Data Handling and Function
- 1. Java/J2EE Programming Training Data Handling and Functions
- 2. Page 2Classification: Restricted Agenda • Implement Single and Multi dimensional array • Declare and Define Functions • Call Functions by value and by reference • Implement Method Overloading • Use String data-type and String-buffer
- 3. Page 3Classification: Restricted Introduction to Arrays
- 4. Page 4Classification: Restricted Meet John Again
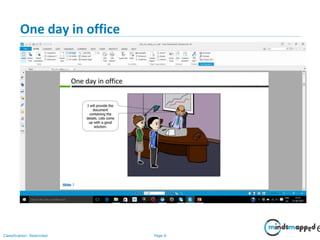
- 5. Page 5Classification: Restricted One day in office
- 6. Page 6Classification: Restricted One day in office 6
- 7. Page 7Classification: Restricted John’s Project – Question Statement
- 8. Page 8Classification: Restricted Daisy was Confused!
- 9. Page 9Classification: Restricted John already had a plan
- 10. Page 10Classification: Restricted John Came up with a solution
- 11. Page 11Classification: Restricted John’s Solution
- 12. Page 12Classification: Restricted John Presented the Solution
- 13. Page 13Classification: Restricted John gets a Promotion
- 14. Page 14Classification: Restricted Why do we use Arrays? • Arrays are an important structure to hold data. • Java allows us to hold many objects of the same type using arrays and it can be used with the help of a loop to access the elements by their index.
- 16. Page 16Classification: Restricted Declaring Arrays
- 17. Page 17Classification: Restricted Declaring Arrays
- 18. Page 18Classification: Restricted Declaring Arrays • Arrays can be declared for primitive and non-primitive data types. • Instead of declaring int a1, a2, a3, a4....a100, we can declare int a[100]. • It is fast and efficient to access an element in an array using the corresponding index without actually traversing through the entire array. • The size of the array is fixed once it is created. • For Example: A character array of 10 characters can be declared as
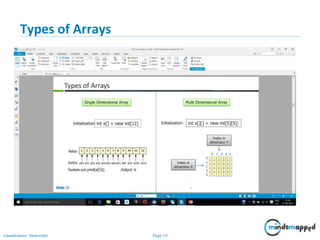
- 19. Page 19Classification: Restricted Types of Arrays
- 20. Page 20Classification: Restricted How Single Dimensional Arrays are used?
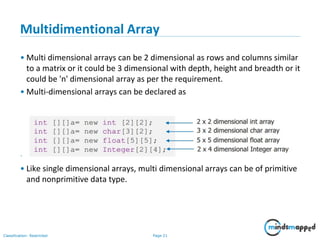
- 21. Page 21Classification: Restricted Multidimentional Array • Multi dimensional arrays can be 2 dimensional as rows and columns similar to a matrix or it could be 3 dimensional with depth, height and breadth or it could be 'n' dimensional array as per the requirement. • Multi-dimensional arrays can be declared as • Usually 2 dimensional arrays are used to perform matrix operations. • Like single dimensional arrays, multi dimensional arrays can be of primitive and nonprimitive data type.
- 22. Page 22Classification: Restricted Question How many bytes are allocated for the array x? int x[][] = new int[5][5];
- 23. Page 23Classification: Restricted Answer An int element takes 4 bytes and array x can store 25 int elements. Hence total number of bytes taken by x is 25*4 = 100
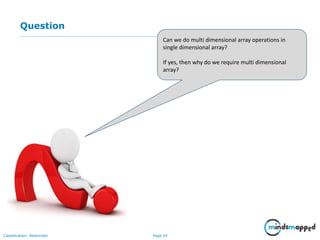
- 24. Page 24Classification: Restricted Question Can we do multi dimensional array operations in single dimensional array? If yes, then why do we require multi dimensional array?
- 25. Page 25Classification: Restricted Answer We can perform all the operations of multi dimensional array in single dimensional array but when the data has more than one dimension, it will be easier to perform operations in multi dimensional array.
