iOS-Application-Security-iAmPr3m
- 1. Prem Kumar @iampr3m https://iampr3m.wordpress.com Advanced iOS Application Security
- 2. Hello Digitalsec2016! About me • Prem Kumar @iAmPr3m • Senior security consultant at Mercedes Benz Research & Development India. • Web/Mobile/Network pentesting guy. • Previously presented and trained at DISC, Null Community and other security conferences. • Bug Hunter (Synack & Hackerone) • Acknowledged and rewarded by various organizations including Facebook, Apple, Yahoo, Vimeo, Nokia, EBay, Mediafire, Barracuda Labs, Telekom and many more for finding security vulnerabilities in their applications. • Personally a huge iOS fan.
- 3. Rough Agenda We will digress! Why Mobile Security? What is iOS? Understanding iOS Architecture/Sandboxing. iOS Application Structure. Types of iOS Applications? How are they distributed? Types of iOS Pen tests What is Jailbreak? Why Jailbreak? Perquisites ! Setting up basic iOS pen test platform. iOS Transport Layer Protection iOS Insecure Local Storage iOS Side Channel Data Leakage iOS Client Side Injections Runtime Analysis? Real life Demos. How To Start on iOS Pentesting?
- 4. Introduction • The growth of mobile device usage in both personal and professional environments continues to grow • The number of mobile-connected devices grew 2.5 times to more than 36 million (2012) • Mobile devices have become a staple computing device used in our lives today. • The massive increased use in mobile devices also brings a corresponding growth in mobile applications • Developers looking to capitalize on this potential. • Research anticipates that mobile app downloads by 2017 would be a more than 253,914 million.
- 6. What is iOS? iPhone Operating System. An mobile operating system developed by Apple Inc. and distributed exclusively for Apple hardware. iOS is derived from OSX, with which it shares the Darwin foundation, and is therefore a UNIX operating system. Its an operating system that powers iPhone, iPad, iPod and Apple TV. Apple designed the iOS platform with security at its core.
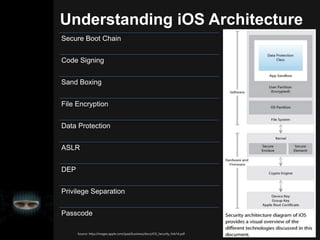
- 7. Understanding iOS Architecture Source: http://images.apple.com/ipad/business/docs/iOS_Security_Feb14.pdf Secure Boot Chain Code Signing Sand Boxing File Encryption Data Protection ASLR DEP Privilege Separation Passcode
- 8. iOS App Sandboxing Source: http://images.apple.com/ipad/business/docs/iOS_Security_Feb14.pdf All the applications running are signed by Apple Developer submits application, apple verifies it and signs the application. Applications are isolated by sandboxing One application can not access the data of the other applications Reading other application directory is not possible All applications run under user mobile All system process run under user root
- 9. iOS Application Structure Source: http://images.apple.com/ipad/business/docs/iOS_Security_Feb14.pdf iOS Applications: – In Development with Apple SDK XCode: • Distributed as XCode Project Folders – Compiled and deployed through the app store: • Compiled as ARM. • Distributed as ‘.ipa’ files. • Zip files containing app resources & ARM executable. Deployed as ‘.app’ directories Executable code is: – Encrypted with FairPlay DRM (AES) – Signed with Apple’s signature
- 10. Types of iOS Applications Web Applications HTML + CSS + JavaScript Run inside Safari/Webkit Native Applications Written in Objective-C (+ C/C++) Compiled into ARM for actual devices, x86 for iOS Simulator Hybrid Applications Combination of Web and Native applications
- 11. iPhone Application Distribution Ad-Hoc Distribution • Ad-Hoc releases have to be provisioned to specific devices. • Limited to 100 devices per membership year. • Your application does not need to be submitted for review by Apple. • Can be installed over-the-air from a web server, or via iTunes. • Provides restriction on specific devices. In-House Distribution • In-House is for distribution to any company device. •There are NO limits to the amount of devices onto which you can deploy an application •Your application does not need to be submitted for review by Apple. • It is important to note that Apple makes it very clear that In-House applications are for internal use only. Over The Air Distribution • Requires In-House provision profile. • Takes 1 minute instead of 2 weeks. • Upload the .ipa, wherever you want. • Example: Click App Store Distribution • Must be part of either an individual or organizational Apple Developer Program. • iTunes Connect, and therefore publish your app to the App Store • Two to Three weeks for approval.
