Computer networks unit iii
- 1. RMK College of Engineering and Technology CS 6551 Computer Networks Department of Electronics and Communication Engineering
- 2. Unit 3 Routing Prepared by Jai Ganesh S Asst.Professor - ECE
- 3. Syllabus • Routing • RIP • OSPF • Metrics • Switch basics • Global internet • Areas • BGP • IPV6 • Multicast Addresses • Multicast Routing • DVMRP • PIM
- 4. Routing
- 5. Introduction • Routing is the most important task in the networks to forward packets from source to destination • The devices like switches and routers take the responsibility of delivering the packets to right destination • This is accomplished by referring to their forwarding table and routing table respectively • The fundamental problem is “how routers acquire the information about the network in their routing table?”
- 6. Understanding – Routing in Real time
- 7. Understanding – Routing in Networks
- 8. Representing Network as a graph • The routing process is well understood by representing a network as a graph. • Each node on the network may represent any host or switch or router. • Each link on the network is associated with a cost. • The ultimate work of the router is to find the path with the lowest cost between any nodes. • These are performed by routing algorithm or routing protocols.
- 9. Types of routing protocols
- 10. Distance Vector Algorithm • The idea behind the DVR is that it maintains a table with distance to every node Assumptions: • Each node contains the cost of link to the other node. These cost are configured by the administrator. • The link that is down is assign with infinite cost.
- 11. Stages in DVR • There are 3 stages in DVR Initialization Sharing Updating
- 12. 1. Initialization Consider the given example network Each node creates an initialization table with the cost to reach all other nodes. Since they do not know about all the nodes, they create only for the neighboring node.
- 13. 2. Sharing From the given network Node A do not know about Node E but Node C knows about Node E. Similarly Node C do not know about Node D but Node A knows about Node D Thus by sharing Node A’s Table to Node C , Node C learns about Node D. By sharing Node C’s Table to Node A , Node A learns about Node E
- 14. 3. Updating Each and every node in the network updates its own table from the table received from the neighbor nodes.Updating process happens in 3 steps 1. Receiving node need to add the cost between itself (A) and sending node(C). (Cost of A C is 2)2. Receiving node have to add the name of the sending node to each row as third column. This acts as the next node information when the table is updated 3. The receiving node compares each row of its old table with the modified table. If the next node entry is different, then the receiving node chooses the lowest value. If the there is a tie, then old value is maintained After several sharing and updates process all nodes in the network becomes stable and knows about the path to reach any node on the network.
- 15. When to update?? • 2 methods • Periodic update • Triggered update
- 16. Instability problem • 2 node instability • 3 node instability
- 18. Remedies for 2 node instability • Defining infinity • Split horizon • Split horizon with poison reverse
- 20. Routing Information Protocol • Considerations • Only networks have routing table not networks • Metric used in Hop Count • Infinity is 16 • Next node column defines the address of the router to reach the destination
- 21. Example scenario
- 22. Link State Routing Alg
- 23. Steps in Link state alg • Reliable dissemination of LSP • Creation of LSP • Flooding of LSP • Calculation of Routes from all received LSP • Formation of Shortest path tree for each node • Calculation of Routing Table
- 24. Creation of LSP • LSP are created with 4 main information • Node identity • The list of links • Sequence numbers • Age (TTL)
- 25. Flooding • Steps in flooding • Creating node floods the LSP • Receiving node compares the LSP with old LSP • If received is old – discarded • If received is new – old is discarded and new LSP is Flooded • Old and new are differentiated by sequence numbers • TTL helps in removing the old packets from the network.
- 26. Formation of shortest path • It is created by using “Dijkstra Algorithm”
- 29. Calculation of Routing Table
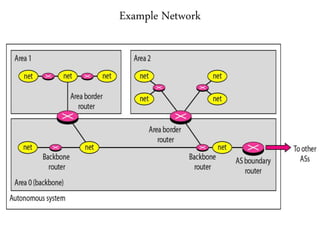
- 30. OSPF Protocol • One of the widely used link state routing is OSPF. • OSPF offers many features • Authentication of routing messages Routing messages are sent to all the nodes. Thus they should be authenticated. • Additional hierarchy This is the tool to make the system more scalable. It allows many networks to be grouped as “Areas” • Load balancing OSPF allows multiple routes with the same cost. Thus the traffic gets distributed all over the network.
- 31. Example Network
- 32. OSPF Header Format Describes the version of the OSPFDescribes the total length of the mesasage Used to identify the sender of the message Used to identify in which area the node is locatedEntire packet except the data field is protected by check sum Defines the type of authentication 0 - No Authentication 1 – simple password 2 – cryptographic authentication Data
- 33. LSP Advertising Packet • The basic building block of OSPF is creating the link state packet and advertising them. There are 2 types of advertisements. • Router should advertise the LSP packets to the directly connected networks • Router should advertise information about the loss of link throughout the network.
