Chapter6TransportLayer header format protocols-2.ppt
- 1. The TCP Segment Header TCP header length in 32 bit words, URG-urgent, ACK- ack number is valid, PSH-push, RST-reset connection, SYN-used to establish connection, FIN-used to release connection
- 2. The TCP Segment Header (2) The pseudoheader (part of the IP header) included in the TCP checksum.
- 3. TCP Options Some TCP options are: Maximum segment size (MSS): Specified what is the payload the sender is able to receive. (Default MSS = 536 bytes, i.e., Segment size = MSS + 20). SMSS/RMSS is Sender/Receiver MSS. Window scale: The window size field allows for upto 2^16 bytes of data. But this might be inefficient for high bw x delay situations. This options TCP indicate a scaling factor. Negative acknowledgement: Lets receiver user NAKs to get realize selective repeat rather than the normal go-back-N TCP behaviour.
- 4. TCP Connection Establishment (a) TCP connection establishment in the normal case. (b) Call collision. 6-31 Initial sequence numbers are not 0. TCP uses a clock tick counter (at 4 usecs rate) to setup the initial sequence numbers. This scheme prevents delayed duplicates.
- 5. TCP Connection Establishment Each side releases the connection independently. If A send a FIN to B and B ACKs that FIN. It only means no data will flow from A to B. Data can still flow from B to A indefinitely. In all 4 messages are required to completely release the connection. A FIN and ACK for each side. However, the second FIN and the first ACK can be combined for 3 messages. TCP avoids the Two-Army problem in connection release using timers. If the FIN is not ACKed within within a fixed time, the connection is released.
- 6. TCP Connection Management Modeling The states used in the TCP connection management finite state machine.
- 7. TCP Connection Management Modeling (2) TCP connection management finite state machine. The heavy solid line is the normal path for a client. The heavy dashed line is the normal path for a server. The light lines are unusual events. Each transition is labeled by the event causing it and the action resulting from it, separated by a slash.
- 8. TCP Transmission Policy Window Management in TCP
- 9. Sender Receiver The senders application performs a 2K write to the receivers buffer, which is now half full. SEQ=0 2K Application does a 2K write Empty 0 4K 2K
- 10. Sender Receiver SEQ=0 2K ACK=2048 WIN=2048 Application does a 2K write Empty 0 4K 2K The receiver acknowledges the first 2048 bytes and informs the sender that there is space in the buffer for 2048 bytes.
- 11. Sender Receiver SEQ=0 2K ACK=2048 WIN=2048 Application does a 2K write SEQ=2048 2K Application does a 2K write Empty 0 4K Full 2K The sender’s application writes another 2K. The receivers buffer is now full and the sender is blocked.
- 12. Sender Receiver SEQ=0 2K ACK=2048 WIN=2048 SEQ=2048 2K ACK=4096 WIN=0 Application does a 2K write Application does a 2K write Sender is blocked Empty 0 4K Full 2K The receiver acknowledges the next 2048 (total of 4096) bytes and informs the sender that there is no space in the buffer. The sender is still blocked.
- 13. Sender Receiver SEQ=0 2K ACK=2048 WIN=2048 SEQ=2048 2K ACK=4096 WIN=0 Application does a 2K write Application does a 2K write { Sender is blocked ACK=4096 WIN=2048 Sender may send up to 2K Empty 0 4K Full 2K 2K The receiver clears 2048 bytes from the buffer and informs the sender that this space is available for use. The sender is now unblocked and may send 2K.
- 14. Sender Receiver SEQ=0 2K ACK=2048 WIN=2048 SEQ=2048 2K ACK=4096 WIN=0 ACK=4096 WIN=2048 Application does a 2K write Application does a 2K write SEQ=4096 1K Application does a 1K write { Sender is blocked Sender may send up to 2K Empty 0 4K Full 2K 2K 2K 1K The sender’s application writes another 1K. The receivers buffer now has 1K of space available.
- 15. TCP Transmission Policy Window management in TCP.
- 16. TCP Transmission Policy Sender TCP is not required to send data as soon as it arrives from the application. Sender TCP might buffer to create larger segments (up to receiver window size) Receiver TCP is not required to send ACK as soon as receives a segment. Receiver might delay ACK for up to 500 msecs hoping to piggyback ACK on data from receiver to sender. Such ACKS are called delayed ACKs
- 17. TCP Transmission Policy Silly window syndrome.
