Create a Data Encryption Strategy using ADE
- 1. 1 Create a Data Encryption Strategy using ADE Ben Peach, Technical Support Engineer
- 2. 2 Credits and Acknowledgements Presenter • Ben Peach, Technical Support Engineer Developers • Jing Cui, Principle Software Engineer (US) • Jianhua Zhou, Software Engineer III (US) Support Subject Matter Experts • Ben Peach, Technical Support Engineer (Aus) • John Jenkins, Technical Support Engineer (UK) • Liam Collier, Technical Support Engineer (US) ©2015 Rocket Software, Inc. All Rights Reserved.
- 3. 3 Abstract Automatic Data Encryption (ADE) is a security tool available for UniData and UniVerse. This session will concentrate on more real world topics rather than ‘how to’ . The intent is to provide the knowledge required for creating a strategy for your application and customers. ©2015 Rocket Software, Inc. All Rights Reserved.
- 4. 4 Agenda Overview Compliance regulations Deciding what to encrypt High Availability and Disaster Recovery Migration Client-side applications Best practices ©2015 Rocket Software, Inc. All Rights Reserved.
- 5. 5 Overview Encrypts data in its resting state Components • Master key • Encryption keys • Wallets • Algorithms • Key Store • Metadata ©2015 Rocket Software, Inc. All Rights Reserved. Encryption modes • WHOLERECORD • Field/Attribute level • @ID • Index
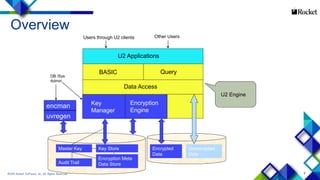
- 6. 6 Unencrypted Data Master Key Key Store Encryption Meta Data StoreAudit Trail encman Encrypted Data Other UsersUsers through U2 clients DB /Sys Admin uvregen U2 Applications BASIC Query Data Access Key Manager Encryption Engine U2 Engine Overview ©2015 Rocket Software, Inc. All Rights Reserved.
- 7. 7 Overview TCL commands - Key • CREATE.ENCRYPTION.KEY • DELETE.ENCRYPTION.KEY • GRANT.ENCRYPTION.KEY • REVOKE.ENCRYPTION.KEY • CHANGE.ENCRYPTION.PASSWORD • LIST.ENCRYPTION.KEY • ACTIVATE.ENCRYPTION.KEY • DEACTIVATE.ENCRYPTION.KEY ©2015 Rocket Software, Inc. All Rights Reserved.
- 8. 8 Overview TCL commands – Wallet • CREATE.ENCRYPTION.WALLET • DELETE.ENCRYPTION.WALLET • GRANT.ENCRYPTION.KEY • REVOKE.ENCRYPTION.KEY • WALLET.ADD.KEY • WALLET.REMOVE.KEY • CHANGE.ENCRYPTION.PASSWORD • LIST.ENCRYPTION.WALLET • ACTIVATE.ENCRYPTION.KEY • DEACTIVATE.ENCRYPTION.KEY ©2015 Rocket Software, Inc. All Rights Reserved.
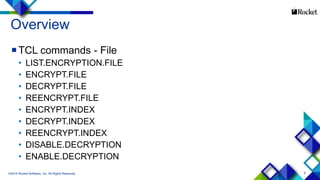
- 9. 9 Overview TCL commands - File • LIST.ENCRYPTION.FILE • ENCRYPT.FILE • DECRYPT.FILE • REENCRYPT.FILE • ENCRYPT.INDEX • DECRYPT.INDEX • REENCRYPT.INDEX • DISABLE.DECRYPTION • ENABLE.DECRYPTION ©2015 Rocket Software, Inc. All Rights Reserved.
- 10. 10 Overview Basic statements • ACTIVATEKEY/DEACTIVATEKEY • DISABLEDEC/ENABLEDEC • STATUS() • FILEINFO() OS level • encman • confcmd (UniData) / uvregen (UniVerse) XAdmin ©2015 Rocket Software, Inc. All Rights Reserved.
- 11. 11 Compliance Regulations PCI DSS HIPAA and HITECH GLBA and FFIEC FISMA Other regulations Can ADE help me adhere to security regulations? Yes! ©2015 Rocket Software, Inc. All Rights Reserved.
- 12. 12 MV Security Model Automatic Data Encryption: • Part of a much bigger picture. ©2015 Rocket Software, Inc. All Rights Reserved.
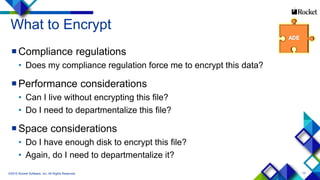
- 13. 13 What to Encrypt Compliance regulations • Does my compliance regulation force me to encrypt this data? Performance considerations • Can I live without encrypting this file? • Do I need to departmentalize this file? Space considerations • Do I have enough disk to encrypt this file? • Again, do I need to departmentalize it? ©2015 Rocket Software, Inc. All Rights Reserved.
