Computer funadamentals
- 1. COMPUTERFUNDAMENTALS 1. INTRODUCTION TO COMPUTER SYSTEM 1.0.Founderof Computer 1.1.Generations Of Computers 1.2. First Generation Computers 1.3. Second Generation Computers 1.4.Third Generation Computers 1.6.Fifth Generation Computers 2. DEFINITION OF COMPUTER AND ITS CONCEPTS. 2.0computer Definition 2.1computer Block Diagram 2.2. Input Devices 2.2.1. Keyboard 2.2.1.2 Keyboard Shortcuts 2.2.2 Mouse 2.2.3 Joystick 2.2.4 Light Pen 2.2.5Track Ball 2.2.6 Scanner 2.2.7 Digitizer [Graphic Tablet] 2.2.8 Microphone 2.2.9.MagneticInk Card Reader(MICR) 2.3. Optical Character Reader (OCR) 2.4 Bar Code Reader 2.5 Webcam 2.6 Biometrics [Thumb Impression / Face Detection] 2.7. Output Devices 2.7.1.Monitors 2.7.2. Cathode-Ray Tube (CRT) Monitor 2.7.3. Flat-Panel Display Monitor 2.8.Printers 2.8.1.ImpactPrinters
- 2. COMPUTERFUNDAMENTALS 2.8.2. Character Printers 2.8.3. Dot Matrix Printer 2.8.4. Daisy Wheel 2.8.5line Printers 2.8.6drum Printer 2.8.7chain Printer 2.8.9.Non-ImpactPrinters 2.9.CharacteristicsofNon-ImpactPrinters 2.9.1laser Printers 2.9.2. Inkjet Printers 3. FUNDAMENTALS OF COMPUTER ARCHITECTURE 3.1. CPU Block Diagram 3.2. CPU Phases 3.3. Memory Unit 3.4. Memory Classification 3.4.1. Random Access Memory [Ram] 3.4.2. SRAM 3.4.3 .DRAM 3.5. Rom Classification 3.5. 1.PROM 3.5.2. EPROM 3.5.3. EEPROM 3.6 Cache Memory 3.7. Control Unit 3.8. Arithmetic Logic Unit [ALU] 3.9. Buses In CPU 3.9.1. Instruction Cycle 3.9.2. Measure of CPU Performance.
- 3. COMPUTERFUNDAMENTALS 4. MOTHERBOARD [INTERNAL COMPONENTS] 4.1Features ofMotherboard 4.2PopularManufacturers 4.3The Important Components of Motherboard 4.4complete Mother Board View 5. COMPUTER –SOFTWARE 5.1.System Software 5.1.1. Operating System 5.1.2. System Development Software 5.1.3. Utility Programs 5.2. Application Software 5.2.2. Custom Software 5.3. Assembler 5.4. Compiler 5.5. Interpreter 6. OPERATING SYSTEM 6.1Basics of operating system 6.2 Types Of Operating System 6.3Process management 6.31Process 6.3.2Process scheduling 7. INTER PROCESSOR COMMUNICATION 7.1introduction 7.1.1. Race Conditions 7.1.2Semaphores 7.1.3Message Passing 7.1.4scheduling Algorithms
- 4. COMPUTERFUNDAMENTALS 8. DEADLOCKS 8.1.1 Definition Of Deadlock 8.1.2 Characteristics 8.1.3deadlock’s Prevention 8.1.4 Banker’s Algorithm 9. MEMORY MANAGEMENT 9.1.1basic Memory Management 9.1 .2definition 9.1.3 Logical &Physical Address Map 9.1.4continuous Memory Allocation 9.1.5fixed And Variable Portion 9.1.6 Internal And External Fragmentation And Compaction 9.1.7paging: Principle Of Operation 9.1.8 Page Allocation 9.1.9hardware Support For Paging 9.1.10protection And Sharing 9.1.11disadvantages Of Paging 9.2 Virtual Memory 9.2. Basics Of Virtual Memory 9.2.1demand Paging 9.2.2.Pagereplacement Algorithm 9.2.3.Reference String 9.2.4.First In First Out Algorithm[FIFO] 9.2.5.Leastrecently Used Algorithm[LRU] 9.2.7 Least Frequently Used Algorithm[LFU] 9.2.8.Most Frequently Used Algorithm[MFU]
- 5. COMPUTERFUNDAMENTALS 10. I/O MANAGEMENT 10.1 I/O Devices, 10.2 Device Controllers 10.3direct Memory Access Principles Of I/O Software: 10.4 Goals of Interrupt Handlers 10.5 Device Drivers 10.6secondary-Storage Structure: 10.7 Disk Structure 10.8 Disk Scheduling Algorithm 10.9. Raid [RedundantArray Of IndependentDisks] 10.10. Disk Attachment 11. FILEMANAGEMENT 11.1 Access Methods 11.2file Types 11.3file Operations 11.4 Directory Structure
- 6. COMPUTERFUNDAMENTALS 1. INTRODUCTION TOCOMPUTER SYSTEM CHARLES BABBAGE [DEC-16-1791toOCT-18-1871]
- 7. COMPUTERFUNDAMENTALS 1. 0.FOUNDER OF COMPUTER 1.0. First-GenerationComputerfromCharlesBabbage CHARLES BABBAGE, [26 December 1791 –18 October 1871] Was A Mathematician, Philosopher, Inventor And Mechanical Engineer, Babbage Is Best Remembered For Originating The Concept Of A Programmable Computer. Parts Of Babbage's Uncompleted Mechanisms Are On Display In The London Science Museum. In 1991, A Perfectly Functioning Difference Was Constructed From Babbage's Original Plans. Built To Tolerances Achievable In The 19th Century, The Success Of The Finished Engine Indicated That Babbage's Machine Would Have Worked. 1. A. First Programmable Computer 1.B.Babbage Engine
- 8. COMPUTERFUNDAMENTALS 1.1.GENERATIONS OF COMPUTERS 1.1.A. Generation Of Computers
- 9. COMPUTERFUNDAMENTALS 1.2. FIRST GENERATION COMPUTERS [1946-1959]. The Computers Of First Generation Used Vacuum Tubes As The Basic Components For Memory And Circuitry For CPU (Central Processing Unit). These Tubes, Like Electric Bulbs, Produced A Lot Of Heat And Were Prone To Frequent Fusing Of The Installations, Therefore, Were Very Expensive And Could Be Afforded Only By Very Large Organizations. In This Generation Mainly Batch Processing Operating System Were Used. Punched Cards, Paper Tape, And Magnetic Tape Were Used As Input And Output Devices. The Computers In This Generation Used Machine Code As Programming Language. 1.2. A. First -Generationcomputer1 1.2.B.First-Generationcomputer2 1.2. C. Top View of First-Generation Computer
- 10. COMPUTERFUNDAMENTALS 1.2.1FIRST GENERATION COMPUTERS FEATURES The main features of first generation are: Vacuum Tube Technology Unreliable Supported Machine Language Only Very Costly Generated Lot Of Heat Slow Input And Output Devices Huge Size Need of A.C. Non-Portable Consumed Lot Of Electricity Some computers of this generation were: ENIAC EDVAC UNIVAC IBM-701 IBM-650 1.2.1. A. John Von Neumann with IAS Computer 1.2.1.B Vacuum Tubes.
- 11. COMPUTERFUNDAMENTALS 1.3. SECOND GENERATION COMPUTERS [1959-1965] In This Generation Transistors Were Used That Were Cheaper, Consumed Less Power, More Compact In Size, More Reliable And Faster Than The First Generation Machines Made Of Vacuum Tubes In This Generation, Magnetic Cores Were Used As Primary Memory And Magnetic Tape And Magnetic Disks As Secondary Storage Devices . In This Generation Assembly Language And High-Level Programming Languages Like FORTRAN, COBOL Was Used. The Computers Used Batch Processing And Multiprogramming Operating System. 1.3.A.Secondgeneration Ibm Computer 1.3.B.Secon Generation Computer 1.3.C Secongeneration Pc 1.3.D.Secondgeneration Pc 1.3.E.Ibmpc [Tranistors Replaced By Vaccumetubes]
- 12. COMPUTERFUNDAMENTALS 1.3.1. SECOND GENERATION COMPUTERS FEATURES The main features of second generation are: Use Of Transistors Reliable In Comparison To First Generation Computers Smaller Size As Compared To First Generation Computers Generated Less Heat As Compared To First Generation Computers Consumed Less Electricity As Compared To First Generation Computers Faster Than First Generation Computers Still Very Costly A.C. Needed Supported Machine And Assembly Languages Some computers of this generation were: IBM 1620 IBM 7094 CDC 1604 CDC 3600 UNIVAC 1108 1.3.1.A.Ibm7090pc 1.3.1.B.Secondgeneration Pc
- 13. COMPUTERFUNDAMENTALS 1.4.THIRD GENERATION COMPUTERS[1965-1971] The Computers Of Third Generation Used Integrated Circuits (IC's) In Place Of Transistors. A Single IC Has Many Transistors, Resistors And Capacitors Along With The Associated Circuitry. The IC Was Invented By Jack Kilby. This Development Made Computers Smaller In Size, Reliable And Efficient. In This Generation Remote Processing, Time-Sharing, Multi-Programming Operating System Were Used. High-Level Languages (FORTRAN-II TO IV, COBOL, PASCAL PL/1, BASIC, ALGOL-68 Etc.) Were Used During This Generation. The Main Features Of Third Generation Are: IC Used More Reliable In Comparison To Previous Two Generations Smaller Size Generated Less Heat Faster Lesser Maintenance Still Costly A.C Needed Consumed Lesser Electricity Supported High-Level Language Some Computers Of This Generation Were: Ibm-360 Series Honeywell-6000 Series PDP(Personal Data Processor) Ibm-370/168 Tdc-316
- 14. COMPUTERFUNDAMENTALS 1.4.1THIRD GENERATION COMPUTERS 1.4.1.A. Third Generation Computer1 [ It Is Developed By High Levelonguage Like C] 1.4.1.B Third Generation Computer [Having Ups Separate Cpu] 1.4.1.C.Corei7based Embedded Computer 1.4.1.D.Third Generation Pc
- 15. COMPUTERFUNDAMENTALS 1.5.FOURTH GENERATION COMPUTERS[1971-1980] The Computers of Fourth Generation Used Very Large Scale Integrated (VLSI) Circuits. VLSI Circuits Having About 5000 Transistors And Other Circuit Elements And Their Associated Circuits On A Single Chip Made It Possible To Have Microcomputers Of Fourth Generation. Fourth Generation Computers Became More Powerful, Compact, Reliable, and Affordable. As A Result, It Gave Rise To Personal Computer (Pc) Revolution. In This Generation Time Sharing, Real Time, Networks, Distributed Operating System Were Used. All The High-Level Languages Like C, C++, Dbase Etc., Were Used In This Generation. 1.5.1.FOURTH GENERATION COMPUTERS FEATURES : The Main Features Of Fourth Generation Are: VLSI Technology Used Very Cheap Portable And Reliable Use Of PC's Very Small Size Pipeline Processing No A.C. Needed Concept Of Internet Was Introduced Great Developments In The Fields Of Networks Computers Became Easily Available Some Computers Of This Generation Were: DEC 10 STAR 1000 PDP 11 CRAY-1(Super Computer)
- 16. COMPUTERFUNDAMENTALS CRAY-X-MP(Super Computer) 1.5.2.FOURTH GENERATION COMPUTERS 1.5.2.A. Fourth Generation Pc 1.5.2.B.Apple Laptop 1.5.2.Apple Pc
- 17. COMPUTERFUNDAMENTALS 1.6.FIFTH GENERATION COMPUTERS[1980-Till Date] In The Fifth Generation, The VLSI Technology Became ULSI (Ultra Large Scale Integration) Technology, Resulting In The Production Of Microprocessor Chips Having Ten Million Electronic Components. This Generation Is Based On Parallel Processing Hardware And AI (Artificial Intelligence) Software. AI Is An Emerging Branch In Computer Science, Which Interprets Means And Method Of Making Computers Think Like Human Beings .All the High-Level Languages like C and C++, Java, .Net Etc., Are Used in This Generation. Fifth Generation Computers Includes: Robotics Neural Networks Game Playing Development of Expert Systems To Make Decisions In Real Life Situations. Natural Language Understanding and Generation. 1.6.A. Fifth Generation Computers Based On Artificial Intelligence [Robots].
- 18. COMPUTERFUNDAMENTALS 1.6.B.Samsung Galaxy Tab S10.5 1.6.C.Apple I Phone6 1.6D.Samsumng S6
- 19. COMPUTERFUNDAMENTALS QUESTIONS ON COMPUTER I/O DEVICES 1. What Are The Disadvantages Of First Generation Of Computers? A) Portable B) Huge Size C) Simple D) Reliable Answer: B 2. Which Programming Was Used In The First Generation Of Computers? A) Machine Code B) High Level C) Assembly Language D) Java Answer: A 3. In First Generation Of Computers Which Type Of OS (Operating System) Was Used? A) Batch Processing B) Windows-95 C) Multiprogramming D) Time Sharing Answer: A 4. ULSI Microprocessor Was Used In Which Generation Of Computers? A) 1st B) 2nd C) 4th D) 5th Answer: D 5. When The Fifth Generations Of Computers Were Used? A) 1980-2000 B) 1965-1980 C) 1980-Onwards D) No Fifth Generations Of Computer Exist Answer: C 6. VLSI Microprocessor Was Used In Which Generation Of Computers? A) 1st B) 2nd C) 3rd D) 4th Answer: D 7. When The Fourth Generations Of Computers Were Used?
- 20. COMPUTERFUNDAMENTALS A) 1946-1959 B) 1975-1995 C) 1971-1980 D) 1980-1995 Answer: C 8. Integrated circuit (IC) was used in which generation of computers? a) First b) Second c) Third d) Fourth Answer: C 9. When the Third generations of computers were used? a) 1946-1965 b) 1965-1971 c) 1956-1965 d) 1971-1980 Answer: B 10. Transistors were used in which generation of computers? a) First b) Second c) Third Answer: B 11.Microprocessor Introduced In Which Generation A) First Generartion B) Second Generation C) Third Generation D) Fouth Generation Answer: D 12. GUI Stands For A) Graphical User Interface B) Graph User Interface C) Graph Universal Interface Answer: A
- 21. COMPUTERFUNDAMENTALS 2. DEFINITION OFCOMPUTER ANDITS CONCEPTS. 2.0. COMPUTER DEFINITION “An Electronic Device Which Is Capable Of Receiving Information (Data) In A Particular Form And Of Performing A Sequence Of Operations In Accordance With A Predetermined But Variable Set Of Procedural Instructions (Program) To Produce A Result In The Form Of Information Or Signals”. 2.1COMPUTER BLOCK DIAGRAM 2.1. A. Computer Block Diagram.
- 22. COMPUTERFUNDAMENTALS 2.2. INPUT DEVICES An Input Device Is Any Hardware Device That Sends Data To A Computer, Allowing You To Interact With And Control The Computer. The Most Commonly Used Input Devices On A Computer Are The Keyboard And Mouse. However, There Are Dozens Of Other Devices That Can Also Be Used To Input Data Into The Computer. Below Is A List Of Computer Input Devices That Can Be Used With A Computer Or A Computing Device. Keyboard Mouse Joy Stick Light Pen Track Ball Scanner Graphic Tablet Microphone Magnetic Ink Card Reader(MICR) Optical Character Reader(OCR) Bar Code Reader Webcam Biometrics (Thumb Impression / Face Detection)
- 23. COMPUTERFUNDAMENTALS 2.2. A. Input and Output Devices of Computer 2.2. Input/output devices
- 24. COMPUTERFUNDAMENTALS 2.2.1. KEYBOARD Keyboard Is The Most Common And Very Popular Input Device Which Helps In Inputting Data To The Computer. The Layout Of The Keyboard Is Like That Of Traditional Typewriter, Although There Are Some Additional Keys Provided For Performing Additional Functions. Keyboards Are Of Two Sizes 84 Keys or 101/102 Keys, But Now Keyboards With 104 Keys Or 108 Keys Are Also Available For Windows And Internet. 2.2.1. A. Gaming Type Keyboard 2.2.1.B.Sumsung Wired Keyboard 2.2.1. Apple Wireless Keyboard
- 25. COMPUTERFUNDAMENTALS The Keys On The Keyboard Are As Follows: SR.NO KEYS DESCRIPTION 1 Typing Keys These Keys Include The Letter Keys (A-Z) And Digit Keys (0-9) Which Generally Give Same Layout As That Of Typewriters. 2 Numeric Keypad It Is Used To Enter Numeric Data Or Cursor Movement. Generally, It Consists Of A Set Of 17 Keys That Are Laid Out In The Same Configuration Used By Most Adding Machines And Calculators. 3 Function Keys The Twelve Function Keys Are Present On The Keyboard Which Is Arranged In A Row At The Top Of The Keyboard. Each Function Key Has Unique Meaning And Is Used For Some Specific Purpose. 4 Control Keys These Keys Provide Cursor And Screen Control. It Includes Four Directional Arrow Keys. Control Keys Also Include Home, End, Insert, Delete, Page Up, Page Down, Control(Ctrl), Alternate(Alt), Escape(Esc). 5 Special Purpose Keys Keyboard Also Contains Some Special Purpose Keys Such As Enter, Shift, Caps Lock, NUM Lock, Space Bar, Tab, And Print Screen. 2.2.1. A. List of Keyboard Keys Table
- 26. COMPUTERFUNDAMENTALS 2.2.1.2 KEYBOARD SHORTCUTS 2.2.1. Keyboard Shortcut Keys Figure
- 27. COMPUTERFUNDAMENTALS 2.2.2 MOUSE Mouse Is Most Popular Pointing Device. It Is A Very Famous Cursor-Control Device Having A Small Palm Size Box With A Round Ball At Its Base Which Senses The Movement Of Mouse And Sends Corresponding Signals To CPU When The Mouse Buttons Are Pressed. Generally It Has Two Buttons Called Left And Right Button And A Wheel Is Present Between The Buttons. Mouse Can Be Used To Control The Position Of Cursor On Screen, But It Cannot Be Used To Enter Text Into The Computer. Advantages Easy To Use Not Very Expensive Moves The Cursor Faster Than The Arrow Keys Of Keyboard. 2.2.2. A.USB type mouse 2.2.2.B.gaming type wireless mouse 2.2.2.c.wireless mouse
- 28. COMPUTERFUNDAMENTALS 2.2.3 JOYSTICK Joystick Is Also A Pointing Device Which Is Used To Move Cursor Position On A Monitor Screen. It Is A Stick Having A Spherical Ball At Its Both Lower And Upper Ends. The Lower Spherical Ball Moves In A Socket. The Joystick Can Be Moved In All Four Directions. The Function Of Joystick Is Similar To That Of A Mouse. It Is Mainly Used In Computer Aided Designing (Cad) And Playing Computer Games. 2.2.3. A. PCJOY Stick 2.2.3.B.Logitech G27racing Wheel. 2.2.3. C. Advanced Joystick
- 29. COMPUTERFUNDAMENTALS 2.2.4 LIGHT PEN Light Pen Is A Pointing Device Which Is Similar To A Pen. It Is Used To Select A Displayed Menu Item Or Draw Pictures On The Monitor Screen. It Consists Of A Photocell And An Optical System Placed In A Small Tube. When The Tip Of A Light Pen Is Moved Over The Monitor Screen And Pen Button Is Pressed. Its Photocell Sensing Element Detects The Screen Location And Sends The Corresponding Signal To The CPU. 2.2.4. A. Win touch Tool 2.2.4.B.Computer Lighten 2.2.4. C. Asus Digitalized Tablet Using Lighten
- 30. COMPUTERFUNDAMENTALS 2.2.5TRACK BALL Track Ball Is An Input Device That Is Mostly Used In Notebook Or Laptop Computer, Instead Of A Mouse. This Is A Ball Which Is Half Inserted And By Moving Fingers On Ball, Pointer Can Be Moved. Since The Whole Device Is Not Moved, A Track Ball Requires Less Space Than A Mouse. A Track Ball Comes In Various Shapes Like A Ball, A Button And A Square. 2.2.5. A. Different Types of Trackball Mousses 2.2.5.B.Logitechmouse 2.2.5. Kingston Mouse with Orbit Ball
- 31. COMPUTERFUNDAMENTALS 2.2.6 SCANNER Scanner Is An Input Device Which Works More Like A Photocopy Machine. It Is Used When Some Information Is Available On A Paper And It Is To Be Transferred To The Hard Disc Of The Computer For Further Manipulation. Scanner Captures Images From The Source Which Are Then Converted Into The Digital Form That Can Be Stored On The Disc. These Images Can Be Edited Before They Are Printed. 2.2.6. A. Epson Scanner 2.2.6.B .Cannon Scanner 2.2.6. C .Cool Computer Scanner
- 32. COMPUTERFUNDAMENTALS 2.2.7 DIGITIZER[GRAPHIC TABLET] Digitizer Is An Input Device Which Converts Analog Information Into Digital Form. Digitizer Can Convert A Signal From The Television Or Camera Into A Series Of Numbers That Could Be Stored In A Computer. They Can Be Used By The Computer To Create A Picture Of Whatever The Camera Had Been Pointed At. Digitizer Is Also Known As Tablet Or Graphics Tablet Because It Converts Graphics And Pictorial Data Into Binary Inputs. A Graphic Tablet As Digitizer Is Used For Doing Fine Works Of Drawing And Image Manipulation Applications. 2.2.7. A. Dizitilizer 2.2.7.B.Apple Tab 2.2.7. C.Painting on tablet
- 33. COMPUTERFUNDAMENTALS 2.2.8 MICROPHONE Microphones Are A Type Of Transducer “A Device Which Converts Energy From One Form To Another. Microphones Convert Acoustical Energy (Sound Waves) Into Electrical Energy (The Audio Signal)”. Different Types Of Microphone Have Different Ways Of Converting Energy But They All Share One Thing In Common The Diaphragm. This Is A Thin Piece Of Material (Such As Paper, Plastic Or Aluminum) Which Vibrates When It Is Struck By Sound Waves . In A Typical Hand-Held MIC Like The One Below, The Diaphragm Is Located In The Head Of The Microphone. Microphone Usage In Our Real Time Computer System Example. http://www.onlinemictest.com/microphone-settings/windows-8 2.2.8. A. microphone block diagram 2.2.8.B.wireless microphone 2.2.8. C.35mm Jack W Flexible Neck Microphone
- 34. COMPUTERFUNDAMENTALS 2.2.9.MAGNETICINKCARDREADER(MICR) MICR Input Device Is Generally Used In Banks Because Of A Large Number Of CHEQUES To Be Processed Every Day. The Bank's Code Number And CHEQUE Number Are Printed On The CHEQUES With A Special Type Of Ink That Contains Particles Of Magnetic Material That Are Machine Readable. This Reading Process Is Called Magnetic Ink Character Recognition (MICR). The Main Advantages Of MICR Is That It Is Fast And Less Error Prone. For better understanding of MCR watch this video https://www.youtube.com/watch?v=LX-FyRcdUmM 2.2.9. A.MICR character recognizer 2.2.9.B.MICR reading code. 2.2.9. C. Epson MICR for multitasking
- 35. COMPUTERFUNDAMENTALS 2.3. OPTICAL CHARACTER READER (OCR) Optical Character Recognition Refers To The Branch Of Computer Science That Involves Reading Text From Paper And Translating The Images Into A Form That The Computer Can Manipulate (For Example, Into ASCII Codes). An OCR System enables you to take a Book or a Magazine Article, Feed It Directly Into An Electronic Computer File, And Then Edit the File Using a Word Processor. All OCR Systems Include An Optical Scanner For Reading Text, And Sophisticated Software For Analyzing Images. Most OCR Systems Use A Combination Of Hardware (Specialized Circuit Boards) And Software To Recognize Characters, Although Some Inexpensive Systems Do It Entirely Through Software. Advanced OCR Systems Can Read Text In Large Variety Of Fonts, But They Still Have Difficulty With Handwritten Text. The Potential Of OCR Systems Is Enormous Because They Enable Users To Harness The Power Of Computers to access Printed Documents. OCR Is Already Being Used Widely In The Legal Profession, Where Searches That Once Required Hours Or Days Can Now Be Accomplished In A Few Seconds. 2.3. A.OCR 2.3.B.Nuscan501ocr 2.3. C. IRIPSEN Optical Character Recognizer
- 36. COMPUTERFUNDAMENTALS 2.4 BAR CODE READER Bar Code Reader Is A Device Used For Reading Bar Coded Data (Data In Form Of Light And Dark Lines). Bar Coded Data Is Generally Used In Labeling Goods, Numbering The Books Etc. It May Be A Hand Held Scanner Or May Be Embedded In A Stationary Scanner. Bar Code Reader Scans A Bar Code Image, Converts It Into An Alphanumeric Value Which Is Then Fed To The Computer To Which Bar Code Reader Is Connected. 2.4. A.Barcode Reader 2.4.B.Datalogic Barcode Reader 2.4. C. Operation of Barcode Reader
- 37. COMPUTERFUNDAMENTALS 2.5 WEBCAME A WEBCAM Is A Video Camera That Feeds Or Streams It’s Image In Real Time To Or Through A Computer To Computer Network. When "Captured" By The Computer, The Video Stream May Be Saved, Viewed Or Sent On To Other Networks Via Systems Such As The Internet, And Email As An Attachment. When Sent To A Remote Location, The Video Stream May Be Saved, Viewed Or On Sent There. Unlike An IP Camera (Which Connects Using Ethernet Or Wi-Fi), A Webcam Is Generally Connected By A USB Cable, Or Similar Cable, Or Built Into Computer Hardware, Such As Laptops. 2.5. A Webcam 2.5.B.Circle Type Webcam 2.5. C. Apple Latest Webcam
- 38. COMPUTERFUNDAMENTALS 2.6 BIOMETRICS [THUMB IMPRESSION / FACE DETECTION] One Of The Widely Used Access Control Biometric Machines In Any Technology Oriented Organization Is Thumb Impression Attendance System. Nowadays, To Avoid Proxy Attendance Or Duplicate Voting Most Employers Use Thumb Impression Attendance System, Which Collects The Thumb Impression Through A Finger Print Scanning Device. A Thumb Impression Attendance System Device Contains Hardware That Scans The Thumb Impression Of A Person And A Software Application That Verifies The Scanned Impression Against The Previously Collected Impression That Is Stored In The Built-In Biometric Database During The Time Of Enrollment. Thumb Impression Attendance System Is Hassle-Free and A Very Convenient Device For Any Security Oriented Business Face Recognition Biometric Attendance Machines Can Help You In Cost Saving Because These Machines Are Available In Very Low Prices. These Devices Help In Bringing Punctuality In The Organization Because They Keep Records Of Employees In And Out Timings. These Machines Come With Different Features Like Card Reader, Face Recognition System, and Thumb Impression Facility . There Is Software For These Machines Which Is Capable Of Generating 150+ Industry Standard Reports. These Machines Comes With A Free Software For Payroll Management Of Your Employees. 2.6. A. Biometric Time Attendance System 2.6.B. Thumb Impression System 2.6.8. C. Face Reorganization System
- 39. COMPUTERFUNDAMENTALS 2.7. OUTPUT DEVICES Following Are Few Of The Important Output Devices Which Are Used In A Computer. Monitors Graphic Plotter Printer 2.7.1.MONITORS Monitors, Commonly Called As Visual Display Unit (VDU), Are The Main Output Device Of A Computer. It Forms Images From Tiny Dots, Called Pixels That Are Arranged In A Rectangular Form. The Sharpness Of The Image Depends Upon The Number Of Pixels. There Are Two Kinds Of Viewing Screen Used For Monitors. Cathode-Ray Tube (CRT) Flat- Panel Display 2.7.2. CATHODE-RAY TUBE (CRT) MONITOR The CRT Display Is Made Up Of Small Picture Elements Called Pixels. The Smaller the Pixels, The Better the Image Clarity, Or Resolution. It Takes More Than One Illuminated Pixel To Form Whole Character, Such As The Letter ‘E’ In The Word Help. A Finite Number Of Characters Can Be Displayed On A Screen At Once. The Screen Can Be Divided Into A Series Of Character Boxes - Fixed Location On The Screen Where A Standard Character Can Be Placed. Most Screens Are Capable Of Displaying 80 Characters Of Data Horizontally And 25 Lines Vertically. There Are Some Disadvantages Of CRT: Large In Size High Power Consumption
- 40. COMPUTERFUNDAMENTALS 2.7.2. A.CRT Deflection System. 2.7.2. B. Samsung CRT Monitor. 2.7.3. FLAT-PANEL DISPLAY MONITOR The Flat-Panel Display Refers To A Class Of Video Devices That Have Reduced Volume, Weight And Power Requirement In Comparison To The CRT. You Can Hang Them On Walls Or Wear Them On Your Wrists. Current Uses Of Flat-Panel Displays Include Calculators, Video Games, Monitors, Laptop Computer, and Graphics Display. The Flat-Panel Display Is Divided Into Two Categories: Emissive Displays - The Emissive Displays Are Devices That Convert Electrical Energy Into Light. Example Are Plasma Panel And LED (Light-Emitting Diodes). Non-Emissive Displays - The Non-Emissive Displays Use Optical Effects To Convert Sunlight Or Light From Some Other Source Into Graphics Patterns. Example Is LCD(Liquid-Crystal Device)
- 41. COMPUTERFUNDAMENTALS 2.7.3. B. NEC 43-Inch Curved LCD 2.7.3. A. AOC LED 2.8.PRINTERS Printer Is An Output Device, Which Is Used To Print Information On Paper. There Are Two Types Of Printers: 1. Impact Printers 2. Non-Impact Printers 2.8.1.IMPACTPRINTERS The Impact Printers Print The Characters By Striking Them On The Ribbon Which Is Then Pressed On The Paper. Characteristics Of Impact Printers Are The Following: Very Low Consumable Costs Very Noisy Useful For Bulk Printing Due To Low Cost There Is Physical Contact With The Paper To Produce An Image 2.8.1. A.Impact Printer 2.8.1.B.Impact Printer (2)
- 42. COMPUTERFUNDAMENTALS IMPACT PRINTERS Are Of Two Types 1. Character Printers 2. Line Printers 2.8.2. CHARACTER PRINTERS Character Printers Are The Printers Which Print One Character At A Time. These Are Further Divided Into Two Types: 1. Dot Matrix Printer(DMP) 2. Daisy Wheel 2.8.3. DOT MATRIX PRINTER In The Market One Of The Most Popular Printers Is Dot Matrix Printer. These Printers Are Popular Because Of Their Ease Of Printing And Economical Price. Each Character Printed Is In Form Of Pattern Of Dots And Head Consists Of A Matrix Of Pins Of Size (5*7, 7*9, 9*7 Or 9*9) Which Come Out To Form A Character That Is Why It Is Called Dot Matrix Printer. 2.8.3. A. Dot-matrix Printer Advantages Inexpensive Widely Used Other Language Characters Can Be Printed Disadvantages Slow Speed Poor Quality
- 43. COMPUTERFUNDAMENTALS 2.8.4. DAISY WHEEL Head Is Lying On A Wheel And Pins Corresponding To Characters Are Like Petals Of Daisy (Flower Name) That Is Why It Is Called Daisy Wheel Printer. These Printers Are Generally Used For Word-Processing In Offices Which Require A Few Letters To Be Sent Here And There With Very Nice Quality. Advantages More Reliable Than DMP Better Quality The Fonts Of Character Can Be Easily Changed Disadvantages Slower Than DMP Noisy More Expensive Than DMP 2.8.4. A. Daisy Wheel 2.8.4.B Daisy Wheel Keyboard 2.8.5LINE PRINTERS Line Printers Are The Printers Which Print One Line At A Time. These Are Of Further Two Types 1. Drum Printer 2. Chain Printer
- 44. COMPUTERFUNDAMENTALS 2.8.6DRUM PRINTER This Printer Is Like A Drum In Shape So It Is Called Drum Printer. The Surface Of Drum Is Divided Into Number Of Tracks. Total Tracks Are Equal To Size Of Paper I.E. For A Paper Width Of 132 Characters, Drum Will Have 132 Tracks. A Character Set Is Embossed On Track. The Different Character Sets Available In The Market Are 48 Character Set, 64 And 96 Characters Set. One Rotation Of Drum Prints One Line. Drum Printers Are Fast In Speed And Can Print 300 To 2000 Lines Per Minute. 2.8.6. A. Drum Type Printer 2.8.6. B .Drum Or Toner Cartridge Advantages Very High Speed Disadvantages Very Expensive Characters Fonts Cannot Be Changed 2.8.7CHAIN PRINTER In This Printer, Chain Of Character Sets Are Used So It Is Called Chain Printer. A Standard Character Set May Have 48, 64, Or 96 Characters.
- 45. COMPUTERFUNDAMENTALS 2.8.7.A.Chain Type Printer Advantages Character Fonts Can Easily Be Changed. Different Languages Can Be Used With The Same Printer. Disadvantages Noisy 2.8.9.NON-IMPACTPRINTERS Non-Impact Printers Print The Characters Without Using Ribbon. These Printers Print A Complete Page At A Time So They Are Also Called As Page Printers. These Printers Are Of Two Types 1. Laser Printers 2. Inkjet Printers 2.9.CHARACTERISTICSOFNON-IMPACTPRINTERS 1. Faster than impact printers. 2. They are not noisy. 3. High quality. 4. Support many fonts and different character size.
- 46. COMPUTERFUNDAMENTALS 2.9.1LASER PRINTERS These are non-impact page printers. They use laser lights to produce the dots needed to form the characters to be printed on a page. 3.9.1. A. HP Laser Printer Advantages 1. Very high speed 2. Very high quality output 3. Give good graphics quality 4. Support many fonts and different character size Disadvantages 1. Expensive. 2. Cannot be used to produce multiple copies of a document in a single printing. 2.9.2. INKJET PRINTERS Inkjet Printers Are Non-Impact Character Printers Based On A Relatively New Technology. They Print Characters By Spraying Small Drops Of Ink Onto Paper. Inkjet Printers Produce High Quality Output With Presentable Features.
- 47. COMPUTERFUNDAMENTALS They Make Less Noise Because No Hammering Is Done And These Have Many Styles Of Printing Modes Available. Color Printing Is Also Possible. Some Models Of Inkjet Printers Can Produce Multiple Copies Of Printing Also. 2.9.2. A. Inject Printer 2.9.2. B. A Canon Inkjet with CMYK Cartridges Advantages 1. High Quality Printing. 2. More Reliable. Disadvantages 1. Expensive As Cost Per Page Is High. 2. Slow As Compared To Laser Printer.
- 48. COMPUTERFUNDAMENTALS QUESTIONS ON COMPUTER I/O DEVICES 1. Which Is An Important Data Transfer Technique: A. CPU B. DMA C. CAD D. None of These ANS: B 2. Which Device Can Be Thought Of As Transducers Which Can Sense Physical Effects And Convert Them Into Machine-Tractable Data: A. Storage Devices B. Peripheral Devices C. Both D. None ANS: B 3. Which Devices Are Usually Designed On The Complex Electromechanical Principle? A. Storage Devices B. Peripheral Devices C. Input Devices D. All of These ANS: C 4. Which disk is one of the important I/O devices and its most commonly used as permanent storage devices in any processor: A. Hard Disk B. Optical Disk C. Magneto Disk D. Magneto Optical Disk ANS: A
- 49. COMPUTERFUNDAMENTALS 5. In storage devices PC have hard disk having capacities in the range of _____: A. 12GB to 15GB B. 15GB to 20GB C. 20GB to 80GB D. 80GB to 85GB ANS: C 6. Which disk is a 3.5-inch diskette with a capacity of 1.44MB? A. Soft Disk B. Floppy Disk C. Both D. None ANS: C 7. Which has a large storage capacity of 2 to8GB? A. Magnetic Tape B. Magnetic Disk C. Soft Disk D. Floppy Disk ANS: A 8. Which disk read the data by reflecting pulses of laser beams on the surface? a. Magnetic disk b. Soft disk c. Floppy disk d. Optical disk ANS: D 9. Data access time of optical disk varies from 200 to 350minutes with transfer rate of ________: A. 130kb/S to 400kb/S B. 130kb/S to 500kb/S C. 150kb/S to 600kb/S D. 150kb/S to 800kb/S ANS: D
- 50. COMPUTERFUNDAMENTALS 10. NAND type flash memory data storage devices integrated with a _______ interface: A. ATM B. LAN C. USB D. DBMS ANS: C 11. Which disk is based on the same principle as the optical disk: A. Optical Disk B. Magnetic Disk C. Magneto-Optical Disk D. All Of These ANS: C 12. WAN stands for: A. Wide Area Network B. Word Area Network C. World Area Network D. Window Area Network ANS: A 13. The human-interactive I/O devices can be further categorized as____: a. Direct b. Indirect c. Both d. None ANS: C 14. I/O devices are categorized in 2 parts are: A. Character Devices B. Block Devices C. Numeral Devices D. Both A & B ANS: D
- 51. COMPUTERFUNDAMENTALS 15. UART stands for: A. Universal Asynchronization Receiver/Transmitter B. Universal Asynchronous Receiver/Transmitter C. United Asynchronous Receiver/Transmitter D. Universal Automatic Receiver/Transmitter ANS: B 16. Which are following pointing devices A. Light Pen B. Joystick C. Mouse D. All of These ANS: D 17. Full form of LED: A. Light Emitting Diode B. Light Encounter Destination C. Live Emitting Diode D. None Of These ANS: A 18. In_______ mouse we use pair of LED: A. Optical B. Digital C. Analog D. All of These ANS: A 19. ______is device that is designed for gaming purposes and based on principle of electricity: a. Joy b. Stick c. Joystick d. None of these ANS: C
- 52. COMPUTERFUNDAMENTALS 20. Joystick uses shaft potentiometers for: A. X-Y Direction B. Only X Direction C. Only Y Direction D. All of These ANS: A 21. Full form of ADC: a. Analog to digital converter b. Digital to analog converter c. Accumulator digital converter d. All of these ANS: A 22. A system that enables computer to recognize human voice called: A. Voice System B. Voice Input System C. Input System D. None of These ANS: B 23. 2 commonly used voice input systems are: A. Micro B. Microphone C. Voice Recognition Software D. Both B & C ANS: D 24. Optical Scanner Devices Are: A. MICR B. OMR C. OCR D. All Of These ANS: D
- 53. COMPUTERFUNDAMENTALS 25. MICR Stands For: A. Magnetic Ink Character Recognition B. Magnetic Initiate Character Recognition C. Both A & B D. None Of These ANS: A 26. _______Technique Is Used In Evaluating Objective Answer Sheets: A. Optical Mark Reader B. Optical Marker Reader C. Optical Marker Reading D. All Of These ANS: A 27. _______Technique Help In Banking Sector: A. OCR B. OMR C. MICR D. None of These ANS: C
- 54. COMPUTERFUNDAMENTALS 3. FUNDAMENTALS OF COMPUTER ARCHITECTURE CPU Consists Of The Following Features: CPU Is Considered As The Brain Of The Computer. CPU Performs All Types Of Data Processing Operations. It Stores Data, Intermediate Results and Instructions (Program). It Controls The Operation Of All Parts Of Computer. 3.1. CPU BLOCK DIAGRAM 3.1. A. CPU Block Diagram 3.1.B.Appple CPU
- 55. COMPUTERFUNDAMENTALS 3.2.CPU PHASES Memory Unit Control Unit ALU Unit 3.3. MEMORY UNIT This Unit Can Store Instructions, Data and Intermediate Results. This Unit Supplies Information to the Other Units of the Computer When Needed. It Is Also Known As Internal Storage Unit Or Main Memory Or Primary Storage Or Random Access Memory (RAM). Its Size Affects Speed, Power and Capability. Primary Memory And Secondary Memory Are Two Types Of Memories In The Computer. Functions Of Memory Unit Are: It Stores All The Data And The Instructions Required For Processing. It Stores Intermediate Results Of Processing. It Stores Final Results Of Processing Before These Results Are Released To An Output Device. All Inputs And Outputs Are Transmitted Through Main Memory 3.3. A Semiconductor Ram. 3.3. B.Hard Disk
- 56. COMPUTERFUNDAMENTALS 3.4. MEMORY CLASSIFICATION 3.4. A. Memory Classification Diagram
- 57. COMPUTERFUNDAMENTALS 3.4.1. RANDOM ACCESS MEMORY [RAM] Ram Is A Memory Scheme Within The Computer System Responsible For Storing Data On A Temporary Basis, So That It Can Be Promptly Accessed By The Processor As And When Needed. It Is Volatile In Nature, Which Means That Data Will Be Erased Once Supply To The Storage Device Is Turned Off. Ram Stores Data Randomly and the Processor Accesses These Data Randomly From the Ram Storage. The Information Stored In The Ram Is Typically Loaded From The Computer's Hard Disk, And Includes Data Related To The Operating System And Certain Applications. When The System Is Switched Off, The Ram Loses All Stored Information . The Data Remains Stored On Secondary Storage Though, And Can Be Retained When The System Is Running Again. Some Of The Earliest Computers Used Delay-Line Format Of Computer Storage. Most Modern Computers Use An Embedded Ram Circuitry On The Motherboard Which Reads Data In Bursts. So, Modern Ram Devices Are Not Random Memory Devices As Such; They Are Burst Memory Access Devices, But the Term Ram Has Stuck In Everyday Usage. There Are Primarily Two Forms Of Ram: STATIC RAM (SRAM) And DYNAMIC RAM (DRAM). 3.4.1. A.RAM1 3.4.1.B.RAM2
- 58. COMPUTERFUNDAMENTALS 3.4.2. SRAM [STATIC RANDOM ASSESSABLE MEMORY] Where The Word Static Indicates That It, Does Not Need To Be Periodically Refreshed, As SRAM Uses Bi stable Latching Circuitry (I.E., Flip-Flops) To Store Each Bit. Each Bit Is Stored As A Voltage Each Memory Cell Requires Six Transistors, Thus Giving Chip Low Density But High Speed. However, SRAM is still volatile in the (Conventional) Sense That Data Is Lost When Power down. Disadvantages Are More Expensive And Also Consumes More Power Than Dram. In High Speed Processors (Such As Pentium), SRAM Is Known as Cache Memory and Is Included On The Processor Chip. However High-Speed Cache Memory Is Also Included External To The Processor To Improve Total Performance. 3.4.2. A.SRAM Chip 3.4.2.B.SRAM Port
- 59. COMPUTERFUNDAMENTALS 3.4.3 .DRAM [DYNAMIC RANDOM ASSESSABLE MEMORY] Its Advantage Over SRAM Is Its Structural Simplicity: Only One Transistor (MOSFET Gates) And A Capacitor (To Store A Bit As A Charge) Are Required Per Bit, Compared To Six Transistors In SRAM. This Allows DRAM To Reach Very High Density. Also It Consumes Less Power And Is Even Cheaper Than SRAM (Except When The System Size Is Less Than 8 K). But The Disadvantage Is That Since It Stores Bit Information As Charge Which Leaks; Therefore Information Needs To Be Read And Written Again Every Few Milliseconds. This Is Known As Refreshing The Memory And It Requires Extra Circuitry, Adding To The Cost Of System. 3.4.3. A.DRAM Views
- 60. COMPUTERFUNDAMENTALS 3.4.4. READ-ONLY MEMORY [ROM] Read Only Memory (ROM) Is An Example Of Nonvolatile Memory. ROM Is A Class Of Storage Medium Used In Computers And Other Electronic Devices. Read Only Memory (ROM), Also Known As Firmware, Is An Integrated Circuit Programmed With Specific Data When It Is Manufactured. The Instructions For Starting The Computer Are Housed On Read Only Memory Chip. ROM Chips Are Used Not Only In Computers, But In Most Other Electronic Items As Well Because Data Is Fully Incorporated At The ROM Chip's Manufacture, Data Stored Can Neither Be Erased Nor Replaced. This Means Permanent And Secure Data Storage However, If A Mistake Is Made In Manufacture, A ROM Chip Becomes Unusable. The Most Expensive Stage Of ROM Manufacture, Therefore, Is Creating The Template. If A Template Is Readily Available, Duplicating The ROM Chip Is Very Easy And Affordable. A ROM Chip Is Also Non Volatile So Data Stored In It Is Not Lost When Power Is Turned Off. ROM Is A Semiconductor Memory That Is Capable Of Operating At Electronics Speed.
- 61. COMPUTERFUNDAMENTALS 3.5. ROM CLASSIFICATION 3.5. A. ROM Classification Diagram 3.5. 1.PROM [PROGRAMMABLE READ ONLY MEMORY] PROM Stands For Programmable Read-Only Memory, A Memory Chip On Which Data Can Be Written Only Once. Once A Program Has Been Written Onto A PROM, It Remains There Forever. Unlike RAM, Proms Retain Their Contents When The Computer Is Turned Off. The Difference Between A PROM And A ROM (Read-Only Memory) Is That A PROM Is Manufactured As Blank Memory, Whereas A ROM Is Programmed During The Manufacturing Process. To Write Data Onto A PROM Chip, You Need A Special Device Called A PROM Programmer Or PROM Burner. The Process Of Programming A PROM Is Sometimes Called Burning The PROM. 3.5.1.A.Prom Programmer 3.5.1.B. Romchip
- 62. COMPUTERFUNDAMENTALS 3.5.2. EPROM [ERASABLE AND PROGRAMMABLE READ ONLY MEMORY] Acronym For Erasable Programmable Read-Only Memory, And Pronounced Ee- Prom, EPROM Is A Special Type Of Memory That Retains Its Contents Until It Is Exposed To Ultraviolet Light. The Ultraviolet Light Clears Its Contents, Making It Possible To Reprogram The Memory. To Write To And Erase An EPROM, You Need A Special Device Called A PROM Programmer Or PROM Burner. 3.5.2.A.Kinstonprndrive 3.5.2.B.EEPROM Chip 3.5.3. EEPROM Short Form of Electrically Erasable Programmable Read-Only Memory is EEPROM EEPROM Is A Special Type Of PROM That Can Be Erased By Exposing It To An Electrical Charge. Like Other Types Of PROM, EEPROM Retains Its Contents Even When The Power Is Turned Off. Also Like Other Types Of ROM, EEPROM Is Not As Fast As RAM. 3.5.3. A. EEPROM Chip 3.5.3.B.EEPROM as NBTV Signal Generator
- 63. COMPUTERFUNDAMENTALS 3.6 CACHE MEMORY Cache Memory, Also Called CPU Memory, Is Random Access Memory (RAM) That A Computer Microprocessor Can Access More Quickly Than It Can Access Regular RAM. This memory is Typically Integrated Directly With The CPU Chip Or Placed On A Separate Chip that Has A Separate Bus Interconnect With The CPU. Cache Memory Operations The Basic Purpose of Cache Memory Is to Store program Instructions That Are Frequently Re-Referenced By Software During Operation. Fast access To These Instructions Increases the Overall Speed of the Software Program. As The Microprocessor Processes Data, It Looks First In The Cache Memory; If It Finds The Instructions There (From A Previous Reading Of Data), It Does Not Have To Do A More Time-Consuming Reading Of Data From Larger Memory Or Other Data Storage Devices. Most Programs Use Very Few Resources Once They Have Been Opened And Operated For A Time, Mainly Because Frequently Re-Referenced Instructions Tend To Be Cached. This Explains Why Measurements Of System Performance In Computers With Slower processors But Larger Caches Tend To Be Faster Than Measurements Of System Performance In Computers With Faster Processors But More Limited Cache Space. Multi-Tier Or Multilevel Caching Has Become Popular In Server And Desktop Architectures, With Different Levels Providing Greater Efficiency Through Managed tiring.
- 64. COMPUTERFUNDAMENTALS Simply Put, The Less Frequently Access Is Made To Certain Data Or Instructions, The Lower Down The Cache Level The Data Or Instructions Are Written. 3.6. A. Cache Memory 3.6. B. Cache Memory Organization
- 65. COMPUTERFUNDAMENTALS 3.7. CONTROL UNIT This Unit Controls The Operations Of All Parts Of Computer But Does Not Carry Out Any Actual Data Processing Operations. Functions Of This Unit Are: It Is Responsible For Controlling The Transfer Of Data And Instructions Among Other Units Of A Computer. It Manages and Coordinates All the Units Of The Computer. It Obtains The Instructions From The Memory, Interprets Them, And Directs The Operation Of The Computer. It Communicates With Input/output Devices for Transfer of Data or Results from Storage. It Does Not Process or Store Data. 3.7. A. Control unit functioning
- 66. COMPUTERFUNDAMENTALS 3.8. ARITHMETIC LOGIC UNIT [ALU] ALU Stands For "Arithmetic Logic Unit." An ALU Is An Integrated Circuit Within A CPU Or GPU That Performs Arithmetic And Logic Operations. Arithmetic Instructions Include Addition, Subtraction, And Shifting Operations, While Logic Instructions Include Boolean comparisons, Such As AND, OR, XOR, And NOT Operations. ALUS Are Designed to Perform Integer calculations. Therefore, Besides Adding And Subtracting Numbers, ALUS Often Handle The Multiplication Of Two Integers, Since The Result Is Also An Integer. However, ALUS Typically Do Not Perform Division Operations, Since The Result May Be A Fraction, Or A "Floating Point" Number. Instead, Division Operations Are Usually Handled By The Floating-Point Unit (FPU), Which Also Performs Other Non-Integer Calculations. While The ALU Is A Fundamental Component Of All Processors. The Design And Function Of An ALU May Vary Between Different Processor Models. For Example, Some ALUS Only Perform Integer Calculations, While Others Are Designed To Handle Floating Point Operations As Well. Some Processors Contain A Single ALU, While Others Include Several Arithmetic Logic Units That Work Together To Perform Calculations.
- 67. COMPUTERFUNDAMENTALS 3.8 A.ALU operation figure 3.8. B.ALU basic operation figure
- 68. COMPUTERFUNDAMENTALS 3.9. BUSES IN CPU 3.9. A .bus computing fig Address Bus Is Used To Specify A Physical Memory Address. This Can Include Primary Memory (E.G. RAM And ROM) Secondary Memory (E.G. Hard Disk Drives) And Any Other Connected Devices. Monitors, Printers, Scanners, And Keyboards Will All Be Mapped To Memory. The Width Of The Address Bus Determines The Amount Of Memory That Can Be Addressed. A 32-Bit Bus Can Address 4,294,967,296 (2 ^ 32) Bytes Of Memory. This Explains The 4 GB Memory Restriction On 32-Bit Operating Systems. Data Bus Connects The Microprocessor (CPU) With Other Devices Mapped Onto The System. This Is Often Described Pictorially Using A Memory Map. Unlike The Address Bus, The Data Bus Is Two-Way (It Supports Read And Write Operations). The Data Bus Is Not Limited To Transferring Data; It Is Also Used To Transfer Program Instructions. Control Bus Carries Commands From And Returns Status Signals To The Microprocessor. The Control Unit Inside A CPU Manages The Internal Control Bus — Internal To The CPU — And The External Control Bus.
- 69. COMPUTERFUNDAMENTALS 3.9.1.INSTRUCTION CYCLE An Instruction Cycle (Sometimes Called Fetch-And-Execute Cycle, Fetch-Decode-Execute Cycle, Or FDX) Is The Basic Operation Cycle Of A Computer. It Is The Process By Which A Computer Retrieves A Program Instruction From Its Memory, Determines What Actions The Instruction Requires, And Carries Out Those Actions. This Cycle Is Repeated Continuously By The Central Processing Unit (CPU), From Boot up to When the Computer Is Shut Down. In Simpler CPUS, The Instruction Cycle Is Executed Sequentially: Each Instruction Is Completely Processed Before The Next One Is Started. In Most Modern CPUS, The Instruction Cycle Is Instead Executed Concurrently In Parallel, As An Instruction Pipeline: The Next Instruction Starts Being Processed Before The Previous Instruction Is Finished, Which Is Possible Because The Cycle Is Broken Up Into Separate Steps. o Program Counter (PC) - An Incrementing Counter That Keeps Track Of The Memory Address Of The Instruction That Is To Be Executed Next Or In Other Words, Holds The Address Of The Instruction To Be Executed Next. o Memory Address Register (MAR) - Holds The Address Of A Memory Block To Be Read From Or Written To. o Memory Data Register (MDR) - A Two-Way Register That Holds Data Fetched From Memory (And Ready for the CPU to Process) or Data Waiting To Be Stored In Memory. (This Is Also Known As the Memory Buffer Register (MBR). o Instruction Register (IR) - A Temporary Holding Ground for the Instruction That Has Just Been Fetched From Memory. o Control Unit (CU) - Decodes The Program Instruction In The Ir, Selecting Machine Resources Such As A Data Source Register And A Particular Arithmetic Operation, And Coordinates Activation Of Those Resources.
- 70. COMPUTERFUNDAMENTALS o Arithmetic Logic Unit (ALU) - Performs Mathematical And Logical Operations. Each Computer's CPU Can Have Different Cycles Based On Different Instruction Sets, But Will Be Similar To The Following Cycle: 1. Fetching The Instruction: The Next Instruction Is Fetched From The Memory Address That Is Currently Stored In The Program Counter (Pc), And Stored In The Instruction Register (IR). At The End Of The Fetch Operation, The Pc Points To The Next Instruction That Will Be Read At The Next Cycle. 2. Decode the Instruction: During This Cycle the Encoded Instruction Present In The IR (Instruction Register) Is Interpreted By The Decoder. 3. Read The Effective Address: In Case Of A Memory Instruction (Direct Or Indirect) The Execution Phase Will Be In The Next Clock Pulse. If The Instruction Has An Indirect Address, The Effective Address Is Read From Main Memory, And Any Required Data Is Fetched From Main Memory To Be Processed And Then Placed Into Data Registers (Clock Pulse: T3). If The Instruction Is Direct, Nothing Is Done At This Clock Pulse. If This Is An I/O Instruction Or A Register Instruction, The Operation Is Performed (Executed) At Clock Pulse. 4. Execute The Instruction: The Control Unit Of The CPU Passes The Decoded Information As A Sequence Of Control Signals To The Relevant Function Units Of The CPU To Perform The Actions Required By The Instruction Such As Reading Values From Registers, Passing Them To The ALU To Perform Mathematical Or Logic Functions On Them, And Writing The Result Back To A Register. If The ALU Is Involved, It Sends A Condition Signal Back To The Cu. The Result Generated By The Operation Is Stored In The Main Memory, Or Sent To An Output Device. Based On The Condition Of Any Feedback From The ALU, Program Counter May Be Updated To A Different Address From Which The Next Instruction Will Be Fetched. The Cycle Is Then Repeated. 3.9.1.A.Instruction Cycle
- 71. COMPUTERFUNDAMENTALS 3.9.1.B.Fectch Cycle 3.6.1.C.Exicution Cycle 3.6.2.D.Insruction Cycle
- 72. COMPUTERFUNDAMENTALS 3.9.2. Measure Of CPU Performance. Computer Performance Is Characterized By The Amount Of Useful Work Accomplished By A Computer System Or Computer Network Compared To The Time And Resources Used. Depending On The Context, High Computer Performance May Involve One Or More Of The Following: 1) Short Response Time For A Given Piece Of Work 2) High Throughput (Rate Of Processing Work) 3) Low Utilization Of Computing Resource(S) 4) High Availability Of The Computing System Or Application 5) Fast (Or Highly Compact) Data Compression And Decompression 6) High Bandwidth 7) Short Data Transmission Time 3.9.2.A.Measure Of Computer Performance
- 73. COMPUTERFUNDAMENTALS Questions On Computer Fundamentals Of Computer Architecture Q1] The Brain Of Any Computer System Is? A.ALU Memory C.CPU D. Control Unit None Of These ANS: A Q2] A Computer Assisted Method For The Recording And Analyzing Of Existing Or Hypothetical Systems Is? A. Data transmission B. Dataflow C. Data Processing D. Data Capture ANS.:B Q3] what are the main parts in central processing unit? A. ALU, Controlunit,Memoryunit B. Axulary devices C. Control unit ,Hard Disk D. Memory ANS: A Q4] The Section Of The CPU That Selects, Interprets And Sees To The Execution Of Program Instructions? A. Memory Unit B. Control Unit C. ALU D. None Of The Above ANS: B
- 74. COMPUTERFUNDAMENTALS Q5]. CPU Fetches The Instruction From Memory According To The Value Of…….. A) Program Counter B) Status Register C) Instruction Register D) Program Status Word ANS: C Q6] A Memory Buffer Used To Accommodate A Speed Differential Is Called……… A) Stack Pointer B) Cache C) Accumulator D) Disk Buffer ANS: B Q7]. Which One Of The Following Is The Address Generated By CPU? A) Physical Address B) Absolute Address C) Logical Address D) None Of The Mentioned ANS: C Q8] Run Time Mapping From Virtual To Physical Address Is Done By…….. A) Memory Management Unit B) CPU C) PCI D) None of the Mentioned ANS: A
- 75. COMPUTERFUNDAMENTALS Q9] Which Of The Following Computer Implemented Binary Numbers, Perform Calculations Using Electronics And Implemented Separate Computation And Memory For The First Time? A) Mark I B) ABC C) Z3 D) None Of Above ANS: B Q10] FORTRAN Is A Programming Language. What Does FORTRAN Stand For? A) File Translation B) Format Translation C) Formula Translation D) Floppy Translation ANS: C Q11] Which Of The Following Memories Needs Refreshing? A) SRAM B) DRAM C) ROM D) All Of Above ANS: B Q12] Can You Tell What Passes Into And Out From The Computer Via Its Ports? A) Data B) Bytes C) Graphics D) Pictures ANS: A
- 76. COMPUTERFUNDAMENTALS Q13] An Output Device That Uses Words Or Messages Recorded On A Magnetic Medium To Produce Audio Response Is A) Magnetic Tape B) Voice Response Unit C) Voice Recognition Unit D) Voice Band ANS: B Q14] Which of the Items Below Are Considered Removable Storage Media? A) Removable Hard Disk Cartridges B) (Magneto-Optical) Disk C) Flexible Disks Cartridges D) All of The Above ANS: D Q15] Which Of The Following Is Not Purely Output Device? A) Screen B) Printer C) Speaker D) Plotter ANS: A Q16] Who Developed A Mechanical Device In The 17th Century That Could Add, Subtract, Multiple, Divide And Find Square Roots? A) Napier B) Babbage C) Pascal D) Leibniz ANS: D
- 77. COMPUTERFUNDAMENTALS Q17] The First Macintosh Computer Was From A) First Generation B) Second Generation C) Third Generation D) Fourth Generation ANS: D Q18] Which of The Following Is Not A Form Of Data? A) Numbers and Characters B) Images C) Sound D) None Of Above ANS: D Q19] Which Is Not A Computer Classification? A) Mainframe B) Max frame C) Mini D) Notebook ANS: B Q20] The Control Unit Of A Microprocessor A) Stores Data In The Memory B) Accepts Input Data From Keyboard C) Performs Arithmetic/Logic Function D) None Of Above ANS: D
- 78. COMPUTERFUNDAMENTALS Q21] Which Of The Following Is Internal Memory? A) Disks B) Pen Drives C) RAM D) CDS ANS: C Q22] Which Operation Is Not Performed By Computer? A) Inputting B) Processing C) Controlling D) Understanding ANS: D Q23] Floppy Disks Which Are Made From Flexible Plastic Material Are Also Called? A) Hard Disks B) High-Density Disks C) Diskettes D) Templates ANS: C Q24]The Magnetic Storage Chip Used To Provide Non-Volatile Direct Access Storage Of Data And That Have No Moving Parts Are Known As A) Magnetic Core Memory B) Magnetic Tape Memory C) Magnetic Disk Memory D) Magnetic Bubble Memory ANS: B
