Evolving Threat Landscapes Web-Based Botnet Through Exploit Kits and Scripts Evolu<on
- 1. Evolving Threat Landscapes Web-‐Based Botnet Through Exploit Kits and Scripts Evolu<on 鄭毓芹 博士生 成功大學電腦與通訊工程研究所 [email protected]
- 2. Outline Part I: Evolving Botnet Threats v Tradi&onal Botnet Threat Landscapes v Evolu&on Considera&ons v Botnet Today Part II: Web Exploit Kits v What is Web Exploit Kits ? v How Exploit Kits Works v Case Study v How Exploit Kits Bring Money In v Exploit Kits Analysis 2
- 3. Part I: Evolving Botnet Threats
- 4. Tradi<onal Botnet Threat Landscapes 4 Bot Bot Bot Bot Bot C&C Server Botmaster • Botnet Characteris<cs: (1) Central C&C Infrastructure (2) C&C based on IRC, HTTP, IM server (3) Single point of failure (4) Predefined execu<ng commands on bot (5) Easy to detect, easy to take down (6) Hard to sell, sharing, transfer and upgrade • Botnet Threats: (1) Spamming (2) Phishing site installing (3) Stealing Confiden<al Data (4) Distributed Denial-‐of-‐Service (DDOS) (5) Compromising and Installing Malware • Bots: a group of compromised computers • Botmaster: human controller • C&C Server ( Command & Control): a channel which botmaster user to send command to bots
- 5. Tradi<onal IRC Botnet C&C Logs 5 . .capture .ddos.syn .ddos.ack .ddos.random .download .findfile .getcdkeys Command Lists .keylog .login .logout .open .procs Easy to inflate into C&C Server and collect all messages in channel
- 6. Evolu<on Considera<ons … 6 Bots Crea<on Botnet Spreading Botnet Controlling Botnet Defending Botnet Commerce Evolving Upgrade Customize bot func<ons and avoid an<virus to detect: • Bot-‐herders assemble(compile) their own func<ons through malware kits • Different malware kits, divide into different bot families. Different func&ons to be enabled, create malware variants. • Techniques used to bypass An&virus: • Code Metamorphism • Packer/ Cryptor / Binder • An<-‐Technology (Protectors)
- 7. Win32/Zbot : Zues Kits (Cont.) 7 Zeus Builder to create zeus bot
- 8. Win32/Zbot : Zues Kits (Cont.) 8 Zues Builder to Compiler Config File into binary sample Enabling kit Func<ons to cause different virustotal scanning results
- 9. Win32/Poison: Poison Auto-Spread Generator 9
- 11. Slice kit func<ons (Logger, Obsfucator, Crypter, Packer, Downloader … ) Keep An<virus low detec<on Rate. 11
- 12. Evolu<on Considera<ons … (Cont.) 12 Bots Crea<on Botnet Spreading Botnet Controlling Botnet Defending Botnet Commerce Evolving Upgrade Setup “Exploit Kit Outposts” to infect computers and distribute malwares efficiently • How to spread out new vic&ms: • Bots automa<cally exploit vulnerabili&es, ex: Conflicker bots (Using dionaea honeypot / IM Honeypots/ ssh honeypots… to collect) • Use social engineering tac&cs to trick users into install malwares • Spam Mail: Send spam messages that contain malware links to malware • Drive-‐by Downloading: Web pages including exploits to use specific browser vulnerabili&es to secretly install malware by exploit kits
- 13. Evolu<on Considera<ons … (Cont.) 13 Bots Crea<on Botnet Spreading Botnet Controlling Botnet Defending Botnet Commerce Evolving Upgrade Bot-‐herders contact C&C servers for instruc<ons • Spamming • Phishing & Fast Flux • Stealing Confiden&al Data • Distributed Denial-‐of-‐Service (DDOS) • Compromising and Installing Malware • Distribu&ng Malware • Click Fraud • Adver&sement Fraud
- 14. Evolu<on Considera<ons … (Cont.) 14 Bots Crea<on Botnet Spreading Botnet Controlling Botnet Defending Botnet Commerce Evolving Upgrade Bot Creators use many techniques to prevent from detected • Enable secure communica&on in IRC channel • Rootkit Component • Scrip&ng Language • Malware Polymorphism • Strong Cryptography • Distributed Network Architecture (P2P Botnet: Storm, Waledac)
- 15. Evolu<on Considera<ons … (Cont.) 15 Bots Crea<on Botnet Spreading Botnet Controlling Botnet Defending Botnet Commerce Evolving Upgrade Black market associated with online communi<es of bot-‐herders and malware authors • Sell/rent bots controlling network to spammers and aeackers • Sell collec&ons of bots • Offer lists of vulnerable IP addresses hos&ng web services • Sell “bulletproof” hosts for C&C server installa&on • Sell undetectable u&li&es such as packer, encryptor, rootkits, … etc.
