iOS Application Penetation Test
- 1. iOS Application Penetration Testing Attack & Defense Author: JongWon Kim [email protected]
- 2. Angenda • What’s the iOS App? • Monoculture – Code Signing – Sandboxing – Encryption • The Perspective of Pen Tester – Compile Option – URLScheme – Insecure Database – Runtime Analysis – Transport Security
- 3. What’s the iOS App? • Development in Xcode – You don’t have to buy a Mac since this is for BlackBox Assessment • Applications written primarily in Objective-C Compiled(ARM) Executable – Need to background about the structure of Objective-C • Encrypted Executable • Installed by “mobile” user – Compared to each Android apps which use different UID/GID
- 4. Angenda • What’s the iOS App? • Monoculture – Code Signing – Sandboxing – Encryption • The Perspective of Pen Tester – Compile Option – URLScheme – Insecure Database – Runtime Analysis – Transport Security
- 5. Monoculture – Code Signing •Code Signing –Provisioning Profiles –Signed Applications –Entitlements
- 6. Monoculture – Code Signing • Provisioning Profile –Asymmetric cryptography –UDIDS(prevents running of restricted devices) –Certificate(with trust based on the signing by a developer) –App ID in the info.plist
- 7. Monoculture – Code Signing • Developer Certificates Developer Program Device Testing Ad Hoc App Store In-House Apple Developer No No No No University Program Yes No No No Standard Program Yes Yes Yes No Enterprise Program Yes Yes No Yes
- 8. Monoculture – Code Signing • Provisioning Profile
- 9. Monoculture – Code Signing • Signed Applications – All iOS executable binaries and applications must be signed by a trusted certificate [Ad-hoc code signed executable]
- 10. Monoculture – Code Signing • Signed Applications – All iOS executable binaries and applications must be signed by a trusted certificate [Normal code signed executable]
- 11. Monoculture – Code Signing •Entitlements –Application-Identifier –Get-task-allow(Debug) –Keychain-access-groups
- 12. Monoculture – Code Signing
- 13. Monoculture – SandBoxing • Sandboxing – Third party apps assigned “container” seatbelt profile – Function calls hooked by the TrustedBSD layer will pass through Sandbox.kext for policy enforcement Compared to Andorid UID/GID
- 14. Monoculture - Encryption • Nand Solite State – Boot: Low Level Bootloader – Plog: Effaceable area(BAGI, Dkey, EMF!) – Nvm: Environments variables – Firm: iBoot, device tree and boot logos – Fsys: OS, DATA – Rsrv: Filesystem partition boot block 0 plog block 1 nvm blocks 2-7 firm blocks 8-15 fsys blocks 16-4084 rsrv blocks 4085- 4100
- 15. Monoculture - Encryption • EMF! – Used to encrypt the filesystem • Dkey – Used to encrypt the master key of the protection class "NSFileProtectionNone" (the majority of files) • BAGI – Used to produce the encryption keys for the other master keys
- 16. Monoculture - Encryption • Data Protection Level Description No Protection The file is not encrypted on the file-system Complete Protection The file is encrypted on the file-system and inaccessible when the device is locked Complete Unless Open The file is encrypted on the file-system and inaccessible while closed. When a device is unlocked an app can maintain an open handle to the file even after it is subsequently locked, however during this time the file will not be encrypted Complete Until First User Authentication The file is encrypted on the file-system and inaccessible until the device is unlocked for the first time. This helps offer some protection against attacks the require a device reboot Dkey on Plog
- 17. Monoculture - Encryption • File System Encryption – Every File is encrypted with unique key "cprotect" key – File key is stored in the file metadata – Metadata is encrypted with EMF Key – Content is grouped into protection class – Each protection class assigned a master encryption key – Master keys are protected by device key and passcode – Protected master keys form system keybag
- 23. Monoculture – Old Things • PIE(Positon Independent Executable) – Exploit mitigation security feature that allows an application to take full advantage of ASLR • Stack-Smashing Protection – “Canary” is placed on the stack directly before the local variables to protect the saved base pointer • Automatic Reference Counting – Introduced in iOS SDK version 5.0 to move the responsibility of memory management from the developer to the compiler – Offers some security benefits as it reduces the likelihood of developers introducing memory corruption(specifically object use-after-free and double free vulnerabilities)