- 18. Nagle's algorithm Purpose is to allow the sender TCP to make efficient use of the network, while still being responsive to the sender applications. Idea: If application data comes in byte by byte, send first byte only. Then buffer all application data till until ACK for first byte comes in. If network is slow and application is fast, the second segment will contain a lot of data. Send second segment and buffer all data till ACK for second segment comes in. This way the algorithm is clocking the sends to speed of the network and simultaneously preventing sending several one byte segments back to back. An exception to this rule is to always send (not wait for ACK) if enough data for half the receiver window or MSS.
- 19. TCP congestion control We looked at how TCP handles flow control. In addition we know the congestion happens. The only real way to handle congestion is for the sender to reduce sending rate. So how does on detect congestion ? In old days, packets were lost due to transmission errors and congestion. But nowadays, transmission errors are very rare (except for wireless). So, TCP assumes a lost packet as an indicator of congestion. So does TCP deal with congestion ? It maintains an indicator of network capacity, called the congestion window
- 20. TCP Congestion Control (a) A fast network feeding a low capacity receiver. (b) A slow network feeding a high-capacity receiver.
- 21. TCP congestion control In essence TCP deals with two potential problems separately: Problem Solution Receiver capacity Receiver window (rwnd) Network capacity Congestion window (cwnd) Each window reflect the number of bytes the sender may transmit. The sender sends the minimum of these two sizes. This size is the effective window. Effective window is the minimum of what the sender thinks is all right to send (congestion window) and what the receiver this is ok to send (receiver window). We assume that both rwnd and cwnd are measured in bytes (an alternative is SMSS).
- 22. TCP Congestion Control – 4 Stages TCP uses these stages in updating cwnd. 1. Slow start: Initial state. Rapidly grow cwnd 2. Congestion avoidance: Slowly grow cwnd. 3. Fast retransmit: Retransmit without waiting for timeout. 4. Fast recovery: Don't reset cwnd. }Control amount of data injected into network READING: TCP Congestion Control RFC 2581 http://www.rfc-editor.org/rfc/rfc2581.txt
- 23. TCP Congestion Control – Slow start This is the initial state or state after loss of data. cwnd grows by multiples of SMSS per ACK Initial window (IW) is 1 SMSS. So after the ACK comes in cwnd becomes 2 SMSS. Then after the 2 ACKs come in the cwnd grows to 4 SMSS and so on. So growth is in fact exponential. After data loss cwnd is set to the Loss Window (LW) size of 1 SMSS. Slow start threshold (ssthresh) is used to change from slow start to congestion avoidance. If cwnd < ssthesh, slow start else congestion avoidance. Initial ssthresh is usually set to rwnd.
- 24. TCP Congestion Control – Congestion Avoidance This stage follows slow start after cwnd > ssthresh cwnd grows by 1 SMSS per RTT. This stage continues until congestion is detected. For every non-duplicate ACK update cwnd using: cwnd += SMSS * (SMSS/cwnd) Assuming cwnd bytes are sent in a burst in full SMSS segments, after an interval of RTT after the burst (cwnd/SMMS) ACKs will be received. So the total cwnd will increase by SMSS * (SMSS/cwnd) * (cwnd/SMSS), which is simply SMMS. Hence using the above updating formula cwnd will increase by 1 SMSS per RTT.
- 25. TCP congestion control – Adjusting ssthresh When TCP detects a loss, cwnd falls to LW (1 SMSS). Also the ssthresh is adjusted using: ssthresh = max (FlightSize / 2, 2*SMSS) FlightSize is the number of unacked bytes (bytes still on the wire). In most cases cwnd is equal to FlightSize.
- 26. TCP Congestion Control An example of the Internet congestion algorithm.
- 27. TCP congestion control – Fast Retransmit and Fast Recovery TCP receiver should send duplicate ACK when out-of-order segment arrives. A duplicate ACK at sender could mean: 1. Lost segment (all subsequent segments will generate duplicate ACKs) 2. Re-ordered segments. 3. Network replicated ACK or data segment. Fast retransmit algo says retransmit segment after getting 3 duplicate acks, without waiting for RTO (Retransmit Timeout) to expire. Fast recovery says don't treat the above retransmit as a lost segment (since RTO did not expire), so don't reset cwnd to LW. The reasoning is that since (duplicate) ACKs are arriving, the receiver is getting segments, so segments are leaving the network. In fast recovery, adjust ssthresh using previous formula.
- 28. TCP Timer Management Of the several timers TCP maintains the most important is the retransmission timer RTO, (also called timeout) . After each segment is sent, TCP starts a retransmission timer, if ACK arrives before timer expires, cancel timer. If timer expires first, consider segment lost. How long should RTO be ? Typically some small multiple of RTT. So how to measure RTT ? Measure time between segment sent and ACK receiver. Unfortunately, in the Internet RTT are not constant, they a vary a lot.
