Lecture5
- 1. Security Concepts And Security Concepts And Web Security Web Security IT1 Course Slide Instructor: Majid Taghiloo
- 2. What will we cover in this course? • Introduction to Computer I t d ti t C t • Secure Sockets Layer k Security – IT Environment, • IP Security Threats and Goals of Computer and Network Security • Virtual Private Networks • Encryption and Cryptography • Malicious Programs, Viruses and • Symmetric Encryption Algorithms Virus Protection Strategies – DES • Fault Tolerance and RAID and UPS • Asymmetric Encryption Systems Algorithms – RSA • Data Backups • Digital Signatures and Message • Email Security Authentication • Pseudo random Pseudo‐random Number • Firewalls Generation and its Computational • Windows NT Security Complexity – CSPRNG • UNIX/Linux Security 2
- 3. What is Computer Security? • The protection afforded to an automated information system in order to attain the y applicable objectives of preserving the integrity, integrity availability and confidentiality of information system resources (includes hardware, software firmware hardware software, firmware, information/data, and telecommunications) is called Computer Security. 3
- 4. What is Computer Security? • For some Computer Security is controlling access to For some Computer Security is controlling access to hardware, software and data of a computerized system. • A large measure of computer security is simply keeping the computer system s information secure. computer system's information secure • In broader terms, computer security can be thought of as the protection of the computer and its resources against accidental or intentional disclosure of confidential data, accidental or intentional disclosure of confidential data unlawful modification of data or programs, the destruction of data, software or hardware. • C Computer security also includes the denial of use of one’s t it l i l d th d i l f f ’ computer facilities for criminal activities including computer related fraud and blackmail. • Finally, computer security involves the elimination of weaknesses or vulnerabilities that might be exploited to cause loss or harm. 4
- 5. Let us start with a story story… • The Story of New Jersey Bankers is a famous one. • It shows how naive people are about security issues. issues 5
- 6. The Need for Computer Security • Why the need for Computer Security? – The value of computer assets and services p • What is the new IT environment? –NNetworks and distributed applications/services k d di ib d li i / i – Electronic Commerce (E‐commerce, E‐business) 6
- 7. The Value of Computer Assets and Services • Most companies use electronic information extensively to support their daily business processes. • Data is stored on customers, products, contracts, financial results, accounting etc. • If this electronic information were to become available to competitors or to become corrupted false or corrupted, disappear, what would happen? What would the consequences be? Could the business still function? 7
- 8. Network Security Issues • “Th “The network is the computer” t k i th t ” • Proliferation of networks has increased security risks much more more. • Sharing of resources increases complexity of system. • Unknown perimeter (linked networks), unknown networks) path. • Many points of attack attack. • Computer security has to find answers to network security problems. yp • Hence today the field is called Computer and Network Security. 8
- 9. Is there a Security Problem in Computing? • Computer fraud in the U.S. alone exceeds $ billion each $3 year. • Less than 1% of all computer fraud cases are detected over 90% of all computer crime goes unreported. • “Although no one is sure how much is lost to EFT crime annually, the consensus is that the losses run in the billions of dollars. Yet few in the financial community are paying any heed.” • Average computer bank theft amounts to $1.5 million. 9
- 10. Computer Crimes ... • O Over 25% of all F f ll Fortune 500 corporations h i have b been victimized by computer crime with an average loss of $2‐ 10 million million. • Total estimated losses due to computer crime range from $300 million to $500 billion per year year. • Computer‐related crime has been escalating at a dramatic rate. • Computer crimes continue to grow and plague companies. • Computer crime is almost inevitable in any organization unless adequate p q protections are p in p put place. 10
- 11. Data From Real World • The following figures are included (source: Datapro Research) as example, to give an idea what i going on i th real world. h t is i in the l ld • Common Causes of damage: Human Error 52%, Dishonest people 10% Technical Sabotage 10% Fire 15% Water 10% 10%, 10%, 15%, and Terrorism 3%. • Who causes damage? Current employees 81%, Outsiders g p y , 13%, Former employees 6%. • Types of computer crime: Money theft 44%, Damage of software 16% Theft of information 16% Alteration of data 16%, 16%, 12%, Theft of services 10%, Trespass 2%. 11
