Inside .NET Smart Card Operating System
- 1. Inside .NET Smart Card Operating System 44Con, September 2012 Behrang Fouladi, SensePost [email protected]
- 2. What is a smart card? VS
- 3. What is a smart card?
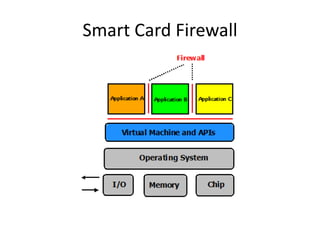
- 4. Single Application Smart Cards
- 5. Multi-Application Smart Card Card Parking Access Control Cashless Payments Computer Access Identification
- 6. Did you know? • How many of you have Orange SIM cards? • What applications are running on your SIM card? • Any other apps working silently?
- 7. Example: SIM Tracker Applet • Operators goal: sending the MMS/APN settings to the new handset • Can also be used for investigation purposes
- 8. In The News… – Oyster card: Crypto-1 encryption algorithm attack, 2004 – Cambridge university: EMV relay attack, 2010 – Sykipot malware Targeting US DoD smart cards, 2011-2012
- 9. In The News…
- 10. Why?
- 11. Why? • • • • • 8 billion smart cards by 2014 The “Internet of Things” Chip-enabled mobile payments Hardware backdoors Malware is everywhere!
- 13. Multi-application Smart Card Platforms .NET card MULTOS JavaCard
- 14. .NET Smart Card • First .NET virtual machine on the chip • Native support in Windows 7 and server 2008 • Used in: – Smart card based corporate badges (Microsoft employees badge) – Remote Access Control (USA DoD and UK MOD)
- 15. .NET smart card overview
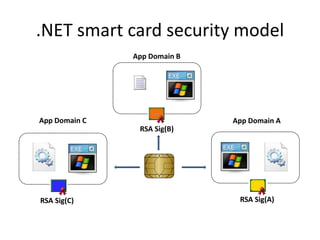
- 16. .NET smart card security model App Domain B App Domain C App Domain A RSA Sig(B) RSA Sig(C) RSA Sig(A)
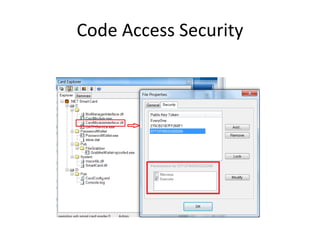
- 17. Public Key Token
- 20. Card application development ?? Deployment & Debugging ?? Communication (APDU) ??
- 21. Card application development .NET assembly Converter Plug-in (1) Compiles program (3) Signed card binary (2) Conversion to card binary (4) .NET remoting comm. Comm. Proxy (5) APDU comm. Vendor’s SDK
- 22. How secure is .NET card? • Has EAL5+ certified Infenion chip • EAL certification is widely used by smart card industry (EAL3 to EAL7) • .NET card OS is designed to achieve EAL4+ • EAL4+ audit: – takes 6 to 9 months, costs high 10sk to low 100sk £ – includes independent penetration testing and source code review in some case • No published vulnerabilities so far
- 23. Rev. Engineering For Vuln. Discovery
- 24. Smart Card Vuln. research • No Chip OS binary is available • Traditional tools (debuggers, disassemblers) are useless • No publicly available testing tools • Secure chips have sensors, shields, encryption • ON-card bytecode/IL code verifier
- 25. “HiveMod” Tool
- 26. HiveMod • Vulnerability research tool, for: – .NET card binary (Hive format) visualization – Card Binary manipulation – Card binary Re-signing
- 27. .NET Card Binary Compiler Header Digital signature Header Object counters Header Namespaces reference table Types reference table Methods reference table Fields reference table Blob definitions Type definitions Method definitions Program code (IL code) RSA signature
- 29. Manipulating Digital Signature Header Compiler Header Digital signature Header Object counters Header Namespaces reference table Types reference table Methods reference table Fields reference table Blob definitions Type definitions Method definitions Program code (IL code) RSA signature offset 32 52 60 64 68 Field name SHA1 hash of the full assembly Public key token RSA modulus length RSA public exponent RSA modulus size 20 8 4 (len) 4 len
- 30. Manipulating Digital Signature Header PBKT=Reverse(Right(SHA1(RSA_modulus),8))
- 31. (Bypassing .NET card app Firewall) Old school attack: Public Key Token Spoofing
- 32. Attack Demo Let’s use the HiveMod tool to test this vulnerability!
