論文紹介 Hyperkernel: Push-Button Verification of an OS Kernel (SOSP’17)
- 1. Hyperkernel: Push-Button Verification of an OS Kernel (SOSP’17) 2017–11–2
- 2. Hyperkernel: Push-Button Verification of an OS Kernel Luke Nelson, Helgi Sigurbjarnarson, Kaiyuan Zhang, Dylan Johnson, James Bornholt, Emina Torlak, and Xi Wang University of Washington SOSP’17 Verification Session URL http://locore.cs.washington.edu/hyperkernel/1 1 (2017–11–2 ) 1
- 3. OS • seL4 [Klein et al., 2009] • 1 C 11 / 20 2
- 4. OS • seL4 [Klein et al., 2009] • 1 C 11 / 20 • SMT • xv6 2
- 5. Appendix
- 6. SMT is ? 3 x > 0, y > 0, 3x = y, x2 = x + y (x = 4, y = 12) 3 3
- 7. Z3( SMT ) (SMT-LIB2 4 ) 1 (declare-const x Int) 2 (declare-const y Int) 3 (assert (> x 0)) 4 (assert (> y 0)) 5 (assert (= (∗ x 3) y)) 6 (assert (= (∗ x x) (+ x y))) 7 (check-sat) 8 (get-model) sat (model (define-fun y () Int 12) (define-fun x () Int 4) ) • (Python ) 4 SMT http://smtlib.cs.uiowa.edu/ 4
- 8. SMT • / • • • • . . . 5
- 9. SMT ∀x. P(x) • • ∃x. ¬P(x) unsat • 1 x = y + 2; 2 if (x >= 0) 3 x = 0; 4 else 5 x++; 6 assert(x <= 0); P ≡ (x0 = y0 + 2) ∧ (x1 = 0) ∧ (x2 = x0 + 1) ∧ ((x0 ≥ 0 ∧ x3 = x1) ∨(x0 < 0 ∧ x3 = x2)) Q ≡ x3 ≤ 0 ¬(P ⇒ Q) ≡ P ∧ ¬Q unsat 6
- 10. SMT (contd.) ∃x. P(x) • • ) • • unreachable • KLEE [Cadar et al., 2008] • White-box fuzzing (SAGE [Godefroid et al., 2012]) 7
- 11. SMT (contd.) ∀x. P(x) = Q(x) • • ∃x. ¬(P(x) = Q(x)) unsat • ) • STACK [Wang et al., 2013] • ) ROP SMT [Vanegue et al., 2012] 8
- 12. HyperKernel
- 13. HyperKernel • OS • 50 • • IPC 9
- 15. ∼Compile∼ Trusted Implementation LLVM IR LLVM C front-end Other code (kernel init, etc.) LLVM Compiler kernel image
- 16. OS 1. 11
- 17. OS 1. • ( ) 11
- 18. OS 1. → 11
- 19. OS 1. → Hyperkenel Interface . . .process1 process2 trap handler 11
- 20. OS 1. → • 11
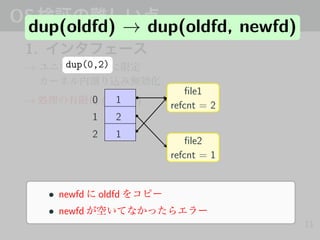
- 21. OS 1. → • 11 dup(2) systemcall dup(oldfd) 0 1 1 2 2 file1 refcnt = 1 file2 refcnt = 1
- 22. OS 1. → • 11 dup(2) systemcall dup(0) 0 1 1 2 2 file1 refcnt = 1 file2 refcnt = 1 1. fd
- 23. OS 1. → • 11 dup(2) systemcall dup(0) 0 1 1 2 2 1 file1 refcnt = 2 file2 refcnt = 1 1. fd 2. fd
- 24. OS 1. → • 11 dup(2) systemcall dup(0) 0 1 1 2 2 1 file1 refcnt = 2 file2 refcnt = 1 • fd • ( )
- 26. OS 1. → → (Finitize) 11 dup(oldfd) → dup(oldfd, newfd) dup(0,2) 0 1 1 2 2 1 file1 refcnt = 2 file2 refcnt = 1 • newfd oldfd • newfd
- 27. OS 1. → → (Finitize) 11 Finitize • • exokernel [Engler et al., 1995] • • • → SMT
- 31. OS 1. → → (Finitize) 2. → (VT-x) identity-mapping 11 Identity Mapping 0 1 2 3 4 5 . . . phys addr virt addr •
- 32. OS 1. → → (Finitize) 2. → (VT-x) identity-mapping 11 User Process Kernel VMX root ring0 Process VMX non-root ring0 VMExit • ring0 (Dune [Belay et al., 2012]) • VMExit • IDT ( )
- 34. OS 1. → → (Finitize) 2. → (VT-x) identity-mapping → HW (VT-d) 11
- 35. OS 1. → → (Finitize) 2. → (VT-x) identity-mapping → HW (VT-d) 3. C 11
- 36. OS 1. → → (Finitize) 2. → (VT-x) identity-mapping → HW (VT-d) 3. C • 11
- 37. OS 1. → → (Finitize) 2. → (VT-x) identity-mapping → HW (VT-d) 3. C → LLVM IR 11
- 38. 2 state-machine specification • • declarative specification (option) • state-machine specification 12
- 40. (dup) 1 def spec dup(state, oldfd, newfd): 2 pid = state.current 3 # Validation Condition 4 valid = And( 5 oldfd >= 0, oldfd < NR FDS, 6 state.proc fd table(pid, oldfd) < NR FILES, 7 newfd >= 0, newfd < NR FDS, 8 state.proc fd table(pid, newfd) >= NR FILES, 9 ) 10 11 # new state 12 new state = state.copy() 13 f = state.proc fd table(pid, oldfd) 14 new state.proc fd table[pid, newfd] = f 15 new state.proc nr fds(pid).inc(newfd) 16 new state.file nr fds(f).inc(pid, newfd) 17 18 return valid, new state 14
- 41. 1 class AbstractKernelState(object): 2 current = PidT() 3 proc fd table = Map((PidT, FdT), FileT) 4 proc nr fds = RefcntMap(PidT, SizeT) 5 file nr fds = RefcntMap(FileT, SizeT) 6 ... • • PidT FdT Z3 ( ) • Map Uninterpreted function 15
- 42. Declarative Specification • state machine specification • ) f = f FD file nr fds(f ) = |{(pid, fd)|proc fd table(pid, fd) = f }| 16
- 43. ∼dup ∼ C • current : PID (global) • procs[NR PROCS] : struct proc (global) • ofile[NR FDS] : FD ( proc ) • files[NR FILES] : (global) 17
- 44. ∼dup ∼ (contd.) global if (current > 0 && current < NR PROCS){...} ↓ Invariant • check rep invariant() invariant • invariant 18
- 45. Verifier 2 1 Refinement state-machine specification (refinement) 2 Crosscutting state-machine specification declarative specification 19
- 46. • s • x (e.g. ) • f (s, x) • fspec • fimpl • I(simpl ) ≡ invariant • sspec ∼ simpl ≡ sspec simpl • sspec ∼I simpl ≡ I(simpl ) ∧ sspec ∼ simpl • P ≡ declarative specification predicate 20
- 47. 1 ∀sspec, simpl , x. sspec ∼I simpl =⇒ fspec(sspec, x) ∼I fimpl (simpl , x) 2 ∀sspecx. P(sspec) =⇒ P(fspec(sspec, x)) 21
- 48. simpl sspec • abstract kernel data structure llvm global(’@current’) == state.current 22
- 49. fimpl LLVM IR • • • (e.g., 0 ) • LLVM IR SMT • • uninterapted function 23
- 50. LLVM IR 1 x = y + 2; 2 if (x >= 0) 3 x = 0; 4 else 5 x /= y; 1 %3 = load i32, i32∗ %2, align 4 2 %4 = add nsw i32 %3, 2 3 store i32 %4, i32∗ %1, align 4 4 %5 = load i32, i32∗ %1, align 4 5 %6 = icmp sge i32 %5, 0 6 br i1 %6, label %7, label %8 7 ; <label>:7: 8 store i32 0, i32∗ %1, align 4 9 br label %12 10 ; <label>:8: 11 %9 = load i32, i32∗ %2, align 4 12 %10 = load i32, i32∗ %1, align 4 13 %11 = sdiv i32 %10, %9 14 store i32 %11, i32∗ %1, align 4 15 br label %12 24
- 51. LLVM IR 1 x = y + 2; 2 if (x >= 0) 3 x = 0; 4 else 5 x /= y; ↓ 1 v2 = v1 + 2 2 assert(v2 >= 0) 3 v3 = 0 1 %3 = load i32, i32* %2, align 4 2 %4 = add nsw i32 %3, 2 3 store i32 %4, i32* %1, align 4 4 %5 = load i32, i32* %1, align 4 5 %6 = icmp sge i32 %5, 0 6 br i1 %6, label %7, label %8 7 ; <label>:7: 8 store i32 0, i32* %1, align 4 9 br label %12 10 ; <label>:8: 11 %9 = load i32, i32∗ %2, align 4 12 %10 = load i32, i32∗ %1, align 4 13 %11 = sdiv i32 %10, %9 14 store i32 %11, i32∗ %1, align 4 15 br label %12 25
