Fault tolerance in wireless sensor networks by Constrained Delaunay Triangulation Coverage Strategy
- 1. A Presentation on Fault Tolerance in Wireless Sensor Networks by Constrained Delaunay Triangulation Coverage Strategy Under Guidance of: Presented by :- Prof. Dr. Santosh Kumar Swain Ramnesh Dubey Dept. of Computer science & Engg. Branch: M. Tech.(CSE) KIIT University Roll no: 1050013 1
- 2. Outline 1. Introduction 2. Literature Survey 3. Motivation 4. Problem Definition 5. Objective 6. Proposed Work 7. Simulation Result 8. Comparison 9. Conclusion 10. Future Work 11. References 2
- 3. Introduction Development of sensor nodes, Advances in with sensing, data processing, wireless and communicating Communications components: low cost low dimension low power consumption Sensing Computing low memory Communication low computational power A wireless sensor network is composed by a large number of sensor sensing self-powered nodes. 3
- 4. Introduction (Contd.) Energy Efficiency Deployed Sensor Coverage network Fault tolerant: The system should be robust against node failure. 4
- 5. Literature Survey • Coverage in WSNs: Coverage Fault Deployment Energy Event Type Radii Tolerance Strategies Efficiency Transfer Target Area Fixed Variable Coverage coverage 5
- 7. Literature Survey (Contd.) Coverage Strategies Coverage Strategies Computational Force Based Grid Based Geometry Based Triangular Lattice Voronoi Diagram Square Grid Delaunay Triangulation Hexagonal Grid Constrained Delaunay Triangulation 7
- 8. Motivation • Coverage strategies proposed so far do not facilitate fault tolerance and energy efficiency together. • Sensor networks are energy constrained as they are battery operated, but in addition to provide fault tolerant coverage, the energy efficiency of the network must be maintained. • K - coverage mechanisms proposed in the literature are not energy efficient as several sensors report simultaneously, leading to excessive energy consumption, congestion, and collisions in the network. • This reduces the quality of service and network performance. 8
- 9. Problem Definition To incorporate in Coverage strategy • Event Reporting. • Energy Efficiency. 9
- 10. Objective My objective is to enhances a fault tolerant coverage protocol that incorporate. • Event reporting with the help of additional support structure and • Energy efficiency by reducing the communication. 10
- 11. Proposed Work Deployment Coverage Backup Coverage Distributed Greedy Algo. Constrained Delaunay Triangulation Algo. And Selection of Backup node 11
- 12. Proposed Work (Contd.) 12
- 13. Proposed Work (Contd.) 13
- 14. Proposed Work (Contd.) Distributed Greedy Algo. • Procedure 2-COVERAGE (S [ ]) • S [ ] is the set of sensor nodes deployed • R is the region to be covered • snode ← S[x] : x is randomly selected node • while (R is not Covered) do • dbl[i]← snode • snode← broadcast() • snode ←recv() • snode ←maxBenifit() • i ←i+1 • end while • end procedure 14
- 15. Proposed Work (Contd.) Algorithm for Constrained Delaunay triangulation CDT 1.Construct DT, set color of each node to WHITE, and broadcast all its 1-hop neighbor information using the packet Neighbor_Packet. 2.Nodes having lowest id among its 2-hop neighbors set their color to BLACK. 3. Each BLACK node chooses a set N of nodes from its 1-hop neighbors using the following method. (a) N = empty (b) n1 = farthest neighbor (c) N = N ᴜ n1 (d) for i = 2, 3,. . . 15