- 24. Angenda • What’s the iOS App? • Monoculture – Code Signing – Sandboxing – Encryption • The Perspective of Pen Tester – Compile Option – URLScheme – Insecure Database – Runtime Analysis – Transport Security
- 25. Compile Option Check • PIE(Positon Independent Executable) • Stack-Smashing Protection • Automatic Reference Counting
- 26. Compile Option Check • Where is the Excutable File? – Smart – Brute
- 27. Compile Option Check • PIE(Positon Independent Executable) – GmailHybrid – FaceBook
- 28. Compile Option Check • Stack-Smashing Protection – GmailHybrid – FaceBook
- 29. Compile Option Check • Automatic Reference Counting – GmailHybrid – FaceBook
- 30. Angenda • What’s the iOS App? • Monoculture – Code Signing – Sandboxing – Encryption • The Perspective of Pen Tester – Compile Option – URLScheme – Insecure Database – Runtime Analysis – Transport Security
- 31. URLSchema - Overview • Noreal Inter-Process Communication • Apps prohibited from sharing because of sandbox • Apps sometimes need to share data • Apps can register a custom protocol handler
- 32. URLSchema - Overview • Two methods for implementing protocol handlers • handleOpenURL – Now deprecated • openURL – Provides bundle identifier – Allows developer to validate source app
- 33. URLSchema - Attack • Skype registers the “skype://” protocol handler • Malicious web site could make calls • Skype app did not prompt or validate before call – Allows developer to validate source app • Play the Video
- 34. Angenda • What’s the iOS App? • Monoculture – Code Signing – Sandboxing – Encryption • The Perspective of Pen Tester – Compile Option – URLScheme – Insecure Database – Runtime Analysis – Transport Security
- 35. Insecure Data Storage • Databases • Plists • Keyboard Cache • Image Cache • Keychain • Cookie Binary • Error Logs • Hidden Files(ex. Citi Mobile app) – Samples: Password_Keeper, Pic Lock, iPassword
- 36. Databases - Overview • Data stored in the Sqlite in un- encrypted • SQLite files are stored un-encrypted in the iOS backups • Delete files can be recovered by carving the HFS Journal • Not deleted completely
- 37. Databases - Attack • Password_Keeper – Interfaces – FaceBook
- 38. Databases - Attack • Password_Keeper – Save ID/Password
- 39. Databases - Attack • Password_Keeper – Clear Text in the Sqlite
- 40. Database - Defense • Do not store sensitive data in clear text • Use custom encryption • Protect Sqlite files with data protection API • Implement classes for secure file wipe • Purge the data upon deletion with VACUUM SQL command – VACUUM rebuild the databases – Doing it for every delete consume time • Before deleting the SQL record, replace the data with junk values – Data and Junk value length has to be same
- 41. Database - Defense – Step 1: Create the Table
- 42. Database - Defense – Step 2: Check out Strings in the Sqlite
- 43. Database - Defense – Step 3: Delete one row and Check out deleted Completely
- 44. Database - Defense – Step 4: Delete it completely
- 45. Insecure Data Storage • Databases(SQLite, coreData) • Plists • Keyboard Cache • Image Cache • Keychain • Cookie Binary • Error Logs • Hidden Files(ex. Citi Mobile app)
- 46. Plists - Overview • Property list files - Key value pairs stored in binary • Identified by a file header – bplist • Designed to store user's properties and configuration information • Not protected by Data protection • But Apps store credentials such as username, password, and session information
- 47. Plists - Attack • Pic Lock – FaceBook
- 48. Plists - Attack • Pic Lock
- 49. Plists – Defense • Do not store sensitive data in Plist files • If required, use custom encryption • Create plist files Library/Caches folder – iTunes does not backup caches directory • For better security, Implement classes for secure file wipe – Before deleting the file overwrite the file bytes with junk values
- 50. Insecure Data Storage • Databases(SQLite, coreData) • Plists • Keyboard Cache • Image Cache • Keychain • Cookie Binary • Error Logs • Hidden Files(ex. Citi Mobile app)
- 51. Keyboard Cache - Overview • Designed to auto complete the predictive common words • Secure fields are not stored – passwords are safe • String with all digits are not stored – Pins and credit card number are safe • Data typed into text fields are cached
- 52. Keyboard Cache - Attack • iPassword
- 53. Keyboard Cache - Attack • Keyboard Cache – iPassword – What if it is banking information?
