. 7, pp. 3255-3265. [3] Gao.C, Yu.B and Xiao.B. (2007) ‘Chemas: Identify suspect nodes in selective forwarding attacks’, J.Parallel Distributed Comput., vol. 67, no.11, pp. 1218-1230. [4] Kozma.W, Lazos.L and Zhang.Y. (2013) ‘Amd: Audit-based misbehavior detection in wireless ad hoc networks’, IEEE Trans. Mob. Comput., prePrints. Published online in Sept. [5] Krunz.M, Lin.S and Shu.T. (2010) ‘Secure data collection in wireless sensor networks using randomized dispersive routes’, IEEE Trans. Mob. Comput, vol. 9, no. 7, pp. 941-954. [6] Krunz.M and Shu.T. (2012) ‘Detection of malicious packet dropping in wireless ad hoc networks based on privacy- preserving public auditing’, in Proc. ACM WiSec, pp.87-98. [7] Liang.X, Lin.X and Shen.X. (2014) ‘Enabling trustworthy service evaluation in service-oriented mobile social networks’, IEEE Trans. Parallel Distr. Sys., vol.25, no.2, pp.310-320. [8] Ren.J Shen.X, Zhang.K and Zhang.Y. (2014) ‘Exploiting channel-aware reputation system against selective forwarding attacks in wsns’, in Proc. IEEE GLOBECOM, pp. 330-335. [9] Ren.J, Shen.X, Zhang.K and Zhang.Y. (2015) ‘Exploiting mobile crowd-sourcing for pervasive cloud services: challenges and solutions’, IEEE Commun, Mag., vol. 53, no. 3, pp. 98-105. [10] Shen.W, Wang.X, and Zou.Y. (2013) ‘Physical-layer security with multiuser scheduling in cognitive radio networks’, IEEE Trans. Commun., vol. 61, no 12, pp. 5103-5113.





![ISSN 2350-1022
International Journal of Recent Research in Mathematics Computer Science and Information Technology
Vol. 4, Issue 1, pp: (23-29), Month: April 2017 – September 2017, Available at: www.paperpublications.org
Page | 29
Paper Publications
The above Fig 4.2 shows that performance evaluation of Adaptive Mobility Based Attack Detection Technique
techniques. As a result implementing these technique the detection rate of malicious nodes get increased therefore it will
reduce the packet loss rate and improve the performance of the wireless sensor network during communication between
the nodes
VI. CONCLUSION
In this paper, a cluster Adaptive Mobility Based Attack Detection Technique with modification is used to detect the
selective forwarding attack in Mobile Wireless Sensor Network. Where the proposed system includes high throughput,
high rate in detection of malicious nodes.
REFERENCES
[1] Baker.M, Giuli.T.J, Lai.K and Marti.S. (2000) ‘Mitigating routing misbehavior in mobile ad hoc networks’, in Proc.
ACM MobiCom, pp. 255-256.
[2] Chen.Z, Liu.A, Shen.X, Zhang.C and Zheng.Z. (2012) ‘Secure and energy-efficient disjoint multipath routing for
wsns’, IEEE Trans. Vehic. Tech, vol. 61, no. 7, pp. 3255-3265.
[3] Gao.C, Yu.B and Xiao.B. (2007) ‘Chemas: Identify suspect nodes in selective forwarding attacks’, J.Parallel
Distributed Comput., vol. 67, no.11, pp. 1218-1230.
[4] Kozma.W, Lazos.L and Zhang.Y. (2013) ‘Amd: Audit-based misbehavior detection in wireless ad hoc networks’,
IEEE Trans. Mob. Comput., prePrints. Published online in Sept.
[5] Krunz.M, Lin.S and Shu.T. (2010) ‘Secure data collection in wireless sensor networks using randomized dispersive
routes’, IEEE Trans. Mob. Comput, vol. 9, no. 7, pp. 941-954.
[6] Krunz.M and Shu.T. (2012) ‘Detection of malicious packet dropping in wireless ad hoc networks based on privacy-
preserving public auditing’, in Proc. ACM WiSec, pp.87-98.
[7] Liang.X, Lin.X and Shen.X. (2014) ‘Enabling trustworthy service evaluation in service-oriented mobile social
networks’, IEEE Trans. Parallel Distr. Sys., vol.25, no.2, pp.310-320.
[8] Ren.J Shen.X, Zhang.K and Zhang.Y. (2014) ‘Exploiting channel-aware reputation system against selective
forwarding attacks in wsns’, in Proc. IEEE GLOBECOM, pp. 330-335.
[9] Ren.J, Shen.X, Zhang.K and Zhang.Y. (2015) ‘Exploiting mobile crowd-sourcing for pervasive cloud services:
challenges and solutions’, IEEE Commun, Mag., vol. 53, no. 3, pp. 98-105.
[10] Shen.W, Wang.X, and Zou.Y. (2013) ‘Physical-layer security with multiuser scheduling in cognitive radio
networks’, IEEE Trans. Commun., vol. 61, no 12, pp. 5103-5113.](https://image.slidesharecdn.com/anadaptivemobilitybased-170623102238/85/An-Adaptive-Mobility-Based-Attack-Detection-Mechanism-to-Detect-Selective-Forwarding-Attack-in-Wireless-Sensor-Network-7-320.jpg)