- 12. How Do We Pentest iOS Apps? Whitebox Testing: • Full information. • Source code provided. Focus: Attack the network communication. Server component. Client component. Blackbox Testing : • No code or information provided. • Working only with downloadable app
- 14. Reminders Personal or Identifying Information (PII) for a mobile app can be different that what you expect. Look for: Usernames Passwords UDID Geolocation Address / Zip DOB Device Name Network Connection Name Application Data Updates to Social Media Chat logs Cookies
- 15. Other Key Areas To Focus During a Pentesting : Network communication Privacy Issues Reverse Engineering URL Schema Runtime Analysis
- 16. What is Jailbreak? The name refers to breaking the device out of its own ‘JAIL’ iOS jail breaking is the process of removing limitations on iOS. Allows installation of apps, which are not present in the AppStore. Three types of jailbreaks i.e. Tethered, Un-Tethered and Semi-Tethered. Why Jailbreak? Say hello to ‘Cydia’. Able to download additional applications, extensions, tweaks, tools etc. that are unavailable through the official Apple App Store. Jailbreaking permits root access to the iOS file system SSH !
- 17. Jailbreak History • iPhone 1.0 Jailbroken (July 10th 2007) • iOS 4.3.2 Redsn0w 0.9.11x (April 2011) • iOS 4.3.3 Jailbreakme.com remote jailbreak (July 2011) • iOS 5.1.1 Absinthe 2.0.x (May 2012) • iOS 6.1 Evasi0n (Jan 30 2013) • iOS 7.0 Evasi0n7 (Dec 2013) • iOS <7.1.2 Pangu (Jun 23 2014) • iOS <8.4 TaiG, PP Jailbreak • iOS <9.3.3 Pangu https://en.wikipedia.org/wiki/IOS_jailbreaking
- 18. How to Jailbreak? (Latest 9.3.3)
- 19. Setting Up iOS Pentesting Platform iDevice / iPhone Simulator Macbook / Windows / Linux Network Jailbreak Recommended Tools BigBoss recommended tools OpenSSH Class-Dump Clutch Cycript Appsync Keychain dumper BurpSuite iPhone Explorers etc.
- 20. SSH Into iPhone • Install Open SSH from Cydia • On workstation install SSH Client • iPhone has two users by default - Root and Mobile (Default password is ‘alpine’) • Connect to the phone as a root user via SSH SSH over WIFI > ssh root@iPhoneIP > password: alpine SSH over USB > ./itunnel_mux --lport 1234 > ssh –p 1234 [email protected] > password: alpine NOTE: Change you default SSH password. >_ SSH
- 21. Analyzing iOS Application: Dynamic Analysis • Executing an application either on the device/simulator/emulator and interacting with the remote services with which the application communicate. • Similar to testing Web application. • Test the application traffic using interception proxy and try to execute all the test cases that you generally use for web application Static Analysis • Plist Files SQLite3 Databases • Keychain Temp Files • Side Channel Data Leakage Logging • File Caching Keyboard Caching • Snapshot Caching Runtime Analysis • Runtime analysis allows an attacker to manipulate the application’s behaviour at runtime to bypass the security locks and access the sensitive information from memory. • Runtime analysis is a huge topic, Hence the very basics and some intermediate topics will be covered in this talk.
- 22. Dynamic Analysis: Clear text transmission (HTTP) • It’s 2016 and we still find apps running on ‘HTTP’. • More possible MITM attacks because of WIFI. E.g. Fire-sheep. • Requires proxy setup to intercept traffic. Encrypted transmission (HTTPS) • HTTPS is required for sensitive data transmission. • In SSL communication, Apps may fail to validate SSL cert, which will not allow MITM. • To capture the traffic, load your proxy (burp) CA Cert to iPhone. Use of Custom or Proprietary protocols • Identify the communication protocol. • On SSH Terminal: tcpdump -w *pcap • Load the .pcap in Wireshark and analyze. • May not respect iPhone proxy settings.
