Linux network tools (Maarten Blomme)
- 1. Linux network tools ● Theory ● Configuration ● Basic tools ● Network analysis ● Network services
- 2. 2 Theory: OSI model Application space ● Layer 7: application protocol ● Layer 5/6: optional Kernel IP stack ● Layer 4: – UDP: connectionless – TCP: stateful ● Layer 3 (IP layer): – Top layer for routers – Possibly multiple IP addresses per network interface ● Layer 2 (MAC layer): – Top layer for switches – One MAC address per physical interface ● Layer 1: electrical specifications – Top layer for hubs and modems – WiFi – Ethernet port / cable
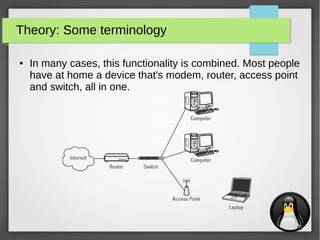
- 3. 3 Theory: Some terminology Modem (layer 1) ● A modem is a device that translates between different technologies Repeater (layer 1) ● A repeater is a device that repeats (amplifies) an existing network connection Hub (layer 2) ● A hub is a 'dumb' device that connects wired network devices, every device connected to a hub sees all traffic passing on the network Access point (layer 2) ● An access point can be seen as a wireless hub, it provides access to the network for wireless clients
- 4. 4 Theory: Some terminology Switch (layer 2) ● A switch is an 'intelligent' hub, it passes only traffic that is destined for a specific device, based on it's MAC address ● There are also so called “level 3” or “level 4” switches, they add some extra features that are based on functionality in the network or transport layer Bridge (layer 2) ● A bridge can be compared to a switch, but it is less advanced and less powerfull Router (layer 3) ● A router does not connect network devices, it connects different networks (eg. your internal home network and the internet) ● It does this based on the IP addresses
- 5. 5 Theory: Some terminology ● In many cases, this functionality is combined. Most people have at home a device that's modem, router, access point and switch, all in one.
- 6. 6 Theory: Level 2: MAC Addresses ● MAC: Media Access Control ● 00:14:c1:43:9d:fb – First three numbers: vendor id – Last three numbers: serial number ● Broadcast: ff:ff:ff:ff:ff:ff ● Used to regulate network traffic on level 2
- 7. 7 Theory: Level 3: IP Addresses ● IP: Internet Protocol – Most used: IPv4 – New: IPv6 ● 192.168.0.5 – Netmask is used to determine to which network the IP address belongs: 255.255.255.0 (or /24) ● Broadcast depends on netmask: 192.255.255.255 ● Used to regulate network traffic on level 3
- 8. 8 Configuration: IP settings ● Most modern linux distributions use NetworkManager service as a backend to configure the network ● On Debian based distros, the network can be configured in /etc/network/interfaces as a simple fallback ● On Red Hat based distros, this can be done in /etc/sysconfig/network ● ifconfig or ip can be used to configure the network manually, but these settings are gone once you reboot
- 9. 9 Configuration: DNS ● Domain Name Service is used to convert server names in IP addresses ● DNS servers are configured in the file /etc/resolv.conf $ cat /etc/resolv.conf nameserver 8.8.8.8 ● Normally you would just use the DNS server received by your router, but you can improve your internet access by changing this to a public server like 8.8.8.8 or 8.8.4.4. These servers, maintained by Google, normally respond faster and do not filter any results (eg. thepiratebay.org). ● You edit the file /etc/hosts to override or add server names
- 10. 10 Configuration: ifconfig ● With ifconfig you can configure a network interface ● On linux it is possible to create virtual network interfaces for different networks ● Configure a virtual network on your wired network interface with a static IP (make sure you all use a different IP!) and check the results $ ifconfig eth0:1 192.168.0.10 $ ifconfig ● You should see your real wired network interface has a dynamic address received via DHCP and the virtual interface has the static address you configured
- 11. 11 Basic tools: arp ● To know what MAC address corresponds with a certain IP address, the Address Resolution Protocol is used ● ARP requests are automatically send by linux whenever you try to connect with a certain IP ● Linux keeps a ARP cache table that can be viewed and modified with the arp command: $ arp Address HWtype HWaddress Flags Mask Iface 192.168.5.1 ether 00:23:48:c7:64:81 C eth0 ● You can clear the table, delete or add entries manually. The ARP cache table is cleared after a certain time.