- 54. Keyboard Cache - Defense • Keyboard Cache – Disable auto correction • Mark it as a secure field – mytextField.secureTextEntry = YES • Copy&Paste
- 55. Insecure Data Storage • Databases(SQLite, coreData) • Plists • Keyboard Cache • Image Cache • Keychain • Cookie Binary • Error Logs • Hidden Files(ex. Citi Mobile app)
- 56. Image Cache - Overview • Takes screen shots of the application to trick you • Sensitive data may get cached – App directory/Library/Caches/Snapshots
- 57. Image Cache - Attack • Image Cache – Mail App Press Home Button Two Times
- 58. Image Cache - Attack • Image Cache – Mail App IPod My Local Machine
- 59. Defense – Image Cache • Remove sensitive data or change the screen before the applicationDidEnterBackground() function returns • Instead of hiding or removing sensitive data you can also prevent back- grounding altogerher by setting the "Application does not run in background" property in the application's Info.plist file
- 60. Databases - Attack • Databases – Mail App
- 61. Databases - Attack • Databases – Mail App(Subject)
- 62. Databases - Attack • Databases – Mail App(Body)
- 63. Insecure Data Storage • Databases(SQLite, coreData) • Plists • Keyboard Cache • Image Cache • Keychain • Cookie Binary • Error Logs • Hidden Files(ex. Citi Mobile app)
- 64. Keychain - Overview • Keychain encryption is tied to the device – Protected entries are tied to the user's passcode • Keychain file is accessible to all the application • Application can only acess it's own key chain items – Based on app keychain access group
- 65. Keychain - Overview Attribute Description kSecAttrAccessibleAlways The keychain item is always accessible kSecAttrAccessibleWhenUnlocked The keychain item is only accessible when the device is unlocked. kSecAttrAccessibleAfterFirstUnlock They keychain item is only accessible after the first unlock from boot. This helps offer some protection against attacks that require a device reboot kSecAttrAccessibleAlwaysThisDevice Only The keychain item is always accessible but cannot be migrated to other devices kSecAttrAccessibleWhenUnlockedThi sDeviceOnly The keychain item is only accessible when the device is unlocked and may not be migrated to other devices kSecAttrAccessibleAfterFirstUnlock ThisDeviceOnly The keychain item is accessible after the first unlock from boot and may not be migrated to other devices
- 66. Keychain - Attack • Keychain_Dumper
- 67. Keychain - Defense • Do not store sensitive data in clear text • Encrypt the data using custom encryption • Use data protection API while storing data in keychain • By default entries are created with kSecAttrAccessibleWhenUnlocked data protection
- 68. Insecure Data Storage • Databases(SQLite, coreData) • Plists • Keyboard Cache • Image Cache • Keychain • Cookie Binary • Error Logs • Hidden Files(ex. Citi Mobile app)
- 69. Coockies Binary • Binary file to store the cookies • Persistent cookies are stored along with the flags(Secure, HTTPOnly) • Most iOS apps not prompt the user for login every time and creates persistent cookies
- 71. Insecure Data Storage • Databases(SQLite, coreData) • Plists • Keyboard Cache • Image Cache • Keychain • Cookie Binary • Error Logs • Hidden Files(ex. Citi Mobile app)