- 23. Setting up an Interception Proxy:
- 24. Setting up an Interception Proxy:
- 25. Dynamic Analysis: Analyze error messages Analyze cacheable information Transport layer security Attack XML processors SQL injection Privacy issues (information disclosure) Improper session handling Decisions via untrusted inputs Broken cryptography Unmanaged code URL Schemes Push notifications Authentication Authorization Session management Data storage Data validation (input, output) Transport Layer protection Denial of service Business logic UDID or MAC ID usage Once you capture the traffic it is a typical web application pentesting, in which attacks are done on the application server.
- 26. Challenges: SSL Pinning Certificate Pinning is an extra layer of security that is used by applications to ensure that the certificate provided by the remote server, is the one which is expected. By including the remote server’s x509 certificate or public key within the application, it is possible to compare the locally stored certificate or key with the one provided by the remote server. Bypassing Certificate Pinning iOS SSL Kill Switch: iOS SSL Kill Switch patches low-level SSL functions within the Secure Transport API, in order to override and disable the system's default certificate validation as well as any kind of custom certificate validation. (https://github.com/iSECPartners/ios-ssl-kill-switch) iOS TrustMe: An extreme method of disabling most certificate verification checks within iOS applications. (https://github.com/intrepidusgroup/trustme)
- 27. iOS Standard Directories • During installation of a new app, the installer creates a number of container directories for the app inside the sandbox directory like, Bundle, Data etc. • Each container directory has a specific role: • The bundle container directory holds the app’s bundle. • ‘Data Container’ directory holds data for both the app and the user. • The data container directory is further divided into a number of subdirectories that the app can use to sort and organize its data. https://developer.apple.com/library/content/documentation/FileManagement/Conceptual/FileSystemProgrammingGuide/FileSyst emOverview/FileSystemOverview.html
- 28. Commonly Used Directories https://developer.apple.com/library/content/documentation/FileManagement/Conceptual/FileSystemProgrammingGuide/FileSyst emOverview/FileSystemOverview.html AppName.app • This is the app’s bundle. • This directory contains the app and all of its resources. Documents/ • Use this directory to store user-generated content. Documents/Inbox • Use this directory to access files that your app was asked to open by outside entities. • Specifically, the Mail program places email attachments associated with your app in this directory. Library/ • This is the top-level directory for any files that are not user data files. tmp/ • Use this directory to write temporary files that do not need to persist between launches of your app.
- 29. Tips & Tricks To Locate App Folders • Apple has a history of changing the paths of application containers, with their new firmware releases. • find / -type d -iname "*.app“ • find / -type d -iname "*.app“ | grep “AppName” • cd /private/var/containers/Bundle/Application/; ls * Locating App Bundle Containers: (iOS 9.*) Locating Data Containers: (iOS 9.*) • By default, the application data container reside in the following path: ~/var/mobile/Containers/Data/Application/ • Navigate to the above path and run the following command: • find /var/mobile/Containers/Data/Application/ -iname "*AppName"
- 30. Static Analysis: • Decrypt the application • Investigate property list files • Analyze iOS keychain • Analyze SQLlite database • Analyze NSUserdefault files etc. • Check for sensitive information in snapshots • Investigate file caching • Insecure data storage in Keyboard and Pasteboard cache • Investigate Cookies.binarycookies Side Channel Data Leakage:
- 31. Decrypting an iOS Application Clutch: • Clutch is a high-speed iOS decryption tool. • Clutch supports the iPhone, iPod Touch, and iPad as well as all iOS version • Loader decrypts app • Clutch sets a breakpoint in loading process • Dumps app from memory
- 32. Decrypting an iOS Application Class-Dump: • Command-line utility for examining the Objective-C runtime information. • From a given executable, ‘class-dump’ and ‘class_dump_z’ will generate header files with class interfaces. • This allows for an analysis of what methods exist in the executable, which can help you guess which ones to hook to get given functionality.