- 79. COMPUTERFUNDAMENTALS Q25]A Collection Of Related Instructions Organized For A Common Purpose Is Referred To As A) File B) Database C) Program D) None Of Above ANS: C Q26]Plotter Accuracy Is Measured In Terms Of Repeatability And A) Buffer Size B) Resolution C) Vertical Dimensions D) Intelligence ANS: B Q27] Computer Instructions Written With The Use Of English Words Instead Of Binary Machine Code Is Called A) Mnemonics B) Symbolic Code C) Gray Codes D) OPCODE ANS: B Q28] Which Language Is Directly Understood By The Computer Without Translation Program? A) Machine Language B) Assembly Language C) High Level Language D) None Of Above ANS: A
- 80. COMPUTERFUNDAMENTALS Q29] On Which Aspect The Analog Computers Are Better Than Digital? A) Speed B) Accuracy C) Reliability D) Automatic ANS: B Q30] Which Of The Following Processors Use RISC Technology? A) 486dx B) Power PC C) 486sx D) 6340 ANS: B Q31] Which of The Following Machine Was Not Invented By Charles Babbage? A) Tabulating Machine B) Analytical Engine C) Difference Engine D) Both C And D ANS: A Q32]. How Many Numbers Could ENIAC Store In Its Internal Memory A) 100 B) 20 C) 80 D) 40 ANS: B
- 81. COMPUTERFUNDAMENTALS Q34] The Subject Of Cybernetics Deals With The Science Of A) Genetics B) Control And Communication C) Molecular Biology D) Biochemistry ANS: B Q33] Why ABC Is Considered Electro-Mechanical Computer? A) Because It Was Invented Before Electronic Computers Were Developed B) Because There Are Wheels, Drums, Bars To Rotate And Move To Produce Result C) Because They Use The Flow Of Electrons In Different Component D) None Of Above ANS: B Q24]Binary Circuit Elements Have A) One Stable State B) Two Stable State C) Three Stable State D) None Of Above ANS: B Q35]Which Of The Following Is Used For Manufacturing Chips? A) Control Bus B) Control Unit C) Parity Unit D) Semiconductor ANS: B
- 82. COMPUTERFUNDAMENTALS Q36] Which Of The Following Is Not A Micro Computer? A) Laptop Pcs B) Tablet Pcs C) Desktop Pcs D) None Of Above ANS: D Q37] The Value Of Each Bead In Earth Is A) 1 B) 3 C) 5 D) 7 ANS: D Q38] When Did John Napier Develop Logarithm? A) 1416 B) 1614 C) 1641 D) 1804 ANS: B Q39] Which Of The Following Terms Is The Most Closely Related To Main Memory? A) Non Volatile B) Permanent C) Control Unit D) Temporary ANS: D
- 83. COMPUTERFUNDAMENTALS Q40] Which Was the World’s First Minicomputer And When Was It Introduced? A) PDP-I, 1958 B) IBM System/36, 1960 C) PDP-II, 1961 D) VAX 11/780, 1962 ANS: A Q41]A Group Of Magnetic Tapes, Videos Or Terminals Usually Under The Control Of One Master Is A) Cylinder B) Surface C) Track D) Cluster ANS: D Q42]The Word Length Of A Computer Is Measured In A) Bytes B) Millimeters C) Meters D) Bits ANS: D Q43] What Type Of Memory Is Not Directly Addressable By The CPU And Requires Special Softw3are Called EMS (Expanded Memory Specification)? A) Extended B) Expanded C) Base D) Conventional ANS: D
- 84. COMPUTERFUNDAMENTALS Q44] Which Unit Holds Data Permanently? A) Input Unit B) Secondary Storage Unit C) Output Unit D) Primary Memory Unit ANS: B Q45] Before A Disk Can Be Used To Store Data. It Must Be_______ A) Formatted B) Reformatted C) Addressed D) None Of The Above ANS: B Q46]Computer System Comprises Of Major Units A) Input Unit, Output Unit, Control Unit B) Input Unit, Output Unit, Control Unit And Storage C) Input Unit, Output Unit, Central Processing Unit And Storage Unit D) Input, Output And Storage Units ANS: C Q47]The First General Purpose Electronic Digital Computer In The World Was A) UNIVAC B) EDVAC C) ENIAC D) All Of Above ANS; A
- 85. COMPUTERFUNDAMENTALS Q48]. Signals Can Be Analog Or Digital And A Computer That Processes The Both Type Of Signals Is Known As A) Analog Computer B) Digital Computer C) Hybrid Computer D) Mainframe Computer ANS: C Q49]. High Level Language Is Also Called A) Problem Oriented Language B) Business Oriented Language C) Mathematically Oriented Language D) All Of The Above ANS: D Q50]. Human Beings Are Referred To As Homo- sapiens, Which Device Is Called Silicon Sapiens? A) Monitor B) Hardware C) Robot D) Computer ANS: D
- 86. COMPUTERFUNDAMENTALS 4. MOTHERBOARD[INTERNALCOMPONENTS] The motherboard serves as a single platform to connect all of the parts of a computer together. A motherboard connects CPU, memory, hard drives, optical drives, video card, sound card, and other ports and expansion cards directly or via cables. It can be considered as the backbone of a computer. 4.A.Mother Board Top View
- 87. COMPUTERFUNDAMENTALS 4.1FEATURES OFMOTHERBOARD A Motherboard Comes With Following Features: Motherboard Varies Greatly In Supporting Various Types Of Components. Normally A Motherboard Supports A Single Type Of CPU And Few Types Of Memories. Video Cards, Hard Disks, Sound Cards Have To Be Compatible With Motherboard To Function Properly Motherboards, Cases And Power Supplies Must Be Compatible To Work Properly Together. 4.2POPULARMANUFACTURERS Intel ASUS An Open ABIT Bio star Gigabyte MSI
- 88. COMPUTERFUNDAMENTALS 4.3. The ImportantConstituentComponentsOfAn ATXMotherboard AreGivenBelow: 1. Mouse & keyboard 2. USB 3. Parallel port 4. CPU Chip 5. RAM slots 6. Floppy controller 7. IDE controller 8. PCI slot 9. ISA slot 10. CMOS Battery 11. AGP slot 12. CPU slot 13. Power supply plug in 1. MOUSE A Computer Mouse Enables Its User To Move A Cursor Smoothly And Intuitively Across A Two-Dimensional Plane. It's Therefore An Essential Input Device For Selecting, Dragging, Hovering, And Clicking. The Mouse Allows Users To Switch Between Applications, Select Options And Buttons, And Move Around The Screen With A Great Degree Of Accuracy And Fluidity. It Is Used To Move Between And Select Links On A Website, Buttons On An Options Screen, Entries On A Menu, And Many More Tasks That Would Be Far More Difficult Using A Keyboard Alone. 2. KEBOARD A Computer Keyboard Is An Input Device Used To Enter Characters And Functions Into The Computer System By Pressing Buttons, Or Keys. It Is The Primary Device Used To Enter Text. A Keyboard Typically Contains Keys For Individual Letters, Numbers And Special Characters, As Well As Keys For Specific Functions 4.3.A.Applekeyboard and Mouse
- 89. COMPUTERFUNDAMENTALS 2. USB I/O Ports- This Is Located In The Rear Panel Of The CPU, This Use To Connect The Outside Hardware Or Peripherals Of The Computer. • PS/2 Ports- These Are Used To Connect The Mouse (Green Color) And The Keyboard (Purple Color) • DB 25 Female Connector (Printer Port)-This Is Use To Connect The Impact Printer, One Of That The DOT MATRIX Printer, Ex. The Epson LX 300 + • DB 9 Male Connector (Serial Or Com1 Port)-This Use To Connect A Serial Device Of The Computer, Such As The Serial Mouse And External Modem. • VGA Port (Built-In)- This Is Use To Interface The DB Cord Of The Monitor Screen Or To Connect The Monitor Screen Of The Computer. The Fastest Video Card Versions Are Based On The Standard Of The VGA Slots, Ex: The AGP And PCI’e Card. • USB 2.0 × 2 Ports- These Are The Ports Of The USB Devices Of The Computer. Attached Externally Of The System Unit, One Of That Are The USB Flash Drives. As Of Now The Versions Or Speed Of The USB Are The 1.0 And 2.0 Compatible. • LAN Port- This Called As Local Area Network Of The Computer. This Is Use To Connect The Numbers Of Node Or Workstations (PC) To Form A Local Area Network Of The Computer With In Their Area. Using Type Of Communication Media Such As The Network Switch And Router. • Audio Port- This Is Use To Connect The Speaker, Mike, And MIDI (Musical Instrument Digital Interface) Device Of The Computer. 2. ATX Power Connector(4 Pin)- This Is Use To Connect The 4 Pin Of The Power Supply Unit(PSU) .This Is Separate Of The 20 Or 24 Pin Of ATX Power Supply To Provide DC Voltage Of Computer Processor. 4.3. B.I/O Ports
- 90. COMPUTERFUNDAMENTALS 3. PARALLEL PORT A Parallel Port Is A Type Of Interface Found On Computers (Personal And Otherwise) For Connecting Peripherals. In Computing, A Parallel Port Is A Parallel Communication Physical Interface. It Is Also Known As A Printer Port. It Was An Industry De Facto Standard For Many Years, And Was Finally Standardized As IEEE 1284 In The Late 1990s, Which Defined The Enhanced Parallel Port (EPP) And Extended Capability Port (ECP) Bi-Directional Versions. Today, The Parallel Port Interface Is Seeing Decreasing Use Because Of The Rise Of Universal Serial Bus (USB) Devices, Along With Network Printing Using 4.3.C.Parallel Port 4.3.D.Parlleport Cable
- 91. COMPUTERFUNDAMENTALS 4. CPU CHIP The Central Processing Unit, Or CPU, Is The Brain Of A Computer. Without This Vital Component, The Computer Wouldn’t Be Able Perform Any Of The Functions Related To Moving And Processing Data. Each New Processor Release From Manufacturers (Primarily AMD And Intel,) CPU Become Faster And More Powerful. Speed And Reliability Is The Name Of The Game When Consumers Compare CPU Chips In New Pcs. For Some, The Brand Of CPU Is A Major Selling Point When Buying A New Computer. For Others, Raw Speed Is More Important. 4.3. E.CPU Chip 4.3.F.Intel Processor
- 92. COMPUTERFUNDAMENTALS 5. RAM SLOTS Located in the Upper-Right Part of the Motherboard, The Memory Slots Are Used to House the Computer’s Memory Modules. The Number Of Slots Can Vary, Depending On Motherboard, From 2, In Low-End Motherboards, All The Way Up To 8 Memory Slots, On High-End And Gaming Motherboards. It Is Important To Pay Close Attention To The Type Of Memory A Motherboard Supports, In Order To Buy The Appropriate Memory Modules. Newer Motherboards Support DDR3 Memory, The Current Industry Standard Memory Architecture, But Motherboards With DDR2 Memory Slots And Even DDR1 Memory Slots Are Still Present On The Market. An Interesting Aspect Is That There Are Some Older Motherboard Models That Supported Different Types Of Memory, And Usually Come With Two DDR1 Memory Slots And 2 DDR2 Memory Slots, Or Two DDR2 Slots And Two DDR3 Slots. These Motherboards Were Great Options For People That Wanted To Upgrade A Motherboard Without Having To Upgrade All The Other Components As Well. 4.3. G. Memory Slots on Mother Board
- 93. COMPUTERFUNDAMENTALS 4.3. I. Memory Slots Arrangement 6. FLOPPY CONTROLLER Definition - What Does Floppy Disk Drive (FDD) Mean? A Floppy Disk Drive (FDD), Or Floppy Drive, Is A Hardware Device That Reads Data Storage Information. It Was Invented In 1967 By A Team At IBM And Was One Of The First Types Of Hardware Storage That Could Read/Write A Portable Device. FDDS Are Used For Reading And Writing On Removable Floppy Discs. Floppy Disks Are Now Outdated, And Have Been Replaced By Other Storage Devices Such As USB And Network File Transfer. 4.3.J. Sony Floppydisk Drive
- 94. COMPUTERFUNDAMENTALS Explanation of Floppy Disk Drive (FDD) A Floppy Disk Commonly Came In Three Sizes, 8 Inches, 5.5 Inches And 3.5 Inches, Becoming Smaller As The Technology Advanced. The Newer, 3.5-Inch Version Used More Cutting-Edge Technology And Held More Data Than Previous Models, While The Original 8-Inch Floppy Drive Was Developed To Load Hardware-Level Instructions And/or Data Structures Called Microcode Into The Ibm System/370 Mainframe. The 8-Inch Flexible Diskette Was Read-Only, Held 80 Kilobytes Of Memory And Was Referred To As A Memory Disk. Eight-Inch Floppy Drives Did Not Connect To The Motherboard, But Rotated On A Turntable That Was Run By An Idler Wheel. As Technology Advanced, Floppy Disks Were Finally Able To Read And Write. By This Point, FDDS Had Four Basic Components: 1. Magnetic Read/Write Heads (One Or Two) 2. A Spindle Clamping Device That Held The Disk In Place As It Was Spinning 300 To 360 Rotations Per Minute 3. A Frame With Levers That Opened And Closed The Device 4. A Circuit Board That Contained All Of The Electronics. 4.3. K.Different Types Of Floppy Disks 4.3.L. Dell Floppy Disk
- 95. COMPUTERFUNDAMENTALS 7. IDE CONTROLLER IDE (Integrated Drive Electronics) Is A Standard Electronic Interface Used Between A Computer Motherboard's Data Paths Or Bus And The Computer's Disk Storage Devices. The IDE Interface Is Based On The IBM PC Industry Standard Architecture (ISA) 16- Bit Bus Standard, But It Is Also Used In Computers That Use Other Bus Standards. IDE Was Adopted As A Standard By The American National Standards Institute (ANSI) In November 1990. The ANSI Name For IDE Is Advanced Technology Attachment (ATA), And The ATA Standard Is One Of Several Related Standards Maintained By The T10 Committee. In Today's Computers, The IDE Controller Is Often Built Into The Motherboard. Prior To The IDE Drive, Controllers Were Separate External Devices So IDE Reduced Problems Associated With Storage Devices And Integrated Controllers. 4.3. M. IDE Controller Chip. 4.3.N. Conneting Ide To Harddisk
- 96. COMPUTERFUNDAMENTALS 8. PCI SLOT [Peripheral Component Interconnect] Since The First Pc, Launched In 1981, The Computer Has Had Expansion Slots Where You Can Install Additional Cards To Add Capabilities Not Available On The Motherboard Of The Computer. Currently, The Most Common Type Of Expansion Slot Available Is Called Pci Express. In This Tutorial, You Will Learn Everything You Need To Know About This Kind Of Connection: How It Works, Versions, Slots, And More. Before Talking About The PCI Express, We Must Talk A Little Bit About The History Of Pc Expansion Slots And Their Main Challenges, So You Can Understand What Makes The PCI Express Different. Below We List The Most Common Types Of Expansion Slots That Were Launched For The Pc Throughout Its History: ISA (Industry Standard Architecture) MCA (Micro Channel Architecture) EISA (Extended Industry Standard Architecture) VLB (VESA Local Bus) PCI (Peripheral Component Interconnect) PCI-X (Peripheral Component Interconnect Extended) AGP (Accelerated Graphics Port) PCI Express (Peripheral Component Interconnect Express) 4.3.O.Pci ,Agp&Isa Slots On Mother Bord 4.3.P.Pci Slots
- 97. COMPUTERFUNDAMENTALS 9. ISA SLOTS Stands For "Industry Standard Architecture." Isa Is A Type Of Bus Used In Pcs For Adding Expansion Cards. For Example, An Isa Slot May Be Used To Add A Video Card, A Network Card, Or An Extra Serial Port. The Original 8-Bit Version Of PCI Uses A 62 Pin Connection And Supports Clock Speeds Of 8 And 33 Mhz. 16-Bit PCI Uses 98 Pins And Supports The Same Clock Speeds. The Original 8-Bit Version Of Isa Was Introduced In 1981 But The Technology Did Not Become Widely Used Until 1984, When The 16-Bit Version Was Released. Two Competing Technologies -- MCA and VLB -- Were Also Used By Some Manufacturers, But Isa Remained the Most Common Expansion Bus for Most Of The 1980s And 1990s. However, By The End Of The Twentieth Century, Isa Ports Were Beginning To Be Replaced By Faster PCI And AGP Slots. Today, Most Computers Only Support PCI and AGP Expansion Cards. 4.3.P.Isa.Pci And Ramslots In Mother Board
- 98. COMPUTERFUNDAMENTALS 1O.CMOS BATTERY The CMOS Is A Physical Part Of The Motherboard It Is A Memory Chip That Houses Setting Configurations And Is Powered By The Onboard Battery. The CMOS Is Reset And Loses All Custom Settings In Case The Battery Runs Out Of Energy, Additionally, The System Clock Resets When The CMOS Loses Power The CMOS Is Also A Computer Chip On The Motherboard, But More Specifically, It Is A RAM Chip. This Is A Type Of Memory Chip Which Stores Information About The Computer Components, As Well As Settings For Those Components. However, Normal RAM Chips Lose The Information Stored In Them When Power Is No Longer Supplied To Them. To Retain The Information In The CMOS Chip, A CMOS Battery On The Motherboard Supplies Constant Power To That CMOS Chip. 4.3.Q.Cmos Battery 4.3.R.CMOS Battery On Mother Board
- 99. COMPUTERFUNDAMENTALS 11. ACCELERATED GRAPHICS PORT [AGP SLOT] Stands For "ACCELERATED GRAPHICS PORT." AGP Is A Type Of Expansion Slot Designed Specifically For Graphics Cards. It Was Developed In 1996 As An Alternative To The PCI Standard. Since The AGP Interface Provides A Dedicated Bus for Graphics Data, AGP Cards Are Able To Render Graphics Faster Than Comparable PCI Graphics Cards. Like PCI Slots, AGP Slots Are Built Into A Computer's Motherboard. They Have A Similar Form Factor To PCI Slots, But Can Only Be Used For Graphics Cards. Additionally, Several AGP Specifications Exist, Including AGP 1.0, 2.0, and 3.0, Which Each Use A Different Voltage. Therefore, AGP Cards Must Be Compatible With The Specification Of The AGP Slot They Are Installed In. Since AGP Cards Require An Expansion Slot, They Can Only Be Used In Desktop Computers. 4.3.S.AGP Slot On Mother Board
- 100. COMPUTERFUNDAMENTALS 12.CPU SLOT Since The Very First CPU, Both Intel And AMD Have Been Creating Several Different Sockets To Be Used By Their Processors. In The Beginning, A CPU Socket Was Compatible With Just One Kind Of Processor. This Scenario Changed With The Launching Of The 486 Processor And The Massive Use Of ZIF (Zero Insertion Force) Sockets, Also Known As LIF (Low Insertion Force). The First Pentium Processors (60 MHZ And 66 MHZ) Used A Pin out Standard Called Socket 4, Which Was Fed With 5 V. Pentium Processors From 75 MHz On Were Fed With 3.3 V, Requiring A New Socket, Called Socket 5, Which Was Incompatible With Socket 4. (For Example, A Pentium-60 Couldn’t Be Installed On Socket 5 And A Pentium-100 Couldn’t Be Installed On Socket 4.). Socket 7 Uses The Same Pin out As Socket 5 With The Addition Of One Key Pin, Accepting The Same Processors Accepted By Socket 5 Plus New CPUS, Especially CPUS Designed By Competing Companies. 4.3.T. Processor Slot 4.3.U.Procesor In Cpu Slot
- 101. COMPUTERFUNDAMENTALS 13. POWER SUPPLY PLUG IN A Power Supply Unit (PSU) Converts Mains Ac To Low-Voltage Regulated Dc Power For The Internal Components Of A Computer. Modern Personal Computers Universally Use A Switched-Mode Power Supply. Some Power Supplies Have A Manual Selector For Input Voltage, While Others Automatically Adapt To The Supply Voltage. Most Modern Desktop Personal Computer Power Supplies Conform To The Atx Specification, Which Includes Form Factor And Voltage Tolerances. While An Atx Power Supply Is Connected To The Mains Supply, It Always Provides A 5 V Standby (5vsb) Voltage So That The Standby Functions On The Computer And Certain Peripherals Are Powered. Atx Power Supplies Are Turned On And Off By A Signal From The Motherboard. They Also Provide A Signal To The Motherboard To Indicate When The Dc Voltages Are In Spec, So That The Computer Is Able To Safely Power Up And Boot. The Most Recent Atx PSU Standard Is Version 2.31 Of Mid-2008. 4.3. V.SMPS 4.3.W.SMPS Connection to Mother Board
- 102. COMPUTERFUNDAMENTALS 4.3.X. Power Cables 4.3.Y. Power Connection To Cpu 4.4COMPLETE MOTHER BOARD VIEW 4.4.A.Connecting Devices To Mother Board
- 103. COMPUTERFUNDAMENTALS 4.4. Complete Mother Board Description
- 104. COMPUTERFUNDAMENTALS Questions on Computer Mother Board Q1 ] UNIVAC IS A. Universal Automatic Computer B. Universal Array Computer C. Unique Automatic Computer D. Unvalued Automatic Computer Correct Answer: A. Universal Automatic Computer Explanation: There Are No Computers With The Name As In Other Options. UNIVAC Was The First General Purpose Electronic Digital Computer Designed For Commercial Use, Produced By Universal Accounting Company Of John M And JP Eckert In 1951. Q2] CD-ROM Stands For A. Compactable Read Only Memory B. Compact Data Read Only Memory C. Compactable Disk Read Only Memory D. Compact Disk Read Only Memory Correct Answer: D. Compact Disk Read Only Memory Explanation: There Are No Objects With The Name As In Other Options. CD-ROM Is A Non- Volatile Optical Data Storage Medium Using The Same Physical Format As Audio Compact Disk, Readable By A Computer With A CD-ROM Drive. The Standard 12 Cm Diameter CD- ROM Store About 660 Megabytes. Q3] ALU Means A. Arithmetic Logic Unit B. Array Logic Unit C. Application Logic Unit D. None Of Above Correct Answer: A. Arithmetic Logic Unit Explanation: ALU Is A Unit In Central Processing Unit In A Computer System That Is
- 105. COMPUTERFUNDAMENTALS Responsible For Arithmetic Calculations And Logical Operations. Apart From ALU, The CPU Contains MU (Memory Unit) And CU (Control Unit). Q4] VGA Is A. Video Graphics Array B. Visual Graphics Array C. Volatile Graphics Array D. Video Graphics Adapter Correct Answer: A. Video Graphics Array Explanation: VGA Is A Type Of Graphics Adapter. Graphic Adapter Is An Electronic board That Controls The Display Of A Monitor. This Device Helps the Motherboard to Work with the Monitor and In VGA and SVGA the Last Letter ‘A’ Stands For ‘Array’ Whereas In MDA, CGA, MCGA the Last Letter ‘A’ Stands For ‘Adapter Q5] I BM 1401 Is A. First Generation Computer B. Second Generation Computer C. Third Generation Computer D. Fourth Generation Computer Correct Answer: B. Second Generation Computer Explanation: IBM 1401 Is A Second Generation Computer And Is The First Computer To Enter Nepal In 2028 BS For Census. Government Of Nepal Had Brought This Computer On Rent And Later Purchased For Data Processing In Bureau Of Statistics. After This Computer, Another ICL 2950/10, A British Computer, Was Purchased By The Fund Of UNDP And UNFPA For The Census Of 2038 BS Is Second Computer In NEPAL. Q6] MSI Stands For A. Medium Scale Integrated Circuits B. Medium System Integrated Circuits
- 106. COMPUTERFUNDAMENTALS C. Medium Scale Intelligent Circuit D. Medium System Intelligent Circuit Correct Answer: A. Medium Scale Integrated Circuits Explanation: After The Invention Of IC Chips The Development Of Computers Plunged Into Next Phase. Small Scale Integration And Medium Scale Integration (SSI And MSI) Were Used In Third Generation Of Computers And Large Scale Integration And Very Large Scale Integration (LSI And VLSI) Are Being Used In Fourth Generation Of Computers. People Are Now Expecting ULSI (Ultra Large Scale Integration) Circuits To Be Used For Fifth Generation Computers. Q7] The Capacity Of 3.5 Inch Floppy Disk Is A. 1.40 MB B. 1.44 GB C. 1.40 GB D. 1.44 MB Correct Answer: D. 1.44 MB Explanation: Microfloppy Disks (3.5 Inch) If It Is High Density (MF2HD) Can Store 1.44 MB And If It Is Low Density (MF2DD), It Can Store 720 KB. Mini Floppy Disks (5.25 Inch) If It Is High Density (MD2HD) Can Store 1.2 MB And Low Density (MD2DD) Stores 360 KB Of Data. Q8.]The First Computer Introduced In Nepal Was A. IBM 1400 B. IBM 1401 C. IBM 1402 D. IBM1402 Correct Answer: B. IBM 1401 Explanation: IBM 1401, A Second Generation Computer Was Brought In Nepal By The government Of Nepal Paying One Lakh And Twenty Five Thousands Per Month To Use In The Census In 2028 B.S. Before This Computer, Nepal Was Using A Calculating Device Called Facet For Statistical Tasks.
- 107. COMPUTERFUNDAMENTALS Correct Answer: B. Wide Area Network Explanation: There Are Three Different Classes Of Computer Network 1. LAN – Local Area Net Work 2. MAN: Metropolitan Net Work 3. WAN: Wide Area Network Q9] WAN Stands For A. WAP Area Network B. Wide Area Network C. Wide Array Net D. Wireless Area Network Q10] MICR Stands For A. Magnetic Ink Character Reader B. Magnetic Ink Code Reader C. Magnetic Ink Cases Reader D. None Correct Answer: A. Magnetic Ink Character Reader Explanation: MICR (Magnetic Ink Character Reader) Is Kind Of Scanner That Can Scan And Identify The Writing Of Magnetic Ink. This Device Is Used In Banks To Verify Signatures In Checks. Q11] Which of the Following Is Not Real Security and Privacy Risk? A. Hackers B. Spam C. Viruses D. Identity Theft Correct Answer: B Q12] Who Is Known As Father of Computers A. Lord Wellington B. Charles Babbage C. Jack Kilby D. Bill Gates Correct Answer: B Q13 ] ROM Stands For ?
- 108. COMPUTERFUNDAMENTALS A. Random Only Memory B. Readable Only Memory C. Read Only Memory D. Random Other Memory Correct Answer: C Q14] N -TH First Generation Computers Built Between (1945 -1956) What Was Used For Calculations A. Transistors B. Integrated Circuits C. Very Large Scale Integration D. Vacuum Tubes Correct Answer: D Q15] UPS Stands For? A United Power Solutions B. Uninterrupted Power Supply C. Uninterrupted Power Solution D. Untied Power Supply Correct Answer: D Q16] The Number System Based On "0" And "1" Only Is Known As A. Binary System B Barter System C. Number System D. HEXA Decimal System Q19 Which of the Following Is an Advantage Of Using A Local Area Network (LAN)? A. Protects Against Virus Infection B. Shared Resources C. Data Security D. Prevents Computer Misuse Correct Answer: B Q17] Server Is A? A. Multimedia CD B. Personal Computer C. Multi – User Computer D. Integrated Data Management Correct Answer: B
- 109. COMPUTERFUNDAMENTALS Q18] What Is Internet? A. Network of All Computers in a Company Not Connected To Web B. Network of All Computers in a Company Not Connected To Web C. Global Network of Computers Correct Answer: C Q19] Which of the Following Is Not an Integral Part of Computer A. CPU B. Mouse C. Monitor D. UPS Correct Answer: A Q20] RAM Stands For? A. Revolutionary Access Memory B. Relational Access Memory C. Random Access Memory D. Rotational Access Memory Correct Answer: C
- 110. COMPUTERFUNDAMENTALS 5. COMPUTER –SOFTWARE Software Is A Set Of Programs, Which Is Designed To Perform A Well- Defined Function. A Program Is A Sequence Of Instructions Written To Solve A Particular Problem. There Are Two Types of Software 1) System Software 2) Application Software 5. A.Software Classification
- 111. COMPUTERFUNDAMENTALS 5.1] SYSTEM SOFTWARE The system software is collection of programs designed to operate, control, and extend the processing capabilities of the computer itself. System software is generally prepared by computer manufactures. These software products comprise of programs written in low-level languages which interact with the hardware at a very basic level. System software serves as the interface between hardware and the end users. Some examples of system software are Operating System, Compilers, Interpreter, and Assemblers etc. 5. 1.A.Examples Of System Software Features Of System Software Are As Follows: Close To System Fast In Speed Difficult To Design Difficult To Understand Less Interactive Smaller In Size Difficult To Manipulate Generally Written In Low-Level Language
- 112. COMPUTERFUNDAMENTALS System Software Can be classified into Following Types 1] Operating system 2] System development software 3] Utility programs 5.1.1. OPERATING SYSTEM Operating System is Software That Communicates With The Hardware And Allows Other Programs To Run. It is comprised of system/The Fundamental Files Your Computer Needs To Boot up And Function. Every Desktop Computer, Tablet, And Smartphone Includes An Operating System That Provides Basic Functionality For The Device. Common Desktop Operating Systems Include windows, Mac OS X, And Linux. While Each OS Is Different, They All Provide A Graphical User Interface, Or GUI, That Includes A Desktop And The Ability To Manage Files And Folders. They Also Allow You To Install And Run Programs Written For The Operating System. While Windows And Linux Can Be Installed On Standard PC Hardware, Mac OS X Can Only Run On Macintosh Computers. Therefore, The Hardware You Choose Affects What Operating System(S) You Can Run. 5.1.1. A.Examples of Operating System
- 113. COMPUTERFUNDAMENTALS 5.1.2. SYSTEM DEVELOPMENT SOFTWARE Software Development Is The Computer Programming, Documenting, Testing, And Bug Fixing Involved In Creating And Maintaining Applications And Frameworks Involved In A Software Release Life Cycle And Resulting In A Software Product. The Term Refers To A Process Of Writing And Maintaining The Source Code, But In A Broader Sense Of The Term. It Includes All That Is Involved Between The Conception Of The Desired Software Through To The Final Manifestation Of The Software, Ideally In A Planned Therefore, Software Development May Include Research, New Development, Prototyping, Modification, Reuse, Re-Engineering, Maintenance, Or Any Other Activities That Result In Software Products.[2] 5.1.2. A.Software Development Cycle
- 114. COMPUTERFUNDAMENTALS 5.1.3. UTILITY PROGRAMS Utility Software Helps To Manage, Maintain And Control Computer Resources. Operating Systems Typically Contain The Necessary Tools For This, But Separate Utility Programs Can Provide Improved Functionality. Utility Software Is Often Somewhat Technical And Targeted At Users With A Solid Knowledge Of Computers. If You Use A Computer Mostly For E-Mail, Some Internet Browsing And Typing Up A Report, You May Not Have Much Need For These Utilities. However, If You Are An Avid Computer User, These Utilities Can Help Make Sure Your Computer Stays In Tip-Top Shape. Examples Of Utility Programs Are Antivirus Software, Backup Software And Disk Tools. Let's Look At Each Of These In A Bit More Detail. Antivirus Software, As The Name Suggests, Helps To Protect A Computer System From Viruses And Other Harmful Programs. 5.1.3. A.Utility Software Example
- 115. COMPUTERFUNDAMENTALS 5.2. APPLICATION SOFTWARE Application Software, Or Simply Applications, Are Often Called Productivity Programs Or End-User Programs Because They Enable The User To Complete Tasks Such As Creating Documents, Spreadsheets, Databases, And Publications, Doing Online Research, Sending Email, Designing Graphics, Running Businesses, And Even Playing Games! Application Software Is Specific To The Task It Is Designed For And Can Be As Simple As A Calculator Application Or As Complex As A Word Processing Application. When You Begin Creating A Document, The Word Processing Software Has Already Set The Margins, Font Style And Size, And The Line Spacing For You. But You Can Change These Settings, And You Have Many More Formatting Options Available. For Example, The Word Processor Application Makes It Easy To Add Color, Headings, And Pictures Or Delete, Copy, Move, And Change The Document's Appearance To Suit Your Needs. Microsoft Word Is A Popular Word-Processing Application That Is Included In The Software Suite Of Applications Called Microsoft Office. A Software Suite Is A Group Of Software Applications With Related Functionality. For Example, Office Software Suites Might Include Word Processing, Spreadsheet, Database, Presentation, And Email Applications.
- 116. COMPUTERFUNDAMENTALS Graphics Suites Such As Adobe Creative Suite Include Applications For Creating And Editing Images, While Sony Audio Master Suite Is Used For Audio Production. 5.2. A.Application Software Examples
- 117. COMPUTERFUNDAMENTALS 5.2.1. USER DEVELOPED PROGRAMS End-user development (EUD) or end-user programming (EUP) refers to activities and tools that allow end-users – people who are not professional software developers – to program computers. People who are not professional developers can use EUD tools to create or modify software artifacts (descriptions of automated behavior) and complex data objects without significant knowledge of programming. Various approaches exist, and it is an active research topic within the field of computer science and human-computer interaction. Examples include spreadsheets, scripting languages (particularly in an office suite or art application), and programming by example. The most popular EUD tool is the spreadsheet. Due to their unrestricted nature, spreadsheets allow relatively un-sophisticated computer users to write programs that represent complex data models, while shielding them from the need to learn lower-level programming languages. Because of their common use in business, spreadsheet skills are among the most beneficial skills for a graduate employee to have, and are therefore the most commonly sought after In the United States of America alone, there are an estimated 13 million end user developers programming with spreadsheets. 5.2.1A.Software Description
- 118. COMPUTERFUNDAMENTALS 5.2.2. CUSTOM SOFTWARE Custom software (also known as bespoke software or tailor-made software) is software that is specially developed for some specific organization or other user. As such, it can be contrasted with the use of software packages developed for the mass market, such as commercial off-the-shelf (COTS) software, or existing free software. Since custom software is developed for a single customer it can accommodate that customer's particular preferences and expectations. Custom software may be designed in stage by stage processes, allowing all nuances and possible hidden dangers to be taken into account, including issues which were not mentioned in the specifications. Especially the first phase in the software development process may involve many departments, including marketing, engineering, research and development and general management. Large companies commonly use custom software for critical functions, including content management, inventory management, customer management, human resource management, or otherwise to fill the gaps present in the existing software packages. Often such software is legacy software, developed before COTS software packages offering the required functionality became available. 5.2.2. B.Custom Software Development Cycle
- 119. COMPUTERFUNDAMENTALS 5.3. ASSEMBLER An Assembler Is Not Equivalent To An Interpreter, Or Compiler, Assembly Language Is A Low Level Language. An Assembler Is One Form Of Program Translation. This Is One Relationship Between Assembler, Compiler And Interpreter. Each Assembly Language Statement Directly Corresponds To One Machine Instruction. The Assembler Changes Assembly Instructions Into Machine Language, Whereas A Compiler Runs A Higher Level Programming Language Instructions Into Assembly Instructions And Then Those Are Converted Into Executable Machine Language. Accumulated Programming Languages Normally Generate Lots Of Lines Of Assembly Instructions For Each Program Report. An Assemblercreatesobject Code by Changing Symbols Or Substitute Names Into machine Code. One Could Conclude That Assembly Language Is Not A Programming Language At All, Just Guilty By Association. Assembly Language Is Nothing More Than A "Shorthand" System Of Writing, Machine Language, Programs Using Symbols That "Friendless Personality Lacking, Knuckle Dragging WOW Players", Otherwise Known As Programmers, Can Understand 5.3. A.AssemblerFig
- 120. COMPUTERFUNDAMENTALS 5.4. COMPILER A Compiler Converts An Entire Program Written In Source Code And Translates It Into Object Code. A Second Relationship Is That The Compiler And Interpreter Both Process Source Code. A Compiler Translates Source Code From A high-Level Programming Language to Assembly Language/ Machine Code. Acompilerworks with What Is Called Higher-Levellanguages3rd Generation languages, Such As Java And C. Typically A Person Writes Source Code Using An Editor In A Language Such As C, Pascal Or C++. The Programmer Then Selects The Appropriate Compiler For The Source Code. 5.4. A.Compiler Phases 5.4. B. General Compilation
- 121. COMPUTERFUNDAMENTALS 5.5. INTERPRETER Another relationship is that the interpreter is the step by step version of a compiler. Obviously this takes a lot of time and resources compared to previously compiled program. An interpreter doesn't have to examine the entire program before it can begin executing code. An interpreter is a computer program that takes source code and processes one line at a time. Interpreters translate code one line at time, executing each line as it is "translated," Interpreters do generate binary code, but that code is never compiled into one program. Instead, the binary code is interpreted every time the program executes. 5.5.A.Interpreter 5.5.B.Compilervs Interpreter
- 122. COMPUTERFUNDAMENTALS QUESITONS ON COMPUTER SOFTWARE 1. If There Are Multiple Recycle Bin For A Hard Disk A. You Can Set Different Size For Each Recycle Bin B. You Can Choose Which Recycle Bin To Use To Store Your Deleted Files C. You Can Make Any One Of Them Default Recycle Bin D. None Of Above ANS: A 2. Identify False Statement A. You Can Find Deleted Files In Recycle Bin B. You Can Restore Any Files In Recycle Bin If You Ever Need C. You Can Increase Free Space Of Disk By Sending Files In Recycle Bin D. You Can Right Click And Choose Empty Recycle Bin To Clean It At Once ANS: C 3. If the Displayed System Time And Date Is Wrong, You Can Reset It Using A. Write B. Calendar C. Write File D. Control Panel ANS: D
- 123. COMPUTERFUNDAMENTALS 4. You Should Save Your Computer From? A. Viruses B. Time Bombs C. Worms D. All of The Above ANS: D 5. World Wide Web Is Being Standard By A. Worldwide Corporation B. W3c C. World Wide Consortium D. World Wide Web Standard ANS: B 6. A Co-Processor A. Is Relatively Easy To Support In Software B. Causes All Processor To Function Equally C. Works With Any Application D. Is Quite Common In Modern Computer ANS: A 7. A Microsoft Windows Is ….. A. Operating System B. Graphic Program C. Word Processing D. Database Program ANS: A
- 124. COMPUTERFUNDAMENTALS 8. Which Of The Following Is Program Group? A. Accessories B. Paint C. Word D. All Of Above ANS: A 9. Which Is Not Application Software? A. Windows.NET B. Page Maker C. Windows XP D. Photoshop ANS: A 10. The ….. Program Compresses Large Files Into A Smaller File A. WinZip B. Win shrinks C. Win style D. None Of Above ANS: A 11. Which Of The Following Is An Example Of A Real Time Operating System? A. Lynx B. MS Dos C. Windows XP D. Process Control ANS: D
- 125. COMPUTERFUNDAMENTALS 12. Which Of The Following Operating System Does Not Implement The Multitasking Truly? A. Windows 98 B. Windows Net C. Windows XP D. MS Dos ANS: D 13. Which Of The Following Windows Version Support 64 Bit Processor? A. Windows 98 B. Windows 2000 C. Windows XP D. Windows 95 ANS: A 14. Which Of The Following Operating System Does Not Implement Multitasking Truly? A. Windows 98 B. Windows Net C. Windows XP D. MS Dos ANS: D 15. What Program Runs First After Computer Is Booted And Loading GUI? A. Desktop Manager B. File Manager C. Windows Explorer D. Authentication ANS: D
- 126. COMPUTERFUNDAMENTALS 16. Which Of The Following Operating System Do You Choose To Implement A Client Server Network? A. MS Dos B. Windows C. Windows 98 D. Windows 2000 ANS: D 17. Which Of The Following Operating Systems Is Better For Implementing A Client-Server Network A. MS Dos B. Windows 95 C. Windows 98 D. Windows 2000 ANS: D 18. My Computer Was Introduced From A. Windows 3.1 B. Windows 3.11 C. Windows 95 D. Windows 98 ANS: C 19. Which Of The Following Windows Do Not Have Start Button A. Windows Vista B. Windows 7 C. Windows 8 D. None Of Above
- 127. COMPUTERFUNDAMENTALS ANS:C 20. Which Is The Latest Version Of MS Windows? A. Windows 2007 B. Windows 8.1 C. Windows 2008 D. Windows 7 ANS: B 21. Which operating system doesn’t support networking between computers? a. Windows 3.1 b. Windows 95 c. Windows 2000 d. Windows NT ANS: A 22. Which Operating System doesn’t support networking between computers? a. Windows 3.1 b. Windows 95 c. Windows 2000 d. Windows NT ANS: A 23. Which of the following does not support more than one program at a time? a. DOS b. Linux c. Windows d. UNIX
- 128. COMPUTERFUNDAMENTALS ANS: A 24. Which of the following is not an operating system? a. DOS b. Linux c. Windows d. Oracle ANS: D 25. Linux is a (n) … operating system a. Open source b. Microsoft c. Windows d. Mac ANS: A
- 129. COMPUTERFUNDAMENTALS 6. OPERATING SYSTEM 6.1BASICS OF OPERATING SYSTEM Os-Definition “An operating system (OS) is a collection of software that manages computer hardware resources and provides common services for computer programs. The operating system is a vital component of the system software in a computer system.” In technical terms, It is a software which manages hardware. An operating System controls the allocation of resources and services such as memory, processors, devices and information. An operating system is a program that acts as an interface between the user and the computer hardware and controls the execution of all kinds of programs. Functions of Operating System Following Are Some Of Important Functions Of An Operating System. Memory Management Processor Management Device Management File Management Security Control Over System Performance Job Accounting Error Detecting Aids Coordination Between Other Software And User
- 130. COMPUTERFUNDAMENTALS 6.1. A.operating system with peripherals 6.1. B .Operating system architecture
- 131. COMPUTERFUNDAMENTALS 6.2.TYPESOFOPERATINGSYSTEM Following Are Few Of The Important Types Of Operating System Which Are Most Commonly Used. 1) Batchoperatingsystem 2) Time-SharingOperatingSystems 3) DistributedOperatingSystem 4) NetworkOperatingSystem 5) RealTime OperatingSystem 1.BATCH OPERATINGSYSTEM The Users Of Batch Operating System Do Not Interact With The Computer Directly. Each User Prepares His Job On An Off-Line Device Like Punch Cards And Submits It To The Computer Operator. To Speed Up Processing, Jobs With Similar Needs Are Batched Together And Run As A Group. Thus, The Programmers Left Their Programs With The Operator. The Operator Then Sorts Programs into Batches with Similar Requirements. The Problems With Batch Systems Are Following. Lack of Interaction between the User and Job. CPU Is Often Idle, Because The Speeds Of The Mechanical I/O Devices Is Slower Than CPU.
- 132. COMPUTERFUNDAMENTALS Difficult To Provide The Desired Priority. 6.2.A.BatchProcessingOperatingSystem 3.TIME-SHARINGOPERATINGSYSTEMS Time Sharing Is A Technique Which Enables Many People, Located At Various Terminals, To Use A Particular Computer System At The Same Time . Time-Sharing Or Multitasking Is A Logical Extension Of Multiprogramming. Processor's Time Which Is Shared Among Multiple Users Simultaneously Is Termed As Time-Sharing. T He Main Difference Between Multiprogrammed Batch Systems And Time-Sharing Systems Is That In Case Of Multiprogrammed Batch Systems, Objective Is To Maximize Processor Use, Whereas In Time-Sharing Systems Objective Is To Minimize Response Time.
- 133. COMPUTERFUNDAMENTALS Multiple Jobs Are Executed By The CPU By Switching Between Them, But The Switches Occur So Frequently. Thus, The User Can Receive An Immediate Response. For Example, In A Transaction Processing, Processor Execute Each User Program In A Short Burst Or Quantum Of Computation. That Is If N Users Are Present, Each User Can Get Time Quantum. When The User Submits The Command, The Response Time Is In Few Seconds At Most. Advantages of Timesharing Operating Systems Are Following Provide Advantage Of Quick Response. Avoids Duplication Of Software. Reduces CPU Idle Time. Disadvantages Of Timesharing Operating Systems Are Following. Problem Of Reliability. Question Of Security And Integrity Of User Programs And Data. Problem Of Data Communication. 6.2. B.Time Sharing Os Operation Cycle
- 134. COMPUTERFUNDAMENTALS 3. DISTRIBUTEDOPERATINGSYSTEM Distributed Systems Use Multiple Central Processors To Serve Multiple Real Time Application And Multiple Users. Data Processing Jobs Are Distributed Among The Processors Accordingly To Which One Can Perform Each Job Most Efficiently. The Processors Communicate With One Another Through Various Communication Lines (Such As High-Speed Buses Or Telephone Lines). These Are Referred As Loosely Coupled Systems Or Distributed Systems. Processors In A Distributed System May Vary In Size And Function. These Processors Are Referred As Sites, Nodes, And Computers And So On. The Advantages Of Distributed Systems Are Following. With Resource Sharing Facility User At One Site May Be Able To Use The Resources Available At Another. Speedup the Exchange Of Data With One Another Via Electronic Mail. Reduction Of The Load On The Host Computer. Reduction Of Delays In Data Processing. 6.2. C. Distributed type operating system
- 135. COMPUTERFUNDAMENTALS 4.NETWORKOPERATINGSYSTEM Network Operating System Runs On A Server And And Provides Server The Capability To Manage Data, Users, Groups, Security, Applications, And Other Networking Functions. The Primary Purpose Of The Network Operating System Is To Allow Shared File And Printer Access Among Multiple Computers In A Network, Typically A Local Area Network (LAN), A Private Network Or To Other Networks. Examples Of Network Operating Systems Are Microsoft Windows Server 2003, Microsoft Windows Server 2008, UNIX, Linux, Mac OS X, Novell Netware, And BSD. The Advantages Of Network Operating Systems Are Following. Centralized Servers Are Highly Stable. Security Is Server Managed. Upgrades to New Technologies and Hardware’s Can Be Easily Integrated Into The System. Remote Access To Servers Is Possible From Different Locations And Types Of Systems. The Disadvantages Of Network Operating Systems Are Following. High Cost Of Buying And Running A Server. Dependency On A Central Location For Most Operations. Regular Maintenance And Updates Are Required. 6.2.D.ClientServer Model
- 136. COMPUTERFUNDAMENTALS 6.2. E.Network Operating System [NOS] 5. REALTIMEOPERATINGSYSTEM Real Time System Is Defines As A Data Processing System In Which The Time Interval Required To Process And Respond To Inputs Is So Small That It Controls The Environment. Real Time Processing Is Always On Line Whereas On Line System Need Not Be Real Time. The Time Taken By The System To Respond To An Input And Display Of Required Updated Information Is Termed As Response Time. So In This Method Response Time Is Very Less As Compared To the Online Processing.
- 137. COMPUTERFUNDAMENTALS Real-Time Systems Are Used When There Are Rigid Time Requirements On The Operation Of A Processor Or The Flow Of Data And Real-Time Systems Can Be Used As A Control Device In A Dedicated Application. Real-Time Operating System Has Well-Defined, Fixed Time Constraints Otherwise System Will Fail. For Example Scientific Experiments, Medical Imaging Systems, Industrial Control Systems, Weapon Systems, Robots, And Home-Appliance Controllers, Air Traffic Control System Etc. There Are Two Types Of Real-Time Operating Systems. HARD REAL-TIME SYSTEMS Hard Real-Time Systems Guarantee That Critical Tasks Complete On Time. In Hard Real-Time Systems Secondary Storage Is Limited Or Missing With Data Stored In ROM. In These Systems Virtual Memory Is Almost Never Found. SOFT REAL-TIME SYSTEMS Soft Real Time Systems Are Less Restrictive. Critical Real-Time Task Gets Priority Over Other Tasks And Retains The Priority Until It Completes. Soft Real-Time Systems Have Limited Utility than Hard Real-Time Systems. For Example, Multimedia, Virtual Reality, Advanced Scientific Projects Like Undersea Exploration And Planetary Rovers Etc.
- 138. COMPUTERFUNDAMENTALS 6.2. D.RTOS Block Diagram 6.2PROCESS MANAGEMENT 6.2.1 .PROCESS. A Process Is A Program In Execution. The Execution Of A Process Must Progress In A Sequential Fashion. Definition Of Process Is Following. A Process Is Defined As An Entity Which Represents The Basic Unit Of Work To Be Implemented In The System.
- 139. COMPUTERFUNDAMENTALS Components Of Process Are Following. S.N. Component & Description 1 Object Program Code To Be Executed. 2 Data Data To Be Used For Executing The Program. 3 Resources While Executing The Program, It May Require Some Resources. 4 Status Verifies The Status Of The Process Execution. A Process Can Run To Completion Only When All Requested Resources Have Been Allocated To The Process. Two Or More Processes Could Be Executing The Same Program, Each Using Their Own Data And Resources. 6.2.1.A. Process Management figure.
- 140. COMPUTERFUNDAMENTALS PROCESSSTATES As A Process Executes, It Changes State. The State Of A Process Is Defined As The Current Activity Of The Process. Process Can Have One Of The Following Five States At A Time. S.N. State & Description 1 New The Process Is Being Created. 2 Ready The Process Is Waiting To Be Assigned To A Processor. Ready Processes Are Waiting To Have The Processor Allocated To Them By The Operating System So That They Can Run. 3 Running Process Instructions Are Being Executed (I.E. The Process That Is Currently Being Executed). 4 Waiting The Process Is Waiting For Some Event To Occur (Such As The Completion Of An I/O Operation). 5 Terminated The Process Has Finished Execution.
- 141. COMPUTERFUNDAMENTALS PROCESSCONTROLBLOCK[PCB] Each Process Is Represented In the Operating System by A Process Control Block (PCB) Also Called A Task Control Block. PCB Is The Data Structure Used By The Operating System. Operating System Groups All Information That Needs About Particular Process. PCB Contains Many Pieces Of Information Associated With A Specific Process Which Are Described Below. S.N. Information & Description 1 Pointer Pointer Points To Another Process Control Block. Pointer Is Used For Maintaining The Scheduling List. 2 Process State Process State May Be New, Ready, Running, Waiting And So On. 3 Program Counter Program Counter Indicates The Address Of The Next Instruction To Be Executed For This Process. 4 CPU Registers CPU Registers Include General Purpose Register, Stack Pointers, Index Registers And Accumulators Etc. Number Of Register And Type Of Register Totally Depends Upon The Computer Architecture. 5 Memory Management Information This Information May Include The Value Of Base And Limit Registers, The Page Tables, Or The Segment Tables Depending On The Memory System Used By The Operating System. This Information Is Useful For DE allocating The Memory When The Process Terminates.
- 142. COMPUTERFUNDAMENTALS 6 Accounting Information This Information Includes The Amount Of CPU And Real Time Used, Time Limits, Job Or Process Numbers, Account Numbers Etc. Process Control Block Includes CPU Scheduling, I/O Resource Management, File Management Information Etc... The PCB Serves As The Repository For Any Information Which Can Vary From Process To Process. Loader/Linker Sets Flags and Registers When a Process Is Created. If That Process Gets Suspended, The Contents Of The Registers Are Saved On A Stack And The Pointer To The Particular Stack Frame Is Stored In The PCB. By This Technique, The Hardware State Can Be Restored So That The Process Can Be Scheduled To Run Again. 6.2.1. B.Process Control Blocks Accessing
- 143. COMPUTERFUNDAMENTALS 6.2.2PROCESS SCHEDULING Definition “The Process Scheduling Is The Activity Of The Process Manager That Handles The Removal Of The Running Process From The CPU And The Selection Of Another Process On The Basis Of A Particular Strategy”. Process Scheduling Is An Essential Part Of A Multiprogramming Operating System. Such Operating Systems Allow More Than One Process To Be Loaded Into The Executable Memory At A Time And Loaded Process Shares The CPU Using Time Multiplexing. SCHEDULINGQUEUES Scheduling Queues Refers To Queues Of Processes Or Devices. When The Process Enters Into The System, Then This Process Is Put Into A Job Queue. This Queue Consists Of All Processes In The System. The Operating System Also Maintains Other Queues Such As Device Queue. Device Queue Is A Queue For Which Multiple Processes Are Waiting For A Particular I/O Device. Each Device Has Its Own Device Queue. This Figure Shows The Queuing Diagram Of Process Scheduling. Queue Is Represented By Rectangular Box. The Circles Represent The Resources That Serve The Queues. The Arrows Indicate The Process Flow In The System.
- 144. COMPUTERFUNDAMENTALS 6.2.1. C. Process Scheduling Queues Queues Are Of Two Types 1. Ready Queue 2. Device Queue A Newly Arrived Process Is Put In The Ready Queue. Processes Waits In Ready Queue For Allocating The CPU. Once The CPU Is Assigned To A Process, Then That Process Will Execute. While Executing The Process, Any One Of The Following Events Can Occur. The Process Could Issue An I/O Request And Then It Would Be Placed In An I/O Queue. The Process Could Create New Sub Process And Will Wait For Its Termination. The Process Could Be Removed Forcibly From the CPU, As A Result Of Interrupt and Put Back In the Ready Queue.
- 145. COMPUTERFUNDAMENTALS TWOSTATE PROCESSMODEL Two State Process Models Refers To Running And Non-Running States Which Are Described Below. S.N. State & Description 1 Running When New Process Is Created By Operating System That Process Enters Into The System As In The Running State. 2 Not Running Processes That Are Not Running Are Kept In Queue, Waiting For Their Turn To Execute. Each Entry In The Queue Is A Pointer To A Particular Process. Queue Is Implemented By Using Linked List. Use Of Dispatcher Is As Follows. When A Process Is Interrupted, That Process Is Transferred In The Waiting Queue. If The Process Has Completed Or Aborted, The Process Is Discarded. In Either Case, The Dispatcher Then Selects A Process From The Queue To Execute. 6.2.1. D. Two state model
- 146. COMPUTERFUNDAMENTALS Questions on operating system 1. What Is Operating System? A) Collection of Programs That Manages Hardware Resources B) System Service Provider to the Application Programs C) Link to Interface the Hardware and Application Programs D) All of the Mentioned ANSWER: D . 2. To Access The Services Of Operating System, The Interface Is Provided By The A) System Calls B) API C) Library D) Assembly Instructions ANSWER: A 3. Which One Of The Following Is Not True? A) Kernel Is The Program That Constitutes The Central Core Of The Operating System B) Kernel Is The First Part Of Operating System To Load Into Memory During Booting C) Kernel Is Made Of Various Modules Which Can Not Be Loaded In Running Operating System D) Kernel Remains In The Memory During The Entire Computer Session ANSWER: C 4. Which One Of The Following Error Will Be Handle By The Operating System? A) Power Failure B) Lack Of Paper in Printer C) Connection Failure in the Network D) All of the Mentioned
- 147. COMPUTERFUNDAMENTALS ANSWER: D 5. The Main Function Of The Command Interpreter Is A) To Get And Execute The Next User-Specified Command B) To Provide The Interface Between The API And Application Program C) To Handle The Files In Operating System D) None Of The Mentioned ANSWER:A 6. By Operating System, The Resource Management Can Be Done Via A) Time Division Multiplexing B) Space Division Multiplexing C) Both (A) And (B) D) None Of The Mentioned ANSWER:C 7. If A Process Fails, Most Operating System Write The Error Information To A A) Log File B) Another Running Process C) New File D) None Of The Mentioned ANSWER: A 8. Which Facility Dynamically Adds Probes To A Running System, Both In User Processes And In The Kernel? A) DTRACE B) DLOCATE C) DMAP D) DADD ANSWER: A