- 16. Proposed Work (Contd.) Algorithm for Constrained Delaunay triangulation CDT { ni = choose ith farthest neighbour if ni makes more than 60 degree angle with n1 , n2 , . . . , ni - 1 then N = N ᴜ ni } 4. Each BLACK node add the constraint edges to the nodes in N and broadcasts these constraint edges information using the message Constraint _Packet. 5. Each WHITE node sets its color = BROWN if it is other end of any constrained edges received using Constraint _Packet. 6. Each BROWN node broadcasts its constraint edge information using the control packet Constraint _Packet. 7. All WHITE and BROWN nodes remove edges connected to it which crosses constraint edged, this information is broadcasted using Edge cross _Packet. 8. Each-BLACK node places a new edge from the WHITE nodes, from which the edge was deleted in the previous step to from new triangles. 16
- 17. Proposed Work (Contd.) Selection of Backup Nodes Algo. • Procedure: BK SELECT (dbl [ ]) • • dbl [ ] is the set of sensor nodes providing 2Coverage • • Neighbors [ ] is the set of Triangle Neighbors of each node • • i ←0 • while i ≠ dbl.end() do • • if dbl[i].area() ≡ Neighbors [ ].area() then • backup[ j] ← dbl[i] • PotPri[] ←nearest(Neighbors[],backup[ j]) • PotPri[] ←median(Neighbors[],backup[ j]) • i ← i+1 • end if • end while • while i ≠ PotPri.end() do • if PotPri.area() ≡ Neighbors [ ].area() then • backup[] ←PotPri[i] • erase(PotPri[i]) • end if • end while • end procedure 17
- 18. Proposed Work (Contd.) • Selection of Backup Nodes: 18
- 19. Proposed Work (Contd.) • Backup Node Functionality: Event Detection Backup Reporting 19
- 20. Proposed Work (Contd.) • Event Reporting a. Several nodes detecting and reporting events to common forwarder. b. A node and its forwarder detecting the event. c. Channel access issues. 20
- 21. Proposed Work (Contd.) • Event Reporting Handle the all three challenges 21
- 22. Simulation Result Simulation Environment Parameter Low Power Value High Power Value Number of nodes 50 50 Area Range (m*m) 1000 1000 Transmission range (m) 195 195 Data Packet size 512 512 Bandwidth (Kbps) 2.4 100 Transmit power (mW) 14.88 660 Receive power (mW) 12.50 395 Idle power (mW) 12.36 350 sleep power (mW) 1.4 300 22
- 23. Simulation Result (Contd.) • Throughput Low Power 23
- 24. Simulation Result (Contd.) • Throughput High Power 24
- 25. Simulation Result (Contd.) • Packet Drop Rate Low Power 25
- 26. Simulation Result (Contd.) • Packet Drop Rate High Power 26
- 27. Simulation Result (Contd.) • Average Packets End to End Delay Low Power 27
- 28. Simulation Result Cont. • Average Packets End to End Delay High Power 28
- 29. Simulation Result (Contd.) Fault Node / Active Node 29
- 30. Simulation Result (Contd.) Fault Node / Active Node 30
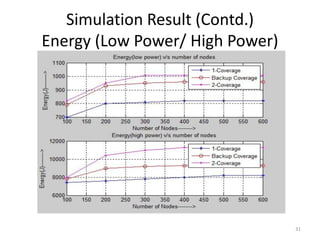
- 31. Simulation Result (Contd.) Energy (Low Power/ High Power) 31
- 32. Comparison Delaunay Triangulation Vs. Constrained Delaunay Triangulation 32
- 33. Comparison (Contd.) Delaunay Triangulation Vs. Constrained Delaunay Triangulation S.No. Features Delaunay Constrained Delaunay Triangulation Coverage Triangulation strategy Coverage strategy 1 Simulation Scenario Matlab Matlab 2 Numbers of 50 50 Nodes 3 Area 1000 1000 4 Dimensions 2D 2D 5 Distance Computed Formula 6 Sensors Communicate Distance Sensing Distance Sensing Condition Range Range 33
- 34. Comparison Cont. S.No. Features Delaunay Triangulation Constrained Delaunay Coverage Triangulation strategy Coverage strategy 7 Coverage Optimization Coverage Area Coverage 8 Sensing Range Irregular Sensing Range Regular Sensing Range 9 Strategy Geometry Based Geometry Based 34
- 35. Comparison (Contd.) Delaunay Triangulation Other Related Work 35
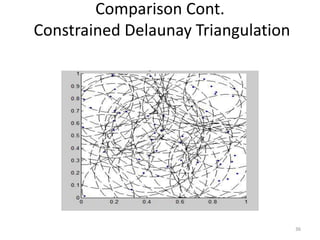
- 36. Comparison Cont. Constrained Delaunay Triangulation 36
- 37. Comparison (Contd.) Constrained Delaunay Triangulation 37
- 38. Conclusion To provide quality service by coverage strategy, there arises a need for developing protocols to provide. • Fault tolerance. • Event reporting and • Maintain energy efficiency. 38