- 33. Plist files • Property list files - /private/var/containers/Bundle/ Application/ - Often used to store user’s properties • Key value pairs are stored in binary format • Easily extracted and modified with property list editor, plutil etc. • Look for usernames , passwords, cookies. • Apps may take Authentication/Authorization decisions • Ex: admin=1, timeout=10 • Plist files can be viewed and modified easily on both the Jailbroken and non Jailbroken iPhones. “An information property list file is a structured text file that contains essential configuration information for a bundled executable”
- 34. Keychain • SQLite database for sensitive data storage • Four tables: genp, inet, cert, keys • Located at: /var/Keychains/keychain-2.db • Keychain data is encrypted - Uses hardware encryption key - Uses user passcode for encryption - Depends on accessibility constant of keychain entry - Can not be moved to other device • Accessible to all the applications. • Application can only access it’s key chain items - On a Jailbroken device It can be bypassed • Keychain Dumper Tool – by github - Displays keychain entries of all the installed applications • Keychain data is encrypted with User Passcode
- 35. Cookies.binarycookies • On the iPhone, Safari browser and third party iOS applications store the cookies in ‘Cookies.binarycookies’ files located at the path shown below: - /ApplicationDirectory/Library/Cookies/ - /private/var/mobile/Library/ • Cookies created only with the future expiration date (persistent cookies) are stored in the binary Cookies.binarycookies file. • “BinaryCookieReader.py” by Satish Bommisetty.
- 36. Side Channel Data Leakage Logging Files • Apps may write sensitive data in logs. • Trouble shooting • Requests & Responses • /private/var/log/syslog Caching • File Caching • Keyboard Caching • Snapshot Caching • Clipboard Caching iOS apps have a number of ‘features’ that can be security vulnerabilities.
- 37. File Caching • If the application uses PDF, Excel, or other files it may be possible that these files may have been cached on the device. These can be found at : ~/<ApplicationDirectory>/Documents/temp.pdf Keyboard Caching • Keystrokes for predictive spellcheck are stored in: ~/private/var/mobile/Library/Keyboard/dynamic-text.dat • This issue is similar to autocomplete for web browsers.
- 38. Snapshot Caching • On minimizing the iOS application, the screen shrinks and moves the application to the background. • To create that shrinking effect, iOS takes a snapshot of the application and stores it in the '/Library/Caches/Snapshots/' folder of the application’s home directory. • This might result in storing the user’s sensitive information on the device which could be accessed by a malicious application. • These persist until reboot.
- 39. URI Schema: iOS URL Schemes in general allow one App to be opened by other Apps, or essentially inter-app communication. Specific actions can be defined to not only open a URL, but populate what it is you’d like to search, for example coordinates, local donut shops, and much more. Here's an example: tel://1-393-222-2222 Got a Problem? Apple does not enforce the unique naming for App schemes. Insecure URI Schema Handling iOS MASQUE Attack. iOS URL Scheme Hijacking (XARA) Attack
- 40. Insecure URI Schema Handling on Facebook
- 42. Runtime Analysis: Runtime analysis allows an attacker to manipulate the application’s behaviour during the runtime. For example, Runtime analysis can be used for analysing and bypassing client side securities implemented by an application like security locks and access the sensitive information from memory. • Cycript is an implementation of JavaScript that can interact with Objective-C classes and objects. • With Cycript, you can manipulate existing objects already in your application’s memory, or instantiate new objects, such as new view controller classes or windows. • The tool works by hooking into the process of the running app by passing the ‘-p’ flag to Cycript, followed by the app name. Cycript:
- 43. Bypassing Passcode Lock on QIWI App
- 44. How to get started? “Damn Vulnerable iOS App (DVIA) is an iOS application that is damn vulnerable. Its main goal is to provide a platform to mobile security enthusiasts/professionals or students to test their iOS penetration testing skills in a legal environment.” • Most of the vulnerabilities, discussed today can be found in this application. • Detailed step by step approach on pentesting iOS application. • http://damnvulnerableiosapp.com/
- 45. References: • Pentesting iOS Application by ‘Jason Haddix’ • Penetration Testing for iPhone Applications by ‘Satish Bommisetty’ • iPwn Apps: Pentesting iOS Applications • BlackHat 2011 - DaiZovi_iOS_Security • Learning iOS Penetration Testing by Swaroop Yermalkar. • Damn Vulnerable iOS Application (DVIA) by ‘Prateek Gianchandani’.
