Efficient Offline Monitoring of LTL with Bit Vectors (Talk at SAC 2021)
- 1. K. Kie, S. Hallé Kun Xie and Sylvain Hallé Université du Québec à Chicoutimi CANADA Offline Monitoring of LTL with Bit Vectors CRSNG NSERC ACM Symposium on Applied Computing, March 24th, 2021
- 2. K. Kie, S. Hallé What is runtime monitoring?
- 3. K. Kie, S. Hallé What is runtime monitoring? System
- 4. K. Kie, S. Hallé What is runtime monitoring? System
- 5. K. Kie, S. Hallé What is runtime monitoring? System Instrumentation
- 6. K. Kie, S. Hallé What is runtime monitoring? System Instrumentation
- 7. K. Kie, S. Hallé What is runtime monitoring? System Instrumentation Trace
- 8. K. Kie, S. Hallé What is runtime monitoring? System Instrumentation Trace Events
- 9. K. Kie, S. Hallé What is runtime monitoring? System Instrumentation Trace Events
- 10. K. Kie, S. Hallé What is runtime monitoring? System Instrumentation Trace Events Monitoring
- 11. K. Kie, S. Hallé What is runtime monitoring? Runtime monitoring is the process of observing an actual run of a system and checking constraints on its execution Monitor Verifies that sequence of events follows specification System Event Event . . . } The execution of the system produces events Specification Gives conditions on events and sequences of events allowed to happen
- 12. K. Kie, S. Hallé p p now p p now q G p F p X p p U q now now Semantics of LTL operators "Globally" "Eventually" "Next" "Until"
- 13. K. Kie, S. Hallé Semantics of LTL operators A call to next must be followed by a call to hasNext No CartCreate request can occur before a LoginResponse message A received order must eventually be shipped Three successive login attempts should trigger an alarm G (next → X hasNext) ¬ CartCreate U hasNext G (receive → F ship) G ¬(fail ∧ (X (fail ∧ X fail)))
- 14. K. Kie, S. Hallé M Classical LTL monitoring
- 15. K. Kie, S. Hallé M Classical LTL monitoring
- 16. K. Kie, S. Hallé M Classical LTL monitoring A e
- 17. K. Kie, S. Hallé M Classical LTL monitoring A e S s X
- 18. K. Kie, S. Hallé M Classical LTL monitoring A e S s X s ’ s ’
- 19. K. Kie, S. Hallé M Classical LTL monitoring A e S s X s ’ s ’
- 20. K. Kie, S. Hallé M Classical LTL monitoring A e S s X s ’ s ’ 2 1 3 4 5 The trace must be read linearly
- 21. K. Kie, S. Hallé Each event is encoded by a set of Boolean variables; each variable can be either true or false in each event. Event sequences as bit vectors We create one bit vector vx for each Boolean variable x, with the property that vx[i] = 1 if and only if x is true in event i. 101001... va = 001100... vb = . . .
- 22. K. Kie, S. Hallé Bit vectors for LTL formulas are built by combining and manipulating bit vectors of simpler formulas. Bit vector manipulations 101001... va = 001100... vb = va∨b = va ⊕ vb ⊕ = 101101... va∨b = Boolean operators are direct! Example:
- 23. K. Kie, S. Hallé For a formula φ, vφ[i] = 1 if and only if the sequence starting at position i satisfies φ. Intuition How to deal with temporal operators?
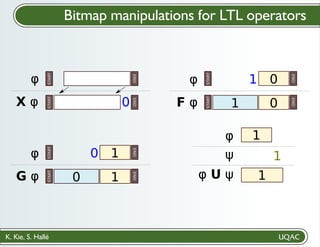
- 24. K. Kie, S. Hallé Bitmap manipulations for LTL operators
- 25. K. Kie, S. Hallé Bitmap manipulations for LTL operators φ X φ
- 26. K. Kie, S. Hallé Bitmap manipulations for LTL operators φ X φ START END
- 27. K. Kie, S. Hallé Bitmap manipulations for LTL operators φ X φ START END START
- 28. K. Kie, S. Hallé Bitmap manipulations for LTL operators φ X φ START END START END 0
- 29. K. Kie, S. Hallé Bitmap manipulations for LTL operators φ X φ START END START END 0 φ F φ
- 30. K. Kie, S. Hallé Bitmap manipulations for LTL operators φ X φ START END START END 0 φ F φ 1 0 1 START END START
- 31. K. Kie, S. Hallé Bitmap manipulations for LTL operators φ X φ START END START END 0 φ F φ 1 0 1 START END START 0 END
- 32. K. Kie, S. Hallé Bitmap manipulations for LTL operators φ X φ START END START END 0 φ F φ 1 0 1 START END START 0 END φ G φ START END START END
- 33. K. Kie, S. Hallé Bitmap manipulations for LTL operators φ X φ START END START END 0 φ F φ 1 0 1 START END START 0 END φ G φ START END START END 0 1 0 1
- 34. K. Kie, S. Hallé Bitmap manipulations for LTL operators φ X φ START END START END 0 φ F φ 1 0 1 START END START 0 END φ G φ START END START END 0 1 0 1 φ φ U ψ ψ
- 35. K. Kie, S. Hallé Bitmap manipulations for LTL operators φ X φ START END START END 0 φ F φ 1 0 1 START END START 0 END φ G φ START END START END 0 1 0 1 φ φ U ψ ψ 1 1