- 39. Future Work • Better mechanisms in choosing the minimal number of nodes for our Coverage Strategy. • Lowering the contention in the Network. • Low latency. 39
- 40. Dissertation R.Dubey, S.K.Swain, C.P.Kashayp, R.Bera “Fault Tolerance in Wireless Sensor Networks Using Constrained Delaunay Triangulation”, International Conference on Electrical Engineering and Computer Science (ICEECS), IRNet, April 2012. • R.Dubey, S.K.Swain, N.S.Mandal, C.M.Mourya, “Constrained Delaunay Triangulation for Wireless Sensor Networks", Elsevier Ad Hoc Networks,2012.( Communicated) 40
- 41. References [1] P.Kumari and Y.Singh. “Delaunay Triangulation Coverage Strategy for Wireless Sensor Networks”. IEEE (ICCCI), pages 1-5, 2012. [2] R.H.Abedi, N.Aslam and S.Ghani “Fault Tolerance Analysis of Heterogeneous Wireless Sensor Network”. CCECE, IEEE International Conference, pages 175-179, 2011. [3] E.Bulut, Z.Wang and B.K.Szymanski. “The effect of neighbor graph connectivity on coverage redundancy in Wireless Sensor Network “. IEEE (ICC), pages 1-5, 2010. [4] M.Marta, Y.Yang and M. Cardei, “Energy-efficient composite event detection in Wireless Sensor Networks”. In Proceedings of the 4th International Conference on Wireless Algorithms , Systems and Application , WASA ‘09, Berlin, Heidelberg, Springer-Velag, Pages 94-103, 2009. [5] C.T.Vu and Y.Li. “Delaunay – Triangulation based complete coverage in Wireless Sensor Networks”. IEEE (PERCOM), pages 1-5, 2009. [6] J.Wang, S.Medidi and M.Medidi.”Energy-efficient K-coverage for Wireless Sensor Network with variable sensing radii”. IEEE (GLOBECOM ), pages 4518-4523, 2009. [7] D. Satyanarayana and S. V. Rao. “Constrained delaunay triangulation for ad-hoc networks”. J. Comp. Sys., Netw., and Comm., January, 2008. [8] D. Wang, B.Xie, and D.P. Agrawal. “Coverage and lifetime optimization of wireless sensor networks with gaussian distribution”. IEEE Transactions on Mobile Computing, pages 1444-1458, December, 2008. [9] J. Wang and S. Medidi. “Mesh-based coverage for wireless sensor networks”. IEEE GLOBECOM, pages 1-5, 2008. 41
- 42. References Cont. [10] Jiong Wang and Sirisha Medidi. “Topology control for reliable sensor-to-sink data transport in sensor networks”. In ICC, pages 3215-3219. IEEE, 2008. [11] Mohamed Hefeeda. “Randomized k-coverage algorithms for dense sensor networks.” In Proceedings of INFOCOM Minisymposium, pages 2376-2380, 2007. [12] Md. M.O.Rashid, M. M. Alam, Md. A. Razzaque, and C. S. Hong. “Reliable event detection and congestion avoidance in wireless sensor networks.” In Ronald H. Perrott, Barbara M. Chapman, Jaspal Subhlok, Rodrigo Fernandes de Mello, and Laurence Tianruo Yang, editors, HPCC, volume 4782 of Lecture Notes in Computer Science, pages 521-532. Springer, 2007. [13] J.Wang and S. Medidi. “Energy ecient coverage with variable sensing radii in wireless sensor networks.” In Proceedings of the Third IEEE International Conference on Wireless and Mobile Computing, Networking and Communications, WIMOB '07, pages 61-69, 2007. [14]C.H.Wu, K.C. Lee, and Y.C.Chung. “A delaunay triangulation based method for wireless sensor network deployment.” Comput. Commun., 2744-2752,October 2007. [15] Y. Zhou and M. Medidi. “Energy-ecient contention-resilient medium access for wireless sensor networks.” IEEE (ICC), pages 3178-3183, 2007. [16] C. F .Hsin, and M. Liu. “Randomly duty-cycled wireless sensor networks: Dynamics of coverage.” IEEE Transactions on Wireless Communications, 5,3182-3192, 2006. [17] K. S.T. Wu and H. C. Jiau. “A two-way coverage mechanism for wireless sensor networks.” In in Personal, Indoor and Mobile Radio Communications, IEEE 17th International Symposium on, pages 1-5, 2006. 42