- 16. Evolu<on Considera<ons … (Cont.) 16 Bots Crea<on Botnet Spreading Botnet Controlling Botnet Defending Botnet Commerce Evolving Upgrade Adver<sing in black market featuring legi<mate e-‐commerce. • Offer poten&al buyer a free trial • Verified seller and seller reputa&on evalua&on • Provide round-‐the-‐clock technical support for purchasers • Scammer informing • Up-‐to-‐date malware crea&on kits on sales • Wri&ng tutorials and answering ques&ons by newcomers
- 17. Hack Forums for different purposes 17 XBOX, PSP, PS3 Hacking Forum
- 18. Hack Forums for different purposes (Cont.) 18 Gaming Hacking and Sharing In this forum
- 19. Hack Forum for different purposes (Cont.) 19 Cracking and Hacking Forums
- 20. Hack Forum for different purposes 20
- 21. Hacker Forum of Russian 21
- 22. Botnet Infrastructure observa<on in 2009 2. Setup Botnet C&C Server and fast-‐flux xxxx.asia xxxx.asia xxxx.asia xxxx.asia xxxx.asia 1.Register Domain xxxx.asia Botnet Developer 3. Bot Controlling 4. Sell botnets 5.Control botnets 6. Criminal Ac<vi<es inside Botnets YouTube ddos exploits downlaod Phishing Sites Click Informa&on Stealer DDOS Exploits / New malware SSH Brute Flooding (new target) Web Panel used to show bots and selling service Most IRC-‐Based Botnet
- 23. Botnet Today 23 Botmaster / Opera&on Team Online Black Market adver<sing Aeacker/ Spammer Phisher buying Proxy Domain Encrypted Commands Control Panel Exploits Pool Control Infrastructure = Fast-‐Flux + C&C Servers +Exploit Kits + Protect Mechanisms Different C&C, different purposes Venerable web applica&ons Inject IFrame into web pages Bots DDOS Exploits / New malware Account Stealer Phishing Sites Click Informa&on Stealer Malicious Ac&vi&es Launch New Vic&ms drive-‐by-‐download aeack drive-‐by-‐download aeack Automa&cally vulnerability Spreading New Vic&ms
- 24. Botnet Today (Cont.) • Most botnets assembling with exploit kits to fast spread, control and upgrade • Evasion technologies make botnet detec&on difficult • Mul&-‐source logs on botnet scenario detec&on • Exploit kits analysis is essen&al to detect malicious ac&vi&es 24
- 25. 25 Botnet caused from RFI Vulnerabili&es
- 27. ? demarc ssh.bl4ze.info 140.127.77.224
- 28. 140.127.77.224 kssa.noorno.com、im.maximum-irc.info ssh.bl4ze.info • Mal/Cimuz-F ,MD5:0DCD39473885EF9FDDAD24DCA1E0AE00 v http://kssa.noorno.com/5506/otpspuppsp/dZom/ooo0qx0zpwvp/0cadihSfBOaS/ v http://kssa.noorno.com/5968/GLHKHMHIKL/51GE/GGGSIPSRHONH/S425A9u7dq2u/ v http://kssa.noorno.com/6747/puqtqvqrur/eapn/ppp1ry10qxwq/1dbejiTgCPbT/ v http://kssa.noorno.com/7556/sxtwtytux1/hdsq/sss4u143t0zt/4gehmlWjFSeW/ v http://kssa.noorno.com/2443/PUQTQVQSPV/EAPN/PPPbRYbaQXWQ/bDBEJI3GmzB3/ v http://kssa.noorno.com/6534/OTPSPUPPSW/D9OM/OOOaQXaZPWVP/aCADIH2FlyA2/ v http://kssa.noorno.com/7297/hmiliniimm/WShf/hhhtjqtsipoi/tVTWbaLY4HTL/ v http://kssa.noorno.com/2059/DIEHEJEFDF/2yDB/DDDPFMPOELKE/P1z276r4anzr/ v http://kssa.noorno.com/2047/1625272321/qm1z/111D3ADC2982/DpnqvufsObnf/ v http://kssa.noorno.com/2840/otpspupqpv/dZom/ooo0qx0zpwvp/0cadihSfBOaS/ v