How to use SELINUX (No I don't mean turn it off)
- 1. HOWTOUSE SELINUX CHUCK REEVES @MANCHUCK NO I DON'T MEAN TURN IT OFF
- 2. ZendCon 2016 HOW TO USE SELINUX - NO I DON'T MEAN TURN IT OFF ABOUT ▸ Built using Kernel Modules ▸ More permissions than CRUD and Access ▸ Allows Multi-Level Security using BLP and Biba Models ▸ Permissions set on the inode instead of the file ▸ Mandatory Access Control (MAC)
- 3. ZendCon 2016 HOW TO USE SELINUX - NO I DON'T MEAN TURN IT OFF
- 4. ZendCon 2016 HOW TO USE SELINUX - NO I DON'T MEAN TURN IT OFF WHAT YOU NEED TO KNOW ▸ Each iNode is given a single context ▸ Each context identifies a user, role, type and level ▸ SELINUX then allows (or denies) access using the context with a policy ▸ Decision is cached in the Access Vector Cache (AVC) ▸ Decisions is made after the DAC access is checked
- 5. ZendCon 2016 HOW TO USE SELINUX - NO I DON'T MEAN TURN IT OFF WHAT YOU NEED TO KNOW ▸ SELINUX manages: ▸ Users ▸ Sockets ▸ Memory ▸ Directories ▸ TCP/UDP connections
- 6. ZendCon 2016 HOW TO USE SELINUX - NO I DON'T MEAN TURN IT OFF PROCESS TYPES ▸ Confined ▸ Runs in own domain (role) ▸ Resources are limited to the roles and policy ▸ Un-Confined ▸ fallback to the DAC policies
- 7. ZendCon 2016 HOW TO USE SELINUX - NO I DON'T MEAN TURN IT OFF CONTEXTS ▸ Policy checks context of inode for access ▸ "If a process is running with <context_foo> then anything with <context_foo_type> is allowed access" ▸ Four parts: user, role, type and level (optional)
- 8. ZendCon 2016 HOW TO USE SELINUX - NO I DON'T MEAN TURN IT OFF CONTEXTS ▸ Set automatically based on the parent context (mostly) ▸ RPM ▸ Management tools (ansible, chef, puppet) ▸ When a File transitions (moving an uploaded file) ▸ By the sysadmin with chcon, restorecon
- 9. ZendCon 2016 HOW TO USE SELINUX - NO I DON'T MEAN TURN IT OFF FINDING CONTEXT ls -alZ /home
- 10. ZendCon 2016 HOW TO USE SELINUX - NO I DON'T MEAN TURN IT OFF FINDING CONTEXT ps -Z
- 11. ZendCon 2016 HOW TO USE SELINUX - NO I DON'T MEAN TURN IT OFF BOOLEANS ▸ On off settings for policies ▸ Allow HTTPD to make network connections ▸ Allow FTP to access home directories ▸ Overcomes issues with over labeling contexts
- 12. ZendCon 2016 HOW TO USE SELINUX - NO I DON'T MEAN TURN IT OFF TURNING IT BACK ON ▸ TARGETED ▸ PERMISSIVE ▸ DISABLED (You already know this one)
- 13. ZendCon 2016 HOW TO USE SELINUX - NO I DON'T MEAN TURN IT OFF TURNING IT BACK ON <edit> /etc/selinux/config
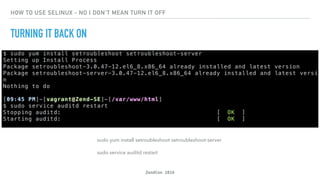
- 14. ZendCon 2016 HOW TO USE SELINUX - NO I DON'T MEAN TURN IT OFF TURNING IT BACK ON sudo yum install setroubleshoot setroubleshoot-server sudo service auditd restart
- 15. ZendCon 2016 HOW TO USE SELINUX - NO I DON'T MEAN TURN IT OFF TURNING IT BACK ON ls -alZ sudo touch /.autorelabel
- 16. ZendCon 2016 HOW TO USE SELINUX - NO I DON'T MEAN TURN IT OFF TURNING IT BACK ON ls -alZ
- 17. ZendCon 2016 HOW TO USE SELINUX - NO I DON'T MEAN TURN IT OFF
- 18. ZendCon 2016 HOW TO USE SELINUX - NO I DON'T MEAN TURN IT OFF
- 19. ZendCon 2016 TEXT TROUBLESHOOTING EXAMPLE: DATABASE tail -f /var/log/audit/audit.log
- 20. ZendCon 2016 TEXT TROUBLESHOOTING EXAMPLE: DATABASE tail -f /var/log/messages
- 21. ZendCon 2016 TEXT TROUBLESHOOTING EXAMPLE: DATABASE sealert -l <message id>
- 22. ZendCon 2016 HOW TO USE SELINUX - NO I DON'T MEAN TURN IT OFF BOOLEANS setsebool -P httpd_can_network_connect 1
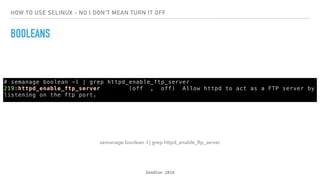
- 23. ZendCon 2016 HOW TO USE SELINUX - NO I DON'T MEAN TURN IT OFF BOOLEANS semanage boolean -l | grep httpd_enable_ftp_server
- 24. ZendCon 2016 HOW TO USE SELINUX - NO I DON'T MEAN TURN IT OFF BOOLEANS getsebool -a getsebool <boolean>
- 25. ZendCon 2016 HOW TO USE SELINUX - NO I DON'T MEAN TURN IT OFF BOOLEANS semanage boolean -l | grep httpd_enable_ftp_server
- 26. ZendCon 2016 TEXT TROUBLESHOOTING EXAMPLE: FILE UPLOAD ls -Z
- 27. ZendCon 2016 TEXT TROUBLESHOOTING EXAMPLE: FILE UPLOAD sealert -l <message id>
- 28. ZendCon 2016 HOW TO USE SELINUX - NO I DON'T MEAN TURN IT OFF SETTING CONTEXT chcon -R -t httpd_sys_content_t web/ ls -Z web
- 29. ZendCon 2016 HOW TO USE SELINUX - NO I DON'T MEAN TURN IT OFF SETTING CONTEXT mkdir web/ touch web/file{1,2,3} ls -Z web
- 30. ZendCon 2016 HOW TO USE SELINUX - NO I DON'T MEAN TURN IT OFF
- 31. ZendCon 2016 HOW TO USE SELINUX - NO I DON'T MEAN TURN IT OFF
- 32. ZendCon 2016 HOW TO USE SELINUX - NO I DON'T MEAN TURN IT OFF
- 33. ZendCon 2016 HOW TO USE SELINUX - NO I DON'T MEAN TURN IT OFF RESOURCES ▸ RedHat Documentation for SELINUX: https://access.redhat.com/ documentation/en-US/Red_Hat_Enterprise_Linux/6/html/Security- Enhanced_Linux/index.html ▸ Servers for Hackers, Batteling SELINUX: https://serversforhackers.com/video/ battling-selinux-cast ▸ SELinux For Mere Mortals: https://www.youtube.com/watch?v=MxjenQ31b70