- 43. References Cont. [18] S. Megerian, F. Koushanfar, M. Potkonjak, M. B. Srivastava. “Worst and best-case coverage in sensor networks.” IEEE Transaction on Mobile Computing, pages 84-92, 2005. [19] G. Xing, X. Wang, Y. Zhang, C. Lu, R. Pless, and C. Gill. “Integrated Coverage and Connectivity Configuration for in Sensor Networks.” ACM Trans. Sen. Netw., pages36–72, 2005. [20] O. B. Akan, Akyildiz and F. Ian “Event-to-sink reliable transport in wireless sensor Networks.” IEEE/ACM Trans. Netw., pages 1003-1016, October 2005. [21] Mihaela Cardei and D.Z.Du. “Improving wireless sensor network lifetime through power aware organization.” ACM Wireless Networks, pages 333-340, 2005. [22] Mihaela Cardei, My T. Thai, Yingshu Li, and Weili Wu. “Energy-ecient target coverage in wireless sensor networks.” In in IEEE Infocom, pages 1976-1984, 2005. [23] H.Zhang and J. C.Hou. “Maintaining sensing coverage and connectivity in large sensor networks.” Ad Hoc & Sensor Wireless Networks, 1, 2005. [24] C. Wook and S. K. Das. “Trade-of between coverage and data reporting latency for energy conserving data gathering in wireless sensor networks.” In Mobile Adhoc and Sensor Systems, IEEE International Conference , pages 503-512, 2004. 43
- 44. References Cont. [25] Z. Zhou, S. Das and H. Gupta. “Connected k-coverage problem in sensor networks”. In Proceedings of the International Conference on Computer Communications and Networks, pages 373-378, 2004. [26] Z. Zhou, S. Das and H. Gupta. “Variable radii connected sensor cover in sensor networks”. In Proc. of the IEEE International Conference on Sensor and Ad Hoc Communications and Networks, 2004. [27] A. Cerpa and D. Estrin. “Ascent: Adaptive self-conguring sensor networks topologies”. IEEE Transactions on Mobile Computing, pages 272-285, July 2004. [28] S. Pattem, S.Poduri and B. Krishnamachari. “Energy-quality tradeos for target tracking in wireless sensor networks”. In Proceedings of the 2nd international conference on Information processing in sensor networks, IPSN'03, Berlin, Heidelberg, Springer-Verlag, pages 32-46, 2003. [29] G. Wang, G. Cao and T. LaPorta. “A bidding protocol for deploying mobile sensors”, 2003. [30] X.Y.Li, P.J.Wan, and O.Frieder. “Coverage in wireless ad-hoc sensor networks. IEEE Transactions on Computers . » pages 753-763, 2003. [31] S. Adlakha and M. Srivastava. “Critical density thresholds for coverage in wireless sensornetworks.” IEEE Wireless Commun. Networking, pages 16-20, 2003. 44
- 45. References Cont. [32] H. Gupta, S. R. Das and Q. Gu. “Connected sensor cover: self-organization of sensor networks for efficient query execution”. pages 189-200, 2003. [33] C. Huang and Y.C. Tseng. “The coverage problem in a wireless sensor network”. In Proceedings of the 2nd ACM international conference on Wireless Sensor Networks and Applications, WSNA '03, pages 115-121, 2003. [34] K. Kar and S. Banerjee. “Node Placement for Connected Coverage in Sensor Networks.” March 2003. [35] Xiang-Yang Li, Gruia Calinescu, Peng-Jun Wan, and Yu Wang. “Localized delaunay triangulation with application in ad hoc wireless networks”. IEEE Transaction on Parallel and Distributed System, 14(9):2003, 2003. [36] B. Liu and D. Towsley. “On the coverage and detectability of wireless sensor networks.” ad hoc Wireless Networks, 3, 2003. [37] S. Pattem, S. Poduri and B. Krishnamachari. “Energy-quality tradeos for target tracking in wireless sensor networks”. In Proceedings of the 2nd international conference on Information processing in sensor networks, IPSN'03, pages 32-046, Springer-Verlag, 2003. [38] I. F. Akyildiz, W. Su, Y. Sankarasubramaniam, and E. Cayirci. Wireless sensor networks: a survey. Computer Networks, pages 393-422, 2002. 45
