Humming code error detector 7_communications.ppt
- 1. Communications Most modern control involves interactions between many microprocessors Examples: PLC: Programming done on PC; uploaded to PLC Complex PLC control requires interaction between many PLC’s e.g. automation controls in an MTR station Microprocessor: Phone Phone (e.g. to exchange phone numbers) Phone PC (to upload address book) Networked video games with multiple players Computers: Internet, EDI
- 2. Communications For devices to exchange data, several things must work together: Assume: Data controlled change of voltage in a wire. Bit-Streams: Example: message = “Wow” W o w 1010 111 1101 111 1110 111 mark 1 0 1 0 1 1 1 stop bits start bit 1 1 0 1 1 1 1 1 1 1 0 1 1 1 idle ASCII V time W: least significant bit most significant bit
- 3. Communications W o w 1010 111 1101 111 1110 111 mark 1 0 1 0 1 1 1 stop bits start bit 1 1 0 1 1 1 1 1 1 1 0 1 1 1 idle For devices to exchange data, several things must work together: - A wire must connect the devices - The voltage levels must match: sender sets “voltage of 5V” ‘1’ => receiver must have a 5V sensor; (must interpret same way) - The duration for each bit (communication frequency, baud rate) - Start bit(s), stop bit(s) - Both must be using ASCII code …
- 4. Asynchronous vs Synchronous communications Why do we need start/stop bits ? Prepares the receiving device to start recording data communication is ASYNCHRONOUS Idle Start bit LSB seven data bits Parity bit Stop bits Idle/next caracter asynchronous 7-bit character + parity bit Coordinated connection between the devices: SYNCHRONOUS communication - Receiver continually hunts for sync character (in ASCII: 1001 0110) - [Copies data into the data register; char available flag ON; data read] x CT - Check against CT; - end sync bit hunt mode. SYNCSYNC D A T A ETX CT SYNC synchronous block of data
- 5. Synchronization of communication Receiver Transmitter and Synchronization generator data synchro (a) Transmitter generates the synchronization reference Receiver Transmitter data synchro clock (b) External synchronization clock unit Receiver Transmitter and Synchronization generator data + synchro (c) Transmitter superposes clock and data
- 6. Serial vs Parallel communication Serial: one signal carrying wire Parallel: 8, 16, or 32 signal carrying wires Parallel: faster, more expensive, used for short-distances only examples: Data bus, Control bus in a microprocessor; parallel port in PC
- 7. Bit coding Binary Direct NRZ (non- return to zero RZ (return to zero) manchester coding differential manchester coding 1 0 1 0 0 0 1 1 0 V NOT Good; constant HIGH voltage delays [due to Capacitance/Inductance] Very commonly used Signal during half-cycle then return to zero High-to-Low ‘1’ Low-to-High ‘0’ Voltage change at start of cycle ‘0’ No change at start of cycle ‘1’ Voltage flips at mid-cycle
- 8. Communication: Handling errors Problem: some data sent from A B may get ‘corrupted’ Why is this a big problem? - How will the receiver know they received ‘bad data’? Probability of communication error is reduced by: Error detection and Correction
- 9. Communications: Error detection and correction schemes Importance of EDC (error detection and correction): Assume error rate of 0.1% Average sentence of text: 125 characters = 125 x 8 = 1000 bits 0.1% error 1 error per sentence! Techniques for EDC: 1. IF receiver detects error requests sender to re-transmit 2. Receiver detects and corrects error without re-transmission
- 10. Error detection: Parity Error detection: some information is added to message, that allows checking for errors. PARITY 1 ASCII char = 7bits; 1 extra bit is added to each character, called parity bit: Even parity: value of parity bit is set to make total number of 1’s even. Odd parity: value of parity bit is set to make total number of 1’s odd. Example: (ASCII) W: 1010 111 (odd parity) W: 0 1010 111 (even parity) W: 1 1010 111
- 11. Error Detection: Checksums Let: message = “Hello, world” == 12 bytes == 128 bits (including parity bit) Hello, world 72 101 108 108 111 44 32 119 111 114 108 100 *assuming: parity bit = 0 Sum = 72 + 101 + 108 + … + 100 = 1128 Checksum [16-bits] = 1128 Checksum [8-bits] = 1128 mod 256 = 104 Message: 72 101 108 108 111 44 32 119 111 114 108 100 104 1 checksum/12 bytes too much overhead typical use: 1 checksum byte per 128 Bytes of data