- 34. Manual testing vs. HiveMod • • • • Rev. engineering the SDK: ~2 months Hex editor for binary patching : Frustrating Modified card binary needs to be signed Destroying at least 10 cards: ~200 Euros
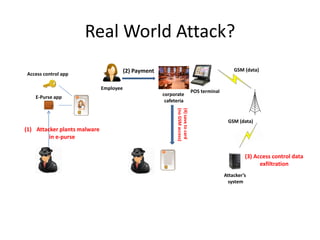
- 35. Real World Attack? GSM (data) (2) Payment Access control app Employee E-Purse app (4) save to card (no GSM access) (1) Attacker plants malware in e-purse corporate cafeteria POS terminal GSM (data) (3) Access control data exfiltration Attacker’s system
- 36. Fiction or Real? Document available on the internet
- 37. Vendor’s Response • “An attacker needs administration key to be able to upload his malicious application on the card, This Key is normally securely stored in a HSM or a smart card based controller”.
- 38. Vendor’s Response • “Knowledge of the Public Key Token of the targeted application is required”.
- 39. Vendor’s Response • “The targeted application must use private file-system storage for its data to be exposed. Therefore, internal (Application Domain) storage is immune to such attack”. byte[] key={0xaf,0x09,0x45,0x12,....};
- 40. More Vulnerabilities... • Unauthorized memory read in InitializeArray(): public static void InitializeArray(Array array,RuntimeFieldHandle fldHandle); • Results: Partial memory dump • Destroys the card (no reliable exploitation yet)
- 42. Conclusions • • • • don’t worry! check the apps PKTs for tampering. Use a secure card management system Smart card apps can be patched/updated , but not the card’s OS! • Smart cards OS and apps and card management software need pen tests too!
- 43. Closing words • HiveMod Tool would be available to Smart Card vendors and security researchers (contact [email protected])
- 44. Questions?
Editor's Notes
- #3: Smartvs Dumb : 1)microprocessor chip 2)Tamper resistance : -it can execute small applications -perform crypto operations; difficult cloning difficult tampering and data extraction : best option for SIM cards that store private key; subscriber identity token + call encryption- Have contact and contactless interfaces
- #4: The IC package contains : CPU, crypto co-processor, ROM, EEPROM and RAM. Modern smart cards: 32bit CPU 10Mhz, ~8KB RAM, ~80KB ROM, 400KB EEPROMProtection against invasive and non-invasive attacks: power analysis, side channel attacks: EM emission – fault injection , modifying the circuits
- #5: -Oyster card,Conditional Access Cards (pay TV), Access control cards-Proprietary operating systems , Proprietary encryption and comm protocols (CRYPTO-1 stream cipher failure)-No post issuance applications
- #6: -Example: Corporate badges, College cards, Military/Law enforcement personnel (access control) -Stores and runs applications with different security importance level-Java, .NET, C and even Google Dalvik code (dkard)-Post issuance application management: Uninstall/update/install apps, encryption keys or data files.
- #8: Orange
- #9: Smart cities: Funded by EU (2007-2013) , 6 countries in north sea region : UK, DE, NL, BL, SE, Norway ; Gov and academic co-work to facilitate : e-Gov servicesNHS: Medical records and EPS Oyster: 22m cards, <300ms transaction processing speed (offline), Project to integrate it in the banking cards (no topup)
- #10: NXPmaifare card : proprietary stream cipher algorithm attack; key recovery attack EMV relay attack: public static and dynamic authentication protocol ; rouge POSSykipot: Steals PIN code using keylogger then When a card is inserted into the reader, the malware then acts as the authenticated user and can access sensitive information. A trend: moving from protocol attacks to smart card software Next?? On the card itself??
- #11: -Was running at least for 3 years before being detected. -Attackers view the list of PKI certificates and logon to protected resources via C&C commands (SSL); common C&C commands we had seen in our analysis of a defense equipment manufacturer network break-in in summer 2011; same actors??Smart card proxy malware had been seen before this incident, but this one was the first attack against an specific product ActivIdentityʼsActivClient solution
- #12: Why the malicious code threat to smart cards is important to research?