- 148. COMPUTERFUNDAMENTALS 9. Which One Of The Following Is Not A Real Time Operating System? A) VX works B) Windows CE C) RTLINUX D) Palm OS ANSWER: D 10. The OS X Has A) Monolithic Kernel B) Hybrid Kernel C) Microkernel D) Monolithic Kernel with Modules ANSWER: B 11. The Systems Which Allows Only One Process Execution At A Time, Are Called A) Uni programming Systems B) Uni processing Systems C) Uni tasking Systems D) None Of The Mentioned ANSWER: A EXPLANATION: Those Systems Which Allows More Than One Process Execution At A Time, Are Called Multiprogramming Systems. Uni processing Means Only One Processor. 12. In Operating System, Each Process Has Its Own A) Address Space And Global Variables B) Open Files C) Pending Alarms, Signals And Signal Handlers D) All Of The Mentioned
- 149. COMPUTERFUNDAMENTALS ANSWER: D 13. In UNIX, Which System Call Creates The New Process? A) Fork B) Create C) New D) None of the Mentioned ANSWER: A 14. A Process Can Be Terminated Due To A) Normal Exit B) Fatal Error C) Killed By Another Process D) All Of The Mentioned ANSWER: D 15. What Is The Ready State Of A Process? A) When Process Is Scheduled To Run After Some Execution B) When Process Is Unable To Run Until Some Task Has Been Completed C) When Process Is Using The CPU D) None Of The Mentioned ANSWER: A EXPLANATION: When Process Is Unable To Run Until Some Task Has Been Completed, The Process Is In Blocked State And If Process Is Using The CPU, It Is In Running State. 16. What Is Interprocess Communication? A) Communication within the Process B) Communication between Two Process C) Communications between Two Threads Of Same Process
- 150. COMPUTERFUNDAMENTALS D) None Of The Mentioned ANSWER: B 17. A Set Of Processes Is Deadlock If A) Each Process Is Blocked And Will Remain So Forever B) Each Process Is Terminated C) All Processes Are Trying To Kill Each Other D) None Of The Mentioned ANSWER: A 18. A Process Stack Does Not Contain A) Function Parameters B) Local Variables C) Return Addresses D) PID Of Child Process ANSWER: D 19. Which System Call Returns The Process Identifier Of A Terminated Child? A) Wait B) Exit C) Fork D) Get ANSWER: A 20. The Address Of The Next Instruction To Be Executed By The Current Process Is Provided By The A) CPU Registers B) Program Counter C) Process Stack D) Pipe ANSWER: B
- 151. COMPUTERFUNDAMENTALS 21) A Process Control Block(PCB) Does Not Contain Which Of The Following : A) Code B) Stack C) Heap D) Data E) Program Counter F) Process State G )Bootstrap Program ANSWER: G 22) The Number Of Processes Completed Per Unit Time Is Known As __________. A) Output B) Throughput C) Efficiency D) Capacity ANSWER: B 23) The State Of A Process Is Defined By : A) The Final Activity Of The Process B) The Activity Just Executed By The Process C) The Activity To Next Be Executed By The Process D) The Current Activity Of The Process ANSWER: D 24) Which Of The Following Is Not The State Of A Process ? A) New B) Old C) Waiting D) Running ANSWER: B 25) The Process Control Block Is: A) Process Type Variable B) Data Structure C) A Secondary Storage Section ANSWER: B
- 152. COMPUTERFUNDAMENTALS 7. INTER PROCESSOR COMMUNICATION 7.1. INTRODUCTION TO IPC Processes Frequently Need To Communicate With Other Processes. For Example, In A Shell Pipeline, The Output Of The First Process Must Be Passed To The Second Process, And So On Down The Line. Thus, There Is A Need For Communication Between Processes, Preferably In A Well- Structured Way Not Using Interrupts. Because, Interrupts Decrease System Performance. That Communication between Processes in the Control of the OS Is Called as Inter process Communication or Simply IPC In Some Operating Systems, Processes That Are Working Together Often Share Some Common Storage Area That Each Can Read And Write. To See How IPC Works In Practice, Let Us Consider A Simple But Common Example, A Print Spooler. When A Process Wants To Print A File, It Enters The File Name In A Special Spooler Directory. Another Process, The Printer Daemon, Periodically Checks To See If There Are Any Files To Be Printed, And If There Are, It Sends Them To Printer And Removes Their Names From The Directory.
- 153. COMPUTERFUNDAMENTALS 7.1A.Inter Process Communication 7.1.1RACE CONDITIONS ‘’A Race Condition Is AnUndesirableSituationThatOccursWhenA Device Or system attempts To Perform Two Or More Operations At The Same Time, But Because Of The Nature Of The Device Or System, The Operations Must Be Done In The Proper Sequence To Be Done Correctly’’. A Simple Example Of A Race Condition Is A Light Switch. In Some Homes There Are Multiple Light Switches Connected To A Common Ceiling Light. When These Types Of Circuits Are Used, The Switch Position Becomes Irrelevant. If The Light Is On, Moving Either Switch From Its Current Position Turns The Light Off. Similarly, If The Light Is Off, Then Moving Either Switch From Its Current Position Turns The Light On. With That In Mind, Imagine What Might Happen If Two People Tried To Turn On The Light Using Two Different Switches At Exactly The Same Time. One Instruction Might Cancel The Other Or The Two Actions Might Trip The Circuit Breaker.
- 154. COMPUTERFUNDAMENTALS Suppose For A Moment That Two Processes Need To Perform A Bit Flip At A Specific Memory Location. Under Normal Circumstances The Operation Should Work Like This: Process 1 Process 2 Memory Value Read Value 0 Flip Value 1 Read Value 1 Flip Value 0 In This Example, Process 1 Performs A Bit Flip, Changing The Memory Value From 0 To 1. Process 2 Then Performs A Bit Flip And Changes The Memory Value From 1 To 0 If A Race Condition Occurred Causing These Two Processes To Overlap, The Sequence Could Potentially Look More Like This: Process 1 Process 2 Memory Value Read Value 0
- 155. COMPUTERFUNDAMENTALS Read Value 0 Flip Value 1 Flip Value 1 In This Example, The Bit Has An Ending Value Of 1 When Its Value Should Be 0. This Occurs Because Process 2 Is Unaware That Process 1 Is Performing A Simultaneous Bit Flip. Preventing Race Conditions In Computing Environments, Race Conditions Can Be Prevented By Serialization Of Memory Or Storage Access. This Means If Read And Write Commands Are Received Close Together, The Read Command Is Executed And Completed First By Default. 7.1.2SEMAPHORES In programming, especially in UNIX systems, semaphores are a technique for coordinating or synchronizing activities in which multiple processes compete for the same operating In Programming, Especially In Unix Systems, Semaphores Are A Technique For Coordinating Or Synchronizing Activities In Which Multiple processes Compete For The Same Operating System Resources. A Semaphore Is A Value In A Designated Place In Operating System (Or Kernel) Storage That Each Process Can Check And Then Change. Depending On The Value That Is Found, The Process Can Use The Resource Or Will Find That It Is Already In Use And Must Wait For Some Period Before Trying Again. Semaphores Can Be binary (0 Or 1) Or Can Have Additional Values.
- 156. COMPUTERFUNDAMENTALS Typically, A Process Using Semaphores Checks The Value And Then, If It Using The Resource, Changes The Value To Reflect This So That Subsequent Semaphore Users Will Know To Wait. Semaphores Are Commonly Used For Two Purposes: To Share A Common Memory Space And To Share Access To Files. Semaphores Are One Of The Techniques For Interprocess Communication (IPC). The C programming Language Provides a Set of Interfaces Or "Functions" For Managing Semaphores. 7.1.2.A.Semaphores
- 157. COMPUTERFUNDAMENTALS 7.1.3MESSAGE PASSING 7.1.3. A.Message Passing Model A Thread That Does A Msg send() To Another Thread (Which Could Be Within Another Process) Will Be Blocked Until The Target Thread Does A Msg receivev(), Processes The Message, And Executes A Msg reply(). If A Thread Executes A msg receive () Without a Previously Sent Message Pending, It Will Block until another Thread Executes a Msg send ().
- 158. COMPUTERFUNDAMENTALS The Message-Passing API Consists Of The Following Functions: Function Description Msg send( ) Send A Message And Block Until Reply. Msg receivev( ) Wait For A Message. Msg reply( ) Reply To A Message. Msg error( ) Reply Only With An Error Status. No Message Bytes Are Transferred. Msg ready( ) Read Additional Data From A Received Message. Msg write( ) Write Additional Data To A Reply Message. Msg info( ) Obtain Info On Received Message. Msg send pulse( ) Send Tiny, Non-Blocking Message (Pulse). Msg deliver event( ) Deliver An Event To A Client. Msg key data() A Message To Allow Security Checks. 7.1.4SCHEDULING ALGORITHMS We'll Discuss Four Major Scheduling Algorithms Here Which Are Following First Come First Serve (FCFS) Scheduling Shortest-Job-First (SJF) Scheduling Priority Scheduling Round Robin(RR) Scheduling Multilevel Queue Scheduling
- 159. COMPUTERFUNDAMENTALS 1. FIRST COME FIRST SERVE (FCFS) SCHEDULING Jobs Are Executed On First Come, First Serve Basis. Easy To Understand And Implement. Poor in Performance As Average Wait Time Is High. Wait Time of Each Process Is Following Process Wait Time : Service Time - Arrival Time P0 0 - 0 = 0 P1 5 - 1 = 4 P2 8 - 2 = 6 P3 16 - 3 = 13 Average Wait Time: (0+4+6+13) / 4 = 5.55
- 160. COMPUTERFUNDAMENTALS 2.SHORTESTJOBFIRST(SJF) 1) Best Approach To Minimize Waiting Time. 2) Impossible To Implement 3) Processer Should Know In Advance How Much Time Process Will Take. Wait Time of Each Process Is Following Process Wait Time : Service Time - Arrival Time P0 3 - 0 = 3 P1 0 - 0 = 0 P2 16 - 2 = 14 P3 8 - 3 = 5
- 161. COMPUTERFUNDAMENTALS Average Wait Time: (3+0+14+5) / 4 = 5.50 3. PRIORITYBASEDSCHEDULING Each Process Is Assigned A Priority. Process With Highest Priority Is To Be Executed First And So On. Processes With Same Priority Are Executed On First Come First Serve Basis. Priority Can Be Decided Based On Memory Requirements, Time Requirements Or Any Other Resource Requirement. Wait Time of Each Process Is Following Process Wait Time : Service Time - Arrival Time P0 9 - 0 = 9 P1 6 - 1 = 5 P2 14 - 2 = 12 P3 0 - 0 = 0 Average Wait Time: (9+5+12+0) / 4 = 6.5
- 162. COMPUTERFUNDAMENTALS 4.ROUNDROBINSCHEDULING Each Process Is Provided A Fix Time To Execute Called Quantum. Once A Process Is Executed For Given Time Period. Process Is Preempted And Other Process Executes For Given Time Period. Context Switching Is Used To Save States Of Preempted Processes. Wait Time of Each Process Is Following Process Wait Time : Service Time - Arrival Time P0 (0-0) + (12-3) = 9 P1 (3-1) = 2 P2 (6-2) + (14-9) + (20-17) = 12 P3 (9-3) + (17-12) = 11 Average Wait Time: (9+2+12+11) / 4 = 8.5
- 163. COMPUTERFUNDAMENTALS 4.MULTIQUEUESCHEDULING Multiple Queues Are Maintained For Processes. Each Queue Can Have Its Own Scheduling Algorithms. Priorities Are Assigned To Each Queue. Multi queue processing
- 164. COMPUTERFUNDAMENTALS Questions On Inter Process Communication 1) Inter Process Communication : A) Allows Processes To Communicate And Synchronize Their Actions When Using The Same Address Space. B) Allows Processes To Communicate And Synchronize Their Actions Without Using The Same Address Space. C) Allows The Processes To Only Synchronize Their Actions Without Communication. D) None of These ANSWER: B 2) Message Passing System Allows Processes To : A) Communicate With One Another Without Resorting To Shared Data. B) Communicate With One Another By Resorting To Shared Data. C) Share Data D) Name The Recipient Or Sender Of The Message ANSWER: A 3) An IPC Facility Provides At Least Two Operations: (Choose Two) A) Write Message B) Delete Message C) Send Message D) Receive Message ANSWER: C AND D 4) Messages Sent By A Process : A) Have To Be Of A Fixed Size B) Have To Be A Variable Size C) Can Be Fixed Or Variable Sized D) None Of These ANSWER: C
- 165. COMPUTERFUNDAMENTALS 5) The Link between Two Processes P and Q to Send and Receive Messages Is Called: A) Communication Link B) Message-Passing Link C) Synchronization Link D) All Of These ANSWER: A 6) Which Of The Following Are TRUE For Direct Communication Choose Two) A) A Communication Link Can Be Associated With N Number Of Process (N = Max. Number Of Processes Supported By System) B) A Communication Link Can Be Associated With Exactly Two Processes C) Exactly N/2 Links Exist Between Each Pair Of Processes (N = Max. Number Of Processes Supported By System) D) Exactly One Link Exists Between Each Pair Of Processes ANSWER: B AND D 7) In Indirect Communication Between Processes P And Q : A) There Is Another Process R To Handle And Pass On The Messages Between P And Q B) There Is Another Machine Between The Two Processes To Help Communication C) There Is A Mailbox To Help Communication Between P And Q D) None Of These ANSWER: C 8) In The Non-Blocking Send : A) The Sending Process Keeps Sending Until The Message Is Received B) The Sending Process Sends The Message And Resumes Operation C) The Sending Process Keeps Sending Until It Receives A Message D) None Of These ANSWER: B
- 166. COMPUTERFUNDAMENTALS 9) IN THE ZERO CAPACITY QUEUE : (CHOOSE TWO) A) The Queue Has Zero Capacity B) The Sender Blocks Until The Receiver Receives The Message C) The Sender Keeps Sending And The Messages Don’t Wait In The Queue D) The Queue Can Store At Least One Message ANSWER: A AND B 10) The Zero Capacity Queue : A) Is Referred To As A Message System With Buffering B) Is Referred To As A Message System With No Buffering C) Is Referred To As A Link D) None Of These ANSWER: B 11) Bounded Capacity And Unbounded Capacity Queues Are Referred To As : A) Programmed Buffering B) Automatic Buffering C) User Defined Buffering D) No Buffering ANSWER: B 12) Round Robin Scheduling Falls Under the Category of: A) Non Preemptive Scheduling B) Preemptive Scheduling C) None of These ANSWER: B 13) With Round Robin Scheduling Algorithm In A Time Shared SystemS, A) Using Very Large Time Slices Converts It Into First Come First Served Scheduling Algorithm B) Using Very Small Time Slices Converts It Into First Come First Served Scheduling Algorithm
- 167. COMPUTERFUNDAMENTALS C) Using Extremely Small Time Slices Increases Performance D) Using Very Small Time Slices Converts It Into Shortest Job First Algorithm ANSWER: A. Explanation: All The Processes Will Be Able To Get Completed. 14) The Portion Of The Process Scheduler In An Operating System That Dispatches Processes Is Concerned With : A) Assigning Ready Processes To CPU B) Assigning Ready Processes To Waiting Queue C) Assigning Running Processes To Blocked Queue D) All Of These ANSWER: A 15) Complex Scheduling Algorithms: A) Are Very Appropriate For Very LargeComputers B) Use Minimal Resources C) Use Many Resources D) All of These ANSWER: A Explanation: Large Computers Are Overloaded With Greater Number Of Processes. 16) The FIFO Algorithm : A) First Executes The Job That Came In Last In The Queue B) First Executes The Job That Came In First In The Queue C) First Executes The Job That Needs Minimal Processor D) First Executes The Job That Has Maximum Processor Needs ANSWER: B. 17) The Strategy Of Making Processes That Are Logically Runnable To Be Temporarily Suspended Is Called: A) Non Preemptive Scheduling B) Preemptive Scheduling C) Shortest Job First
- 168. COMPUTERFUNDAMENTALS D) First Come First Served ANSWER: B 18) Scheduling Is: A) Allowing A Job to Use the Processor B) Making Proper Use of Processor C) Both A and B D) None of These Answer: C 19) There Are 10 Different Processes Running On A Workstation. Idle Processes Are Waiting For An Input Event In The Input Queue. Busy Processes Are Scheduled With The Round-Robin Timesharing Method. Which Out Of The Following Quantum Times Is The Best Value For Small Response Times, If The Processes Have A Short Runtime, E.G. Less Than 10ms? A) TQ = 15ms B) TQ = 40ms C) TQ = 45ms D) TQ = 50ms ANSWER: A 20) Orders Are Processed In The Sequence They Arrive If _______ Rule Sequences The Jobs. A) Earliest Due Date B) Slack Time Remaining C) First Come, First Served D) Critical Ratio ANSWER: C
- 169. COMPUTERFUNDAMENTALS 21) Which Of The Following Algorithms Tends To Minimize The Process Flow Time ? A) First Come First Served B) Shortest Job First C) Earliest Deadline First D) Longest Job First ANSWER: B 22) Under Multiprogramming, Turnaround Time For Short Jobs Is Usually ________ And That For Long Jobs Is Slightly ___________. A) Lengthened; Shortened B) Shortened; Lengthened C) Shortened; Shortened D) Shortened; Unchanged ANSWER: B 23) Which Of The Following Statements Are True? I. Shortest Remaining Time First Scheduling May Cause Starvation II. Preemptive Scheduling May Cause Starvation III. Round Robin Is Better Than FCFS In Terms Of Response Time A) I Only B) I And III Only C) II And III Only D) I, II And III ANSWER: D Explanation: I) Shortest Remaining Time First Scheduling Is A Preemptive Version Of Shortest Job Scheduling. It May Cause Starvation As Shorter Processes May Keep Coming And A Long CPU Burst Process Never Gets CPU. II) Preemption May Cause Starvation. If Priority Based Scheduling With Preemption Is Used, Then A Low Priority Process May Never Get CPU. III) Round Robin Scheduling Improves Response Time As All Processes Get CPU After A Specified Time. 8. Deadlocks
- 170. COMPUTERFUNDAMENTALS 8. DEADLOCKS 8.1.1. DEFINITION OF DEADLOCK “A Deadlock Is A Situation In Which Two Computer Programs Sharing The Same Resource Are Effectively Preventing Each Other From Accessing The Resource, Resulting In Both Programs Ceasing To Function”. The Earliest Computer Operating Systems Ran Only One Program At A Time. All Of The Resources Of The System Were Available To This One Program. Later, Operating Systems Ran Multiple Programs At Once, Interleaving Them. Programs Were Required To Specify In Advance What Resources They Needed So That They Could Avoid Conflicts With Other Programs Running At The Same Time. Eventually Some Operating Systems Offered Dynamic Allocation of Resources. Programs Could Request Further Allocations Of Resources After They Had Begun Running. To define deadlock, first I would define process. Process: As we know process is nothing but a program in execution. Resource: To execute a program process needs some resources. Resource categories may include memory, printers, CPUs, open files, tape drives, CD-ROMS, etc. Deadlock : Deadlock is a situation or condition when two or more processes are holding some resources and trying to acquire some more resources, and they cannot release the resources until they finish there execution.
- 171. COMPUTERFUNDAMENTALS Deadlock condition or situation In the above diagram there are two process P1 and p2 and there are two resources R1 and R2. Resource R1 is allocated to process P1 and resource R2 is allocated to process p2. To complete execution of process P1 needs resource R2, so P1 request for R2, but R2 is already allocated to P2. In the same way Process P2 to complete its execution needs R1, but R1 is already allocated to P1. both the processes cannot release their resource until and unless the complete their execution. So both are waiting for other resources and they will wait forever. So this is a DEADLOCK Condition. 8.1.2. CHARACTERSTICS OF DEADLOCK In order for deadlock to occur, four conditions must be true. 1. Mutual exclusion - Each resource is either currently allocated to exactly one process or it is available. (Two processes cannot simultaneously control the same resource or be in their critical section). 2. Hold and Wait - processes currently holding resources can request new resources. 3. No preemption - Once a process holds a resource, it cannot be taken away by another process or the kernel. 4. Circular wait - Each process is waiting to obtain a resource which is held by another process. And all these condition are satisfied in above diagram.
- 172. COMPUTERFUNDAMENTALS 8.1.3. DEADLOCK’S PREVENTION You Have Already Seen What Deadlock Is And The Necessary Conditions For A Deadlock To Happen. We Can Try To Prevent Or Avoid Deadlock, And If That Doesn’t Work Out, We Should Detect Deadlock And Try To Recover From Deadlock. Deadlock Prevention Deadlock Prevention Algorithms Ensure That At Least One Of The Necessary Conditions (Mutual Exclusion, Hold And Wait, No Preemption And Circular Wait) Does Not Hold True. However Most Prevention Algorithms Have Poor Resource Utilization, And Hence Result In Reduced Throughputs. Mutual Exclusion Not Always Possible To Prevent Deadlock By Preventing Mutual Exclusion (Making All Resources Shareable) As Certain Resources Are Cannot Be Shared Safely. Hold and Wait We Will See Two Approaches, But Both Have Their Disadvantages. A Resource Can Get All Required Resources Before It Start Execution. This Will Avoid Deadlock, But Will Result In Reduced Throughputs As Resources Are Held By Processes Even When They Are Not Needed. They Could Have Been Used By Other Processes During This Time. Second Approach Is To Request For A Resource Only When It Is Not Holing Any Other Resource. This May Result In A Starvation As All Required Resources Might Not Be Available Freely Always. No Preemption We Will See Two Approaches Here. If A Process Request For A Resource Which Is Held By Another Waiting Resource, Then The Resource May Be Preempted From The Other Waiting Resource. In The Second Approach, If A Process Request For A Resource Which Are Not Readily Available, All Other Resources That It Holds Are Preempted. The Challenge Here Is That The Resources Can Be Preempted Only If We Can Save The Current State Can Be Saved And Processes Could Be Restarted Later From The Saved State.
- 173. COMPUTERFUNDAMENTALS Circular Wait To Avoid Circular Wait, Resources May Be Ordered And We Can Ensure That Each Process Can Request Resources Only In An Increasing Order Of These Numbers. The Algorithm May Itself Increase Complexity And May Also Lead To Poor Resource Utilization. Deadlock Avoidance Most Prevention Algorithms Have Poor Resource Utilization, And Hence Result In Reduced Throughputs. Instead, We Can Try To Avoid Deadlocks By Making Use Prior Knowledge About The Usage Of Resources By Processes Including Resources Available, Resources Allocated, Future Requests And Future Releases By Processes. Most Deadlock Avoidance Algorithms Need Every Process To Tell In Advance The Maximum Number Of Resources Of Each Type That It May Need. Based On All These Info We May Decide If A Process Should Wait For A Resource Or Not, And Thus Avoid Chances For Circular Wait. If A System Is Already In A Safe State, We Can Try To Stay Away From An Unsafe State And Avoid Deadlock. Deadlocks Cannot Be Avoided In An Unsafe State. A System Can Be Considered To Be In Safe State If It Is Not In A State Of Deadlock And Can Allocate Resources Up to The Maximum Available. A Safe Sequence Of Processes And Allocation Of Resources Ensures A Safe State. Deadlock Avoidance Algorithms Try Not To Allocate Resources To A Process If It Will Make The System In An Unsafe State. Since Resource Allocation Is Not Done Right Away In Some Cases, Deadlock Avoidance Algorithms Also Suffer From Low Resource Utilization Problem.
- 174. COMPUTERFUNDAMENTALS Consider The Image With Calm Edges As Below: If R2 Is Allocated To P2 And If P1 Request For R2, There Will Be A Deadlock. The Resource Allocation Graph Is Not Much Useful If There Are Multiple Instances For A Resource In Such A Case, We Can Use Banker’s Algorithm. In This Algorithm, Every Process Must Tell Upfront The Maximum Resource Of Each Type It Need, Subject To The Maximum Available Instances For Each Type. Allocation Of Resources Is Made Only, If The Allocation Ensures A Safe State; Else The Processes Need To Wait. The Banker’s Algorithm Can Be Divided Into Two Parts: Safety Algorithm If A System Is In A Safe State Or Not. The Resource Request Algorithm Make An Assumption Of Allocation And See If The System Will Be In A Safe State. If The New State Is Unsafe, The Resources Are Not Allocated And The Data Structures Are Restored To Their Previous State; In This Case The Processes Must Wait For The Resource. You Can Refer To Any Operating System Text Books For Details Of These Algorithms.
- 175. COMPUTERFUNDAMENTALS Deadlock Detection If Deadlock Prevention And Avoidance Are Not Done Properly, As Deadlock May Occur And Only Things Left To Do Is To Detect The Recover From The Deadlock. If All Resource Types Has Only Single Instance, Then We Can Use A Graph Called Wait-For-Graph, Which Is A Variant Of Resource Allocation Graph. Here, Vertices Represent Processes And A Directed Edge From P1 To P2 Indicate That P1 Is Waiting For A Resource Held By P2. Like In The Case Of Resource Allocation Graph, A Cycle In A Wait-For-Graph Indicate A Deadlock. So The System Can Maintain A Wait-For-Graph And Check For Cycles Periodically To Detect Any Deadlocks. The Wait-For-Graph Is Not Much Useful If There Are Multiple Instances For A Resource, As A Cycle May Not Imply A Deadlock. In Such A Case, We Can Use An Algorithm Similar To Banker’s Algorithm To Detect Deadlock. We Can See If Further Allocations Can Be Made On Not Based On Current Allocations. You Can Refer To Any Operating System Text Books For Details Of These Algorithms.
- 176. COMPUTERFUNDAMENTALS Deadlock Recovery Once A Deadlock Is Detected, You Will Have To Break The Deadlock. It Can Be Done Through Different Ways, Including, Aborting One Or More Processes To Break The Circular Wait Condition Causing The Deadlock And Preempting Resources From One Or More Processes Which Are Deadlocked. 8.1.4. Banker’s Algorithm This Approach To The Deadlock Problem Anticipates Deadlock Before It Actually Occurs. This Approach Employs An Algorithm To Access The Possibility That Deadlock Could Occur And Acting Accordingly. This Method Differs From Deadlock Prevention, Which Guarantees That Deadlock Cannot Occur By Denying One Of The Necessary Conditions Of Deadlock. If The Necessary Conditions For A Deadlock Are In Place, It Is Still Possible To Avoid Deadlock By Being Careful When Resources Are Allocated. Perhaps The Most Famous Deadlock Avoidance Algorithm, Due To DIJKSTRA [1965], Is The Banker’s Algorithm. So Named Because The Process Is Analogous To That Used By A Banker In Deciding If A Loan Can Be Safely Made. Banker’s Algorithm In This Analogy Customers ≡ Processes Units ≡ Resources, Say, Tape Drive Banker ≡ Operating System
- 177. COMPUTERFUNDAMENTALS Customers Used Max A B C D 0 0 0 0 6 5 4 7 Available Units = 10 Fig. 1 In The Above Figure, We See Four Customers Each Of Whom Has Been Granted A Number Of Credit Nits. The Banker Reserved Only 10 Units Rather Than 22 Units To Service Them. At Certain Moment, The Situation Becomes Customers Used Max A B C D 1 1 2 4 6 5 4 7 Available Units = 2 Fig. 2 Safe State The Key To A State Being Safe Is That There Is At Least One Way For All Users To Finish. In Other Analogy, The State of Figure 2 Is Safe Because with 2 Units Left, The Banker Can Delay Any Request Excerpt’s, Thus Letting C Finish And Release All Four Resources. With Four Units In Hand, The Banker Can Let Either D Or B Have The Necessary Units And So On.
- 178. COMPUTERFUNDAMENTALS Unsafe State Consider What Would Happen If A Request From B For One More Unit Were Granted In Above Figure 2. We Would Have Following Situation Customers Used Max A B C D 1 2 2 4 6 5 4 7 Available Units = 1 Fig. 3 This Is An Unsafe State. If All The Customers Namely A, B, C, And D Asked For Their Maximum Loans, Then Banker Could Not Satisfy Any Of Them And We Would Have A Deadlock.
- 179. COMPUTERFUNDAMENTALS Questions on dead locks 1. What Is The Reusable Resource? A) That Can Be Used By One Process At A Time And Is Not Depleted By That Use B) That Can Be Used By More Than One Process At A Time C) That Can Be Shared Between Various Threads D) None Of The Mentioned ANSWER: A 2. Which Of The Following Condition Is Required For Deadlock To Be Possible? A) Mutual Exclusion B) A Process May Hold Allocated Resources While Awaiting Assignment Of Other Resources C) No Resource Can Be Forcibly Removed From A Process Holding It D) All Of The Mentioned ANSWER: D 3. A System Is In The Safe State If A) The System Can Allocate Resources To Each Process In Some Order And Still Avoid A Deadlock B) There Exist A Safe Sequence C) Both (A) And (B) D) None Of The Mentioned ANSWER: C 4. The Circular Wait Condition Can Be Prevented By A) Defining A Linear Ordering Of Resource Types B) Using Thread C) Using Pipes D) All Of The Mentioned ANSWER: A
- 180. COMPUTERFUNDAMENTALS 5. Which One Of The Following Is The Deadlock Avoidance Algorithm? A) Banker’s Algorithm B) Round-Robin Algorithm C) Elevator Algorithm D) Kern’s Algorithm ANSWER: A 6. What Is the Drawback of Banker’s Algorithm? A) In Advance Processes Rarely Know That How Much Resource They Will Need B) The Number Of Processes Changes As Time Progresses C) Resource Once Available Can Disappear d) all of the mentioned ANSWER: D 7. For Effective Operating System, When to Check For Deadlock? A) Every Time A Resource Request Is Made B) At Fixed Time Intervals C) Both (A) And (B) D) None Of The Mentioned ANSWER: C 8. A Problem Encountered In Multitasking When A Process Is Perpetually Denied Necessary Resources Is Called A) Deadlock B) Starvation C) Inversion D) Aging ANSWER: B
- 181. COMPUTERFUNDAMENTALS 9. Which One Of The Following Is A Visual ( Mathematical ) Way To Determine The deadlock Occurrence? A) Resource Allocation Graph B) Starvation Graph C) Inversion Graph D) None of the Mentioned ANSWER: A 10. To Avoid Deadlock A) There Must Be A Fixed Number Of Resources To Allocate B) Resource Allocation Must Be Done Only Once C) All Deadlocked Processes Must Be Aborted D) Inversion Technique Can Be Used ANSWER: A
- 182. COMPUTERFUNDAMENTALS 9. MEMORY MANAGEMENT 9.1. 1BASIC MEMORY MANAGEMENT Memory Management Is The Functionality Of An Operating System Which Handles Or Manages Primary Memory. Memory Management Keeps Track Of Each And Every Memory Location either It Is Allocated To Some Process or It Is Free. It Checks How Much Memory Is To Be Allocated To Processes. It Decides Which Process Will Get Memory At What Time. It Tracks Whenever Some Memory Gets Freed Or Unallocated And Correspondingly It Updates The Status. Memory Management Provides Protection By Using Two Registers, A Base Register And A Limit Register. The Base Register Holds The Smallest Legal Physical Memory Address And The Limit Register Specifies The Size Of The Range. For Example, If The Base Register Holds 300000 And The Limit Register Is 1209000, Then The Program Can Legally Access All Addresses From 300000 Through 411999. 9.1. A.Memory Management Unit
- 183. COMPUTERFUNDAMENTALS 9.1.2. Defination “Memory Management Is The Process Of Controlling And Coordinating Computer Memory, Assigning Portions Called Blocks To Various Running Programs To Optimize Overall System Performance. Memory Management Resides In Hardware, In The OS (Operating System), And In Programs And Applications”. In Hardware, Memory Management Involves Components That Physically Store Data, Such As RAM (Random Access Memory) Chips, Memory Caches, And Flash- Based SSDS (Solid-State Drives). In The OS, Memory Management Involves The Allocation (And Constant Reallocation) Of Specific Memory Blocks To Individual Programs As User Demands Change. At The Application Level, Memory Management Ensures The Availability Of Adequate Memory For The Objects And Data Structures Of Each Running Program At All Times. Application Memory Management Combines Two Related Tasks, Known As Allocation And Recycling. When The Program Requests A Block Of Memory, A Part Of The Memory Manager Called The Allocator Assigns That Block To The Program. When A Program No Longer Needs The Data In Previously Allocated Memory Blocks, Those Blocks Become Available For Reassignment. This Task Can Be Done Manually (By the Programmer) or Automatically (By The Memory Manager). 9.1.2. A. I/O Memory Management
- 184. COMPUTERFUNDAMENTALS 9.1.3. LOGICAL &PHYSICAL ADDRESS MAP Logical Vs. Physical Address Space An Address Generated By The CPU Is Commonly Referred To As A Logical A Logical Address. The Set Of All Logical Addresses Generated By A Program Is Known As Logical Address Space. Whereas, An Address Seen By The Memory Unit- That Is, The One Loaded Into The Memory-Address Register Of The Memory- Is Commonly Referred To As Physical Address. The Set Of All Physical Addresses Corresponding To The Logical Addresses Is Known As Physical Address Space. The Compile-Time And Load-Time Address-Binding Methods Generate Identical Logical And Physical Addresses. However, In The Execution-Time Address-Binding Scheme, The Logical And Physical-Address Spaces Differ. The User Program Never Sees The Physical Addresses. The Program Creates A Pointer To A Logical Address, Say 346, Stores It In Memory, Manipulate It, and Compares It To Other Logical Addresses- All As The Number 346. Only When A Logical Address Is Used As Memory Address, It Is Relocated Relative To The Base/Relocation Register. The Memory-Mapping Hardware Device Called The Memory- Management Unit (MMU) Converts Logical Addresses Into Physical Addresses. Logical Addresses Range from 0 To Max. User Program That Generates Logical Address Thinks That The Process Runs In Locations 0 To Max. Logical Addresses Must Be Mapped To Physical Addresses Before They Are Used. Physical Addresses Range from (R+0) To (R + Max) For A Base/Relocation Register Value R. Example:
- 185. COMPUTERFUNDAMENTALS Mapping From Logical To Physical Addresses Using Memory Management Unit (Mmu) And Relocation/Base Register The Value In Relocation/Base Register Is Added To Every Logical Address Generated By A User Process, At The Time It Is Sent To Memory, To Generate Corresponding Physical Address. In The Above Figure, Base/ Relocation Value Is 14000, Then An Attempt By The User To Access The Location 346 Is Mapped To 14346. 9.1.4. CONTINUOUS MEMORY ALLOCATION Definition - What Does Contiguous Memory Allocation Mean? Contiguous Memory Allocation Is A Classical Memory Allocation Model That Assigns A Process Consecutive Memory Blocks (That Is, Memory Blocks Having Consecutive Addresses). Contiguous Memory Allocation Is One Of The Oldest Memory Allocation Schemes. When A Process Needs To Execute, Memory Is Requested By The Process. The Size Of The Process Is Compared With The Amount Of Contiguous Main Memory Available To Execute The Process. If Sufficient Contiguous Memory Is Found, The Process Is Allocated Memory To Start Its Execution. Otherwise, It Is Added To A Queue Of Waiting Processes Until Sufficient Free Contiguous Memory Is Available. Explanation of Memory Allocation The Contiguous Memory Allocation Scheme Can Be Implemented In Operating Systems With The Help Of Two Registers, Known As The Base And Limit Registers. When A Process Is Executing In Main Memory, Its Base Register Contains The Starting Address Of The Memory Location Where The Process Is Executing, While The Amount Of Bytes Consumed By The Process Is Stored In The Limit Register. A Process Does Not Directly Refer To The Actual Address For A Corresponding Memory Location. Instead, It Uses A Relative Address With Respect To Its Base Register. All Addresses Referred By A Program Are Considered As Virtual Addresses. The CPU Generates The Logical Or Virtual Address, Which Is Converted Into An Actual
- 186. COMPUTERFUNDAMENTALS Address With The Help Of The Memory Management Unit (MMU). The Base Address Register Is Used For Address Translation By The MMU. Thus, A Physical Address Is Calculated As Follows: Physical Address = Base Register Address + Logical Address/Virtual Address The Address Of Any Memory Location Referenced By A Process Is Checked To Ensure That It Does Not Refer To An Address Of A Neighboring Process. This Processing Security Is Handled By The Underlying Operating System. One Disadvantage Of Contiguous Memory Allocation Is That The Degree Of Multiprogramming Is Reduced Due To Processes Waiting For Free Memory. Main memory organization
- 187. COMPUTERFUNDAMENTALS Fixed &Variable Size Partitions By Using Fixed Variable Size Partitions We Can Overcome The Disadvantages Present In Fixed Equal Size Partitioning. This Is Shown In The Figure Below: With Unequal-Size Partitions, There Are Two Ways To Assign Processes To Partitions. Use Multiple Queues: - For Each And Every Process One Queue Is Present, As Shown In The Figure Below. Assign Each Process To The Smallest Partition Within Which It Will Fit, By Using The Scheduling Queues, I.E., When A New Process Is To Arrive It Will Put In The Queue It Is Able To Fit Without Wasting The Memory Space, Irrespective Of Other Blocks Queues.
- 188. COMPUTERFUNDAMENTALS Advantages o Minimize Wastage Of Memory. Disadvantages o This Scheme Is Optimum From The System Point Of View. Because Larger Partitions Remains Unused. Use Single Queue:- In This Method Only One Ready Queue Is Present For Scheduling The Jobs For All The Blocks Irrespective Of Size. If Any Block Is Free Even Though It Is Larger Than The Process, It Will Simply Join Instead Of Waiting For The Suitable Block Size. It Is Depicted In The Figure Below: Advantages o It Is Simple And Minimum Processing Overhead. Disadvantages o The Number Of Partitions Specified At The Time Of System Generation Limits The Number Of Active Processes. o Small Jobs Do Not Use Partition Space Efficiently.
- 189. COMPUTERFUNDAMENTALS VARIABLE PARTITION MULTIPROGRAMMING Given That Memory Is A Highly Desirable Resource, Multiple Fixed Partitions Isn’t A Desirable Approach Due To Internal Fragmentation (Programs Are Rarely A Perfect Match For The Partitions They Go Into, Leading To Wasted Memory) And Due To The Problem Of Deciding What Partition Sizes To Create (Lots Of Small Partitions? A Few Small And A Few Medium Sized Ones? A Couple Of Big Partitions?). An Improvement Over Multiple Fixed Partitions Is Variable Partition Multiprogramming, Where Partitions Are Created Dynamically As They Are Needed And To The Size Needed. Figure 1. Variable Figure 2. Holes in Variable Partition Multiprogramming
- 190. COMPUTERFUNDAMENTALS Consider the Example in Figure 5 As New Processes Get Created, The Operating System Allocates Each Process Into Available Memory And Is Given The Exact Amount Of Memory Required By The Process. As Processes Exit (Figure 6), They Create Holes: Regions Of Free Memory. When New Processes Get Created, The Operating System Tries To Fit A Process Into An Available Hole. If A Fit Is Found, It Is Unlikely That The New Process Will Be The Exact Same Size As The Previous One (And It Cannot Be Bigger), So A Smaller Hole Will Be Left. We Can Combine The Holes (Unused Memory) By Relocating Processes Down (Move Process 2 To The Top Of Process 0 And Then Move Process 4 To The Top Of The Relocated Process 2). This Is Known As Memory Compaction And Is Usually Not Done Because It Takes Up Too Much CPU Time. 9.1.6. INTERNAL VS EXTERNAL FRAGMENTATION Difference Between Internal And External Fragmentation Is A Topic Of Interest To Many Who Like To Improve Their Computer Knowledge. Before Knowing This Difference, We Have To See What Fragmentation Is. Fragmentation Is A Phenomenon That Occurs In Computer Memory Such As Random Access Memory (RAM) Or Hard Disks, Which Causes Wastage And Inefficient Usage Of Free Space. While The Efficient Usage Of Available Space Is Hindered, This Causes Performance Issues, As Well.
- 191. COMPUTERFUNDAMENTALS Internal Fragmentation Occurs When Memory Allocation Is Based On Fixed-Size Partitions Where After A Small Size Application Is Assigned To A Slot The Remaining Free Space Of That Slot Is Wasted. External Fragmentation Occurs When Memory Is Dynamically Allocated Where After Loading And Unloading Of Several Slots Here And There The Free Space Is Being Distributed Rather Than Being Contiguous. What Is Internal Fragmentation? Consider The Figure Above Where A Fixed Sized Memory Allocation Mechanism Is Being Followed. Initially, The Memory Is Empty and the Allocator Has Divided the Memory into Fixed Size Partitions. Then Later Three Programs Named A, B, C Have Been Loaded To The First Three Partitions While The 4th Partition Is Still Free. Program A Matches The Size Of The Partition, So There Is No Wastage In That Partition, But Program B And Program C Are Smaller Than The Partition Size.
- 192. COMPUTERFUNDAMENTALS So In Partition 2 And Partition 3 There Is Remaining Free Space. However, This Free Space Is Unusable As The Memory Allocator Only Assigns Full Partitions To Programs But No T Parts Of It. This Wastage Of Free Space Is Called Internal Fragmentation. In The Above Example, It Is Equal Sized Fixed Partitions But This Can Even Happen In A Situation Where Partitions Of Various Fixed Sizes Are Available. Usually The Memory Or Hardest Space Is Divided Into Blocks That Are Usually The Size Of Powers Of 2 Such As 2, 4, 8, 16 Bytes. So A Program Or A File Of 3 Bytes Will Be Assigned To A 4 Byte Block But One Byte Of That Block Will Become Unusable Causing Internal Fragmentation. What Is External Fragmentation? Consider The Figure Above Where Memory Allocation Is Done Dynamically. In Dynamic Memory Allocation, The Allocator Allocates Only The Exact Needed Size For That Program. First Memory Is Completely Free. Then The Programs A, B, C, D and E Of Different Sizes Are Loaded One After The Other And They Are Placed In Memory Contiguously In That Order. Then Later, Program A and Program C Closes And They Are Unloaded From Memory.
- 193. COMPUTERFUNDAMENTALS Now There Are Three Free Space Areas In The Memory, But They Are Not Adjacent. Now A Large Program Called Program F Is Going To Be Loaded But Neither Of The Free Space Block Is Not Enough For Program F. The Addition Of All The Free Spaces Is Definitely Enough For Program F, But Due To The Lack Of Adjacency That Space Is Unusable For Program F. This Is Called External Fragmentation. What Is The Difference Between Internal And External Fragmentation? Internal Fragmentation Occurs When A Fixed Size Memory Allocation Technique Is Used. External Fragmentation Occurs When A Dynamic Memory Allocation Technique Is Used. Internal Fragmentation Occurs When A Fixed Size Partition Is Assigned To A Program/File With Less Size Than The Partition Making The Rest Of The Space In That Partition Unusable. External Fragmentation Is Due To The Lack Of Enough Adjacent Space After Loading And Unloading Of Programs Or Files For Some Time Because Then All Free Space Is Distributed Here And There. External Fragmentation Can Be Mined By Compaction Where The Assigned Blocks Are Moved To One Side, So That Contiguous Space Is Gained. However, This Operation Takes Time And Also Certain Critical Assigned Areas For Example System Services Cannot Be Moved Safely. We Can Observe This Compaction Step Done On Hard Disks When Running The Disk Defragmenter In Windows. External Fragmentation Can Be Prevented By Mechanisms Such As Segmentation And Paging. Here A Logical Contiguous Virtual Memory Space Is Given While In Reality The Files/Programs Are Spitted Into Parts And Placed Here And There.
- 194. COMPUTERFUNDAMENTALS Internal Fragmentation Can Be Maimed By Having Partitions Of Several Sizes And Assigning A Program Based On The Best Fit. However, Still Internal Fragmentation Is Not Fully Eliminated. 9.1.7. PAGING: PRINCIPLE OF OPERATION External Fragmentation Is Avoided By Using Paging Technique. Paging Is A Technique In Which Physical Memory Is Broken Into Blocks Of The Same Size Called Pages (Size Is Power Of 2, Between 512 Bytes And 8192 Bytes). When A Process Is To Be Executed, its Corresponding Pages Are Loaded Into Any Available Memory Frames. Logical Address Space Of A Process Can Be Non-Contiguous And A Process Is Allocated Physical Memory Whenever The Free Memory Frame Is Available. Operating System Keeps Track Of All Free Frames. Operating System Needs N Free Frames To Run A Program Of Size N Pages. Address Generated By CPU Is Divided Into Page Number (P) -- Page Number Is Used As An Index Into A Page Table Which Contains Base Address Of Each Page In Physical Memory. Page Offset (D) -- Page Offset Is Combined With Base Address To Define The Physical Memory Address.
- 195. COMPUTERFUNDAMENTALS 9.1.8. PAGE ALLOCATION 9.1.7. A.Paging mechanism With 4 Kb Pages (Figure 9.1.7.A), A 2-Level Page Table Hierarchy Is Used. The Cr3 Register Points To The Top-Level Table, Called The Page Directory. It Contains 1024 Page Directory Entries (PDES) And Is Indexed By The Top 10 Bits Of The Linear Address. Each Page Directory Entry Contains The Base Address Of A Partial Page Table That Is Indexed By The Next 10 Bits Of The Linear Address. This Table Contains The Page Table Entry (PTE) That Contains The Top 20 Bits Of The Physical Address. The Bottom 12 Bits Are Obtained From The Linear (Virtual) Address And Are The Offset Into The Page Frame.
- 196. COMPUTERFUNDAMENTALS 9.1.7. B. 32bit paging with 4 KB Pages With 4 Mb Pages (Figure 9.1.7.C), A Single Paging Table Is Used. The Cr3 Points to the Page Table, Which Contains 1024 Entries and Is Indexed By the Top 10 Bits of the Linear Address. Each Entry In The Page Directory Contains The Page Table Entry, Which Contains The Top 18 Bits Of A 40 Bit Physical Address. The Bottom 22 Bits Are The Obtained Directly From The Linear Address And Are The Offset Into A 4 Mb Page Frame. 9.1.7. C. 32bitpaging with 4MB Pages
- 197. COMPUTERFUNDAMENTALS 9.1.9. HARDWARE SUPPORT FOR PAGING To Implement Paging, The Simplest Method Is To Implement The Page Table As A Set Of Registers However, The Size Of Register Is Limited And The Size Of Page Table Is Usually Large Therefore, The Page Table Is Kept In Main Memory If We Want To Access Location I, We Must First Index Into Page Table, This Requires One Memory Access With This Scheme, TWO Memory Access Are Needed To Access A Byte The Standard Solution Is To Use A Special, Small, Fast Cache, Called Translation Look-Aside Buffer (TLB) Or Associative Memory TLB If The Page Number Is Not In The TLB (TLB Miss) A Memory Reference To The Page Table Must Be Made. In Addition, We Add the Page Number and Frame Number into TLB If The TLB Already Full, the OS Have To Must Select One for Replacement Some TLBS Allow Entries to Be Wire Down, Meaning That They Cannot Be Removed From the TLB, For Example Kernel Codes The Percentage of Times That A Particular Page Number Is Found In the TLN Is Called Hit Ratio If It Takes 20 Nanosecond to Search the TLB And 100 Nanosecond to Access Memory If Our Hit Ratio Is 80%, The Effective Memory Access Time Equal: 0.8*(100+20) + 0.2 *(100+100) =140 If Our Hit Ratio Is 98%, The Effective Memory Access Time Equal: 0.98*(100+20) + 0.02 *(100+100) =122
- 198. COMPUTERFUNDAMENTALS 9.1.10. PROTECTION AND SHARING Requirements of Protection Processes Should Not Be Able To Reference Memory Locations In Another Process Without Permission Impossible To Check Absolute Addresses At Compile Time Must Be Checked At Run Time Requirements: Sharing Allow several processes to access the same portion of memory • Better to allow each process access to the same copy of the program rather than have their own separate copy
- 199. COMPUTERFUNDAMENTALS 9.1.11DISADVANTAGES OF PAGING Advantages of Paging The Advantages Of Paging Are, In Address Translation Where Each Task Has The Same Virtual Address. Address Translation Will Turn Fragmented Physical Addresses Into Contiguous Virtual Addresses. It Provides Memory Protection (Buggy Or Malicious Tasks Can’t Harm Each Other Or The Kernel) And Shared Memory Between Tasks That A Fast Type Of IPC, Also Conserves Memory When Used For Dlls). It Helps In Demand Loading Which Prevents Big Load On CPU When A Task First Starts Running, Conserves Memory. Paging Requires Memory Mapped Files, Virtual Memory Swapping Which Let System Degrade Gracefully When Memory Required Exceeds RAM Size. The Process Can Be Run Whose Virtual Address Space Is Larger Than Physical Memory. It Is Flexibly In Sharing Machine Between Processes, Which Address Sizes Exceed The Physical Memory Size. It Also Supports A Wide Range Of User Level Stuff. Disadvantages of Paging The Disadvantages Of Paging Are Extra Resource Consumption, Memory Overhead For Storing Page Tables. The Worst Cases Are When Page Table May Take Up A Significant Portion Of Virtual Memory. Solution Is To Page The Page Table Or Go To A More Complicated Data Structure For Translations. Other Disadvantage Is Translation Overhead.
- 200. COMPUTERFUNDAMENTALS Questions on Memory Management 1. CPU fetches the instruction from memory according to the value of a) program counter b) status register c) instruction register d) program status word ANSWER: A 2. A memory buffer used to accommodate a speed differential is called a) stack pointer b) cache c) accumulator d) disk buffer ANSWER: B 3. Which one of the following is the address generated by CPU? a) Physical address b) absolute address c) logical address d) none of the mentioned ANSWER: C 4. Run time mapping from virtual to physical address is done by a) memory management unit b) CPU c) PCI d) none of the mentioned ANSWER: A 5. Memory management technique in which system stores and retrieves data from secondary storage for use in main memory is called a) fragmentation b) paging c) mapping
- 201. COMPUTERFUNDAMENTALS d) none of the mentioned ANSWER: B 6. The address of a page table in memory is pointed by a) stack pointer b) page table base register c) page register d) program counter ANSWER: B 7. Program always deals with a) logical address b) absolute address c) physical address d) relative address ANSWER: A 8. The page table contains a) base address of each page in physical memory b) page offset c) page size d) none of the mentioned ANSWER: A 9. What is compaction? a) a technique for overcoming internal fragmentation b) a paging technique c) a technique for overcoming external fragmentation d) a technique for overcoming fatal error ANSWER: C
- 202. COMPUTERFUNDAMENTALS 10. Operating System maintains the page table for a) each process b) each thread c) each instruction d) each address ANSWER: A 11) Physical Memory Is Broken Into Fixed-Sized Blocks Called ________. A) Frames B) Pages C) Backing Store D) None Of These ANSWER: A 12) Logical Memory Is Broken Into Blocks Of The Same Size Called _________. A) Frames B) Pages C) Backing Store D) None Of These ANSWER: B 13) Every Address Generated By The CPU Is Divided Into Two Parts : (Choose Two) A) Frame Bit B) Page Number C) Page Offset D) Frame Offset ANSWER: B AND C
- 203. COMPUTERFUNDAMENTALS 14) The __________ Is Used As An Index Into The Page Table. A) Frame Bit B) Page Number C) Page Offset D) Frame Offset ANSWER: B 15) The _____ Table Contains The Base Address Of Each Page In Physical Memory. A) Process B) Memory C) Page D) Frame ANSWER: C. 16) The Size Of A Page Is Typically : A) Varied B) Power Of 2 C) Power Of 4 D) None Of These ANSWER: B 17) If The Size Of Logical Address Space Is 2 To The Power Of M, And A Page Size Is 2 To The Power Of N Addressing Units, Then The High Order _____ Bits Of A Logical Address designate The Page Number, And The ____ Low Order Bits Designate The Page Offset. A) M, N B) N, M C) M – N, M D) M – N, N ANSWER: D
- 204. COMPUTERFUNDAMENTALS 18) With Paging There Is No ________ Fragmentation. A) Internal B) External C) Either Type Of D) None of These ANSWER: B 19) The Operating System Maintains A ______ Table That Keeps Track Of How Many Frames Have Been Allocated, How Many Are There, And How Many Are Available. A) Page B) Mapping C) Frame D) Memory ANSWER: C 20) Paging Increases The ______ Time. A) Waiting B) Execution C) Context – Switch D) All Of These ANSWER: C 21) Smaller Page Tables Are Implemented As A Set Of _______. A) Queues B) Stacks C) Counters D) Registers ANSWER: D. 22) The Page Table Registers Should Be Built With _______. A) Very Low Speed Logic B) Very High Speed Logic
- 205. COMPUTERFUNDAMENTALS C) A Large Memory Space D) None Of These ANSWER: B 23) For Larger Page Tables, They Are Kept In Main Memory And A __________ Points To The Page Table. A) Page Table Base Register B) Page Table Base Pointer C) Page Table Register Pointer D) Page Table Base ANSWER: A 24) For Every Process There Is A __________. A) Page Table B) Copy Of Page Table C) Pointer to Page Table D) All of These ANSWER: A 25) Time Taken In Memory Access Through PTBR Is : A) Extended By A Factor Of 3 B) Extended By A Factor Of 2 C) Slowed By A Factor Of 3 D) Slowed By A Factor Of 2 ANSWER: D 21) In Segmentation, Each Address Is Specified By: A) A Segment Number B) an Offset C) A Value
- 206. COMPUTERFUNDAMENTALS D) A Key ANSWER: A AND B 22) In Paging The User Provides Only ________, Which Is Partitioned By The Hardware Into ________ And ______. A) One Address, Page Number, Offset B) One Offset, Page Number, Address C) Page Number, Offset, Address D) None Of These ANSWER: A 23) Each Entry in A Segment Table Has A : A) Segment Base B) Segment Peak C) Segment Limit D) Segment Value ANSWER: A AND C 24) The Segment Base Contains The : A) Starting Logical Address Of The Process B) Starting Physical Address Of The Segment In Memory C) Segment Length D) None Of These ANSWER: B 25) The Segment Limit Contains The : A) Starting Logical Address Of The Process B) Starting Physical Address Of The Segment In Memory C) Segment Length D) None Of These ANSWER: C
