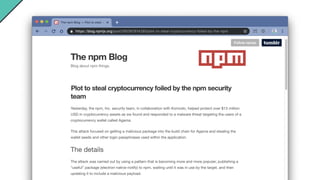
Analysis of an OSS supply chain attack - How did 8 millions developers download an exploit with no one noticing?
- 1. Jarrod Overson - BSidesPDX Why are imitation attacks such a problem? Analysis of an OSS supply chain attack How did millions of developers download malicious code with no one noticing? Jarrod Overson - BSidesPDX
- 2. Jarrod Overson - BSidesPDX
- 3. Jarrod Overson - BSidesPDX
- 4. Jarrod Overson - BSidesPDX
- 5. Jarrod Overson - BSidesPDX npm install [anything]
- 6. Jarrod Overson - BSidesPDX The threat is real And it's coming from inside the house.
- 7. Jarrod Overson - BSidesPDX How it happened What it did Where it leaves us 1 2 3 Agenda
- 8. Jarrod Overson - BSidesPDX Who am I? • Director at Shape Security & Google Dev Expert. • Write/talk/record about JS reverse engineering & breaking web apps. • Old-school video game hacker. • @jsoverson most everywhere This guy
- 9. Jarrod Overson - BSidesPDX ?
- 10. Jarrod Overson - BSidesPDX Ever heard of YKK?
- 11. Jarrod Overson - BSidesPDX
- 12. Jarrod Overson - BSidesPDX You used Shape this week. We're the reason you log in a lot less and see fewer CAPTCHAs.
- 13. Jarrod Overson - BSidesPDX How it happened What it did Where it leaves us 1 2 3 Agenda
- 14. Jarrod Overson - BSidesPDX JS It started with a package, event-stream
- 15. Jarrod Overson - BSidesPDX
- 16. Jarrod Overson - BSidesPDX
- 17. Jarrod Overson - BSidesPDX
- 18. Jarrod Overson - BSidesPDX
- 19. Jarrod Overson - BSidesPDX JS event-stream was maintained by prolific developer Dominic Tarr
- 20. Jarrod Overson - BSidesPDX
- 21. Jarrod Overson - BSidesPDX
- 22. Jarrod Overson - BSidesPDX
- 23. Jarrod Overson - BSidesPDX JS Domenic gave ownership to right9ctrl in September of 2018 *
- 24. Jarrod Overson - BSidesPDX Q: Why?
- 25. Jarrod Overson - BSidesPDX
- 26. Jarrod Overson - BSidesPDX
- 27. Jarrod Overson - BSidesPDX JS right9ctrl gained trust by committing several innocent changes. ...b550f5: upgrade dependencies ...37c105: add map and split examples ...477832: remove trailing in split example ...2c2095: better pretty.js example ...a644c5: update readme event-stream
- 28. Jarrod Overson - BSidesPDX JS On Sept 9 2018 right9ctrl added a new dependency and released version 3.3.6 JS v3.3.6 JS v0.1.0 flatmap-stream event-stream
- 29. Jarrod Overson - BSidesPDX About that caret...
- 30. Jarrod Overson - BSidesPDX Semantic Versioning (semver) Major.Minor.Patch e.g. 3.4.9 Breaking changes New features Bug fixes Increasing risk
- 31. Jarrod Overson - BSidesPDX Semver pattern matching Symbol Example Matches ^ ^0.1.0 0.*.* ~ ~0.1.0 0.1.*
- 32. Jarrod Overson - BSidesPDX JS right9ctrl then removed flatmap-stream and updated event-stream to v4.0.0. v4.0.0 event-stream
- 33. Jarrod Overson - BSidesPDX Note: Nothing malicious has emerged thus far.
- 34. Jarrod Overson - BSidesPDX Total time between first commit and v4.0.0? 12 days
- 35. Jarrod Overson - BSidesPDX JS On October 5th 2018 (T+31) [email protected] was published. JS v3.3.6 v0.1.1 flatmap-stream event-stream JS v0.1.0
- 36. Jarrod Overson - BSidesPDX JS [email protected] installed fresh now pulls in [email protected] because of the ^ JS v3.3.6 v0.1.1 flatmap-stream event-stream
- 37. Jarrod Overson - BSidesPDX [email protected] was stable for 2+ years. JSJS v3.3.6 event-stream
- 38. Jarrod Overson - BSidesPDX A LOT depended on event-stream^3.3.5 and would get updated to 3.3.6 automatically. JS JS JS JS JS JS JS JS JS
- 39. Jarrod Overson - BSidesPDX Time between [email protected] and exposure: 48 days Time between malicious control and discovery: 77 days
- 40. Jarrod Overson - BSidesPDX How it happened What it did Where it leaves us 1 2 3 Agenda
- 41. Jarrod Overson - BSidesPDX First, how was it discovered?
- 42. Payload A used a method deprecated in node v11.0.0
- 43. Node v11.0.0 was released 18 days into the exploit.
- 44. Unrelated projects started getting deprecation warnings.
- 45. Finally someone started putting it together.
- 46. Jarrod Overson - BSidesPDX So how was it discovered? Luck.
- 49. Jarrod Overson - BSidesPDX Payload A The bootstrap.
- 65. Jarrod Overson - BSidesPDX Recap • The script decrypts and compiles a new module. • The key comes from a package description somewhere. • The encrypted JS comes from testData[0]. • The compiled module exports testData[1].
- 66. Jarrod Overson - BSidesPDX What does this mean? The script only serves its purpose if the code runs from an npm script in a directory that has a package.json with a "description" field containing a specific string that can act as the key.
- 67. Jarrod Overson - BSidesPDX What this means for us We need to start trolling through package.json files.
- 69. 😂
- 70. Jarrod Overson - BSidesPDX Strategy • Iterate through every package. • Decrypt testData[0]. • Run the decrypted data through a JS Parser. • If successful then we have a winner.
- 71. Jarrod Overson - BSidesPDX
- 72. Jarrod Overson - BSidesPDX
- 73. Copay, the Secure Bitcoin Wallet.
- 74. Jarrod Overson - BSidesPDX Payload B The injector.
- 75. Payload B
- 76. Payload B
- 77. Jarrod Overson - BSidesPDX npm scripts redux npm run-script script-name [0] [1] [2]argv:
- 78. Payload B
- 80. Payload B
- 81. Jarrod Overson - BSidesPDX Recap • Payload B noops unless run in copay's build stage. • Decrypts payload C just like payload B. • Injects payload C into a file used in copay's mobile app. • Payload C is then executed in the mobile app while on a user's mobile device.
- 82. Jarrod Overson - BSidesPDX Payload C The final payload.
- 83. Payload C
- 84. Jarrod Overson - BSidesPDX Payload C in a nutshell • Harvested private keys • Targeted wallets with over 100 BTC or 1000 BCH • Communicated with third party server copayapi.host
- 85. Jarrod Overson - BSidesPDX How it happened What it did Where it leaves us 1 2 3 Agenda
- 86. Jarrod Overson - BSidesPDX This is NOT node/npm specific Any public repository of code is susceptible.
- 87. Jarrod Overson - BSidesPDX The Good News. Once the issue was brought to light the community • responded rapidly • investigated quickly • mitigated the issue immediately • and produced tools to help others right away.
- 88. Jarrod Overson - BSidesPDX The Bad News. It has happened multiple times since.
- 91. The dependency problem is not ideal.
- 92. Jarrod Overson - BSidesPDX This could have been much worse. event-stream was depended on things like the - azure-cli - dozens of build tools and plugins - Microsoft's monaco editor (the editor for VSCode)
- 93. Jarrod Overson - BSidesPDX This will likely get much worse. Properly addressing this problem requires rethinking node, dependencies, and package management. Hard things with lots of compatibility implications.
- 94. Jarrod Overson - BSidesPDX
- 95. Jarrod Overson - BSidesPDX What can you do? • Audit your dependencies. • Lock your dependencies. • Check in your dependencies. • Think twice before adding dependencies.
- 96. Jarrod Overson - BSidesPDX When in doubt, don't add it. • Dependencies are risks. • Risks are gambles. • You gamble when cost is low and value is high.
- 97. Jarrod Overson - BSidesPDX Why are imitation attacks such a problem?Thank You! @jsoverson on bit.ly/jsoverson-youtube





