Introduction to Secure Sockets Layer
- 1. SSL: SECURED SOCKET LAYER Presented by: Sheikh Shaer Hassan Taj Islam Mohammad Mahfuzur Rahman Khaled Md. Imran www.nascenia.com
- 2. BACKGROUND WHY AND HOW HOW TO CHECK IN THE BROWSER.
- 3. MAIN CONCERNS SSL is a Secure Sockets Layer and SSL is the standard security technology for establishing an encrypted link between a web server and a browser. This link ensures that all data passed between the web server and browsers remain private and integral
- 4. Authentication of server How does client know who they are dealing with? Information integrity How do we know third party has not altered data en route? Change so item shipped to Darth Address information Bob’s web site Alice thinks she is at Bob’s site, but Darth is spoofing it Bob’s web site
- 5. SSL HISTORY Netscape developed The Secure Sockets Layer Protocol (SSL) in 1994, as a response to the growing concern over security on the Internet. SSL was originally developed for securing web browser and server communications.
- 6. SSL VERSION There are several versions of the SSL protocol defined. The latest version, the Transport Layer Security Protocol (TLS), is based on SSL 3.0 SSL Version 1.0 SSL Version 2.0 SSL Version 3.0 TLS Version 1.0 TLS Version 1.0 with SSL Version 3.0 compatibility
- 7. HOW IT WORKS Encryption of sensitive data like DES,RSA algorithm Sent between client and server through Certification like very sign
- 8. HOW IT WORKS IN BROWSER: HTTP www.aiub.edu
- 9. HOW IT WORKS IN BROWSER: HTTPS www.gmail.com
- 10. HOW IT WORKS IN BROWSER: HTTPS WITHOUT CERTIFICATION https://www.varsityadmission.com/
- 11. HOW IT WORKS IN BROWSER: HTTPS WITHOUT CERTIFICATION
- 12. OVERALL PROCESS AND FIRST FOUR STEPS
- 13. CERTIFICATES Web sites that deal in ecommerce must have certificates for authentication Installed at server Transmitted to client for authentication Validated using CA’s public key Client machine Browser Request for secure session Server machine Web Container (JSP, ASP) Certificate signed by CA CA
- 14. SECURE SOCKET LAYER PROTOCOL Secure Socket Layer protocol for web communication Latest upgrade: Transport Layer Security (TLS) Same structure as SSL, somewhat more secure
- 15. SSL PROTOCOL: PHASE 1 Phase 1: Information exchange Problem: Large number of encryption algorithms in use How do client and server agree on which to use? How does client tell server which ones it supports?
- 16. SSL PROTOCOL: PHASE 1 Client passes preferred algorithms to server via https request Public key encryption algorithms Private key encryption algorithms Hash algorithms Compression algorithms Also random number for key generation Server replies with algorithms that will be used Also passes own random number
- 17. SSL PROTOCOL: PHASE 2 Phase 2: Server Identification and Key Exchange Server passes their certificates to client Client uses issuer public key to verify identity Client retrieves server public key from certificate Server may pass many certificates for authentication
- 18. SSL PROTOCOL: PHASE 2 If no certificate containing a public key, separate public key must be passed Certificate contains RSA public key, so no separate key passed No certificate, so Diffie-Hellman key exchange parameters passed
- 19. SSL PROTOCOL: PHASE 2 Server can also request appropriate client certificates to authenticate client Online banking Remote access to company database
- 20. SSL PROTOCOL: PHASE 3 Phase 3: Client Identification and Key Exchange Client sends certificate or public key if requested by server
- 21. SSL KEY GENERATION Client generates “pre-master key” Sends to client encrypted with server public key Client and server use to generate master key used to create cipher keys Also use client, server random numbers exchanged in phase 1
- 24. SSL KEY GENERATION Key material used to generate: Keys for encryption and authentication (MAC) IV’s for block cipher chaining
- 25. PHASE 4: FINAL HANDSHAKE Client and server verify protocols and keys Sender signs/encrypts “finished” message Receiver decrypts/verifies message to confirm keys
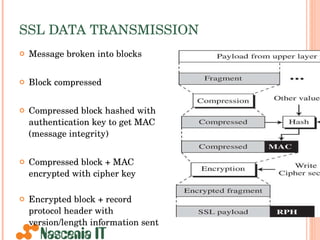
- 26. SSL DATA TRANSMISSION Message broken into blocks Block compressed Compressed block hashed with authentication key to get MAC (message integrity) Compressed block + MAC encrypted with cipher key Encrypted block + record protocol header with version/length information sent
- 27. SSL DATA TRANSMISSION MAC algorithm is modified HMAC Two stage hash with secret MAC key inserted at each stage Values similar to IPAD and OPAD also inserted
- 28. SSL DATA TRANSMISSION ALGORITHM USED CERTIFICATE]ION AUTHORITY SSL IN BANGLADESH
- 29. ALGORITHM USED DES. Data Encryption Standard, an encryption algorithm used by the U.S. Government. DSA. Digital Signature Algorithm, part of the digital authentication standard used by the U.S. Government. KEA. Key Exchange Algorithm, an algorithm used for key exchange by the U.S. Government. MD5. Message Digest algorithm developed by Rivest. RC2 and RC4 . Rivest encryption ciphers developed for RSA Data Security. RSA. A public-key algorithm for both encryption and authentication. Developed by Rivest, Shamir, and Adleman. RSA key exchange. A key-exchange algorithm for SSL based on the RSA algorithm. SHA-1. Secure Hash Algorithm, a hash function used by the U.S. Government. SKIPJACK. A classified symmetric-key algorithm implemented in FORTEZZA-compliant hardware used by the U.S. Government. (For more information, see FORTEZZA Cipher Suites.) Triple-DES. DES applied three times.