- 12. Computer Viruses • 53% of BYTE readers h % f d have suffered l ff d losses of f data that cost an average of $14,000 per occurrence. • There are over 3000 viruses with new ones developed daily. • A survey of over 600 companies and government agencies in the U.S. and Canada shows that 63% found at least one virus on their PCs last year. 12
- 13. Natural Disasters – Another Dimension • Milli Millions of d ll of d f dollars f damage resulted f lt d from th 1989 the San Francisco earthquake. • The fire at Subang International Airport knocked out the computers controlling the flight display system. A post office near the Computer Room was also affected by the soot which decommissioned the post office counter terminals. According to the caretaker, the computers were not burnt but crashed because soot entered the hard disks. • Fire, Earthquakes, Floods, Electrical hazards, etc. • How to prevent? 13
- 14. Negligence ‐ The Human Factor • Over 85% of the destruction of valuable computer data involves inadvertent acts. p • How to prevent? –PProper user training t i i – Idiot proofing 14
- 15. Computer Security Requirements • Secrecy • Integrity • Availability • Authenticity • Non repudiation Non‐repudiation • Access control 15
- 16. Secrecy (Confidentiality) • Secrecy requires that the information in a computer system only be accessible for p y y reading by authorized parties. • This type of access includes: – Printing – Displaying – Other forms of disclosure, including simply , g py revealing the existing of an object 16
- 17. Integrity • Integrity requires that the computer system i i h h asset can be modified only by authorized parties. • Modification includes: – Writing – Changing – Changing status – Deleting and – Creating 17
- 18. More About Integrity • Integrity: In lay usage, information has integrity when it is timely, accurate, complete, and consistent. However, computers are unable t provide or protect all of th bl to id t t ll f these qualities. Th f liti Therefore, iin the computer security field, integrity is often discussed more narrowly as having two data integrity and system integrity data integrity system integrity. • “Data integrity is a requirement that information and programs are changed only in a specified and authorized manner.” g y p • System integrity is a requirement that a system “performs its intended function in an unimpaired manner, free from deliberate or inadvertent unauthorized manipulation of the system.” • The definition of integrity has been, and continues to be, the subject of much debate among computer security experts. 18
- 19. Availability • Availability requires that computer system assets are available to authorized parties. p • Availability is a requirement intended to assure that systems work promptly and service is not denied to authorized users. 19
- 20. Security of Data Data Data Data Confidentiality Integrity Availability Data 20 Secure Data
- 21. Authenticity • Authenticity means that parties i a h i i h i in information services can ascertain the identity of parties trying to access information services. • Also means that the origin of the message is certain. • Therefore two types: – Principal Authentication – Message Authentication 21
- 22. Non‐repudiation Non repudiation • O i i t of communications can’t d Originator f i ti ’t deny it later. • Wi h Without non‐repudiation you could place an di i ld l order for 1 million dollars of equipment online and then simply deny it later later. • Or you could send an email inviting a friend to the dinner and then disclaim it later later. • Non‐repudiation associates the identity of the originator with th t i i t ith the transaction i a non‐ ti in deniable way. 22
- 23. Access Control • Unauthorized users are k h i d kept out of the system. f h • Unauthorized users are kept out of places on the system/disk. • Typically makes use of Directories or Access yp y Control Lists (ACLs) or Access Control Matrix • Objects: Resources that need to be protected • Subjects: Entities that need access to resources • Rights: Permissions • Each entry is a triple <subject, object, rights> 23
- 24. Access Control Matrix OBJECT 1 OBJECT 2 OBJECT 3 OBJECT 4 SUBJECT 1 ORW ORW R X SUBJECT 2 R RW R R SUBJECT 3 X X ORW ORW SUBJECT 4 R R R RW SUBJECT N X R R X 24
- 26. Security Requirements are often Combined • For example: Confidentiality y • User authentication a thentication used for access authorization control purposes in p p confidentiality. • Non repudiation is Non‐repudiation Integrity Availability combined with authentication. h 26
- 27. Type of Attacks/Threats in Computer Systems • A th t i a d threat is danger which could affect th hi h ld ff t the security (confidentiality, integrity, availability) of assets, leading to a potential loss or damage. • Interruption • Interception • Modification • Fabrication 27
- 28. Type of Attacks in Computer Systems 28
- 29. Normal Flow of Information 29
