Application layer protocols-SMTP Unit-V.ppt
- 2. Domain Name System (DNS) • The Domain Name System (DNS) is a supporting program that is used by other programs such as e-mail. • A user of an e-mail program may know the e-mail address of the recipient; however, the IP protocol needs the IP address. • The DNS client program sends a request to a DNS server to map the e-mail address to the corresponding IP address. • When the Internet was small, mapping was done by using a host file. The host file had only two columns: name and address. • Every host could store the host file on its disk and update it periodically from a master host file. When a program or a user wanted to map a name to an address, the host consulted the host file and found the mapping. • Today, however, it is impossible to have one single host file to relate every address with a name and vice versa. The host file would be too large to store in every host. • One solution is to divide this huge amount of information into smaller parts and store each part on a different computer. • In this method, the host that needs mapping can contact the closest computer holding the needed information. This method is used by the Domain Name System (DNS). Name Space symmetry • The names must be unique because the addresses are unique. A name space that maps each address to a unique name can be organized in two ways: • Flat Name Space-A name is assigned to an address. A name in this space is a sequence of characters without structure. It cannot be used in a large system such as the Internet. • Hierarchical Name Space-Each name is made of several parts. The first part can define the nature of the organization, the second part can define the name of an organization, and the third part can define departments in the organization, and so on.
- 3. Domain Name Space • To have a hierarchical name space, a domain name space was designed. In this design the names are defined in an inverted-tree structure with the root at the top. The tree can have only 128 levels: level 0 (root) to level 127 (see Fig.5.19). Fig.5.19 Domain Name Space Label • Each node in the tree has a label, which is a string with a maximum of 63 characters. The root label is a null string (empty string). • DNS requires that children of a node (nodes that branch from the same node) have different labels, which guarantees the uniqueness of the domain names.
- 4. Fig.5.20 Domain names and labels Domain Name • Each node in the tree has a domain name as in fig.5.20. A full domain name is a sequence of labels separated by dots (.). • The domain names are always read from the node up to the root. • The last label is the label of the root (null). • This means that a full domain name always ends in a null label, which means the last character is a dot because the null string is nothing.
- 5. Fig.5.21 Domains Domain • A domain is a subtree of the domain name space. • The name of the domain is the domain name of the node at the top of the subtree. Fig.5.21 shows some domains. • Note that a domain may itself be divided into domains (or subdomains as they are sometimes called). Distribution of Name Space • The information contained in the domain name space must be stored. • However, it is very inefficient because responding to requests from all over the world places a heavy load on the system. • The solution to these problems is to distribute the information among many computers called DNS servers. • One way to do this is to divide the whole space into many domains based on the first level.
- 6. Zone • Since the complete domain name hierarchy cannot be stored on a single server, it is divided among many servers. • What a server is responsible for or has authority over is called a zone. We can define a zone as a contiguous part of the entire tree. • A primary server loads all information from the disk file; the secondary server loads all information from the primary server. • When the secondary downloads information from the primary, it is called zone transfer. DNS in the Internet • DNS is a protocol that can be used in different platforms. • In the Internet, the domain name space (tree) is divided into three different sections: generic domains, country domains, and the inverse domain (see Fig.5.22). Fig.5.22 DNS used in the internet
- 7. 1. Generic Domains • The generic domains define registered hosts according to their generic behavior as in fig.5.23. • Each node in the tree defines a domain, which is an index to the domain name space database. Fig.5.23 Generic domains
- 8. 2. Country Domains • The country domains section uses two-character country abbreviations (e.g., us for United States). • Second labels can be organizational, or they can be more specific, national designations. • The United States, for example, uses state abbreviations as a subdivision of us (e.g., ca.us.).Fig.5.24 shows the country domains section. • The address anza.cup.ca.us can be translated to De Anza College in Cupertino, California, in the United States. Fig.5.24 Country Domain
- 9. 3. Inverse Domain • The inverse domain is used to map an address to a name. This may happen, for example, when a server has received a request from a client to do a task. • Although the server has a file that contains a list of authorized clients, only the IP address of the client is listed. • The server asks its resolver to send a query to the DNS server to map an address to a name to determine if the client is on the authorized list. Fig.5.25 Inverse Domain • This type of query is called an inverse or pointer (PTR) query. To handle a pointer query, the inverse domain is added to the domain name space with the first-level node called arpa (for historical reasons) as shown in fig.5.25. • The second level is also one single node named in-addr (for inverse address). The rest of the domain defines IP addresses. • The servers that handle the inverse domain are also hierarchical. This means the netid part of the address should be at a higher level than the subnetid part, and the subnetid part.
