Breaking the Edge -- A Journey Through Cloud, Edge and Fog Computing
- 1. Advanced Technology Office 28 rue Jean Rostand 91400, Orsay France Angelo Corsaro, PhD Chief Technology Officer ADLINK Tech. Inc. [email protected] AT() BREAKING the EdgeA Journey Through Cloud, Edge and Fog Computing
- 2. State of Practice Innovating Together
- 4. Hardware Tiers in IoT A generic IoT/IIoT system has three different hardware tiers Off-premises data-centre which may be private or public On-premises edge infrastructure Things with computational, communication and storage capacity
- 5. Hardware Tiers in IoT The key architectural variations that are discussed today all depends on the bias, or lack of thereof, on a specific tier
- 7. Cloud Centric Architectures The majority of IoT (and Telco infrastructures) systems are today cloud- centric These systems are characterised by device- to-cloud communication and in-cloud analytics
- 8. Cloud Centric Perspective The IoT application is deployed, managed and monitored using the Cloud IaaS infrastructure
- 9. Cloud-Centric Perspective The early days of IoT/IIoT have been biased by a cloud centric perspective The cloud infrastructure is mature and operationally convenient… Yet cloud centric architectures don’t fit well for a large class of IoT/IIoT applications
- 11. Cloud Computing There is sufficient bandwidth to push data to the Cloud. Assumption #1
- 12. This slides have been crafted by Angelo Corsaro Any use of these slides that does include me as Author/Co-Author is plagiary Smart Factory 0.5 TB of data produced per day
- 13. Cloud Computing Connectivity is not an issue. A device will (almost) always be connected to the cloud. Assumption #2
- 14. This slides have been crafted by Angelo Corsaro Any use of these slides that does include me as Author/Co-Author is plagiary Searching Operator…
- 15. Cloud Computing The latency induced by cloud-centralised analytics and control is compatible with the system’s dynamic Assumption #3
- 16. This slides have been crafted by Angelo Corsaro Any use of these slides that does include me as Author/Co-Author is plagiary Autonomous Vehicles coordination of fast moving autonomous vehicles intermittent connectivity dynamic pairing of devices
- 17. Cloud Computing The connectivity cost is negligible Assumption #4
- 18. Cost of connectivity is an issue in Smart Grids as the operator has to pay for the 2G/3G/4G data-link
- 19. Cloud Computing Companies are comfortable with exposing their data to the cloud. Assumption #5
- 20. ARE YOU SURE?
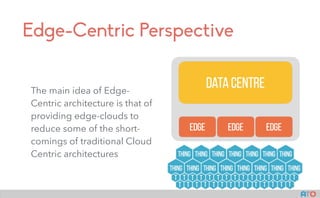
- 22. Edge-Centric Perspective The main idea of Edge- Centric architecture is that of providing edge-clouds to reduce some of the short- comings of traditional Cloud Centric architectures
- 23. Edge-Centric Perspective The application is deployed, managed and monitored using the Cloud IaaS infrastructure which cooperates with edge Cloud infra.
- 24. Edging the Edge
- 25. The Fuzzy Edge The edge is an extremely fuzzy concept as it depends entirely from infrastructure ownership structure and application domain. What’s the edge in the image below? MEC InfraNet-Core EDGE Infra Things, Machines, User Terminal, …
- 26. Hamletic Moment
- 27. To edge, or not to edge: that is the question: Whether ‘tis nobler in the mind to suffer The slings and arrows of outrageous boundaries, Or to take arms against a sea of edges, And by opposing end them?
- 28. Reflection Time…
- 29. Cloud, Edge, and Things Cloud Computing gives operationally convenient abstractions and tools to manage and provision data-centre resources Edge Computing alleviates some of the challenges posed by cloud computing at the cost of introducing some fragmentation in the infrastructure. But how about the Things? In a large class of system we need to manage and provision them too…
- 30. What’s Really Needed? A scalable, location transparent, data- centric layer that allows us to effectively get the data where needed while minimising resource usage 1
- 31. What’s Really Needed? A geo-distributed, location transparent, storage infrastructure that allows us to store data where it makes sense to support local computing while maintaining location transparent access to it. 2 Home/Building Management – Edge Computing As we tackle the problem, it would also make sense to address edge computing and ensure that our solution will allow for location transparent and uniform access to data even if that is living on the edge.