- 12. Error Detection: Cyclic Redundancy Check (CRC) Basic idea of CRC: Number: 629 Divisor: 25 mod( Number, Divisor): mod(629, 25) = 4 Transmit: (629,4) Receiver: mod( 629, 25) == 4 ? Transmission probably OK Pre-agreed between sender/receiver
- 13. Error Detection: Cyclic Redundancy Check (CRC) Implementation of CRC: Number: Bitstream of 1 Block (e.g. 128 Bytes) Divisor: common CRC schemes are: CRC12 1100000001011 CRC16 11000000000000101 CRC-CCITT 10001000000100001 CRC32 100000100110000010001110110110111 M = mod( Number, Divisor): computed very efficiently with simple circuits Receiver: FRAME: Number MOD mod(Number MOD, CRC) = = M ? Yes Transmission probably OK
- 14. Error detection and Correction Parity, Checksum, CRC: detect error, request re-transmit on error Redundant data transmission: detect error, and correct automatically! Common methods: Repeating Hamming codes Reed-Muller codes, etc… Majority coding: Data: 010 Transmit: 000111000 Receive (with error): 001011000 0 1 0 select majority from each group of 3 Accepted data: 010
- 15. Hamming codes Problem of Majority coding: (1) too much redundancy (2) burst errors can’t be handled Hamming code: main idea of a (7, 4) Hamming code Data: 0011 Add 1-bit to each circle, total of each circle even
- 16. (7, 4) Hamming code Data: 0011 transmit receiver red-circle: parity ERROR green circle: parity ERROR blue circle: parity OK Error must be in bit shared by red and green
- 17. (7, 4) Hamming code… Data: 0011 transmit receiver red-circle: parity OK green circle: parity OK blue circle: parity ERROR Error must be in unshared bit of Blue circle! HW: verify that ALL 1-bit errors can be detected and corrected!
- 18. Hamming code… Data: bit-stream write data in particular sequence receiver checks Hamming codes, corrects errors transmit compute, add hamming code bits to data Corrected data Common Hamming code used: (12, 8) Hamming code
- 19. Extending Hamming code for longer bit-stream 1. All bit positions that are powers of two are used as parity bits. (positions 1, 2, 4, 8, 16, 32, 64, etc.) 2. All other bit positions are for the data to be encoded. (positions 3, 5, 6, 7, 9, 10, 11, 12, 13, 14, 15, 17, etc.) 3. Each parity bit stores the parity for assigned bits in the code word: The position of the parity bit determines the sequence of bits that it alternately checks and skips. Position 1: skip 0 bits, check 1 bit, skip 1 bit, check 1 bit, skip 1 bit, … Position 2: skip 1 bit, check 2 bits, skip 2 bits, check 2 bits, skip 2 bits, … Position 4: skip 3 bits, check 4 bits, skip 4 bits, check 4 bits, skip 4 bits, … Position 8: skip 7 bits, check 8 bits, skip 8 bits, check 8 bits, skip 8 bits, … Position 16: skip 15 bits, check 16 bits, skip 16 bits, check 16 bits, skip 16 bits, … Position 32: skip 31 bits, check 32 bits, skip 32 bits, check 32 bits, skip 32 bits, …
- 20. Burst errors Problem with Hamming: burst errors: several contiguous data bits in error) Handling burst errors: - Interleaving - Reed-Solomon coding Examples of usage: storage media (CDROM’s), …
- 21. Packets Long message p(error) is high Need to re-transmit [part] of message Solution: Break message into small “packets” send packets 1-by-1 To address From address Long message part 1 of 3 part 2 of 3 part 3 of 3 To address From address data (part 1 of 3) EDC 1/3 To address From address data (part 2 of 3) EDC 2/3 To address From address data (part 3 of 3) EDC 3/3 packets transmit Receiver Re-constructs Message from three parts received Typical packet size: 2048 - 4096 Bytes Question: Why do some web pages load in non-sequential fashion (some pictures load first, others later) Note: later we’ll see structure of packet in more detail
- 22. Network terminology LAN: Local Area Network A network of communicating devices in a small area (e.g. a building, a factory, etc.) WAN: Wide Area Network Two or more LAN’s connected to each other, over a large area, e.g. international communication networks. Common ways of physically connecting computers in a LAN: Cables (wires), Bluetooth, Wi-Fi… Common ways of connecting between LAN’s in a WAN: Telephone networks, Long-distance cables, Satellites
- 23. Network topologies Suppose N computers need to communicate with each other Pairwise connections: How many ? Problems ?