- 10. ELECTRONIC MAIL (Email) • One of the most popular Internet services is electronic mail (e-mail). • It allows a message to include text, audio, and video. It also allows one message to be sent to one or more recipients. • E-mail system includes three main components: user agent, message transfer agent(MTA), and message access agent(MAA). Architecture • The sender and the receiver of the e-mail are users (or application programs) on the same system; they are directly connected to a shared system. • The administrator has created one mailbox for each user where the received messages are stored. • A mailbox is part of a local hard drive, a special file with permission restrictions. • Only the owner of the mailbox has access to it. When Alice, a user, needs to send a message to Bob, another user, Alice runs a user agent (UA) program to prepare the message and store it in Bob's mailbox. • The message has the sender and recipient mailbox addresses (names of files). • Bob can retrieve and read the contents of his mailbox at his convenience, using a user agent. Fig.5.1 SMTP concept
- 11. • In the next scenario, the sender and the receiver of the e-mail are users (or application programs) on two different systems. • The message needs to be sent over the Internet. Here we need user agents (UAs) and message transfer agents (MTAs). Fig.5.2 UAs and MTAs • When the sender is connected to the mail server via a LAN or a WAN, we need two UAs and two pairs of MTAs (client and server).
- 12. • In the most common scenario, Bob is also connected to his mail server by a WAN or a LAN. • Bob uses an MAA client to retrieve his messages. When both sender and receiver are connected to the mail server via a LAN or a WAN, we need two UAs, two pairs of MTAs (client and server), and a pair of MAAs (client and server). Fig.5.3 Today’s most Common Scenario for E-mail System
- 13. There are two components, they are • User Agent (It provides service to the user to make the process of sending and receiving a message easier) • Message Transfer Agent(MTA) Services Provided by a User Agent • A user agent is a software package (program) that composes, reads, replies to, and forwards messages. It also handles mailboxes. • Composing Messages: A user agent helps the user compose the e-mail message to be sent out. • Reading Messages: When a user invokes a user agent, it first checks the mail in the incoming mailbox. Each e-mail contains the following fields. – A number field – A flag field that shows the status of the mail such as new, already read but not replied to, or read and replied to – The size of the message – The sender – The optional subject field • Replying to Messages: After reading a message, a user can use the user agent to reply to a message. The reply message may contain the original message and the new message. • Forwarding Messages: Forwarding is defined as sending the message to a third party. • Handling Mailboxes: A user agent normally creates two mailboxes: an inbox and an outbox. The inbox keeps all the received e-mails and outbox keeps all the sent e-mails
- 14. User Agent Types There are two types of user agents: • Command-driven: It accepts a one-character command from the keyboard to perform its task. Some examples of command-driven user agents are mail, pine, and elm. • GUI-based: They contain graphical-user interface (GUI) components that allow the user to interact with the software by using both the keyboard and the mouse. Some examples of GUI-based user agents are Eudora, Microsoft's Outlook, and Netscape. Sending Mail • To send mail, the user, through the UA, creates mail that looks very similar to postal mail. It has an envelope and a message as in fig. Fig.5.4 Format of an e-mail • Envelope: It contains the sender and the receiver addresses. • Message: It contains the header and the body. • Receiving Mail: The user agent is triggered by the user (or a timer). If a user has mail, the UA informs the user with a notice. • Addresses: The address consists of two parts: a local part and a domain name, separated by an @ sign as in fig. Fig.5.5 Email address
- 15. Multipurpose Internet Mail Extensions (MIME) • Email can send messages only in NVT 7-bit ASCII format. For example, it cannot be used for languages that are not supported by 7-bit ASCII characters (such as French, German, Hebrew, Russian, Chinese, and Japanese). • Multipurpose Internet Mail Extensions (MIME) is a supplementary protocol that transforms non-ASCII data at the sender site to NVT ASCII data and delivers them to the client MTA to be sent through the Internet as in fig.5.6. • MIME defines five headers that can be added to the original e-mail header section to define the transformation parameters. 1. MIME-Version: This header defines the version of MIME used. The current version is 1.1. MIME-Version:1.1 2. Content-Type: This header defines the type of data used in the body of the message. The content type and the content subtype are separated by a slash. Depending on the subtype, the header may contain other parameters. Content-Type<type Jsubtype; parameters> 3. Content-Transfer-Encoding: This header defines the method used to encode the messages into 0s and 1s for transport: Content-Transfer-Encoding :< type> 4. Content-Id This header uniquely identifies the whole message in a multiple-message environment. Content-Id:id=<content-id> 5. Content-Description: This header defines whether the body is image, audio, or video. Content-Description :< description> Fig.5.6 MIME
- 16. Message Access Agent: POP and IMAP Currently two message access protocols are available: – Post Office Protocol, version 3(POP3) – Internet Mail Access Protocol, version 4 (IMAP4) Fig.5.7 POP3 and SMTP
- 17. Post Office Protocol Version 3(POP3) • The client POP3 software is installed on the recipient computer; the server POP3 software is installed on the mail server. • Mail access starts with the client when the user needs to download e-mail from the mailbox on the mail server. The client opens a connection to the server on TCP port 110. • It then sends its user name and password to access the mailbox. The user can then list and retrieve the mail messages, one by one. • POP3 has two modes: the delete mode and the keep mode. In the delete mode, the mail is deleted from the mailbox after each retrieval. In the keep mode, the mail remains in the mailbox after retrieval. Internet Mail Access Protocol version 4(IMAP4) • IMAP4 is similar to POP3.IMAP4 is more powerful and more complex. It provides the following extra functions: – A user can check the e-mail header prior to downloading. – A user can search the contents of the e-mail for a specific string of characters prior to downloading. – A user can partially download e-mail. This is especially useful if bandwidth is limited and the e-mail contains multimedia with high bandwidth requirements. – A user can create, delete, or rename mailboxes on the mail server. – A user can create a hierarchy of mailboxes in a folder for e-mail storage.
