Data Encryption Standard (DES)
- 1. DATA ENCRYPTION STANDARD (DES) MUHAMMAD HARIS AHMED [email protected] 12CS45
- 2. SYMMETRIC SYSTEMS • Several types of symmetric algorithms are used today. They have different methods of providing encryption and decryption functionality • The one thing they all have in common is that they are symmetric algorithms, meaning the sender and receiver are using two instances of the same key
- 3. SYMMETRIC ALGORITHMS • Data Encryption Standard (DES) • 3DES (Triple DES) • Blowfish • Twofish • IDEA (International Data Encryption Algorithm) • RC4, RC5, RC6 • AES (Advanced Encryption Standard) • SAFER (Secure and Fast Encryption Routine
- 4. DES FIRST BREAK! • In 1998, the Electronic Frontier Foundation built a computer system for $250,000 that broke DES in three days by using a brute force attack against the keyspace
- 5. DES FIRST BREAK! • It contained 1,536 microprocessors running at 40MHz, which performed 60 million test decryptions per second per chip
- 6. WHAT IS DES? DES Use Symmetric system means both sender and receiver side we used same key for encryption and decryption.
- 7. WHAT IS DES? DES used 64 bits of block for encryption and decryption. Sixteen rounds of transposition and substitution are performed in order to achieve DES.
- 9. HOW DOES DES WORK ? • DES is a symmetric block encryption algorithm. When 64-bit blocks of plaintext go in, 64-bit blocks of cipher text come out. • It is also a symmetric algorithm, meaning the same key is used for encryption and decryption. • It uses a 64-bit key: 56 bits make up the true key, and 8 bits are used for parity.
- 10. HOW DOES DES WORK ? …. • When the DES algorithm is applied to data, it divides the message into blocks and operates on them one at a time. • The blocks are put through 16 rounds of transposition and substitution functions. • The result is 64-bit blocks of ciphertext.
- 11. DES MODES • Block ciphers have several modes of operation. Each mode specifies how a block cipher will operate.
- 12. DES MODES • Electronic Code Book (ECB) • Cipher Block Chaining (CBC) • Cipher Feedback (CFB) • Output Feedback (OFB) • Counter Mode (CTR)
- 13. • It Inherit core functionality from their parent block which is Symmetric System. • Like 64 bits of block use for encryption and decryption. • Use Same key for encryption and decryption of all blocks of data. ELECTRONIC CODE BOOK MODE
- 14. ELECTRONIC CODE BOOK MODE
- 15. • User for the Small amount of text not for large amount of data. • Reason • Same block of plain text and key generate same cypher text each time • Easy to find Pattern with large amount of data ELECTRONIC CODE BOOK MODE
- 16. ELECTRONIC CODE BOOK MODE ECB mode operates like a code book. A 64- bit data block is entered into the algorithm with a key, and a block of ciphertext is produced For a given block of plaintext and a given key, the same block of ciphertext is always produced ECB is the easiest and fastest mode to use, but as we will see, it has its dangers
- 17. ELECTRONIC CODE BOOK MODE… •So, two bad things can happen here: • An attacker could uncover the key and thus have the key to decrypt all the blocks of data, or • An attacker could gather the ciphertext and plaintext of each block and build the code book that was used, without needing the key.
- 18. CIPHER BLOCK CHAINING MODE • Cipher Block Chaining (CBC) does not reveal a pattern, because each block of text, the key, and the value based on the previous blocks. • This results in more random ciphertext • This provides dependence between the blocks, in a sense chaining them together
- 19. CIPHER BLOCK CHAINING MODE
- 20. CIPHER BLOCK CHAINING MODE • This chaining effect means that a particular ciphertext block is dependent upon all blocks before it, not just the previous block. • When we encrypt our very first block using CBC, we do not have a previous block of ciphertext • If we do not add a piece of randomness when encrypting this first block to save from hackers.
- 21. • So, The solution is to use Initialization Vector that generate randomness in first block. CIPHER BLOCK CHAINING MODE
- 22. CIPHER FEEDBACK MODE (CFB) • The CBC mode is great to use when you need to send large chunks of data at a time but when the need of send small amount of data at a time we use CFB. • Cipher Feedback is the combination of block cipher and stream cipher.
- 23. CIPHER FEEDBACK MODE (CFB) • Keep One copy of Cipher text.
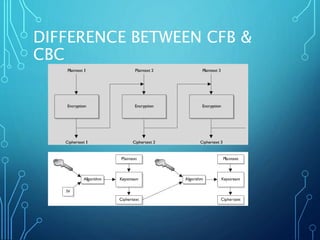
- 24. DIFFERENCE BETWEEN CFB & CBC • Major Difference between both of them is CBC works with 64 bits of data only but CFB also work with 8 bits or so on.
- 25. DIFFERENCE BETWEEN CFB & CBC
- 26. OUTPUT FEEDBACK MODE • It Cover the weakness of Cipher feedback mode. • Almost Same process of encryption and decryption.
- 27. OUTPUT FEEDBACK MODE • It’s similar to the Cipher Block Chaining Mode but there is one minor changing in it.
- 28. DIFFERENCE IN OFB & CFB
- 29. COUNTER MODE (CTR) • There is no chaining involved in Counter Mode (CTR) like other three types. I. Cipher block Chaining. II. Cipher Feedback. III. Output Feeback.
- 30. COUNTER MODE (CTR) • Each block is individually decrypted without depending on other blocks. • the encryption of the individual blocks can happen in parallel, which increases the performance.
- 31. COUNTER MODE (CTR) • No use of initialization Vector instead it use counter.
- 32. THANK YOU