- 72. Error Logs • Apps may write sensitive data in logs – Debugging(NSLog calls) – Trouble shooting – Request & Response • Located at - /private/var/log/syslog • Syslog is out of sandbox - Any app can access it • Do not write sensitive data in the syslog file
- 73. Insecure Data Storage • Databases(SQLite, coreData) • Plists • Keyboard Cache • Image Cache • Keychain • Cookie Binary • Error Logs • Hidden Files(ex. Citi Mobile app[Fixed])
- 74. Angenda • What’s the iOS App? • Monoculture – Code Signing – Sandboxing – Encryption • The Perspective of Pen Tester – Compile Option – URLScheme – Insecure Database – Runtime Analysis – Transport Security
- 75. Runtime Analysis - Overview • Developed in Objective – Superset of C – Exiting methods can be overwritten easily • Self distributed Apps are not encrypted • AppStore binaries are encrypted • Decrypts the apps when loaded into memory
- 76. Runtime Analysis - Tools • Clutch – Decrypt the binary • Class-Dump-Z – Extract the class information and identify interesting class • Cycript – Combination of JavaScript and Objective-C interpreter – Gives access to all classes and instance variables within the app • GDB & IDA Pro Samples: Coupang, Password_Keeper, piracydemo2
- 77. Runtime Analysis – Decrypt Manually ARM v6 ARM v7 Encryped Binary
- 78. Runtime Analysis – Decrypt Manually (gdb) set sharedlibrary load-rules ".*" ".*" none (gdb) set inferior-auto-start-dyld off (gdb) set sharedlibrary preload-libraries off (gdb) rb doModInitFunctions Breakpoint 1 at 0x2fe0d526 <function, no debug info> __dyld__ZN16ImageLoaderMachO18doModInitFunctionsERKN11Ima ge (gdb) r Starting program: /private/var/mobile/Applications/3DC4CAC7- A429-449E-BB6C-A985E3A644 Program received signal SIGABRT, Aborted. 0x3a5b7350 in ?? () (gdb) dump memory coupang.bin 12288 950272 (gdb) kill Kill the program being debugged? (y or n) y (gdb) q
- 79. Runtime Analysis – Decrypt Manually • Success, but it consumes time!!!
- 80. Runtime Analysis • Authentication bypass • Breaking simple locks • Bypassing restriction that stops apps from running on Jailbroken device • Extract hardcode encryption keys • Extract app passcodes • Malicious code injection
- 81. Runtime Analysis - Attack • Bypassing Lock Screen – Password_Keeper – FaceBook
- 83. Runtime Analysis – Decrypt Automatically • Clutch
- 84. Runtime Analysis - ClassDump • ClassDump No More Obfuscation
- 85. Runtime Analysis - ClassDump • ClassDump
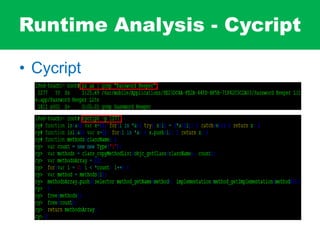
- 86. Runtime Analysis - Cycript • Cycript
- 87. Runtime Analysis - ClassDump • Cycript
- 88. Runtime Analysis - Cycript • Cycript
- 89. Runtime Analysis - Cycript • Cycript Step(1/3) Enter the Code
- 90. Runtime Analysis - Cycript • Cycript Step(2/3)
- 91. Runtime Analysis - Cycript • Cycript Step(3/3) Get rid of Lock Screen
- 92. Runtime Analysis • Authentication bypass • Breaking simple locks • Bypassing restriction that stops apps from running on Jailbroken device • Extract hardcode encryption keys • Extract app passcodes • Malicious code injection
- 93. Runtime Analysis - Attack • Bypassing JailBreak Detection – Demo_App
- 94. Runtime Analysis - Attack • Figure out Attractive Instance
- 95. Runtime Analysis - Attack • Figure out Attractive Instance
- 96. Runtime Analysis - Attack • Figure out Attractive Instance
- 97. Runtime Analysis - GDB • GDB – Set the BreakPoint
- 98. Runtime Analysis - GDB • GDB - Continue Continue on GDB and Hit the “Am I Jailbroken?”