- 52. LLVM IR 1 x = y + 2; 2 if (x >= 0) 3 x = 0; 4 else 5 x /= y; ↓ 1 v2 = v1 + 2 2 assert(v2 < 0) 3 // check v1 != 0 4 v3 /= v1 1 %3 = load i32, i32* %2, align 4 2 %4 = add nsw i32 %3, 2 3 store i32 %4, i32* %1, align 4 4 %5 = load i32, i32* %1, align 4 5 %6 = icmp sge i32 %5, 0 6 br i1 %6, label %7, label %8 7 ; $<$label$>$:7: 8 store i32 0, i32∗ %1, align 4 9 br label %12 10 ; <label>:8: 11 %9 = load i32, i32* %2, align 4 12 %10 = load i32, i32* %1, align 4 13 %11 = sdiv i32 %10, %9 14 store i32 %11, i32* %1, align 4 15 br label %12 26
- 53. 1 Ownership ∀o, o′ ∈ O. own(o) = own(o′ ) =⇒ o = o′ ↓ ∀o ∈ O. ownedby(own(o)) = o 27
- 54. 2 reference-counted shared ownership ∀r.refcnt(r) = |{o ∈ O|own(o) = r}| ↓ ∀r.∀0 ≤ i < |O|. own(π(r, i)) = r =⇒ i < refcnt(r) ∧ own(π(r, i)) ̸= r =⇒ i ≥ refcnt(r) π r object ( ) 28
- 55. • (init) • • (e1000 & lwIP stack) • Linux user emulation (syscall unmodified linux ) 29
- 56. • boot checker ( ) • stack checker • link checker 30
- 57. Limitation • /TCB • hyperkenel finite POSIX • CoW fork, (xv6 ) 31
- 58. HyperKernel • rust • Ownership • OS C • • xv6 • Dune 32
- 59. 7,419 C,asm invariant 197 C state-machine specification 804 Python declaratie specification 263 Python 10,025 C,asm 2,878 C++,Python • xv6 • 2 hyperkenel i7-7700K(8core) 15 33
- 60. xv6 xv6 Hyperkernel • 5 → Hyperkernel ( ) • 3 → Hyperkernel kernel 34
- 61. Linux Hyperkernel Hyp-Linux syscall 125 490 136 fault 2,917 615 722 appel1 637,562 459,522 519,235 appel2 623,062 452,611 482,596 • syscall hypercall • • Hyp-Linux Hyperkernel linux emulation 35
- 62. • SMT • python LLVM IR SMT • xv6 xv6 36
- 63. • Z3 • • • LLVM IR SMT 37
- 64. /
- 65. Coq Isabelle/HOL • Coq Isabelle/HOL Proof Asistant • ( ) • • SMT Coq • Coq • Coq • Ocaml or Haskell 38
- 66. Coq Jitk [Wang et al., 2014] • BPF Jit Coq (+CompCert) • Coq Ocaml • → BPF → CompCert → • CompCert [Leroy, 2009] • CompCert C • CompCert C Coq 39
- 67. C .. • C • C Proof Asistant • seL4 [Klein et al., 2009] 40
- 68. • • • SMT • “ ” ( ) • hyperkernel ( ) 41
- 69. OS • seL4 [Klein et al., 2009] • Isabelle/HOL • microkernel on ARM • ExpressOS [Mai et al., 2013] • Dafny • Ironclad [Hawblitzel et al., 2014] • Dafny • CertikOS [Gu et al., 2016] • Coq • concurrent OS on x86 42
- 70. • Hyper-V [Leinenbach and Santen, 2009] • ( ?) • MinVisor [McCoyd et al., 2013] • Virtual CPU Validation [Amit et al., 2015] • HW validation tool hypervisor • VCPU • 43
- 71. SOSP’17 • Pensieve [Zhang et al., 2017] • • SMT • ARC [Gember-Jacobson et al., 2017] • configuration error MaxSAT • Komodo [Ferraiuolo et al., 2017] • SGX ( ) • Dafny(Z3) • BLITZ [Schlaipfer et al., 2017] • Sketch [Solar-Lezama et al., 2006] SQL 44
- 72. Appendix
- 74. • • • • • • • . . . / 45
- 76. (Theorem Proving) • Hoare Logic • • ( etc) • • Coq, Isabelle/HOL, Lean, . . . • VCC, Frama-C, Dafny, . . . 47
- 77. (Model Checking) • ( ) (Finite State Machine) • • ( ) • : • SPIN ,CBMC, . . . 48
- 79. SAT SMT
- 81. SAT 1 (x ∨ y) ∧ ¬x (x = false, y = true) 2 (x ∨ ¬y) ∧ (¬x ∨ y) ∧ (¬x ∨ ¬y) ∧ (x ∨ y) • NP • • : 1) 2) 51
- 82. SAT DPLL • Davis-Putnam-Logemann-Loveland • • CNF (Tseitin ) 1. Unit Propagation ( ) 2. 3. 52
- 83. Tseitin Encoding • equi-satisfiable CNF • φ[a ∧ b] φ[c] ∧ (c ↔ a ∧ b) CDCL • Conflict-Driven Clause Learning • DPLL • • 53
- 85. SMT • Satisfiable Modulo Theories • • (theory) • SAT x > 0, y > 0, 3x = y, x2 = x + y (x = 4, y = 12) 55
- 86. SMT • / • ( ) • Equality and Uninterpreted Functiion (EUF) • • . . . (Nelson-Oppen Theory Combination) 56
- 87. • Linear Integer Arithmetics (LIA) • NP • branch and cut / omega test • Linear Real Arithmetics (LRA) • • General Simplex ( ) 57
- 88. • • NP • Bit blasting SAT 58
- 89. Equalty and Uninterpreted Functions =, x, y, . . . , f , g, . . . , p, q, . . . • ∀x. x = x • ∀x, y. x = y → y = x • ∀x, y, z. x = y ∧ y = z → x = z • ∀x1, . . . , xn, y1, . . . , yn. (x1 = y1 ∧ . . . xn = yn) → (f (x1, . . . , xn) = f (y1, . . . , yn)) • ∀x1, . . . , xn, y1, . . . , yn. (x1 = y1 ∧ . . . xn = yn) → (p(x1, . . . , xn) ↔ p(y1, . . . , yn)) 59
- 90. read, write, =, x, y, z, . . . • ∀i. read(write(a, i, v), i) = v • ∀i, j. ¬(i = j) → read(write(a, i, v), j) = read(a, j)) • (∀i. read(a, i) = read(b, i)) → a = b 60
- 91. SMT DPLL (T) • CNF : φ = φ0 ∧ φ1 ∧ . . . ∧ φn • T • • DPLL • DPLL Nelson-Oppen 61
- 92. SMT Z3 https://github.com/Z3Prover/z3 CVC4 http://cvc4.cs.stanford.edu/web/ MathSAT http://mathsat.fbk.eu/ Boolector http://fmv.jku.at/boolector/ Yices2 http://yices.csl.sri.com/ 62
- 93. Z3 • SMT [De Moura and Bjørner, 2008] • • sat ( ; ) • unsat ( ) • unkown ( ; Z3 ) • SMT • SAT 63
- 94. Z3 (SMT-LIB2 5 ) 1 (declare-const x Int) 2 (declare-const y Int) 3 (assert (> x 0)) 4 (assert (> y 0)) 5 (assert (= (∗ x 3) y)) 6 (assert (= (∗ x x) (+ x y))) 7 (check-sat) 8 (get-model) sat (model (define-fun y () Int 12) (define-fun x () Int 4) ) • (Python ) 5 SMT http://smtlib.cs.uiowa.edu/ 64
- 95. Z3 ? → Hoare Logic 65
- 97. Hoare Logic • C.A.R Hoare [Hoare, 1969] • {P}S{Q} P S Q S P Q 66
- 98. Hoare Logic S ::= x := E | S1; S2 | if C then S1 else S2 | while C do S end 67
- 99. {P} skip {P} {Q[E/x]} x := E {Q} {P1}S{Q1} P ⇒ P1 Q1 ⇒ Q {P}S{Q} {P}S1{R} {R}S2{Q} {P}S1; S2{Q} ) {P ∧ C}S1{Q} {P ∧ ¬C}S2{Q} {P} if C then S1 else S2 {Q} {P ∧ C}S{P} {P} while C do S end {P ∧ ¬C} A B 68
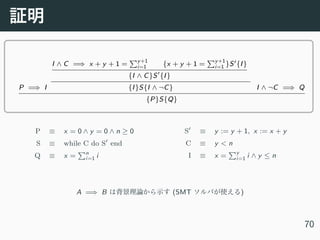
- 100. 1 {x = 0, y = 0, n >= 0} 2 while (y < n) do 3 y := y + 1 4 x := x + y 5 end 6 {x = n i=1 i} 69
- 101. P =⇒ I I ∧ C =⇒ x + y + 1 = y+1 i=1 {x + y + 1 = y+1 i=1 }S′{I} {I ∧ C}S′ {I} {I}S{I ∧ ¬C} I ∧ ¬C =⇒ Q {P}S{Q} P ≡ x = 0 ∧ y = 0 ∧ n ≥ 0 S ≡ while C do S′ end Q ≡ x = n i=1 i S′ ≡ y := y + 1, x := x + y C ≡ y < n I ≡ x = y i=1 i ∧ y ≤ n A =⇒ B (SMT ) 70
- 102. SMT : P S Q unsat → 6 Z3 ; (assert ...) ; (assert (not (...)) (check-sat) 6 P ⇒ Q P ⇒ Q = ¬P ∨ Q ¬(P ⇒ Q) = P ∧ ¬Q 71
- 103. {x < 0} x := x + 10 {x < 10} (declare-const x Int) (assert (< x 0)) (assert (not (< (+ x 10) 10))) (check-sat) if {x < 10} if x < 5 then x := 5 else x := x + 1 {x ≥ 5, x ≤ 10} (declare-const x Int) (assert (< x 10)) (assert (not (and (>= (ite (< x 5) 5 (+ x 1)) 5) (<= (ite (< x 5) 5 (+ x 1)) 10) ))) (check-sat) 72
- 104. while {x ≤ 0} while x < 0 do x := x + 1 end {x ≤ 0 ∧ ¬x < 0} (declare-const x Int) (assert (and (<= x 0) (< x 0))) (assert (not (<= (+ x 1) 0))) (check-sat) Recall: while {P ∧ C}S{P} {P} while C do S end {P ∧ ¬C} • P ( x ≤ 0) • 73