- 12. 12 Basic tools: ping ● ping is a tool that used ICMP echo requests to detect if a host is alive ● ICMP traffic can be blocked, so this is not 100% reliable ● ping has a lot of options to modify it's behavior, you can change the interval, number of pings, network interface, … ● Example: first look at the ARP table, then ping a host, then check the ARP table again $ arp Address HWtype HWaddress Flags Mask Iface $ ping 192.168.0.1 PING 192.168.0.10 (192.168.0.10) 56(84) bytes of data. 64 bytes from 192.168.0.10: icmp_seq=1 ttl=64 time=0.774 ms $ arp Address HWtype HWaddress Flags Mask Iface 192.168.0.1 ether b4:b5:2f:cc:a1:08 C eth0
- 13. 13 Basic tools: route ● To connecting to different networks (eg. from the local network to the internet), linux uses a routing table to know where to send what packets ● You can view and change this routing table with the route command Kernel IP routing table Destination Gateway Genmask Flags Metric Ref Use Iface default 10.25.32.1 0.0.0.0 UG 0 0 0 eth0 10.25.0.0 * 255.255.0.0 U 0 0 0 eth0 192.168.0.0 * 255.255.255.0 U 0 0 0 eth0 ● There is a default gateway (10.25.32.1) defined for all traffic that is for an unknown network ● Data for 10.25.x.x and 192.168.0.x (see masks) goes to eth0 ● By configuring eth0:1 with 192.168.0.10, linux added an entry to the routing table
- 14. 14 Basic tools: traceroute ● Use the traceroute command to see what path a packet takes to a certain destination: $ traceroute 172.21.1.6 traceroute to 172.21.1.6 (172.21.1.6), 30 hops max, 60 byte packets 1 10.25.32.1 (10.25.32.1) 0.880 ms 1.288 ms 1.291 ms 2 10.65.255.1 (10.65.255.1) 1.281 ms 1.960 ms 2.255 ms 3 172.21.1.33 (172.21.1.33) 5.357 ms 5.366 ms 5.347 ms 4 172.21.1.5 (172.21.1.5) 34.239 ms 34.268 ms 34.261 ms 5 172.21.1.6 (172.21.1.6) 27.104 ms * * ● This works because every IP packet has a TTL (Time To Live) value that is decreased with every hop. This is used to make sure that packets that can't be delivered are not send around in circles. ● Some types of packets can be blocked by your provider. To circument this, try to use a different packet type for traceroute (eg. traceroute -I)
- 15. 15 Basic tools: DNS tools ● There are several tools that can be used to lookup information about domain names or IP addresses: host, nslookup, dig and whois. ● Example: lookup a domain name or IP address $ host www.google.be www.google.be has address 74.125.136.94 www.google.be has IPv6 address 2a00:1450:4013:c01::5e $ host 74.125.136.94 94.136.125.74.in-addr.arpa domain name pointer ea-in- f94.1e100.net. ● With whois, you can get information about the domain name registrar
- 16. 16 Basic tools: Wi-Fi ● There are three basic cli tools for wireless networks: iwlist, iwconfig and wpa_supplicant ● iwlist is used to scan for networks $ iwlist wlan0 scan ● iwconfig is used to configure a wireless network interface $ iwconfig wlan0 essid MyNetwork ● wpa_supplicant is used to configure encryption for wireless networks ● There are several tools for hacking WEP-encrypted networks, but WPA(2) is still secure
- 17. 17 Basic tools: Wi-Fi access point ● Setting up a Wi-Fi access point (hotspot) can easily be done with the NetworkManager ● Doing it manually requires two tools: hostapd and dnsmasq. hostapd changes your wireless network interface in an access point, while dnsmasq is a basic DHCP and DNS server.
