Building Multi-tenant, Configurable, High Quality Applications on .NET for any Cloud – Demystified
- 1. Building Multi-tenant Highly Secured Applications on .NET for any Cloud - Demystified 26-Jun-2013 www.techcello.com (A Division of Asteor Software Inc)
- 2. © Techcello www.techcello.com Housekeeping Instructions All phones are set to mute. If you have any questions, please type them in the Chat window located beside the presentation panel. We have already received several questions from the registrants, which will be answered by the speakers during the Q & A session. We will continue to collect more questions during the session as we receive and will try to answer them during today’s session. In case if you do not receive answers to your question today, you will certainly receive answers via email shortly. Thanks for your participation and enjoy the session!
- 3. © Techcello www.techcello.com Techcello Introduction Cloud Ready, SaaS/Multi- Tenant Application Development Framework Provides end-end SaaS Lifecycle Management Solution Redefines the way enterprise softwares are built and managed Saves anywhere between 30- 50% of time and cost
- 4. © Techcello www.techcello.com Speaker Profiles 14+ years of experience in architecting cloud and SaaS solutions for both ISVs and Enterprises Chief architect in designing and constructing CelloSaaS framework Plays consultative role with customers in implementing technical solutions Jothi Rengarajan Senior Technical Architect TechCello James McGovern Chief Architect Hewlett-Packard One of the top 10 enterprise technologists in the world Has authored more than 6 books on computing and dozens of published articles Twenty years experience in developing, managing and deploying large scale technology systems, business processes, and strategies
- 5. © Techcello www.techcello.com Protection of information. It deals with the prevention and detection of unauthorized actions and ensuring confidentiality, integrity of data. Tenant data isolation RBAC – Prevent unauthorized action Data security Web related top threats as per OWASP Security Audit trail Security in Multi-Tenancy
- 6. © Techcello www.techcello.com Tenant Data Isolation Database Routing Based On Tenant Application Layer Auto Tenant Filter Tenant Based View Filter
- 7. © Techcello www.techcello.com Authentication • Kinds of authentication tokens and source • Username Password • Multi factor authentication • Claims based Authentication • User identification information • Encrypted cookie • Session Identity store • Custom Store • Password encryption/ hashing • Password change policy externalization • Active Directory Integration • Identity Federation Role Based Access Control (RBAC)
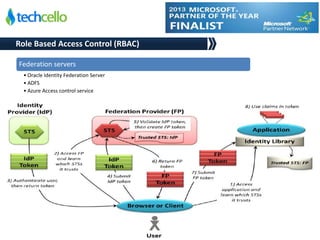
- 8. © Techcello www.techcello.com Federation servers • Oracle Identity Federation Server • ADFS • Azure Access control service Role Based Access Control (RBAC)
- 9. © Techcello www.techcello.com Role Based Access Control (RBAC) Authorization • Use privileges to define roles • Privilege based control for actions • Privilege based access for data • Role mapped to privileges and user mapped to roles • Code demands necessary privileges • Roles should be defined by business users • Configuration based privilege control
- 10. © Techcello www.techcello.com OWASP – TOP 10 Threats 2013 A1 Injection A2 Broken Authentication and Session Management (was formerly A3) A3 Cross-Site Scripting (XSS) (was formerly A2) A4 Insecure Direct Object References A5 Security Misconfiguration (was formerly A6) A6 Sensitive Data Exposure (merged from former A7 Insecure Cryptographic Storage and former A9 Insufficient Transport Layer Protection) A7 Missing Function Level Access Control (renamed/broadened from former A8 Failure to Restrict URL Access) A8 Cross-Site Request Forgery (CSRF) (was formerly A5) A9 Using Known Vulnerable Components (new but was part of former A6 – Security Misconfiguration) A10 Unvalidated Redirects and Forwards
- 11. © Techcello www.techcello.com Web application top threats • Man in middle attack • Use secure channel - https • SQL Injection • Use parameterized queries • Malicious script injection and Cross Site Scripting • Validate input if it is a safe HTML • URL escape, Html escape and Javascript escape untrusted data • Cross site request • Challenge-Response such as CAPTCHA • Synchronizer Token • Origin header OWASP – open web application security project
- 12. © Techcello www.techcello.com Encryption • Preferred Symmetric compared to asymmetric due to performance • Use Strong Keys • Change Keys Periodically Key storage • Store in Key Vault and store away from encrypted data • Double encryption • Dual key storage Database encryption • Watch for Performance implications • Encrypt only necessary columns Data Security – Data Storage
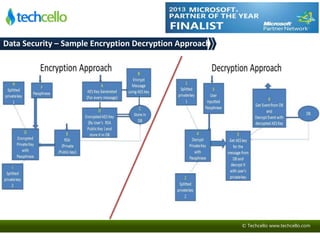
- 13. © Techcello www.techcello.com Data Security – Sample Encryption Decryption Approach
- 14. © Techcello www.techcello.com Web Server to Application server • Soap Web Service • WS-Security • message security • transport security -https • client authentication - username, certificate, claims federation • Rest • Https • Custom asymmetric encryption • custom authentication Data Security – Data Transit End user browser to web server • Https • Custom encryption Application to Database • Transport Security
- 15. © Techcello www.techcello.com Event Audit • Covers • Who does the action? • What action is performed? • What is the context in which the operation is performed? • What time is the action performed? • Event audit information – subject, target, context, user, datetime • Audit details stored in a separate datastore for better performance • Realtime audit details – audit cache server Security Audit
- 16. © Techcello www.techcello.com Transaction and Change Audit • Transaction Audit • Snapshot: Exact copy of the row stored in history tables • More suitable if requests to access past data are more • More data growth • Change Audit • Only the delta of the state change captured as part of change tables • More suitable when changes need to be reported and past data are not required much • Used more for Security tracking purposes • Easier to implement by using methods available out of the box in RDBMS such as CDC for SQL server • Asynchronous Mode : For better performance and if we wish that audit should not roll back the transactions it is advisable to audit in a asynchronous thread. Security Audit
- 17. How does it work? Cloud Ready, Multi-Tenant Application Development Framework Tenant Provisioning Licensing Metering Billing Data Backup Administrative Modules User Management Role/Privilege Mgmt. Single Sign-on Dynamic Data Scope Auditing Security Modules Business Rules Workflow Dynamic Forms Enterprise Engines Events Notification Templates Integration Modules Query Chart Reports Ad-hoc Builders Code Templates Master Data Mgmt. Forms Generation Productivity Boosters Application Multi-Tenancy & Tenant Data Isolation Custom Fields Custom LoV Settings Template Themes & Logo Pre & Post Processors Configurability Modules Cello Cloud Adapters Cello Stack – At a Glance
- 18. © Techcello www.techcello.com Contact Details Jothi Rengarajan ([email protected]) James McGovern ([email protected]) Reference URLs Web : http://www.techcello.com ROI Calculator : http://www.techcello.com/techcello-roi-calculator Demo Videos : http://www.techcello.com/techcello-resources/techcello- product-demo SaaS e-Book: http://www.techcello.com/techcello-resources/techcello- resources-white-papers Thank You