- 105. 7 Verification Condition Generator (VCG) SMT Solver • ( ) 7 74
- 106. Verification Condition Generator • SMT • {P}S{Q} {P}S1{R1}, {R1}S2{R2}, . . . , {Rn1 }Sn2 {Q} (Proof Obligations) • weakest liberal precondition Weakest (Liberal) Precondition [Dijkstra, 1976] • {P′ }S{Q} P′ P′ ⇒ P P Weakest Liberal Precondition wlp(S, Q) • {P}S{Q} P ⇒ wlp(S, Q) valid 75
- 107. wlp • wlp(skip, Q) = Q • wlp(x := E, Q) = Q[E/x] • wlp(S1; S2, Q) = wlp(S1, wlp(S2, Q)) • wlp(if C then S1 else S2, Q) = (C ⇒ wlp(S1, Q)) ∧ (¬C ⇒ wlp(S2, Q)) • wlp(while C do S end, Q) = ✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿ if C then wlp(S, wlp(while C do S end, Q)) else Q while wlp → approximate wlp (awp) 76
- 108. awp • awp(skip, Q) = Q • awp(x := E, Q) = Q[E/x] • awp(S1; S2, Q) = awp(S1, awp(S2, Q)) • awp(if C then S1 else S2, Q) = (C ⇒ awp(S1, Q)) ∧ (¬C ⇒ awp(S2, Q)) • awp(while C do {I} S end, Q) = I while awp(S, Q) = wlp(S, Q) I ( ) 77
- 109. VCG VC(S, Q) ∧ (P ⇒ awp(S, Q)) • VC(skip, Q) = true • VC(x := E, Q) = true • VC(S1; S2, Q) = VC(S1) ∧ VC(S1, awp(S2, Q)) • VC(if C then S1 else S2, Q) = VC(S1, Q) ∧ VC(S1, Q) • VC(while C do {I} S end, Q) = (I ∧ C ⇒ awp(S, I)) ∧ VC(S, I) ∧ (I ∧ ¬C ⇒ Q) while (1) P ⇒ I, (2) I ∧ C ⇒ wlp(C, I), (3) I ∧ ¬C ⇒ Q 78
- 110. Strongest postconditions • weakest precondition strongest postcondition (sp) 79
- 111. Hoare ( ) • • Separation Logic [Reynolds, 2002] • • [Hoare, 1975] • Owicki-Gries reasoning [Owicki and Gries, 1976] 80
- 112. • VCG (Intermediate Verification Language) Source IVL Verification Condition Solver/ Prover IVL • Boogie (Microsoft) [Leino, 2008] • VCC [Cohen et al., 2009], Dafny [Leino and Moskal, 2013], Spec# [Leino et al., 2006], SMACK [Rakamari´c et al., 2014], . . . • Why3 (LRI, France) [Bobot et al., 2011] • Frama-C [Kirchner et al., 2015], Krakatoa [March´e et al., 2009], SPARK 2014 [Dross et al., 2014], . . . 81
- 113. Boogie Boogie Z3 SMT Lib Coq Isabelle/HOL ... VCC (C) Spec# (C#) Dafny SMACK (LLVM IR) ... • Z3 • 82
- 114. Why3 Why3 Z3 SMT Lib Coq Isabelle/HOL ... Frama-C (C) Jessie Krakatoa (Java) SPARK 2014 ... • ML • Coq 83
- 115. VCC 1 #include <vcc.h> 2 #include <limits.h> 3 4 unsigned lsearch(int elt, int ∗ar, unsigned sz) 5 (requires thread local array(ar, sz)) 6 (ensures result != UINT MAX ==> ar[result] == elt) 7 (ensures forall unsigned i; i < sz && i < result ==> ar[i] != elt) 8 { 9 unsigned i; 10 for (i = 0; i < sz; i++) 11 (invariant forall unsigned j; j < i ==> ar[j] != elt) 12 { 13 if (ar[i] == elt) return i; 14 } 15 16 return UINT MAX; 17 } • https://rise4fun.com/Vcc/lsearch • ( ) 84
- 116. Dafny 1 method Add(x: int, y: int) returns (r: int) 2 requires 0 <= x && 0 <= y 3 ensures r == 2∗x + y 4 { 5 r := 2∗x; 6 var n := y; 7 while n != 0 8 invariant r == 2∗x+y−n && 0 <= n 9 { 10 r := r + 1; 11 n := n − 1; 12 } 13 } • https://rise4fun.com/Dafny/Add • Dafny C# BoogieAsm • : ExpressOS [Mai et al., 2013], Ironclad apps [Hawblitzel et al., 2014], IronFleet[Hawblitzel et al., 2015], Komodo [Ferraiuolo et al., 2017], Vale [Bond et al., 2017] 85
- 117. Frama-C 1 size type find(const value type∗ a, size type n, value type val) 2 { 3 /∗@ 4 loop invariant 0 <= i <= n; 5 loop invariant forall integer k; 0 <= k < i ==> a[k] != val; 6 loop assigns i; 7 loop variant n−i; 8 ∗/ 9 for (size type i = 0; i < n; i++) { 10 if (a[i] == val) { 11 return i; 12 } 13 } 14 return n; 15 } • ACSL (ANSI/ISO C Specification Language) 86
- 118. Z3
- 119. Z3 Python git clone https://github.com/Z3Prover/z3 cd z3 python scripts/mk make.py −−python −−pypkgdir=/path/to/lib/python3.5/site−packages/ −−prefix=/path/to/z3/ cd build make make install Z3 /path/to/z3 −smt2 a.smt 87
- 120. Z3 in Python from z3 import ∗ x = Int(’x’) y = Int(’y’) solve(x > 0, y > 0, 3∗x == y, x∗x == x + y) # [y = 12, x = 4] • • http://ericpony.github.io/z3py-tutorial/guide-examples.htm • http: //ericpony.github.io/z3py-tutorial/advanced-examples.htm 88
- 122. • 1994 • http://ws.cs.kobe-u.ac.jp/~masa-n/ses2011/ ses2011_tutorial4.pdf • Washington 18 : https: //courses.cs.washington.edu/courses/cse507/17w • Washington 2: https://courses.cs. washington.edu/courses/cse599w/16sp/ • Harvard : https: //www.seas.harvard.edu/courses/cs252/2017fa/ • UCSB : http://www.cs.ucsb.edu/ ~bultan/courses/267/lectures/lectures.html 8 89
- 123. Amit, N., Tsafrir, D., Schuster, A., Ayoub, A., and Shlomo, E. (2015). Virtual cpu validation. In Proceedings of the 25th Symposium on Operating Systems Principles, SOSP ’15, pages 311–327, New York, NY, USA. ACM. Belay, A., Bittau, A., Mashtizadeh, A., Terei, D., Mazi`eres, D., and Kozyrakis, C. (2012). Dune: Safe user-level access to privileged CPU features. In Presented as part of the 10th USENIX Symposium on Operating Systems Design and Implementation (OSDI 12), pages 335–348, Hollywood, CA. USENIX. 90
- 124. (contd.) Bobot, F., Filliˆatre, J.-C., March´e, C., and Paskevich, A. (2011). Why3: Shepherd your herd of provers. In Boogie 2011: First International Workshop on Intermediate Verification Languages, pages 53–64, Wroclaw, Poland. https://hal.inria.fr/hal-00790310. Bond, B., Hawblitzel, C., Kapritsos, M., Leino, R., Lorch, J., Parno, B., Rane, A., Setty, S., and Thompson, L. (2017). Vale: Verifying high-performance cryptographic assembly code. In Proceedings of the USENIX Security Symposium. USENIX. 91
- 125. (contd.) Cadar, C., Dunbar, D., and Engler, D. (2008). Klee: Unassisted and automatic generation of high-coverage tests for complex systems programs. In Proceedings of the 8th USENIX Conference on Operating Systems Design and Implementation, OSDI’08, pages 209–224, Berkeley, CA, USA. USENIX Association. Cohen, E., Dahlweid, M., Hillebrand, M., Leinenbach, D., Moskal, M., Santen, T., Schulte, W., and Tobies, S. (2009). Vcc: A practical system for verifying concurrent c. In International Conference on Theorem Proving in Higher Order Logics, pages 23–42. Springer. 92
- 126. (contd.) De Moura, L. and Bjørner, N. (2008). Z3: An efficient SMT solver. Tools and Algorithms for the Construction and Analysis of Systems, pages 337–340. Dijkstra, E. W. (1976). A discipline of programming. Prentice-Hall, Englewood Cliffs, NJ. Dross, C., Efstathopoulos, P., Lesens, D., Mentr´e, D., and Moy, Y. (2014). Rail, space, security: Three case studies for spark 2014. Engler, D. R., Kaashoek, M. F., et al. (1995). Exokernel: An operating system architecture for application-level resource management, volume 29. ACM. 93