- 14. 14 Compliance Regulations Know your application and data • Do I have to adhere to any compliance regulations? Know your regulation(s) inside out Compliance regulations will be the main driver of what is encrypted on your system ©2015 Rocket Software, Inc. All Rights Reserved.
- 15. 15 Performance Any additional feature on a file will add processing time ADE is no exception • Record Level = 1 pass • Attribute Level = 1 pass per encrypted attribute • @ID = 1 additional pass • Encrypted Index = 1 additional pass per encrypted index Added processing time per record imperceptible • Only noticeable in large batches ©2015 Rocket Software, Inc. All Rights Reserved.
- 16. 16 Space Encryption almost always grows the data Data is padded to make 32-bit/64-bit blocks • Independent of algorithm ‘strength’ More encrypted ‘segments’ = more padding • Record level only padded once or not at all Better for larger records • Attribute level padded for each encrypted field ©2015 Rocket Software, Inc. All Rights Reserved.
- 17. 17 High Availability and Disaster Recovery Backups – business data Backups – encryption key data Local and Offsite storage Failover Disaster recovery ©2015 Rocket Software, Inc. All Rights Reserved.
- 18. 18 Backups Important regardless of ADE Ensure encryption components backed up • ENCINFO and KEYSTORE • product.info (UniData) and .uvconfig (UniVerse) • Loss of keys or master key may lead to data loss Verify and test backups ADE key requirement for archived data • If you change a key, archived data unreadable • Must save a snapshot of key setup ©2015 Rocket Software, Inc. All Rights Reserved.
- 19. 19 Local and Offsite Storage Best of both worlds • Local = Fast recovery • Offsite = Protection against physical threats Separate master key from data • Fire safe, escrow company, another server Master key doesn’t need to be ‘known’ to access data • Needs to be present in product.info/.uvconfig • Only needs to be entered for admin tasks • If you lose it/forget it, decrypt everything asap ©2015 Rocket Software, Inc. All Rights Reserved.
- 20. 20 Failover Depends greatly on method used Target system must have same master key and keys • Can change passwords • CHANGE.ENCRYPTION.PASSWORD Data can be ‘synced’ by front and back ends • Activate key > copy clear text > write to encrypted file • Move encrypted files at OS level Keys can be ‘synced’ by front and back ends • encman –export/import • Move ENCINFO/KEYSTORE at OS level – requires retag ©2015 Rocket Software, Inc. All Rights Reserved.
- 21. 21 U2 Replication Master key and keys must match on publisher and subscriber • Passwords can be different Replication is not ADE aware • It doesn’t need to be • The two work perfectly side by side, but not together • Encrypt/decrypt file must be done ‘outside’ of Replication Risk of clear and cipher text in same file, one will be inaccessible • Same applies to other features RFS, Transaction Logging etc. ©2015 Rocket Software, Inc. All Rights Reserved.
- 22. 22 Disaster Recovery Get the master key back • product.info (UniData) • .uvconfig (UniVerse • confcmd –m (UniData) • uvregen –m (UniVerse) Get the encryption keys back • ENCINFO/KEYSTORE • encman –import • encman –retag ©2015 Rocket Software, Inc. All Rights Reserved.
- 23. 23 Migration XAdmin and encman Export/Import • Migrates key and metadata information • Added at UniData 7.2 and UniVerse 10.3 • Platform independent, encrypted • Password protected (optional) • Can change key owner • Can change file path Retag • Use after copying KEYSTORE/ENCINFO to new server • Added security, ties key store to server ©2015 Rocket Software, Inc. All Rights Reserved.
- 24. 24 Export/Import ©2015 Rocket Software, Inc. All Rights Reserved.
- 25. 25 Export/Import ©2015 Rocket Software, Inc. All Rights Reserved.
- 26. 26 Export/Import ©2015 Rocket Software, Inc. All Rights Reserved.
- 27. 27 Export/Import ©2015 Rocket Software, Inc. All Rights Reserved.
- 28. 28 Client-side Applications UniObjects.NET, UniObjects for Java, ODBC, JDBC, etc. UCI.config can hold wallet ID and password • Previously held clear text • UCI Editor in latest U2 Clients can now encrypt Any client that can be coded can activate a wallet • ACTIVATE_ENCRYPTION_WALLET() ©2015 Rocket Software, Inc. All Rights Reserved.
- 29. 29 Best Practices Master key Reach back Wallets Password policies Changing passwords Re-encryption Decryption disablement ©2015 Rocket Software, Inc. All Rights Reserved.
- 30. 30 Best Practices Master key • Role based administration • Not a single person • Password protection Split responsibility between two groups Reach back • Keep ‘snapshot’ of master key and keys • Separate from archived data • Clearly labelled ©2015 Rocket Software, Inc. All Rights Reserved.
- 31. 31 Best Practices Wallets • Single access point to a group of keys • Can grant or revoke access ad hoc • Changing a wallet does not affect data Password policies • XAdmin or encman • Range of configurables Length, Age, Complexity, Repetition • Master key, keys, and wallets ©2015 Rocket Software, Inc. All Rights Reserved.