- 32. What’s Really Needed? 3 An infrastructure that allows us to federate compute, storage, I/O and communication resources regardless of their location (Fog Infrastructure)
- 33. Filling the Gap
- 34. Connectivity
- 35. Internet protocol For historical reasons, internet has been built on a host-centric communication model. (machine-to-machine)
- 36. The Internet today Most of the application on the internet today are data / content centric. What matters to the user is the data not as much who has it…
- 37. Internet protocol The internet protocol is inherently one-to-one. Broadcast and multicast communications are not viable in wide networks. Thus the diffusion of the same data to multiple consumers is very inefficient.
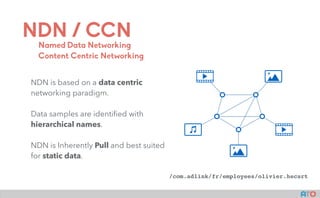
- 38. NDN / CCN NDN is based on a data centric networking paradigm. Data samples are identified with hierarchical names. NDN is Inherently Pull and best suited for static data. Named Data Networking Content Centric Networking /com.adlink/fr/employees/olivier.hecart
- 39. DDS is a great data centric technology which embraces powerful concepts like strong decoupling between publishers and subscribers. But DDS has been designed for small to medium systems and suffers from major scalability issues on larger systems. It is push based which makes uneasy to retrieve specific data or to properly filter data streams. Data Distribution Service
- 40. The Internet of Tomorrow With the raise of IoT, the different devices connected to the internet use very heterogeneous networking technologies (TCP/IP, BLE, 3G, 6LowPan, …). Some endpoints are extremely constrained w.r.t computational, communication resources as well as energy.
- 41. Internet scale data-centric protocol that unifies data-sharing between any kind of device including those constrained with respect to the node resources, such as computational resources and power, as well as the network.
- 42. Conceptual Model zenoh provides a data-centric abstraction in which applications can read and write data autonomously and asynchronously. The data read and written by zenoh applications is associated with one or more resources identified by a URI. DDS Global Data Space ... Data Writer Data Writer Data Writer Data Reader Data Reader Data Reader Data Reader Data Writer R1 R2 R i Rn -- These are Resources /myhouse/floor/1/musicroom/LightStatus /myhouse/floor/2/musicroom/LightStatus /myhouse/floor/2/bedroom/erik/LightStatus -- These are Selections /myhouse/floor/2/bedroom/*/LightStatus /myhouse/**/LightStatus /myhouse/**
- 43. Conceptual Model Data can be pushed to subscribers and storages and be queried from storages. zenoh pub/sub protocol (push) storage/query protocol (pull) Publisher SubscriberStorage write / stream subscribestore query
- 44. Conceptual Model Data can be pushed-to, pulled or queried-from applications periodically or asynchronously.
- 45. Routing Adaptative, fault tolerant, brokering and routing.
- 46. Reliability & Ordering Z1 Z2 Z6 Z3 Z5 Z4A1 A2 application-to-application reliability first-to-last-broker Zenoh supports 3 levels of reliability : • Hop to hop reliability. Ensures reliability and ordering when NO failures. • App-to-app reliability. • First-to-last-broker reliability. More scalable than app-to-app reliability.
- 47. Zenoh clients • Low footprint C client • OCaml client • Python client • Bash client
- 48. A piece of code Publisher : z = zenoh.connect('127.0.0.1:7447') pub = z.declare_publisher('/demo/hello') pub.write('Hello world'.encode()) Subscriber : z = zenoh.connect('127.0.0.1:7447') z.declare_subscriber(‘/demo/**', lambda rid, data: print('received {}'.format(data.tobytes().decode())))
- 49. Performance
- 50. Throughput 0 2500 5000 7500 10000 8 16 32 64 128 256 512 1024 2048 4096 8192 16384 zenoh Cyclone DDS Mbps
- 51. Key Highlights
- 52. Key Highlights Extremely Resource Constrained Environments Defined the most wire/power/memory efficient protocol in the market to provide connectivity to extremely constrained targets Support for: - Peer-to-peer and brokered communication - Batched data and deltas - Ordered reliability and fragmentation - Queries zenoh zenoh 6LowPAN 802.15.4 BLE 2G/3G/ LTE Unspecified API App App App … Application TCP UDP IP
- 53. Key Highlights Protocol implementation for a 8-bit micro-controllers takes 300 Bytes of RAM and has wire-overhead of 4 bytes for data samples 7 6 5 4 3 2 1 0 +-+-+-+-+-+-+-+-+ |R|S|P| SDATA | +---------------+ ~ SN ~ +---------------+ ~ RID | SID ~ +---------------+ ~ PRID ~ +---------------+ ~ [Payload] ~ +---------------+
- 54. Storage
- 55. Home/Building Management Imagine that we have a collection of houses in a residence or equivalently buildings on a business park that we would like to monitor and manage. In other terms, we would like to read, write and observe data specic to the house/building. More importantly we would want to do this from anywhere. //residence-1/house-1/kitchen/airquality //residence-1/house-1/alert //residence-1/house-1/utilities/electricity //residence-1/house-1/laundry/washer/schedule //residence-1/house-n/kitchen/airquality //residence-1/house-n/alert //residence-1/house-n/utilities/electricity //residence-1/house-n/laundry/washer/schedule ...