- 24. Network topologies Network topology describes how different devices are (physically) connected to each other. 1 2 3 4 5 6 1 2 3 4 5 6 Central Hub 1 2 3 4 5 6 1 2 3 4 5 6 • • • •• • Tap Bus Stub (a) Ring topology (b) Star topology (c) Mesh topology (d) Bus topology Terminator
- 25. Network communication basics Computer Networking: A Top Down Approach Featuring the Internet, 3rd edition. Jim Kurose, Keith Ross Addison-Wesley, July 2004. The following slides, based largely on the those provided by Kurose and Ross, will be used to get an introduction to real-world network communications.
- 26. What’s the Internet ? • millions of connected computing devices: hosts = end systems • running network applications • communication links – fiber, copper, radio, satellite – transmission rate = bandwidth • routers: forward packets local ISP UST network regional ISP router workstation server mobile
- 27. What’s the Internet.. • protocols control sending, receiving of msgs – e.g., TCP, IP, HTTP, FTP, PPP • Internet: “network of networks” – public: Internet – private: Intranet • Internet standards – RFC: Request for comments – IETF: Internet Engineering Task Force local ISP UST network regional ISP router workstation server mobile
- 28. What’s a protocol? a human protocol and a computer network protocol: Hi Hi What’s the time? 2pm TCP connection req TCP connection response Get http://www.awl.com/kurose-ross <file> time protocols define format, order of msgs sent and received among network entities, and actions taken on msg transmission, receipt
- 29. A closer look at network structure • network edge: applications and hosts • network core: – routers – network of networks • access networks, physical media: communication links
- 30. The network edge • end systems (hosts): – run application programs – e.g. Web, email – at “edge of network” • client/server model – client host requests, receives service from always-on server – e.g. Web browser/server; email client/server
- 31. Network edge: connection-oriented service Goal: data transfer between end systems • handshaking: setup (prepare for) data transfer ahead of time – Hello, hello back human protocol – set up “state” in two communicating hosts TCP service [RFC 793] • reliable, in-order byte-stream data transfer – loss: acknowledgements and retransmissions • flow control: – sender won’t overwhelm receiver • congestion control: – senders “slow down sending rate” when network congested e.g.
- 32. Network edge: connectionless service Goal: data transfer between end systems App’s using TCP: • HTTP (Web), FTP (file transfer), Telnet (remote login), SMTP (email) App’s using UDP: • streaming media, teleconferencing, DNS, Internet telephony UDP - User Datagram Protocol: connectionless unreliable data transfer no flow control no congestion control e.g.