- 30. Interruption • An asset of the system i d f h is destroyed or d becomes unavailable or unusable. This is an attack on the availability. • Examples include destruction of a p p piece of hardware, such as a hard disk, the cutting of a communication link, or the disabling of the file , g management system. • DOS ‐ Denial of Service Attacks have become very well known. 30
- 31. Interruption 31
- 32. Interception • Information di l f i disclosure/information l k /i f i leakage • An unauthorized party gains access to an p yg asset. • This is an attack on confidentiality confidentiality. • The unauthorized party could be a person, a program, program or a computer. computer • Examples include: – wiretapping to capture data in a network – the illicit copying of files or programs py g p g 32
- 33. Interception 33
- 34. Modification • Modification is integrity violation. • An unauthorized party not only gains access to but tampers with an asset. • Thi i an attack on the i This is k h integrity. i • Examples include changing values in a data p g g file, altering a program so that it performs differently, differently and modifying the content of a message being transmitted in a network. 34
- 35. Modification 35
- 36. Fabrication • An unauthorized party inserts counterfeit objects into the system. This is an attack on j y the authenticity. • Examples include the insertion of spurious messages in a network or the addition of records to a f l file. 36
- 37. Fabrication 37
- 38. Classification of Attacks • Computer Security attacks can be classified g into two broad categories: – Passive Attacks can only observe communications or data. – Active Attacks can actively modify communications or data Often difficult to data. perform, but very powerful. Examples include • Mail forgery/modification • TCP/IP spoofing/session hijacking 38
- 39. Passive Attacks and Active Attacks 39
- 40. Passive Attacks and Active Attacks 40
- 41. Passive Attacks • Eavesdropping on or monitoring of transmission. • The goal of the opponent is to obtain information that is being transmitted transmitted. • Two types: – Release‐of‐message contents – Traffic Analysis 41
- 42. Release‐of‐message Release of message Contents • Opponent finds out the contents or the actual messages being transmitted. g g • How to protect? –EEncryption ti – Steganography 42
- 43. Traffic Analysis • More subtle than release‐of‐message contents. • Messages may be kept secret by masking or g y p y g encryption but … • The opponent figures out information being carried by the messages based on the frequency and timings of th message. d ti i f the • How to protect? – Data/Message Padding – Filler Sequences q 43
- 44. Passive Attacks Problems • Difficult to detect because there is no modification of data. • Protection approach should be based on prevention rather than detection detection. 44
- 45. Active Attacks • Active attacks involve some sort of modification of the data stream or the creation of a false stream. • Four sub categories: sub‐categories: – Masquerade – Replay – Modification of Messages g – Denial of service 45
- 46. Masquerade • An entity pretends to be another. • For the purpose of doing some other form of attack. • E Example a system claims i IP address to b l l i its dd be what it is not, IP spoofing. • How to protect? – Principal/Entity Authentication 46
- 47. Replay • First passive capture of d i i f data and then i d h its retransmission to produce an unauthorized effect. • Could be disastrous in case of critical messages such as authentication sequences, even if the password were encrypted. p yp • How to protect? – Time stamps – Sequence Numbers 47
- 48. Modification of Messages • Some portion of a legitimate message is altered or messages are delayed or reordered g y to produce an unauthorized effect. • How to protect? – Message Authentication Codes – Chaining 48
- 49. Denial of Service ‐ DOS • P Prevents the normal use or management of t th l t f communication facilities. • S h attacks h Such k have b become very common on the Internet especially against web servers. • On the Internet remotely l h l located h k can d hackers crash the TCP/IP software by exploiting known vulnerabilities in various implementations. implementations • One has to constantly look out for software updates and security patches t protect d t d it t h to t t against these attacks. 49
- 50. Problems with Active Attacks • Easy to detect but difficult to prevent. • Efforts are directed to quickly recover from disruption or delays. • G d thing i that d Good hi is h detection will h i ill have a deterrent effect. 50
- 51. How Threats Affect Computer Systems Interruption Interception (Denial of Service) (Theft) HARDWARE Interruption Interception (Deletion) (Theft) SOFTWARE Modification (Malicious Code) Interruption Interception (Loss) (Eavesdropping) ( pp g) DATA 51 Modification Fabrication
- 52. A Model for Network Security 52
