Hacking WebApps for fun and profit : how to approach a target?
- 1. Hacking WebApps for fun and profit : how to approach a target? Yassine ABOUKIR
- 2. What not to expect? • This session is not about penetration testing. • This session will not cover all web vulnerabilities. • This session will not cover basic technical knowledge.
- 3. What to expect? • An introduction to bug bounty industry • How to start your journey in bug hunting. • How to conduct web vulnerabilities assessment (Black- box approach) • Introduction to some essential hacking tools. • How to bypass a few common vulnerabilities protection. • How to write a kick-ass security report.
- 4. Presentation • Security Analyst at HackerOne Inc. • Author at InfoSec Magazine. • Occasional bug bounty hunter (Listed in Microsoft, Yahoo, Facebook, Google, Twitter etc Hall of fame) – Ranked 11th on HackerOne. • Student at ISCAE (MSc in Corporate Finance) - Casablanca • Double Degree at IESEG School Of Management (MSc in Management of Information Systems) - Lille, France
- 5. Quick Questions • How many of you have basic technical background (HTTP, TCP/IP, Web technologies etc.)? • How many of you know about OWASP TOP10? • How many of you participated in a Bug Bounty Program?
- 6. Bug Bounty Industry Facebook offers a minimum of $500 US and paid out over $4.3 million to researchers around the globe. Microsoft offers a minimum of $500 US and paid out over $500K
- 7. Perks of being a bug bounty hunter Hacking legally. Have fun. Earn money. Sharpen your skills. Build your CV. Expand your network. Make the world more secure.
- 9. Vulnerabilities Assessment VS Pentesting • Vulnerability assessment is more about identifying and prioritizing security vulnerabilities. • Penetration testing (Pentesting) is designed to achieve a specific, attacker-simulated goal (Access private network, database etc.)
- 11. Planning It is extremely important to read the program brief thouroughly before starting. • Domains and IPs In-Scope. • In-Scope Vulnerabilities. • Out Of Scope Vulnerabilities. • Other Useful Information. Eg: Twitter bug bounty program (https://hackerone.com/twitter)
- 12. Burp Suite is an integrated platform for performing security testing of web applications. Its various tools work seamlessly together to support the entire. Functionalities: • Web Proxy • Web Crawler • Reapeter • Intruder • Web Scanner • Comparer • Extender
- 13. Reconnaissance • Understand web application logic. • Map the used stack (Tool: Wappalyzer Addon) • Spidering the application (Tool: Burpsuite) • Check Robots.txt file. • Google Hacking. • Bruteforcing Directories (Tool: DirBuster)
- 14. DNS Recon Check the server’s DNS records using DNSRecon. Interesting things to look for : • DNS Zone transfer (Nslookup –query=axfr example.com) • SPF records (Spoofing Demo : https://emkei.cz/) • MX records (Uber $10,000 US bug to Uranium238) • DNSSEC configuration • Etc.
- 15. Port Scanning Use Nmap to look for open ports in a web server and corresponding services. • 25 for SMTP • 22 for SSH • 23 Telnet • 21 for FTP • 115 for SFTP • 110 for POPs • 443 HTTPS • 80 HTTP Sudo apt-get install nmap
- 16. SSL/TLS Web applications use TLS to secure all communications between their servers and web browsers. Heartbleed Drown attack Poodle attack Use of weak ciphers (RC4) Expired TLS certificate Insecure Client-Initiated Renegotiation (Should be disabled) Etc.
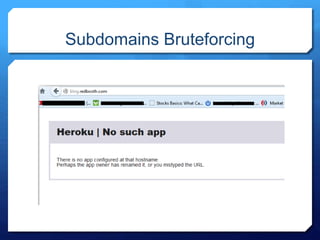
- 18. Subdomains Bruteforcing Check for subdomains with private instances. stage.example.com, dev.example.Com, testing.example.com, vpn.example.com Check for potential subdomains takeover. Support.example.com, help.example.com, forums.example.com Tool : Sublist3r
- 20. Subdomains Bruteforcing W0rm$ host blog.redbooth.com Non-authoritative answer: og.redbooth.com is an alias for teambox-redirect-to-new-blog.herokuapp.com.
- 22. Github Leakage Hard coding credentials and pushing the code to GitHub is a common mistake. Look for : AWS Keys (AWS_SECRET_ACCESS_KEY) Passwords Slack tokens (xoxs-token) Private API Keys SSH Keys (id_rsa, ---BEGIN RSA PRIVATE KEY---) Etc.
- 24. Cross-Site Scripting (XSS) XSS attacks occur when an attacker uses a web application to send malicious code, generally in the form of a browser side script, to a different end user. Types: Reflected XSS Stored XSS DOM-Based XSS Cookie-based XSS Flash-based XSS
- 25. Cross-Site Scripting (XSS) Exploitation : • Execution of malicious Javascript • Execute Client-Side Exploits • Bypass CSRF protection • Temporary defacements and other nuisances
- 26. Cross-Site Scripting (XSS) • Reflected XSS Demonstration. • Stored XSS Demonstration. • Exploitation of Stored XSS : Hijacking Session Cookie.
- 27. Cross-Site Scripting (XSS) Testing for XSS: • '';!--"<img>=&{()} • <img/src=x onerror=alert(0)> • <svg/onload=alert(0)> • <SCRIPT/SRC=//⒕₨?