- 33. The Network Core • mesh of interconnected routers • the fundamental question: how is data transferred through net? – circuit switching: dedicated circuit per call: telephone net – packet-switching: data sent through net in discrete “chunks”
- 34. Network Core: Circuit Switching End-end resources reserved for “call” • link bandwidth, switch capacity • dedicated resources: no sharing • circuit-like (guaranteed) performance • call setup required
- 35. Network Core: Packet Switching Each end-end data stream divided into packets • user A, B packets share network resources • each packet uses full link bandwidth • resources used as needed Resource allocation: • total resource demand can exceed amount available • congestion: packets queue, wait for link use • store and forward: packets move one hop at a time – Node receives complete packet before forwarding Bandwidth division into “pieces” Dedicated allocation Resource reservation
- 36. Packet-switching: store-and-forward • Packet Length: L bits • Baud rate: R bps • Time to push packet on link: L/R sec • Entire packet must arrive at router before it can be transmitted on next link: store and forward • delay = 3L/R Example: • L = 7.5 Mbits • R = 1.5 Mbps • delay = 15 sec R R R L
- 37. Access networks and physical media Q: How to connect end systems to edge router? • residential access nets • institutional access networks (school, company) • mobile access networks
- 38. Residential access: point to point access • Phone modem – up to 56Kbps direct access to router (often less) – Can’t surf and phone at same time: can’t be “always on” • ADSL: asymmetric digital subscriber line [similar to NOW Broadband] – up to 1 Mbps upstream – up to 8 Mbps downstream
- 39. Residential access… Cable modems home cable headend cable distribution network (simplified)
- 40. Residential access: cable modems Diagram: http://www.cabledatacomnews.com/cmic/diagram.html
- 41. Company access: local area networks • company/univ local area network (LAN) connects end system to edge router • Ethernet: – shared or dedicated link connects end system and router – 10 Mbs, 100Mbps, Gigabit Ethernet
- 42. Wireless access networks • shared wireless access network connects end system to router – via base station aka “access point” • wireless LANs: – 802.11b (WiFi): 11 Mbps (good for networks) – bluetooth: 720Kbps (good for device-to-device) base station mobile hosts router
- 43. Home networks Typical home network components: • ADSL or cable modem • router/firewall/NAT • Ethernet • wireless access point wireless access point wireless laptops router/ firewall cable modem to/from cable headend Ethernet
- 44. Internet structure: network of networks • a packet passes through many networks! Tier 1 ISP Tier 1 ISP Tier 1 ISP Network Access Point Tier-2 ISP Tier-2 ISP Tier-2 ISP Tier-2 ISP Tier-2 ISP local ISP local ISP local ISP local ISP local ISP Tier 3 ISP local ISP local ISP local ISP
- 45. Protocol “Layers” Networks are complex! • many “pieces”: – hosts – routers – links of various media – applications – protocols – hardware, software
- 46. Analogy: Organization of air travel ticket (purchase) baggage (check) gates (load) runway takeoff airplane routing ticket (complain) baggage (claim) gates (unload) runway landing airplane routing airplane routing
- 47. ticket (purchase) baggage (check) gates (load) runway (takeoff) airplane routing departure airport arrival airport intermediate air-traffic control centers airplane routing airplane routing ticket (complain) baggage (claim gates (unload) runway (land) airplane routing ticket baggage gate takeoff/landing airplane routing Layering of airline functionality Layers: each layer implements a service – via its own internal-layer actions – relying on services provided by layer below
- 48. Why layering? Dealing with complex systems: • explicit structure allows identification, relationship of complex system’s pieces – layered reference model for discussion • modularization eases maintenance, updating of system – change of implementation of layer’s service transparent to rest of system – e.g., change in gate procedure doesn’t affect rest of system • layering considered harmful?
