Introduction To Intrusion Detection Systems
- 1. Introduction to Intrusion Detection Systems Paul Green CISSP
- 2. What is IDS? Software or hardware device Monitors network or hosts for: Malware (viruses, trojans, worms) Network attacks via vulnerable ports Host based attacks, e.g. privilege escalation
- 3. What is in an IDS? An IDS normally consists of: Various sensors based within the network or on hosts These are responsible for generating the security events A central engine This correlates the events and uses heuristic techniques and rules to create alerts A console To enable an administrator to monitor the alerts and configure/tune the sensors
- 4. Different types of IDS Network IDS (NIDS) Examines all network traffic that passes the NIC that the sensor is running on Host based IDS (HIDS) An agent on the host that monitors host activities and log files Stack-Based IDS An agent on the host that monitors all of the packets that leave or enter the host Can monitor a specific protocol(s) (e.g. HTTP for webserver)
- 5. Why do we need IDS? Firewalls use rules to reject unwanted network traffic Hackers can hide attacks in “acceptable” network traffic, therefore bypassing the firewall IDS actually monitor the network traffic, packet by packet IDS use rules as well as signatures to identify unwanted network traffic IDS can learn acceptable network traffic
- 6. Passive versus Reactive (IPS) A passive system detects the anomaly, logs the information and creates an alert Can be used to track a potential security breach without alerting the hacker A reactive system detects the anomaly and performs an action to limit the impact Also known as Intrusion Prevention System (IPS) Example actions: Reset the suspicious connection Create a new firewall rule to block the attack
- 7. NIDS in more detail Detects malicious activity such as port scans by monitoring network traffic Monitors incoming and outgoing network traffic Does not alter or affect the traffic on the wire, non-intrusive Compares activity to known attack signatures Can sometimes detect shellcodes in transit Example : snort
- 8. HIDS in more detail Monitors which program accesses what resources and when Monitors log files (syslog, event log etc) Monitors access to system files (e.g. password database) using a checksum database Monitors use of privileged users (administrator, root etc) Monitors system memory structures (vtables) Examples : Tripwire, OSSEC
- 9. Host-based IDS in more detail Monitors network packets as they traverse up the OSI layers Can monitor for specific protocols Allows the IDS to pull the packet before it gets to the application or OS Normally a hybrid HIDS agent Implementations differ from various vendors Examples : RealSecure
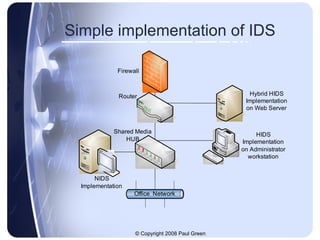
- 10. Simple implementation of IDS
- 11. Simple implementation of IDS Place HIDS on all hosts to be monitored Use hybrid HIDS where specific applications can be monitored Set the NIDS server NIC to promiscuous mode (to enable the NIDS to see all traffic) The HUB broadcasts all traffic on the network segment to all network nodes Need a NIDS on all network segments that need to be monitored
- 12. IDS in a switched network Switches do not broadcast network traffic to all nodes (point to point) Therefore, you need to copy traffic Need to use either a TAP or SPAN the required ports A tap will splice the data line copying all traffic without interfering with the original traffic SPAN is a switch feature that copies all traffic from a range of ports to another port (SPAN port), the IDS is then connected to the SPAN port
- 13. IDS in a switched network (TAP) TAP copies all packets to the NIDS There is no change or delay to existing packets To enable the copying of packets in both directions the TAP will need to provide two connections to NIDS
- 14. IDS in a switched network (SPAN) SPAN copies all packets (TX and RX) to the Span port Some packets are not copied (e.g. undersize/oversize packets) Can easily overload the Span port IDS is vulnerable to attack Need to use stealth mode Can affect the performance of the switch
- 15. Further reading Snort Intrusion Detection and Prevention Toolkit Brian Caswell et al Implementing Intrusion Detection Systems Tim Crothers Wikipedia – Search for IDS
- 16. Paul Green CISSP, MACS Paul is an information security practitioner, currently residing in Brisbane, Queensland. He has worked with government and financial institutions to help them understand their information security risks and identify suitable process and technical solutions to mitigate those risks. He has experience working with authentication and access control; network security; and monitoring solutions, as well as performing information security reviews and creation of security policies. Paul may be contacted through LinkedIN or via personal email : [email_address]













![Paul Green CISSP, MACS Paul is an information security practitioner, currently residing in Brisbane, Queensland. He has worked with government and financial institutions to help them understand their information security risks and identify suitable process and technical solutions to mitigate those risks. He has experience working with authentication and access control; network security; and monitoring solutions, as well as performing information security reviews and creation of security policies. Paul may be contacted through LinkedIN or via personal email : [email_address]](https://image.slidesharecdn.com/introduction-to-intrusion-detection-systems-1229416178037248-2/85/Introduction-To-Intrusion-Detection-Systems-16-320.jpg)