- 29. TCP Timer Management (a) Probability density of ACK arrival times in the data link layer. (b) Probability density of ACK arrival times for TCP.
- 30. Maintaining RTO TCP dynamically updates the current RTT and most recent measurement M (how long it took to receive the last ACK) using: However, using a constant multiple of RTT as the RTO is inflexible since it fails to respond to variance. TCP keep an estimator of deviation D. D keeps track of the the variance in RTT, i.e, in RTT – M using: The final retransmission timeout (RTO) is calculated as: M RTT RTT ) 1 ( | | ) 1 ( M RTT D D D RTT Timeout 4 8 7
- 31. RTO exceptions Assume a segment times out and is then retransmitted. An ACK for the segment arrives. So for purposes for calculating M how do we decide if the ack is for the first send or the retransmission ? We cannot. It might be for the first, but very delayed, or might be for the second. So we cannot use ACKs of retransmitted segments for calculating M (or updating RTT). Rule: Don't use acks of retransmitted segments to update RTT. Instead, if segment times out, simply double RTO. This is called the Karn's algorithm.
- 32. Other timers Persistent timer: Assume receiver advertises a window = 0. Sender stop sending. Receiver send segment with new window size. This segment is lost. Sender will keep waiting forever. After getting a window of 0 the sender uses a persistent timer periodically to probe the receiver to send window advertisements. Once it gets a non-zero window the timer is stopped. Keep alive timer: During long periods of inactivity, one side might send to the other a keep alive probe to check if the other side is alive.
- 33. Wireless TCP Wireless network can lose packet in wireless “links”. Since TCP assumes loss is due to route congestion, it will reduce sending rate. If the loss due to wireless link, TCP should resend asap, i.e., increase overall sending rate. Therefore, the usual TCP will perform very badly on lossy wireless networks. Problem complicated by heterogeneous networks. If part wired and part wireless, then reaction of TCP should depend on where the loss occurred (wired or wireless part).
- 34. Split TCP Splitting a TCP connection into two connections. But now ACK to sender does not mean mobile host got it. It simply means the base station got it. No end-to-end semantics.
- 35. Wireless TCP – Balakrishnan et. al Wireless Snooping agent Snooping agent caches segments from fixed to mobile hosts and forwards it to mobile host with small timeout of its own. If agent does not see mobile host's ack, the agent retransmits the segment. If agent sees two duplicates acks from mobile host (indicator of lost segment) it drops the acks (does not forwards to fixed host) and retransmits from cache. Advantage: It is completely transparent to both hosts. Fixed host Mobile host Base station
- 36. Transactional TCP (a) Remote Procedure Call (RPC) using normal TPC. (b) RPC using T/TCP.
- 37. Performance Issues a) Performance Problems in Computer Networks b) Network Performance Measurement c) System Design for Better Performance d) Fast TPDU Processing
- 38. Performance Problems in Computer Networks (a) At t = 0, (b) After 500 μsec, (c) After 20 msec, (d) After 40 msec. ransmitting 1MB from San Diego to Boston Other network performance problem causes: Synchronous overload: Broadcast storm due to bad UDP broadcast Segment. Power loss leading to DHCP/file server overload.
- 39. Network Performance Measurement The basic loop for improving network performance. A. Measure relevant network parameters, performance. B. Try to understand what is going on. C. Change one parameter.
- 40. Network Performance Measurement Make sure that the sample size is large enough Make sure that he samples are representatives Be careful when using a coarse-grained clock Be sure that nothing unexpected is going on during your tests. Caching can wreak havoc with measurements. Understand what you are measuring. Be careful about extrapolating the results.
- 41. System Design for Better Performance Rules: A. CPU speed is more important than network speed. B. Reduce packet count to reduce software overhead. C. Minimize context switches. D. Minimize copying. E. You can buy more bandwidth but not lower delay. F. Avoiding congestion is better than recovering from it. G. Avoid timeouts.
- 42. Fast TPDU Processing The fast path from sender to receiver is shown with a heavy line. The processing steps on this path are shaded.
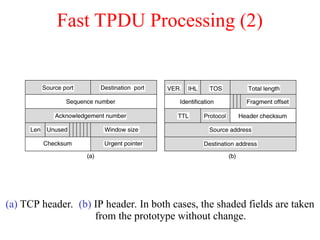
- 43. Fast TPDU Processing (2) (a) TCP header. (b) IP header. In both cases, the shaded fields are taken from the prototype without change.
- 44. Timing Wheel A timing wheel.