- 28. Cross-Site Scripting (XSS) Techniques to bypassing XSS filters: • Use polyglot payload : <input type="text" value=" jaVasCript:/*-/*`/*`/*'/*"/**/(/* */oNcliCk=alert() )//%0D%0A%0d%0a//</stYle/</titLe/</teXtarEa/</scRipt/-- !>x3csVg/<sVg/oNloAd=alert()//>x3e "></input> • XSS in Link inputs: javascript://www.google.com/%0Aalert(1337);//http:// • Bypasses list : https://www.owasp.org/index.php/XSS_Filter_Evasion_Cheat_Sheet • Polyglot payloads : https://github.com/0xsobky/HackVault/wiki/Unleashing-an-Ultimate-XSS-Polyglot
- 33. Cross-Site Request Forgery Protection bypass techniques : • Remove token parameter. • Leave token value blank. • Alter token value but keep same length. • Try another user token. • Check if token is regenerated upon logout/login. • Analyze token complexity.
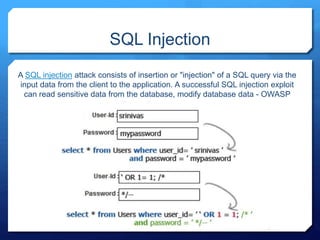
- 34. Clickjacking Attack Clickjacking, also known as a "UI redress attack", is when an attacker uses multiple transparent or opaque layers to trick a user into clicking on a button or link on another page when they were intending to click on the the top level page.
- 35. Clickjacking Attack X-Frame-Options: DENY X-Frame-Options: SAMEORIGIN X-Frame-Options: ALLOW-FROM https://example.com/
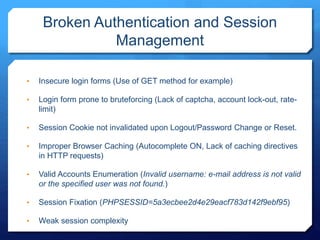
- 37. SQL Injection A SQL injection attack consists of insertion or "injection" of a SQL query via the input data from the client to the application. A successful SQL injection exploit can read sensitive data from the database, modify database data - OWASP
- 38. SQL Injection Types of SQLi Error-based SQLi Blind SQLi Boolean-based (content-based) Blind SQLi Time-based SQLi
- 39. SQL Injection Damn Vulnerable Web Application www.dvwa.co.uk Demonstration
- 40. -u : Specify the vulnerable target -d : Vulnerable parameter (Injection point) --Cookie: Cookies --data : Parameters in case of a POST request --dbs : List all databases --tables : List all tables or tables of a specific database --columns : List all columns, or columns of a specific table in a DB. --dump : Extract information from the database.
- 41. SQL Injection Testing for SQLi : Single Quote : ‘ Boolean expression : 1' or '1' = '1 ' or 1=1 /* Time expressions : 1' AND (SELECT * FROM (SELECT(SLEEP(5)))x) AND '1'='1 ‘ and sleep(10)/* BENCHMARK(10000000,SHA1(1)) ';waitfor delay '0:0:10'--
- 42. Insecure Direct Object References Insecure Direct Object References occur when an application provides direct access to objects based on user-supplied input. As a result of this vulnerability attackers can bypass authorization and access resources in the system directly, for example database records or files. (User A) https://www.mybank.com/balance.php?account_id=123 (User B) https://www.mybank.com/balance.php?account_id=124
- 43. Insecure Direct Object References POST Request: https://hackerone.com/reports/136114
- 44. Open Redirects Unvalidated redirects and forwards are possible when a web application accepts untrusted input that could cause the web application to redirect the request to a URL contained within untrusted input. https://mail.google.com/?redirect=http://mail.gooogle.com/
- 45. Open Redirects Bypass methods: • http://www.example.com/login?redirect=//evil.Com • http://www.example.com/login?redirect=evil.Com • http://www.example.com/[email protected] • http://www.example.com/login?redirect=//evil.Com • http://www.example.com/login?redirect=http://evil.com • http://www.example.com/login?redirect=http:google.com • http://www.example.com/login?redirect=http:///@evil.com//
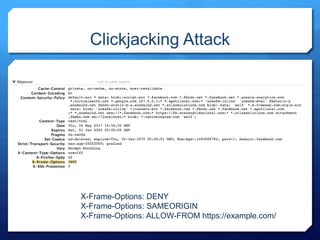
- 46. Broken Authentication and Session Management • Insecure login forms (Use of GET method for example) • Login form prone to bruteforcing (Lack of captcha, account lock-out, rate- limit) • Session Cookie not invalidated upon Logout/Password Change or Reset. • Improper Browser Caching (Autocomplete ON, Lack of caching directives in HTTP requests) • Valid Accounts Enumeration (Invalid username: e-mail address is not valid or the specified user was not found.) • Session Fixation (PHPSESSID=5a3ecbee2d4e29eacf783d142f9ebf95) • Weak session complexity
- 47. Report Redaction • Executive Summary • Vulnerability Description • Affected URL/Parameters • Risk assessment • Steps Of Reproduction • Proof Of Concept • Recommended fix • References
- 48. Resources Useful links: • http://hackerone.com/hacktivity • https://github.com/ngalongc/bug-bounty-reference/blob/master/README.md
- 49. Let’s stay in touch E-mail : [email protected] Twitter : @Yassineaboukir LinkedIn : /in/yaboukir Blog : http://www.yassineaboukir.com/blog/