http://kssa.noorno.com/3618/MRNQNSNOOQ/B7MK/MMMYOVYXNUTN/YA8BGF0Djw80/ v http://kssa.noorno.com/4397/v0wzw1wxyw/kgvt/vvv7x476w32w/7jhkpoZmIVhZ/ v http://kssa.noorno.com/5190/injmjojklq/XTig/iiiukrutjqpj/uWUXcbMZ5IUM/ • P2P-Worm.Win32.Palevo.rmm :0F48EE11F8AD24456B28C36328990D29 v im.maximum-irc.info: 93.62.62.208、140.127.77.224、147.8.75.135、163.20.82.20、180.214.42.135 • IM-Worm.Win32.Zeroll.b: 54EE505C58D88D60D5ED22CD0776D918 v ssh.bl4ze.info : 93.62.62.208、129.10.137.173、129.21.118.15、139.91.102.100、 139.91.102.101、140.127.77.224、147.8.75.135、147.102.159.9、180.214.42.135 28
- 29. Part II: Web Exploit Kits
- 30. What is exploit kits ? • An exploit kit is a web applica&on that serves mul&ple exploits through browsers or applica&ons to carry out automated drive-‐by-‐ downloading aeacks for malware distribu&ng. (Exploit Driven) • Web browser as aeack vector 30
- 31. Exploit kits by numbers 31 Data from MalwareDomainList Reference: Exploit Kits – A Different View hep://www.securelist.com/en/analysis/204792160/Exploit_Kits_A_Different_View 1. Phoenix 2. Eleonore 3. Neosploit
- 32. What is exploit kits ? (Cont.) • Exploit Kits Components: v Exploits Pack v Install file v Configura<on file v Database Schema v Administra<on Panel: • Launch and manage exploits using the central management console • Connect to database for logging and repor&ng • Upload malwares to vic&ms • Upload spam mail content and recipients lists 32
- 33. What is Web Exploit Kits: (Cont.) • Exploit kits installed onto a web server as a web applica&on such as Apache + PHP + MySQL • Special features developed to present exploit kits author’s mo&va&on, most likely bypass AVs scanning and IPS v Code obfuscated v URL Random Link Structure v Code Cryptor v Exploit rota&on • The first exploit kit tool is MPack 33 Exploit Kits Name Authors From Price Vulnerability MPack (2006. 12) Russian Cracker $500~ $1000 $50~$150 (new!) MS06-‐014, MS06-‐006, MS06-‐044, ANI overflow, XML Overflow, WebViewFolderIcon overflow, WinZip Ac&veX overflow, QuickTime overflow
- 34. 34 CVE-‐2003-‐O111 M503-‐O11 -‐ ByteCode Verifier component flaw in Microsov VM CVE-‐2004-‐1043 MSOS-‐OO1 HTML vulnerabili&es CVE-‐2004-‐0549 MSHTML IE6 CVE-‐2005-‐2127 COM Object Instantaa&on Memory Corrup&on (Msdssdll) CVE-‐2005-‐2265 FF CompareTo MFSA2005-‐50 -‐ Firefox Install VersioncompareTo CVE-‐2005-‐0055 IE 5.01, 5.5, and 6 DHTML Method Heap Memory Corrup&on Vulnerability CVE-‐2006-‐0003 MDAC MS06-‐014 for lE6/Microsov Data Access Components (MDAC) Remote Code Execu&on CVE-‐2006-‐0005 FF EMBED / MS06-‐006 MS06-‐006 -‐ Windows Media Player plug-‐in vulverabiIity for Firefox & Opera CVE-‐2006-‐1359 MS06-‐013 -‐ CreateTextRange CVE-‐2006-‐3643 Microsov Management Console (MMC) Redirect Cross-‐Site Scrip&ng (XSS) vulnerability (IE) CVE-‐2006-‐3677 Firefox Jno / JNO Firefox -‐js navigator Object Code CVE-‐2006-‐3730 WebViewFolderlcon (IE) CVE-‐2006-‐4777 DirectAnima&on Ac&veX Controls Memory Corrup&on Vulnerability CVE-‐2006-‐4868 MSO6-‐055 -‐ Windows Vector Markup Language Vulnerability CVE-‐2006-‐5559 IE6 MDAC MS07-‐009-‐ lE6/Microsov Data Access Components (MDAC) Remote Code Execu&on CVE-‐2006-‐5745 Microsov XML Core Services Vulnerability CVE-‐2006-‐5820 AOL SuperBuddy Ac&veX Control LinkSBlcons() Vulnerability CVE-‐2006-‐6884 Winzip FileView Ac&veX (IE) CVE-‐2007-‐0015 Apple QuickTime RTSP URI (lE) CVE-‐2007-‐0018 NCTsov NCTAudioFile2 Ac&veX Control Remote Buffer Overflow Vulnerability CVE-‐2007-‐0024 Vector Markup Language Vulnerability (IE) CVE-‐2007-‐0071 FLASH 9 Integer overflow in Adobe Flash Player 9 CVE-‐2007-‐0243 JAVA GIF PARSE : Java GIF file parsing vulnerability CVE-‐2007-‐3147/3148 Yahoo! Messenger Webcam (IE) CVE-‐2007-‐4034 Yahoo! Widgets YDP (IE) Usually to use known vulnerabili<es:
- 35. 35 CVE-‐2007-‐4336 DirectX -‐ DirectTransform FlashPix Ac&veX (IE) CVE-‐2007-‐5327 CA BrightStor ARCserve Backup Mul&ple VulnerabiIi&es CVE-‐2007-‐5659/2008-‐0655 collab, collectEmaillnfo PDF Exploit -‐collab, collectEmaillnfo CVE-‐2007-‐5755 AOL Radio AmpX Buffer Overflow CVE-‐2007-‐6250 AOL Radio AmpX (AOLMediaPlaybackControl) Ac&veX control vulnerability CVE-‐2008-‐0015 IE6/IE7 DSHOW MS09-‐032 DirectX DirectShow (IE) CVE-‐2008-‐1309 RealPlayer Ac&veX Control Console Property Memory Corrup&on CVE-‐2008-‐2463 M508-‐041 -‐ MS Access Snapshot Viewer CVE-‐2008-‐2992 PDF Exploit• u&l.prin{ CVE-‐2008-‐4844 Iexml Internet Explorer 7 XML Exploit CVE-‐2008-‐5353 JAVA JRE / Javad0 / Javado / Java Calendar / javaold/JavaSr0 Javad0—JRECalendar Java Deserialize CVE-‐2009-‐0075/0076 IE7 MEMCOR in IE7 MS09-‐002 MS09-‐002 -‐ lE7 Memory Corrup&on CVE-‐2009-‐0355 Firefoxdiffer Firefox -‐ Components/sessionstore/src/nsSessionStore.js CVE-‐2009-‐0836 PDFOPEN Adobe Reader -‐ Foxit Reader PDF OPEN CVE-‐2009-‐0927 PDF collab.getIcon / pdf-‐gi PDF Exploit-‐ collab.getlcon CVE-‐2009-‐1136 Spreadsheet MSO9-‐043 -‐ lE OWC Spreadsheet Ac&veX control Memory Corrup&on CVE-‐2009-‐1538 MS09-‐028 Microsov DirectShow Remote Code Execu&on. CVE-‐2009-‐1671 Java buffer overflows in the Deployment Toolkit Ac&veX control in deploytk.dll CVE-‐2009-‐1862 Memory corrup&on via a craved Flash applica&on in a .pdf file or a craved .swf fil (authplay.dll) CVE-‐2009-‐1869 Flash 10 Integer overflow in the AVM2 abcFile parser in Adobe Flash Player CVE-‐2009-‐2477 Firefox 3.5 contains a vulnerability in TraceMonkey components of Firefox's JavaScript engine CVE-‐2009-‐2477 Mozilla FF 3.5 Exploit / font tags Firefox -‐ Font tags CVE-‐2009-‐3269 TELNET -‐ for OPERA 9.0 -‐ 9.25 or OPERA Telnet for Opera Th3270 CVE-‐2009-‐3867 JAVA GSB Java Run&me Env. getSoundBank Stack BOF CVE-‐2009-‐3958 download mgr buffer overflows in the NOS Microsystems getPlus Helper Ac&veX control before 1.6.2.49 in gp.ocx in the Download Manager in Adobe Reader and Acrobat CVE-‐2009-‐4324 PDF mediaNewPlayer / pdf-‐mp PDF Exploit -‐ docmedianewPlayer
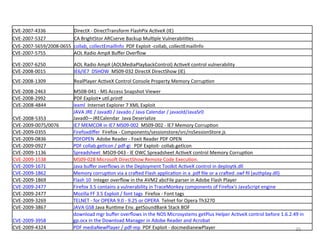
