Innovating Faster with Continuous Application Security
- 1. Innovating Faster with Continuous Application Security By Jeff Williams, CTO and co-founder Contrast Security @planetlevel
- 2. The Average application is extremely vulnerable 71%unused Libraries 26.7Vulnerabilities 2Vulnerabilities 8%USED Libraries 21%Custom Code
- 3. DevSecCon Boston 2018: Building a Practical DevSecOps Pipeline for Free 3 You are Under AttacK
- 4. Unless otherwise indicated, these slides are © 2013-2018 Pivotal Software, Inc. and licensed under a Creative Commons Attribution-NonCommercial license: http://creativecommons.org/licenses/by-nc/3.0/ Traditional AppSec Doesn’t Scale Experts Expert Tools Application Portfolio Assurance Coverage Process Fit Awful Results $$$$ Traditional AppSec Program
- 5. Unless otherwise indicated, these slides are © 2013-2018 Pivotal Software, Inc. and licensed under a Creative Commons Attribution-NonCommercial license: http://creativecommons.org/licenses/by-nc/3.0/ DevSecOps Is Very Promising 5 https://itrevolution.com/the-three-ways-principles-underpinning-devops/ 1.Establish work flow 2.Ensure instant feedback 3.Culture of experimentation 1.Establish security work flow 2.Ensure instant security feedback 3.Build a security culture DEVOPS DEVSECOPS
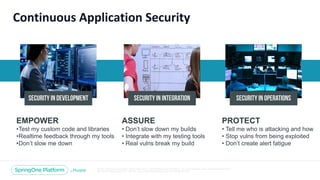
- 6. Unless otherwise indicated, these slides are © 2013-2018 Pivotal Software, Inc. and licensed under a Creative Commons Attribution-NonCommercial license: http://creativecommons.org/licenses/by-nc/3.0/ Continuous Application Security Security in development Security in integration Security in operations PROTECT • Tell me who is attacking and how • Stop vulns from being exploited • Don’t create alert fatigue ASSURE • Don’t slow down my builds • Integrate with my testing tools • Real vulns break my build EMPOWER •Test my custom code and libraries •Realtime feedback through my tools •Don’t slow me down
- 7. Unless otherwise indicated, these slides are © 2013-2018 Pivotal Software, Inc. and licensed under a Creative Commons Attribution-NonCommercial license: http://creativecommons.org/licenses/by-nc/3.0/ IAST and RASP Runtime Application Self-Protection (RASP) •Prevents exploit ofvulnerabilities in both custom code and libraries. Your Application or API Config Sensors Code Sensors Control Flow Sensors HTTP Sensors Backend Sensors Data Flow Sensors Library Sensors Exploit Prevented Vulnerability Confirmed ✘ Interactive Application Security Testing (IAST) •Detects vulnerabilities in both custom code and libraries
- 8. Unless otherwise indicated, these slides are © 2013-2018 Pivotal Software, Inc. and licensed under a Creative Commons Attribution-NonCommercial license: http://creativecommons.org/licenses/by-nc/3.0/ A Fully Automated Pipeline with Security Development CI/CD/QA Operations IAST IAST/RASP RASP
- 9. Unless otherwise indicated, these slides are © 2013-2018 Pivotal Software, Inc. and licensed under a Creative Commons Attribution-NonCommercial license: http://creativecommons.org/licenses/by-nc/3.0/ Adding IAST/RASP to PCF application 9 cf login cf push spring-petclinic cf create-user-provided-service contrast-security-service -p "teamserver_url, username, api_key, service_key” cf bind-service spring-petclinic contrast-security-service cf restage spring-petclinic
- 10. 10 • Must be extremely accurate • Must work on modern apps with APIs and OSS Test my custom code AND libraries • Must integrate with tools I’m already using – NO PDF! Realtime feedback through my tools • Must not create bottleneck – NO SCANNING! Don’t slow me down Security in Development
- 11. Unless otherwise indicated, these slides are © 2013-2018 Pivotal Software, Inc. and licensed under a Creative Commons Attribution-NonCommercial license: http://creativecommons.org/licenses/by-nc/3.0/ Automation is all about speed, accuracy, and ease-of-use 11 OWASP Benchmark Free and open application benchmark with thousands of security test cases
- 12. Unless otherwise indicated, these slides are © 2013-2018 Pivotal Software, Inc. and licensed under a Creative Commons Attribution-NonCommercial license: http://creativecommons.org/licenses/by-nc/3.0/ Download an IAST/RASP Agent 12 1. Download 2. Install 3. Enjoy agent
- 13. Unless otherwise indicated, these slides are © 2013-2018 Pivotal Software, Inc. and licensed under a Creative Commons Attribution-NonCommercial license: http://creativecommons.org/licenses/by-nc/3.0/ Empower developers to assess their own security! 13 PRODDEV CI/CD APIs Containers PrivateCloud APIs ContainersPrivate Public Cloud Custom Code - and - Open Source
- 14. Unless otherwise indicated, these slides are © 2013-2018 Pivotal Software, Inc. and licensed under a Creative Commons Attribution-NonCommercial license: http://creativecommons.org/licenses/by-nc/3.0/ Security in Everyday environment 14 IDE ChatOps Browser Others:
- 15. 15 • Fully automated security testing with every build Don’t slow down my builds • Plugins, integrations, webhooks, and FULL REST API Integrate with my testing tools • Set criteria for when to break the build Break my build… but only for real issues Security In Integration