![Jarrod Overson - BSidesPDX
npm install [anything]](https://image.slidesharecdn.com/bsides-pdx-191025194656/85/Analysis-of-an-OSS-supply-chain-attack-How-did-8-millions-developers-download-an-exploit-with-no-one-noticing-5-320.jpg)


























































![Jarrod Overson - BSidesPDX
Recap
• The script decrypts and compiles a new module.
• The key comes from a package description somewhere.
• The encrypted JS comes from testData[0].
• The compiled module exports testData[1].](https://image.slidesharecdn.com/bsides-pdx-191025194656/85/Analysis-of-an-OSS-supply-chain-attack-How-did-8-millions-developers-download-an-exploit-with-no-one-noticing-65-320.jpg)




![Jarrod Overson - BSidesPDX
Strategy
• Iterate through every package.
• Decrypt testData[0].
• Run the decrypted data through a JS Parser.
• If successful then we have a winner.](https://image.slidesharecdn.com/bsides-pdx-191025194656/85/Analysis-of-an-OSS-supply-chain-attack-How-did-8-millions-developers-download-an-exploit-with-no-one-noticing-70-320.jpg)






![Jarrod Overson - BSidesPDX
npm scripts redux
npm run-script script-name
[0] [1] [2]argv:](https://image.slidesharecdn.com/bsides-pdx-191025194656/85/Analysis-of-an-OSS-supply-chain-attack-How-did-8-millions-developers-download-an-exploit-with-no-one-noticing-77-320.jpg)