- 18. 18 Network analysis: netstat ● netstat is used to see what connections are open on your linux system. The options -n (no name resolving) and -t (only TCP connections) are quite useful $ netstat -nt Active Internet connections (w/o servers) Proto Recv-Q Send-Q Local Address Foreign Address State tcp 0 0 127.0.0.1:54395 127.0.0.1:5939 ESTABLISHED tcp 38 0 10.25.46.157:44261 23.21.220.152:443 CLOSE_WAIT tcp 0 0 10.25.46.157:51457 188.172.204.18:443 ESTABLISHED tcp 38 0 10.25.46.157:38185 54.192.95.120:443 CLOSE_WAIT tcp 0 0 10.25.46.157:48293 10.64.150.31:443 ESTABLISHED tcp 0 0 127.0.0.1:44554 127.0.0.1:48750 ESTABLISHED tcp 0 0 10.25.46.157:43487 74.125.136.189:443 ESTABLISHED tcp 38 0 10.25.46.157:37828 54.192.95.120:443 CLOSE_WAIT tcp 0 0 10.25.46.157:57952 10.64.150.31:443 ESTABLISHED tcp 38 0 10.25.46.157:48434 54.192.95.164:443 CLOSE_WAIT tcp 0 0 10.25.46.157:49543 10.64.150.31:443 ESTABLISHED tcp 0 0 127.0.0.1:53553 127.0.0.1:34226 ESTABLISHED tcp 0 0 10.25.46.157:42063 108.160.165.33:443 ESTABLISHED tcp 0 0 10.25.46.157:51878 198.252.206.25:443 ESTABLISHED tcp 0 0 10.25.46.157:57250 173.194.65.102:443 ESTABLISHED tcp 38 0 10.25.46.157:38281 23.21.219.56:443 CLOSE_WAIT tcp 38 0 10.25.46.157:37985 54.192.95.120:443 CLOSE_WAIT
- 19. 19 Network analysis: iptraf ● With iptraf (sometimes called iptraf-ng) you can see in great detail what and how much traffic passes through your system, right from the command line!
- 20. 20 Network analysis: Nmap ● Nmap (“Network Mapper”) is an extremely powerful utility for network discovery and security auditing ● Nmap can be used for: discovering devices on a network and what services they provide, detect what OS a host is running, ... ● Examples: – scan all hosts on a subnet and see what services they provide: nmap 192.168.0.* – the same thing, but 'in secret': nmap -sS 192.168.0.* – check what OS a host is running: nmap -O 192.168.0.1
- 21. 21 Network analysis: iperf ● iperf is used to measure the effective network bandwidth for TCP or UDP traffic between two hosts ● Example: – Host 1 (192.168.0.1): $ iperf -s ------------------------------------------------------------ Server listening on TCP port 5001 TCP window size: 85.3 KByte (default) ------------------------------------------------------------ [ 4] local 192.168.0.1 port 5001 connected with 192.168.0.10 port 47693 [ ID] Interval Transfer Bandwidth [ 4] 0.0-10.1 sec 113 MBytes 93.8 Mbits/sec – Host 2 (192.168.0.10): $ iperf -c 192.168.0.1 ------------------------------------------------------------ Client connecting to 192.168.0.1, TCP port 5001 TCP window size: 85.0 KByte (default) ------------------------------------------------------------ [ 3] local 192.168.0.10 port 47693 connected with 192.168.0.1 port 5001 [ ID] Interval Transfer Bandwidth [ 3] 0.0-10.0 sec 113 MBytes 94.7 Mbits/sec
- 22. 22 Network analysis: wireshark ● Wireshark is a network packet sniffer. It is used to capture packets on a network and do an advanced analysis. It is one of the most powerful open-source tools available for network debugging.
