Layer8 exploitation: Lock'n Load Target
- 1. www.cdicconference.com “Is Your Privacy at Risk? Security and Privacy Challenges in the Digital Modernity” อ. ประธาน พงศ์ทิพย์ฤกษ์ SANS GIAC GPEN, eCPPT, ECSA, CEH, CPTS, CIW Security Analyst, CWNA, CWSP, Security+, ITIL-F Section Manager, Senior Information Security Consultant อ. สุทธาพงศ์ วราอัศวปติ Information Security Consultant 1
- 2. Let’s Talk Layer 8 Exploitation Lock’n Load Target Automated Exploitation 2 2
- 3. Layer 8 Exploitation 3 3
- 4. Types of Hacking Network services Web Application / Mobile Application Remote dial-up war dial Wireless Security Social Engineering Physical Security Cryptanalysis Client Side (Layer 8) 4 4
- 5. Client-side Hacking Client-side Software + Social Engineering “There is no patch for stupid” Client-side software Web browsers Media Players Microsoft Office Adobe Reader Java runtime environment Flash player Etc 5 5
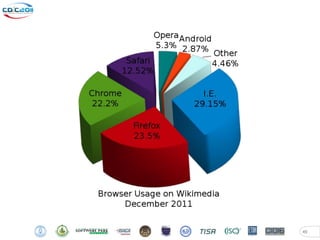
- 6. Web Browser Security Fight !! 6 11
- 7. Google Hands out $60k 7 12
- 8. PWN2OWN 2012 Hacking Contest 8 13
- 9. No software is unbreakable! 9 14
- 10. PWN2OWN: Result Google Chrome is the first browser to fail at pwn2own Bypass DEP/ASLR Bypass Sandbox Internet Explorer 9 is the second browser It will work on IE6-10 on Window 8 Firefox 10.0.2 is the Third browser Bypass DEP/ASLR Heap spray Exploit 10 15
- 11. Lock’n Load Target 11 16
- 12. Lock the target Information gathering Social Networking Job Requisition Document Metadata Harvesting Email Social Engineering Spear Phishing 12 17
- 13. LinkedIn Search 13 18
- 14. Job Requisition 14 19
- 15. Document Metadata Most document formats include a significant amount of metadata (data about data) Information sometimes included in metadata Usernames Operating Systems Network info Internal Server info Device info Software version 15 20
- 16. Document Types that are Rich in Metadata Most types of documents have some metadata in them, but the following types are often especially interesting 16 21
- 17. Exif Tool 17 22
- 18. Libextractor Tool 18 23
- 19. FOCA Tool 19 24
- 20. FOCA: Case Study 20 25
- 21. FOCA: Case Study 21 26
- 22. FOCA: Case Study 22 27
- 23. FOCA: Case Study 23 28
- 24. Harvesting Email 24 29
- 25. Spear Phishing 25 30
- 26. Intranet Internet 31 26
- 27. Protection ? User Awareness Training Security Policy Clean all public documents 27
- 28. Clean your documents: MSoffice 2k7 28
- 29. Clean your documents: MSoffice 2k7 29
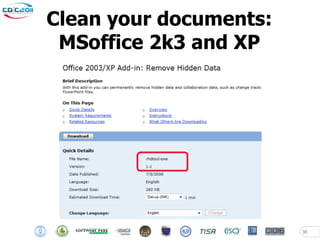
- 30. Clean your documents: MSoffice 2k3 and XP 30
- 31. Automated Exploitation 31 32
- 32. Blackbox Hacking 32 33
- 33. Old Style Hacking 33 34
- 34. New Style Hacking 34 34
- 35. Hacking Object 35 35
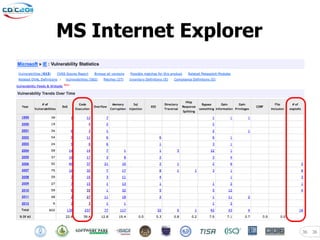
- 36. MS Internet Explorer 36 36
- 37. Opera Opera 37 37
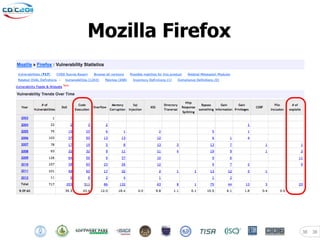
- 38. Mozilla Firefox 38 38
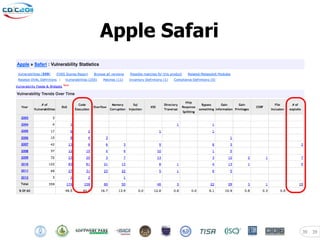
- 39. Apple Safari 39 39
- 40. Google Chrome 40 40
- 41. 41 41
- 42. CVE-2010-1349 Opera 10.10, 10.50 on Windows CVE-2011-1260 IE6, IE7, IE8 MS11-050 2000, 2003, XP, Vista, 7 CVE-2011-0065 Firefox 3.5.19, 3.6.17 42 42
- 43. CVE-2011-0611 Adobe flash player 10.2.154.27 Adobe reader 10.0.2 CVE-2011-3544 Java 6 update 27 Java 7 43 43
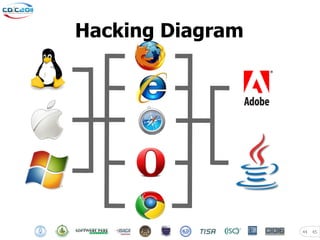
- 44. Hacking Diagram 44 45
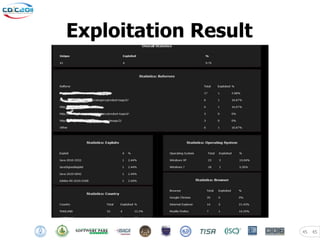
- 45. Exploitation Result 45 45
- 46. 46
- 47. 47
- 48. 48
- 49. 49
- 50. Exploitation Demonstration 50 45
- 51. How to Avoid Automate Exploitation? 51 20
- 52. Thank You www.cdicconference.com 52 34