- 28. Page 28Classification: Restricted Daisy Seek’s Help
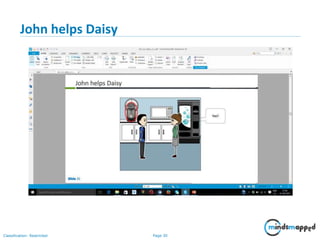
- 29. Page 29Classification: Restricted John helps Daisy
- 30. Page 30Classification: Restricted John helps Daisy
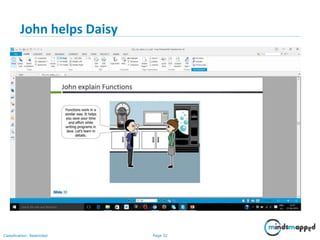
- 31. Page 31Classification: Restricted John explain Functions
- 32. Page 32Classification: Restricted John helps Daisy
- 33. Page 33Classification: Restricted Functions • Scope specifier modifier return type function name (arguments) • A function/method has group of statements to be executed. • A function has a task to perform. • A function is declared as public static void say Hello(int a, int b)
- 34. Page 34Classification: Restricted Why do we use functions? • We use functions to provide different kinds of functionality. • For example: • absolute() • To find the absolute value of a number. • square() • To find the square of a number. • sqrt() • To find the square root of a number.
- 35. Page 35Classification: Restricted Features of Functions • Scope specifier • This option specifies the visibility of the function. It could be public, private, protected or default (package). • Modifier • This is optional. • This will change the meaning of the function. Some of the options could be final, static, native,synchronized etc. • Return type • This option specifies the data that will be returned by the function. • It could be primitive data type or objects. • Function name • It is the name given to the function. Using function name, functions can be invoked. • Arguments • This is optional but can be used. Using this, one can pass values to the function for computation.
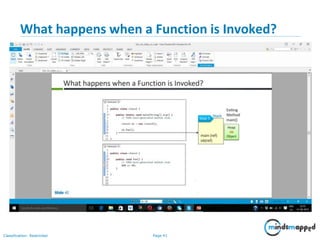
- 36. Page 36Classification: Restricted What happens when a Function is Invoked? • When a function is called from the main method, main method() address is stored on top of the stack. • Control jumps to execute the function. • After executing the function, main method address is popped from the stack and main method execution resumes.
- 37. Page 37Classification: Restricted What happens when a function is invoked?
- 38. Page 38Classification: Restricted What happens when a function is invoked?
- 39. Page 39Classification: Restricted What happens when a function is invoked?
- 40. Page 40Classification: Restricted What happens when a Function is Invoked?
- 41. Page 41Classification: Restricted What happens when a Function is Invoked?
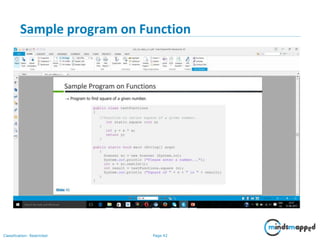
- 42. Page 42Classification: Restricted Sample program on Function
- 43. Page 43Classification: Restricted Sample program on Functions (Contind..)
- 44. Page 44Classification: Restricted Sample program on Functions(Contd..) 4
- 45. Page 45Classification: Restricted Sample Program on Functions (contd..)
- 46. Page 46Classification: Restricted Sample Program on Functions (contd..)
- 47. Page 47Classification: Restricted Function Calling ways
- 48. Page 48Classification: Restricted Call by Value • When value of the primitive data type is passed as an argument from the calling function, data is being sent to the function. • At the receiving end, a new variable is created and the data is copied. This is call by value. • All the programs we have done till now is done using call by value.
- 49. Page 49Classification: Restricted Call by Reference
- 50. Page 50Classification: Restricted Call by Reference
- 52. Page 52Classification: Restricted Function Overloading
- 53. Page 53Classification: Restricted Function Overloading (contd.)
- 54. Page 54Classification: Restricted Function Overloading (contd.)