- 99. Runtime Analysis - GDB • GDB – Set the breakpoints at “objc_msgSend”
- 100. Runtime Analysis - GDB • GDB – Check Out Breakpoints
- 101. Runtime Analysis - GDB • GDB – That’s not what we want
- 102. Runtime Analysis - GDB • GDB – That’s not what we want
- 103. Runtime Analysis - GDB • GDB – That’s not what we want
- 104. Runtime Analysis - GDB • GDB – That’s exactly what we want
- 105. Runtime Analysis - GDB • GDB – Manipulate the r0
- 106. Runtime Analysis - GDB • GDB
- 107. Runtime Analysis - GDB • GDB - Sueccess
- 108. Runtime Analysis - Defense • Detection JailBreak(1) – Sandbox
- 109. Runtime Analysis - Defense • Detection JailBreak(2) – Filesystem 1. /Library/MobileSubstrate/MobileSubstrate.dylib 2. /Application/Cydia.app 3. /var/cache/apt 4. /var/lib/apt 5. /var/lib/cydia 6. /var/log/syslog 7. /var/tmp/cydia.log 8. /bin/bash, /bin/sh 9. /usr/sbin/sshd 10. /usr/libexec/ssh-keysign 11. /etc/ssh/sshd_config 12. /etc/apt
- 110. Runtime Analysis - Defense • Detection JailBreak(3) – Symbolic Link 1. /Library/Ringtones 2. /Library/Wallpaper 3. /Library/arm-apple-darwin9 4. /usr/include 5. /usr/libexec 6. /usr/share
- 111. Runtime Analysis - Defense • Protect Runtime – OZ option: Inline compile – Strip: Get rid of unnessesary symbol table – Debugging Flag: P_Traced – dladdr: Checking address space
- 112. Angenda • What’s the iOS App? • Monoculture – Code Signing – Sandboxing – Encryption • The Perspective of Pen Tester – Compile Option – URLScheme – Insecure Database – Runtime Analysis – Transport Security
- 113. Transport Security - Overview •UDID •GeoLocation •SSL •Mac Address
- 114. Transport Security - UDID • Much like the Pentium 3 CPU, each Apple iPhone is equipped with a unique, application-visible serial number(40- characcter) called a Unique Device ID (UDID). • According to Apple, the use of UDIDs allows businesses to ensure that devices continue to comply with required policies. • Not Any more!!!
- 115. Transport Security - UDID
- 116. Transport Security - UDID
- 117. Transport Security - Overview •UDID •GeoLocation •SSL •Mac Address
- 118. Transport Security - GeoLocation • Provided by the Core Location framework • Avoid being “too accurate” • Can be set by one of the following constants: – kCLLocationAccuracyBestForNavigation; – kCLLocationAccuracyBest; – kCLLocationAccuracyNearestTenMeters; – kCLLocationAccuracyHundredMeters; – kCLLocationAccuracyKilometer; – kCLLocationAccuracyThreeKilometers;
- 119. Transport Security - GeoLocation • Without Agreement
- 120. Transport Security - GeoLocation • Without Agreement
- 121. Transport Security - Overview •UDID •GeoLocation •SSL •Mac Address
- 122. Transport Security - SSL • Vunerable to MITM – ex) Global Banking App(It uses “allowsAnyHTTPSCertificateForHost” which overrides self-signed certificate)
- 123. Transport Security - SSL • Password Authentication
- 124. Transport Security - SSL • Password Authentication
- 125. Transport Security - SSL • Password Authentication
- 126. Transport Security - SSL • Password Authentication
- 127. Transport Security - SSL • Password Authentication
- 128. Transport Security – SSL(Defense) • NSURLRequest – Prohibit the use of self-signed certificates(!allowsAnyHTTPSCertificateForHost) • NSURLConnection – Ignore cert usingcontinueWithoutCredentialForAuthenticationCha llenge selector • CFNetwork framework – kCFStreamSSLAllowsExpiredCertificates – kCFStreamSSLAllowsAnyRoot – kCFStreamSSLAllowsAnyRoot – kCFStreamSSLValidatesCertificateChain
- 129. Transport Security - Overview •UDID •GeoLocation •SSL •Mac Address
