Defcon Moscow #0x0A - Mikhail Firstov "Hacking routers as Web Hacker"
- 3. WHOAMI • Researcher @ hlsec.ru • @cyberpunkych • Attacking MongoDB @ ZN2012 • Database honeypot by design @ Defcon Russia • Meme Master
- 4. Routers everywhere. • Home • Work • Hospitals • Banks • In your bag • etc
- 5. But I’m web hacker, what can I do? • Router’s web control panel == web site • Connect managers with web interface, such as Yota Access • ISP (statistics, billing, management, etc)
- 6. Routerzzz
- 7. OWASP TOP 10 for routers • Default credentials • Auth bypass • XSS • CSRF • Command Injection • Sensitive info leak • Bugs in third party libraries • RCE, XXE, etc
- 8. Default credentials Should I say anything?
- 9. Authentication Bypass/No Auth • Hello, Yota Many • Hello, D-Link’s backdoor • Hello, MTS 4G Router • Hello, others (DIR-100, DI-524, DI-604, etc)
- 10. CSRF/XSS everywhere Srlsy, it’s everywhere. But why? Because **** you, that’s why. (Zyxel Keenetic v1)
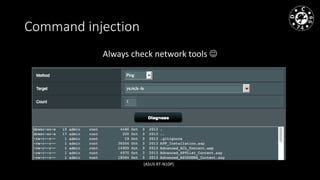
- 11. Command injection Always check network tools (ASUS RT-N10P)
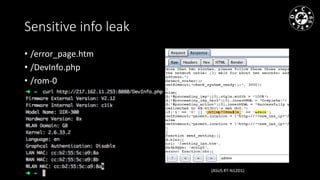
- 12. Sensitive info leak • /error_page.htm • /DevInfo.php • /rom-0 (ASUS RT-N12D1)
- 13. Bugs in third party libraries • Heartbleed • ShellShock • RomPager • etc
- 15. WARNINNG! ВАС ПРИСТРЕЛЯТ ПО УТРУ – НЕ РАБОТАЙТЕ ПО РУ!
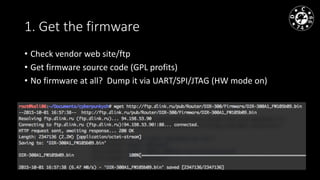
- 16. 1. Get the firmware • Сheck vendor web site/ftp • Get firmware source code (GPL profits) • No firmware at all? Dump it via UART/SPI/JTAG (HW mode on)
- 17. 2. Unpack it • Binwalk -> search for signature and try to unpack • Firmware-mod-kit pack/unpack • If NO_SUCCESS -> analyze firmware entropy • Sasquatch for squashfs, other fs -> google for tools
- 18. 3. CHECK AUTH • Black Box => White Box • for i in *; do curl http://router_ip/$i; done • You know what to do ;)
- 19. 4. СHECK CMD INJECTION • PING -> ya.ru;ls • CONFIG backup to FTP/TFTP • Any place where command execution is used • Check all shell symbols • Error-based command injection for output # ping ya.ru || ls # ping $(uname) # ping `uname` # ping ya.ru && ls # ping ya.ru; ls # ping $USER.ya.ru ...
- 20. 5. Check for XSS • <script>alert(1)</script> for every param! • Check hostname, sometimes it can help you • Even 1 XSS => PROFIT!!1 • Stored XSS => Compromised web interface
- 21. 5. Check for XSS • <script>alert(1)</script> for every param! • Check hostname, sometimes it can help you • Even 1 XSS => PROFIT!!1 • Stored XSS => Compromised web interface Typical attack scheme: Link/Page with XSS => AJAX => getElementsByTagName(‘input’)[*].value => log data
- 22. Hide myself from web aka rookit hostname Hello, 1'}]"); ! Hide’n’seek from browser via xss in Zyxel Keenetic.
- 23. 6. Check for CSRF • Inspect for anti-csrf tokens • Check X-Requested-With • Referer check
- 24. 6. Check for CSRF • Inspect for anti-csrf tokens • Check X-Requested-With • Referer check Referer checking:
- 25. 6. Check for CSRF • Inspect for anti-csrf tokens • Check X-Requested-With • Referer check Any other == bad referer:
- 26. 6. Check for CSRF • Inspect for anti-csrf tokens • Check X-Requested-With • Referer check Open Redirect trick to bypass regexp:
- 27. CSRF => MITM All you need is love CSRF via updating DNS settings! ( <img src=“csrf”>, habrahabr, you know. )
- 28. XSS + Smart CSRF 1. Get the internal IP address using a nice WebRTC hack 2. Get router IP (no so many requests 8) ) 3. Make CSRF Request via XSS payload (better for stored XSS) 4. Get all data (sometimes passwords stored in input.value’s) 5. Redirect to page with XSS 6. ??? 7. All your data are belong to us!
- 29. Support Software
- 30. Support Software • %operator_name% Connect (Huawei modems), Yota Access, etc • Sometimes they also use web inside apps! • Binary bugs (BOF, etc) • Bugs with bad privileges • Sniff requests to ISP => new bugs
- 31. Support Software From CSRF to RCE! video_here
- 32. ISP
- 33. ISP – Just another target • Google/Yandex dork • Cabinet/Balance/etc on provider’s site • Subdomains • Popular services
- 34. Why it is important? • Update server control • Client-side tricks (crossdomain.xml) • Remote device administration • New default credentials • Attack firmware developers
- 35. Google it!
- 36. Just google.
- 38. Example from real life
- 39. Conclusion • Router == web site • Black Box => White Box • XSS/CSRF everywhere • Vuln1+vuln2->vuln3 • The RCE is out there • R.E.S.H.E.T.O.
















![5. Check for XSS
• <script>alert(1)</script> for every param!
• Check hostname, sometimes it can help you
• Even 1 XSS => PROFIT!!1
• Stored XSS => Compromised web interface
Typical attack scheme:
Link/Page with XSS => AJAX => getElementsByTagName(‘input’)[*].value => log data](https://image.slidesharecdn.com/defconmoscow0x0a-mikhailfirstovhackingroutersaswebhacker-151009145654-lva1-app6892/85/Defcon-Moscow-0x0A-Mikhail-Firstov-Hacking-routers-as-Web-Hacker-21-320.jpg)
![Hide myself from web aka rookit hostname
Hello, 1'}]"); !
Hide’n’seek from browser via xss in Zyxel Keenetic.](https://image.slidesharecdn.com/defconmoscow0x0a-mikhailfirstovhackingroutersaswebhacker-151009145654-lva1-app6892/85/Defcon-Moscow-0x0A-Mikhail-Firstov-Hacking-routers-as-Web-Hacker-22-320.jpg)