Azure Low Lands 2019 - Building secure cloud applications with Azure Key Vault
- 1. Building secure cloud applications with Azure Key Vault Tom Kerkhove Azure Architect at Codit, MSFT Azure MVP
- 2. Thank you to our sponsors! Gold Sponsors Silver Sponsors Community Sponsors
- 3. Hi! Tom Kerkhove • Azure Architect at Codit • Microsoft Azure MVP & Advisor • Belgian Azure User Group (AZUG) blog.tomkerkhove.be @TomKerkhove tomkerkhove
- 5. Great! Let’s ship it?! × No centralized secret management × No secure storage for sensitive information × No way to revoke access for a specific user/application × No way to updating secrets when they have expired/been rolled × No control over whom has access
- 6. Introducing Azure Key Vault • Provides secure storage for sensitive information, including storing cryptographic keys in hardware security modules (HSM) • Automatically failing over to secondary region in read-only mode • Allows you to : • Store sensitive information as secret • Use keys for cryptographical purposes • Manage certificates
- 7. Keys & Secrets • Secret • Used to store sequences of bytes • Consumers can read & write secret values to it • Encrypted before stored in vault • Limited to 10 kB • Typically used for connection strings, authentication keys, etc. • Key • Stores a RSA 2048, 3072 & 4096 key • Can be used to perform crypto operations such as encryption & signing • Cannot be read back • Higher latency
- 8. Different types of keys • Software Keys • Operations performed on VM in Azure • Typically used for Dev/Test • Cheap • HSM Keys • Stored encrypted in HSM • Operations performed on HSM directly • Requires Premium Vault • More secure
- 9. Personas
- 10. Last March this happend....
- 12. Use Certificates
- 14. Authenticating to Azure Key Vault • Authentication is fully handled by Azure Active Directory • Only works for the default Azure AD directory • Use basic or certificate authentication • However, you still need to store authentication information in your configuration private async Task<string> AuthenticationCallback(string authority, string resource, string scope) { var adApplicationId = configuration.Get<string>("KeyVault.Auth.ApplicationId"); var adApplicationSecret = configuration.Get<string>("KeyVault.Auth.AppSecret"); var authContext = new AuthenticationContext(authority); var clientCredential = new ClientCredential(adApplicationId, adApplicationSecret); var token = await authContext.AcquireTokenAsync(resource, clientCredential); return token.AccessToken; }
- 15. Authenticating to Azure Key Vault
- 17. Code
- 18. Great! Let’s ship it?! ✓ Control over whom has access ✓ Centralized secret management ✓ Secure storage for sensitive information ✓ Capability to revoke access for a specific user/application ✓ Capability to update secrets when they have expired/been rolled × Keys to the kingdom are still stored as before
- 19. Enter Azure AD Managed Service Identity (MSI) • Delegate authentication to the Azure resource that runs your app • Azure Resource Manager will create & assign an Azure AD Application to your resource • Currently only supports system-defined AD Application names • Not all Azure services support this, yet • No authentication information nor authentication logic required • Super easy and more secure
- 21. Great! Let’s ship it?! ✓ Control over whom has access ✓ Centralized secret management ✓ Secure storage for sensitive information ✓ Capability to revoke access for a specific user/application ✓ Capability to update secrets when they have expired/been rolled ✓ Authentication delegated to Azure ❕ Not all Azure services already support MSI
- 22. Authorization
- 23. Authorization • Managing vault instance (“control-plane”) • Based on RBAC roles • Managing vault contents (“data-plane”) • Defined in “Advanced Access Policies” • Granular control over assigned permissions • Permissions defined on a vault-level • Assigned to AD user, group or application • Ie. only set secrets without being able to see them
- 24. Demo Time!