- 16. Unless otherwise indicated, these slides are © 2013-2018 Pivotal Software, Inc. and licensed under a Creative Commons Attribution-NonCommercial license: http://creativecommons.org/licenses/by-nc/3.0/ Fail the build 16
- 17. Unless otherwise indicated, these slides are © 2013-2018 Pivotal Software, Inc. and licensed under a Creative Commons Attribution-NonCommercial license: http://creativecommons.org/licenses/by-nc/3.0/ Automatic Bugtracking Integration 17
- 18. Unless otherwise indicated, these slides are © 2013-2018 Pivotal Software, Inc. and licensed under a Creative Commons Attribution-NonCommercial license: http://creativecommons.org/licenses/by-nc/3.0/ Measuring Attack Surface 18
- 19. Jumpstarting Your DevSecOps Pipeline with IAST and RASP | @planetlevel 19 Measuring Security Testing Coverage
- 20. 20 • I need actionable threat intelligence Tell me who is attacking and how • Must not overblock (FP) or underblock (FN) Stop vulnerabilities from being exploited • Don’t warn me about meaningless probes Don’t create alert fatigue Security in operations
- 21. Unless otherwise indicated, these slides are © 2013-2018 Pivotal Software, Inc. and licensed under a Creative Commons Attribution-NonCommercial license: http://creativecommons.org/licenses/by-nc/3.0/ Protect Applications and APIs with RASP 21 Custom Code Open Source Libraries and Frameworks Application Server and Platform • PREVENTS Known Vulnerabilities from exploit • Prevents LATENT Vulnerabilities from exploit • Fast response to prevent NOVEL vulnerabilities from exploit
- 22. Unless otherwise indicated, these slides are © 2013-2018 Pivotal Software, Inc. and licensed under a Creative Commons Attribution-NonCommercial license: http://creativecommons.org/licenses/by-nc/3.0/ RASP Deploys with Your Application 22 • Ansible • Puppet • Docker • Kubernetes • Whatever…
- 23. Unless otherwise indicated, these slides are © 2013-2018 Pivotal Software, Inc. and licensed under a Creative Commons Attribution-NonCommercial license: http://creativecommons.org/licenses/by-nc/3.0/ RASP Protects Against OSS Vulnerabilities 23 March 7 CVE-2017-5638 Disclosed, Apache releases fixed version March 8 We observe widespread attacks Mid-May Equifax breach occurs July29 Equifax learns of breach Sept 7 Equifax discloses, Four more Struts2 CVEs disclosed No updates You must have infrastructure to respond within hours. DisasterNo detection
- 24. Unless otherwise indicated, these slides are © 2013-2018 Pivotal Software, Inc. and licensed under a Creative Commons Attribution-NonCommercial license: http://creativecommons.org/licenses/by-nc/3.0/ RASP Supports Complex and Backend Protocols 24 Application Untrusted deserialization Name: Smith, James Record ID: 123456 Owner: Finance Application expects to receive this object Bad Guy AcmeInternalType#cmd: java.lang.Runtime AcmeInternalType#mtd: getRuntime().exec AcmeInternalType#args: ‘cmd.exe’,’/C’,’calc’ AcmeInternalType#cmd: java.lang.Runtime AcmeInternalType#mtd: getRuntime().exec AcmeInternalType#args: ‘cmd.exe’,’/C’,’calc’ Attacker sends malicious object
- 25. Unless otherwise indicated, these slides are © 2013-2018 Pivotal Software, Inc. and licensed under a Creative Commons Attribution-NonCommercial license: http://creativecommons.org/licenses/by-nc/3.0/ RASP Is Fast 25 +50 µs 100x faster than wafRASP waf +5 ms
- 26. Unless otherwise indicated, these slides are © 2013-2018 Pivotal Software, Inc. and licensed under a Creative Commons Attribution-NonCommercial license: http://creativecommons.org/licenses/by-nc/3.0/ RASP Provides AppSec Threat Intelligence 26
- 27. Unless otherwise indicated, these slides are © 2013-2018 Pivotal Software, Inc. and licensed under a Creative Commons Attribution-NonCommercial license: http://creativecommons.org/licenses/by-nc/3.0/ Continuous Application Security Security in development Security in integration Security in operations PROTECT • Tell me who is attacking and how • Stop vulns from being exploited • Don’t create alert fatigue ASSURE • Don’t slow down my builds • Integrate with my testing tools • Real vulns break my build EMPOWER •Test my custom code and libraries •Realtime feedback through my tools •Don’t slow me down
- 28. Unless otherwise indicated, these slides are © 2013-2018 Pivotal Software, Inc. and licensed under a Creative Commons Attribution-NonCommercial license: http://creativecommons.org/licenses/by-nc/3.0/ Fully Continuous AppSec
- 29. Unless otherwise indicated, these slides are © 2013-2018 Pivotal Software, Inc. and licensed under a Creative Commons Attribution-NonCommercial license: http://creativecommons.org/licenses/by-nc/3.0/ Contrast Community Edition 21,000,000 DEVELOPERS IN THE WORLD AND ONLY 6% HAVE ACCESS TO DECENT SECURITY TOOLS Contrast CE is a totally free and full-strength application security platform combining: • Assess web apps and APIs for vulnerabilities (AST) • Monitor open source (SCA) • Runtime exploit prevention (RASP) Faster, more accurate, more scalable, better integrated, and more DevSecOps-friendly than any other application security solution. Coming Soon: https://www.contrastsecurity.com/contrast-community-edition
- 30. > Go Fast and Be Secure. Try Continuous Application Security Now! #springone@s1p