- 36. 36 CVE-‐2010-‐0188 PDF Lib&ff / Lib PDF Exploit -‐ LibTiff Integer Overflow CVE-‐2010-‐0249 Aurora se-‐aver-‐free vulnerability in Microsov Internet Explorer 6, 6 SP1, 7, and 8 cve-‐2010-‐0094 Javarmi Java Run&me Environment component in Oracle Java SE CVE-‐2010-‐0806 IEPeers msiemc IEPeers Remote Code Execu&on IE7 Uni&alized Memory Corrup&on CVE-‐2010-‐0840 JAVA TC (?) javagetval OBE Trusted Method Chaining -‐ Java getValue Remote Code Execu&on CVE-‐2010-‐0842 JAVA MIDI Java OBE Unspecified vulnerability in the Sound component in Oracle Java SE and Java for Business 6 Update 18, 5.0 Update 23, 1.4.2_25, and 1.3.1_27 allows remote aeackers to affect confiden&ality, integrity, and availability via unknown vectors. NOTE: the previous informa&on was obtained from the March 2010 CPU. Oracle has not commented on claims from a reliable researcher that this is an uncontrolled array index that allows remote aeackers to execute arbitrary code via a MIDI file with a craved MixerSequencer object, related to the GM_Song structure. CVE-‐2010-‐0886 JAVA SMB / JAVA JDT Java SMB / Java JDT in Oracle Java SE and Java for Business JDK and JRE 6 Upd 10-‐19 * Requires xtra components CVE-‐2010-‐1240 PDFOPEN Open/Launch embedded exe via built in func&onality, ability to change user prompt text. Reported by Didier Stevens. CVE-‐2010-‐1297 Adobe PDF SWF CVE-‐2010-‐1423 javanew JWS Java Deployment Toolkit Remote Argument Injec&on Vulnerability (Taviso) CVE-‐2010-‐1818 QuickTime 6.x, 7.x Read func&on in QTPlugin.ocx allows remote aeackers to execute arbitrary code via the _Marshaled_pUnk aeribute CVE-‐2010-‐1885 HCP Help Center URL Valida&on Vulnerability CVE-‐2010-‐2883 PDF FONT / Cooltype PDF Exploit Adobe Reader Stack-‐based buffer overflow in CoolType.dll CVE-‐2010-‐2884 Adobe authplay.dll Ac&onScript AVM2 memory corrup&on Vulnerability – Adobe Reader < 9.4.0 – ALL Windows CVE-‐2010-‐3552 JAVA SKYLINE Unspecified vulnerability in the New Java Plug-‐in – Java 6 < Update 22 – IE Only – ALL Windows CVE-‐2010-‐3653 The Director module (dirapi.dll) in Adobe Shockwave Player CVE-‐2010-‐3962 CSS Clip Use-‐aver-‐free vulnerability in Microsov Internet Explorer 6, 7, and 8 CVE-‐2010-‐3971 IE-‐8 css parser Use-‐aver-‐free vulnerability in the CSharedStyleSheet::No&fy func&on in the Cascading Style Sheets (CSS) parser in mshtml.dll CVE-‐2010-‐4452 Sun Java Applet2ClassLoader Remote Code Execu&on Exploit "Java JSM” maybe means JMS CVE-‐2010-‐4438 ? OSVDB-‐61964 AOL 9.5 Phobos.Playlist (Phobos.dll) Ac&veX Control Import EDB-‐11175 Windows Media Player 11 Ac&veX launchURL() files download
- 37. Case Study: Ice-‐Pack Exploit • Released on 2007.06 by IDT Group in Russian • A tool kit for installing malware through exploits • Allow automa&c injec&on of malicious iframes into websites • Price: v Lite Edi&on ($30): only MS06-‐014 and MS06-‐006 exploits v Pla&num Edi&on ($400) • Exploits: v MSIE 6: MDAC(RDS), Zenturi, XML Core Services, VML, WebViewFolderIcon v MSIE 7: x16 v Firefox: WMF Firefox v Opera 9-‐9.20 v Opera 7: .ANI(animated cursor) v QuickTime overflow buffer flow 37
- 38. Ice-‐Pack administra&on panel 38 GENERAL STATISTICS FTP WORK TOOLS LOGOUT OS Browsers Loads Countries Referers Clean Import Check Inject Clean Iframe Traffic Sekng Scripts with FTP tools will automate iframe injec<on into websites
- 39. Obfusca&on technology in ICEPack 39