- 207. COMPUTERFUNDAMENTALS 9.2. VIRTUAL MEMORY Virtual Memory Is A Technique That Allows The Execution Of Processes Which Are Not Completely Available In Memory. The Main Visible Advantage Of This Scheme Is That Programs Can Be Larger Than Physical Memory. Virtual Memory Is The Separation Of User Logical Memory From Physical Memory. This Separation Allows An Extremely Large Virtual Memory To Be Provided For Programmers When Only A Smaller Physical Memory Is Available. Following Are The Situations, When Entire Program Is Not Required To Be Loaded Fully In Main Memory. User Written Error Handling Routines Are Used Only When An Error Occurred In The Data Or Computation. Certain Options And Features Of A Program May Be Used Rarely. Many Tables Are Assigned A Fixed Amount Of Address Space Even Though Only A Small Amount Of The Table Is Actually Used. The Ability To Execute A Program That Is Only Partially In Memory Would Counter Many Benefits. Less Number Of I/O Would Be Needed To Load Or Swap Each User Program Into Memory. A Program Would No Longer Be Constrained By The Amount Of Physical Memory That Is Available. Each User Program Could Take Less Physical Memory, More Programs Could Be Run the Same Time, With A Corresponding Increase In CPU Utilization And Throughput. Virtual Memory Is Commonly Implemented By Demand Paging. It Can Also Be Implemented In A Segmentation System. Demand Segmentation Can Also Be Used To Provide Virtual Memory.
- 208. COMPUTERFUNDAMENTALS 9.2. A. Virtual Memory 9.2.1.DEMANDPAGING A Demand Paging System Is Quite Similar To A Paging System With Swapping. When We Want To Execute A Process, We Swap It Into Memory. Rather Than Swapping The Entire Process Into Memory, However, We Use A Lazy Swapper Called Pager. When A Process Is To Be Swapped In, The Pager Guesses Which Pages Will Be Used Before The Process Is Swapped Out Again.
- 209. COMPUTERFUNDAMENTALS Instead Of Swapping In A Whole Process, The Pager Brings Only Those Necessary Pages Into Memory. Thus, It Avoids Reading Into Memory Pages That Will Not Be Used In Anyway, Decreasing The Swap Time And The Amount Of Physical Memory Needed. Hardware Support Is Required To Distinguish Between Those Pages That Are In Memory And Those Pages That Are On The Disk Using The Valid-Invalid Bit Scheme. Where Valid And Invalid Pages Can Be Checked By Checking The Bit. Marking A Page Will Have No Effect If The Process Never Attempts To Access The Page. While The Process Executes And Accesses Pages That Are Memory Resident, Execution Proceeds Normally. 9.2.1. A. Demand Paging Access To A Page Marked Invalid Causes A Page-Fault Trap. This Trap Is The Result Of The Operating System's Failure To Bring The Desired Page Into Memory. But Page Fault Can Be Handled As Following
- 210. COMPUTERFUNDAMENTALS 9.2.1. B. Shared Library Using Virtual Memory Step Description Step 1 Check An Internal Table For This Process, To Determine Whether The Reference Was A Valid Or It Was An Invalid Memory Access. Step 2 If The Reference Was Invalid, Terminate The Process. If It Was Valid, But Page Have Not Yet Brought In, Page In The Latter. Step 3 Find A Free Frame. Step 4 Schedule A Disk Operation To Read The Desired Page Into The Newly Allocated Frame. Step 5 When The Disk Read Is Complete, Modify The Internal Table Kept
- 211. COMPUTERFUNDAMENTALS With The Process And The Page Table To Indicate That The Page Is Now In Memory. Step 6 Restart The Instruction That Was Interrupted By The Illegal Address Trap. The Process Can Now Access The Page As Though It Had Always Been In Memory. Therefore, The Operating System Reads The Desired Page Into Memory And Restarts The Process As Though The Page Had Always Been In Memory. Advantages Following Are the Advantages of Demand Paging Large Virtual Memory. More Efficient Use of Memory. Unconstrained Multiprogramming. There Is No Limit On Degree Of Multiprogramming. Disadvantages Following Are the Disadvantages of Demand Paging Number Of Tables And Amount Of Processor Overhead For Handling Page Interrupts Are Greater Than In The Case Of The Simple Paged Management Techniques. Due to The Lack Of An Explicit Constraints On A Jobs Address Space Size. 9.2.2.PAGEREPLACEMENTALGORITHM Page Replacement Algorithms Are The Techniques Using Which Operating System Decides Which Memory Pages To Swap Out, Write To Disk When A Page Of Memory Needs To Be Allocated. Paging Happens Whenever A Page Fault Occurs And A Free Page Cannot Be Used For Allocation Purpose Accounting To Reason That Pages Are Not Available Or The Number Of Free Pages Is Lower Than Required Pages.
- 212. COMPUTERFUNDAMENTALS When The Page That Was Selected For Replacement And Was Paged Out, Is Referenced Again Then It Has To Read In From Disk, And This Requires For I/O Completion. This Process Determines The Quality Of The Page Replacement Algorithm: The Lesser The Time Waiting For Page-Ins, The Better Is The Algorithm. A Page Replacement Algorithm Looks At The Limited Information About Accessing The Pages Provided By Hardware, And Tries To Select Which Pages Should Be Replaced To Minimize The Total Number Of Page Misses, While Balancing It With The Costs Of Primary Storage And Processor Time Of The Algorithm Itself. There Are Many Different Page Replacement Algorithms. We Evaluate An Algorithm By Running It On A Particular String Of Memory Reference And Computing The Number Of Page Faults. 9.2.2.A. Pagereplacementalgorithm
- 213. COMPUTERFUNDAMENTALS 9.2.3.REFERENCESTRING The String Of Memory References Is Called Reference String. Reference Strings Are Generated Artificially Or By Tracing A Given System And Recording The Address Of Each Memory Reference. The Latter Choice Produces A Large Number Of Data, Where We Note Two Things. For A Given Page Size We Need To Consider Only The Page Number, Not The Entire Address. If We Have A Reference To A Page P, Then Any Immediately Following References To Page P Will Never Cause A Page Fault. Page P Will Be In Memory After The First Reference; The Immediately Following References Will Not Fault. For Example, Consider The Following Sequence Of Addresses - 123,215,600,1234,76,96 If Page Size Is 100 Then The Reference String Is 1,2,6,12,0,0 9.2.4.FIRSTINFIRSTOUT(FIFO)ALGORITHM Oldest Page In Main Memory Is The One Which Will Be Selected For Replacement. Easy To Implement, Keep A List, Replace Pages From The Tail And Add New Pages At The Head.
- 214. COMPUTERFUNDAMENTALS 9.2.5.LEAST RECENTLYUSED(LRU)ALGORITHM Page Which Has Not Been Used For The Longest Time In Main Memory Is The One Which Will Be Selected For Replacement. Easy To Implement, Keep A List, Replace Pages By Looking Back Into Time. 9.2.6.PAGEBUFFERINGALGORITHM To Get Process Start Quickly, Keep A Pool Of Free Frames. On Page Fault, Select A Page To Be Replaced. Write New Page In The Frame Of Free Pool, Mark The Page Table And Restart The Process. Now Write The Dirty Page Out Of Disk And Place The Frame Holding Replaced Page In Free Pool. 9.2.7.LEAST FREQUENTLYUSED(LFU)ALGORITHM Page With The Smallest Count Is The One Which Will Be Selected For Replacement. This Algorithm Suffers From The Situation In Which A Page Is Used Heavily During The Initial Phase Of A Process, But Then Is Never Used Again.
- 215. COMPUTERFUNDAMENTALS 9.2.8..MOSTFREQUENTLYUSED(MFU)ALGORITHM This Algorithm Is Based On The Argument That The Page With The Smallest Count Was Probably Just Brought In And Has Yet To Be Used. Questions on Virtual Memory 1. Because of virtual memory, the memory can be shared among a) processes b) threads c) instructions d) none of the mentioned View Answer ANSWER: A 2. _____ is the concept in which a process is copied into main memory from the secondary memory according to the requirement. a) Paging b) Demand paging c) Segmentation d) Swapping ANSWER: B. 3. The pager concerns with the a) individual page of a process b) entire process c) entire thread d) first page of a process View Answer ANSWER: A 4. Swap space exists in a) primary memory b) secondary memory c) CPU
- 216. COMPUTERFUNDAMENTALS d) none of the mentioned ANSWER: B 5. When a program tries to access a page that is mapped in address space but not loaded in physical memory, then a) segmentation fault occurs b) fatal error occurs c) page fault occurs d) no error occurs ANSWER: C 6. Effective access time is directly proportional to a) page-fault rate b) hit ratio c) memory access time d) none of the mentioned ANSWER: A 7. In FIFO page replacement algorithm, when a page must be replaced a) oldest page is chosen b) newest page is chosen c) random page is chosen d) none of the mentioned ANSWER: A 8. Which algorithm chooses the page that has not been used for the longest period of time whenever the page required to be replaced? a) first in first out algorithm b) additional reference bit algorithm c) least recently used algorithm d) counting based page replacement algorithm ANSWER: C
- 217. COMPUTERFUNDAMENTALS 9. A process is thrashing if a) it is spending more time paging than executing b) it is spending less time paging than executing c) page fault occurs d) swapping cannot take place ANSWER: A 10. Working set model for page replacement is based on the assumption of a) modularity b) locality c) globalization d) random access ANSWER: B 11) Which Of The Following Page Replacement Algorithms Suffers from Belay’s Anomaly? A) Optimal Replacement B) LRU C) FIFO D) both Optimal Replacement and FIFO ANSWER: C 12) A Process Refers To 5 Pages, A, B, C, D, E In The Order : A, B, C, D, A, B, E, A, B, C, D, E. If The Page Replacement Algorithm Is FIFO, The Number Of Page Transfers With An Empty Internal Store Of 3 Frames Is : A) 8 B) 10 C) 9 D) 7 ANSWER: C
- 218. COMPUTERFUNDAMENTALS 13) In Question 2, If the Number of Page Frames Is Increased To 4, Then the Number of Page Transfers: A) Decreases B) Increases C) Remains the Same D) None of These ANSWER: B 14) A Memory Page Containing A Heavily Used Variable That Was Initialized Very Early and Is In Constant Use Is Removed, Then the Page Replacement Algorithm Used Is: A) LRU B) LFU C) FIFO D) None of These ANSWER: C 15) A Virtual Memory System Uses First In First Out (FIFO) Page Replacement Policy And Allocates A Fixed Number Of Frames To A Process. Consider The Following Statements: P: Increasing The Number Of Page Frames Allocated To A Process Sometimes Increases The Page Fault Rate Q : Some Programs Do Not Exhibit Locality Of Reference Which Of The Following Is TRUE? A) Both P And Q Are True, And Q Is The Reason For P B) Both P And Q Are True, But Q Is Not The Reason For P C) P Is False But Q Is True D) Both P And Q Are False ANSWER: C 16) Users _______ That Their Processes Are Running On a Paged System. A) Are Aware B) Are Unaware
- 219. COMPUTERFUNDAMENTALS C) None of These ANSWER: B 17) If No Frames Are Free, _____ Page Transfer(S) Is/Are Required. A) One B) Two C) Three D) Four ANSWER: B 18) When A Page Is Selected For Replacement, and Its Modify Bit Is Set: A) The Page Is Clean B) the Page Has Been Modified Since It Was Read In From the Disk C) the Page Is Dirty D) A and B ANSWER: B AND C 19) The Aim of Creating Page Replacement Algorithms Is To: A) Replace Pages Faster B) Increase the Page Fault Rate C) Decrease the Page Fault Rate D) To Allocate Multiple Pages to Processes Answer: C 20) A FIFO Replacement Algorithm Associates With Each Page The _______ A) Time It Was Brought Into Memory B) Size Of The Page In Memory C) Page After And Before It D) All Of These ANSWER: A
- 220. COMPUTERFUNDAMENTALS 21) Optimal Page – Replacement Algorithm Is : A) Replace The Page That Has Not Been Used For A Long Time B) Replace The Page That Has Been Used For A Long Time C) Replace The Page That Will Not Be Used For A Long Time D) None Of These ANSWER: C 22) Optimal Page – Replacement Algorithm Is Difficult To Implement, Because : A) It Requires A Lot Of Information B) It Requires Future Knowledge Of The Reference String C) It Is Too Complex D) It Is Extremely Expensive ANSWER: B. 23) LRU Page – Replacement Algorithm Associates with Each Page The ______ A) Time It Was Brought into Memory B) The Time of That Page’s Last Use C) Page after and before It D) All of These ANSWER: B 24) For 3 Page Frames, The Following Is The Reference String: 7 0 1 2 0 3 0 4 2 3 0 3 2 1 2 0 1 7 0 1 I) How Many Page Faults Does The LRU Page Replacement Algorithm Produce? A) 10 B) 15 C) 11 D) 12 ANSWER: D
- 221. COMPUTERFUNDAMENTALS 10. I/OMANAGEMENT 10.1 I/O DEVICES Computers Operate On Many Kinds Of Devices. General Types Include Storage Devices (Disks, Tapes), Transmission Devices (Network Cards, Modems), and Human-Interface Devices (Screen, Keyboard, Mouse). Other Devices Are More Specialized. A Device Communicates With A Computer System By Sending Signals Over A Cable Or Even Through The Air. The Device Communicates With The Machine Via A Connection Point Termed A Port (For Example, A Serial Port). If One Or More Devices Use A Common Set Of Wires, The Connection Is Called A Bus. In Other Terms, A Bus Is A Set Of Wires And A Rigidly Defined Protocol That Specifies A Set Of Messages That Can Be Sent On The Wires. DaisyChain When Device A Has A Cable That Plugs Into Device B, And Device B Has A Cable That Plugs Into Device C, And Device C Plugs Into A Port On The Computer, This Arrangement Is Called A Daisy Chain. It Usually Operates As A Bus
- 222. COMPUTERFUNDAMENTALS 10.1. A.I/O. Devices Management 10.2 DEVICE CONTROLLERS A Controller Is A Collection Of Electronics That Can Operate A Port, A Bus, Or A Device. A Serial-Port Controller Is An Example Of A Simple Device Controller. This Is A Single Chip In The Computer That Controls The Signals On The Wires Of A Serial Port. The SCSI Bus Controller Is Often Implemented As A Separate Circuit Board (A Host Adapter) That Plugs Into The Computer. It Contains A Processor, Microcode, And Some Private Memory To Enable It To Process The SCSI Protocol Messages. Some Devices Have Their Own Built-In Controllers.
- 223. COMPUTERFUNDAMENTALS 10.2. A. A Serial-Port Controller Is an Example of a Simple Device Controller 10.2.B. A Serial-Port Controller
- 224. COMPUTERFUNDAMENTALS 10.2.1.I/OPORT An I/O Port Typically Consists of Four Registers, Called the Status, Control, Data-In, And data-Out Registers. S.N. Register & Description 1 Status Register The Status Register Contains Bits That Can Be Read By The Host. These Bits Indicate States Such As Whether The Current Command Has Completed, Whether A Byte Is Available To Be Read From The Data-In Register, And Whether There Has Been A Device Error. 2 Control Register The Control Register Can Be Written By The Host To Start A Command Or To Change The Mode Of A Device. For Instance, A Certain Bit In The Control Register Of A Serial Port Chooses Between Full-Duplex And Half-Duplex Communication, Another Enables Parity Checking, A Third Bit Sets The Word Length To 7 Or 8 Bits, And Other Bits Select One Of The Speeds Supported By The Serial Port. 3 Data-In Register The Data-In Register Is Read By The Host To Get Input. 4 Data-Out Register The Data Out Register Is Written By The Host To Send Output.
- 225. COMPUTERFUNDAMENTALS 10.2.1.A.I/OPort 10.2.2. POLLING Polling Is A Process By Which A Host Waits For Controller Response. It Is A Looping Process, Reading The Status Register Over And Over Until The Busy Bit Of Status Register Becomes Clear. The Controller Uses/Sets The Busy Bit When It Is Busy Working On A Command, And Clears The Busy Bit When It Is Ready To Accept The Next Command. The Host Signals Its Wish Via The Command-Ready Bit In The Command Register. The Host Sets The Command-Ready Bit When A Command Is Available For The Controller To Execute. In The Following Example, the Host Writes Output through a Port, Coordinating With the Controller by Handshaking
- 226. COMPUTERFUNDAMENTALS The Host Repeatedly Reads The Busy Bit Until That Bit Becomes Clear. The Host Sets The Write Bit In The Command Register And Writes A Byte Into The Data-Out Register. The Host Sets The Command-Ready Bit. When The Controller Notices That The Command-Ready Bit Is Set, It Sets The Busy Bit. The Controller Reads The Command Register And Sees The Write Command. It Reads The Data-Out Register To Get The Byte, And Does The I/O To The Device. The Controller Clears The Command-Ready Bit, Clears The Error Bit In The Status Register To Indicate That The Device I/O Succeeded, And Clears The Busy Bit To Indicate That It Is Finished. 10.2.2. A.Pollingcontainer
- 227. COMPUTERFUNDAMENTALS 10.2.3.I/ODEVICES I/O Devices Can Be Categorized Into Following Category. S.N. Category & Description 1 Human Readable Human Readable Devices Are Suitable For Communicating With The Computer User. Examples Are Printers, Video Display Terminals, Keyboard Etc. 2 Machine Readable Machine Readable Devices Are Suitable For Communicating With Electronic Equipment. Examples Are Disk And Tape Drives, Sensors, Controllers And Actuators. 2 Communication Communication Devices Are Suitable For Communicating With Remote Devices. Examples Are Digital Line Drivers And Modems. Following Are The Differences Between I/O Devices S.N. Criteria & Description 1 Data Rate There May Be Differences Of Several Orders Of Magnitude Between The Data Transfer Rates. 2 Application Different Devices Have Different Use In The System. 3 Complexity Of Control A Disk Is Much More Complex Whereas Printer Requires Simple Control Interface.
- 228. COMPUTERFUNDAMENTALS 4 Unit Of Transfer Data May Be Transferred As A Stream Of Bytes Or Characters Or In Larger Blocks. 5 Data Representation Different Data Encoding Schemes Are Used For Different Devices. 6 Error Conditions The Nature Of Errors Differs Widely From One Device To Another. 10.3DIRECT MEMORY ACCESS PRINCIPLES OF I/O SOFTWARE 10.3.A. DMA Architecture
- 229. COMPUTERFUNDAMENTALS Definition - What Does Direct Memory Access (DMA) Mean? Direct Memory Access (DMA) Is A Method That Allows An Input/output (I/O) Device To Send Or Receive Data Directly To Or From The Main Memory, Bypassing The CPU To Speed Up Memory Operations. The Process Is Managed By A Chip Known As A DMA Controller (DMAC). The DMA Request Line Is Used To Request A DMA Transfer. The Bus Request (BR) Signal Is Used By The DMA Controller To Request The CPU To Relinquish Control Of The Buses. The CPU Activates The Bus Grant (BG) Output To Inform The External DMA That Its Buses Are In A High-Impedance State (So That They Can Be Used In The DMA Transfer.) The Address Bus Is Used To Address The DMA Controller And Memory At Given Location The Device Select (DS) And Register Select (RS) Lines Are Activated By Addressing The DMA Controller. The RD And WR Lines Are Used To Specify Either A Read (RD) Or Write (WR) Operation On The Given Memory Location. The DMA Acknowledge Line Is Set When The System Is Ready To Initiate Data Transfer. The Data Bus Is Used To Transfer Data Between The I/O Device And Memory. When The Last Word Of Data In The DMA Transfer Is Transferred, The DMA Controller Informs The Termination Of The Transfer To The CPU By Means Of The Interrupt Line. Many Computers Avoid Burdening The Main CPU With Programmed I/O By Offloading Some Of This Work To A Special Purpose Processor. This Type Of Processor Is Called, A Direct Memory Access (DMA) Controller. A Special Control Unit Is Used To Transfer Block Of Data Directly Between An External Device And The Main Memory, Without Intervention By The Processor. This Approach Is Called Direct Memory Access (DMA). DMA Can Be Used With Either Polling Or Interrupt Software. DMA Is Particularly Useful On Devices Like Disks, Where Many Bytes Of Information Can Be Transferred
- 230. COMPUTERFUNDAMENTALS In Single I/O Operations. When Used With An Interrupt, The CPU Is Notified Only After The Entire Block Of Data Has Been Transferred. For Each Byte Or Word Transferred, It Must Provide The Memory Address And All The Bus Signals Controlling The Data Transfer. Interaction With A Device Controller Is Managed Through A Device Driver. Handshaking Is A Process Between The DMA Controller And The Device Controller. It Is Performed Via Wires Using Terms DMA Request And DMA Acknowledge. 10.4. Goals of Interrupt Handlers The CPU Hardware Uses An Interrupt Request Line Wire Which Helps CPU To Sense After Executing Every Instruction. When The CPU Checks That A Controller Has Put A Signal On The Interrupt Request Line, The CPU Saves A State, Such As The Current Value Of The Instruction Pointer, And Jumps To The Interrupt Handler Routine At A Fixed Address. The Interrupt Handler Part Determines The Cause Of The Interrupt, Performs The Necessary Processing And Executes A Interrupt Instruction To Return The CPU To Its Execution State. The Basic Mechanism Of Interrupt Enables The CPU To Respond To An Asynchronous Event, Such As When A Device Controller Become Ready For Service. Most CPUS Have Two Interrupt Request Lines. Non-Mask able Interrupt - Such Kind Of Interrupts Are Reserved for Events like Unrecoverable Memory Errors. Mask able Interrupt - Such Interrupts Can Be Switched off by the CPU before the Execution of Critical Instructions That Must Not Be Interrupted. The Interrupt Mechanism Accepts An Address - A Number That Selects A Specific Interrupt Handling Routine/Function From A Small Set. In Most Architecture, This Address Is An Offset Stored In A Table Called The Interrupt Vector Table. This Vector Contains The Memory Addresses Of Specialized Interrupt Handlers.
- 231. COMPUTERFUNDAMENTALS 10.4. A. Interrupt handler What Is A Non-Mask able Interrupt (NMI) And What Is Its Role? The Basic Idea Is That A Processor Can Mask Or Block Interrupt Requests To Have The Processor Perform A Task. A Processor Will Typically Not Do This Unless It Gets Really Bogged Down Or Busy. A Non-Mask able Interrupt Is Used For Very High Priority Tasks That You Don't Want The Processor To Be Able To Mask When It Gets Bogged Down. 10.4. A. Non Mask able Interrupt Handler
- 232. COMPUTERFUNDAMENTALS 10.5. DEVICE DRIVERS Device Driver Is A Program Or Routine Developed For An I/O Device. A Device Driver Implements I/O Operations Or Behaviors On A Specific Class Of Devices. For Example A System Supports One Or A Number Of Multiple Brands Of Terminals, All Slightly Different Terminals May Have A Single Terminal Driver. In The Layered Structure Of I/O System, Device Driver Lies Between Interrupt Handler And Device Independent I/O Software. The Job Of A Device Driver Are Following. To Accept Request From The Device Independent Software Above It. To See To It That The Request Is Executed. How A Device Driver Handles A Request Is As Follows: Suppose A Request Comes To Read A Block N. If The Driver Is Idle At The Time A Request Arrives, It Starts Carrying Out The Request Immediately. Otherwise, If The Driver Is Already Busy With Some Other Request, It Places The New Request In The Queue Of Pending Requests.
- 233. COMPUTERFUNDAMENTALS 10.6. SECONDARY-STORAGE STRUCTURE: Secondary Storage Is Mainly Consisting Of Following 1. Disk Structure 2. Disk Scheduling 3. Disk Management 4. Swap-Space Management 5. Disk Reliability 6. Stable-Storage Implementation 10.7.1.. DISK STRUCTURE 10.7. A. Disk structure
- 234. COMPUTERFUNDAMENTALS Disk Drives Are Addressed As Large 1-Dimensional Arrays Of Logical Blocks –The Logical Block Is The Smallest Unit Of Transfer. The 1-Dimensional Array Of Logical Blocks Is Mapped Into The Sectors Of The Disk Sequentially. –Sector 0 Is The First Sector Of The First Track On The Outermost Cylinder. Mapping Proceeds In Order Through That Track Then The Rest Of The Tracks In That Cylinder And Then through the Rest of the Cylinders from Outermost To Innermost. – Mapping Proceeds (Cylinder, Track, Sector) –In Practice, Not Always Possible Defective Sectors # Of Tracks Per Cylinders Is Not A Constant 10.7.2. DISK SCHEDULING The Operating System Is Responsible For Using Hardware Efficiently — For The Disk Drives, This Means Having A Fast Access Time And Disk Bandwidth. Access Time Has Two Major Components Seek Time Is The Time For The Disk Are To Move The Heads To The Cylinder Containing The Desired Sector. Rotational Latency Is The Additional Time Waiting For The Disk To Rotate The Desired Sector To The Disk Head. Minimize Seek Time Seek Time Seek Distance Disk Bandwidth Is The Total Number Of Bytes Transferred, Divided By The Total Time Between The First Request For Service And The Completion Of The Last Transfer. Several Algorithms Exist To Schedule The Servicing Of Disk I/O Requests. We Illustrate Them With A Request Queue (0-199). 98, 183, 37, 122, 14, 124, 65, 67 Head Pointer 53
- 235. COMPUTERFUNDAMENTALS 10.7.3. DISK MANAGEMENT Platter (single and multiple) and surface Track and cylinder Sector Armature and heads: Fixed head and movable head Contact, fixed or aerodynamic gags Removable and non-removable 10.7.4. SWAP-SPACE MANAGEMENT Sector size: 512 bytes Cylinders per disk (tracks per platter): 6962 Platters: 3 - 12 Rotational speed: 10000 RPM Storage size: 4 - 18 GB Seek time: 5 - 12 milliseconds Latency: 3milliseconds Transfer rate: 14 - 20 MB/sec
- 236. COMPUTERFUNDAMENTALS 10.7.5. DISK RELIABILITY Disk Reliability Refers To An Important Property Of Any Kind Of Database System. Reliable Operation Is Very Important For A System. One Aspect Of Such A Reliable Operation Is That All Data Captured In A Committed Transaction Has To Be Stored In A Nonvolatile Area. An Assessment Help Says That This Very Is Safe In Terms Of Power Loss, Operating System Failure, And Hardware Failure. This Kind Of Requirement Can Be Met With Successfully Writing The Data To The Computer's Permanent Storage. In Case When A Computer Is Fatally Damaged And The Disk Drives Continue To Exist. Such Requirement Can Be Moved To Another Computer With Similar Hardware. In This Transaction Process All Committed Will Remain Intact. 10.7.6. STABLE STORAGE IMPLEMENTATION
- 237. COMPUTERFUNDAMENTALS 10.8. DISK SCHEDULING ALGORITHM 1. First Come First Served Disk Scheduling [FCFS] In FCFS, we process the requests in the order they arrive, without regard to the current position of the heads. 10.8. A. illustration shows total head movement of 640 cylinders
- 238. COMPUTERFUNDAMENTALS 2. Shortest-Seek-Time-First (SSTF) Disk-Scheduling The shortest-seek-time-first (SSTF) disk-scheduling algorithm moves the heads the minimum amount it can to satisfy any pending request. Selects The Request With The Minimum Seek Time From The Current Head Position. SSTF Scheduling Is A Form Of SJF Scheduling; May Cause Starvation Of Some Requests. Illustration Shows Total Head Movement of 236 Cylinders. 10.8. B. The shortest-seek-time-first (SSTF) disk-scheduling
- 239. COMPUTERFUNDAMENTALS 3. SCAN DISK-SCHEDULING ALGORITHM An Elevator Is Designed To Visit Floors That Have People Waiting. In General, An Elevator Moves From One Extreme To The Other (Say, The Top Of The Building To The Bottom), Servicing Requests As Appropriate. The SCAN Disk-Scheduling Algorithm Works In A Similar Way, Except Instead Of Moving Up And Down, The Read/Write Heads Move In Toward The Spindle, Then Out Toward The Platter Edge, Then Back Toward The Spindle, And So Forth. The Disk Arm Starts At One End Of The Disk, And Moves Toward The Other End, Servicing Requests Until It Gets To The Other End Of The Disk, Where The Head Movement Is Reversed And Servicing Continues. Sometimes Called The Elevator Algorithm. Illustration Shows Total Head Movement Of 208 Cylinders. 10.8. C.Scan Disk-Scheduling Algorithm
- 240. COMPUTERFUNDAMENTALS 4. C-SCAN Provides A More Uniform Wait Time Than SCAN. The Head Moves from One End of the Disk to the Other. Servicing Requests As It Goes. When It Reaches The Other End, However, It Immediately Returns To The Beginning Of The Disk, Without Servicing Any Requests On The Return Trip. Treats The Cylinders As A Circular List That Wraps Around From The Last Cylinder To The First One. 10.8. D. C-Scan Output 5. C-LOOK Version of C-SCAN Arm only goes as far as the last request in each direction, then reverses direction immediately, without first going all the way to the end of the disk. 10.8. E.C-LOOK
- 241. COMPUTERFUNDAMENTALS 10.9. RAID [Redundant Array of Independent disks] RAID – multiple disk drives provides reliability via redundancy. Redundant Array of Independent Disks (RAID) RAID is arranged into six different levels. Several improvements in disk-use techniques involve the use of multiple disks working cooperatively. Disk striping uses a group of disks as one storage unit. RAID schemes improve performance and improve the reliability of the storage system by storing redundant data. o Mirroring or shadowing keeps duplicate of each disk. o Block interleaved parity uses much less redundancy
- 242. COMPUTERFUNDAMENTALS RID levels Raid levels 0 through 2 Backup and parity drives are shaded RID levels [continued] Raid levels 3 through 5 Backup and parity drives are shaded
- 243. COMPUTERFUNDAMENTALS 10.10. A.DISK ATTACHMENT Disks may be attached one of two ways: 1. Host attached via an I/O port 2. Network attached via a network connection 1. Host Attached Via An I/O Port 2. Network Attached Via A Network Connection
- 244. COMPUTERFUNDAMENTALS Questions On I/O Management . 1. I/O Hardware Contains A) Bus B) Controller C) I/O Port And Its Registers D) All Of The Mentioned ANSWER: D 2. The Data-In Register Of I/O Port Is A) Read By Host To Get Input B) Read By Controller To Get Input C) Written By Host To Send Output D) Written By Host To Start A Command ANSWER: A 3. The Host Sets _____ Bit When A Command Is Available For The Controller To Execute. A) Write B) Status C) Command-Ready D) Control Answer: C 4. When Hardware Is Accessed By Reading And Writing To The Specific Memory Locations, Then It Is Called A) Port-Mapped I/O B) Controller-Mapped I/O C) Bus-Mapped I/O D) None Of The Mentioned ANSWER: D Explanation: It Is Called Memory-Mapped I/O.
- 245. COMPUTERFUNDAMENTALS 5. Device Drivers Are Implemented To Interface A) Character Devices B) Block Devices C) Network Devices D) All Of The Mentioned ANSWER: D 6. Which Hardware Triggers Some Operation After Certain Programmed Count? A) Programmable Interval Timer B) Interrupt Timer C) Programmable Timer D) None Of The Mentioned ANSWER: A 7. The Device-Status Table Contains A) Each I/O Device Type B) Each I/O Device Address C) Each I/O Device State D) All Of The Mentioned ANSWER: D 8. Which Buffer Holds The Output For A Device? A) Spool B) Output C) Status D) Magic ANSWER: A 9. Which One Of The Following Connects High-Speed High-Bandwidth Device To Memory Subsystem And CPU.
- 246. COMPUTERFUNDAMENTALS A) Expansion Bus B) PCI Bus C) SCSI Bus D) None Of The Mentioned ANSWER: A 10. A Process Is Moved To Wait Queue When I/O Request Is Made With A) Non-Blocking I/O B) Blocking I/O C) Asynchronous I/O D) Synchronous I/O ANSWER: B 1) In _______, Information Is Recorded Magnetically On Platters. A) Magnetic Disks B) Electrical Disks C) Assemblies D) Cylinders ANSWER : A 2) The Heads Of The Magnetic Disk Are Attached To A _____ That Moves All The Heads As A Unit. A) Spindle B) Disk Arm C) Track D) None Of These ANSWER: B
- 247. COMPUTERFUNDAMENTALS 3) The Set Of Tracks That Are At One Arm Position Make Up A ___________. A) Magnetic Disks B) Electrical Disks C) Assemblies D) Cylinders ANSWER: D 4) The Time Taken To Move The Disk Arm To The Desired Cylinder Is Called The : A) Positioning Time B) Random Access Time C) Seek Time D) Rotational Latency ANSWER: C 5) The Time Taken For The Desired Sector To Rotate To The Disk Head Is Called : A) Positioning Time B) Random Access Time C) Seek Time D) Rotational Latency ANSWER: D 6) When The Head Damages The Magnetic Surface, It Is Known As _________. A) Disk Crash B) Head Crash C) Magnetic Damage D) All Of These ANSWER: B 7) A Floppy Disk Is Designed To Rotate ___________ As Compared To A Hard Disk Drive. A) Faster
- 248. COMPUTERFUNDAMENTALS B) Slower C) At The Same Speed D) None Of These ANSWER: B. 8) The Host Controller Is : A) Controller Built At The End Of Each Disk B) Controller At The Computer End Of The Bus C) Both A And B D) Neither A Nor B ANSWER: B. 9) ______ Controller Sends The Command Placed Into It, Via Messages To The _____ Controller. A) Host, Host B) Disk, Disk C) Host, Disk D) Disk, Host ANSWER: C. Explanation: None. 10) The Disk Bandwidth Is : A) The Total Number Of Bytes Transferred B) Total Time Between The First Request For Service And The Completion On The Last Transfer C) The Total Number Of Bytes Transferred Divided By The Total Time Between The First request For Service And The Completion On The Last Transfer D) None Of These ANSWER : C. Explanation: None. 1) RAID Level 3 Supports A Lower Number Of I/Os Per Second, Because _______________. A) Every Disk Has To Participate In Every I/O Request B) Only One Disk Participates Per I/O Request
- 249. COMPUTERFUNDAMENTALS C) I/O Cycle Consumes A Lot Of CPU Time D) All Of These ANSWER: A. Explanation: None. 2) RAID Level _____ Is Also Known As Block Interleaved Parity Organization And Uses Block Level Striping And Keeps A Parity Block On A Separate Disk. A) 1 B) 2 C) 3 D) 4 ANSWER: D Explanation: None. 3) A Performance Problem With _________ Is The Expense Of Computing And Writing Parity. A) Non-Parity Based RAID Levels B) Parity Based RAID Levels C) All RAID Levels D) None Of These ANSWER: B Explanation: None. 4) In RAID Level 4, One Block Read, Accesses __________. A) Only One Disk B) All Disks Simultaneously C) All Disks Sequentially D) None Of These ANSWER: A. Explanation: Other Requests Are Allowed To Be Processed By Other Disks. 5) The Overall I/O Rate In RAID Level 4 Is : A) Low B) Very Low C) High D) None Of These ANSWER: C Explanation: All Disks Can Be Read In Parallel.
- 250. COMPUTERFUNDAMENTALS 11. FILEMANAGEMENT FILE A File Is A Named Collection Of Related Information That Is Recorded On Secondary Storage Such As Magnetic Disks, Magnetic Tapes And Optical Disks.In General, A File Is A Sequence Of Bits, Bytes, Lines Or Records Whose Meaning Is Defined By The Files Creator And User. FILESTRUCTURE File Structure Is A Structure, Which Is According To A Required Format That Operating System Can Understand. A File Has A Certain Defined Structure According To Its Type. A Text File Is A Sequence Of Characters Organized Into Lines. A Source File Is A Sequence Of Procedures And Functions. An Object File Is A Sequence Of Bytes Organized Into Blocks That Are Understandable By The Machine. When Operating System Defines Different File Structures, It Also Contains The Code To Support These File Structure. Unix, MS-DOS Support Minimum Number Of File Structure. ExampleFileStructure
- 251. COMPUTERFUNDAMENTALS 11.1.FILEACCESSING METHODS Information is kept in files. Files reside on secondary storage. When this information is to be used, it has to be accessed and brought into primary main memory. Information in files could be accessed in many ways. It is usually dependent on an application. There are three file access methods. 1. SEQUENTIAL ACCESS A simple access method, information in a file is accessed sequentially one record after another. To process the with record all the 1-1 records previous to 1 must be accessed. Sequential access is based on the tape model that is inherently a sequential access device. Sequential access is best suited where most of the records in a file are to be processed. For example, transaction files. 11.1. A. Transaction file
- 252. COMPUTERFUNDAMENTALS 2. DIRECT ACCESS: Sometimes it is not necessary to process every record in a file. It may not be necessary to process records in the order in which they are present. Information present in a record of a file is to be accessed only if some key value in that record is known. In all such cases, direct access is used. Direct access is based on the disk that is a direct access device and allows random access of any file block. Since a file is a collection of physical blocks, any block and hence the records in that block are accessed. For example, master files. Databases are often of this type since they allow query processing that involves immediate access to large amounts of information. All reservation systems fall into this category. Not all operating systems support direct access files. Usually files are to be defined as sequential or direct at the time of creation and accessed accordingly later. Sequential access of a direct access file is possible but direct access of a sequential file is not 11.1. B.Reservation file
- 253. COMPUTERFUNDAMENTALS 3. INDEXED SEQUENTIAL ACCESS: This access method is a slight modification of the direct access method. It is in fact a combination of both the sequential access as well as direct access. The main concept is to access a file direct first and then sequentially from that point onwards. This access method involves maintaining an index. The index is a pointer to a block. To access a record in a file, a direct access of the index is made. The information obtained from this access is used to access the file. For example, the direct access to a file will give the block address and within the block the record is accessed sequentially. Sometimes indexes may be big. So hierarchies of indexes are built in which one direct access of an index leads to info to access another index directly and so on till the actual file is accessed sequentially for the particular record. The main advantage in this type of access is that both direct and sequential access of files is possible. 11.C.IndexSequentialBased Files
- 254. COMPUTERFUNDAMENTALS 11.2FILE TYPES FILETYPE File Type Refers To The Ability Of The Operating System To Distinguish Different Types Of File Such As Text Files Source Files And Binary Files Etc. Many Operating Systems Support Many Types Of Files. Operating System Like MS-DOS And UNIX Have The Following Types Of Files: 1. Ordinary Files These Are The Files That Contain User Information. These May Have Text, Databases Or Executable Program. The User Can Apply Various Operations On Such Files Like Add, Modify, Delete Or Even Remove The Entire File. 2. Directory Files These Files Contain List Of File Names And Other Information Related To These Files. 3. Special Files: These Files Are Also Known As Device Files. These Files Represent Physical Device Like Disks, Terminals, Printers, Networks, and Tape Drive Etc. These Files Are Of Two Types Character Special Files - Data Is Handled Character By Character As In Case Of Terminals Or Printers. Block Special Files - Data Is Handled In Blocks As In The Case Of Disks And Tapes.
- 255. COMPUTERFUNDAMENTALS 11.2. A. Example files 11.3. FILE OPERATIONS The Os Provides Systems Calls To Create, Write, Read, Reset, And Delete Files. The Following Discusses The Specific Duties An Os Must Do For Each Of The Five Basic File Operations. Creating A File. First, A Space In The File System Must Be Found For The File. Second, An Entry For The New File Must Be Made In The Directory. The Directory Entry Records The Name Of The File And The Location In The File System.
- 256. COMPUTERFUNDAMENTALS Writing A File. To Write A File, A System Call Is Made Specifying Both The Name And The File And The Information To Be Written To The File. Given The Name Of The File, The System Searches The Directory To Find The Location Of The File. The Directory Entry Will Need To Store A Pointer To The Current Block Of The File (Usually The Beginning Of The File). Using This Pointer, The Address Of The Next Block Can Be Computed Where The Information Will Be Written. The Write Pointer Must Be Updated – In This Way, Successive Writes Can Be Used To Write A Sequence Of Blocks To The File. Reading A File. To Read A File, A System Call Is Made That Specifies That Specifies The Name Of The File And Where (In Memory) The Next Block Of The File Should Be Put. Again, The Directory Is Searched For The Associated Directory Entry, And The Directory Will Need A Pointer To The Next Block To Be Read. Once The Block Is Read, The Pointer Is Updated. Resetting A File. The Directory Is Searched For The Appropriate Entry, And The Current File Position Is Reset To The Beginning Of The File. Deleting A File. To Delete A File, The Directory Is Searched For The Named File. Having Found The Associated Directory Entry, The Space Allocated To The File Is Released (So It Can Be Reused By Other Files) And Invalidates The Directory Entry The Five Operations Described Comprise Only The Minimal Set Of Required File Operations. More Commonly, We Shall Also Want To Edit The File And Modify Its Contents.
- 257. COMPUTERFUNDAMENTALS A Special Case Of Editing A File Is Appending New Information At The End Of The File. Copies Of The File Can Also Be Created, And Since Files Are Named Object, Renaming An Existing File May Also Be Needed. If The File Is A Binary Object Format, We May Also Want To Execute It. Also Of Use Are Facilities To Lock Sections Of An Open File For Multiprocessing Access, To Share Sections, And Even To Map Sections Into Memory Or Virtual- Memory Systems. This Last Function Allows A Part Of The Virtual Address To Be Logically Associated With Section Of A File. Reads And Writes To That Memory Region Are Then Treated As Reads And Writes To The File. To That Memory Region Are Then Treated As Reads And Writes To The File, Greatly Simplifying File Use 11.4. DIRECTORY STRUCTURE Files Are Used For Storing The Information Of The User. Generally For Arranging All The Files Directories Or Folders Are Used. A Folder Or Directory Is Also Called As The Container Of The Files In Which Many Sub Directors And Files Are Stored. So That Files System Specifies The Arrangement Of The Files In The System. There Are Following Directory Structures Available For Organizing All The Files. 1. Hierarchical In This All The Files Are Organized In The Form Of Parent And Child Relationship. Means In This There Is The Parent Directory Which Contains All The Sub Files. For Example There Is A Folder Which Contains Many Sub Directories And Their Files. So In This All The Files Are Stored In The Parent And Child Mode. And If We Want To Access A Directory Or A File Then We Must Have To Move All The Parent Directories And Files For Better Understanding See The Following Figures.
- 258. COMPUTERFUNDAMENTALS 11.4. A.Hierarchical File System Here Rohit Is The Parent Directory Or Top Most Directory. And All Rajat And The Microsoft Are The Child Directories Of This Parent Directory. Note: Rectangle Denotes All Directories And Circles Represents Files.
- 259. COMPUTERFUNDAMENTALS 2. Single Level Directory In This There Is A Single Directory Which Contains All The Files Into. But This Is Not The Best Way Because All The Files Are Stored Into The Single Folder So This Is Very Difficult For A User To Search A File. There Is Only One Directory Which Contains The Other Files So That Many Times This Is Not Used Because This Will Contains Huge Amount Of Files And This Will Makes Difficult For The Users To Locate Or Find A File. 11.4. B.Single -level directory
- 260. COMPUTERFUNDAMENTALS 3. Two Level Directories In This A Directory Also Contains A Another Directory And All The Files Are Organized Into The Sub Directory. In The Two Level A Directory Also Contains Sub Directory And The Files. We Can Say That A Single Directory Will Be The Container Of Many Other Files And The Directories So That When A User Wants To Access Any Directory Then He Has To Travel All The Other Directories And Files From That Directory. 11.4. C. Two –level architecture
- 261. COMPUTERFUNDAMENTALS 4. Acyclic Graph Directory If A Directory Contains A Directory And Files Then It Is Called As The Acyclic Directory In This A Single Directory Contains Both Directory And Files And All The Directories Are Connected With Some Paths Means A Single Folder Or File Can Be Accessible Via Another Files. In This Each Directory And A File Is Linked With One Or More Directories And The Files. When A Single File Or Directory Can Be Reached From Any Directory Or From Any File, Then It Is Called As The Acyclic Directory. In The Acyclic Graph A Single File Or A Directory Can Be Reached From Any File Because There Are Multiple Paths Exists Between That File. Or There Are More Routs For That Single File Or Directory. 11.4.D. A Cyclic Graph Directory
- 262. COMPUTERFUNDAMENTALS Explain Process: Any Operation Or Any Request For A Service Is Called As The Process; Process May A Request For Moving The Mouse, Reading The Data From The File Or Writing The Data Into The File, Printing A Document Or Any Work Which Is Given By The User Is Known As The Process. We Can Also Say A Program Which Is Requested By The User For The Execution Is Also Known As The Process. There Are Many Models Which Watches The Processes And Which Describes The States Of The Processes Means What Is The State Of The Process, Whether They Are Running, Or Whether They Are Requesting For The Input And Output, All These Will Be Determine With The Help Processing Models.
- 263. COMPUTERFUNDAMENTALS Questions on Files 1. ______ Is A Unique Tag, Usually A Number, Identifies The File Within The File System. A) File Identifier B) File Name C) File Type D) None Of The Mentioned ANSWER: A 2. To Create A File A) Allocate The Space In File System B) Make An Entry For New File In Directory C) Both (A) And (B) D) None Of The Mentioned ANSWER: C 3. By Using The Specific System Call, We Can A) Open The File B) Read The File C) Write Into The File D) All Of The Mentioned ANSWER: D 4. File Type Can Be Represented By A) File Name B) File Extension C) File Identifier D) None Of The Mentioned ANSWER: B
- 264. COMPUTERFUNDAMENTALS 5. Which File Is a Sequence of Bytes Organized into Blocks Understandable by the System’s Linker? A) Object File B) Source File C) Executable File D) Text File ANSWER: A 6. What Is The Mounting Of File System? A) Crating Of A File system B) Deleting A File system C) Attaching Portion Of The File System Into A Directory Structure D) Removing Portion Of The File System Into A Directory Structure ANSWER: C 7. Mapping Of File Is Managed By A) File Metadata B) Page Table C) Virtual Memory D) File System ANSWER: A 8. Mapping Of Network File System Protocol To Local File System Is Done By A) Network File System B) Local File System C) Volume Manager D) Remote Mirror ANSWER: A 9. Which One Of The Following Explains The Sequential File Access Method? A) Random Access According To The Given Byte Number B) Read Bytes One At A Time, In Order
- 265. COMPUTERFUNDAMENTALS C) Read/Write Sequentially By Record D) Read/Write Randomly By Record ANSWER: B 10. File System Fragmentation Occurs When A) Unused Space Or Single File Are Not Contiguous B) Used Space Is Not Contiguous C) Unused Space Is Non-Contiguous D) Multiple Files Are Non-Contiguous ANSWER: A 11) To Organize File Systems On Disk, : A) They Are Split Into One Or More Partitions B) Information About Files Is Added To Each Partition C) They Are Made On Different Storage Spaces D) All Of These ANSWER: A AND B 12) The Directory Can Be Viewed As A _________, That Translates File Names Into Their Directory Entries. A) Symbol Table B) Partition C) Swap Space D) Cache ANSWER: A 13) In The Single Level Directory : A) All Files Are Contained In Different Directories All At The Same Level B) All Files Are Contained In The Same Directory C) Depends On The Operating System
- 266. COMPUTERFUNDAMENTALS D) None Of These ANSWER: B 14) In the Single Level Directory: A) All Directories Must Have Unique Names B) All Files Must Have Unique Names C) All Files Must Have Unique Owners D) All of These ANSWER: B 15) In The Two Level Directory Structure : A) Each User Has His/Her Own User File Directory B) The System Has Its Own Master File Directory C) Both A And B D) None Of These ANSWER: C 16) When A User Job Starts In A Two Level Directory System, Or A User Logs In : A) The Users User File Directory Is Searched B) The System’s Master File Directory Is Searched C) The Master File Directory Is Indexed By User Name Or Account Number, And Each Entry Points To The UFD For That User D) All Of These ANSWER: B AND C 17) When A User Refers To Particular File, : A) System MFD Is Searched B) His Own UFD Is Searched C) Both MFD And UFD Are Searched D) Every Directory Is Searched ANSWER: B AND C
- 267. COMPUTERFUNDAMENTALS 18) The Disadvantage Of The Two Level Directory Structure Is That : A) It Does Not Solve The Name Collision Problem B) It Solves The Name Collision Problem C) It Does Not Isolate Users From One Another D) It Isolates Users From One Another ANSWER: D 19) In The Tree Structured Directories, A) The Tree Has The Stem Directory B) The Tree Has The Leaf Directory C) The Tree Has The Root Directory D) All Of These ANSWER: C 20) The Current Directory Contains, Most of the Files That Are: A) Of Current Interest to the User B) Stored Currently In the System C) Not Used In the System D) Not Of Current Interest to the System ANSWER: A 21) Path Names Can Be Of Two Types: (Choose Two) A) Absolute B) Local C) Global D) Relative ANSWER: A AND D
![sivannarayana bandi[శివబాల], profile picture](https://cdn.slidesharecdn.com/profile-photo-sivannarayanabandi-48x48.jpg?cb=1567566828)
![COMPUTERFUNDAMENTALS
1. INTRODUCTION TO COMPUTER SYSTEM
1.0.Founderof Computer
1.1.Generations Of Computers
1.2. First Generation Computers
1.3. Second Generation Computers
1.4.Third Generation Computers
1.6.Fifth Generation Computers
2. DEFINITION OF COMPUTER AND ITS CONCEPTS.
2.0computer Definition
2.1computer Block Diagram
2.2. Input Devices
2.2.1. Keyboard
2.2.1.2 Keyboard Shortcuts
2.2.2 Mouse
2.2.3 Joystick
2.2.4 Light Pen
2.2.5Track Ball
2.2.6 Scanner
2.2.7 Digitizer [Graphic Tablet]
2.2.8 Microphone
2.2.9.MagneticInk Card Reader(MICR)
2.3. Optical Character Reader (OCR)
2.4 Bar Code Reader
2.5 Webcam
2.6 Biometrics [Thumb Impression / Face Detection]
2.7. Output Devices
2.7.1.Monitors
2.7.2. Cathode-Ray Tube (CRT) Monitor
2.7.3. Flat-Panel Display Monitor
2.8.Printers
2.8.1.ImpactPrinters](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-1-320.jpg)
![COMPUTERFUNDAMENTALS
2.8.2. Character Printers
2.8.3. Dot Matrix Printer
2.8.4. Daisy Wheel
2.8.5line Printers
2.8.6drum Printer
2.8.7chain Printer
2.8.9.Non-ImpactPrinters
2.9.CharacteristicsofNon-ImpactPrinters
2.9.1laser Printers
2.9.2. Inkjet Printers
3. FUNDAMENTALS OF COMPUTER ARCHITECTURE
3.1. CPU Block Diagram
3.2. CPU Phases
3.3. Memory Unit
3.4. Memory Classification
3.4.1. Random Access Memory [Ram]
3.4.2. SRAM
3.4.3 .DRAM
3.5. Rom Classification
3.5. 1.PROM
3.5.2. EPROM
3.5.3. EEPROM
3.6 Cache Memory
3.7. Control Unit
3.8. Arithmetic Logic Unit [ALU]
3.9. Buses In CPU
3.9.1. Instruction Cycle
3.9.2. Measure of CPU Performance.](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-2-320.jpg)
![COMPUTERFUNDAMENTALS
4. MOTHERBOARD [INTERNAL COMPONENTS]
4.1Features ofMotherboard
4.2PopularManufacturers
4.3The Important Components of Motherboard
4.4complete Mother Board View
5. COMPUTER –SOFTWARE
5.1.System Software
5.1.1. Operating System
5.1.2. System Development Software
5.1.3. Utility Programs
5.2. Application Software
5.2.2. Custom Software
5.3. Assembler
5.4. Compiler
5.5. Interpreter
6. OPERATING SYSTEM
6.1Basics of operating system
6.2 Types Of Operating System
6.3Process management
6.31Process
6.3.2Process scheduling
7. INTER PROCESSOR COMMUNICATION
7.1introduction
7.1.1. Race Conditions
7.1.2Semaphores
7.1.3Message Passing
7.1.4scheduling Algorithms](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-3-320.jpg)
![COMPUTERFUNDAMENTALS
8. DEADLOCKS
8.1.1 Definition Of Deadlock
8.1.2 Characteristics
8.1.3deadlock’s Prevention
8.1.4 Banker’s Algorithm
9. MEMORY MANAGEMENT
9.1.1basic Memory Management
9.1 .2definition
9.1.3 Logical &Physical Address Map
9.1.4continuous Memory Allocation
9.1.5fixed And Variable Portion
9.1.6 Internal And External Fragmentation And
Compaction
9.1.7paging: Principle Of Operation
9.1.8 Page Allocation
9.1.9hardware Support For Paging
9.1.10protection And Sharing
9.1.11disadvantages Of Paging
9.2 Virtual Memory
9.2. Basics Of Virtual Memory
9.2.1demand Paging
9.2.2.Pagereplacement Algorithm
9.2.3.Reference String
9.2.4.First In First Out Algorithm[FIFO]
9.2.5.Leastrecently Used Algorithm[LRU]
9.2.7 Least Frequently Used Algorithm[LFU]
9.2.8.Most Frequently Used Algorithm[MFU]](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-4-320.jpg)
![COMPUTERFUNDAMENTALS
10. I/O MANAGEMENT
10.1 I/O Devices,
10.2 Device Controllers
10.3direct Memory Access Principles Of I/O Software:
10.4 Goals of Interrupt Handlers
10.5 Device Drivers
10.6secondary-Storage Structure:
10.7 Disk Structure
10.8 Disk Scheduling Algorithm
10.9. Raid [RedundantArray Of IndependentDisks]
10.10. Disk Attachment
11. FILEMANAGEMENT
11.1 Access Methods
11.2file Types
11.3file Operations
11.4 Directory Structure](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-5-320.jpg)
![COMPUTERFUNDAMENTALS
1. INTRODUCTION TOCOMPUTER SYSTEM
CHARLES BABBAGE
[DEC-16-1791toOCT-18-1871]](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-6-320.jpg)
![COMPUTERFUNDAMENTALS
1. 0.FOUNDER OF COMPUTER
1.0. First-GenerationComputerfromCharlesBabbage
CHARLES BABBAGE, [26 December 1791 –18 October 1871] Was A Mathematician,
Philosopher, Inventor And Mechanical Engineer, Babbage Is Best Remembered For
Originating The Concept Of A Programmable Computer.
Parts Of Babbage's Uncompleted Mechanisms Are On Display In The London Science
Museum.
In 1991, A Perfectly Functioning Difference Was Constructed From Babbage's
Original Plans.
Built To Tolerances Achievable In The 19th Century, The Success Of The Finished
Engine Indicated That Babbage's Machine Would Have Worked.
1. A. First Programmable Computer 1.B.Babbage Engine](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-7-320.jpg)