- 30. CERTIFICATION AUTHORITY 50 root certificate authority worldwide Needs to listed on browsers. Undergo annual security audit (e.g. by Webtrust). The large authorities are Verisign (acquired Thawte and Geotrust) has 48 %, GoDaddy 23%, and Combodo 15%, others 14%
- 32. IN BANGLADESH SSL Wireless provides Verisign certification: www.sslwireless.com
- 33. CODING DIFFERENT VERSIONS OF SSL
- 34. OPENSSL OpenSSL is an open source implementation of the SSL and TLS protocols. The core library (written in the C programming language) implements the basic cryptographic functions and provides various utility functions.
- 35. OVERVIEW OF SSL APPLICATION WITH OPENSSL APIS
- 36. INITIALIZATION SSL_library_init(); /* load encryption & hash algorithms for SSL */ SSL_load_error_strings(); /* load the error strings for good error reporting */ meth = SSLv3_method(); ctx = SSL_CTX_new(meth); /*creates a new SSL_CTX object as framework to establish TLS/SSL enabled connections */
- 37. CERTIFICATE VERIFICATION IN THE CLIENT SIDE err = SSL_connect(ssl); /* initiates the TLS/SSL handshake */ if(SSL_get_peer_certificate(ssl) != NULL) { if(SSL_get_verify_result(ssl) == X509_V_OK) BIO_printf(bio_c_out, "client verification with SSL_get_verify_result() succeeded.\n"); else{ BIO_printf(bio_err, "client verification with SSL_get_verify_result() failed.\n"); exit(1); } } else BIO_printf(bio_c_out, -the peer certificate was not presented.\n-);
- 38. SSL HANDSHAKE The SSL handshake is a complicated process that involves significant cryptographic key exchanges. However, the handshake can be completed by calling SSL_accept () on the SSL server and SSL_connect () on the SSL client. The SSL_accept () API waits for an SSL handshake initiation from the SSL client. On server side- err = SSL_accept(ssl); On client side- err = SSL_connect(ssl);
- 39. SSL VERSIONS Version 1.0 was never publicly released; version 2.0 was released in February 1995 but "contained a number of security flaws which ultimately led to the design of SSL version 3.0" SSL Version 1.0 SSL Version 2.0 SSL Version 3.0 TLS version 1.0 TLS version 1.1 TLS version 1.2
- 40. FLAWS OF SSL 2.0 Identical cryptographic keys are used for message authentication and encryption. SSL v2 has a weak MAC construction and relies solely on the MD5 hash function. SSL v2 does not have any protection for the handshake, meaning a man-in-the-middle downgrade attack can go undetected.
- 41. SSL VERSION 3.0 VERSUS SSL VERSION 2.0 Uses SHA-1 instead of MD5: The SHA-1 hashing algorithm is considered to be more secure than the MD5 hashing algorithm. Having SHA-1 allows SSL Version 3.0 to support additional cipher suites which use SHA-1 instead of MD5. Reduces MITM attack: SSL Version 3.0 protocol reduces man-in-the-middle (MITM) type of attacks from occurring during SSL handshake processing. In SSL Version 2.0, it was possible, though unlikely, that a MITM attack could accomplish cipher specification weakening.
- 42. SOURCES USED Cryptography and Network Security, Principles and Practices, 4 th Ed., William Stallings www.wikipedia.com A few other internet resources
- 43. THANK YOU



























![SSL DATA TRANSMISSION ALGORITHM USED CERTIFICATE]ION AUTHORITY SSL IN BANGLADESH](https://image.slidesharecdn.com/ssl-100817071829-phpapp02/85/Introduction-to-Secure-Sockets-Layer-28-320.jpg)