- 40. How Ice-‐Pack Exploit Kits Works 40 Malicious Links IFrame Injec&on URL Redirect Vic&ms Exploit Kits Botnet C&C Vulnerable website 1. Iframe Injec&on 2. HTTP Redirec&on 2. HTTP Redirec&on 3.Grab OS/ Browser Version 4. Exploits pack 6. Download Bots 5. Exploits infec&ng 7. Connect to C&C
- 41. Case Study: Phoenix Exploit 41
- 42. Case Study: Phoenix Exploit (Cont.) • Original from Russian, price from 200USD to 2000USD • One of the best Browser Exploit Pack (BEP) in black market, also one of the most ac&ve malicious crimeware today. • Kits keep to update by upda&ng the exploit base and improving the administra&on panel 42 • Phoenix Exploit’s Kit v1.31 • Phoenix Exploit’s Kit v1.3 • Phoenix Exploit’s Kit v1.2 • Phoenix Exploit’s Kit v1.1 • Phoenix Exploit’s Kit v1.0 • Phoenix Exploit’s Kit v1.0beta • Phoenix Exploit’s Kit v2.7 • Phoenix Exploit’s Kit v2.5 (2011.01) • Phoenix Exploit’s Kit v2.4 • Phoenix Exploit’s Kit v2.3 • Phoenix Exploit’s Kit v2.21 • Phoenix Exploit’s Kit v2.2 • Phoenix Exploit’s Kit v2.1 • Phoenix Exploit’s Kit v2.0 • Phoenix Exploit’s Kit v1.4
- 43. Case Study: Phoenix Exploit (Cont.) 43 Installa<on Wizard
- 44. Case Study: Phoenix Exploit (Cont.) 44 Installa&on Complete Phoenix Exploit Panel Samba Pool Exploits Update
- 45. Case Study: Phoenix Exploit (Cont.) 45 Bypass AVs Scanning Only Kit Owner can reach correct links and filename Data to access sta<s<cs: hep://xxx.xxx.xxx.xxx/phoenix/bnyojnxzfsariuatk7.php Link for traffics: hmp://xxx.xxx.xxx.xxx/phoenix/hscrasg6.php Name of config's file: awfpkqynhpgmdqxw.php Name of .exe file: epczgvksingvesam.exe Server-‐Side Polymorphism
- 46. Case Study: Phoenix Exploit (Cont.) 46 Exploits Sta&s&cs Opera&on systems sta&s&cs Advanced browsers sta&s&cs Countries Sta&s&cs Panel to upload malwares
- 47. Case Study: Phoenix Exploit (Cont.) • Features: v Password to access administrtor panel encoded in SHA1 v Detect OS and browsers to exploit • XPIE7: IE7+WinXP, IE7+WinXP SP2, IE7+Win2003 • VISTAIE7: IE7+WinVista • XPIE8: IE8+WinXP, IE8+WinXP SP2, IE8+Win2003 • VISTAIE8: IE8+WinVista • IE: not IE7 or IE8 • WIN7IE: IE7+Win7 • XPOTHER: Browser+ WinXP/WinXP SP2/Win2003 • VISTAOTHER: Browsers + WinVista • WIN7OTHER: Browsers + Win7 47
- 48. Case Study: Phoenix Exploit (Cont.) • Exploits Lists: v CVE-‐2006-‐0003: IE MDAC v CVE-‐2007-‐0071: Adobe Flash 9 v CVE-‐2009-‐1869: Adobe Flash 10 v CVE-‐2007-‐5659: Adobe Reader CollectEmailInfo v CVE-‐2008-‐2992: Adobe Reader u&l.prin{ v CVE-‐2009-‐0927: Adobe Reader Collab GetIcon v CVE-‐2009-‐4324: Adobe Reader newPlayer v CVE-‐2010-‐0188: Adobe Reader LibTiff v CVE-‐2010-‐1297: Adobe PDF SWF v CVE-‐2009-‐0836: Adobe Reader/Foxit Reader PDF OPEN v CVE-‐2009-‐3867: Java HsbParser.getSoundBank (GSB) v CVE-‐2008-‐5353: Java Run&me Environment (JRE) v CVE-‐2010-‐0746: Java SMB v CVE-‐2010-‐0806: IE iepeers v CVE-‐2010-‐1885: Windows Help Center (HCP) v CVE-‐2008-‐2463 : IE SnapShot Viewer Ac&veX • Java has become the leading exploit vector including three Java exploits v JAVA RMI v JAVA MIDI v JAVA SKYLINE 48
