Hardware hacking 101
- 1. HARDWARE HACKING 101 An introduction to hardware hacking and why it matters...
- 2. SPEAKER • BSc Software Engineering University of Brighton • MSc by Research in Computer Security and Forensics Univ of Bedfordshire • PhD Dropout • Enjoys breaking stuff • Founder @ptcoresec • Organizer of @Bsideslisbon with @morisson • Never had electronics lessons or any type of background • You should know me by now... It’s my 6th time speaking @confraria!
- 3. TOPICS
- 4. AGENDA • Hardware Hacking • What • Why • Bill of materials • Protocols • Hardware hackz • Demos
- 5. HARDWARE HACKING - WHAT Q:What is hardware hacking, and why should I care about it ? A:Your secure software is only as secure as the hardware it is running on... Imagine implementing all your crypto correctly but then a tiny itsy bitsy of a “problem” with your RNG.
- 6. HARDWARE HACKING - WHAT
- 7. HARDWARE HACKING - WHY • Electronic equipment is virtually everywhere we look. • How safe is this hardware? Should be important to know if it is safe, since we have a ton of things running on chips and using protocols that we take for granted as “secure”.... • Hardware hacking is still a taboo, people feel that its harder to get into it – It’s high school all over again “maths is hard, physics is hard...” • Old attacks work still work on hardware... • Lot’s of security by obscurity... “black box devices”
- 8. HARDWARE HACKING – WHY WHITEHAT VERSION • We see plenty of articles, most of them say “China hacked X, Y and Z” • Do we forget that there is also something that has the word “China” everywhere? The chips that run in pretty much all the hardware we use are mass built in China. “Made in china” • What if they decided to mass backdoor these chips? Or even better what if they decided to “selectively” backdoor and affect military “grade” chips only?
- 9. HARDWARE HACKING – WHY BLACKHAT VERSION • Stealing a service – Smartmeter hacking anyone? “Via verde” can also be funny one to look at – Oh, ISP Routers, are the lulz. • Cloning – Company X builds cool Whoopadywoo Gold edition gadget and company Z hires hardware reverse engineer to understand how it works. • Authentication – fake an authentication or bruteforcing it!
- 10. HARDWARE HACKING – CONCEPTS • You do need a bit of Physics
- 11. HARDWARE HACKING – CONCEPTS • Voltage - Simply put, voltage is used to provide power. In digital circuits it can be used to transmit data in binary form ON/OFF 1/0. Also in digital circuits it is usually found in form of 3.3V and 5V. Two types of voltage exist: AC and DC • AC (alternative current) – This is what you usually find on the wall. It’s produced in higher voltage at a power station and then reduced to be used at home by your equipment using a transformer for example. • DC (Direct current) – is what you find in batteries, essentially if a battery is 6V it will stay that way until it depletes.
- 12. HARDWARE HACKING – CONCEPTS • To measure voltage you can use a multimeter or an oscilloscope (we will look at these devices further down in this presentation). A few important points to remember about voltage: • You can only check voltage when your system is powered up. • Voltage must be read between two points (test point and ground point). • Voltage follows a direction – if you see negative values on the multimeter you’re probably putting the ground/black probe on the wrong point.
- 13. HARDWARE HACKING – CONCEPTS Resistance – a measurement that indicated the amount of current opposition created by a resistor. A resistor is usually represented by the symbol and it has two leads to which a resistor is connected to a circuit. Resistance is measured in Ohms and the symbol used is Ω (Omega)
- 14. HARDWARE HACKING BILL OF MATERIALS • Soldering iron • Desoldering Tool • Solder • Multimeter • Logic Analyzer • Microscope / Magnifier • Digital Circuit Design software • Wires – long, small, different sizes • Microcontroller reprogrammer • Prototyping microcontroller • Oscilloscope • Breadboards • Random electronic components • Hardware to break!
- 15. HARDWARE HACKING BILL OF MATERIALS Soldering iron Price: range 50€ - 5000€> Multiple types: Gas, Laser, Heat...