- 18. FILE TRANSFER • Transferring files from one computer to another is one of the most common tasks expected from a networking or internetworking environment. File Transfer Protocol (FTP) • File Transfer Protocol (FTP) is the standard mechanism provided by TCP/IP for copying a file from one host to another. • FTP differs from other client/server applications in that it establishes two connections between the hosts. One connection is used for data transfer, the other for control information (commands and responses). • Separation of commands and data transfer makes FTP more efficient. The control connection uses very simple rules of communication. • FTP uses two well-known TCP ports: Port 21 is used for the control connection, and port 20 is used for the data connection. Fig.5.32 shows the basic model of FTP. • The client has three components: user interface, client control process, and the client data transfer process. • The server has two components: the server control process and the server data transfer process. The control connection is made between the control processes. • The data connection is made between the data transfer processes. • The control connection remains connected during the entire interactive FTP session. • When a user starts an FTP session, the control connection opens. While the control connection is open, the data connection can be opened and closed multiple times if several files are transferred. Fig.5.32 FTP
- 19. Communication over Control Connection • FTP uses the same approach as SMTP to communicate across the control connection as in fig.5.33. • It uses the 7-bit ASCII character set. Communication is achieved through commands and responses. • This simple method is adequate for the control connection because we send one command (or response) at a time. Each command or response is only one short line, so we need not worry about file format or file structure. • Each line is terminated with a two-character (carriage return and line feed) end-of-line token. Fig.5.33 Communication over Control Connection
- 20. Communication over Data Connection • File transfer occurs over the data connection under the control of the commands sent over the control connection as in fig.5.34. However, we should remember that file transfer in FTP means one of three things: – A file is to be copied from the server to the client. This is called retrieving aft/e. It is done under the supervision of the RETR command. – A file is to be copied from the client to the server. This is called storing aft/e. It is done under the supervision of the STOR command. – A list of directory or file names is to be sent from the server to the client. This is done under the supervision of the LIST command. • The client must define the type of file to be transferred, the structure of the data, and the transmission mode. • Before sending the file through the data connection, we prepare for transmission through the control connection. • The heterogeneity problem is resolved by defining three attributes of communication: file type, data structure, and transmission mode. Fig.5.34 Communication over Data Connection Anonymous FTP • To use FTP, a user needs an account (user name) and a password on the remote server. Some sites have a set of files available for public access, to enable anonymous FTP. • To access these files, a user does not need to have an account or password. Instead, the user can use anonymous as the user name and guest as the password. • User access to the system is very limited. Some sites allow anonymous users only a subset of commands. For example, most sites allow the user to copy some files, but do not allow navigation through the directories.
- 21. World Wide Web (WWW) and Hyper Text Transfer Protocol (HTTP) • The World Wide Web (WWW) is a repository of information linked together from points all over the world. • The WWW has a unique combination of flexibility, portability, and user-friendly features that distinguish it from other services provided by the Internet. Architecture • The WWW today is a distributed client/server service, in which a client using a browser can access a service using a server. However, the service provided is distributed over many locations called sites. • Each site holds one or more documents, referred to as Web pages. • Each Web page can contain a link to other pages in the same site or at other sites. • The pages can be retrieved and viewed by using browsers shown in Fig. The client needs to see some information that it knows belongs to site A. • It sends a request through its browser, a program that is designed to fetch Web documents. • The request, among other information, includes the address of the site and the Web page, called the URL.
