How to encrypt everything that moves and keep it usable
- 1. UNCLASSIFIED//COMSEC//CRYPTO UNCLASSIFIED//COMSEC//CRYPTO nsa How to Encrypt Everything That Moves and Keep It Usable Denis Gundarev, Application Solutions Architect, VMware [email protected] @fdwl Delivered From: @FDWL Dated: 20150722 Page 0
- 2. UNCLASSIFIED//COMSEC//CRYPTO UNCLASSIFIED//COMSEC//CRYPTO nsafdwl@E0D23:~# gpg –d message -----BEGIN PGP SIGNED MESSAGE----- Hash: SHA1 Hi %username%, my name is Denis Gundarev, I’m a Senior MTS/Architect at VMware I hope you understand that the opinions expressed here represent my own and not those of my employer. All data and information provided in this presentation is for informational purposes only. -----BEGIN PGP SIGNATURE----- iD8DBkjNWQIQFFxqRFCkjNWQIMEeCgg7y6IUikeCgg7yjNWQIW6eCgg7y3QE= =aAhr -----END PGP SIGNATURE-----
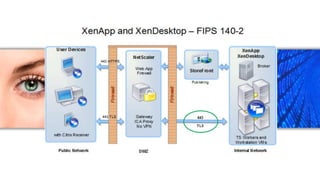
- 4. FIPS 140-2 Compliant & Common Criteria Certified Certified Security Worldwide recognition as the industry standard for App and Desktop security XenApp & XenDesktop are Common Criteria Certified XenApp & XenDesktop are FIPS compliant, simplifying highly regulated compliance FIPS Compliance Documents http://www.citrix.com/about/legal/security-compliance/security-standards.html Common Criteria Certificates http://www.cesg.gov.uk/finda/Pages/CCITSECResults.aspx?post=1&company=Citrix+Systems+Inc&status=Certified&sort=name
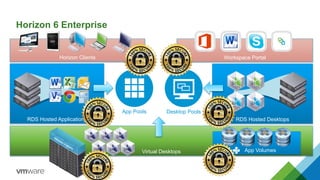
- 6. Workspace PortalHorizon Clients Virtual Desktops RDS Hosted DesktopsRDS Hosted Applications Horizon 6 Enterprise App Volumes Desktop PoolsApp Pools
- 7. Agenda Introduction to PKI TLS for you IPsec is your friend Security regulations in a real world 7
- 8. Introduction to Public Key Infrastructure (PKI)
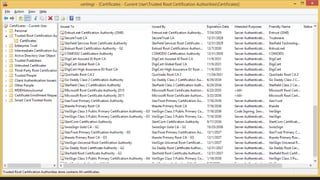
- 9. Certificates
- 10. Root Certification Authority Subordinate Certification Authority Certificate Certificate Certificate Certificate Public Key Infrastructure
- 14. Privet! I will send you encrypted message, use secret word “secret” to decrypt it! Hello x secret= ЙЦГШЩЗЪФ ЮБЬИЧЯЖД / secret = Nice to meet you ЙЦГШЩЗЪФ! ЙЦГШЩЗЪФ / secret= HelloЮБЬИЧЯЖД! Nice to meet you x secret= ЮБЬИЧЯЖД Got It! Symmetric Encryption
- 15. I want to send you a private message but don’t want anyone else to read it… Hello x a12f2d8ac = ЙЦГШЩЗЪФ ЙЦГШЩЗЪФ! ЙЦГШЩЗЪФ / privatesecret= Hello Got It! Not a problem, here’s my public key – a12f2d8ac Asymmetric Encryption
- 16. Howdy-doo! hablemos español! Here’s my ID, public key and my 6bcfae6a Privet! I want to speak privately with Yosemite Sam. I can speak Russian, Chinese, Spanish and English here’s my random e77dfb41 Hmm, California, USA, ok I trust your ID Encrypt (convertir en Español (E77dfb41 + 6bcfae6a)) Here’s pre- master, en español, encrypted with your private Decrypt (pre- master) Lo tengo! (Got it!) 𝑀𝐴𝐶 = 𝑏2 − 4𝑎𝑐 2𝑎 𝑀𝐴𝐶 = 𝑏2 − 4𝑎𝑐 2𝑎 es tan genial para hablar en privado sí, es difícil hablar libre en estos días SSL/TLS Handshake Hmm, California, USA, ok I trust your ID
- 18. Just need to see your I.D. please. Sorry, but we don’t sell beer to Russians
- 20. 20
- 23. I heard that self- signed certificates are not secure!!!
- 25. Keep Private Keys Private NTFS ACL Windows private key ACL Use Hardware Security modules Windows support out of the box Apache support Avoid using shared wildcard certificates
- 26. Subordinate Certification Authority ESX Hosts Network equipment Users Public Key Infrastructure Root Certification Authority Mobile devices
- 27. TLS recommendations Use TLS or DTLS for everything that moves over the wire RDP https://technet.microsoft.com/en-us/magazine/ff458357.aspx XenDesktop http://blogs.citrix.com/2014/10/16/xenapp-and-xendesktop-7-6-security-fips-140-2-and-ssl- to-vda/ Horizon View https://pubs.vmware.com/horizon-view-60/topic/com.vmware.ICbase/PDF/horizon-view- 60-scenarios-ssl-certificates.pdf SQL Server http://blogs.msdn.com/b/sqlserverfaq/archive/2012/04/04/can-tls-certificate-be-used-for- sql-server-encryption-on-the-wire.aspx LDAP http://social.technet.microsoft.com/wiki/contents/articles/2980.ldap-over-ssl-ldaps- certificate.aspx Use other encryption methods for other protocols SMB Encryption http://blogs.technet.com/b/filecab/archive/2012/05/03/smb-3-security-enhancements- in-windows-server-2012.aspx Horizon View https://pubs.vmware.com/horizon-view-60/topic/com.vmware.ICbase/PDF/horizon-view- 60-security.pdf
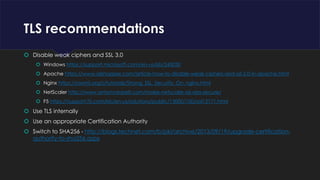
- 28. TLS recommendations Disable weak ciphers and SSL 3.0 Windows https://support.microsoft.com/en-us/kb/245030 Apache https://www.sslshopper.com/article-how-to-disable-weak-ciphers-and-ssl-2.0-in-apache.html Nginx https://raymii.org/s/tutorials/Strong_SSL_Security_On_nginx.html NetScaler http://www.antonvanpelt.com/make-netscaler-ssl-vips-secure/ F5 https://support.f5.com/kb/en-us/solutions/public/13000/100/sol13171.html Use TLS internally Use an appropriate Certification Authority Switch to SHA256 - http://blogs.technet.com/b/pki/archive/2013/09/19/upgrade-certification- authority-to-sha256.aspx
- 29. Know the difference Self-signed vs. preinstalled certificate Check the date/name Intended usage Make sure that you use correct templates Encryption vs. Obfuscation Unsecured private key = obfuscation
- 32. Demo time
- 34. FIPS/Common Criteria Remember who do you trust Certified software/hardware doesn’t secure you automatically. Security policy “System Cryptography: Use FIPS compliant algorithms for encryption, hashing, and signing.” does not affect third-party and breaks .net Certification may take years, release cycle usually shorter
- 35. Compliance A foolproof plan for security Nothing is foolproof to a sufficiently talented fool Standardized environments are easier to hack Additional budget for IT Enforcing documentation Just a checklist to impress auditor
- 38. your questions. It’s now safe to ask
Editor's Notes
- #5: 4