- 127. (contd.) Ferraiuolo, A., Baumann, A., Hawblitzel, C., and Parno, B. (2017). Komodo: Using verification to disentangle secure-enclave hardware from software. In Proceedings of the 26th Symposium on Operating Systems Principles, SOSP ’17, pages 287–305, New York, NY, USA. ACM. Gember-Jacobson, A., Akella, A., Mahajan, R., and Liu, H. H. (2017). Automatically repairing network control planes using an abstract representation. In Proceedings of the 26th Symposium on Operating Systems Principles, SOSP ’17, pages 359–373, New York, NY, USA. ACM. Godefroid, P., Levin, M. Y., and Molnar, D. (2012). Sage: Whitebox fuzzing for security testing. Queue, 10(1):20:20–20:27. 94
- 128. (contd.) Gu, R., Shao, Z., Chen, H., Wu, X. N., Kim, J., Sj¨oberg, V., and Costanzo, D. (2016). Certikos: An extensible architecture for building certified concurrent OS kernels. In 12th USENIX Symposium on Operating Systems Design and Implementation (OSDI 16), pages 653–669, GA. USENIX Association. Hawblitzel, C., Howell, J., Kapritsos, M., Lorch, J., Parno, B., Roberts, M. L., Setty, S., and Zill, B. (2015). Ironfleet: Proving practical distributed systems correct. In Proceedings of the ACM Symposium on Operating Systems Principles (SOSP). ACM Association for Computing Machinery. 95
- 129. (contd.) Hawblitzel, C., Howell, J., Lorch, J. R., Narayan, A., Parno, B., Zhang, D., and Zill, B. (2014). Ironclad apps: End-to-end security via automated full-system verification. In Proceedings of the 11th USENIX Conference on Operating Systems Design and Implementation, OSDI’14, pages 165–181, Berkeley, CA, USA. USENIX Association. Hoare, C. A. R. (1969). An axiomatic basis for computer programming. Communications of the ACM, 12(10):576–580. Hoare, C. A. R. (1975). Parallel programming: An axiomatic approach. Comput. Lang., 1(2):151–160. 96
- 130. (contd.) Kirchner, F., Kosmatov, N., Prevosto, V., Signoles, J., and Yakobowski, B. (2015). Frama-c: a software analysis perspective. Formal Aspects of Computing, 27(3):573–609. Klein, G., Elphinstone, K., Heiser, G., Andronick, J., Cock, D., Derrin, P., Elkaduwe, D., Engelhardt, K., Kolanski, R., Norrish, M., et al. (2009). seL4: Formal verification of an OS kernel. In Proceedings of the ACM SIGOPS 22nd symposium on Operating systems principles, pages 207–220. ACM. Leinenbach, D. and Santen, T. (2009). Verifying the microsoft hyper-v hypervisor with vcc. In Proceedings of the 2Nd World Congress on Formal Methods, FM ’09, pages 806–809, Berlin, Heidelberg. Springer-Verlag. 97
- 131. (contd.) Leino, R. (2008). This is boogie 2. Microsoft Research. Leino, R. et al. (2006). Building a program verifier. Microsoft Research. Leino, R. and Moskal, M. (2013). Co-induction simply: Automatic co-inductive proofs in a program verifier. Technical report. Leroy, X. (2009). Formal verification of a realistic compiler. Commun. ACM, 52(7):107–115. 98
- 132. (contd.) Mai, H., Pek, E., Xue, H., King, S. T., and Madhusudan, P. (2013). Verifying security invariants in expressos. In Proceedings of the Eighteenth International Conference on Architectural Support for Programming Languages and Operating Systems, ASPLOS ’13, pages 293–304, New York, NY, USA. ACM. March´e, C. et al. (2009). The krakatoa tool for deductive verification of java programs. McCoyd, M., Krug, R. B., Goel, D., Dahlin, M., and Young, W. (2013). Building a hypervisor on a formally verifiable protection layer. In System Sciences (HICSS), 2013 46th Hawaii International Conference on, pages 5069–5078. IEEE. Owicki, S. and Gries, D. (1976). An axiomatic proof technique for parallel programs i. Acta Inf., 6(4):319–340. 99
- 133. (contd.) Rakamari´c, Z. et al. (2014). SMACK: Decoupling source language details from verifier implementations. In Biere, A. and Bloem, R., editors, Proceedings of the 26th International Conference on Computer Aided Verification (CAV), volume 8559 of Lecture Notes in Computer Science, pages 106–113. Springer. Reynolds, J. C. (2002). Separation logic: A logic for shared mutable data structures. In Logic in Computer Science, 2002. Proceedings. 17th Annual IEEE Symposium on, pages 55–74. IEEE. Schlaipfer, M., Rajan, K., Lal, A., and Samak, M. (2017). Optimizing big-data queries using program synthesis. In Proceedings of the 26th Symposium on Operating Systems Principles, SOSP ’17, pages 631–646, New York, NY, USA. ACM. 100
- 134. (contd.) Sigurbjarnarson, H., Bornholt, J., Torlak, E., and Wang, X. (2016). Push-Button Verification of File Systems via Crash Refinement. In 12th USENIX Symposium on Operating Systems Design and Implementation (OSDI 16), pages 1–16, Savannah, GA. USENIX Association. Solar-Lezama, A., Tancau, L., Bodik, R., Seshia, S., and Saraswat, V. (2006). Combinatorial sketching for finite programs. ACM SIGOPS Operating Systems Review, 40(5):404–415. Vanegue, J., Heelan, S., and Rolles, R. (2012). Smt solvers for software security. In Proceedings of the 6th USENIX Conference on Offensive Technologies, WOOT’12, pages 9–9, Berkeley, CA, USA. USENIX Association. 101
- 135. (contd.) Wang, X., Lazar, D., Zeldovich, N., Chlipala, A., and Tatlock, Z. (2014). Jitk: A trustworthy in-kernel interpreter infrastructure. In Proceedings of the 11th USENIX Conference on Operating Systems Design and Implementation, OSDI’14, pages 33–47, Berkeley, CA, USA. USENIX Association. Wang, X., Zeldovich, N., Kaashoek, M. F., and Solar-Lezama, A. (2013). Towards optimization-safe systems: Analyzing the impact of undefined behavior. In Proceedings of the Twenty-Fourth ACM Symposium on Operating Systems Principles, SOSP ’13, pages 260–275, New York, NY, USA. ACM. 102
- 136. (contd.) Zhang, Y., Makarov, S., Ren, X., Lion, D., and Yuan, D. (2017). Pensieve: Non-intrusive failure reproduction for distributed systems using the event chaining approach. In Proceedings of the 26th Symposium on Operating Systems Principles, SOSP ’17, pages 19–33, New York, NY, USA. ACM. 103