- 22. Fig.5.8 Architecture of WWW • The server at site A finds the document and sends it to the client. • When the user views the document, she finds some references to other documents, including a Web page at site B. • The reference has the URL for the new site. The user is also interested in seeing this document. • The client sends another request to the new site, and the new page is retrieved.
- 23. Client (Browser) • Each browser usually consists of three parts: a controller, client protocol, and interpreters. • The controller receives input from the keyboard or the mouse and uses the client programs to access the document as in fig.5.9. • After the document has been accessed, the controller uses one of the interpreters to display the document on the screen. • The client protocol can be one of the protocols described previously such as FTP or HTTP. • The interpreter can be HTML, Java, or JavaScript, depending on the type of document. Fig.5.9 Browser Architecture
- 24. Uniform Resource Locator (URL) • A client that wants to access a Web page needs the address. To facilitate the access of documents distributed throughout the world, HTTP uses locators. • The uniform resource locator (URL) is a standard for specifying any kind of information on the Internet. The URL defines four things: protocol, host computer, port, and path as in Fig.5.10. Fig.5.10 URL • The protocol is the client/server program used to retrieve the document. • The host is the computer on which the information is located, although the name of • the computer can be an alias. • The URL can optionally contain the port number of the server. If the port is included, it is inserted between the host and the path, and it is separated from the host by a colon. • Path is the pathname of the file where the information is located. Cookie • Cookies are small files which are stored on a user's computer. They are designed to hold a modest amount of data specific to a particular client and website, and can be accessed either by the web server or the client computer.
- 25. Web Documents • The documents in the WWW can be grouped into three broad categories: static, dynamic, and active. 1. Static Documents • Static documents are fixed-content documents that are created and stored in a server as shown in fig.5.19. The client can get only a copy of the document. • Of course, the contents in the server can be changed, but the user cannot change them. Fig.5.11 Static document Hypertext Markup Language (HTML) • Hypertext Markup Language (HTML) is a language for creating Web pages. • For an example, to make part of a text displayed in boldface with HTML, we put beginning and ending boldface tags (marks) in the text, as shown in Fig.5.12.
- 26. Fig.5.12 Boldface tags • The two tags <B> and </B> are instructions for the browser. When the browser sees these two marks, it knows that the text must be boldfaced. • A markup language such as HTML allows us to embed formatting instructions in the file itself. The instructions are included with the text. • A Web page is made up of two parts: the head and the body. The head is the first part of a Web page. • The head contains the title of the page and other parameters that the browser will use. The actual contents of a page are in the body, which includes the text and the tags.
- 27. Example 1: This example shows how tags are used to let the browser format the appearance of the text. <HTML> <HEAD> <TITLE> First Sample Document </TITLE> </HEAD> <BODY> <CENTER> <H1><B> ATTENTION </B></H1> </CENTER> You can get a copy of this document by: <UL> <LI> Writing to the publisher <LI> Ordering online <LI> Ordering through a bookstore </UL> </BODY> </HTML>
- 28. Example 2: This example shows how tags are used to import an image and insert it into the text. <HTML> <HEAD> <TITLE> Second Sample Document </TITLE> </HEAD> <BODY> This is the picture of a book: <IMG SRC="Pictures/book1.gif" ALIGN=MIDDLE> </BODY> </HTML>
- 29. 2. Dynamic Documents • A dynamic document is created by a Web server whenever a browser requests the document as in fig.5.13. • When a request arrives, the Web server runs an application program or a script that creates the dynamic document. • The server returns the output of the program or script as a response to the browser that requested the document. Because a fresh document is created for each request, the contents of a dynamic document can vary from one request to another. • A very simple example of a dynamic document is the retrieval of the time and date from server. Fig.5.13 Dynamic document Common Gateway Interface (CGI) • The Common Gateway Interface (CGI) is a technology that creates and handles dynamic documents. • CGI is a set of standards that defines how a dynamic document is written, how data are input to the program, and how the output result is used.
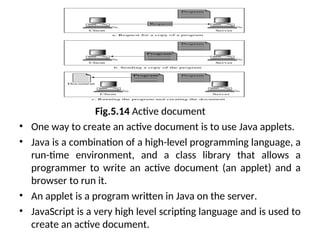
- 30. 3. Active Documents • For many applications, we need a program or a script to be run at the client site. These are called active documents. • For example, suppose we want to run a program that creates animated graphics on the screen or a program that interacts with the user. • The program definitely needs to be run at the client site where the animation or interaction takes place. • When a browser requests an active document, the server sends a copy of the document or a script. The document is then run at the client (browser) site.