- 34. LSP Advertisement Packet Format They are equal to the TTL.Defines the router that created the advertisementThey are used to detect the old or duplicate LSA’sThey are used to protect the entire advertisement packet.It defines the length of the complete LSA in bytes Link ID and Link Data They are used to identify the link along with the router IDThey are used to define the cost of the link It defines the type of the link. There are 4 types of links 1. Point to point link 2. Transient link 3. Stub link 4. Virtual link It is used for defining the type of service. It is possible to assign different cost for the same route based on the type of service
- 35. Metrics • The metrics that we have discussed so far were assumed that they are a known factor for executing the algorithm. • Drawbacks in simply assuming the metric • They do not distinguish links on latency basis • They do no distinguish links in capacity basis • They do no distinguish links based on their current load.
- 36. Solution • There are several methods evolved to calculate the metrics. • But all we need is to test the various methods on a common flat form. • One such flat form is known as ARPANET • Further details about the ARPANET can be studied in the given link. https://en.wikipedia.org/wiki/ARPANET
- 37. 3 stages of ARPANET • Original ARPANET • New Routing Mechanism • Revised ARPANET Routing Metric • Each version uses different logics to compute the metric.
- 38. Original ARPANET • In this method the metric is computed based on the “ Number of packets queued for transmission on each link” • Link with 10 packets queued for the transmission is assigned larger cost than the link which has 5 packets queued for transmission.
- 39. New Routing Mechanism • In this mechanism both latency and bandwidth is considered for calculation of metrics. • The arrival time and depart time are captured from the time stamp added to the packet. • Delay is computed as • Delay = (depart time – arrival time) + Transmission time + latency. • Based on this delay the cost will be assigned.
- 40. Revised ARPANET Routing Metric • The major changes done in this versions are • Compress the dynamic range of metric considerably • Smoothen the variation of the metric with time • Compression is achieved by taking the function of measured utilization , link type and link speed. • Smoothing can be achieved in 2 ways • Averaging the delay instead of taking the trials • Setting up a hard limit on how much the metric could change from one cycle to another cycle.
- 41. Switch Basics • The conceptual structure of the switch is shown in the figure.
- 42. 1. Control processor • This block is responsible for moving the data from interface to memory without the intervention of the CPU
- 43. 2. Ports • The ports communicates with the outside worlds • It contains fiber optic receivers, buffers for holding the packets that are to be transmitted. • In case of virtual circuit, the port contains the virtual circuit identifier • In case of ethernet, the port contains the forwarding table .
- 44. 3. Fabrics • They are very Basic and important function of a switch. • They are responsible for forwarding the packets from input port to output port with minimal delay and max throughput. • Types of Fabrics: • Shared Bus: • They are found in conventional processors. The bus is shared because in the conventional system the bus bandwidth determines the throughput. • Shared Memory: • They are found in the modern switches. They have common memory for both input and output port. Here the memory decides the throughput. • Cross Bar: • They are the matrix of pathways that can be configured to connect any input port to any output port. • Self Routing: • Self routing fabrics relay on some information in a pack header to direct each packet to its correct destination.
- 45. Global Internet
- 46. Some Techniques to address the Problems • Areas • Border gateway Protocol • IP Version 6
- 47. Areas
- 48. Back bone Area or Area 0
- 49. • Inter domain Routing • Intra domain Routing BGP
- 51. Types of autonomous systems • There are 3 types • Stub autonomous system • This type of as carries only local traffic. Ex. Small corporation • Multi homed autonomous system • They carries traffic for more than 2 AS. Ex. Large Corporation • Transit autonomous system • They carry traffic for more than 1 AS. This carries both transit traffic and local traffic.. Ex. Back bone Providers
- 52. Challenges in Intra domain routing • It should focus on finding the non looping path • Backbone router should be able to route the packet anywhere in the network • Varying nature of the AS should be addressed • Multiple ISP’s may create a problem of reliability coz, different ISP have Different Policies.
- 53. Path Vector Routing • 3 stages • Initialization • Sharing • Updating
- 54. 1.Initialization
- 55. 2. Sharing • A1 shares with B1 and C1 • B1 shares with A1 and C1 • C1 shares with A1, B1, and C1 • D1 shares with C1
- 56. 3.Updating
- 57. Looping problem
- 60. DVMRP • Distance Vector Multicast Routing Protocol. • Sharing of routing tables with the neighboring routers are not possible here. • Each router have to create routing table from the scratch. Based on the information of the uni cast routing. • This can be achieved in 4 methods: • Flooding • Reverse Path Forwarding (RPF) • Reverse Path Broadcasting (RPB) • Reverse Path Multicasting (RPM)
- 61. 1. Flooding • default flooding concept. • Router floods the all the received packets to all the ports, except the incoming port. • Drawbacks: • By this method only broad casting is achieved not the multicasting. • A router may receive multiple packets.
- 62. Reverse path Forwarding (RPF) • In this method the packets are sent only to the shortest path. • This shortest path information is obtained from the unicast routing tables. • The router will not forward the table if the source address and destination address are same. (in case of receiving multiple copies)
- 65. Ipv6 header
- 66. End of Unit - 3
Editor's Notes
- #13: View in Slide Show Mode