![OS
• seL4 [Klein et al., 2009]
• 1 C 11 /
20
2](https://image.slidesharecdn.com/hyperkernel-171102110014/85/Hyperkernel-Push-Button-Verification-of-an-OS-Kernel-SOSP-17-3-320.jpg)
![OS
• seL4 [Klein et al., 2009]
• 1 C 11 /
20
• SMT
• xv6
2](https://image.slidesharecdn.com/hyperkernel-171102110014/85/Hyperkernel-Push-Button-Verification-of-an-OS-Kernel-SOSP-17-4-320.jpg)





![SMT (contd.)
∃x. P(x)
•
• )
•
• unreachable
• KLEE [Cadar et al., 2008]
• White-box fuzzing
(SAGE [Godefroid et al., 2012])
7](https://image.slidesharecdn.com/hyperkernel-171102110014/85/Hyperkernel-Push-Button-Verification-of-an-OS-Kernel-SOSP-17-10-320.jpg)
![SMT (contd.)
∀x. P(x) = Q(x)
•
• ∃x. ¬(P(x) = Q(x)) unsat
• )
• STACK [Wang et al., 2013]
• ) ROP
SMT
[Vanegue et al., 2012]
8](https://image.slidesharecdn.com/hyperkernel-171102110014/85/Hyperkernel-Push-Button-Verification-of-an-OS-Kernel-SOSP-17-11-320.jpg)