- 31. Fig.5.14 Active document • One way to create an active document is to use Java applets. • Java is a combination of a high-level programming language, a run-time environment, and a class library that allows a programmer to write an active document (an applet) and a browser to run it. • An applet is a program written in Java on the server. • JavaScript is a very high level scripting language and is used to create an active document.
- 32. Hypertext Transfer Protocol (HTTP) • The Hypertext Transfer Protocol (HTTP) is a protocol used mainly to access data on the World Wide Web. • HTTP functions as a combination of FTP and SMTP. • It is similar to FTP because it transfers files and uses the services of TCP. However, it is much simpler than FTP because it uses only one TCP connection. • HTTP is like SMTP because the data transferred between the client and the server look like SMTP messages. • Unlike SMTP, the HTTP messages are not destined to be read by humans; they are read and interpreted by the HTTP server and HTTP client (browser). • SMTP messages are stored and forwarded, but HTTP messages are delivered immediately. • The commands from the client to the server are embedded in a request message. The contents of the requested file or other information are embedded in a response message. • HTTP uses the services of TCP on well-known port 80.
- 33. HTTP Transaction • Although HTTP uses the services of TCP, HTTP itself is a stateless protocol. • The client initializes the transaction by sending a request message. • The server replies by sending a response.Fig.5.15 illustrates the HTTP transaction between the client and server. Fig.5.15 HTTP transaction
- 34. Messages • The formats of the request and response messages are similar; both are shown in Fig.5.16. A request message consists of a request line, a header, and sometimes a body. • A response message consists of a status line, a header, and sometimes a body. Fig.5.16 Request and Response messages • Request and Status Lines: The first line in a request message is called a request line; the first line in the response message is called the status line. Fig.5.17 Request Line
- 35. • Request type: This field is used in the request message. In version 1.1 of HTTP, several request types are defined. • URL: Uniform Resource Locator • Version: The most current version of HTTP is 1.1. Fig.5.18 Status Line • Status code: This field is used in the response message. The status code field is similar to those in the FTP and the SMTP protocols. • It consists of three digits. Whereas the codes in the 100 range are only informational, the codes in the 200 range indicate a successful request. • The codes in the 300 range redirect the client to another URL, and the codes in the 400 range indicate an error at the client site. • Finally, the codes in the 500 range indicate an error at the server site. • Status phrase: This field is used in the response message. It explains the status code in text form. • Header: The header exchanges additional information between the client and the server. • Body: The body can be present in a request or response message. Usually, it contains the document to be sent or received.
- 36. REMOTE LOGGING • In the Internet, users may want to run application programs at a remote site and create results that can be transferred to their local site. • After logging on, a user can use the services available on the remote computer and transfer the results back to the local computer. TELNET • TELNET is an abbreviation for TErminaL NETwork. • It is the standard TCP/IP protocol for virtual terminal service as proposed by the International Organization for Standards (ISO). • TELNET enables the establishment of a connection to a remote system in such a way that the local terminal appears to be a terminal at the remote system. Timesharing Environment • TELNET was designed at a time when most operating systems, such as UNIX, were operating in a timesharing environment. • In such an environment, a large computer supports multiple users. • The interaction between a user and the computer occurs through a terminal, which is usually a combination of keyboard, monitor, and mouse.
- 37. Logging • In a timesharing environment, users are part of the system with some right to access resources. • Each authorized user has identification and probably, a password. The user identification defines the user as part of the system. • To access the system, the user logs into the system with a user id or log-in name. • The system also includes password checking to prevent an unauthorized user from accessing the resources. Fig.5.29 and Fig.5.30 shows the logging process. • When a user logs into a local timesharing system, it is called local log-in. Fig.5.29 Local login
- 38. • As a user types at a terminal or at a workstation running a terminal emulator, the keystrokes are accepted by the terminal driver. • The terminal driver passes the characters to the operating system. The operating system interprets the combination of characters and invokes the desired application program or utility. • When a user wants to access an application program or utility located on a remote machine, she performs remote log-in. • The commands or text, in NVT form as in fig.5.31, travel through the Internet and arrive at the TCP/IP stack at the remote machine. • The operating system then passes the characters to the appropriate application program. Fig.5.30 Remote login Fig.5.31 Concept of NVT
- 40. Introduction • Cryptography means secret writing. • It refers to the tools and techniques used to make messages secure for communication between the participants and make messages immune to attacks by hackers. • For private communication through public network, cryptography plays a very crucial role. • The message to be sent through an unreliable medium is known as plaintext, which is encrypted before sending over the medium. • The encrypted message is known as cipher text, which is received at the other end of the medium and decrypted to get back the original plaintext message. • There are two cryptographic algorithms. They are Symmetric key (Secret-key)cryptography Asymmetric key (Public key cryptography)cryptography Fig. A simple cryptography model
- 41. Figure :Encryption and decryption In cryptography, the encryption/decryption algorithms are public; the keys are secret.