- 46. References Cont. [39] K. Chakrabarty, S. S. Iyengar, H. Qi and E.Cho. “Grid coverage for surveillance and target location in distributed sensor networks.”IEEE Transactions on Computers, pages 1448-1453, 2002. [40] A. Howard, M. J. Mataric and G. S. Sukhatme. “Mobile sensor network deployment using potential fields: A distributed, scalable solution to the area coverage problem”. pages 299-308, 2002. [41] M.X. Cheng. M. Min X.Jia D. Li D.z Du M. Cardie, D. MacCallum. ‘’Wireless sensor networks with energy ecient organization.” Jouranal of International Networks, pages 213-229, 2002. [42] D. Tian and N. D. Georganas. “A Coverage-Preserving Node Scheduling Scheme for LargeWireless Sensor Networks”. ACM, pages 32–41, 2002. [43] S. Meguerdichian, F. Koushanfar, M. Potkonjak and M. B. Srivastava. “Coverage problems in wireless Ad-hoc sensor networks.” In in IEEE INFOCOM, pages 1380-1387, 2001. [44] S. Meguerdichian, F. Koushanfar, G. Qu and M. Potkonjak.”Exposure in wireless ad-hoc sensor networks,” 2001. [45] S. Slijepcevic and M. Potkonjak. “Power ecient organization of wireless sensor networks.” pages 472-476, 2001. [46] Jie Wu and Hailan Li. “On calculating connected dominating set for efficient routing in ad hoc wireless networks.” In Proceedings of the 3rd international workshop on Discrete algorithms and methods for mobile computing and communications, DIALM '99, pages 7-14, ACM,1999. [47] F. Aurenhammer. “Voronoi diagrams a survey of a fundamental geometric data structure.”ACM Computing Surveys, pages 345-405, 1991. [48] Teerawat Issariyakul and Ekram Hossain. “Introduction to Network Simulator NS2.”,Springer Publishing Company, Incorporated, 1 edition, 2008. 46
- 47. References Cont. [49] S. Lu F. Ye, G. Zhong and L. Zhang. “Energy ecient robust sensing coverage in large sensor networks”. In Proceedings of the 1st ACM international workshop on Wireless sensor networks and applications. technical report,UCLA. [50] M.Cardei and J.Wu, “Coverage in wireless sensor networks.” In M.Ilyas and I.Mahgoub, editors, Handbook of Sensor Networks: Compact Wireless and Wired Sensing Systems, pages 361-372. CRC PRESS LLC. [51] L. P. Chew ,“Constrained delaunay triangulations.”, 1987. [52] http://en.wikipedia.org/wiki/MATLAB. [53] http://www.isi.edu/nsnam/ns/. [54] Esq David J. Stein,“Wireless Sensor Network Simulator.”, 2006. 47
- 48. THANK YOU 48














![Proposed Work (Contd.)
Distributed Greedy Algo.
• Procedure 2-COVERAGE (S [ ])
• S [ ] is the set of sensor nodes deployed
• R is the region to be covered
• snode ← S[x] : x is randomly selected node
• while (R is not Covered) do
• dbl[i]← snode
• snode← broadcast()
• snode ←recv()
• snode ←maxBenifit()
• i ←i+1
• end while
• end procedure
14](https://image.slidesharecdn.com/faulttoleranceinwirelesssensornetworks-121122234855-phpapp02/85/Fault-tolerance-in-wireless-sensor-networks-by-Constrained-Delaunay-Triangulation-Coverage-Strategy-14-320.jpg)


![Proposed Work (Contd.)
Selection of Backup Nodes Algo.
• Procedure: BK SELECT (dbl [ ])
•
• dbl [ ] is the set of sensor nodes providing 2Coverage
•
• Neighbors [ ] is the set of Triangle Neighbors of each node
•
• i ←0
• while i ≠ dbl.end() do
•
• if dbl[i].area() ≡ Neighbors [ ].area() then
• backup[ j] ← dbl[i]
• PotPri[] ←nearest(Neighbors[],backup[ j])
• PotPri[] ←median(Neighbors[],backup[ j])
• i ← i+1
• end if
• end while
• while i ≠ PotPri.end() do
• if PotPri.area() ≡ Neighbors [ ].area() then
• backup[] ←PotPri[i]
• erase(PotPri[i])
• end if
• end while
• end procedure
17](https://image.slidesharecdn.com/faulttoleranceinwirelesssensornetworks-121122234855-phpapp02/85/Fault-tolerance-in-wireless-sensor-networks-by-Constrained-Delaunay-Triangulation-Coverage-Strategy-17-320.jpg)





















![References
[1] P.Kumari and Y.Singh. “Delaunay Triangulation Coverage Strategy for Wireless Sensor Networks”. IEEE
(ICCCI), pages 1-5, 2012.
