Mastering IoT Design: Sense, Process, Connect: Processing: Turning IoT Data into Intelligence
- 1. Sponsored by: EETimes University Course: Mastering IoT Design: Sense, Process, Connect Day 2: Processing: Turning IoT Data into Intelligence Presented by: Deepak Shankar Founder and Vice President, Technology Mirabilis Design Inc. 1
- 2. Sponsored by: Our Speaker: 2 Deepak Shankar Founder and Vice President, Technology Mirabilis Design Inc.
- 3. Sponsored by: Agenda Introduction to processing at Edge Computing Trends Challenges Case Study and Analysis Conclusion 3
- 4. Sponsored by: Enabling Data Center Connected Devices • 50 billion IoT devices generate 79.4ZB requires – Huge bandwidth – Massive and expensive cloud processing – 99.999% reliability – Cybersecurity – Variable response latency • Solution: Edge Computing – Process and analyze data locally – Make instant decisions • Applications that benefit from Edge Computing – Safety, health care, security, autonomous vehicles, smart cities – Manufacturing, VR, AR, stream services, customer care – Smart homes 4
- 5. Sponsored by: Architecture of Edge Computing • Edge computing is at the outermost edge of network • Sensor data is collected, filtered, compressed, and encrypted locally and a small quantity is sent to the cloud • Network transfer can be done in batch or offline • Increases the number of processing layers • Server location is critical • Tracking and diagnostic is critical and adds layers 5
- 6. Sponsored by: Trends • Edge gateway separates the processing and end-point – Increases the battery life of the connected devices – Add more sensors and trackers at the device • Example – Smart electricity meters generate lots of measurements at short intervals – Using data from temperature, light and other sensors, Edge Computing can respond to environment changes quickly, reducing operational cost and increasing comfort • Filtering edge data reduces cloud transfers, which increases battery life • Example – Mercedes AMG F1 team filters less valuable telemetry and transfers relevant data for offline processing 6
- 7. Sponsored by: Trends • There is no “single” edge – Depending on the application, the edge architecture will be different – Manufacturing plant [Edge servers and gateways aggregate multiple servers and devices in a distributed location] – Telecommunications provider [architectures break down into a provider far edge, a provider access edge, and a provider aggregation edge] • Edge computing doesn’t need to be connected – An edge device running autonomously in a hard-to-reach place like a rural mining site can keep running when a connection drops – When connection resumes, the system can sync and transfer data 7
- 8. Sponsored by: Computing Trends • Edge is getting “foggy” – Fog computing adds a new filtering layer – Example • Temperature sensor generates data every one second • With fog layer, data that meet the metrics are sent to cloud • Advanced communication and AI technology enable mass connection – Wi-Fi 6 and 5G/6G covers most edge devices – About 99.4% of the physical objects are still unconnected 8
- 9. Sponsored by: Challenges • Latency (Response times) – Applications, like the health care, financial transactions, and automotive cannot tolerate latency – Stringent requirements need to be met and thus the components need to be selected to meet such needs • Bandwidth – Applications, like Smart surveillance systems and traffic management, require significant bandwidth – Buffer overflow, retransmissions can severely affect application performance 9
- 10. Sponsored by: Challenges • Edge has same cyber risk as any other local network server – “AT&T Cybersecurity Insights report: Securing the Edge” found that 74% of businesses have been compromised – Sniffing attacks, DDoS, supply chain attacks, etc. • Power – Edge servers rely on battery as their primary power source – IoT device batteries are not easily replaceable • Fire alarm sensors, underwater sensors, wildlife tracking devices, medical implants, space and satellite devices 10
- 11. Sponsored by: Designing Edge Computing Requires Early Architecture Planning • Early system model can eliminate bottlenecks and measure – Processing requirements – Expected application latency – Required bandwidth for seamless operation – Power profile of the edge devices – Behavior of the system under different failure conditions and threats • To enable this, the system modeling solution requires IP libraries and simulators for hardware, software, and network – VisualSim Architect from Mirabilis Design ticks all the boxes
- 12. Sponsored by: Why is System Performance Exploration Required? Scheduling/Arbitration proportional share WFQ static dynamic fixed priority EDF TDMA FCFS Communication Templates Architecture # 1 Architecture # 2 Computation Templates DSP AI GPU DRAM CPU FPGA m E DSP TDMA Priority EDF WFQ RISC DSP LookUp Cipher AI DS P CPU GP U mE DD R static Which architecture is better suited for our application? 12
- 13. Sponsored by: Block Diagram of Data-Enabled Application Device 1 AFE ARM/ RISC-V core BLE/ Wifi/ 5G Radio Transceiv er Network Hub [Edge Gateways + Fog layers] Data Center
- 14. Sponsored by: IoT to Data Center Model • Power consumption of each device • Optimal HW and SW configuration to meet the end-to- end application timing deadline • Performance with Big data and fast data workloads 14