- 25. Authorization • Be careful about whom can manage your vault instance • Take into account that people can add themselves to permissions to the vault contents • Use least-priviledge principle • If they don’t need it, don’t give it to them
- 27. Great! Let’s ship it?! ✓ Secrets securely stored × Everybody can access each others secrets × Single point of failure • Think about your security boundaries • Vault level permissions – Be careful whom can do what • Use multiple Key Vault instances if they have different security boundaries • Use resource locks on your vault instance • Prevent people from accidentally deleting all your secrets
- 30. Web Worker WorkerWorkerWorker Worker Worker WorkerWorkerWorker Worker Web WebWebWeb Web Web WebWebWeb
- 31. Great! Let’s ship it?! ✓ Secrets securely stored ✓ Seperation of domains × Not scalable • Cache secrets • Avoids hitting Azure Key Vault when scaling out • Avoids unrequired network calls • Use in-memory cache only and make it short-lived • Your application should be aware of this
- 32. Web Worker WorkerWorkerWorker Worker Worker WorkerWorkerWorker Worker Web WebWebWeb Web Web WebWebWeb Cache Cache CacheCacheCache Cache Cache CacheCacheCache
- 33. Web Worker Appsettings.json “Using API Key ‘XYZ’” Cache
- 34. Great! Let’s ship it?! × You cannot trust your vault consumers × People leave the company, but what do they take with them? × Leaked credentials are not being revoked • Automatically generate new authentication keys • Limits risk of leaked credentials usage • (Azure) Automation is your best friend • Your application should be aware of this ❕ You cannot do this with all secrets ❕ Be careful – Other applications might be using the same credentials
- 35. WebCache Key: foo Secret: ServiceBus Name: ServiceBus Secret: foo Step 1: Generate new secondary key Step 2: Update secret to use secondary key Step 3: Generate new primary key Step 4: Update secret to use primary key Generate keys
- 36. Name: ServiceBus Secret: bar WebCache Key: foo Secret: ServiceBus Name: ServiceBus Secret: foo Step 1: Generate new secondary key Step 2: Update secret to use secondary key Step 3: Generate new primary key Step 4: Update secret to use primary key Generate keys Get uncached secret Key: bar
- 37. Key Rotation in Action
- 38. Key Vault enables new scenarios
- 39. Key Vault enables new scenarios • Sync on-premises HSMs to Azure Key Vault • Enables Bring-Your-Own-Key • Azure SQL Database / SQL Server • Azure Data Lake Store • Azure Storage • Automatically rotatation Azure Storage keys
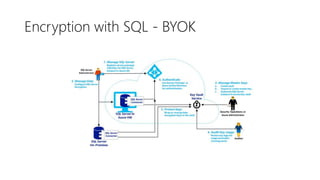
- 40. Encryption with SQL - BYOK
- 41. Encryption with SQL - BYOK
- 43. Auditing & Operations • Full audit trail containing every action • “Azure Key Vault Analytics” solution in Log Analytics (http://bit.ly/key-vault-log-analytics)
- 44. Tips
- 45. Tips • Be transparent • Secrets & keys are versioned, make sure that consumers are aware of these • This is important for cryptographical scenarios where decryption needs to use the correct version of the key • Key Vault is not a configuration store • You need to build your own configuration store • Dependencies fail • Make sure you handle downtime of your dependency, if possible at all • Key Vault integration in VSTS
- 46. Managing secrets in VSTS Variable Groups* Build / Release Environment Built-in Task* Inline** * Integration with Azure Key Vault
- 47. Using Key Vault in variable groups
- 48. Getting secrets inside your build/release
- 49. Making security in Azure simpler
- 50. Secrets made easy with • OSS library that makes it easier to build secure apps on Azure. • Provides a (cached*) Key Vault secret provider out-of-the-box, more to come. • GitHub – https://github.com/arcus-azure/arcus.security • Docs - security.arcus-azure.net * Memory cache only for now, as this is most secure
- 51. Secrets made easy with Arcus • Get started quickly: • PM> Install-Package Arcus.Security.Secrets.AzureKeyVault -Version 0.1.0-alpha • Example: var clientId = Configuration.GetValue<string>("Arcus:ServicePrincipal:ClientId"); var clientKey = Configuration.GetValue<string>("Arcus:ServicePrincipal:AccessKey"); var keyVaultUri = Configuration.GetValue<string>("Arcus:KeyVault:Uri"); var vaultAuthenticator = new ServicePrincipalAuthenticator(clientId, clientKey); var vaultConfiguration = new KeyVaultConfiguration(keyVaultUri); var keyVaultSecretProvider = new KeyVaultSecretProvider(vaultAuthenticator, vaultConfiguration); var secretValue = await keyVaultSecretProvider.Get(“EventGrid-AuthKey");
- 52. Wrap-Up
- 53. Takeaways • Security should not be an after thought • It is about limiting the risk of exposure, not removing it • Go Key Vault all the way, including build & release • Do not use one central Key Vault, use one per security domain • Delegate authentication to Azure with Azure AD MSI • Automatically roll your secrets and keep your vault up to date • Use Arcus.Security to get easily started! (open for feedback) • More information on security.arcus-azure.net
- 54. 54
- 55. Track 1 • 11:55 – 12:40 • Architecting Autonomous Driving Solutions on Azure • Kristof Rennen Track 2 • 11:55 – 12:40 • From One Release Per Quarter To 30 Times A Day • Marcel de Vries
Editor's Notes
- #18: Evangelistisch overkomen – adviseren Gevoel: heeft visie .
- #23: Evangelistisch overkomen – adviseren Gevoel: heeft visie .
- #25: Evangelistisch overkomen – adviseren Gevoel: heeft visie .
- #38: Evangelistisch overkomen – adviseren Gevoel: heeft visie .
- #39: Evangelistisch overkomen – adviseren Gevoel: heeft visie .
- #43: Evangelistisch overkomen – adviseren Gevoel: heeft visie .
- #45: Evangelistisch overkomen – adviseren Gevoel: heeft visie .
- #50: Evangelistisch overkomen – adviseren Gevoel: heeft visie .
- #53: Evangelistisch overkomen – adviseren Gevoel: heeft visie .