Cryptography using rsa cryptosystem
- 1. Cryptography using RSA cryptosystem Saksham Saxena (2K13/EP/061) Samdish Arora (2K13/EP/062)
- 2. What is Cryptography? • Cryptography is the practice and study of techniques for conveying information securely. • The goal of cryptography is to allow the intended recipients of a message to receive the message securely.
- 3. Why do we need it? • Recently there has been a shift towards IT applications realized as embedded systems, large share of which are wireless, which makes the communication channel especially vulnerable and the need for security even more obvious. • Millions of electronic transactions are completed each day, and the rapid growth of eCommerce has made security a vital issue for many consumers. • Critical digital data stored on foreign servers, like in a Cloud service, demands high level of security while transmitting it through the network across multiple devices and clients.
- 4. Quick Example • In some electronics competitions, where wireless RF modules are required, the use of decoder and encoder IC’s becomes inevitable due to secure communication issues. Unless the status of address pins of both the ICs matches, no communication between receiver and transmitter takes place. Thus, when number of competitors increase, there is a possibility of clashing of address bits, leading to someone else controlling your vehicle!
- 6. Quick Example • Cryptographic hash functions are used to check the integrity of a file, i.e., to see if the file received from some other source is corrupt or not. Here, the file's hash value is compared to a previously calculated value. If these match then the file is presumed to be unmodified. • These became popular when the bit-torrent community grew and many files were shared through it, which often got corrupted.
- 7. Diagramatic representation of a peer connected to other seeds and peers in a swarm.
- 8. Cryptography and Network Security • Network security is one of the several models of security which exist today. This is also the most efficient and widely used model worldwide. • Here the focus is to control network access to various hosts and their services, rather than controlling individual host security. • Hence, modern cryptography techniques are implemented in the Network Security Model, as it proves to be affordable, functional and reliable.
- 9. Elementary Network Security Model
- 10. Modern Cryptography • It is heavily based on mathematical theory and computer science practice. • Cryptographic algorithms are designed around computational hardness assumptions, making such algorithms hard to break in practice by any adversary.
- 11. Important Terms • Plaintext – The message in its original form. • Ciphertext – Message altered to be unreadable by anyone except the intended recipients. • Cipher- The algorithm used to encrypt the message. • Cryptosystem – The combination of algorithm, key, and key management functions used to perform cryptographic operations
- 12. Types of cryptography • Private-key cryptography or Symmetric-key algorithms • Public-key cryptography or Asymmetric-key algorithms
- 13. Private Key Cryptography • A single key is used for both encryption and decryption. That's why its called “symmetric” key as well. • The sender uses the key to encrypt the plain-text and the receiver applies the same key to decrypt the message. • The biggest difficulty with this approach, thus, is the distribution of the key, which generally a trusted third-party VPN does.
- 14. Schematic representation of Private-key cryptography
- 15. Public-Key Cryptography • Each user has a pair of keys: a public key and a private key. • The public key is used for encryption. This is released in public. • The private key is used for decryption. This is known to the owner only.
- 16. Schematic representation of Public-key cryptography
- 17. RSA CRYPTOSYSTEM • The most famous algorithm used today is RSA algorithm. • It is a public key cryptosystem developed in 1976 by MIT mathematicians - Ronald Rivest, Adi Shamir, and Leonard Adleman. • RSA today is used in hundreds of software products and can be used for digital signatures, or encryption of small blocks of data.
- 18. Mathematical Prerequisites • Euclid's Algorithm and its extension • Modulo operator, its congruence, and multiplicative inverse • Euler's Phi Function and Theorem
- 19. Euclid's Algorithm • It is a method of computing Greatest Common Divisor of two integers (generally positive) . • It is based on two observations : a) If a perfectly divides b, then GCD(a,b) = a b) If a = b * t + l where t and l are integers, then GCD(a,b) = GCD(b,l) • It is applied in chain until the remainder is zero.
- 20. Example
- 21. Modulo Arithmetic • The modulo operation finds the remainder of division of one number by another. • For example, 14 mod 12 = 2 , as when 14 is divided by 12 we get the remainder as 2.
- 22. Modulo Arithmetic • The modular congruence, indicated by "≡" followed by "mod" between parentheses, means that the operator "mod", applied to both members, gives the same result. • For example, 38 ≡ 14 (mod 12) is same as 38 mod 12 = 14 mod 12 , which both yield 2.
- 23. Modulo Arithmetic • The modular multiplicative inverse of a mod m is an integer x such that a*x ≡ 1 (mod m) • For example, we wish to find modular multiplicative inverse x of 3 mod 11. We can write this as • 3 -1 ≡ x (mod 11) which is same as 3*x ≡ 1 (mod 11) • Since RHS is 1, we need to find x such that (3*x) mod 11 = 1 which would give minimum positive value of x as 4.