[2] R.H.Abedi, N.Aslam and S.Ghani “Fault Tolerance Analysis of Heterogeneous Wireless Sensor
Network”. CCECE, IEEE International Conference, pages 175-179, 2011.
[3] E.Bulut, Z.Wang and B.K.Szymanski. “The effect of neighbor graph connectivity on coverage
redundancy in Wireless Sensor Network “. IEEE (ICC), pages 1-5, 2010.
[4] M.Marta, Y.Yang and M. Cardei, “Energy-efficient composite event detection in Wireless Sensor
Networks”. In Proceedings of the 4th International Conference on Wireless Algorithms , Systems and
Application , WASA ‘09, Berlin, Heidelberg, Springer-Velag, Pages 94-103, 2009.
[5] C.T.Vu and Y.Li. “Delaunay – Triangulation based complete coverage in Wireless Sensor Networks”.
IEEE (PERCOM), pages 1-5, 2009.
[6] J.Wang, S.Medidi and M.Medidi.”Energy-efficient K-coverage for Wireless Sensor Network with
variable sensing radii”. IEEE (GLOBECOM ), pages 4518-4523, 2009.
[7] D. Satyanarayana and S. V. Rao. “Constrained delaunay triangulation for ad-hoc networks”. J. Comp.
Sys., Netw., and Comm., January, 2008.
[8] D. Wang, B.Xie, and D.P. Agrawal. “Coverage and lifetime optimization of wireless sensor networks
with gaussian distribution”. IEEE Transactions on Mobile Computing, pages 1444-1458, December,
2008.
[9] J. Wang and S. Medidi. “Mesh-based coverage for wireless sensor networks”. IEEE GLOBECOM, pages
1-5, 2008.
41](https://image.slidesharecdn.com/faulttoleranceinwirelesssensornetworks-121122234855-phpapp02/85/Fault-tolerance-in-wireless-sensor-networks-by-Constrained-Delaunay-Triangulation-Coverage-Strategy-41-320.jpg)
![References Cont.
[10] Jiong Wang and Sirisha Medidi. “Topology control for reliable sensor-to-sink data transport in
sensor networks”. In ICC, pages 3215-3219. IEEE, 2008.
[11] Mohamed Hefeeda. “Randomized k-coverage algorithms for dense sensor networks.” In
Proceedings of INFOCOM Minisymposium, pages 2376-2380, 2007.
[12] Md. M.O.Rashid, M. M. Alam, Md. A. Razzaque, and C. S. Hong. “Reliable event detection and
congestion avoidance in wireless sensor networks.” In Ronald H. Perrott, Barbara M. Chapman,
Jaspal Subhlok, Rodrigo Fernandes de Mello, and Laurence Tianruo Yang, editors, HPCC, volume
4782 of Lecture Notes in Computer Science, pages 521-532. Springer, 2007.
[13] J.Wang and S. Medidi. “Energy ecient coverage with variable sensing radii in wireless sensor
networks.” In Proceedings of the Third IEEE International Conference on Wireless and Mobile
Computing, Networking and Communications, WIMOB '07, pages 61-69, 2007.
[14]C.H.Wu, K.C. Lee, and Y.C.Chung. “A delaunay triangulation based method for wireless sensor
network deployment.” Comput. Commun., 2744-2752,October 2007.
[15] Y. Zhou and M. Medidi. “Energy-ecient contention-resilient medium access for wireless sensor
networks.” IEEE (ICC), pages 3178-3183, 2007.
[16] C. F .Hsin, and M. Liu. “Randomly duty-cycled wireless sensor networks: Dynamics of coverage.”
IEEE Transactions on Wireless Communications, 5,3182-3192, 2006.
[17] K. S.T. Wu and H. C. Jiau. “A two-way coverage mechanism for wireless sensor networks.” In in
Personal, Indoor and Mobile Radio Communications, IEEE 17th International Symposium on, pages
1-5, 2006.