- 16. HARDWARE HACKING BILL OF MATERIALS Desoldering gun / pump Price range: 10€ - 500€> Multiple types: Pump, Gun
- 17. HARDWARE HACKING BILL OF MATERIALS Solder Price range: 2€ - 200€> Multiple types and sizes
- 18. HARDWARE HACKING BILL OF MATERIALS Multimeter Price range: 11€ - 9000€> Multiple types: Digital and Analog
- 19. HARDWARE HACKING BILL OF MATERIALS Multimeter A multimeter is a device that can be used to measure multiple things, the most basic multimeters are able to measure the following: • Voltage • Current • Resistance The accuracy of these devices usually depends a lot on the price as well.
- 20. HARDWARE HACKING BILL OF MATERIALS
- 21. HARDWARE HACKING BILL OF MATERIALS Putting the black probe (ground) on the negative side and the red probe on the positive, and then choosing DC Voltage 2V on the multimeter shows the following result
- 22. HARDWARE HACKING BILL OF MATERIALS The same thing can be done for resistors. If we grab a random resistor: And then we connect the probes. (In this case I used a bit of cable to connect them as they wouldn’t stick for the photo , also it doesn’t matter to what end you connect each probe. Unlike voltage, resistance isn’t directional.)
- 23. HARDWARE HACKING BILL OF MATERIALS Logic Analyzer Price range: irrelevant. What you want is this: The Salae Logic Analyzer - 140 € Used to understand which protocols are running and To debug different chips/protocols.
- 24. HARDWARE HACKING BILL OF MATERIALS Microscope or Magnifier Price range: 10€ - 5000€
- 25. HARDWARE HACKING BILL OF MATERIALS Digital circuit software Price range: 0 € - 5000 € http://fritzing.org/
- 26. HARDWARE HACKING BILL OF MATERIALS Wires Price range: 5€ - 400€ Made of multiple materials, different sizes, lenght etc...
- 27. HARDWARE HACKING BILL OF MATERIALS Microcontroller reprogrammer Price range: 20€ - 500€> Different protocols, capacity, speed, functionality... In my case I have a Bus Pirate “The Bus Pirate is an open source hacker multi-tool that talks to electronic stuff. It's got a bunch of features an intrepid hacker might need to prototype their next project.” http://dangerousprototypes.com/docs/Bus_Pirate
- 28. HARDWARE HACKING BILL OF MATERIALS • Bus Pirate • Talks multiple protocols • Built in Terminal • Can be controlled using python or c • Connects via USB • Protocols: 1-wire, UART, i2c, SPI, raw-2 wire, raw-3 wire, MIDI, PC Keyboard, JTAG
- 29. HARDWARE HACKING BILL OF MATERIALS • Bus Pirate
- 30. HARDWARE HACKING BILL OF MATERIALS Microcontroller reprogrammer Price range: 20€ - 500€> Different protocols, capacity, speed, functionality... In my case I also happen to have a GoodFET 31
- 31. HARDWARE HACKING BILL OF MATERIALS Prototyping microcontroller Price range: 20€ - xxxx€> Different protocols, capacity, speed, functionality... In my case I have multiple arduinos
- 32. HARDWARE HACKING BILL OF MATERIALS Prototyping microcontroller Price range: 38€ Different protocols, capacity, speed, functionality... Another great choice are the new beagle Boards. For the price they look even better then the arduinos.
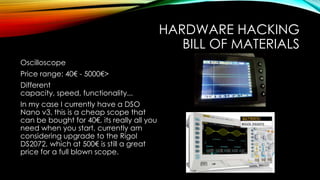
- 33. HARDWARE HACKING BILL OF MATERIALS Oscilloscope Price range: 40€ - 5000€> Different capacity, speed, functionality... In my case I currently have a DSO Nano v3, this is a cheap scope that can be bought for 40€, its really all you need when you start, currently am considering upgrade to the Rigol DS2072, which at 500€ is still a great price for a full blown scope.
- 34. HARDWARE HACKING BILL OF MATERIALS Breadboards Price range: 5€ - 50€ Different sizes.