Editor's Notes
- #5: Mobile technology has come a long way in a relatively short space of time. In less than 30 years we’ve moved away from big, brick-like cellular phones and a nascent internet to a world of super-slim and powerful smartphones, tablets and convertible laptops that are able to transmit and store data, as well as hook up the internet, with a simple tap. While these devices offer us increased internet connectivity and day-to-day convenience, they also carry considerable security risks. In this feature we take a look the reasons behind the growing threat of mobile-related cybercrime. And cybercriminals know this. As a result, they were shifting their focus and efforts to smartphones and tablets, appreciative of the fact that they can possibly steal more money and data from their victims this way.
- #6: Mobile technology has come a long way in a relatively short space of time. In less than 30 years we’ve moved away from big, brick-like cellular phones and a nascent internet to a world of super-slim and powerful smartphones, tablets and convertible laptops that are able to transmit and store data, as well as hook up the internet, with a simple tap. While these devices offer us increased internet connectivity and day-to-day convenience, they also carry considerable security risks. In this feature we take a look the reasons behind the growing threat of mobile-related cybercrime. And cybercriminals know this. As a result, they were shifting their focus and efforts to smartphones and tablets, appreciative of the fact that they can possibly steal more money and data from their victims this way.
- #13: Three areas to focus on: Attack the network communication Attack the server component Attack the client component
- #14: Three areas to focus on: Attack the network communication Attack the server component Attack the client component
- #15: Three areas to focus on: Attack the network communication Attack the server component Attack the client component
- #16: Three areas to focus on: Attack the network communication Attack the server component Attack the client component
- #17: Three areas to focus on: Attack the network communication Attack the server component Attack the client component
- #18: Three areas to focus on: Attack the network communication Attack the server component Attack the client component
- #19: Three areas to focus on: Attack the network communication Attack the server component Attack the client component
- #20: Three areas to focus on: Attack the network communication Attack the server component Attack the client component
- #21: Three areas to focus on: Attack the network communication Attack the server component Attack the client component
- #22: Three areas to focus on: Attack the network communication Attack the server component Attack the client component
- #23: Three areas to focus on: Attack the network communication Attack the server component Attack the client component
- #24: Three areas to focus on: Attack the network communication Attack the server component Attack the client component
- #25: Three areas to focus on: Attack the network communication Attack the server component Attack the client component
- #26: Three areas to focus on: Attack the network communication Attack the server component Attack the client component
- #27: Three areas to focus on: Attack the network communication Attack the server component Attack the client component
- #28: Three areas to focus on: Attack the network communication Attack the server component Attack the client component
- #29: Three areas to focus on: Attack the network communication Attack the server component Attack the client component
- #30: Three areas to focus on: Attack the network communication Attack the server component Attack the client component
- #31: Three areas to focus on: Attack the network communication Attack the server component Attack the client component
- #32: Three areas to focus on: Attack the network communication Attack the server component Attack the client component
- #33: Three areas to focus on: Attack the network communication Attack the server component Attack the client component
- #34: Three areas to focus on: Attack the network communication Attack the server component Attack the client component
- #35: Three areas to focus on: Attack the network communication Attack the server component Attack the client component
- #36: Three areas to focus on: Attack the network communication Attack the server component Attack the client component
- #37: Three areas to focus on: Attack the network communication Attack the server component Attack the client component
- #38: Three areas to focus on: Attack the network communication Attack the server component Attack the client component
- #39: Three areas to focus on: Attack the network communication Attack the server component Attack the client component
- #40: Three areas to focus on: Attack the network communication Attack the server component Attack the client component
- #41: Three areas to focus on: Attack the network communication Attack the server component Attack the client component
- #42: Three areas to focus on: Attack the network communication Attack the server component Attack the client component
- #43: Three areas to focus on: Attack the network communication Attack the server component Attack the client component
- #44: Three areas to focus on: Attack the network communication Attack the server component Attack the client component
- #45: Three areas to focus on: Attack the network communication Attack the server component Attack the client component
- #46: Three areas to focus on: Attack the network communication Attack the server component Attack the client component