CIS14: Consolidating Authorization for API and Web SSO using OpenID Connect
- 2. CONSOLIDATING AUTHENTICATION AND API AUTHORIZATION USING OPENID CONNECT John Bradley Copyright © 2014 Ping Identity Corp.All rights reserved. 2Confidential — do not distribute
- 3. SAML SOAP WS-* SAML Web SSO SAML SOAP WS-* Typical SAML Deployment model Confidential — do not distribute Copyright © 2014 Ping Identity Corp.All rights reserved. 3
- 4. Typical SAML Deployment model Confidential — do not distribute Copyright © 2014 Ping Identity Corp.All rights reserved. 4 • Two flows – One using Web SSO for Authentication. – One call to a STS to exchange authentication token for security token. – Typically no user consent. – Not mobile friendly.
- 5. OpenID Connect OpenID Connect Deployment model Confidential — do not distribute Copyright © 2014 Ping Identity Corp.All rights reserved. 5 OAuth 2
- 6. OpenID Connect Deployment model Confidential — do not distribute Copyright © 2014 Ping Identity Corp.All rights reserved. 6 • Single flow – One request returns both Identity Assertion and security token for access. – Opportunity for user consent for API and login in a single interface. – Mobile/REST friendly.
- 7. Connect Rolls Confidential — do not distribute Copyright © 2014 Ping Identity Corp.All rights reserved. 7 • Authorization Server (IdP) – Authorization endpoint – Token endpoint • Client (SP) • Resource Server (API)
- 8. Authentication & Authorization request Confidential — do not distribute Copyright © 2014 Ping Identity Corp.All rights reserved. 8 • The basic OAuth Authorization request contains a list of scopes (resources) that the client is requesting access to. • Connect adds a single scope to the request called “openid” that causes the Identity assertion to be returned.
- 9. Authorization Response Confidential — do not distribute Copyright © 2014 Ping Identity Corp.All rights reserved. 9 • The Authorization server response is standard OAuth • The Authorization server returns a single use artifact called a code. • This prevents PII leakage via the browser, and prevents large redirect URI that cause problems in some browsers.
- 10. Request for tokens Confidential — do not distribute Copyright © 2014 Ping Identity Corp.All rights reserved. 10 • The client uses its credentials to make a direct authenticated request to the Authorization Server with the code received from the Authorization server via the users browser. • This is a simple http POST request. • This request is standard OAuth.
- 11. Token Response Confidential — do not distribute Copyright © 2014 Ping Identity Corp.All rights reserved. 11 • Standard OAuth response containing – Refresh Token – Access Token – JWT id_token (Connect extension to OAuth)
- 12. Identity Assertion Confidential — do not distribute Copyright © 2014 Ping Identity Corp.All rights reserved. 12 • JWT Contains – Audience – Issuer – Subject – Issued At – Expiry – Other optional claims like Authentication context.
- 13. Refresh Token Confidential — do not distribute Copyright © 2014 Ping Identity Corp.All rights reserved. 13 • Used to make additional requests for access tokens. – Allows access tokens to be short lived. – Allows Authorization server to revoke API access by not granting new access tokens. – Revoked refresh tokens cause the client to attempt reauthorization by the Resource owner (user).
- 14. Access Token Confidential — do not distribute Copyright © 2014 Ping Identity Corp.All rights reserved. 14 • The token is added to REST calls to a Resource server’s API. – The token can be a signed JWT – The token can be opaque and introspected via callback to the Authorization server.
- 15. Delta between Oauth 2 and Connect to add basic Authentication Confidential — do not distribute Copyright © 2014 Ping Identity Corp.All rights reserved. 15 • One additional scope requested “openID” • One additional parameter returned id_token.
- 16. Native Applications Confidential — do not distribute Copyright © 2014 Ping Identity Corp.All rights reserved. 16 • Many social native applications use the id_token from a login at google to authenticate to their own API.
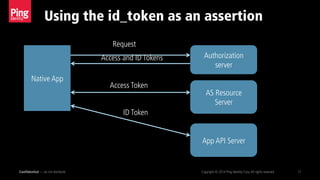
- 17. Using the id_token as an assertion Confidential — do not distribute Copyright © 2014 Ping Identity Corp.All rights reserved. 17 Native App Authorization server App API Server AS Resource Server Request Access and ID Tokens Access Token ID Token
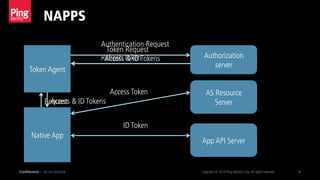
- 18. NAPPS Confidential — do not distribute Copyright © 2014 Ping Identity Corp.All rights reserved. 18 Token Agent Authorization server App API Server AS Resource Server Authentication Request Refresh Token Access Token ID Token Native App Request Token Request Access & ID Tokens Access & ID Tokens
- 19. QUESTIONS? John Bradley @ve7jtb Confidential — do not distribute Copyright © 2014 Ping Identity Corp.All rights reserved. 19