- 130. Transport Security - MAC • Ads
- 131. Transport Security - MAC • Ads
- 132. Transport Security - MAC • Ads
- 133. Reference - 1 • Half of iOS apps 'violate Apple's privacy policy – http://www.digitalspy.co.uk/tech/news/a493520/half-of-ios-apps- violate-apples-privacy-policy.html • iOS_Application Insecurity final – http://www.mdsec.co.uk/research/iOS_Application_Insecurity_fin al.pdf • iOS Application Insecurity wp v1.0 final – http://www.mdsec.co.uk/research/iOS_Application_Insecurity_wp _v1.0_final.pdf • Introduction to ios platform security – http://blog.mdsec.co.uk/2012/05/introduction-to-ios-platform- security.html • Code Signing – http://installbuilder.bitrock.com/docs/installbuilder- userguide/ar01s16.html – http://developer.apple.com/library/mac/#technotes/tn2206/_index .html
- 134. Reference - 2 • Pentesting iPhone Applications – http://resources.infosecinstitute.com/pentesting-iphone-applications/ – http://www.securitylearn.net/ • iOS Application Security part4 – http://resources.infosecinstitute.com/ios-application-security-part-4-runtime-analysis- using-cycript-yahoo-weather-app/ • Cycript_Tricks – http://iphonedevwiki.net/index.php/Cycript_Tricks • Keychain Dumper – https://github.com/ptoomey3/Keychain-Dumper • Books – Hacking and Securing iOS Applications • iOS Secure Development Source Boston 2011 – https://www.isecpartners.com/media/12964/ios_secure_development_source_bosto n_2011.pdf • Auditting iPhone and iPad applications by Ilja van Sprundel • DaiZovi/BH_US_11_DaiZovi_iOS_Security_WP – http://media.blackhat.com/bh-us- 11/DaiZovi/BH_US_11_DaiZovi_iOS_Security_WP.pdf
- 135. Reference - 3 • Reverse engineering sous Android et iOS – www.ossir.org/jssi/jssi2013/3A.pdf • iPhone data protection in depth – http://conference.hitb.org/hitbsecconf2011ams/materials/D2T2%20-%20Jean- Baptiste%20Be%CC%81drune%20&%20Jean%20Sigwald%20- %20iPhone%20Data%20Protection%20in%20Depth.pdf • Apple Sandbox – http://securityevaluators.com/files/papers/apple-sandbox.pdf • iOS_data_protection – http://ensiwiki.ensimag.fr/images/7/7f/SecurIMAG-2012-09-27- iOS_data_protection.pdf • syscan11 breaking ios code signing – http://reverse.put.as/wp- content/uploads/2011/06/syscan11_breaking_ios_code_signing.pdf • Syscan-2012-iOS-Applications-and-the-Lion-City-Presso – http://reverse.put.as/wp-content/uploads/2011/06/Syscan-2012-iOS- Applications-and-the-Lion-City-Presso.pdf • BlackHat_EU_2011_Dhanjani_Attacks_Against_Apples_iOS-WP – http://media.blackhat.com/bh-eu- 11/Nitesh_Dhanjani/BlackHat_EU_2011_Dhanjani_Attacks_Against_Apples_iO S-WP.pdf
- 136. - Thank you -









![Monoculture – Code Signing
• Signed Applications
– All iOS executable binaries and applications
must be signed by a trusted certificate
[Ad-hoc code signed executable]](https://image.slidesharecdn.com/iosapplicationpenetationtestpublish-130915101729-phpapp02/85/iOS-Application-Penetation-Test-9-320.jpg)
![Monoculture – Code Signing
• Signed Applications
– All iOS executable binaries and applications
must be signed by a trusted certificate
[Normal code signed executable]](https://image.slidesharecdn.com/iosapplicationpenetationtestpublish-130915101729-phpapp02/85/iOS-Application-Penetation-Test-10-320.jpg)






























































![Insecure Data Storage
• Databases(SQLite, coreData)
• Plists
• Keyboard Cache
• Image Cache
• Keychain
• Cookie Binary
• Error Logs
• Hidden Files(ex. Citi Mobile app[Fixed])](https://image.slidesharecdn.com/iosapplicationpenetationtestpublish-130915101729-phpapp02/85/iOS-Application-Penetation-Test-73-320.jpg)