- 23. 23 Network analysis: tcpdump ● tcpdump is a command line program with the same functionality as wireshark $ tcpdump -i eth0 tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 65535 bytes 05:01:39.393785 ARP, Request who-has 10.25.41.51 tell 10.25.46.74, length 46 05:01:39.393842 ARP, Request who-has 10.25.40.100 tell 10.25.46.74, length 46 05:01:39.402624 ARP, Request who-has 10.25.31.8 tell 10.25.46.24, length 46 05:01:39.613080 ARP, Request who-has 10.25.31.11 tell 10.25.32.1, length 46 05:01:39.761154 IP 10.65.120.11.2052 > 10.65.120.255.1005: UDP, length 74 05:01:39.846803 ARP, Request who-has 10.25.31.8 tell 10.25.46.39, length 46
- 24. 24 Network analysis: etherape ● etherape provides a visual representation of who talks to who via your network connection
- 25. 25 Network services: remote cli with telnet and SSH ● There are two major ways to connect remotely to a host via the command line: telnet and SSH (Secure SHell) ● Telnet provides an insecure connection, while SSH is fully encrypted. SSH also offers other major features like port forwarding, login with keys and secure file transfer. Always use SSH if possible, all data send through telnet can easily be seen by someone else on the network! ● Example: try to login with telnet and SSH on a server. If you view the telnet traffic in wireshark you will see that everything (even the password) is send in the clear!
- 26. 26 Network services: file transfer with SSH ● SSH can be used to transfer files securely over any network (including the internet) ● Command line tool: scp $ scp localfile [email protected]:/home/pinguin/file ● Nautilus file manager can connect with the ssh:// or sftp:// prefixes: ● It is also possible to mount a directory locally with sshfs: $ sshfs [email protected]:/home/pinguin localdir
- 27. 27 Network services: file transfer with FTP ● FTP can be used in much the same way as SSH, but as with telnet, FTP is not encrypted and thus highly insecure! ● Command line tool: ftp $ ftp 192.168.0.1 Connected to 192.168.0.1 (192.168.0.1). 220 (vsFTPd 3.0.2) Name (192.168.0.1:maarten): pinguin 331 Please specify the password. Password: 230 Login successful. Remote system type is UNIX. Using binary mode to transfer files. ftp> put localfile ● Nautilus file manager can connect with the ftp:// prefix ● It is also possible to mount a directory locally with curlftpfs: $ curlftpfs ftp://pinguin:[email protected] localdir
- 28. 28 Network services: file transfer with NFS ● The Network File System is a filesystem designed to be shared over the network ● NFS is historically the oldest network filesystem available and is described in several official RFC's ● NFS supports the same user permission functionality like other linux filesystems ● NFS is not encrypted, and should only be used on trusted networks! ● NFS mounts can not be accessed in Nautilus, they need to be mounted by root ● Check the export list with showmount: $ showmount -e 192.168.0.1 Export list for 192.168.0.1: /home/pinguin (everyone) ● You can mount an NFS share like this: $ mount -t nfs 192.168.0.1:/home/pinguin localdir
- 29. 29 Network services: file transfer with Samba ● Samba is the open source implementation for the Microsoft Windows network share protocol (SMB- protocol) ● Samba is used more then NFS, it supports Windows hosts and has more features, but it is also not encrypted! ● Command line: use smbget to transfer a file ● Nautilus: use the smb:// prefix ● You can mount an SMB share locally like this: $ mount -t smbfs -o username=pinguin,password=pinguin //192.168.0.1/pinguin localdir