- 35. HARDWARE HACKING BILL OF MATERIALS Random electronic components • Resistors • Batteries • Capacitors • Sensors • Diodes • Transistors
- 36. HARDWARE HACKING BILL OF MATERIALS Hardware to break! mobile Nook Tamagotchi IM-ME Routers
- 37. HARDWARE HACKING BILL OF MATERIALS Hardware to break! femtocell Printer Random Hardware
- 38. HARDWARE HACKING BILL OF MATERIALS Hardware to break! Medical devices
- 39. HARDWARE HACKING PROTOCOLS SPI - Serial Peripheral Interface – operates in full duplex, is a synchronous serial data link, the devices communicate between them in a master/slave model. For SPI you will see a minimum of 3 pins. I2C – Inter Integrated Circuit – Uses 2 bidirectional lines SDA (Serial Data Line ) and SDC (Serial Data Clock). It operates in half duplex and since it uses 2 lines you will see 2 pins on devices.
- 40. HARDWARE HACKING PROTOCOLS • JTAG - Joint Test Action Group – usually used to debug devices. There are two possible pin layouts for JTAG: • 4 pins • TDI (Test Data In) • TDO (Test Data Out) • TCK (Test Clock) • TMS (Test Mode Select) • 5 pins • TDI (Test Data In) • TDO (Test Data Out) • TCK (Test Clock) • TMS (Test Mode Select) • TRST (Test Reset) optional.
- 41. HARDWARE HACKING PROCESS • The process to start some hardware hacking should be the following: 1. Crack open the surrouding case to access PCB – Watch out for safety measures – (secure seals, protective plastics) 2. Identify pins and components get access to datasheet 3. Connect and acquire useful data 4. Reverse 5. ??? 6. Profit OUR FOCUS
- 42. HARDWARE HACKING PROCESS – PIN IDENTIFICATION • We know the different protocols, we know the number of pins, but how do we find what each pin is? 1. Use multimeter – Measure voltage on all different pins 1. If pin has 3.3 volts or less its most likely used for data 2. If pin has >5v power source! 3. 0 volts = unused pin or ground 2. Connect a scope, identify Square waves (these are digital signals) 3. Connect logic analyzer to those pins, separate clock from data pins 4. Analyze data and being reversing... Source:http://www.turbosq uid.com/FullPreview/Index.c fm/ID/428945
- 43. HARDWARE HACKING PROCESS – COMPONENT IDENTIFICATION • What if I don’t want to poke all the pins and connections? • You can try to identify the different components and access their data sheets, where u can get all the technical information you might need • Vendor and part numbers are usually printed on the components • Look for manufacturers logo • Alphanumeric codes to identify
- 44. HARDWARE HACKING PROCESS – COMPONENT IDENTIFICATION • http://www.chipdocs.com/logos/logotypes.html
- 45. HARDWARE HACKING PROCESS – DATASHEETS • Data sheets are documents that contain technical information about the component • Some are free, others are paid • http://octopart.com/ • http://www.findchips.com/ • http://datasheetlocator.com/ • http://www.eem.com/ • http://www.ihs.com/products/product-design-sourcing/component-supplier- data/caps-expert.aspx
- 46. HARDWARE HACKING PROCESS – DATASHEETS
- 47. HARDWARE HACKING HACKZ • Real man wear pink pagers!
- 48. HARDWARE HACKING HACKZ • Wiring IM-ME for custom firmware installation! 1 2 3 3 4 1 - !RST - Reset 2 – DD – Debug Data 3 – DC – Debug Clock 4 - +2,5V - Power 5 – Gnd - Ground More information: http://travisgoodspeed.blogspot.pt/2010/03/im-me-goodfet-wiring-tutorial.html
- 49. HARDWARE HACKING HACKZ • TV tuner + all mighty clock!