- 15. Sponsored by: Architect Hardware-Software of Edge Device DRAM Display IO A M B A A X I B u s CPU GPU Display Ctrl P C I e Video Camera SRAM Packet • System Overview – Camera: 30fps, VGA corresponds – CPU: Multi-core ARM Cortex-A53 1.2GHz – GPU: 64Cores(8Warps×8PEs), 32Threads, 1GHz – DisplayCtrl: DisplayBuffer 293,888Byte – SRAM: SDR, 64MB, 1.0GHz – DRAM: DDR3, 64MB, 2.4GHz Explore at the board- and semiconductor-level to size uP/GPU, memory bandwidth and bus/switch configuration 15
- 16. Sponsored by: Conducting Architecture Trade-off • By changing the amount of video input data (packet numbers), observe the SRAM -> DRAM transfer performance and examine the upper limit performance of the video input that the system can tolerate. 210 packets/s 12ms 21 packets/s 414us 300 packets/s • 250 packets/s is the system limit • With 300 packets/s, simulation cannot be executed due to FIFO buffer overflow. 16
- 17. Sponsored by: Compare Edge Compute System using ARM vs RISC-V Processors Using ARM Cores Using RISC-V Cores NOTE: Depending on the application profile run, the performance and power observed would vary • Compare application latency with and without custom instructions tailored for AI and data filtering • Average power consumption in different scenarios 17
- 18. Sponsored by: Selecting Network Interface to Data Center Using 1000 Mbps links 1000 Mbps link + Edge Processing (Single- and multi-core) Sizing of network resources to Edge devices is important to get optimal performance 18
- 19. Sponsored by: Bluetooth (BLE) Power State Transition (FSM) • Depending on the abstraction required, the subsystems can be built with great details • Here, Bluetooth module has been modeled with all the state transition details 19
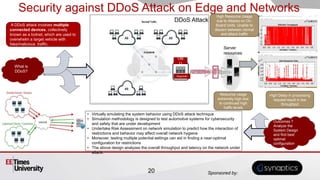
- 20. Sponsored by: Resource usage extremely high due to continued high traffic levels Security against DDoS Attack on Edge and Networks A DDoS attack involves multiple connected devices, collectively known as a botnet, which are used to overwhelm a target vehicle with fake/malicious traffic. • Virtually emulating the system behavior using DDoS attack technique • Simulation methodology is designed to test automotive systems for cybersecurity and safety that are under development • Undertake Risk Assessment on network simulation to predict how the interaction of restrictions and behavior may affect overall network hygiene • Moreover, testing multiple potential settings can aid in finding a near-optimal configuration for restrictions • The above design analyzes the overall throughput and latency on the network under attack. High Delay in processing request result in low throughput What is DDoS? DDoS Attack Outcomes ? Analyze the System Design and find best optimal configuration High Resource Usage due to Attacks on On- Board Units. Unable to discern between normal and attack traffic OB U Diagnostic 20
- 21. Sponsored by: Failure and Cybersecurity Threat Analysis Normal Operation Under Attack Effective throughput is reduced and significant bursts in response times are observed 21
- 22. Sponsored by: Evaluate Bottlenecks and Security Threats Stable Response Time Malicious Devices are Blacklisted Without Firewall With Firewall 22 22
- 23. Sponsored by: Edge Computing Architecture is Key for Data Intelligence • System exploration must be performed during the planning stage • Distribution of processing to IoT, edge, fog, and data center must be based on the application requirements • Edge, Network, and IoT System specification must be fully validated for both power-performance and failure-security • Data size, processing needs, and software tasks must be determined in advance • System must be scalable for future requirements • Edge computing is the Future
- 24. Sponsored by: About Mirabilis Design Software Company based in Silicon Valley Integrates Model-based Systems Engineering with the electronics development flow Development and Support Centers USA, India, China, South Korea, Japan and Europe VisualSim Architect - Modeling and Simulation Software Graphical modeling, multi-domain simulator, system-level IP, analysis tools and open API Market Segments Semiconductors, Automotive and, Aerospace and Defense Design Enablement Architecture trade-offs, system validation, early functional testing and communication Networking 24






![Sponsored by:
Trends
• There is no “single” edge
– Depending on the application, the edge architecture will be different
– Manufacturing plant [Edge servers and gateways aggregate multiple
servers and devices in a distributed location]
– Telecommunications provider [architectures break down into a provider far
edge, a provider access edge, and a provider aggregation edge]
• Edge computing doesn’t need to be connected
– An edge device running autonomously in a hard-to-reach place like a rural
mining site can keep running when a connection drops
– When connection resumes, the system can sync and transfer data
7](https://image.slidesharecdn.com/eetimesuniversityday2ch-230920120529-2abcbd08/85/Mastering-IoT-Design-Sense-Process-Connect-Processing-Turning-IoT-Data-into-Intelligence-7-320.jpg)





![Sponsored by:
Block Diagram of Data-Enabled Application
Device 1
AFE
ARM/
RISC-V
core
BLE/
Wifi/ 5G
Radio
Transceiv
er
Network
Hub
[Edge Gateways
+ Fog layers]
Data
Center](https://image.slidesharecdn.com/eetimesuniversityday2ch-230920120529-2abcbd08/85/Mastering-IoT-Design-Sense-Process-Connect-Processing-Turning-IoT-Data-into-Intelligence-13-320.jpg)