- 30. 30 Network services: file transfer with wget & curl ● wget and curl are both cli utilities that are used to get files via several protocols (they also support authentication): – wget: FTP, HTTP & HTTPS – curl: DICT, FILE, FTP, FTPS, GOPHER, HTTP, HTTPS, IMAP, IMAPS, LDAP, LDAPS, POP3, POP3S, RTMP, RTSP, SCP, SFTP, SMB, SMBS, SMTP, SMTPS, TELNET and TFTP $ wget http://192.168.0.1/index.html --2015-06-02 17:04:43-- http://192.168.0.1/index.html Connecting to 192.168.0.1:80... connected. HTTP request sent, awaiting response... 200 OK Length: 11510 (11K) [text/html] Saving to: ‘index.html’ index.html 100%[==========================>] 11.24K --.-KB/s in 0.001s 2015-06-02 17:04:43 (16.5 MB/s) - ‘index.html’ saved [11510/11510] $ curl http://192.168.0.1/index.html -o index.html % Total % Received % Xferd Average Speed Time Time Time Current Dload Upload Total Spent Left Speed 100 11510 100 11510 0 0 2126k 0 --:--:-- --:--:-- --:--:-- 2248k
- 31. 31 Network services: remote desktop ● The two most used types of remote desktop on linux are VNC (Virtual Network Computing) and RDP (Remote Desktop Protocol). VNC is an open-source standard, while RDP is a Microsoft protocol. ● Both VNC and RDP are not suitable for use over the internet because they are not encrypted ● There are several clients for linux: vinagre, krdc, rdesktop, … Use the one that you like most. ● Most distro's offer an easy way to setup VNC ● There are several commercial (but free) services that can be used on linux, like TeamViewer and Google Chrome remote desktop
- 32. 32 Network services: secure access ● Be very careful when using insecure services over a public network. Eavesdropping is easy! ● Use a secure alternative if possible (eg. ssh/telnet, sftp/ftp) ● If you must use an insecure service like VNC, there are two main solutions: – Tunneling/port forwarding through SSH $ ssh -L 3323:localhost:23 [email protected] $ telnet localhost 3323 – VPN (Virtual Private Network): this is an encrypted, virtual network over an existing, unsafe network
- 33. 33 Extra ● Firewall: iptables, ufw, fwbuilder ● Bridging: brctl ● VLAN: vconfig ● Traffic shaping: tc ● Anonymity online: Tor ● Add blocking



















![21
Network analysis: iperf
●
iperf is used to measure the effective network bandwidth for
TCP or UDP traffic between two hosts
● Example:
– Host 1 (192.168.0.1):
$ iperf -s
------------------------------------------------------------
Server listening on TCP port 5001
TCP window size: 85.3 KByte (default)
------------------------------------------------------------
[ 4] local 192.168.0.1 port 5001 connected with 192.168.0.10 port 47693
[ ID] Interval Transfer Bandwidth
[ 4] 0.0-10.1 sec 113 MBytes 93.8 Mbits/sec
– Host 2 (192.168.0.10):
$ iperf -c 192.168.0.1
------------------------------------------------------------
Client connecting to 192.168.0.1, TCP port 5001
TCP window size: 85.0 KByte (default)
------------------------------------------------------------
[ 3] local 192.168.0.10 port 47693 connected with 192.168.0.1 port 5001
[ ID] Interval Transfer Bandwidth
[ 3] 0.0-10.0 sec 113 MBytes 94.7 Mbits/sec](https://image.slidesharecdn.com/networktools-150604094513-lva1-app6891/85/Linux-network-tools-Maarten-Blomme-21-320.jpg)








![30
Network services: file transfer with wget & curl
●
wget and curl are both cli utilities that are used to get files
via several protocols (they also support authentication):
– wget: FTP, HTTP & HTTPS
– curl: DICT, FILE, FTP, FTPS, GOPHER, HTTP, HTTPS, IMAP, IMAPS, LDAP, LDAPS,
POP3, POP3S, RTMP, RTSP, SCP, SFTP, SMB, SMBS, SMTP, SMTPS, TELNET and
TFTP
$ wget http://192.168.0.1/index.html
--2015-06-02 17:04:43-- http://192.168.0.1/index.html
Connecting to 192.168.0.1:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 11510 (11K) [text/html]
Saving to: ‘index.html’
index.html 100%[==========================>]
11.24K --.-KB/s in 0.001s
2015-06-02 17:04:43 (16.5 MB/s) - ‘index.html’ saved [11510/11510]
$ curl http://192.168.0.1/index.html -o index.html
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 11510 100 11510 0 0 2126k 0 --:--:-- --:--:-- --:--:-- 2248k](https://image.slidesharecdn.com/networktools-150604094513-lva1-app6891/85/Linux-network-tools-Maarten-Blomme-30-320.jpg)