![OS
1.
→
→ (Finitize)
11
Finitize
•
• exokernel [Engler et al., 1995]
•
•
•
→ SMT](https://image.slidesharecdn.com/hyperkernel-171102110014/85/Hyperkernel-Push-Button-Verification-of-an-OS-Kernel-SOSP-17-27-320.jpg)




![OS
1.
→
→ (Finitize)
2.
→ (VT-x)
identity-mapping
11
User Process
Kernel
VMX root
ring0
Process
VMX non-root
ring0
VMExit
• ring0 (Dune [Belay et al., 2012])
• VMExit
• IDT
( )](https://image.slidesharecdn.com/hyperkernel-171102110014/85/Hyperkernel-Push-Button-Verification-of-an-OS-Kernel-SOSP-17-32-320.jpg)







![(dup)
1 def spec dup(state, oldfd, newfd):
2 pid = state.current
3 # Validation Condition
4 valid = And(
5 oldfd >= 0, oldfd < NR FDS,
6 state.proc fd table(pid, oldfd) < NR FILES,
7 newfd >= 0, newfd < NR FDS,
8 state.proc fd table(pid, newfd) >= NR FILES,
9 )
10
11 # new state
12 new state = state.copy()
13 f = state.proc fd table(pid, oldfd)
14 new state.proc fd table[pid, newfd] = f
15 new state.proc nr fds(pid).inc(newfd)
16 new state.file nr fds(f).inc(pid, newfd)
17
18 return valid, new state
14](https://image.slidesharecdn.com/hyperkernel-171102110014/85/Hyperkernel-Push-Button-Verification-of-an-OS-Kernel-SOSP-17-40-320.jpg)