![COMPUTERFUNDAMENTALS
1.2. FIRST GENERATION COMPUTERS [1946-1959].
The Computers Of First Generation Used Vacuum Tubes As The Basic Components
For Memory And Circuitry For CPU (Central Processing Unit).
These Tubes, Like Electric Bulbs, Produced A Lot Of Heat And Were Prone To
Frequent Fusing Of The Installations, Therefore, Were Very Expensive And Could Be
Afforded Only By Very Large Organizations.
In This Generation Mainly Batch Processing Operating System Were Used. Punched
Cards, Paper Tape, And Magnetic Tape Were Used As Input And Output Devices. The
Computers In This Generation Used Machine Code As Programming Language.
1.2. A. First -Generationcomputer1 1.2.B.First-Generationcomputer2
1.2. C. Top View of First-Generation Computer](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-9-320.jpg)

![COMPUTERFUNDAMENTALS
1.3. SECOND GENERATION COMPUTERS [1959-1965]
In This Generation Transistors Were Used That Were Cheaper, Consumed Less
Power, More Compact In Size, More Reliable And Faster Than The First Generation
Machines Made Of Vacuum Tubes
In This Generation, Magnetic Cores Were Used As Primary Memory And Magnetic
Tape And Magnetic Disks As Secondary Storage Devices
. In This Generation Assembly Language And High-Level Programming Languages
Like FORTRAN, COBOL Was Used. The Computers Used Batch Processing And
Multiprogramming Operating System.
1.3.A.Secondgeneration Ibm Computer 1.3.B.Secon Generation Computer
1.3.C Secongeneration Pc 1.3.D.Secondgeneration Pc 1.3.E.Ibmpc
[Tranistors Replaced By Vaccumetubes]](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-11-320.jpg)