- 50. HARDWARE HACKING HACKZ • TV tuner + all mighty clock! Results: http://adamsblog.aperturelabs.com/2013/03/you-can-ring-my-bell-adventures-in-sub.html
- 51. HARDWARE HACKING HACKZ • Linksys WMB54G and others! Connector J9 Pin 1 – TX – Transmission Pin 2 – RX – Receiver Pin 8 – GND - Ground RAMDISK: ext2 filesystem found at block 0 RAMDISK: Loading 4096 blocks [1 disk] into ram disk... done. Freeing initrd memory: 4096k freed VFS: Mounted root (ext2 filesystem). Freeing unused kernel memory: 60k freed mount /proc file system ok! serial console detected. Disabling virtual terminals. init started: BusyBox v1.00-pre8 (2008.01.17-05:54+0000) multi-call binary BusyBox v1.00-pre8 (2008.01.17-05:54+0000) Built-in shell (ash) Enter 'help' for a list of built-in commands. # http://www.devttys0.com/2012/07/hacking-the-linksys-wmb54g/
- 52. HARDWARE HACKING HACKZ • Hardware Random Number Generator • Two types of RNG: True and Pseudo • Pseudo – Created by algorithm • Problem – if someone knows your algorithm in theory can predict your random numbers • True – generates sequences that are impossible to predict. Use random physical events as sources of randomness. Component Quantity Arduino 1 2N3904 Transistor 3 4.7k Resistor 2 10k Resistor 1 1.5M Resistor 1 0.1µf Capacitor 1 10µf Capacitor 1 Breadboard 1 12v DC Adapter 1
- 54. HARDWARE HACKING HACKZ 1. The two transistors create avalanche noise 2. Third transistor amplifies the noise 3. Noise is sent across voltage dividers to the arduino
- 55. HARDWARE HACKING HACKZ 1 0 1 0 0 1 1 0 Arduino applies Von Neumann filtering to remove possible bias Provides network service that feeds random numbers
- 56. HARDWARE HACKING DEMOS • Logic analyzer and SMC WAAG EU
- 57. HARDWARE HACKING DEMOS • 2x Arduinos bomb Man in the middle Timer Activator
- 58. HARDWARE HACKING COMPLICATIONS • Hard to access pins for probing! • Solution!
- 59. HARDWARE HACKING COMPLICATIONS • Epoxy! • Heat gun • Dremel tool and sharp wooden stick • Best solution: Fuming Nitric Acid • Warm the nitric acid to 60 degree celsium • Putt small drops on the epoxy it will come right off
- 60. HARDWARE HACKING CONCLUSION • Hardware hacking can be lots of fun even for software peeps • The initial part is simple and doesn’t have a HIGH learning curve • The more complicated parts will come naturally because you had so much fun with the beginning • Tools for hardware hacking have lowered in price where a beginners kit can easily be bough for 300-350 euros • Protocols down there still need to improve a lot on security
Editor's Notes
- #23: If we look at the display we can see that the resistor measures as 1.46Ω, we can then assume that this is a 1.5M Ω resistor.
- #38: Charlie miller research on batteries of mac books – it used i2cWii nunchuck = i2cPower button on laptop = SMBus which is i2c
- #52: Does anyone remember the times we used to buy Motorola modems for cable and then switch the configs to get higher speeds? DOCSIS 2.0
- #56: It considers bits two at a time, taking one of three actions: when two successive bits are equal, they are discarded; a sequence of 1,0 becomes a 1; and a sequence of 0,1 becomes a zero. It thus represents a falling edge with a 1, and a rising edge with a 0It cannot assure randomness in its output, however. What it can do (with significant numbers of discarded bits) is transform a biased random bit stream into an unbiased one.

















































![HARDWARE HACKING HACKZ
• Linksys WMB54G and others!
Connector J9
Pin 1 – TX – Transmission
Pin 2 – RX – Receiver
Pin 8 – GND - Ground
RAMDISK: ext2 filesystem found at block 0
RAMDISK: Loading 4096 blocks [1 disk] into
ram disk... done.
Freeing initrd memory: 4096k freed
VFS: Mounted root (ext2 filesystem).
Freeing unused kernel memory: 60k freed
mount /proc file system ok!
serial console detected. Disabling virtual
terminals.
init started: BusyBox v1.00-pre8
(2008.01.17-05:54+0000) multi-call binary
BusyBox v1.00-pre8 (2008.01.17-05:54+0000)
Built-in shell (ash)
Enter 'help' for a list of built-in commands.
#
http://www.devttys0.com/2012/07/hacking-the-linksys-wmb54g/](https://image.slidesharecdn.com/hardwarehacking101-130608195527-phpapp01/85/Hardware-hacking-101-51-320.jpg)