- 36. K. Kie, S. Hallé Bitmap manipulations for LTL operators φ X φ START END START END 0 φ F φ 1 0 1 START END START 0 END φ G φ START END START END 0 1 0 1 φ φ U ψ ψ 1 1 1
- 37. K. Kie, S. Hallé Experimental evaluation Goal: compare processing speed and memory consumption between LTL bitmap evaluation and a baseline Sample of 50+ LTL formulas Between 2 and 20 operators Nesting depth between 2 and 11 Evaluated on traces of 1M events Reference: Event stream processing library Front-end accepting LTL formulas (Polyglot) Hallé & Khoury, RV 2018 10.1007/978-3-030-03769-7_27
- 38. K. Kie, S. Hallé LTL in BeepBeep f → =? a 1 2 f ∧ =? b 1 2 ¬ X f =? c 1 U f =? d 1 a → (¬ (b ∧ X c) U d) S. Hallé. (2018). Event Stream Processing with BeepBeep 3, chapter 5. ISBN 978-2-7605-5102-2
- 39. K. Kie, S. Hallé 1.6x106 1.8x106 2x106 2.2x106 2.4x106 2.6x106 2.8x106 3x106 3.2x106 3.4x106 3.6x106 0 5 10 15 20 25 Throughput (Hz) Formula size 0 500000 1x106 1.5x106 2x106 2.5x106 3x106 0 5 10 15 20 25 Throughput (Hz) Formula size Raw bit vectors BeepBeep 3 Throughput comparison
- 40. K. Kie, S. Hallé 1.6x106 1.8x106 2x106 2.2x106 2.4x106 2.6x106 2.8x106 3x106 3.2x106 3.4x106 3.6x106 0 5 10 15 20 25 Throughput (Hz) Formula size 0 500000 1x106 1.5x106 2x106 2.5x106 3x106 0 5 10 15 20 25 Throughput (Hz) Formula size Raw bit vectors BeepBeep 3 Throughput comparison
- 41. K. Kie, S. Hallé 0 5 10 15 20 25 Throughput (Hz) Formula size 0 500000 1x106 1.5x106 2x106 2.5x106 3x106 0 5 10 15 20 25 Throughput (Hz) Formula size Raw bit vectors BeepBeep 3 500000 1x106 1.5x106 2x106 2.5x106 3x106 Throughput comparison
- 42. K. Kie, S. Hallé Formula S01 Formula S02 Memory consumption 0 200000 400000 600000 800000 1x106 1.2x106 1.4x106 1.6x106 1.8x106 200000 300000 400000 500000 600000 700000 800000 900000 1x106 Memory (B) Trace length EWAH64 Roaring Concise Raw BeepBeep EWAH32 WAH 0 2x106 4x106 6x106 8x106 1x107 1.2x107 1.4x107 1.6x107 1.8x107 2x107 2.2x107 200000 300000 400000 500000 600000 700000 800000 900000 1x106 Memory (B) Trace length EWAH64 Roaring Concise Raw BeepBeep EWAH32 WAH
- 43. K. Kie, S. Hallé Formula S01 Formula S02 Memory consumption 0 200000 400000 600000 800000 1x106 1.2x106 1.4x106 1.6x106 1.8x106 200000 300000 400000 500000 600000 700000 800000 900000 1x106 Memory (B) Trace length EWAH64 Roaring Concise Raw BeepBeep EWAH32 WAH 0 2x106 4x106 6x106 8x106 1x107 1.2x107 1.4x107 1.6x107 1.8x107 2x107 2.2x107 200000 300000 400000 500000 600000 700000 800000 900000 1x106 Memory (B) Trace length EWAH64 Roaring Concise Raw BeepBeep EWAH32 WAH (¬(X (X ((G f) ∧ (X ((!a) ∨ d)))))) → ((X i) ∧ (X (i → e)))
- 44. K. Kie, S. Hallé Formula S01 Formula S02 Memory consumption 0 200000 400000 600000 800000 1x106 1.2x106 1.4x106 1.6x106 1.8x106 200000 300000 400000 500000 600000 700000 800000 900000 1x106 Memory (B) Trace length EWAH64 Roaring Concise Raw BeepBeep EWAH32 WAH 0 2x106 4x106 6x106 8x106 1x107 1.2x107 1.4x107 1.6x107 1.8x107 2x107 2.2x107 200000 300000 400000 500000 600000 700000 800000 900000 1x106 Memory (B) Trace length EWAH64 Roaring Concise Raw BeepBeep EWAH32 WAH (¬(X (X ((G f) ∧ (X ((!a) ∨ d)))))) → ((X i) ∧ (X (i → e))) ((X (g → b)) ∧ ((¬g) → ((¬(X (X (G (F (b ∧ c)))))) → f))) ∨ (F ((G (F (X g))) → ((¬(c ∨ g)) → (e ∨ (G (¬a))))))
- 45. K. Kie, S. Hallé Upsides: Take-home points Bit vector manipulations can be done on multiple bits at a time (32 or 64): parallelism "for free" Leverages quasi-random access to vector elements Implementation incurs a speed-up over linear BeepBeep of up to 10x Future work: Only works offline How to deal with more expressive logics (e.g. LTL-FO+)?




















![K. Kie, S. Hallé
Each event is encoded by a set of Boolean
variables; each variable can be either true or false
in each event.
Event sequences as bit vectors
We create one bit vector vx for each Boolean
variable x, with the property that vx[i] = 1 if and
only if x is true in event i.
101001...
va =
001100...
vb =
.
.
.](https://image.slidesharecdn.com/slideshow-210319223048/85/Efficient-Offline-Monitoring-of-LTL-with-Bit-Vectors-Talk-at-SAC-2021-21-320.jpg)

![K. Kie, S. Hallé
For a formula φ, vφ[i] = 1 if and only if the
sequence starting at position i satisfies φ.
Intuition
How to deal with temporal operators?](https://image.slidesharecdn.com/slideshow-210319223048/85/Efficient-Offline-Monitoring-of-LTL-with-Bit-Vectors-Talk-at-SAC-2021-23-320.jpg)