![COMPUTERFUNDAMENTALS
1.4.THIRD GENERATION COMPUTERS[1965-1971]
The Computers Of Third Generation Used Integrated Circuits (IC's) In Place Of
Transistors.
A Single IC Has Many Transistors, Resistors And Capacitors Along With The
Associated Circuitry. The IC Was Invented By Jack Kilby.
This Development Made Computers Smaller In Size, Reliable And Efficient.
In This Generation Remote Processing, Time-Sharing, Multi-Programming Operating
System Were Used.
High-Level Languages (FORTRAN-II TO IV, COBOL, PASCAL PL/1, BASIC, ALGOL-68
Etc.) Were Used During This Generation.
The Main Features Of Third Generation Are:
IC Used
More Reliable In Comparison To Previous Two Generations
Smaller Size
Generated Less Heat
Faster
Lesser Maintenance
Still Costly
A.C Needed
Consumed Lesser Electricity
Supported High-Level Language
Some Computers Of This Generation Were:
Ibm-360 Series
Honeywell-6000 Series
PDP(Personal Data Processor)
Ibm-370/168
Tdc-316](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-13-320.jpg)
![COMPUTERFUNDAMENTALS
1.4.1THIRD GENERATION COMPUTERS
1.4.1.A. Third Generation Computer1
[ It Is Developed By High Levelonguage Like C] 1.4.1.B Third Generation
Computer
[Having Ups Separate Cpu]
1.4.1.C.Corei7based Embedded Computer 1.4.1.D.Third Generation Pc](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-14-320.jpg)
![COMPUTERFUNDAMENTALS
1.5.FOURTH GENERATION COMPUTERS[1971-1980]
The Computers of Fourth Generation Used Very Large Scale Integrated (VLSI)
Circuits.
VLSI Circuits Having About 5000 Transistors And Other Circuit Elements And Their
Associated Circuits On A Single Chip Made It Possible To Have Microcomputers Of
Fourth Generation.
Fourth Generation Computers Became More Powerful, Compact, Reliable, and
Affordable. As A Result, It Gave Rise To Personal Computer (Pc) Revolution.
In This Generation Time Sharing, Real Time, Networks, Distributed Operating
System Were Used.
All The High-Level Languages Like C, C++, Dbase Etc., Were Used In This Generation.
1.5.1.FOURTH GENERATION COMPUTERS FEATURES :
The Main Features Of Fourth Generation Are:
VLSI Technology Used
Very Cheap
Portable And Reliable
Use Of PC's
Very Small Size
Pipeline Processing
No A.C. Needed
Concept Of Internet Was Introduced
Great Developments In The Fields Of Networks
Computers Became Easily Available
Some Computers Of This Generation Were:
DEC 10
STAR 1000
PDP 11
CRAY-1(Super Computer)](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-15-320.jpg)