![∼dup ∼
C
• current : PID (global)
• procs[NR PROCS] : struct proc (global)
• ofile[NR FDS] : FD ( proc )
• files[NR FILES] : (global)
17](https://image.slidesharecdn.com/hyperkernel-171102110014/85/Hyperkernel-Push-Button-Verification-of-an-OS-Kernel-SOSP-17-43-320.jpg)






















![Coq
Jitk [Wang et al., 2014]
• BPF Jit Coq (+CompCert)
• Coq Ocaml
• → BPF
→ CompCert →
•
CompCert [Leroy, 2009]
• CompCert C
• CompCert C Coq
39](https://image.slidesharecdn.com/hyperkernel-171102110014/85/Hyperkernel-Push-Button-Verification-of-an-OS-Kernel-SOSP-17-66-320.jpg)
![C ..
• C
• C Proof Asistant
• seL4 [Klein et al., 2009]
40](https://image.slidesharecdn.com/hyperkernel-171102110014/85/Hyperkernel-Push-Button-Verification-of-an-OS-Kernel-SOSP-17-67-320.jpg)

![OS
• seL4 [Klein et al., 2009]
• Isabelle/HOL
• microkernel on ARM
• ExpressOS [Mai et al., 2013]
• Dafny
• Ironclad [Hawblitzel et al., 2014]
• Dafny
• CertikOS [Gu et al., 2016]
• Coq
• concurrent OS on x86
42](https://image.slidesharecdn.com/hyperkernel-171102110014/85/Hyperkernel-Push-Button-Verification-of-an-OS-Kernel-SOSP-17-69-320.jpg)
![• Hyper-V [Leinenbach and Santen, 2009]
• ( ?)
• MinVisor [McCoyd et al., 2013]
• Virtual CPU Validation [Amit et al., 2015]
• HW validation tool hypervisor
• VCPU
•
43](https://image.slidesharecdn.com/hyperkernel-171102110014/85/Hyperkernel-Push-Button-Verification-of-an-OS-Kernel-SOSP-17-70-320.jpg)
![SOSP’17
• Pensieve [Zhang et al., 2017]
•
• SMT
• ARC [Gember-Jacobson et al., 2017]
• configuration error
MaxSAT
• Komodo [Ferraiuolo et al., 2017]
• SGX ( )
• Dafny(Z3)
• BLITZ [Schlaipfer et al., 2017]
• Sketch [Solar-Lezama et al., 2006] SQL
44](https://image.slidesharecdn.com/hyperkernel-171102110014/85/Hyperkernel-Push-Button-Verification-of-an-OS-Kernel-SOSP-17-71-320.jpg)











![Tseitin Encoding
• equi-satisfiable CNF
• φ[a ∧ b] φ[c] ∧ (c ↔ a ∧ b)
CDCL
• Conflict-Driven Clause Learning
• DPLL
•
•
53](https://image.slidesharecdn.com/hyperkernel-171102110014/85/Hyperkernel-Push-Button-Verification-of-an-OS-Kernel-SOSP-17-83-320.jpg)









![Z3
• SMT
[De Moura and Bjørner, 2008]
•
• sat ( ; )
• unsat ( )
• unkown ( ; Z3 )
• SMT
• SAT
63](https://image.slidesharecdn.com/hyperkernel-171102110014/85/Hyperkernel-Push-Button-Verification-of-an-OS-Kernel-SOSP-17-93-320.jpg)



![Hoare Logic
• C.A.R Hoare
[Hoare, 1969]
•
{P}S{Q}
P S
Q S P Q
66](https://image.slidesharecdn.com/hyperkernel-171102110014/85/Hyperkernel-Push-Button-Verification-of-an-OS-Kernel-SOSP-17-97-320.jpg)

![{P} skip {P}
{Q[E/x]} x := E {Q}
{P1}S{Q1} P ⇒ P1 Q1 ⇒ Q
{P}S{Q}
{P}S1{R} {R}S2{Q}
{P}S1; S2{Q}
)
{P ∧ C}S1{Q} {P ∧ ¬C}S2{Q}
{P} if C then S1 else S2 {Q}
{P ∧ C}S{P}
{P} while C do S end {P ∧ ¬C}
A
B
68](https://image.slidesharecdn.com/hyperkernel-171102110014/85/Hyperkernel-Push-Button-Verification-of-an-OS-Kernel-SOSP-17-99-320.jpg)