- 49. Internet protocol stack • application: supporting network applications – FTP, SMTP, STTP • transport: host-host data transfer – TCP, UDP • network: routing of datagrams from source to destination – IP, routing protocols • link: data transfer between neighboring network elements – PPP, Ethernet • physical: bits “on the wire” application transport network link physical
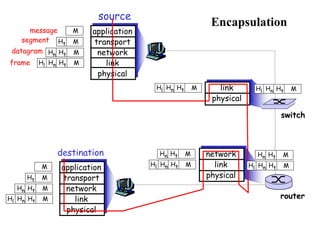
- 50. message segment datagram frame source application transport network link physical Ht Hn Hl M Ht Hn M Ht M M destination application transport network link physical Ht Hn Hl M Ht Hn M Ht M M network link physical link physical Ht Hn Hl M Ht Hn M Ht Hn Hl M Ht Hn M Ht Hn Hl M Ht Hn Hl M router switch Encapsulation
- 51. The Network Layer: Internet Protocol • What’s inside a router • Internet Protocol and IP addresses • How packets are routed Internet Protocol (IP) The Internet Protocol (IP) is a network-layer (Layer 3) protocol that contains addressing information and some control information that enables packets to be routed.
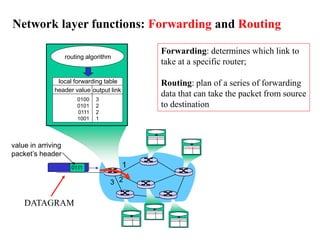
- 52. 1 2 3 0111 value in arriving packet’s header routing algorithm local forwarding table header value output link 0100 0101 0111 1001 3 2 2 1 Network layer functions: Forwarding and Routing Forwarding: determines which link to take at a specific router; Routing: plan of a series of forwarding data that can take the packet from source to destination DATAGRAM
- 53. IP datagram format ver length 32 bits data (variable length, typically a TCP or UDP segment) 16-bit identifier Internet checksum time to live 32 bit source IP address IP protocol version number header length (bytes) max number remaining hops (decremented at each router) for fragmentation/ reassembly total datagram length (bytes) upper layer protocol to deliver payload to head. len type of service “type” of data flgs fragment offset upper layer 32 bit destination IP address Options (if any) E.g. timestamp, record route taken, specify list of routers to visit. how much overhead with TCP? • 20 bytes of TCP • 20 bytes of IP • = 40 bytes + app layer overhead
- 54. Datagram networks • packets forwarded using destination host address – packets between same source-dest pair may take different paths application transport network data link physical application transport network data link physical 1. Send data 2. Receive data Main router functions: • run routing algorithms/protocol (RIP, OSPF, BGP) • forwarding datagrams from incoming to outgoing link
- 55. IPAddressing: introduction • IP address: 32-bit identifier for host, router interface • interface: connection between host/router and physical link – router’s typically have multiple interfaces – host may have multiple interfaces – IP addresses associated with each interface 223.1.1.1 223.1.1.2 223.1.1.3 223.1.1.4 223.1.2.9 223.1.2.2 223.1.2.1 223.1.3.2 223.1.3.1 223.1.3.27 223.1.1.1 = 11011111 00000001 00000001 00000001 223 1 1 1
- 56. Subnets • IP address: – subnet part (high order bits) – host part (low order bits) • What’s a subnet ? – device interfaces with same subnet part of IP address – can physically reach each other without intervening router 223.1.1.1 223.1.1.2 223.1.1.3 223.1.1.4 223.1.2.9 223.1.2.2 223.1.2.1 223.1.3.2 223.1.3.1 223.1.3.27 network consisting of 3 subnets LAN
- 57. 223.1.1.0/24 223.1.2.0/24 223.1.3.0/24 • To determine the subnets, detach each interface from its host or router, creating islands of isolated networks. Each isolated network is called a subnet. Subnet mask: /24 Subnets
- 59. IP addresses: how to get one? Q: How does host get IP address? • hard-coded by system administrator in a file – Wintel: control-panel->network->configuration->tcp/ip->properties • DHCP: Dynamic Host Configuration Protocol: dynamically get address from as server – “plug-and-play”
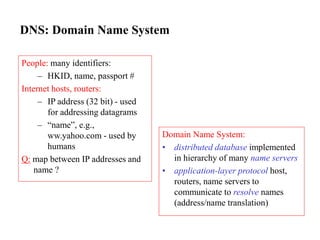
- 60. DNS: Domain Name System People: many identifiers: – HKID, name, passport # Internet hosts, routers: – IP address (32 bit) - used for addressing datagrams – “name”, e.g., ww.yahoo.com - used by humans Q: map between IP addresses and name ? Domain Name System: • distributed database implemented in hierarchy of many name servers • application-layer protocol host, routers, name servers to communicate to resolve names (address/name translation)
- 61. Transport services and protocols • provide logical communication between app processes running on different hosts • Most common transport protocol: TCP application transport network data link physical application transport network data link physical network data link physical network data link physical network data link physical network data link physical network data link physical The TCP provides a reliable, continuous stream of data - protocol for automatically requesting missing data - reordering IP packets that arrive out of order - converting IP datagrams to a streaming protocol - routing data within a computer to the correct application.