- 56. Cloud Centric Home/Building Management One solution is to push the data to the Cloud Applications can use the cloud as the place to go and get or set any information concerning our house/buildings. That is a very commont approach... But, is this a solution to the problem, or is it just delaying the problem? //residence-1/house-i/kitchen/airquality //residence-1/house-i/alert //residence-1/house-i/utilities/electricity //residence-1/house-i/laundry/washer/schedule
- 57. Scaling Out At some point scaling-up won’t be a solution and we will have to scale-out and leverage multiple cloud regions. With multiple cloud regions the unifed view of the system is lost, and we are back to the starting point.
- 58. Home/Building Management – Edge Computing As we tackle the problem, it would also make sense to address edge computing and ensure that our solution will allow for location transparent and uniform access to data even if that is living on the edge.
- 59. Introducing Yaks
- 60. YAKS provides a distributed service that implements an eventually consistent, scalable, location transparent, high performance, and distributed key/value store with pluggable back-ends and front-end. YAKS is equipped with dynamic discovery and supports extremely well dynamic environments YAKS data is globally accessible without requiring local replication as in traditional key/ value stores.
- 61. Home/Building Management with YAKS Regardless of wether data is the device, the edge infrastructure or the cloud, YAKS provides location transparent access through a distributed key-value store abstraction. All the details concerning how to get the data from were it is to were it needs to are handled by YAKS.
- 62. Architecture
- 63. YAKS Architecture YAKS has a modular architecture relying on different kinds of plugins Engine AccessControl Crypto Authetication DBMS … Memory Socket … REST zenoh Security Plugin Backend Plugin Transport Plugin Frontend Plugin GPS Clock Logical C/C++ Go Java JavaScript … API
- 64. Deployment Topology zenoh zenoh zenoh zenoh zenoh zenoh routing infrastructure zenoh
- 65. Abstractions
- 66. YAKS YAKS is a distributed service to define, manage and operate on key/value spaces The key abstractions at the core of yaks are Path, Value, Selector, Storage, Workspace, and Admin Space
- 67. YAKS Values A YAKS Value is defined by the following tuple: v = e, c, t Where e is the encoding and c represents the content and t is a logical timestamp used for ordering.
- 68. YAKS Path A Path in YAKS is a string having the following format: /s1/s2/…/sn Where si does not contain wildcard characters such as ‘*’ and ‘**’ Example: /com/adlink/factory/shanghai/line/1/machine/ /net/icorsaro/home/livingroom/lightbulb/10
- 69. YAKS Selector A Selector in YAKS is the conjunction of an expression identifying a set of keys and optionally a predicate on values /se1/se2/…/sen [? [predicate] [(properties)]] [#projection] Where: • sei may contain wildcard characters such as ‘*’ and ‘**’ • the predicate has the form: f1 op v1 f2 op v2… fn op vn (where op can be , =, =, =, and !=) • the properties is a semicolon separated list of key=value • the projection is a semicolon separated list of fields to project. Example: /net/icorsaro/home/*/lightbulb?luminosity50#id /net/icorsaro/home/*/consumption/statistics?(start=yesterday;end=now)#average;std
- 70. Selector / Path matching ‘*’ to match 1 segment (full or partial): Examples: /home/bob/*/light /home/bob/room*/light /home/bob/*/light matches matches doesn’t match /home/bob/kitchen/light /home/bob/room1/light /home/bob/floor1/room2/light Examples: /home/bob/**/light /home/bob/** matches also matches /home/bob/kitchen/light /home/bob/floor1/room2/light /home/bob/floor2/room1/temp ‘**’ to match several segments (full):
- 71. YAKS Storage A Storage in YAKS is defined by means of a selector s and backend B. Where the back-end B may be one of supported backends, such as main-memory, DBMS, etc. A Storage with selector s will store path,value for which s matches the path.
