Dynamic Source Routing Sink hole attack
- 1. © Tetcos 2014 Mobile Adhoc Networks NetSim v9NetSim v9 Network Simulation/Emulation Platform
- 2. © Tetcos 2014 Outline Introduction Reactive Routing Protocol DSR AODV Advantages and Disadvantages Summary www.tetcos.com
- 3. © Tetcos 2014 Wireless Network Wireless LAN Infrared or radio links very flexible within the reception area low bandwidth compared to wired networks. Adhoc Networks useful when infrastructure not available, impractical or expensive military applications, rescue, home networking www.tetcos.com
- 4. © Tetcos 2014 Infrastructure-based Network AP Wired Backbone www.tetcos.com
- 5. © Tetcos 2014 STA STA STA STA Ad-hoc Network peer-peer connections www.tetcos.com
- 6. © Tetcos 2014 Mobile Adhoc Networks Frequent Host movement Frequent Topology change No infrastructure Data must be routed via intermediate nodes A B D C A D B C www.tetcos.com
- 7. © Tetcos 2014 Why Adhoc Network ? Setting up of fixed Access point and backbone infrastructure is not always viable Infrastructure may not be present in the disaster area or war zone Infrastructure may not be practical for short range radios Adhoc Networks Do not need backbone infrastructure support Are easy to deploy Useful when infrastructure is absent, destroyed or impractical www.tetcos.com
- 8. © Tetcos 2014 Many Applications Personal area networking Cell phone, laptop, ear phone, wrist watch Military environments Soldiers, tanks, planes Civilian environments Taxi cab networks Meeting rooms Sports stadiums Boats, small aircraft Emergency operations Search and rescue Policing and fire fighting
- 9. © Tetcos 2014 MANET protocol stack Application layer Transport layer UDP Network layer DSR/AODV Data Link layer 802.11 b MAC Physical layer 802.11 b PHY
- 10. © Tetcos 2014 Routing in MANET www.tetcos.com
- 11. © Tetcos 2014 Routing Protocols Proactive protocols Traditional distributed shortest-path protocols Maintain routes between every host pair at all times Based on periodic updates; High routing overhead Example: DSDV (destination sequenced distance vector) Reactive protocols Determine route if and when needed Source initiates route discovery Example: DSR (dynamic source routing) Hybrid protocols Adaptive; Combination of proactive and reactive Example : ZRP (zone routing protocol) www.tetcos.com
- 12. © Tetcos 2014 Protocol Trade-offs Proactive protocols Always maintain routes Little or no delay for route determination Consume bandwidth to keep routes up-to-date Maintain routes which may never be used Reactive protocols Lower overhead since routes are determined on demand Significant delay in route determination Employ flooding (global search) Control traffic may be bursty Which approach achieves a better trade-off depends on the traffic and mobility patterns www.tetcos.com
- 13. © Tetcos 2014 Reactive Routing Protocols www.tetcos.com
- 14. © Tetcos 2014 Two basic mechanisms Route Discovery •Route Request (RREQ) •Route Reply (RREP) Route Maintenance •Route Error (RERR) •Acknowledgement. Dynamic source Routing protocol (DSR) www.tetcos.com
- 15. © Tetcos 2014 DSR Basic Processes Route Discovery Route message creation (RREQ, RREP) Route message processing at each node Check route table for destination address route entry Reverse route entry for originator and precursors Route Discovery- Node Actions
- 16. © Tetcos 2014 DSR When node A wants to send a packet to node G, but does not know a route to G, node A initiates a route discovery Source node A floods Route Request (RREQ) Each node appends own identifier when forwarding RREQ www.tetcos.com
- 17. © Tetcos 2014 Route Discovery in DSR A B C E D G H F A A A-B A-C A-C-E A-C-E A-C-E A-B-D A has Data Destinatio n www.tetcos.com
- 18. © Tetcos 2014 Route Discovery in DSR Destination G on receiving the first RREQ, sends a Route Reply (RREP) RREP is sent on a route obtained by reversing the route appended to received RREQ RREP includes the route from A to G on which RREQ was received by node G www.tetcos.com
- 19. © Tetcos 2014 Route Discovery in DSR A B C E D G H F A A A-B A-C A-C-E A-C-E A-C-E A-B-D A-B-D-G A-B-D-G A-B-D-G Route reply www.tetcos.com
- 20. © Tetcos 2014 DSR Node A on receiving RREP, caches the route included in the RREP When node A sends a data packet to G, the entire route is included in the packet header hence the name source routing Intermediate nodes use the source route included in a packet to determine to whom a packet should be forwarded www.tetcos.com
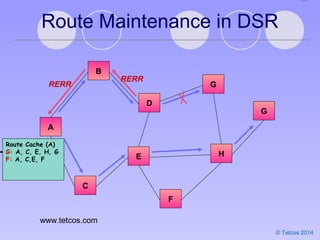
- 21. © Tetcos 2014 Route Maintenance in DSR A B C E D G H F G RERR RERR Route Cache (A) G: A, B, D, G G: A, C, E, H, G F: B, C,E, F Route Cache (A) G: A, C, E, H, G F: A, C,E, F www.tetcos.com
- 22. © Tetcos 2014 Advantages Routes are discovered only they are needed Reduces overhead of route maintenance Route caching reduce the cost of route discovery A single route discovery may yield many routes to the destination due to intermediate nodes may reply route request from local caches. Disadvantages Packet header size grows with route length due to source routing inefficiency Route request packet may reach all nodes in the network. REQ flooding Increased contention if too many route replies come back Route Reply Storm DSR: Advantages/ Disadvantages www.tetcos.com
- 23. © Tetcos 2014 Summary In this lecture we discussed the Dynamic Source Routing Protocol (DSR) ❍ Route Discovery • Source Routing (Accumulation of routes in the packet header) • Role of route cache in speeding up the route discovery and reducing the propagation of RREQs/RREPs ❍ Route Maintenance • Route cache and the role it plays in route maintenance www.tetcos.com
- 24. © Tetcos 2014 Thank You www.tetcos.com