[muCon2017]DevSecOps: How to Continuously Integrate Security into DevOps
- 1. DevSecOps: How to Continuously Integrate Security Into DevOps with the Open Source Way Daniel Oh / @danieloh30
- 2. ABOUT ME ● Senior Specialist Solution Architect at Red Hat ● Agile & DevOps Community of Practice Manager at Red Hat [email protected] @danieloh30 ● Transform Microservices apps ● Container Platform, PaaS ● Java EE with MicroProfile, JBoss for Cloud Native Runtimes ● Evangelism
- 4. HOW DEV AND OPS VIEW SECURITY?
- 5. WHY DevSecOps? ● DevOps “purists” point out that security was always part of DevOps ● Did people just not read the book? Are practitioners skipping security? ● DevSecOps practitioners say it’s about how to continuously integrate and automate security at scale
- 6. Source: IT Revolution, DevOps Enterprise abstract word cloud, 2014.
- 7. Source: IT Revolution, DevOps Enterprise abstract word cloud, 2014.
- 8. Has much changed? Ironically. Shift-left much?
- 9. GLASS HALF EMPTY, GLASS HALF FULL “... we estimate that fewer than 20% of enterprise security architects have engaged with their DevOps initiatives to actively and systematically incorporate information security into their DevOps initiatives; and fewer still have achieved the high degrees of security automation required to qualify as DevSecOps.” “By 2019, more than 70% of enterprise DevOps initiatives will have incorporated automated security vulnerability and configuration scanning for open source components and commercial packages, up from less than 10% in 2016.” Gartner Inc. September 2016
- 10. …utilizing billions of available libraries, frameworks and utilities ● Not all are created equal, some are healthy and some are not ● All go bad over time, they age like milk, not like wine ● Data shows enterprises consumed an average 229,000 software components annually, of which 17,000 had a known security vulnerability. Applications are ‘assembled’…
- 11. ● Cloud ● DevOps ● Open Source Software innovation explosion ● Containers/Microservices ● Digital transformation THE PERFECT STORM
- 12. NEW PARADIGM …. AND SECURITY ON DEVOPS REUSE MICROSERVICES AUTOMATION IMMUTABILITY PERVASIVE ACCESS SPEED SOFTWARE DEFINED CONTAINERS RAPID TECH CURN FLEXIBLE DEPLOYS
- 13. NEW PARADIGM …. AND SECURITY ON DEVOPS REUSE MICROSERVICES AUTOMATION IMMUTABILITY PERVASIVE ACCESS SPEED SOFTWARE DEFINED CONTAINERS RAPID TECH CURN FLEXIBLE DEPLOYS MANAGEMENT RISKS
- 14. YOU MANAGE RISK BY ● Securing the Assets ● Securing the Dev ● Securing the Ops ● Securing the APIs OPEN SOURCE WAY
- 15. SECURING THE ASSETS ● Building code ○ Watching for changes in how things get built ○ Signing the builds ● Built assets ○ Scripts, binaries, packages (RPMs), containers (OCI images), machine images (ISOs, etc.) ○ Registries (Service, Container, App) ○ Repositories (Local on host images assets) Safe at Titan Missile Museum https://upload.wikimedia.org/wikipedia/commons/5/59/Red_Safe%2C_Titan_Missile_Museum.jp g
- 16. Is your public sources secure and available?
- 17. SECURING THE SOFTWARE ASSETS - E.G. IMAGE REGISTRY Public and private registries ● Do you require a private registry? ● What security meta-data is available for your images? ● Are the images in the registry updated regularly? ● Are there access controls on the registry? How strong are they? Who can push images to the registry?
- 18. SECURING THE ASSETS HEALTH - Security freshness ● Freshness Grade for container security. ● Monitor image registry to automatically replace affected images ● Use policies to gate what can be deployed: e.g. if a container requires root access, prevent deployment
- 19. SECURING THE DEVELOPMENT PROCESS ● Potentially lots of parallel builds ● Source code ○ Where is it coming from? ○ Who is it coming from? ● Supply Chain Tooling ○ CI tools (e.g. Jenkins) ○ Testing tools ○ Scanning Tools (e.g. Black Duck, Sonatype) Boeing's Everett factory near Seattle https://upload.wikimedia.org/wikipedia/commons/c/c8/At_Boeing%27s_Everett_factory_near_Seattle_%289130160595%29.jpg Creative Commons
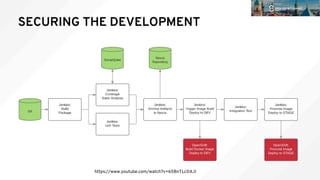
- 20. Security & continuous integration ● Layered packaging model supports separation of concerns ● Integrate security testing into your build / CI process ● Use automated policies to flag builds with issues ● Trigger automated rebuilds MANAGING CONTAINER BUILDS Operations Architects Application developers
- 22. SECURING THE OPERATIONS Deployment ○ Trusted registries and repos ○ Signature authenticating and authorizing ○ Image scanning ○ Policies ○ Ongoing assessment with automated remediation Mission Control - Apollo 13 https://c1.staticflickr.com/4/3717/9460197822_9f6ab3f30c_b.jpg
- 23. CONTAINER DEPLOYMENT PERMISSIONS (SCC)
- 24. SCAN YOUR IMAGES (ATOMIC SCAN)
- 25. SECURING THE OPERATIONS Lifecycle ○ Blue Green or A/B or Canary, continuous deployments ○ Monitoring deployments ○ Possibly multiple environments
- 26. SECURING THE OPERATIONS - LOGGING EFK Stack ● ElasticSearch, Fluentd, Kibana ● Based on log aggregation ● Event system - all events container, system, kubernetes, captured by EFK and issues or errors ● Good for ad hoc analytics ● Good for post mortem forensics because of extensive log information
- 27. SECURING THE OPERATIONS - MONITORING AND METRICS
- 28. MONITORING: HAWKULAR ● REST API to store and retrieve availability, counter, and gauge measurements ● Visualization and alerting ● Application performance management ● Integration with ManageIQ (cloud mgmt) ● Most associated with large scale central IT teams with lots of apps
- 29. MONITORING: PROMETHEUS ● Time series data model identified by metric name and key/value pairs ● Collection happens via a pull model over HTTP ● Values reliability even under failure conditions over 100% accuracy ● Most associated with web-scale DevSecOps
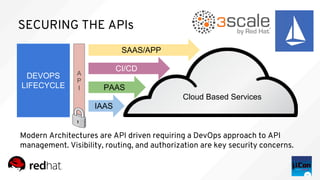
- 30. SECURING THE APIs DEVOPS LIFECYCLE SAAS/APP PAAS IAAS A P I Modern Architectures are API driven requiring a DevOps approach to API management. Visibility, routing, and authorization are key security concerns. Cloud Based Services CI/CD
- 31. THE SECURITY ECOSYSTEM ● Identity and Access management / Privileged Access Management ● External Certificate Authorities ● External Vaults / Key Management solutions ● Container content scanners & vulnerability management tools ● Container runtime analysis tools ● Security Information and Event Monitoring (SIEM) For enhanced security, or to meet existing policies, integrate with enterprise security tools, such as
- 32. SECURITY ECOSYSTEM: OPENSHIFT PRIMED Sysdig NGINX AquaSecurityJFrog, Inc. Signal Sciences Cisco Contiv Aporeto big switch Sonatype f5 Black Duck NeuVector Treasure Data Contrail Tremolo nuagenetworks dynatrace Avi Networks @danieloh30
- 33. THANK YOU & QUESTIONS Contacting me: [email protected] / @danieloh30