- 62. The Application layer • Principles of network applications • Web and HTTP • FTP • Electronic Mail – SMTP, POP3, IMAP • DNS • Socket programming with TCP • Building a Web server
- 63. Creating a network app Write programs that – run on different end systems and – communicate over a network. – e.g., Web: Web server software communicates with browser software No software written for devices in network core – Network core devices do not function at app layer – This design allows for rapid app development application transport network data link physical application transport network data link physical application transport network data link physical
- 64. Client-server architecture server: – always-on host – permanent IP address clients: – communicate with server – may be intermittently connected – may have dynamic IP addresses – do not communicate directly with each other
- 65. Sockets • process sends/receives messages to/from its socket • socket analogous to door – sending process shoves message out door – sending process relies on transport infrastructure on other side of door which brings message to socket at receiving process process TCP with buffers, variables socket host or server process TCP with buffers, variables socket host or server Internet controlled by OS controlled by app developer
- 66. Addressing processes • For a process to receive messages, it must have an identifier • A host has a unique32-bit IP address • Q: does the IP address of the host on which the process runs suffice for identifying the process? • Answer: No, many processes can be running on same host • Identifier includes both the IP address and port numbers associated with the process on the host. • Example port numbers: – HTTP server: 80 – Mail server: 25
- 67. Socket programming Socket API • introduced in BSD4.1 UNIX, 1981 • explicitly created, used, released by apps • client/server paradigm • two types of transport service via socket API: – unreliable datagram – reliable, byte stream-oriented a host-local, application-created, OS-controlled interface (a “door”) into which application process can both send and receive messages to/from another application process socket Goal: learn how to build client/server application that communicate using sockets
- 68. Socket-programming using TCP Socket: a door between application process and end-end-transport protocol (UCP or TCP) TCP service: reliable transfer of bytes from one process to another process TCP with buffers, variables socket controlled by application developer controlled by operating system host or server process TCP with buffers, variables socket controlled by application developer controlled by operating system host or server internet
- 69. Socket programming with TCP Client must contact server • server process must first be running • server must have created socket (door) that welcomes client’s contact Client contacts server by: • creating client-local TCP socket • specifying IP address, port number of server process • When client creates socket: client TCP establishes connection to server TCP • When contacted by client, server TCP creates new socket for server process to communicate with client – allows server to talk with multiple clients – source port numbers used to distinguish clients TCP provides reliable, in-order transfer of bytes (“pipe”) between client and server application viewpoint
- 70. Stream terminology • A stream is a sequence of characters that flow into or out of a process. • An input stream is attached to some input source for the process, eg, keyboard or socket. • An output stream is attached to an output source, eg, monitor or socket.