42](https://image.slidesharecdn.com/faulttoleranceinwirelesssensornetworks-121122234855-phpapp02/85/Fault-tolerance-in-wireless-sensor-networks-by-Constrained-Delaunay-Triangulation-Coverage-Strategy-42-320.jpg)
![References Cont.
[18] S. Megerian, F. Koushanfar, M. Potkonjak, M. B. Srivastava. “Worst and best-case coverage in sensor
networks.” IEEE Transaction on Mobile Computing, pages 84-92, 2005.
[19] G. Xing, X. Wang, Y. Zhang, C. Lu, R. Pless, and C. Gill. “Integrated Coverage and Connectivity
Configuration for in Sensor Networks.” ACM Trans. Sen. Netw., pages36–72, 2005.
[20] O. B. Akan, Akyildiz and F. Ian “Event-to-sink reliable transport in wireless sensor Networks.”
IEEE/ACM Trans. Netw., pages 1003-1016, October 2005.
[21] Mihaela Cardei and D.Z.Du. “Improving wireless sensor network lifetime through power aware
organization.” ACM Wireless Networks, pages 333-340, 2005.
[22] Mihaela Cardei, My T. Thai, Yingshu Li, and Weili Wu. “Energy-ecient target coverage in wireless
sensor networks.” In in IEEE Infocom, pages 1976-1984, 2005.
[23] H.Zhang and J. C.Hou. “Maintaining sensing coverage and connectivity in large sensor networks.”
Ad Hoc & Sensor Wireless Networks, 1, 2005.
[24] C. Wook and S. K. Das. “Trade-of between coverage and data reporting latency for energy
conserving data gathering in wireless sensor networks.” In Mobile Adhoc and Sensor Systems, IEEE
International Conference , pages 503-512, 2004.
43](https://image.slidesharecdn.com/faulttoleranceinwirelesssensornetworks-121122234855-phpapp02/85/Fault-tolerance-in-wireless-sensor-networks-by-Constrained-Delaunay-Triangulation-Coverage-Strategy-43-320.jpg)
![References Cont.
[25] Z. Zhou, S. Das and H. Gupta. “Connected k-coverage problem in sensor networks”. In Proceedings
of the International Conference on Computer Communications and Networks, pages 373-378,
2004.
[26] Z. Zhou, S. Das and H. Gupta. “Variable radii connected sensor cover in sensor networks”. In Proc.
of the IEEE International Conference on Sensor and Ad Hoc Communications and Networks, 2004.
[27] A. Cerpa and D. Estrin. “Ascent: Adaptive self-conguring sensor networks topologies”. IEEE
Transactions on Mobile Computing, pages 272-285, July 2004.
[28] S. Pattem, S.Poduri and B. Krishnamachari. “Energy-quality tradeos for target tracking in wireless
sensor networks”. In Proceedings of the 2nd international conference on Information processing in
sensor networks, IPSN'03, Berlin, Heidelberg, Springer-Verlag, pages 32-46, 2003.
[29] G. Wang, G. Cao and T. LaPorta. “A bidding protocol for deploying mobile sensors”, 2003.
[30] X.Y.Li, P.J.Wan, and O.Frieder. “Coverage in wireless ad-hoc sensor networks. IEEE Transactions on
Computers . » pages 753-763, 2003.
[31] S. Adlakha and M. Srivastava. “Critical density thresholds for coverage in wireless sensornetworks.”
IEEE Wireless Commun. Networking, pages 16-20, 2003.
44](https://image.slidesharecdn.com/faulttoleranceinwirelesssensornetworks-121122234855-phpapp02/85/Fault-tolerance-in-wireless-sensor-networks-by-Constrained-Delaunay-Triangulation-Coverage-Strategy-44-320.jpg)
![References Cont.
[32] H. Gupta, S. R. Das and Q. Gu. “Connected sensor cover: self-organization of sensor networks for
efficient query execution”. pages 189-200, 2003.
[33] C. Huang and Y.C. Tseng. “The coverage problem in a wireless sensor network”. In Proceedings of
the 2nd ACM international conference on Wireless Sensor Networks and Applications, WSNA '03,
pages 115-121, 2003.
[34] K. Kar and S. Banerjee. “Node Placement for Connected Coverage in Sensor Networks.” March
2003.
[35] Xiang-Yang Li, Gruia Calinescu, Peng-Jun Wan, and Yu Wang. “Localized delaunay triangulation with
application in ad hoc wireless networks”. IEEE Transaction on Parallel and Distributed System,
14(9):2003, 2003.
