CIS 2015 Practical Deployments Enterprise Cloud Access Management Platform - Matt Cochran
- 1. Ma# Cochran Architect, GE Corporate [email protected] Prac%cal deployments Enterprise cloud access management pla;orm
- 2. Disclaimer The views and opinions expressed in this presentaAon are my own and do not necessarily represent the views or opinions of the General Electric Company or any of its subsidiaries.
- 7. A changing IT landscape Close 32 datacenters & migrate 8000+ apps to cloud Enterprise WAM capability needs to grow with use cases Apps Legacy WAM Partners Customers Self service Improve services around B2B & B2C Mobile, SaaS & 3rd party use cases on the rise Focus on self service & enabling automation
- 8. Client Cloud Mobile SaaS API dev Risk pla9orm Legacy AM Biz AuthZ data Extended user data Biz APIs Corp APIs Admin App dev Developers Enterprise WAM – Legacy model End User Firewall Internal app SM agent ü Application logic ü Consuming headers ü Bolt on security at end ü Agent support ü Biz specific policy ü Network dependent ü Stateful Support teams Operations Data owners Platform teams
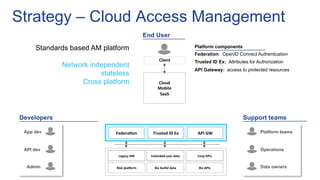
- 9. Federa%on Trusted ID Ex API GW Client Cloud Mobile SaaS API dev Risk pla9orm Legacy AM Biz AuthZ data Extended user data Biz APIs Corp APIs Admin App dev Developers Strategy – Cloud Access Management End User Standards based AM platform Network independent stateless Cross platform Federation: OpenID Connect Authentication Trusted ID Ex: Attributes for Authorization API Gateway: access to protected resources Platform components Support teams Operations Data owners Platform teams
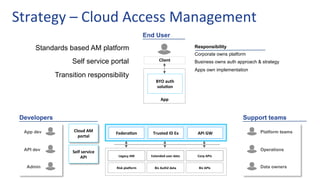
- 10. Federa%on Trusted ID Ex API GW Client Cloud Mobile SaaS API dev Request portal Risk pla9orm Legacy AM Biz AuthZ data Extended user data Biz APIs Corp APIs Admin App dev Developers Strategy – Cloud Access Management End User Self service API Standards based AM platform Self service portal Request portal: Self service workflows & documentation Self service API: Secured admin APIs for self service regi. Developer tools Support teams Operations Data owners Platform teams
- 11. Federa%on Trusted ID Ex API GW Client Cloud Mobile SaaS API dev Cloud AM portal Risk pla9orm Legacy AM Biz AuthZ data Extended user data Biz APIs Corp APIs Admin App dev Developers Strategy – Cloud Access Management End User Self service API Standards based AM platform Self service portal Transition responsibility App BYO auth solu%on Corporate owns platform Business owns auth approach & strategy Apps own implementation Responsibility Support teams Operations Data owners Platform teams
- 12. Federa%on Trusted ID Ex API GW BYO auth solu%on Client App API dev Cloud AM portal Risk pla9orm Legacy AM Biz AuthZ data Extended user data Biz APIs Corp APIs Admin App dev OpenID Connect REST / SCIMDevelopers ü Seamless ü It just works ü Self service ü Standards based ü Cross platform ü Improve platform ü Focus on architecture ü Refine solutions Cloud AM: Cross platform design pattern End User Self service API Request Client_id: mattsApp Client_secret: wut Scopes: openid, profile, api1 Response { “id_token” : “abc.def.geh”, “access_token” : “abc123”, “refresh_token” : “1234567” } Support teams Operations Data owners Platform teams
- 13. Federa%on Trusted ID Ex API GW Client OpenID Connect Cloud AM: Web applications Web Server Mod auth openidc App server App code App Deployment example • mod auth openidc, written by Hans Zandbelt • Open source apache plugin Features • Fully implemented OpenID Connect OP • Language agnostic (apache plugin) • Easy setup – Chef • Can write path specific attribute policy for AuthZ • Can bind to virtual directory for biz specific attributes Other solutions • Mod_ox from Gluu • Apache Oltu • Spring Security • Forgerock OpenIG • PingAccess
- 14. Federa%on Trusted ID Ex API GW Mobile device Cloud AM: Mobile applications Managed app 1 (hybrid) Mobile device – Corporate container Deployment example Swift: https://github.com/p2/OAuth2 ObjC: https://github.com/nxtbgthng/OAuth2Client Hybrid: homegrown library Features • Authenticate users via in-app OS browser using custom URL schemes, eg. Myapp://redirect_url • Browser used as “NAPPS Light” for cross application SSO (apps reuse session stored in browser cookie) • Refresh tokens can be stored in keychain, unlocked with touchID or pin (depending on use case) Other solutions • NAPPS Authorization agents • Auth0 • CA API Management (Layer 7) SSO Managed app 2 (na%ve) Auth lib Auth lib Safari SSO session OpenID Connect OAuth2access token
- 15. AuthorizaAon – fine grain, risk based Gen 2 API Management integraAon B2B: IDP as a service, 3rd party in use cases (IDaaS) IdenAty assurance Next steps
- 16. Appendix
- 17. Cloud AM: Strategy Push responsibility to business - App teams (not Corporate) own implementation & support Provide repeatable design patterns, documentation & guidance Create network independent, standards based, self service abstraction layer on top of legacy AM TrustednetworkExposed mobile Cloud SaaS 3rd Party Legacy WAM Directories Federation: OpenID Connect Authentication Platform Components Federa%on Trusted ID Ex API GW Trusted ID Ex: Attributes for Authorization API Gateway: access to protected resources