- 49. Case Study: Phoenix Exploit (Cont.) • Exploit Vulnerability: CVE-‐2009-‐3867 v Java applica&on using import javax.sound.midi.* v an error in the implementa&on of the HsbParser.getSoundBank func&on that can be exploited to result in a stack-‐based buffer overflow. 49
- 50. Exploit Kits Analysis (The First Step is to find possible landing pages) 50 • Unknow • Tor • Target-‐Exploit • Smart pack • RDS • My poly sploit • mul<sploit • mypack-‐009 • mypack-‐091 • mypack-‐086 • mypack-‐081 • Mpack0.91 • Infector • Ice-‐pack-‐1 • G-‐pack • Firepack -‐1 • Fiesta • Cry 217 • Armitage • Adpack -‐1 • Blackhole • Spyeye • Phonix • Open Source exploit kit • Neosploit • Zues • Crimepack URL Structure Iden<ty Exploits Collec<on The Order of Exploits Suppor<ng Func<ons Web Page Web Page Web Page Web Page Web Page Web Page Web Page Web Page Web Page Web Page Web Page Web Page Web Page Web Page Web Page Web Page Web Page Tes&ng Mapping
- 51. Exploit Kits Analysis (Cont.) URL Structure Iden<ty 51 • hep://nijade.info/shop/cmbrepksx.php • hep://mafddy.net/f1/bsfokphmbvbmguxqxoal7.php • hep://1gov.co.cc/pk1/fqduxtgqgsaoamdnj5.php • hep://deliverme1.com/phoenix/yqgpksgwhzaqbrc.php • hep://sanstag.com/adv/astr/dmx{zysjq.php • hep://ops06.lianade.co.cc/jmxvcsfp.php • hep://unfor&neg.com/vbdd2syptp.php?a=2048508 • hep://78.24.216.8/graucwjucugvfo2.php?n=9831383 • hep://92.63.99.108/graucwjucugvfo2.php?n=9831383 • hep://4ogne5yh98f.com/ywdngzevkw.php?n=USAPUTIN • hep://9kq6z1j.co.cc/d3vic3/iuivklkq.php?n=2412 • hep://4bfa61.co.cc/d3vic3/iuivklkq.php?n=173 • hep://dofubuhud57.co.cc/7box/awhwhwhvhujqdpko6.php?n=setup2412 Phoenix Exploits: Blackhole exploit kit hep://gamq.cz.cc/index.php?tp=7036fe8a9511ef97 hep://analy&cs2.virgilguard1.com/index.php?tp=98a8c9d4da3191f5 hep://ko6l.co.cc/index.php?tp=8f08c7d047b89566 hep://greenpix2.in/forum.php?tp=ef21b9264369e755 hep://sqnytcnq.co.tv/forum.php?tp=dd05b6b7bbcae20d hep://ojcefurhxw.zapto.org/forum.php?tp=64cec1960ed52132 hep://bjktyhdasffer.tld.tc/index.php?tp=79b7135bf7723a7c hep://servisd‚jdeet.com/index.php?tp=453bebƒ70600d45 Neosploit Exploit kit hep://ujgesfovsd.in/cgi-‐bin/azz hep://ujgesfovsd.in/cgi-‐bin/ion hep://nade.co.cc/cgi-‐bin/gzd hep://nade.co.cc/cgi-‐bin/ouy
- 52. Exploit Kits Analysis (Cont.) Exploits Collec<on 52 Obfusca<on Technology v.s Exploit Code
- 53. Exploit Kits Analysis (Cont.) MS09-‐002: Internet Explorer Remote Code Execu<on Vulnerability 53
- 54. Exploit Kits Analysis (Cont.) 54
- 55. Exploit Kits Analysis (Cont.) The Order of Exploits 55 Order of explots browser: • hep://xxx.in/cgi-‐bin/azz • hep://xxx.in/cgi-‐bin/etn • hep://xxx.in/cgi-‐bin/gjj • hep://xxx.in/cgi-‐bin/gyw • hep://xxx.in/cgi-‐bin/io • hep://xxx.in/cgi-‐bin/iok • hep://xxx.in/cgi-‐bin/ion • hep://xxx.in/cgi-‐bin/ip • hep://xxx.in/cgi-‐bin/jjo Exploit Pack IE MS06-‐006 Winzip MS06-‐014 MS06-‐057 JAVA JRE Firefox MS06-‐006 Opera Quick&me MS06-‐006