![COMPUTERFUNDAMENTALS
1.6.FIFTH GENERATION COMPUTERS[1980-Till Date]
In The Fifth Generation, The VLSI Technology Became ULSI (Ultra Large Scale
Integration) Technology, Resulting In The Production Of Microprocessor Chips
Having Ten Million Electronic Components.
This Generation Is Based On Parallel Processing Hardware And AI (Artificial
Intelligence) Software.
AI Is An Emerging Branch In Computer Science, Which Interprets Means And
Method Of Making Computers Think Like Human Beings
.All the High-Level Languages like C and C++, Java, .Net Etc., Are Used in This
Generation.
Fifth Generation Computers Includes:
Robotics
Neural Networks
Game Playing
Development of Expert Systems To Make Decisions In Real Life Situations.
Natural Language Understanding and Generation.
1.6.A. Fifth Generation Computers Based On Artificial Intelligence [Robots].](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-17-320.jpg)








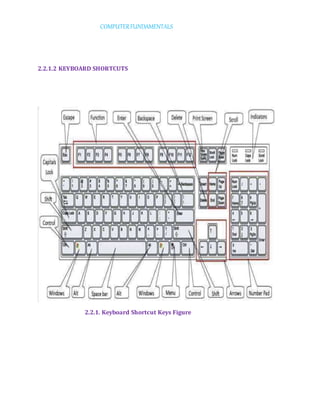





![COMPUTERFUNDAMENTALS
2.2.7 DIGITIZER[GRAPHIC TABLET]
Digitizer Is An Input Device Which Converts Analog Information Into Digital Form.
Digitizer Can Convert A Signal From The Television Or Camera Into A Series Of
Numbers That Could Be Stored In A Computer.
They Can Be Used By The Computer To Create A Picture Of Whatever The Camera
Had Been Pointed At.
Digitizer Is Also Known As Tablet Or Graphics Tablet Because It Converts Graphics
And Pictorial Data Into Binary Inputs.
A Graphic Tablet As Digitizer Is Used For Doing Fine Works Of Drawing And Image
Manipulation Applications.
2.2.7. A. Dizitilizer 2.2.7.B.Apple Tab
2.2.7. C.Painting on tablet](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-32-320.jpg)





![COMPUTERFUNDAMENTALS
2.6 BIOMETRICS [THUMB IMPRESSION / FACE DETECTION]
One Of The Widely Used Access Control Biometric Machines In Any
Technology Oriented Organization Is Thumb Impression Attendance System. Nowadays, To
Avoid Proxy Attendance Or Duplicate Voting Most Employers Use Thumb Impression
Attendance System, Which Collects The Thumb Impression Through A Finger Print
Scanning Device.
A Thumb Impression Attendance System Device Contains Hardware That Scans The
Thumb Impression Of A Person And A Software Application That Verifies The Scanned
Impression Against The Previously Collected Impression That Is Stored In The Built-In
Biometric Database During The Time Of Enrollment. Thumb Impression Attendance
System Is Hassle-Free and A Very Convenient Device For Any Security Oriented Business
Face Recognition Biometric Attendance Machines Can Help You In Cost Saving
Because These Machines Are Available In Very Low Prices.
These Devices Help In Bringing Punctuality In The Organization Because They Keep
Records Of Employees In And Out Timings.
These Machines Come With Different Features Like Card Reader, Face Recognition
System, and Thumb Impression Facility
. There Is Software For These Machines Which Is Capable Of Generating 150+
Industry Standard Reports.
These Machines Comes With A Free Software For Payroll Management Of Your
Employees.
2.6. A. Biometric Time Attendance System 2.6.B. Thumb Impression System
2.6.8. C. Face Reorganization System](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-38-320.jpg)


