- 71. Socket programming with TCP Example client-server app: 1) client reads line from standard input (inFromUser stream) , sends to server via socket (outToServer stream) 2) server reads line from socket 3) server converts line to uppercase, sends back to client 4) client reads, prints modified line from socket (inFromServer stream) outToServer to network from network inFromServer inFromUser keyboard monitor Process clientSocket input stream input stream output stream TCP socket Client process client TCP socket
- 72. Client/server socket interaction: TCP wait for incoming connection request connectionSocket = welcomeSocket.accept() create socket, port=x, for incoming request: welcomeSocket = ServerSocket() create socket, connect to hostid, port=x clientSocket = Socket() close connectionSocket read reply from clientSocket close clientSocket Server (running on hostid) Client send request using clientSocket read request from connectionSocket write reply to connectionSocket TCP connection setup
- 73. Example: Java client (TCP) import java.io.*; import java.net.*; class TCPClient { public static void main(String argv[]) throws Exception { String sentence; String modifiedSentence; BufferedReader inFromUser = new BufferedReader(new InputStreamReader(System.in)); Socket clientSocket = new Socket("hostname", 6789); DataOutputStream outToServer = new DataOutputStream(clientSocket.getOutputStream()); Create input stream Create client socket, connect to server Create output stream attached to socket
- 74. Example: Java client (TCP), cont. BufferedReader inFromServer = new BufferedReader(new InputStreamReader(clientSocket.getInputStream())); sentence = inFromUser.readLine(); outToServer.writeBytes(sentence + 'n'); modifiedSentence = inFromServer.readLine(); System.out.println("FROM SERVER: " + modifiedSentence); clientSocket.close(); } } Create input stream attached to socket Send line to server Read line from server
- 75. Example: Java server (TCP) import java.io.*; import java.net.*; class TCPServer { public static void main(String argv[]) throws Exception { String clientSentence; String capitalizedSentence; ServerSocket welcomeSocket = new ServerSocket(6789); while(true) { Socket connectionSocket = welcomeSocket.accept(); BufferedReader inFromClient = new BufferedReader(new InputStreamReader(connectionSocket.getInputStream())); Create welcoming socket at port 6789 Wait, on welcoming socket for contact by client Create input stream, attached to socket
- 76. Example: Java server (TCP), cont DataOutputStream outToClient = new DataOutputStream(connectionSocket.getOutputStream()); clientSentence = inFromClient.readLine(); capitalizedSentence = clientSentence.toUpperCase() + 'n'; outToClient.writeBytes(capitalizedSentence); } } } Read in line from socket Create output stream, attached to socket Write out line to socket End of while loop, loop back and wait for another client connection



![Asynchronous vs Synchronous communications
Why do we need start/stop bits ?
Prepares the receiving device to start recording data
communication is ASYNCHRONOUS
Idle
Start
bit
LSB
seven data bits
Parity
bit Stop bits
Idle/next caracter
asynchronous 7-bit character + parity bit
Coordinated connection between the devices: SYNCHRONOUS communication
- Receiver continually hunts for sync character (in ASCII: 1001 0110)
- [Copies data into the data register; char available flag ON; data read] x CT
- Check against CT;
- end sync bit hunt mode.