- 32. 32 Best Practices ©2015 Rocket Software, Inc. All Rights Reserved.
- 33. 33 Best Practices ©2015 Rocket Software, Inc. All Rights Reserved.
- 34. 34 Best Practices Change passwords • Most compliance regulations require this • Master key passwords uvregen –p (UniVerse) confcmd –p (UniData) xAdmin • Encryption key/wallet passwords CHANGE.ENCRYPTION.PASSWORD XAdmin ©2015 Rocket Software, Inc. All Rights Reserved.
- 35. 35 Best Practices One pass re-encryption • Compliance regulations Re-key • REENCRYPT.FILE • XAdmin • Single command • Takes roughly 66% of the time Will vary depending on system, data, application ©2015 Rocket Software, Inc. All Rights Reserved.
- 36. 36 Best Practices Decryption disablement • DISABLEDEC - Basic • DISABLE.DECRYPTION – ECL/TCL • Performance Can save unnecessary passes through encryption engine Don’t need that field during this program? Don’t decrypt it • Privilege Departmentalized file may require different user privilege Decrypt what you have access to, disable the rest • Only available for Attribute Level mode ©2015 Rocket Software, Inc. All Rights Reserved.
- 37. 37 Summary Overview Compliance regulations Deciding what to encrypt High Availability and Disaster Recovery Migration Client-side applications Best practices And now… ©2015 Rocket Software, Inc. All Rights Reserved.
- 38. 38 Create Your Encryption Strategy Compliance: What MUST be encrypted Commercial security: What SHOULD be encrypted Encryption key management • Policies • Identities Key and password managers System administrators Data administrators Data users Departments ©2015 Rocket Software, Inc. All Rights Reserved.
- 39. 39 Create Your Encryption Strategy Other product features • Replication, RFS, TL etc. Document the strategy Test the complete strategy • Do not put live data at risk until you are sure • Someone not involved in the original process Implement Regularly check and verify your backups, HADR, etc. Revisit strategy annually and at major business changes ©2015 Rocket Software, Inc. All Rights Reserved.
- 40. 40 Additional Resources Links http://www.rocketsoftware.com http://en.wikipedia.org/wiki/Category:Security_compliance http://www.rocketsoftware.com/resource/u2-technical-documentation Need help? [email protected] support.rocketsoftware.com http://www.rocketsoftware.com/rocket-u2-professional-services-request ©2015 Rocket Software, Inc. All Rights Reserved.
- 41. 41 Disclaimer THE INFORMATION CONTAINED IN THIS PRESENTATION IS PROVIDED FOR INFORMATIONAL PURPOSES ONLY. WHILE EFFORTS WERE MADE TO VERIFY THE COMPLETENESS AND ACCURACY OF THE INFORMATION CONTAINED IN THIS PRESENTATION, IT IS PROVIDED “AS IS”, WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED. IN ADDITION, THIS INFORMATION IS BASED ON ROCKET SOFTWARE’S CURRENT PRODUCT PLANS AND STRATEGY, WHICH ARE SUBJECT TO CHANGE BY ROCKET SOFTWAREWITHOUT NOTICE. ROCKET SOFTWARE SHALL NOT BE RESPONSIBLE FOR ANY DAMAGES ARISING OUT OF THE USE OF, OR OTHERWISE RELATED TO, THIS PRESENTATION OR ANY OTHER DOCUMENTATION. NOTHING CONTAINED IN THIS PRESENTATION IS INTENDED TO, OR SHALL HAVE THE EFFECT OF: • CREATING ANY WARRANTY OR REPRESENTATION FROM ROCKET SOFTWARE(OR ITS AFFILIATES OR ITS OR THEIR SUPPLIERS AND/OR LICENSORS); OR • ALTERING THE TERMS AND CONDITIONS OF THE APPLICABLE LICENSE AGREEMENT GOVERNING THE USE OF ROCKET SOFTWARE. ©2015 Rocket Software, Inc. All Rights Reserved.
- 42. 42 Trademarks and Acknowledgements The trademarks and service marks identified in the following list are the exclusive properties of Rocket Software, Inc. and its subsidiaries (collectively, “Rocket Software”). These marks are registered with the U.S. Patent and Trademark Office, and may be registered or pending registration in other countries. Not all trademarks owned by Rocket Software are listed. The absence of a mark from this page neither constitutes a waiver of any intellectual property rights that Rocket Software has established in its marks nor means that Rocket Software is not owner of any such marks. Aldon, CorVu, Dynamic Connect, D3, FlashConnect, Pick, mvBase, MvEnterprise, NetCure, Rocket, SystemBuilder, U2, U2 Web Development Environment, UniData, UniVerse, and wIntegrate Other company, product, and service names mentioned herein may be trademarks or service marks of others. ©2015 Rocket Software, Inc. All Rights Reserved.
- 43. 43