- 42. Symmetric-key cryptography • The cipher, an algorithm that is used for converting the plaintext to cipher text, operates on a key, which is essentially a specially generated number (value). • To decrypt a secret message (cipher text) to get back the original message (plaintext), a decrypt algorithm uses a decrypt key. • In symmetric key cryptography, same key is shared, i.e. the same key is used in both encryption and decryption as shown in Fig.5.36. • The algorithm used to decrypt is just the inverse of the algorithm used for encryption. For example, if addition and division is used for encryption, multiplication and subtraction are to be used for decryption. • Symmetric key cryptography algorithms are simple requiring lesser execution time. As a consequence, these are commonly used for long messages. However, these algorithms suffer from the following limitations: – Requirement of large number of unique keys. For example for n users the number of keys required is n (n-1)/2. – Distribution of keys among the users in a secured manner is difficult.
- 43. Figure :Symmetric-key cryptography In symmetric-key cryptography, the same key is used by the sender (for encryption) and the receiver (for decryption). The key is shared.
- 44. Symmetric-Key Cryptography Symmetric-Key Cryptography Traditional Ciphers Substitution cipher Monoalphabetic Polyalphabetic Transposition ciphers
- 45. Substitution cipher Monoalphabetic Substitution • One simple example of symmetric key cryptography is the Monoalphabetic substitution. • In this case, the relationship between a character in the plaintext and a character in the cipher text is always one-to-one. • An example Monoalphabetic substitution is the Caesar cipher. • In this approach a character in the cipher text is substituted by another character shifted by three places, e.g. A is substituted by D. • Key feature of this approach is that it is very simple but the code can be attacked very easily. Figure :Caesar cipher
- 46. Polyalphabetic Substitution • This is an improvement over the Caesar cipher. Here the relationship between characters in the plaintext and a character in the cipher text is always one-to-many. • Example of polyalphabetic substitution is the Vigenere cipher. • In this case, a particular character is substituted by different characters in the cipher text depending on its position in the plaintext. • In figure, the top row shows different characters in the plaintext and the characters in different bottom rows show the characters by which a particular character is to be replaced depending upon its position in different rows from row-0 to row-25. • Key feature of this approach is that it is more complex and the code is harder to attack successfully. • In polyalphabetic substitution, the relationship between a character in the plaintext and a character in the cipher text is one-to-many. Figure . Vigenere cipher
- 47. Transpositional cipher • The transpositional cipher, the characters remain unchanged but their positions are changed to create the cipher text. • It illustrates how five lines of a text get modified using transpositional cipher. • The characters are arranged in two-dimensional matrix and columns are interchanged according to a key is shown in the middle portion of the diagram. • The key defines which columns are to be swapped. As per the key, character of column is to be swapped to column 3, character of column 2 is to be swapped to column 6, and so on. • Decryption can be done by swapping in the reverse order using the same key. • Transpositional cipher is also not a very secure approach. • The attacker can find the plaintext by trial and error utilizing the idea of the frequency of occurrence of characters.
- 48. Figure :Operation of a Transpositional cipher
- 49. Block Ciphers • Block ciphers use a block of bits as the unit of encryption and decryption. • To encrypt a 64-bit block, one has to take each of the 264 input values and map it to one of the 264 output values. • The mapping should be one-to-one. • Some operations, such as permutation and substitution, are performed on the block of bits based on a key (a secret number) to produce another block of bits. • In the decryption process, operations are performed in the reverse order based on the same key to get back the original block of bits.
- 50. Figure : Transformations in Block cipher
- 51. Figure: Permutation operation used in Block Ciphers Permutation: •The permutation is performed by a permutation box at the bit-level, which keeps the number of 0s and 1s same at the input and output. •Although it can be implemented either by hardware or software, the hardware implementation is faster.
- 52. Figure : Substitution operation used in Block Ciphers Substitution: •The substitution is implemented with the help of three building blocks - a decoder, one p-box and an encoder. For an n-bit input, the decoder produces a 2n bit output having only one 1, which is applied to the P-box. •The P-box permutes the output of the decoder and it is applied to the encoder. The encoder, in turn, produces an n-bit output. For example, if the input to the decoder is 011, the output of the decoder is 00001000. Let the permuted output is 01000000, the output of the encoder is 011.