- 24. Extended Euclid's Algorithm • The Extended Euclid's Algorithm computes the integers x and y in the equation called Bézout's identity which is : ax + by = GCD(a,b) • When a and b are co-primes, x is given as a-1≡ x (mod b) and y is given as b-1≡ y (mod a) • Hence we can easily find out the modular multiplicative inverse this way.
- 25. Euler's Phi Function • Euler's Phi function, φ(n) , is an arithmetic function that counts the positive integers less than or equal to n that are relatively prime to n, i.e., GCD(k,n)=1 . The number of values of k here is φ(n). • For example, φ(8) = 4, since there are 4 integers {1,3,5,7} • For any prime p, φ(p) = p-1 • Also, for relative primes p and q, φ(p*q) = φ(p)*φ(q)
- 26. Euler's Theorem • Euler's Theorem states that if GCD (a,n)=1, i.e., a and n are co-primes, then aφ(n)≡ 1 (mod n) • If n is prime, then we have an-1≡ 1 (mod n) • If n is the product of two primes p and q, then a(p-1)*(q-1)≡ 1 (mod n) . This concept forms the basis of encryption process in RSA cryptosystem.
- 27. Setting up RSA Cryptosystem Algorithm 1. A user must first choose two large prime numbers, say p and q. Example 1.Let Alice choose p=11 and q=19.
- 28. Setting up RSA Cryptosystem Algorithm 2.Calculate n = p * q Example 2.Alice calculated p * q as 11 * 19 and got the value of n = 209.
- 29. Setting up RSA Cryptosystem Algorithm 3.Calculate φ(n) = (p-1) * (q-1) Example 3.Alice calculated (p-1) * (q-1) as 10 * 18 and got the value of φ(n) = 180.
- 30. Setting up RSA Cryptosystem Algorithm 4.Choose a value of e such that GCD(e,φ(n)) = 1. Example 4.Alice randomly chose e as 103 which is co-prime to 180.
- 31. Setting up RSA Cryptosystem Algorithm 5.Calculate d such that e * d ≡ 1 (mod φ(n)) , or in other words, find the modular multiplicative inverse of e. Example 5.To find the required inverse, Alice would use Euclid's Algorithm in reverse manner and then use its extension to find the inverse. Here's how:
- 32. Setting up RSA Cryptosystem • Applying Euclid's: 180 = 1 * 103 + 77 103 = 1 * 77 + 26 77 = 2 * 26 + 25 26 = 1 * 25 + 1 Remember, Alice chose e = 103 and φ(n) = 180
- 33. Setting up RSA Cryptosystem • Reversing Euclid's: 1 = 26 – 25 = 26 – (77 – 2*26) = 3 * 26 – 77 = 3 * (103 – 77) – 77 = 3 * 103 – 4 * 77 = 3 * (103) – 4 * (180 – 103) = 7 * 103 – 4 * 180 Remember, Bezout's Identity is in the form ax + by = gcd(a,b) (Bezout's Identity)
- 34. Setting up RSA Cryptosystem • Finding Inverse: We now write our Bézout's Identity as ex + φ(n)y = 1, and we just determined x as 7. Now, the inverse of e is e-1≡ x (mod φ(n)) ≡ 7 (mod 180) Hence, d = 7
- 35. Setting up RSA Cryptosystem Algorithm 6.The Public keys are (e,n), 7.The Private keys are (d,n) . Example 6.Alice thus obtained her Public Key as (103,209) and Private Key as (7, 209)
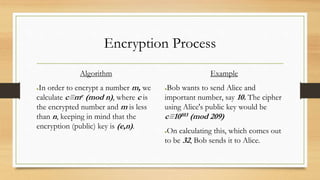
- 36. Encryption Process Algorithm ●In order to encrypt a number m, we calculate c≡me (mod n), where c is the encrypted number and m is less than n, keeping in mind that the encryption (public) key is (e,n). Example ●Bob wants to send Alice and important number, say 10. The cipher using Alice's public key would be c≡10103 (mod 209) ●On calculating this, which comes out to be 32, Bob sends it to Alice.
- 37. Decryption Process Algorithm ●In order to decrypt a cipher c, we calculate m≡cd (mod n), where m is the original number, keeping in mind that the decryption (private) key is (d,n) . Example ●Alice receives the encrypted number. The decrypted number using her private key would be m≡32 7 (mod 209) ●On calculating this, she gets m=10, which was desired.
- 38. Reliability of RSA Cryptosystem • The typical RSA Key Sizes in use today vary from 1024 bits to 4096 bits. These are practically unbreakable on home computers. • Further computational algorithms are designed to reduce the computational cost of generating the cipher as well as decoding the cipher. This encourages the use of long keys for encryption.
- 39. Conclusion • The RSA Cryptosystem is perhaps the most beautiful application of mathematics. Theorems of Euler and Euclid we discussed were proved around 300 years ago, and we find it's application today extensively in network security, computer software algorithms and in further advancement of technology to create a better world.