[36] B. Liu and D. Towsley. “On the coverage and detectability of wireless sensor networks.” ad hoc
Wireless Networks, 3, 2003.
[37] S. Pattem, S. Poduri and B. Krishnamachari. “Energy-quality tradeos for target tracking in wireless
sensor networks”. In Proceedings of the 2nd international conference on Information processing in
sensor networks, IPSN'03, pages 32-046, Springer-Verlag, 2003.
[38] I. F. Akyildiz, W. Su, Y. Sankarasubramaniam, and E. Cayirci. Wireless sensor networks: a survey.
Computer Networks, pages 393-422, 2002.
45](https://image.slidesharecdn.com/faulttoleranceinwirelesssensornetworks-121122234855-phpapp02/85/Fault-tolerance-in-wireless-sensor-networks-by-Constrained-Delaunay-Triangulation-Coverage-Strategy-45-320.jpg)
![References Cont.
[39] K. Chakrabarty, S. S. Iyengar, H. Qi and E.Cho. “Grid coverage for surveillance and target location in
distributed sensor networks.”IEEE Transactions on Computers, pages 1448-1453, 2002.
[40] A. Howard, M. J. Mataric and G. S. Sukhatme. “Mobile sensor network deployment using potential
fields: A distributed, scalable solution to the area coverage problem”. pages 299-308, 2002.
[41] M.X. Cheng. M. Min X.Jia D. Li D.z Du M. Cardie, D. MacCallum. ‘’Wireless sensor networks with
energy ecient organization.” Jouranal of International Networks, pages 213-229, 2002.
[42] D. Tian and N. D. Georganas. “A Coverage-Preserving Node Scheduling Scheme for LargeWireless
Sensor Networks”. ACM, pages 32–41, 2002.
[43] S. Meguerdichian, F. Koushanfar, M. Potkonjak and M. B. Srivastava. “Coverage problems in wireless
Ad-hoc sensor networks.” In in IEEE INFOCOM, pages 1380-1387, 2001.
[44] S. Meguerdichian, F. Koushanfar, G. Qu and M. Potkonjak.”Exposure in wireless ad-hoc sensor
networks,” 2001.
[45] S. Slijepcevic and M. Potkonjak. “Power ecient organization of wireless sensor networks.” pages
472-476, 2001.
[46] Jie Wu and Hailan Li. “On calculating connected dominating set for efficient routing in ad hoc
wireless networks.” In Proceedings of the 3rd international workshop on Discrete algorithms and
methods for mobile computing and communications, DIALM '99, pages 7-14, ACM,1999.
[47] F. Aurenhammer. “Voronoi diagrams a survey of a fundamental geometric data structure.”ACM
Computing Surveys, pages 345-405, 1991.
[48] Teerawat Issariyakul and Ekram Hossain. “Introduction to Network Simulator NS2.”,Springer
Publishing Company, Incorporated, 1 edition, 2008.
46](https://image.slidesharecdn.com/faulttoleranceinwirelesssensornetworks-121122234855-phpapp02/85/Fault-tolerance-in-wireless-sensor-networks-by-Constrained-Delaunay-Triangulation-Coverage-Strategy-46-320.jpg)
![References Cont.
[49] S. Lu F. Ye, G. Zhong and L. Zhang. “Energy ecient robust sensing coverage in large sensor
networks”. In Proceedings of the 1st ACM international workshop on Wireless sensor networks and
applications. technical report,UCLA.
[50] M.Cardei and J.Wu, “Coverage in wireless sensor networks.” In M.Ilyas and I.Mahgoub, editors,
Handbook of Sensor Networks: Compact Wireless and Wired Sensing Systems, pages 361-372. CRC
PRESS LLC.
[51] L. P. Chew ,“Constrained delaunay triangulations.”, 1987.
[52] http://en.wikipedia.org/wiki/MATLAB.
[53] http://www.isi.edu/nsnam/ns/.
[54] Esq David J. Stein,“Wireless Sensor Network Simulator.”, 2006.
47](https://image.slidesharecdn.com/faulttoleranceinwirelesssensornetworks-121122234855-phpapp02/85/Fault-tolerance-in-wireless-sensor-networks-by-Constrained-Delaunay-Triangulation-Coverage-Strategy-47-320.jpg)