- 56. Exploit Kits Analysis (Cont.) Suppor<ng Func<ons • Code obfusca<on are composed: v Encrypt / Decryptor • Base 64 Encoding • Dean Edwards packer • String splits • Gzip Encoding • Custom Encoders • ionCube Loader: a PHP extension that works to decode PHP scripts previously encoded by the ionCube PHP Encoder package v Mul&-‐level Loop based on algorithm • An<-‐Authen<ca<on Bypass • Self-‐Cryptor Algorithm • …. 56
- 57. How Exploit Kits Bring Money In 1. Kits and vic&ms ren&ng 2.Steal cri&cal informa&on 3.Sending spam Control Panel Exploit Kit Creator Exploit Kit Operator Botnet Herders, Spammers Underground Criminals Online Black Market Kits adver&sing Vic<ms adver<sing Buy malicious ac&vity ex:DDOS Buy cri&cal informa&on Pay for exploit kits (100USD~1000USD) 1. Pay for traffic providers to click exploit codes 2. Pay for install third party sovwares • Spambots • Informa&on stealers like Zeus • Password stealers • Fake AVs Service Traffic Providers (Click Fraud) Pay-‐Per-‐Install Operator Pay for generic malware func&ons ex: cryptors Pay for installa&on of malicious applica&on, such Fake AV
- 58. Pay-‐per-‐Install • One of the business models by which an affiliate system provides a set of "clients” • Paying each a percentage of money as a commission for each installa&on the malicious applica&on successful. 58
- 59. Exploit Kits in Black Market 59
- 60. The Trend of Exploit Kits: • Easy to find exploits kits adver&sements in black markets • Install exploit kits on free or cheap hos&ng services • Kits author keeps to upgrade, bug fixed and support on exploit kits by adding new exploits • Java/Browser/PDF/Flash are major vulnerabili&es to be infected. • Using a complicated obfusca&on to handle AVs and IPSs • Combine with SEO poisoning • Increase the probability of successful when mul&ple exploits are used against dissimilar targets. 60
- 61. Conclusions: • Botnet and exploit kits are closely related. • Exploit kits detec&on is essen&al to eliminate botnet threats • How exploit kits work: v Inject HTML iframe/Scripts into web pages v Embed HTML iframe in spam mail v Exploi&ng Un-‐patched vulnerabli&es v Drive-‐by-‐download install malware • Hope to rise exploit kits threat to all par&cipants. 61
- 62. References • Web Exploits: There's an App for That v hep://www.google.com.tw/url?sa=t&source=web&cd=1&ved=0CBgQFjAA&url=hep%3A%2F %2Fwww.m86security.com%2Fdocuments%2Fpdfs%2Fsecurity_labs %2Fm86_web_exploits_report.pdf&ei=2XEkTsiDNcromAWzpvGcAw&usg=AFQjCNGennJqF62s uQXrvXgXmRMn9f4Dfw&sig2=WNzmg6BN6O5WuY43KALYg • Modern Botnets: A Survey and Future DirecCons v hep://docs.karamatli.com/paper/karamatli-‐modern_botnets.pdf • Volume 9. January through June 2010. Microsos | Security Intelligence Report v download.microsov.com/download/8/1/B/81B3A25C-‐95A1-‐4BCD-‐88A4-‐2D3D0406CDEF/ Microsov_Security_Intelligence_Report_volume_9_Jan-‐June2010_English.pdf • Exploit Kits: A different View v hep://www.securelist.com/en/analysis/204792160/Exploit_Kits_A_Different_View • Phoenix Exploit Kit (2.4) -‐ Infec<on Analysis v hep://secniche.blogspot.com/2010/10/phoenix-‐exploit-‐kit-‐24-‐analysis.html • Phoenix Exploit’s Kit From the mythology to a criminal business v hep://www.malwareint.com/docs/pek-‐analysis-‐en.pdf 62
- 63. Q & A Thank you for your amen<on !!