![COMPUTERFUNDAMENTALS
3.4.1. RANDOM ACCESS MEMORY [RAM]
Ram Is A Memory Scheme Within The Computer System Responsible For Storing
Data On A Temporary Basis, So That It Can Be Promptly Accessed By The Processor
As And When Needed.
It Is Volatile In Nature, Which Means That Data Will Be Erased Once Supply To The
Storage Device Is Turned Off.
Ram Stores Data Randomly and the Processor Accesses These Data Randomly From
the Ram Storage.
The Information Stored In The Ram Is Typically Loaded From The Computer's Hard
Disk, And Includes Data Related To The Operating System And Certain Applications.
When The System Is Switched Off, The Ram Loses All Stored Information
. The Data Remains Stored On Secondary Storage Though, And Can Be Retained
When The System Is Running Again.
Some Of The Earliest Computers Used Delay-Line Format Of Computer Storage.
Most Modern Computers Use An Embedded Ram Circuitry On The Motherboard
Which Reads Data In Bursts.
So, Modern Ram Devices Are Not Random Memory Devices As Such; They Are Burst
Memory Access Devices, But the Term Ram Has Stuck In Everyday Usage.
There Are Primarily Two Forms Of Ram: STATIC RAM (SRAM) And DYNAMIC RAM
(DRAM).
3.4.1. A.RAM1 3.4.1.B.RAM2](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-57-320.jpg)
![COMPUTERFUNDAMENTALS
3.4.2. SRAM [STATIC RANDOM ASSESSABLE MEMORY]
Where The Word Static Indicates That It, Does Not Need To Be Periodically
Refreshed, As SRAM Uses Bi stable Latching Circuitry (I.E., Flip-Flops) To Store Each
Bit. Each Bit Is Stored As A Voltage
Each Memory Cell Requires Six Transistors, Thus Giving Chip Low Density But High
Speed.
However, SRAM is still volatile in the (Conventional) Sense That Data Is Lost When
Power down.
Disadvantages Are More Expensive And Also Consumes More Power Than Dram.
In High Speed Processors (Such As Pentium), SRAM Is Known as Cache
Memory and Is Included On The Processor Chip.
However High-Speed Cache Memory Is Also Included External To The Processor To
Improve Total Performance.
3.4.2. A.SRAM Chip 3.4.2.B.SRAM Port](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-58-320.jpg)
![COMPUTERFUNDAMENTALS
3.4.3 .DRAM [DYNAMIC RANDOM ASSESSABLE MEMORY]
Its Advantage Over SRAM Is Its Structural Simplicity: Only One Transistor (MOSFET
Gates) And A Capacitor (To Store A Bit As A Charge) Are Required Per Bit, Compared
To Six Transistors In SRAM.
This Allows DRAM To Reach Very High Density.
Also It Consumes Less Power And Is Even Cheaper Than SRAM (Except When The
System Size Is Less Than 8 K).
But The Disadvantage Is That Since It Stores Bit Information As Charge Which
Leaks;
Therefore Information Needs To Be Read And Written Again Every Few
Milliseconds.
This Is Known As Refreshing The Memory And It Requires Extra Circuitry, Adding
To The Cost Of System.
3.4.3. A.DRAM Views](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-59-320.jpg)
![COMPUTERFUNDAMENTALS
3.4.4. READ-ONLY MEMORY [ROM]
Read Only Memory (ROM) Is An Example Of Nonvolatile Memory.
ROM Is A Class Of Storage Medium Used In Computers And Other Electronic Devices.
Read Only Memory (ROM), Also Known As Firmware, Is An Integrated Circuit
Programmed With Specific Data When It Is Manufactured.
The Instructions For Starting The Computer Are Housed On Read Only Memory
Chip.
ROM Chips Are Used Not Only In Computers, But In Most Other Electronic Items As
Well
Because Data Is Fully Incorporated At The ROM Chip's Manufacture, Data Stored Can
Neither Be Erased Nor Replaced. This Means Permanent And Secure Data Storage
However, If A Mistake Is Made In Manufacture, A ROM Chip Becomes Unusable. The
Most Expensive Stage Of ROM Manufacture, Therefore, Is Creating The Template.
If A Template Is Readily Available, Duplicating The ROM Chip Is Very Easy And
Affordable.
A ROM Chip Is Also Non Volatile So Data Stored In It Is Not Lost When Power Is
Turned Off.
ROM Is A Semiconductor Memory That Is Capable Of Operating At Electronics
Speed.](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-60-320.jpg)
![COMPUTERFUNDAMENTALS
3.5. ROM CLASSIFICATION
3.5. A. ROM Classification Diagram
3.5. 1.PROM [PROGRAMMABLE READ ONLY MEMORY]
PROM Stands For Programmable Read-Only Memory,
A Memory Chip On Which Data Can Be Written Only Once.
Once A Program Has Been Written Onto A PROM, It Remains There Forever. Unlike
RAM, Proms Retain Their Contents When The Computer Is Turned Off.
The Difference Between A PROM And A ROM (Read-Only Memory) Is That A PROM
Is Manufactured As Blank Memory, Whereas A ROM Is Programmed During The
Manufacturing Process.
To Write Data Onto A PROM Chip, You Need A Special Device Called A PROM
Programmer Or PROM Burner.
The Process Of Programming A PROM Is Sometimes Called Burning The PROM.
3.5.1.A.Prom Programmer 3.5.1.B. Romchip](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-61-320.jpg)
![COMPUTERFUNDAMENTALS
3.5.2. EPROM [ERASABLE AND PROGRAMMABLE READ ONLY MEMORY]
Acronym For Erasable Programmable Read-Only Memory, And Pronounced Ee-
Prom, EPROM Is A Special Type Of Memory That Retains Its Contents Until It Is
Exposed To Ultraviolet Light.
The Ultraviolet Light Clears Its Contents, Making It Possible To Reprogram The
Memory.
To Write To And Erase An EPROM, You Need A Special Device Called A PROM
Programmer Or PROM Burner.
3.5.2.A.Kinstonprndrive 3.5.2.B.EEPROM Chip
3.5.3. EEPROM
Short Form of Electrically Erasable Programmable Read-Only Memory is EEPROM
EEPROM Is A Special Type Of PROM That Can Be Erased By Exposing It To An
Electrical Charge. Like Other Types Of PROM, EEPROM Retains Its Contents Even
When The Power Is Turned Off.
Also Like Other Types Of ROM, EEPROM Is Not As Fast As RAM.
3.5.3. A. EEPROM Chip 3.5.3.B.EEPROM as NBTV Signal Generator](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-62-320.jpg)



![COMPUTERFUNDAMENTALS
3.8. ARITHMETIC LOGIC UNIT [ALU]
ALU Stands For "Arithmetic Logic Unit." An ALU Is An Integrated Circuit Within
A CPU Or GPU That Performs Arithmetic And Logic Operations. Arithmetic Instructions
Include Addition, Subtraction, And Shifting Operations, While Logic Instructions
Include Boolean comparisons, Such As AND, OR, XOR, And NOT Operations.
ALUS Are Designed to Perform Integer calculations.
Therefore, Besides Adding And Subtracting Numbers, ALUS Often Handle The
Multiplication Of Two Integers, Since The Result Is Also An Integer.
However, ALUS Typically Do Not Perform Division Operations, Since The Result May
Be A Fraction, Or A "Floating Point" Number.
Instead, Division Operations Are Usually Handled By The Floating-Point Unit (FPU),
Which Also Performs Other Non-Integer Calculations.
While The ALU Is A Fundamental Component Of All Processors.
The Design And Function Of An ALU May Vary Between Different Processor Models.
For Example, Some ALUS Only Perform Integer Calculations, While Others Are
Designed To Handle Floating Point Operations As Well.
Some Processors Contain A Single ALU, While Others Include Several Arithmetic
Logic Units That Work Together To Perform Calculations.](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-66-320.jpg)






![COMPUTERFUNDAMENTALS
Questions On Computer Fundamentals Of Computer Architecture
Q1] The Brain Of Any Computer System Is?
A.ALU
Memory
C.CPU
D. Control Unit None Of These
ANS: A
Q2] A Computer Assisted Method For The Recording And Analyzing Of Existing Or Hypothetical
Systems Is?
A. Data transmission
B. Dataflow
C. Data Processing
D. Data Capture
ANS.:B
Q3] what are the main parts in central processing unit?
A. ALU, Controlunit,Memoryunit
B. Axulary devices
C. Control unit ,Hard Disk
D. Memory
ANS: A
Q4] The Section Of The CPU That Selects, Interprets And Sees To The Execution Of Program
Instructions?
A. Memory Unit
B. Control Unit
C. ALU
D. None Of The Above
ANS: B](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-73-320.jpg)
![COMPUTERFUNDAMENTALS
Q5]. CPU Fetches The Instruction From Memory According To The Value Of……..
A) Program Counter
B) Status Register
C) Instruction Register
D) Program Status Word
ANS: C
Q6] A Memory Buffer Used To Accommodate A Speed Differential Is Called………
A) Stack Pointer
B) Cache
C) Accumulator
D) Disk Buffer
ANS: B
Q7]. Which One Of The Following Is The Address Generated By CPU?
A) Physical Address
B) Absolute Address
C) Logical Address
D) None Of The Mentioned
ANS: C
Q8] Run Time Mapping From Virtual To Physical Address Is Done By……..
A) Memory Management Unit
B) CPU
C) PCI
D) None of the Mentioned
ANS: A](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-74-320.jpg)
![COMPUTERFUNDAMENTALS
Q9] Which Of The Following Computer Implemented Binary Numbers, Perform
Calculations Using Electronics And Implemented Separate Computation And Memory
For The First Time?
A) Mark I
B) ABC
C) Z3
D) None Of Above
ANS: B
Q10] FORTRAN Is A Programming Language. What Does FORTRAN Stand For?
A) File Translation
B) Format Translation
C) Formula Translation
D) Floppy Translation
ANS: C
Q11] Which Of The Following Memories Needs Refreshing?
A) SRAM
B) DRAM
C) ROM
D) All Of Above
ANS: B
Q12] Can You Tell What Passes Into And Out From The Computer Via Its Ports?
A) Data
B) Bytes
C) Graphics
D) Pictures
ANS: A](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-75-320.jpg)
![COMPUTERFUNDAMENTALS
Q13] An Output Device That Uses Words Or Messages Recorded On A Magnetic
Medium To Produce Audio Response Is
A) Magnetic Tape
B) Voice Response Unit
C) Voice Recognition Unit
D) Voice Band
ANS: B
Q14] Which of the Items Below Are Considered Removable Storage Media?
A) Removable Hard Disk Cartridges
B) (Magneto-Optical) Disk
C) Flexible Disks Cartridges
D) All of The Above
ANS: D
Q15] Which Of The Following Is Not Purely Output Device?
A) Screen
B) Printer
C) Speaker
D) Plotter
ANS: A
Q16] Who Developed A Mechanical Device In The 17th Century That Could Add,
Subtract, Multiple, Divide And Find Square Roots?
A) Napier
B) Babbage
C) Pascal
D) Leibniz
ANS: D](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-76-320.jpg)
![COMPUTERFUNDAMENTALS
Q17] The First Macintosh Computer Was From
A) First Generation
B) Second Generation
C) Third Generation
D) Fourth Generation
ANS: D
Q18] Which of The Following Is Not A Form Of Data?
A) Numbers and Characters
B) Images
C) Sound
D) None Of Above
ANS: D
Q19] Which Is Not A Computer Classification?
A) Mainframe
B) Max frame
C) Mini
D) Notebook
ANS: B
Q20] The Control Unit Of A Microprocessor
A) Stores Data In The Memory
B) Accepts Input Data From Keyboard
C) Performs Arithmetic/Logic Function
D) None Of Above
ANS: D](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-77-320.jpg)
![COMPUTERFUNDAMENTALS
Q21] Which Of The Following Is Internal Memory?
A) Disks
B) Pen Drives
C) RAM
D) CDS
ANS: C
Q22] Which Operation Is Not Performed By Computer?
A) Inputting
B) Processing
C) Controlling
D) Understanding
ANS: D
Q23] Floppy Disks Which Are Made From Flexible Plastic Material Are Also Called?
A) Hard Disks
B) High-Density Disks
C) Diskettes
D) Templates
ANS: C
Q24]The Magnetic Storage Chip Used To Provide Non-Volatile Direct Access
Storage Of Data And That Have No Moving Parts Are Known As
A) Magnetic Core Memory
B) Magnetic Tape Memory
C) Magnetic Disk Memory
D) Magnetic Bubble Memory
ANS: B](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-78-320.jpg)
![COMPUTERFUNDAMENTALS
Q25]A Collection Of Related Instructions Organized For A Common Purpose Is
Referred To As
A) File
B) Database
C) Program
D) None Of Above
ANS: C
Q26]Plotter Accuracy Is Measured In Terms Of Repeatability And
A) Buffer Size
B) Resolution
C) Vertical Dimensions
D) Intelligence
ANS: B
Q27] Computer Instructions Written With The Use Of English Words Instead Of
Binary Machine Code Is Called
A) Mnemonics
B) Symbolic Code
C) Gray Codes
D) OPCODE
ANS: B
Q28] Which Language Is Directly Understood By The Computer Without Translation
Program?
A) Machine Language
B) Assembly Language
C) High Level Language
D) None Of Above
ANS: A](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-79-320.jpg)
![COMPUTERFUNDAMENTALS
Q29] On Which Aspect The Analog Computers Are Better Than Digital?
A) Speed
B) Accuracy
C) Reliability
D) Automatic
ANS: B
Q30] Which Of The Following Processors Use RISC Technology?
A) 486dx
B) Power PC
C) 486sx
D) 6340
ANS: B
Q31] Which of The Following Machine Was Not Invented By Charles Babbage?
A) Tabulating Machine
B) Analytical Engine
C) Difference Engine
D) Both C And D
ANS: A
Q32]. How Many Numbers Could ENIAC Store In Its Internal Memory
A) 100
B) 20
C) 80
D) 40
ANS: B](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-80-320.jpg)
![COMPUTERFUNDAMENTALS
Q34] The Subject Of Cybernetics Deals With The Science Of
A) Genetics
B) Control And Communication
C) Molecular Biology
D) Biochemistry
ANS: B
Q33] Why ABC Is Considered Electro-Mechanical Computer?
A) Because It Was Invented Before Electronic Computers Were Developed
B) Because There Are Wheels, Drums, Bars To Rotate And Move To Produce Result
C) Because They Use The Flow Of Electrons In Different Component
D) None Of Above
ANS: B
Q24]Binary Circuit Elements Have
A) One Stable State
B) Two Stable State
C) Three Stable State
D) None Of Above
ANS: B
Q35]Which Of The Following Is Used For Manufacturing Chips?
A) Control Bus
B) Control Unit
C) Parity Unit
D) Semiconductor
ANS: B](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-81-320.jpg)
![COMPUTERFUNDAMENTALS
Q36] Which Of The Following Is Not A Micro Computer?
A) Laptop Pcs
B) Tablet Pcs
C) Desktop Pcs
D) None Of Above
ANS: D
Q37] The Value Of Each Bead In Earth Is
A) 1
B) 3
C) 5
D) 7
ANS: D
Q38] When Did John Napier Develop Logarithm?
A) 1416
B) 1614
C) 1641
D) 1804
ANS: B
Q39] Which Of The Following Terms Is The Most Closely Related To Main Memory?
A) Non Volatile
B) Permanent
C) Control Unit
D) Temporary
ANS: D](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-82-320.jpg)
![COMPUTERFUNDAMENTALS
Q40] Which Was the World’s First Minicomputer And When Was It Introduced?
A) PDP-I, 1958
B) IBM System/36, 1960
C) PDP-II, 1961
D) VAX 11/780, 1962
ANS: A
Q41]A Group Of Magnetic Tapes, Videos Or Terminals Usually Under The Control Of
One Master Is
A) Cylinder
B) Surface
C) Track
D) Cluster
ANS: D
Q42]The Word Length Of A Computer Is Measured In
A) Bytes
B) Millimeters
C) Meters
D) Bits
ANS: D
Q43] What Type Of Memory Is Not Directly Addressable By The CPU And Requires
Special Softw3are Called EMS (Expanded Memory Specification)?
A) Extended
B) Expanded
C) Base
D) Conventional
ANS: D](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-83-320.jpg)
![COMPUTERFUNDAMENTALS
Q44] Which Unit Holds Data Permanently?
A) Input Unit
B) Secondary Storage Unit
C) Output Unit
D) Primary Memory Unit
ANS: B
Q45] Before A Disk Can Be Used To Store Data. It Must Be_______
A) Formatted
B) Reformatted
C) Addressed
D) None Of The Above
ANS: B
Q46]Computer System Comprises Of Major Units
A) Input Unit, Output Unit, Control Unit
B) Input Unit, Output Unit, Control Unit And Storage
C) Input Unit, Output Unit, Central Processing Unit And Storage Unit
D) Input, Output And Storage Units
ANS: C
Q47]The First General Purpose Electronic Digital Computer In The World Was
A) UNIVAC
B) EDVAC
C) ENIAC
D) All Of Above
ANS; A](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-84-320.jpg)
![COMPUTERFUNDAMENTALS
Q48]. Signals Can Be Analog Or Digital And A Computer That Processes The Both
Type Of Signals Is Known As
A) Analog Computer
B) Digital Computer
C) Hybrid Computer
D) Mainframe Computer
ANS: C
Q49]. High Level Language Is Also Called
A) Problem Oriented Language
B) Business Oriented Language
C) Mathematically Oriented Language
D) All Of The Above
ANS: D
Q50]. Human Beings Are Referred To As Homo- sapiens, Which Device Is Called
Silicon Sapiens?
A) Monitor
B) Hardware
C) Robot
D) Computer
ANS: D](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-85-320.jpg)
![COMPUTERFUNDAMENTALS
4. MOTHERBOARD[INTERNALCOMPONENTS]
The motherboard serves as a single platform to connect all of the parts of a
computer together.
A motherboard connects CPU, memory, hard drives, optical drives, video card,
sound card, and other ports and expansion cards directly or via cables.
It can be considered as the backbone of a computer.
4.A.Mother Board Top View](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-86-320.jpg)









![COMPUTERFUNDAMENTALS
8. PCI SLOT [Peripheral Component Interconnect]
Since The First Pc, Launched In 1981,
The Computer Has Had Expansion Slots Where You Can Install Additional Cards To
Add Capabilities Not Available On The Motherboard Of The Computer.
Currently, The Most Common Type Of Expansion Slot Available Is Called Pci Express.
In This Tutorial, You Will Learn Everything You Need To Know About This Kind Of
Connection: How It Works, Versions, Slots, And More.
Before Talking About The PCI Express, We Must Talk A Little Bit About The History
Of Pc Expansion Slots And Their Main Challenges, So You Can Understand What
Makes The PCI Express Different.
Below We List The Most Common Types Of Expansion Slots That Were Launched For The
Pc Throughout Its History:
ISA (Industry Standard Architecture)
MCA (Micro Channel Architecture)
EISA (Extended Industry Standard Architecture)
VLB (VESA Local Bus)
PCI (Peripheral Component Interconnect)
PCI-X (Peripheral Component Interconnect Extended)
AGP (Accelerated Graphics Port)
PCI Express (Peripheral Component Interconnect Express)
4.3.O.Pci ,Agp&Isa Slots On Mother Bord 4.3.P.Pci Slots](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-96-320.jpg)


![COMPUTERFUNDAMENTALS
11. ACCELERATED GRAPHICS PORT [AGP SLOT]
Stands For "ACCELERATED GRAPHICS PORT." AGP Is A Type Of Expansion Slot
Designed Specifically For Graphics Cards.
It Was Developed In 1996 As An Alternative To The PCI Standard. Since The AGP
Interface Provides A Dedicated Bus for Graphics Data, AGP Cards Are Able To
Render Graphics Faster Than Comparable PCI Graphics Cards.
Like PCI Slots, AGP Slots Are Built Into A Computer's Motherboard.
They Have A Similar Form Factor To PCI Slots, But Can Only Be Used For Graphics
Cards.
Additionally, Several AGP Specifications Exist, Including AGP 1.0, 2.0, and 3.0, Which
Each Use A Different Voltage.
Therefore, AGP Cards Must Be Compatible With The Specification Of The AGP Slot
They Are Installed In.
Since AGP Cards Require An Expansion Slot, They Can Only Be Used In Desktop
Computers.
4.3.S.AGP Slot On Mother Board](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-99-320.jpg)




![COMPUTERFUNDAMENTALS
Questions on Computer Mother Board
Q1 ] UNIVAC IS
A. Universal Automatic Computer
B. Universal Array Computer
C. Unique Automatic Computer
D. Unvalued Automatic Computer
Correct Answer: A. Universal Automatic Computer
Explanation: There Are No Computers With The Name As In Other Options. UNIVAC Was
The First General Purpose Electronic Digital Computer Designed For Commercial Use,
Produced By Universal Accounting Company Of John M And JP Eckert In 1951.
Q2] CD-ROM Stands For
A. Compactable Read Only Memory
B. Compact Data Read Only Memory
C. Compactable Disk Read Only Memory
D. Compact Disk Read Only Memory
Correct Answer: D. Compact Disk Read Only Memory
Explanation: There Are No Objects With The Name As In Other Options. CD-ROM Is A Non-
Volatile Optical Data Storage Medium Using The Same Physical Format As Audio Compact
Disk, Readable By A Computer With A CD-ROM Drive. The Standard 12 Cm Diameter CD-
ROM Store About 660 Megabytes.
Q3] ALU Means
A. Arithmetic Logic Unit
B. Array Logic Unit
C. Application Logic Unit
D. None Of Above
Correct Answer: A. Arithmetic Logic Unit
Explanation: ALU Is A Unit In Central Processing Unit In A Computer System That Is](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-104-320.jpg)
![COMPUTERFUNDAMENTALS
Responsible For Arithmetic Calculations And Logical Operations. Apart From ALU, The CPU
Contains MU (Memory Unit) And CU (Control Unit).
Q4] VGA Is
A. Video Graphics Array
B. Visual Graphics Array
C. Volatile Graphics Array
D. Video Graphics Adapter
Correct Answer: A. Video Graphics Array
Explanation: VGA Is A Type Of Graphics Adapter. Graphic Adapter Is An Electronic board
That Controls The Display Of A Monitor. This Device Helps the Motherboard to Work with
the Monitor and In VGA and SVGA the Last Letter ‘A’ Stands For ‘Array’ Whereas In MDA,
CGA, MCGA the Last Letter ‘A’ Stands For ‘Adapter
Q5] I BM 1401 Is
A. First Generation Computer
B. Second Generation Computer
C. Third Generation Computer
D. Fourth Generation Computer
Correct Answer: B. Second Generation Computer
Explanation: IBM 1401 Is A Second Generation Computer And Is The First Computer To
Enter Nepal In 2028 BS For Census. Government Of Nepal Had Brought This Computer On
Rent And Later Purchased For Data Processing In Bureau Of Statistics. After This Computer,
Another ICL 2950/10, A British Computer, Was Purchased By The Fund Of UNDP And
UNFPA For The Census Of 2038 BS Is Second Computer In NEPAL.
Q6] MSI Stands For
A. Medium Scale Integrated Circuits
B. Medium System Integrated Circuits](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-105-320.jpg)
![COMPUTERFUNDAMENTALS
C. Medium Scale Intelligent Circuit
D. Medium System Intelligent Circuit
Correct Answer: A. Medium Scale Integrated Circuits
Explanation: After The Invention Of IC Chips The Development Of Computers Plunged Into
Next Phase. Small Scale Integration And Medium Scale Integration (SSI And MSI) Were
Used In Third Generation Of Computers And Large Scale Integration And Very Large Scale
Integration (LSI And VLSI) Are Being Used In Fourth Generation Of Computers. People Are
Now Expecting ULSI (Ultra Large Scale Integration) Circuits To Be Used For Fifth
Generation Computers.
Q7] The Capacity Of 3.5 Inch Floppy Disk Is
A. 1.40 MB
B. 1.44 GB
C. 1.40 GB
D. 1.44 MB
Correct Answer: D. 1.44 MB
Explanation: Microfloppy Disks (3.5 Inch) If It Is High Density (MF2HD) Can Store 1.44 MB
And If It Is Low Density (MF2DD), It Can Store 720 KB. Mini Floppy Disks (5.25 Inch) If It Is
High Density (MD2HD) Can Store 1.2 MB And Low Density (MD2DD) Stores 360 KB Of
Data.
Q8.]The First Computer Introduced In Nepal Was
A. IBM 1400
B. IBM 1401
C. IBM 1402
D. IBM1402
Correct Answer: B. IBM 1401
Explanation: IBM 1401, A Second Generation Computer Was Brought In Nepal By The
government Of Nepal Paying One Lakh And Twenty Five Thousands Per Month To Use In
The Census In 2028 B.S. Before This Computer, Nepal Was Using A Calculating Device
Called Facet For Statistical Tasks.](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-106-320.jpg)
![COMPUTERFUNDAMENTALS
Correct Answer: B. Wide Area Network
Explanation: There Are Three Different Classes Of Computer Network 1. LAN – Local Area
Net Work 2. MAN: Metropolitan Net Work 3. WAN: Wide Area Network
Q9] WAN Stands For
A. WAP Area Network
B. Wide Area Network
C. Wide Array Net
D. Wireless Area Network
Q10] MICR Stands For
A. Magnetic Ink Character Reader
B. Magnetic Ink Code Reader
C. Magnetic Ink Cases Reader
D. None
Correct Answer: A. Magnetic Ink Character Reader
Explanation: MICR (Magnetic Ink Character Reader) Is Kind Of Scanner That Can Scan And
Identify The Writing Of Magnetic Ink. This Device Is Used In Banks To Verify Signatures In
Checks.
Q11] Which of the Following Is Not Real Security and Privacy Risk?
A. Hackers B. Spam C. Viruses D. Identity Theft
Correct Answer: B
Q12] Who Is Known As Father of Computers
A. Lord Wellington B. Charles Babbage C. Jack Kilby D. Bill Gates
Correct Answer: B
Q13 ] ROM Stands For ?](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-107-320.jpg)
![COMPUTERFUNDAMENTALS
A. Random Only Memory B. Readable Only Memory C. Read Only Memory D. Random
Other Memory
Correct Answer: C
Q14] N -TH First Generation Computers Built Between (1945 -1956) What Was Used For
Calculations
A. Transistors B. Integrated Circuits C. Very Large Scale Integration D. Vacuum Tubes
Correct Answer: D
Q15] UPS Stands For?
A United Power Solutions B. Uninterrupted Power Supply C. Uninterrupted Power Solution
D. Untied Power Supply
Correct Answer: D
Q16] The Number System Based On "0" And "1" Only Is Known As
A. Binary System B Barter System C. Number System D. HEXA Decimal System
Q19 Which of the Following Is an Advantage Of Using A Local Area Network (LAN)?
A. Protects Against Virus Infection B. Shared Resources C. Data Security D. Prevents
Computer Misuse
Correct Answer: B
Q17] Server Is A?
A. Multimedia CD B. Personal Computer C. Multi – User Computer D. Integrated
Data Management
Correct Answer: B](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-108-320.jpg)
![COMPUTERFUNDAMENTALS
Q18] What Is Internet?
A. Network of All Computers in a Company Not Connected To Web
B. Network of All Computers in a Company Not Connected To Web
C. Global Network of Computers
Correct Answer: C
Q19] Which of the Following Is Not an Integral Part of Computer
A. CPU B. Mouse C. Monitor D. UPS
Correct Answer: A
Q20] RAM Stands For?
A. Revolutionary Access Memory B. Relational Access Memory C. Random Access Memory
D. Rotational Access Memory
Correct Answer: C](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-109-320.jpg)

![COMPUTERFUNDAMENTALS
5.1] SYSTEM SOFTWARE
The system software is collection of programs designed to operate, control, and
extend the processing capabilities of the computer itself.
System software is generally prepared by computer manufactures.
These software products comprise of programs written in low-level languages
which interact with the hardware at a very basic level.
System software serves as the interface between hardware and the end users.
Some examples of system software are Operating System, Compilers, Interpreter,
and Assemblers etc.
5. 1.A.Examples Of System Software
Features Of System Software Are As Follows:
Close To System
Fast In Speed
Difficult To Design
Difficult To Understand
Less Interactive
Smaller In Size
Difficult To Manipulate
Generally Written In Low-Level Language](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-111-320.jpg)
![COMPUTERFUNDAMENTALS
System Software Can be classified into Following Types
1] Operating system
2] System development software
3] Utility programs
5.1.1. OPERATING SYSTEM
Operating System is Software That Communicates With The Hardware And Allows
Other Programs To Run.
It is comprised of system/The Fundamental Files Your Computer Needs To Boot
up And Function.
Every Desktop Computer, Tablet, And Smartphone Includes An Operating System
That Provides Basic Functionality For The Device.
Common Desktop Operating Systems Include windows, Mac OS X, And Linux. While
Each OS Is Different, They All Provide A Graphical User Interface, Or GUI, That
Includes A Desktop And The Ability To Manage Files And Folders.
They Also Allow You To Install And Run Programs Written For The Operating
System.
While Windows And Linux Can Be Installed On Standard PC Hardware, Mac OS X
Can Only Run On Macintosh Computers.
Therefore, The Hardware You Choose Affects What Operating System(S) You Can
Run.
5.1.1. A.Examples of Operating System](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-112-320.jpg)
![COMPUTERFUNDAMENTALS
5.1.2. SYSTEM DEVELOPMENT SOFTWARE
Software Development Is The Computer Programming, Documenting, Testing,
And Bug Fixing Involved In Creating And Maintaining
Applications And Frameworks Involved In A Software Release Life Cycle And
Resulting In A Software Product.
The Term Refers To A Process Of Writing And Maintaining The Source Code, But In
A Broader Sense Of The Term.
It Includes All That Is Involved Between The Conception Of The Desired Software
Through To The Final Manifestation Of The Software, Ideally In A Planned
Therefore, Software Development May Include Research, New Development,
Prototyping, Modification, Reuse, Re-Engineering, Maintenance, Or Any Other
Activities That Result In Software Products.[2]
5.1.2. A.Software Development Cycle](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-113-320.jpg)






















![COMPUTERFUNDAMENTALS
6.2. E.Network Operating System [NOS]
5. REALTIMEOPERATINGSYSTEM
Real Time System Is Defines As A Data Processing System In Which The Time
Interval Required To Process And Respond To Inputs Is So Small That It Controls
The Environment.
Real Time Processing Is Always On Line Whereas On Line System Need Not Be Real
Time.
The Time Taken By The System To Respond To An Input And Display Of Required
Updated Information Is Termed As Response Time.
So In This Method Response Time Is Very Less As Compared To the Online
Processing.](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-136-320.jpg)




![COMPUTERFUNDAMENTALS
PROCESSCONTROLBLOCK[PCB]
Each Process Is Represented In the Operating System by A Process Control Block
(PCB) Also Called A Task Control Block.
PCB Is The Data Structure Used By The Operating System. Operating System
Groups All Information That Needs About Particular Process.
PCB Contains Many Pieces Of Information Associated With A Specific Process
Which Are Described Below.
S.N. Information & Description
1 Pointer
Pointer Points To Another Process Control Block. Pointer Is Used For
Maintaining The Scheduling List.
2 Process State
Process State May Be New, Ready, Running, Waiting And So On.
3 Program Counter
Program Counter Indicates The Address Of The Next Instruction To Be
Executed For This Process.
4 CPU Registers
CPU Registers Include General Purpose Register, Stack Pointers, Index
Registers And Accumulators Etc. Number Of Register And Type Of Register
Totally Depends Upon The Computer Architecture.
5 Memory Management Information
This Information May Include The Value Of Base And Limit Registers, The Page
Tables, Or The Segment Tables Depending On The Memory System Used By The
Operating System. This Information Is Useful For DE allocating The Memory
When The Process Terminates.](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-141-320.jpg)


































![COMPUTERFUNDAMENTALS
Deadlock Recovery
Once A Deadlock Is Detected, You Will Have To Break The Deadlock.
It Can Be Done Through Different Ways, Including, Aborting One Or More Processes
To Break The Circular Wait Condition Causing The Deadlock And Preempting
Resources From One Or More Processes Which Are Deadlocked.
8.1.4. Banker’s Algorithm
This Approach To The Deadlock Problem Anticipates Deadlock Before It Actually
Occurs.
This Approach Employs An Algorithm To Access The Possibility That Deadlock
Could Occur And Acting Accordingly.
This Method Differs From Deadlock Prevention, Which Guarantees That Deadlock
Cannot Occur By Denying One Of The Necessary Conditions Of Deadlock.
If The Necessary Conditions For A Deadlock Are In Place, It Is Still Possible To Avoid
Deadlock By Being Careful When Resources Are Allocated. Perhaps The Most Famous
Deadlock Avoidance Algorithm, Due To DIJKSTRA [1965], Is The Banker’s Algorithm. So
Named Because The Process Is Analogous To That Used By A Banker In Deciding If A Loan
Can Be Safely Made.
Banker’s Algorithm
In This Analogy
Customers ≡ Processes
Units ≡
Resources, Say,
Tape Drive
Banker ≡
Operating
System](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-176-320.jpg)



























































![COMPUTERFUNDAMENTALS
10.8. DISK SCHEDULING ALGORITHM
1. First Come First Served Disk Scheduling [FCFS]
In FCFS, we process the requests in the order they arrive, without regard to the current
position of the heads.
10.8. A. illustration shows total head movement of 640 cylinders](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-237-320.jpg)



![COMPUTERFUNDAMENTALS
10.9. RAID [Redundant Array of Independent disks]
RAID – multiple disk drives provides reliability via redundancy.
Redundant Array of Independent Disks (RAID)
RAID is arranged into six different levels.
Several improvements in disk-use techniques involve the use of multiple disks
working cooperatively.
Disk striping uses a group of disks as one storage unit.
RAID schemes improve performance and improve the reliability of the storage
system by storing redundant data.
o Mirroring or shadowing keeps duplicate of each disk.
o Block interleaved parity uses much less redundancy](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-241-320.jpg)
![COMPUTERFUNDAMENTALS
RID levels
Raid levels 0 through 2
Backup and parity drives are shaded
RID levels [continued]
Raid levels 3 through 5
Backup and parity drives are shaded](https://image.slidesharecdn.com/computerfunadamentals-171107085708/85/Computer-funadamentals-242-320.jpg)
