- 72. KV Space Operations YAKS primitives to operate on the key/value space are: • put, update, remove, get • subscribe/unsubscribe • register_eval/unregister_eval, eval
- 73. Put/Get put Data are published via put/update. Matching storages receive and store the data. Later on, applications can query the data
- 74. Put/Get get Data are published via put/update. Matching storages receive and store the data. Later on, applications can query the data get
- 75. Subscriptions subscribe put subscribe Data are published via put/update. Yaks routes the publications to all matching subscribers.
- 76. Evals register_eval eval Any application can bind a computation with a path. Applications can trigger the execution of these functions by evaluating the path.
- 77. Key Primitives class Workspace(object): def put(self, path, value) def update(self, path, value) def remove(self, path) def get(self, selector) def subscribe(self, selector, listener) def unsubscribe(self, subscription_id) def register_eval(self, path, callback) def unregister_eval(self, path) def eval(self, selector)
- 78. Play with it…. us-west.yaks.is /demo/uswc/** us-east.yaks.is /demo/us-east/** eu-central.yaks.is /demo/eu/** ap-southeast.yaks.is /demo/ap/** Example: • Put data: curl -X PUT -d 'Hello World!' http://us-west.yaks.is:8000/demo/eu/test • Get data: curl http://ap-southeast.yaks.is:8000/demo/*/test
- 80. Vision fogOS aims at providing a decentralised infrastructure for provisioning and managing (1) compute, (2) storage, (3) communication and (3) I/O resources available anywhere across the network. fogOS addresses highly heterogeneous systems even those with extremely resource-constrained nodes.
- 81. — Decentralised Design fogOS can manage and provision any network connected device on which it agent is running Its decentralised architecture allows to manage the system from anywhere and does not need any specific set of nodes running as “servers”
- 82. Architecture
- 83. Modules Fog Infrastructure Manager Virtualises the hardware infrastructure, such as computational, communication, storage and I/O resources, and abstract the key primitives provided by system software, such as the OS Provides primitives for managing these virtualised infrastructure Provides infrastructure level monitoring information. Fog Atomic Entity Manager (FAEM) Fog Entity Orchestrator Fog Infrastructure Manager (FIM)
- 84. Modules Fog Atomic Entity Manager Manages the Fog Atomic Entity (FAE) life-cycle and maps then into FDU to be deployed by the FIM. Triggers the FAE specific monitoring plug-ins in response to relevant events such as migration, failure, etc. This information may be used by the Fog Entity Orchestrator (FEO) to trigger re-allocation, restart, etc. The main abstraction provided by the FAEM is the Fog Atomic Entity Fog Atomic Entity Manager (FAEM) Fog Entity Orchestrator Fog Infrastructure Manager (FIM)
- 85. Modules Fog Entity Orchestrator Validates the entity specification Decides based on available resources and entity constraints if it can be accepted. Device an allocation of the entity that optimises resource utilisation while satisfying the entity’s functional and non-functional requirements Executes the allocation by proper coordination with the FAEM and FIM Continuously monitors and reconfigures entity allocation to ensure that the constraints are satisfied. Fog Atomic Entity Manager (FAEM) Fog Entity Orchestrator Fog Infrastructure Manager (FIM)
- 86. Entity An entity fragment is directed acyclic graph of atomic entities. An entity is a directed acyclic graph of atomic entities and entity fragments. VM C UK C BE UK VM: Virtual Machine C: Container UK: Uni Kernel BE: Binary Executable uS: micro Service uS BE UKUK
- 87. AT() Information Model fogOS’s information model defines the describes associated with nodes, entities and networks. Additionally it provides an abstract way to describe applications and relations between them. It is implemented as a set of YANG Models.
- 88. AT() Relation with ETSI NFV and MEC IM fogOS information model is a super-set of the ETSI (European Telecommunications Standards Institute) MEC and ETSI NFV Specifically, fogOS supports the declaration of I/O constraints. YANG models have also been defined for fogOS abstractions.