- #13: 8bn Excluding RFID chips Internet of Thing : radio tags are embedded in things and things people ware or carry which can identify them to computer systems or small GSM connectivity modules used in M2M . Remote monitoring of utility meters, high value items tracking, smart energy grids; challenge: deploying application securely, over the air management ; tamper resistance smart cardsFirst NFC SIM cards rolled out in France by orange in Jun (beats the NFC chip on handset approach) , Microsoft Windows 8 digital wallet , jun 2012, Wallet API and wallet vulnerabilitiesCyberwar is going on silently and we have seen malware was delivered and planted successfully in high security isolated environments, Smart cards are cosy place to plant malicious code in a very large scale. Compare with something like web servers and web apps on the netIntegrated NFC, SIM or microSD, Fob or Sticker
- #14: Fixed : Phone cards, Health card, RFID tags, most of Access Control Cards- Dynamic:Banking card, SIM card, Government Identity Cards
- #15: - Application sandboxing
- #16: MULTOS:Gov and Military grade security; Expensive and complicated development process; Proprietary VM (MULTOS Executable Language) MELJavacard: Developed by Sun/Oracle; The most popular smart card; mainly used in telecomm (SIM cards) and banking sector as well as a certificate storage card (cheap); runs on different chips from different vendors .NET card: Smart card of choice for multi-factor authentication and remote access to Windows networks; has easy to use SDK for Microsoft Visual Studio 2005 to 2010
- #17: - First embedded MS .NET implementation in 2004, even before .NET Micro (2009)MS:Over 300.000 badges delivered since 2005USA DoD: combination of .NET and JavaCardsUK DoD: .NET smart card for remote access to ISA 2006 and (intelligent app gateway) IAG 2007
- #18: Adds smart card based OTP to FIM
- #19: Windows like file system1 base class library: mscorlib.dll , 1 smart card specific library: PIN and transaction management, .NET remoting
- #24: -APDU : Application protocol data unit; format: <instruction class><intsr code><command data> /<response data>; 4 bytes header
- #26: Evaluation assurance level (EAL) : numeric grade for evaluation the security IT products.Widely used by smart card vendors to give “assurance” to consumer; performed by approved companies certifited by CBELA5 means that independent pen test was done on chip OS and hardware ELA4+ independent pen testing and possibility source code audit
- #27: We have good tools and procedures for rev engineering the software and even embedded systems, however this is not the case for smart cards: they are designed to resists hardware reving and hacks; a smart card test lab would cost more than 200K USDNormally begins with profiling the target software (dynamic analysis of file system, registry , network access) or identifying the CPU architecture, hardware security measures and operating system type for embedded systems firmware or binary code disassembly Running firmware or its components inside emulator; file format, network protocol fuzzingMonitoring the target process or JTAG or serial port
- #28: Sensors: light, power Shields: protects against probsEncryption: logic encryption and os code encryptionMakes chip hardware reverse engineering very expensive My goal was finding vulns in the virtual machine not reversing an algorithm running on the chip My approach: reverse engineering the converter program in the SDK that converts the MS .NET assembly to .NET card binary -> knowledge of card binary metadata and their meanings-> model the way that card’s VM loads and execute apps-> identify interesting metadata and manipulate them to trigger vulns in the card’s VM
- #30: - The first such tool for smart cards
- #31: -More technical details is available at sensepost research web site
- #32: Decided to create limited set of test cases forHIVE headers which will be parsed by ContentManagerIL code section which will be verified and executed by the VMDigital signature header was interesting case, because card security model was built on assemblies public key
- #33: RSA modulus and public exponent were the only required information to a) verify the card binary’s signature a) compute the PBKTWhy the PBKT is already there?For performance reasons??
- #34: PBKT can be easily computed by knowing the RSA_modulusPBKT is the application’s identity token
- #35: Can we modify it to spoof the identity of other apps and bypass the app firewall?
- #36: Backdoor or vuln??
- #38: Rev. engineering: includes analysis of obfuscated code of the converter, writing small .NET programs to map different .NET types and method to their hive binary data, find out how different metadata tables are built and how they can be parsed correctly.Hex editor: can be trivial for modifying different sections of the same binary, but is not easy to use with different card binaries which have the same header or metadata table in a different file offsetRandomly modifying the card binary and loading it into the card can damge VM memory and render the card useless
- #40: Picture of attack
- #41: Case study document from MULTOS web site; NATO member militaryMulti-application card ; cashless payment and health care apps sit next to access control app
- #42: How many of you use smart card based authentication?Do you use HSM or card management solution?If the attacker had admin key, then he could simply download the file and there was not need to exploit PBKT vulnerability
- #43: - Public key is public!
- #45: - Exploit: Modifying the fldHnadle to types without hasRVA modifier->Raw memory read
- #46: Picture of the dead card


































![Vendor’s Response
• “The targeted application must use private
file-system storage for its data to be exposed.
Therefore, internal (Application Domain)
storage is immune to such attack”.
byte[] key={0xaf,0x09,0x45,0x12,....};](https://image.slidesharecdn.com/44connetcard-120910103019-phpapp02/85/Inside-NET-Smart-Card-Operating-System-39-320.jpg)