- 53. A block Cipher: A block cipher realized by using substitution and permutation operations is shown in Fig. It performs the following steps: Step-1: Divide input into 8-bit pieces Step-2: Substitute each 8-bit based on functions derived from the key Step-3: Permute the bits based on the key All the above three steps are repeated for an optimal number of rounds. Fig.5.43 Encryption by using substitution and permutation
- 54. Data Encryption Standard (DES) • One example of the block cipher is the Data Encryption Standard (DES). Basic features of the DES algorithm are given below: • A monoalphabetic substitution cipher using a 64-bit character. • It has 19 distinct stages. • Although the input key for DES is 64 bits long, the actual key used by DES is only 56 bits in length. • The decryption can be done with the same password; the stages must then be carried out in reverse order. • DES has 16 rounds, meaning the main algorithm is repeated 16 times to produce the cipher text. • As the number of rounds increases, the security of the algorithm increases exponentially. • Once the key scheduling and plaintext preparation have been completed, the actual encryption or decryption is performed with the help of the main DES algorithm.
- 55. Figure :DES Fig.64-bit Data Encryption Standard
- 56. Figure :General scheme of DES
- 58. Figure :Triple DES Triple DES Triple DES, popularly known as 3DES, is used to make DES more secure by effectively increasing the key length. Its operation is explained below: • Each block of plaintext is subjected to encryption by K1, decryption by K2 and again encryption by K1 in a sequence as shown in Fig. • CBC is used to turn the block encryption scheme into a stream encryption scheme. The DES cipher uses the same concept as the Caesar cipher, but the encryption/decryption algorithm is much more complex due to the sixteen 48-bit keys derived from a 56-bit key.
- 59. Operation Modes DES can encrypt a block of 64 bits. However, to encrypt blocks of larger size, there exist several modes of operation as follows: – Electronic Code Book (ECB) – Cipher Block Chaining (CBC) – Cipher Feedback Mode (CFB) – Output Feedback Mode (OFB)
- 60. Figure :ECB mode 1. Electronic Code Book (ECB) This is part of the regular DES algorithm. Data is divided into 64-bit blocks and each block is encrypted one at a time separately. Separate encryptions with different blocks are totally independent of each other. Disadvantages of ECB • If a message contains two identical blocks of 64-bits, the cipher text corresponding to these blocks are identical. This may give some information to the eavesdropper • Someone can modify or rearrange blocks to his own advantage • Because of these flaws, ECB is rarely used.
- 61. Figure :CBC mode 2. Cipher Block Chaining (CBC) In this mode of operation, encrypted cipher text of each block of ECB is XORed with the next plaintext block to be encrypted, thus making all the blocks dependent on all the previous blocks. The initialization vector is sent along with data
- 62. Figure: CFM 3. Cipher Feedback Mode (CFB) • In this mode, blocks of plaintext that is less than 64 bits long can be encrypted. • This is commonly used with interactive terminals • It can receive and send k bits (say k=8) at a time in a streamed manner
- 63. Figure :CSM 4. Output Feedback Mode (OFB) Key features of this mode are mentioned below: OFB is also a stream cipher Encryption is performed by XORing the message with the one-time pad One-time pad can be generated in advance If some bits of the cipher text get garbled, only those bits of plaintext get garbled The message can be of any arbitrary size Less secure than other modes
- 64. Public-Key Cryptography Public-Key Cryptography RSA(Rivest, Shamir and Adleman) Choosing Public and Private Keys
- 65. Figure :Public-key cryptography Public key Cryptography In public key cryptography, there are two keys: a private key and a public key. The public key is announced to the public; where as the private key is kept by the receiver. The sender uses the public key of the receiver for encryption and the receiver uses his private key for decryption as shown in Fig.
- 66. Advantages: • The pair of keys can be used with any other entity. • The number of keys required is small. • Public-key algorithms are more efficient for short messages. Disadvantages: • It is not efficient for long messages. • Association between an entity and its public key must be verified.
- 67. RSA Algorithm • The most popular public-key algorithm is the RSA (named after their inventors Rivest, Shamir and Adleman) as shown in Fig. Key features of the RSA algorithm are given below: • Public key algorithm that performs encryption as well as decryption based on number theory. • Variable key length; long for enhanced security and short for efficiency (typical 512 bytes). • Variable block size, smaller than the key length. • The private key is a pair of numbers (d, n) and the public key is also a pair of numbers (e, n) • Choose two large primes p and q (typically around 256 bits) • Compute n = p x q and Ф = (p-1)x(q-1) • Choose a random integer number e. He then calculates d so that d*e=1 mod Ф (e x d mod (p-1)x(q-1) = 1 ). • Bob announces e and n to the public; he keeps Ф and d secret. • For encryption: C = Pe (mod n) • For decryption: P = Cd (mod n)
- 68. Figure :RSA • For encryption: C = Pe (mod n) • For decryption: P = Cd (mod n) • Bob chooses 7 and 17 as p and q and calculates n=7*17=119. • The value of Ф=(7-1)(17-1) or 96. • Now he chooses two keys, e and d. • If he chooses e to be 5,then d is 77. • Now imagine alice sends the plaintext 6 to bob. She uses the public key 5 to encrypt 6. • Plaintext:6 • C=65 mod 119 =7776 mod 119=41 • Ciphertext:41 • P=4177 mod 119=6 • Plaintext:6
- 69. An example of the RSA algorithm
- 70. Digital Signatures • Symmetric-Key Signatures • Public-Key Signatures • Message Digests • The Birthday Attack
- 71. Symmetric-Key Signatures • Digital signatures with Big Brother.