SYNCSYNC D A T A ETX CT SYNC
synchronous block of data](https://image.slidesharecdn.com/7communications-240417013630-2a6178e1/85/Humming-code-error-detector-7_communications-ppt-4-320.jpg)


![Bit coding
Binary Direct
NRZ (non-
return to zero
RZ (return
to zero)
manchester
coding
differential
manchester
coding
1 0 1 0 0 0 1 1
0 V
NOT Good;
constant HIGH voltage
delays [due to Capacitance/Inductance]
Very commonly used
Signal during half-cycle
then return to zero
High-to-Low ‘1’
Low-to-High ‘0’
Voltage change at start of cycle ‘0’
No change at start of cycle ‘1’
Voltage flips at mid-cycle](https://image.slidesharecdn.com/7communications-240417013630-2a6178e1/85/Humming-code-error-detector-7_communications-ppt-7-320.jpg)



![Error Detection: Checksums
Let: message = “Hello, world” == 12 bytes == 128 bits (including parity bit)
Hello, world
72 101 108 108 111 44 32 119 111 114 108 100
*assuming: parity bit = 0
Sum = 72 + 101 + 108 + … + 100 = 1128
Checksum [16-bits] = 1128 Checksum [8-bits] = 1128 mod 256 = 104
Message: 72 101 108 108 111 44 32 119 111 114 108 100 104
1 checksum/12 bytes too much overhead
typical use: 1 checksum byte per 128 Bytes of data](https://image.slidesharecdn.com/7communications-240417013630-2a6178e1/85/Humming-code-error-detector-7_communications-ppt-11-320.jpg)









![Packets
Long message p(error) is high Need to re-transmit [part] of message
Solution: Break message into small “packets” send packets 1-by-1
To address From address Long message
part 1 of 3 part 2 of 3 part 3 of 3
To address From address data (part 1 of 3) EDC
1/3
To address From address data (part 2 of 3) EDC
2/3
To address From address data (part 3 of 3) EDC
3/3
packets
transmit
Receiver
Re-constructs
Message from
three parts received
Typical packet size: 2048 - 4096 Bytes
Question: Why do some web pages load in non-sequential fashion (some pictures load first, others later)
Note: later we’ll see structure of packet in more detail](https://image.slidesharecdn.com/7communications-240417013630-2a6178e1/85/Humming-code-error-detector-7_communications-ppt-21-320.jpg)









![Network edge: connection-oriented service
Goal: data transfer between end
systems
• handshaking: setup (prepare
for) data transfer ahead of time
– Hello, hello back human
protocol
– set up “state” in two
communicating hosts
TCP service [RFC 793]
• reliable, in-order byte-stream data
transfer
– loss: acknowledgements and
retransmissions
• flow control:
– sender won’t overwhelm
receiver
• congestion control:
– senders “slow down sending
rate” when network congested
e.g.](https://image.slidesharecdn.com/7communications-240417013630-2a6178e1/85/Humming-code-error-detector-7_communications-ppt-31-320.jpg)






![Residential access: point to point access
• Phone modem
– up to 56Kbps direct access to router
(often less)
– Can’t surf and phone at same time: can’t
be “always on”
• ADSL: asymmetric digital subscriber line [similar to NOW Broadband]
– up to 1 Mbps upstream
– up to 8 Mbps downstream](https://image.slidesharecdn.com/7communications-240417013630-2a6178e1/85/Humming-code-error-detector-7_communications-ppt-38-320.jpg)































![Example: Java client (TCP)
import java.io.*;
import java.net.*;
class TCPClient {
public static void main(String argv[]) throws Exception
{
String sentence;
String modifiedSentence;
BufferedReader inFromUser =
new BufferedReader(new InputStreamReader(System.in));
Socket clientSocket = new Socket("hostname", 6789);
DataOutputStream outToServer =
new DataOutputStream(clientSocket.getOutputStream());
Create
input stream
Create
client socket,
connect to server
Create
output stream
attached to socket](https://image.slidesharecdn.com/7communications-240417013630-2a6178e1/85/Humming-code-error-detector-7_communications-ppt-73-320.jpg)

![Example: Java server (TCP)
import java.io.*;
import java.net.*;
class TCPServer {
public static void main(String argv[]) throws Exception
{
String clientSentence;
String capitalizedSentence;
ServerSocket welcomeSocket = new ServerSocket(6789);
while(true) {
Socket connectionSocket = welcomeSocket.accept();
BufferedReader inFromClient =
new BufferedReader(new
InputStreamReader(connectionSocket.getInputStream()));
Create
welcoming socket
at port 6789
Wait, on welcoming
socket for contact
by client
Create input
stream, attached
to socket](https://image.slidesharecdn.com/7communications-240417013630-2a6178e1/85/Humming-code-error-detector-7_communications-ppt-75-320.jpg)