- 55. Page 55Classification: Restricted Function Overloading
- 56. Page 56Classification: Restricted Function Overloading 5
- 57. Page 57Classification: Restricted Program on Function Overloading
- 58. Page 58Classification: Restricted Meet Mr. Letter and Miss Sentence!
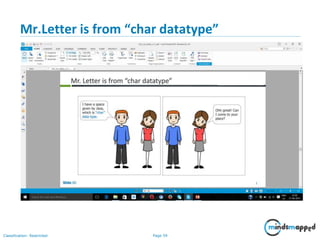
- 59. Page 59Classification: Restricted Mr.Letter is from “char datatype”
- 60. Page 60Classification: Restricted Miss Sentence is sad!
- 61. Page 61Classification: Restricted Miss Sentence has her own Place in Java
- 62. Page 62Classification: Restricted Why do we use String?
- 63. Page 63Classification: Restricted String • String is a class in Java to store string data. • You can assign string data simply by defining the string object and assign the string like this: • You can concatenate two string using + symbol. • For Example: • Output of the program is • Appended string is: HelloWorld String str; String str = “Focusthread” String str = new String (“Focusthread”);
- 64. Page 64Classification: Restricted Where do we use string?
- 65. Page 65Classification: Restricted String Functions • length() • Returns the length of the string. • charAt(int) • Returns a character at the specified position. Index of the String starts from 0. • concat (String str) • It concatenates the with the string object. It is same as using '+' operator for concatenation. • equals(String str) • Checks whether string object and str and return true if they are same else returns false. • EqulsIgnoreCase (String str) • Same as above function except that this function ignores the case and checks for the equality of the strings. • indexOf(String str) • Returns the index of the specified string in the string object. • lastIndexOf(String str) • Same as above function but checks from back of the string.
- 66. Page 66Classification: Restricted String Functions • replace(char ch, char ch1) • Replaces the character ch with Character ch1 in the string. • toLowerCase() • Converts the given string to lowercase. • toUpperCase() • Converts the given string to uppercase. • trim() • Removes the leading and trailing spaces of the string.
- 69. Page 69Classification: Restricted Question When should we use String and StringBuffer? why?
- 70. Page 70Classification: Restricted Answer When we do not need to modify string objects then String can be used else using StringBuffer is a better option since it is mutable.
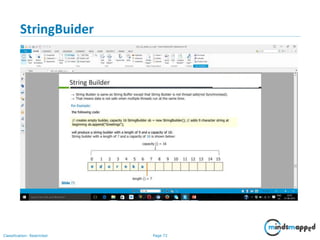
- 71. Page 71Classification: Restricted Program on StringBuffer
- 73. Page 73Classification: Restricted StringBuilder Constructors
- 74. Page 74Classification: Restricted Assignment – Single Dimentional Array
- 75. Page 75Classification: Restricted Assignment – Two Dimentational Array
- 76. Page 76Classification: Restricted Assignment - Functions
- 77. Page 77Classification: Restricted Assignment – Functions Overloading
- 78. Page 78Classification: Restricted Module Assignment
- 79. Page 79Classification: Restricted Module Assignment
- 80. Page 80Classification: Restricted Module Assignment
- 81. Page 81Classification: Restricted Agenda for Next Class













![Page 18Classification: Restricted
Declaring Arrays
• Arrays can be declared for primitive and non-primitive data types.
• Instead of declaring int a1, a2, a3, a4....a100, we can declare int
a[100].
• It is fast and efficient to access an element in an array using the
corresponding index without actually traversing through the entire
array.
• The size of the array is fixed once it is created.
• For Example: A character array of 10 characters can be declared as](https://image.slidesharecdn.com/day3datahandlingandfunction-180731213124/85/Data-Handling-and-Function-18-320.jpg)

![Page 22Classification: Restricted
Question
How many bytes are allocated for the array x?
int x[][] = new int[5][5];](https://image.slidesharecdn.com/day3datahandlingandfunction-180731213124/85/Data-Handling-and-Function-22-320.jpg)