- 72. Public-Key Signatures • Digital signatures using public-key cryptography.
- 73. Message Digests • Digital signatures using message digests.
- 74. SHA-1 • Use of SHA-1 and RSA for signing nonsecret messages.
- 75. SHA-1 (2) • (a) A message padded out to a multiple of 512 bits. • (b) The output variables. (c) The word array.
- 76. Management of Public Keys • Certificates • X.509 • Public Key Infrastructures
- 77. Problems with Public-Key Encryption • A way for Trudy to subvert public-key encryption.
- 78. Certificates • A possible certificate and its signed hash.
- 79. X.509 • The basic fields of an X.509 certificate.
- 80. Public-Key Infrastructures • (a) A hierarchical PKI. (b) A chain of certificates.
- 81. Communication Security • IPsec • Firewalls • Virtual Private Networks • Wireless Security
- 82. IPsec • The IPsec authentication header in transport mode for IPv4.
- 83. IPsec (2) • (a) ESP in transport mode. (b) ESP in tunnel mode.
- 84. Firewalls • A firewall consisting of two packet filters and an application gateway.
- 85. Virtual Private Networks • (a) A leased-line private network. (b) A virtual private network.
- 86. 802.11 Security • Packet encryption using WEP.
- 87. Authentication Protocols • Authentication Based on a Shared Secret Key • Establishing a Shared Key: Diffie-Hellman • Authentication Using a Key Distribution Center • Authentication Using Kerberos • Authentication Using Public-Key Cryptography
- 88. Authentication Based on a Shared Secret Key • Two-way authentication using a challenge-response protocol.
- 89. Authentication Based on a Shared Secret Key (2) • A shortened two-way authentication protocol.
- 90. Authentication Based on a Shared Secret Key (3) • The reflection attack.
- 91. Authentication Based on a Shared Secret Key (4) • A reflection attack on the protocol of Fig. 8-32.
- 92. Authentication Based on a Shared Secret Key (5) • Authentication using HMACs.
- 93. Establishing a Shared Key: The Diffie-Hellman Key Exchange • The Diffie-Hellman key exchange.
- 94. Establishing a Shared Key: The Diffie-Hellman Key Exchange • The bucket brigade or man-in-the-middle attack.
- 95. Authentication Using a Key Distribution Center • A first attempt at an authentication protocol using a KDC.
- 96. Authentication Using a Key Distribution Center (2) • The Needham-Schroeder authentication protocol.
- 97. Authentication Using a Key Distribution Center (3) • The Otway-Rees authentication protocol (slightly simplified).
- 98. Authentication Using Kerberos • The operation of Kerberos V4.
- 99. Authentication Using Public-Key Cryptography • Mutual authentication using public-key cryptography.
- 100. E-Mail Security • PGP – Pretty Good Privacy • PEM – Privacy Enhanced Mail • S/MIME
- 101. PGP – Pretty Good Privacy • PGP in operation for sending a message.
- 102. PGP – Pretty Good Privacy (2) • A PGP message.
- 103. Web Security • Threats • Secure Naming • SSL – The Secure Sockets Layer • Mobile Code Security
- 104. Secure Naming • (a) Normal situation. (b) An attack based on breaking into DNS and modifying Bob's record.
- 105. Secure Naming (2) • How Trudy spoofs Alice's ISP.
- 106. Secure DNS An example RRSet for bob.com. The KEY record is Bob's public key. The SIG record is the top-level com server's signed has of the A and KEY records to verify their authenticity.
- 107. Self-Certifying Names • A self-certifying URL containing a hash of server's name and public key.
- 108. SSL—The Secure Sockets Layer • Layers (and protocols) for a home user browsing with SSL.
- 109. SSL (2) • A simplified version of the SSL connection establishment subprotocol.
- 110. SSL (3) • Data transmission using SSL.
- 111. Java Applet Security • Applets inserted into a Java Virtual Machine interpreter inside the browser.