![Verification Condition Generator
• SMT
• {P}S{Q}
{P}S1{R1}, {R1}S2{R2}, . . . , {Rn1 }Sn2 {Q}
(Proof Obligations)
• weakest liberal precondition
Weakest (Liberal) Precondition [Dijkstra, 1976]
• {P′
}S{Q} P′
P′
⇒ P P
Weakest Liberal Precondition wlp(S, Q)
• {P}S{Q} P ⇒ wlp(S, Q)
valid
75](https://image.slidesharecdn.com/hyperkernel-171102110014/85/Hyperkernel-Push-Button-Verification-of-an-OS-Kernel-SOSP-17-106-320.jpg)
![wlp
• wlp(skip, Q) = Q
• wlp(x := E, Q) = Q[E/x]
• wlp(S1; S2, Q) = wlp(S1, wlp(S2, Q))
• wlp(if C then S1 else S2, Q) =
(C ⇒ wlp(S1, Q)) ∧ (¬C ⇒ wlp(S2, Q))
• wlp(while C do S end, Q) =
✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿✿
if C then wlp(S, wlp(while C do S end, Q)) else Q
while wlp
→ approximate wlp (awp)
76](https://image.slidesharecdn.com/hyperkernel-171102110014/85/Hyperkernel-Push-Button-Verification-of-an-OS-Kernel-SOSP-17-107-320.jpg)
![awp
• awp(skip, Q) = Q
• awp(x := E, Q) = Q[E/x]
• awp(S1; S2, Q) = awp(S1, awp(S2, Q))
• awp(if C then S1 else S2, Q) =
(C ⇒ awp(S1, Q)) ∧ (¬C ⇒ awp(S2, Q))
• awp(while C do {I} S end, Q) = I
while awp(S, Q) = wlp(S, Q)
I ( )
77](https://image.slidesharecdn.com/hyperkernel-171102110014/85/Hyperkernel-Push-Button-Verification-of-an-OS-Kernel-SOSP-17-108-320.jpg)


![Hoare
( )
•
• Separation Logic [Reynolds, 2002]
•
• [Hoare, 1975]
• Owicki-Gries reasoning [Owicki and Gries, 1976]
80](https://image.slidesharecdn.com/hyperkernel-171102110014/85/Hyperkernel-Push-Button-Verification-of-an-OS-Kernel-SOSP-17-111-320.jpg)
![• VCG
(Intermediate Verification Language)
Source IVL
Verification
Condition
Solver/
Prover
IVL
• Boogie (Microsoft) [Leino, 2008]
• VCC [Cohen et al., 2009], Dafny [Leino and Moskal, 2013],
Spec# [Leino et al., 2006], SMACK [Rakamari´c et al., 2014], . . .
• Why3 (LRI, France) [Bobot et al., 2011]
• Frama-C [Kirchner et al., 2015], Krakatoa [March´e et al., 2009],
SPARK 2014 [Dross et al., 2014], . . .
81](https://image.slidesharecdn.com/hyperkernel-171102110014/85/Hyperkernel-Push-Button-Verification-of-an-OS-Kernel-SOSP-17-112-320.jpg)


![VCC
1 #include <vcc.h>
2 #include <limits.h>
3
4 unsigned lsearch(int elt, int ∗ar, unsigned sz)
5 (requires thread local array(ar, sz))
6 (ensures result != UINT MAX ==> ar[result] == elt)
7 (ensures forall unsigned i; i < sz && i < result ==> ar[i]
!= elt)
8 {
9 unsigned i;
10 for (i = 0; i < sz; i++)
11 (invariant forall unsigned j; j < i ==> ar[j] != elt)
12 {
13 if (ar[i] == elt) return i;
14 }
15
16 return UINT MAX;
17 }
• https://rise4fun.com/Vcc/lsearch
• ( )
84](https://image.slidesharecdn.com/hyperkernel-171102110014/85/Hyperkernel-Push-Button-Verification-of-an-OS-Kernel-SOSP-17-115-320.jpg)
![Dafny
1 method Add(x: int, y: int) returns (r: int)
2 requires 0 <= x && 0 <= y
3 ensures r == 2∗x + y
4 {
5 r := 2∗x;
6 var n := y;
7 while n != 0
8 invariant r == 2∗x+y−n && 0 <= n
9 {
10 r := r + 1;
11 n := n − 1;
12 }
13 }
• https://rise4fun.com/Dafny/Add
• Dafny C# BoogieAsm
• : ExpressOS [Mai et al., 2013], Ironclad
apps [Hawblitzel et al., 2014], IronFleet[Hawblitzel et al., 2015],
Komodo [Ferraiuolo et al., 2017], Vale [Bond et al., 2017]
85](https://image.slidesharecdn.com/hyperkernel-171102110014/85/Hyperkernel-Push-Button-Verification-of-an-OS-Kernel-SOSP-17-116-320.jpg)
![Frama-C
1 size type find(const value type∗ a, size type n, value type val)
2 {
3 /∗@
4 loop invariant 0 <= i <= n;
5 loop invariant forall integer k; 0 <= k < i ==> a[k] != val;
6 loop assigns i;
7 loop variant n−i;
8 ∗/
9 for (size type i = 0; i < n; i++) {
10 if (a[i] == val) {
11 return i;
12 }
13 }
14 return n;
15 }
• ACSL (ANSI/ISO C Specification Language)
86](https://image.slidesharecdn.com/hyperkernel-171102110014/85/Hyperkernel-Push-Button-Verification-of-an-OS-Kernel-SOSP-17-117-320.jpg)


![Z3 in Python
from z3 import ∗
x = Int(’x’)
y = Int(’y’)
solve(x > 0, y > 0, 3∗x == y, x∗x == x + y)
# [y = 12, x = 4]
•
• http://ericpony.github.io/z3py-tutorial/guide-examples.htm
• http:
//ericpony.github.io/z3py-tutorial/advanced-examples.htm
88](https://image.slidesharecdn.com/hyperkernel-171102110014/85/Hyperkernel-Push-Button-Verification-of-an-OS-Kernel-SOSP-17-120-320.jpg)