- 89. Architecture fogOS is composed by: NDN. At its lowest level, it leverages a Named Data Network (NDN) infrastructure based on zenoh. DDS can also be used as a transport — not necessarily an NDN YAKS. A distributed key-value store that leverages the NDN for scalability Agent. The core logic of fogOS, it takes care of managing, monitoring and orchestrating entities through plugins Plugins. Plugins provide supports for atomic entities, OS, networks, etc. zenoh YAKS AgentPlugins Network Data Link Physical Transport
- 90. AT() Plugins fog 5 leverages plugins interact and manage: Atomic Entities (Runtimes) Networks OSes Monitoring Resource Orchestration Resource Management For each type of plugin an interface has been defined. For instance, plugins that manage atomic entities have to implement the FSM for the kind of atomic entity they will be managing. zenoh YAKS AgentPlugins Network Data Link Physical Transport
- 91. Local/Global and Actual/Desired fogOS uses YAKS to maintain the actual and desired state for global and node-specific information This separation ensures that there is never write concurrency on the actual state and that the evolution is entirely under the control of the agent Desired Global Store Actual Global Store Actual node-local Store Desired node-local Store AgentWorld Actual node-local Constraint Store Desired node-local Constraint Store Plug-in 1 Plug-in 2 Plug-in N Normal Node MCU MCU MCU Desired Global Store Actual Global Store Actual node-local Store Desired node-local Store Agent Plug-insWorld
- 92. AT() Interact with fogOS To interact with fogOS we provide a set of API for Python3. These API uses interact with fogOS using the distributed data store. The demo that we show uses this API. API Docs: https://atolab.github.io/fog05- doc/fog05.html#module-fog05.api
- 93. — The Eclipse Project Since June 2018
- 94. OpenFog and 5GPPP fogOS is one of the infrastructure identified as compliant with the 5G principles and requirements by the EU 5GPPP working group fogOS architecture is compatible with the OpenFog Reference Architecture. Additionally fogOS is used as the reference fog platform in several test-beds
- 95. Users and Press Mm2 Multi-access edge platform manager - NFV (MEPM-V) MEAO fog05 + MEPM-V plugin 5GCity Components ETSI NFV Components ETSI MEC Components Multilayer Orchestrator Operation Support System Os-Ma-nfvo NFVO VNFM (ME app LCM) VNFM (ME platform LCM) Virtualisation Infrastructure Manager Multi-access edge platform (VNF) NFVI Data plane (VFN/PNF) Os-Ma-nfvo Me app (VNF) Service Mm5 Mp1 Mp2 Or-Vnfm Or-Vi Ve-Vnfm-vnf Nf-Vi Nf-Vn Nf-Vn Ve-Vnfm-em Vi-Vnfm = Mm6 Mv3 Mv2 Mv1 ETSI NFV Reference points ETSI MEC Reference points ETSI NFV-MEC Reference points • Mv1 ~ Os-Ma-nfvo • Mv2 ~ Ve-Vnfm-em • Mv3 ~ Ve-Vnfm-vnf Mm3* Mm1 fog05 + MEAO plugin
- 96. Wrapping Up
- 97. Key Takeaways Cloud Computing is operationally convenient but it has several limitations that limit its applicability in a large class of applications. 1
- 98. Key Takeaways The Edge is fuzzy in essence and limiting by nature. We should focus on infrastructure that allows to unify the computational, communication, communication and I/O resources end-to-end 2
- 99. Key Takeaways The world outside of the data-center is constrained, heterogeneous, and tricky. Yet, that’s the place where the difference can be made. 3



















































![Key Highlights
Protocol implementation for a
8-bit micro-controllers takes
300 Bytes of RAM and has
wire-overhead of 4 bytes for
data samples
7 6 5 4 3 2 1 0
+-+-+-+-+-+-+-+-+
|R|S|P| SDATA |
+---------------+
~ SN ~
+---------------+
~ RID | SID ~
+---------------+
~ PRID ~
+---------------+
~ [Payload] ~
+---------------+](https://image.slidesharecdn.com/2019-190502144523/85/Breaking-the-Edge-A-Journey-Through-Cloud-Edge-and-Fog-Computing-53-320.jpg)















![YAKS Selector
A Selector in YAKS is the conjunction of an expression identifying a set of keys and
optionally a predicate on values
/se1/se2/…/sen [? [predicate] [(properties)]] [#projection]
Where:
• sei may contain wildcard characters such as ‘*’ and ‘**’
• the predicate has the form: f1 op v1 f2 op v2… fn op vn
(where op can be , =, =, =, and !=)
• the properties is a semicolon separated list of key=value
• the projection is a semicolon separated list of fields to project.
Example:
/net/icorsaro/home/*/lightbulb?luminosity50#id
/net/icorsaro/home/*/consumption/statistics?(start=yesterday;end=now)#average;std](https://image.slidesharecdn.com/2019-190502144523/85/Breaking-the-Edge-A-Journey-Through-Cloud-Edge-and-Fog-Computing-69-320.jpg)






