- 53. Security Protocols • A protocol i a series of steps, i l i two or more l is i f involving parties, designed to accomplish a task. –EEvery one i l d i a protocol must k involved in t l t know th protocol the t l and all of the steps to follow in advance. – Everyone involved in the protocols must agree to follow it it. – The protocol must be unambiguous; each step must be well defined and there must be no chance of misunderstanding. – The protocol must be complete; there must be a specified action for every possible situation. situation – It should not be possible to do more or learn more than what is specified in the p p protocol. 53
- 54. The Actors in Security Protocols • Alice l First participant in all the protocols ll h l • Bob Second participant in all the protocols • Caroll Participant in three‐ and f h d four‐party protocols l • Dave Participant in four‐party protocols • Eve Eavesdropper d • Mallory Malicious active intruder • Trent Trusted arbitrator d bi • Victor Verifier • Peggy P Prover P • Walter Warden; he’ll be guarding Alice and Bob in some protocols 54
- 55. Security Protocol Trent Types Alice Bob • A bi Arbitrated P d Protocols l • Adjudicated Protocols • Self Enforcing (a) Arbitrated Protocol Protocols Alice Bob Trent • Example Protocols – Key Exchange Protocols – Authentication (After the fact) Protocols Evidence Evidence – Time stamping Service (b) Adjudicated Protocol Alice Bob – Digital Cash 55 (c) Self-enforcing Protocol
- 56. Application Email - S/MIME Application Security Presentation Presentation Protocol Layers Session SSL Session Transport Transport The further down you go, Network IPSec Network the more Datalink PPP - ECP Datalink transparent it is Physical Physical The further up you go the go, Encrypting Encrypting easier it is to NIC PHYSICAL NETWORK NIC deploy 56
- 57. Security Services Provided by Security Protocols • A Access control: P t t against unauthorized t l Protects i t th i d use. • A h i i Authentication: Provides assurance of P id f someone's identity. • Confidentiality: Protects against d l fid i li disclosure to unauthorized identities. • Integrity: Protects from unauthorized data alteration. • Non‐repudiation: Protects against originator of communications later denying it. 57
- 58. Security Mechanisms • Th Three b i b ildi bl k are used: basic building blocks d – Encryption is used to provide confidentiality, can provide authentication and integrity protection protection. – Digital signatures are used to provide authentication, authentication integrity protection and non‐ protection, non repudiation. – Checksums/hash algorithms are used to provide / g p integrity protection, can provide authentication. • One or more security mechanisms are y combined to provide a security service/protocol. 58
- 59. Services, Mechanisms Services Mechanisms, Algorithms • A typical security protocol provides one or i l i l id more security services (authentication, secrecy, integrity, etc.) • Services are built from mechanisms. • Mechanisms are implemented using algorithms. algorithms SSL Services S i (Security Protocols) Signatures Encryption Hashing Mechanisms DSA RSA RSA DES SHA1 MD5 Algorithms 59
- 60. Services, Mechanisms Services Mechanisms, Algorithms Security Protocols (Services) Proprietary Security Standards-based Security Protocols Protocols PrivateWi SSL IPSec Big Brother re Mechanisms Key Encryption yp Signature g Hashing g Exchange E h Algorithms Symmetr Asymmet Asymmetr Symmetri ic ric ic c MD-5 Diffie- DES RSA DSA DESMA SHA 1 SHA-1 Hellman AES ECC RSA C 60
- 61. Encryption and Security • Encryption is a key enabling technology to implement computer security. p p y • But Encryption is to security like bricks are to buildings. buildings • In the next module we will study encryption in detail. 61
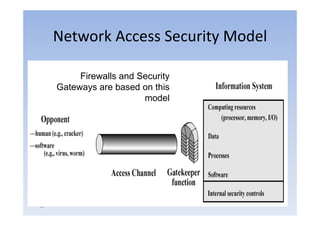
- 62. Network Access Security Model Firewalls and Security Gateways are based on this model 62
- 63. Computer security is based on eight major elements: 1. Computer security should support the mission of the organization. 2. 2 Computer security is an integral element of sound management. 3. Computer security should be cost‐effective. p y 4. Computer security responsibilities and accountability should be made explicit. 5. S System owners h have computer security responsibilities i ibili i outside their own organizations. 6. 6 Computer security requires a comprehensive and integrated approach. 7. Computer security should be periodically reassessed. 8. Computer security is constrained by societal factors. 63
- 64. Usability and Security ∝ Determine where on this line your organization needs lie Convenience / Usability 0 Security ∝ 64
- 65. Typical Security Solutions and Technologies • Physical Ph i l securityi • U authentication User h i i • Encryption • Passwords and • Access controll passphrases h • Automatic call back • Challenge‐response • Node authentication systems • Differentiated access • Token or smart cards rights i ht • Exchange of secret • Antivirus software protocol • P bli K I f t t Public Key Infrastructure • Personal characteristics • Firewalls ‐ Biometrics 65